
OPTIMISED MODEL OF INFORMATION TRANSFER IN
VIRTUAL ENTERPRISES IN CLOUD COMPUTING
ENVIRONMENT
Rongqian Ni, Runtong Zhang
Institute of Information Systems, Beijing Jiaotong University, #3 Shangyuancun, Haidian District, 100044, China
Yuan Lin, Thérèse Libourel
Université Montpellier2, LIRMM, 161 rue Ada, 34392 Montpellier Cedex 5, France
Keywords: Cloud computing, Virtual enterprises, Communication mechanism.
Abstract: The information transfer in a virtual enterprise is a crux of achieving effective integral management of
virtual enterprises. We implement cloud computing in information transfer of virtual enterprises, the model
of which is simulated by JSP language.
1 INTRODUCTION
With the development of economic globalization
and the deepening of enterprise management
practices, virtual enterprise management (VEM) has
gradually become one of the most important ways to
enhance each company’s competitiveness. The
achievement of virtual enterprise management is
greatly due to the mechanism of communication and
information processing. Also data transfer, data
collection, data storage and data processing are very
important. In the current Internet environment,
however, due to the limitations of information
infrastructure platform itself, it is difficult to truly
solve the problems of virtual enterprise problems.
The main characteristics of cloud computing is that
the computing resources can be dynamically and
efficiently allocated, and buyers can maximize their
use of computing resources without managing the
underlying complexity of this technology, which can
serve to solve the existing problems of virtual
enterprise management(Brian Hayes, 2008). In
order to meet the requirements of future
development of virtual enterprise management, this
paper will propose a novel communication
mechanism of virtual enterprises in cloud computing
environment, and then implement JSP to achieve the
model.
2 LITERATURE REVIEW
Cloud computing is a network carrier which
provides the infrastructure, platform, software and
other services to form a large-scale integration of
scalable computation, storage, data, applications and
other distributed computing resources to conduct a
dynamic and easily extended super-computing
model ( Lizhe Wang et al,2008 ) . In the cloud
computing model, users just need to pay the fee to
cloud computing service providers, and then easily
obtain the required computing, storage and other
resources through the network. With future software
installed and data stored in the "cloud" side, users
are able to accomplish remote computing, data
processing through a browser with results displayed
in the client side.(Sahinoglu, M. and Cueva-Parra,
L., 2011)
The commercial value of cloud computing may
be reflected as follows: on the one hand, resources
provided by cloud computing is cheaper than
companies themselves can provide. The most
important reason for companies to willingly give up
the control of their own resources and allow them to
exist in a virtual cloud is cost saving, including the
management costs and application costs. (Michael
Miller, 2008) On the other hand, with greater
flexibility and scalability, cloud computing can be
195
Ni R., Zhang R., Lin Y. and Libourel T..
OPTIMISED MODEL OF INFORMATION TRANSFER IN VIRTUAL ENTERPRISES IN CLOUD COMPUTING ENVIRONMENT.
DOI: 10.5220/0003442301950202
In Proceedings of the 13th International Conference on Enterprise Information Systems (ICEIS-2011), pages 195-202
ISBN: 978-989-8425-56-0
Copyright
c
2011 SCITEPRESS (Science and Technology Publications, Lda.)
virtualized between different applications in order to
increase the utility of Servers (Vouk, M.A., 2008).
With considerable advantages stated above, this
paper indicates a new method for communication
mechanism of virtual enterprises using cloud
computing.
3 MODEL DESIGN
3.1 Organization Structure
In order to adapt to the dynamic variability of the
external environment, the organization structure of
virtual enterprise is an “a myriad of stars surround
the moon” type distributed topology. According to
the needs of a task, the organization structure can be
divided into several virtual work teams (the smallest
organization unit), which consist of working groups
from each business partner. The agility of partners
must be considered when designing virtual
enterprise organization structure, which means the
partners should be agile enterprises themselves. The
upper management agency is Virtual Enterprise
Operation Management Center (referred to as
VEOMC), which manages the operation of virtual
enterprises. (Assimakopoulos, 2006)Based on the
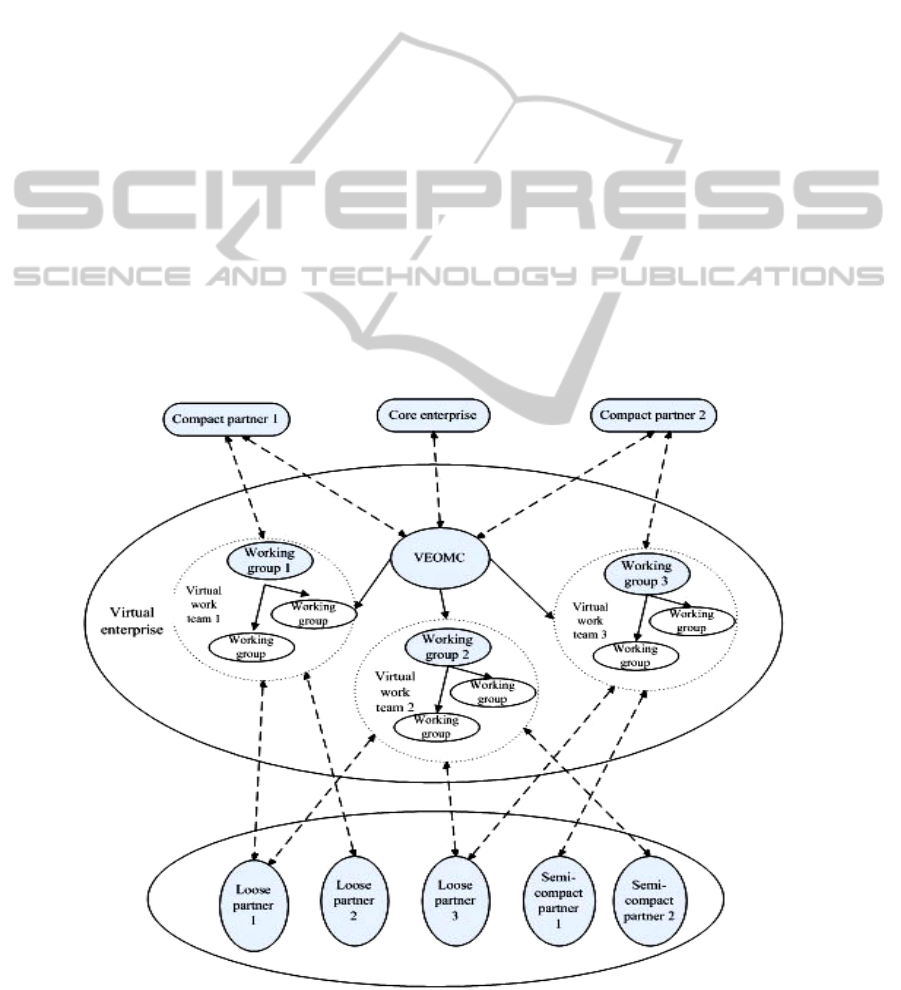
above principles of organization design, Figure 1
shows a typical organization structure of virtual
enterprise.
It is known from Figure 1 that the VEOMC is
composed of core enterprise and compact partners.
Virtual work team, consisting of working groups, is
a unit of sub-task, and each virtual work team is led
and managed by a core working group. Core
working group generally comes from the core
enterprise or compact partners, such as compact
partner 1 of working group 1 from virtual work team
1 shown in Figure 1; other working groups come
from the compact or semi-compact partners. Once a
sub-task is completed, the virtual work team will be
disintegrated, and the working groups will be return-
type partners. When new tasks arise, the working
groups form a new virtual work team. All of the
above processes are accompanied by data transfer,
data collection, data storage and data processing,
making the management of virtual enterprises looks
very complicated. In order to establish the model,
we set aside some of details and simplify the process
of virtual enterprise management.
Figure 1: Organization structure of virtual enterprise.
ICEIS 2011 - 13th International Conference on Enterprise Information Systems
196
3.2 Model Design
3.2.1 Idea Review
In a virtual enterprise, each company that
participates in a sub-task, whether it is core
enterprise, compact partner, semi-compact partner,
or loose partner, needs to share information which
includes the performance of a partner completing a
sub-task, the constraint information that VEOMC
manages each virtual work team. (Dragoi George et
al, 2006) Obviously, it is of great importance to
share this information as soon as possible. Suppose
that there is a communication network being used in
the virtual enterprise, which allows data set (or file)
to be transferred from one company computer to
another. This example is illustrated in Figure 2:
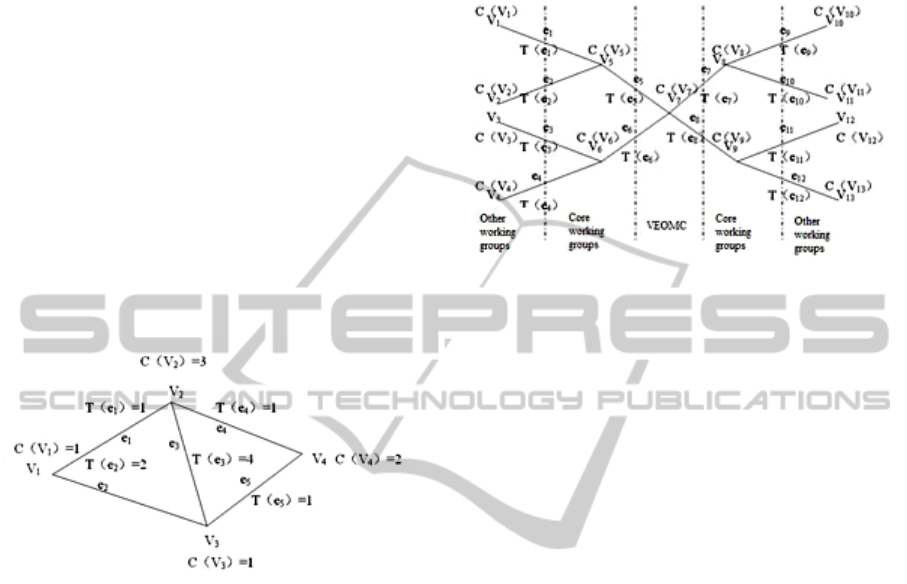
In Figure 2, vertex V1, V2... Vm refers to
computers that process information in each virtual
Figure 2: Sample graph.
enterprise entity; edge e1, e2... en, means file
information to be transferred; T(ex) means time
needed to transfer Files ex; C(Vy) means the
processing capacity of computer Vy, i.e. the number
of files that can be transferred at a time. File transfer
must occupy all the time required of two relevant
computers transferring files. C(Vy) = 1 means that
the computer Vy can only transfer one file once.
What needs to be solved here is to arrange the
transfer so as to cost as little time as possible to
complete the transfer of all documents. The total
time is called “completion time” in the Operations
Research. (Hua Chen et al, 2006)
To facilitate the establishment of the model, the
problem is described as follows: there are 13 entities
in the virtual enterprise model, including one
VEOMC, four core working groups and eight other
working groups. Assume that each entity has only
one computer, and each computer is represented as a
vertex in Figure 3. There are 12 files to be
transferred between entities within a day. Edges in
Figure 10 represent file transfer. In this network, for
all x, y, T(ex) = 1, C(Vy) = 1, we are to find out the
schedule of the transfer and the corresponding
completion time. The graphical model is shown in
Figure 3:
Figure 3: Model Design.
It is concluded from Figure 3 that we should
figure out the shortest time of file transfer with
constrains of limited computer processing capacity
and transfer time.
To simplify the calculation, here are some basic
assumptions:
(1) Communication network graph is a simple
undirected graph. There are no overlapping
edges between any two vertices, which means
all the information transferred between two
computers can be included in one file.
(2) Preparation time of files to be transferred is
negligible, namely, zero. So the process of
communication network file transfer can be
continuous.
(3) The transfer time of each file is a fixed number.
(4) All files are independent of each other, and there
is no order or priority among them.
(5) There allows no interruption during the process
of transfer. Once a file is being transferred, it
has to be finished continuously.
(6) Communications network won’t break down
during the transfer process.
(7) Suppose the time required is identical, T(ex) =
1.
(8) Each computer can only process one file once,
i.e. C(Vy) = 1.
3.2.2 Model and Solution in the Local
Cluster Environment
The assumption that the transfer time of each file
T(ex) = 1, and each computer's processing capacity
C(Vy) = 1, makes the problem-solving relatively
simple. If all the files are to be transferred in the
shortest possible time, files have to be processed in
OPTIMISED MODEL OF INFORMATION TRANSFER IN VIRTUAL ENTERPRISES IN CLOUD COMPUTING
ENVIRONMENT
197
batches, and the batch number is the minimum
completion time. There are different files being
transferred in each unit of time, which correspond to
the edge set without the same endpoint in the graph,
namely, one match in Figure 3. Different matches
have different edges, and the union set constitute
Figure 3. Thus, the optimal transfer schedule is to
divide Figure 3 into as few non-overlapping matches
as possible, the number of which is the optimal
completion time.
Based on the maximum cardinality bipartite
graph matching algorithm, method is designed as
follows:
Step 1: Let E (u) be the set of all edges of G, set
STAGE = 1.
Step 2: Calculate a maximum cardinality match of
E(u); the edges in the match are noted as
“labelled”.
Step 3: Remove the labelled edges from E(u).
Step 4: If E(u) is not empty, go to step 5; otherwise
terminate the calculation, STAGE is the
optimal completion time.
Step 5: STAGE = STAGE +1, return to Step 2.
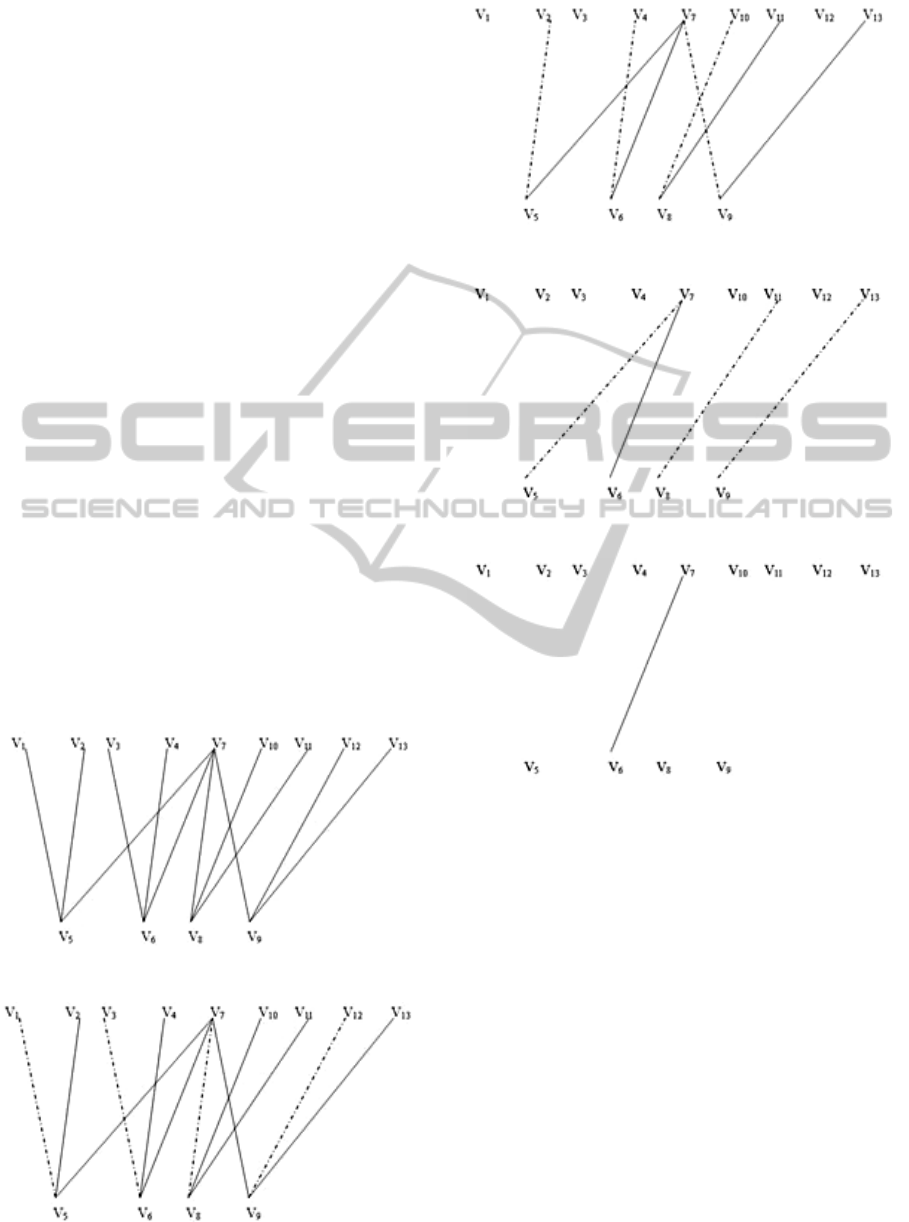
Reflected in the form of bipartite graph of
Figure 3, we get Figure 4. Find out the maximum
cardinality match in Figure 4 (dashed-line edges in
Figure 5), the corresponding file of whose edge is to
be transferred in the first batch. Remove these edges
to get Figure 6. Repeat the above steps in Figure 6 to
get Figure 7 and again Figure 8.
Figure 4: Step 1.
Figure 5: Step 2.
Figure 6: Step 3.
Figure 7: Step 4.
Figure 8: Step 5.
By the above analysis of the solution, 4 files are
transferred in the first unit of time, then 4 files in the
second unit of time, 3 files in the third and 1 file in
the fourth. The completion time is 4 units of time,
which is also the optimal completion time.
3.2.3 Model in Cloud Computing
Environment
In the cloud computing environment, the
participating entities share data processing capability
from the “cloud” through browsers. Virtual
enterprises can provide information infrastructures
and integrate all the virtual enterprise data into one
global database without considering the data
location and the type of systems used in various
entities. Currently, the various entities in the virtual
enterprise use the heterogeneous IT environment,
ICEIS 2011 - 13th International Conference on Enterprise Information Systems
198
which means the data source systems are different.
(Cheng, G et al, 2010) According to the agreement
on data source systems that provide item data,
several virtualized levels need to be set to the virtual
enterprise:
(1) If all the participating entities are in favour of a
uniform flat file format of providing item data,
then the virtual enterprise can use a distributed
file system. If so, the virtual enterprise can
access to data on the basis of flat file.
(2) If the agreement only includes item data file
format itself, but with a different file type, then
the virtual enterprise requires a virtual data layer,
which is used to shield different file types and
provide a unified access to source of data.
(3) If the agreement merely includes the format of
the item data, rather the types of data source,
then the virtual enterprise need to be able to
integrate data provided by different data systems
transparently in a virtual layer, such as relational
or non-relational DBMS, and a variety of
different types of flat files.
To simplify the modeling, this article assumes
that global virtual database is within VEOMC, and
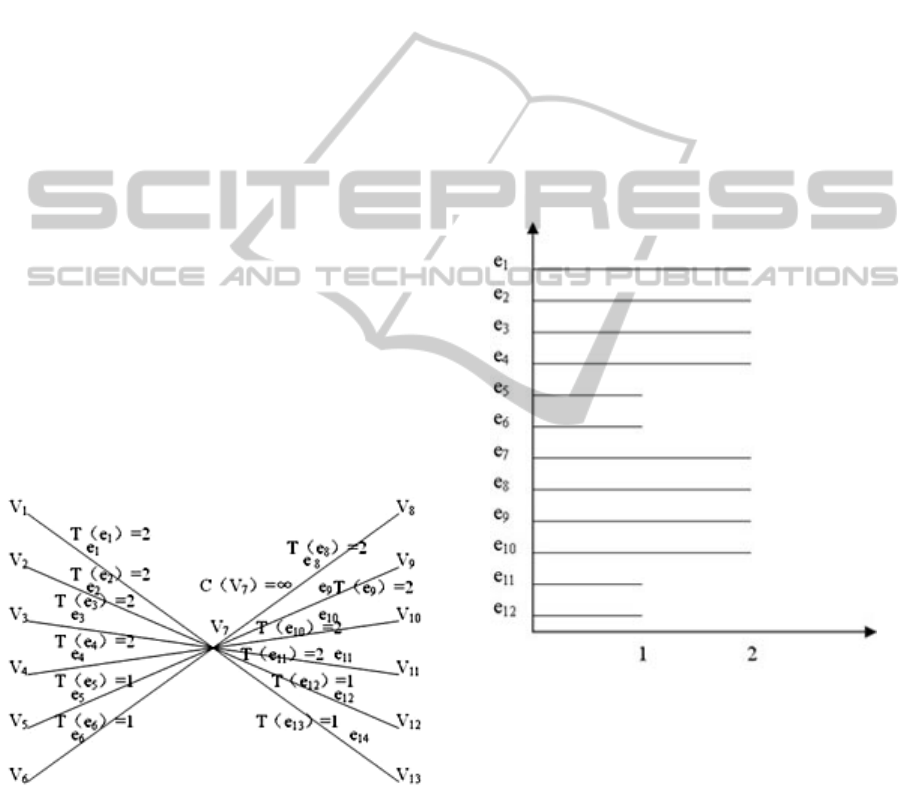
then Figure 3 can be transformed into Figure 9. In
Figure 9, the C(V7) is set to ∞, because the
processing capacity of the entire communication
system can be utilized based on the purchased
capability according to characteristics of cloud
computing, the power of which is much larger than a
single computer's data processing capacity.
Figure 9: Brief graph of the model in cloud computing
environment.
In Figure 9, since both the processing capacity
and the transfer time is not all 1, the maximum
cardinality matching algorithm cannot be directly
used to calculate the completion time. A method to
solve this problem is to introduce the "pseudo-
vertex" concept, that is, if the capacity of a vertex is
3, then introduce two pseudo-vertexes in the original
image, and set 1 to the capacity of original vertex
and “pseudo-vertexes”. If so, maximum cardinality
matching and maximum weight matching algorithm
can be used in the changed graph. Meanwhile, the
edge formed between “pseudo-vertexes” is
“equivalent edge”.
Due to the “pseudo-vertex” and “equivalent
edge”, even though the maximum cardinality
matching and the maximum weight matching
algorithm (transfer time is inconsistent) can be used
in the transformed graph G’= (V’, E’) (the capacity
of each vertex is 1), the match can only contain one
edge of all the “equivalent edges”. So once an edge
is selected into the match, other equivalent edges
have to be removed immediately from the graph.
Based on the above analysis, due to the use of
maximum cardinality matching and maximum
weight matching algorithms, we get Figure 10.
Figure 10: The maximum weight matching algorithm.
According to Figure 10, it is obvious that it takes
only two units of time to transfer 12 files, which is
the optimal completion time.
3.2.4 Model Comparison and Extension
As is elaborated above, the optimal completion time
in cloud computing environment is two units less
than that in non-cloud environment, which is the
advantage of the cloud in data processing. It is
because the hierarchical progression is reduced in
cloud computing environment where the transferred
time decreases.
OPTIMISED MODEL OF INFORMATION TRANSFER IN VIRTUAL ENTERPRISES IN CLOUD COMPUTING
ENVIRONMENT
199

To facilitate the modeling, this paper utilizes
the simplest fact-based chain structure of virtual
enterprise modeling. But in reality, the structure of
virtual enterprise network is much more complex
than the model, and the mode of composition is
multi-layered. With the increase of virtual enterprise
structure complexity, extended analysis indicates a
continuous decrease of completion time. Imagine if
all the resources in the world are run in the cloud
computing platform, the savings of completion time
will be amazing.
Meanwhile, since all the virtual enterprise
information platforms share the cloud computing
environment, it is reasonable to view all the
processing power in a virtual global database,
making the information transfer even simpler. The
whole virtual enterprise can be viewed as a "tree",
the global database is the “root” of the “tree”.
Therefore maximum weight of the path of the “tree”
can be used to obtain the “optimal completion time”.
4 JSP SIMULATION
This section aims to find out a solution of the
maximum weight of the tree by JSP language, with
the results shown directly in the form of web page,.
4.1 Model Algorithm
The maximum weight recursive backtracking
algorithm is used in the accomplishment of the
model, which is as follows:
Step 1: Look for leaves from all nodes, and assign an
array to all the leaves.
Step 2: Calculate the length of the array.
Step 3: Look for the parent node of each leaf, and
then the parent node which is the child node
of the previous parent node until you find the
root up. Calculate the weight of each path.
Step 4: Calculate all the weights of each full-path,
and compare to get the maximum value.
The logic flow chart of the algorithm is shown in
Figure 11.
The algorithm code is referred to Appendix.
4.2 Database Interface Design
4.2.1 Datasheet Design
ACCESS is used as the database to achieve the
model. The specific design shown in Table 1:
Figure 11: Logic flow chart of algorithm.
Table1: Datasheet Design.
Data item Code Type Length
Identifier
id long integer
Parent node
parent_id text 8
Child node
son_id text 8
Weight
total_weight float
4.2.2 Database Interface Code
The interface code is as follows:
<%
Class.forName("sun.jdbc.odbc.JdbcOdb
cDriver") ;
Connection conn =
DriverManager.getConnection("jdbc:odbc:
parent_son");
Statement、
stmt=conn.createStatement(ResultSet.TYP
E_SCROLL_SENSITIVE,ResultSet.CONCUR_UPD
ATABLE) ;
%>
4.3 Model Demonstration
Figure 12 shows a web page which runs the program
of the optimized model.
ICEIS 2011 - 13th International Conference on Enterprise Information Systems
200

Figure 12: Webpage of model program.
Here, integer is input in text boxes of the parent and
child nodes, such as 0 for the parent node, 1 for the
child node; float is input in the text box of weights,
such as 3.0 for the weight. After clicking the "Add"
button to submit, you can continue to input, such as
0 for the parent node, 2 for the child node, 4.0 for
the weight. Thus, the input model is shown in Figure
13.
Figure 13: Webpage of data input.
Click on the “Optimal Time Calculation” button, the
results are shown in Figure 14. (Code referred to
Appendix).
Figure 14: Webpage of result output.
5 CONCLUSIONS
After the establishment of an optimized model of
virtual enterprise in cloud computing environment,
the great advantages of cloud computing are
demonstrated in the virtual enterprise environment.
And the simulation of the model by JSP language
further illustrates the advantage and trend of the use
of cloud computing in supply chain management.
Although this paper focuses on the processing of
information flow in the supply chain, cloud
computing environment for virtual enterprise
management model can also be from other aspects,
such as the model of actual management process of
virtual enterprise, which is the future direction for
further research.
ACKNOWLEDGEMENTS
This work is partially supported by Beijing Natural
Science Foundation with grant number 4112047.
REFERENCES
Brian Hayes, 2008. Cloud Computing. Commun. ACM,
Vol. 51, No. 7. (July 2008), pp. 9-11.
Lizhe Wang, Jie Tao, Kunze M, Castellanos
A.C., Kramer D., Karl W.,2008, Scientific Cloud
Computing: Early Definition and Experience, High
Performance Computing and Communications, 2008.
HPCC’08. 10th IEEE International Conference on 25-
27 Sept. 2008, 825-830.
Sahinoglu, M. and Cueva-Parra, L., 2011, CLOUD
Computing. Wiley Interdisciplinary Reviews
Computational Statistics, 3 47–68.
Michael Miller, 2008, Cloud Computing: Web-Based
Applications That Change the Way You Work and
Collaborate Online, Que Publishing Company, 12-13.
Vouk, M.A., 2008, Cloud Computing-Issues, Research
and Implementations, Information Technology
Interfaces, 2008. ITI 2008. 30th International
Conference on 23-26 June 2008, 31-40.
Assimakopoulos, Nikitas A., Riggas, Anastasios N., 2006,
Designing a virtual enterprise architecture using
structured system dynamics, Human Systems
Management, 2006, 25(1): 13-29.
Dragoi George, Cotet Costel Emil, Rosu Luminita, et all,
2006. The role of virtual networks in a virtual
enterprise, Journal of Mechanical Engineering, , 52(7-
8): 526-531.
Hua Chen, Rujia Zhao, Yan Cao , et al. 2006. Partner
selection system of virtual enterprise based on grey
relation analysis, Chinese Journal of Mechanical
Engineering, 2006, 42(6): 78-85.
OPTIMISED MODEL OF INFORMATION TRANSFER IN VIRTUAL ENTERPRISES IN CLOUD COMPUTING
ENVIRONMENT
201

Cheng, G., Jin, H., Zou, D. and Zhang, X. 2010. Building
dynamic and transparent integrity measurement and
protection for virtualized platform in cloud computing.
Concurrency and Computation: Practice and
Experience, 22: 1893–1910.
Rajkumar Buyya, Chee Shin Yeo, Srikumar Venugopal,
James Broberg, Ivona Brandic, 2009. Cloud
computing and emerging IT platforms: Vision, hype
and reality for delivering computing at the 5
th
utility,
Future generation computer systems, 2009, 599-616.
APPENDIX
<%
String strSQL;
strSQL = "select son_id from
parent_son where son_id not in(select
parent_id from parent_son) ";
ResultSet
rs=stmt.executeQuery(strSQL);
ArrayList leaf=new ArrayList();
String leaf_id="";
while (rs.next())
{
leaf_id=rs.getString("son_id");
leaf.add(leaf_id);
}
rs.close();
Object oleaf[]=leaf.toArray();
float ototal[]=new
float[oleaf.length];
PreparedStatement ps=null;
String cquery="select parent_id
,total_weight from parent_son where
son_id=?";
String t_son_id="";
float Max=0;
outer1:for(int i=oleaf.length-
1;i>=0;i--)
{
float ftotal=0;
float total_weight;
t_son_id=oleaf[i].toString();
int insert_sequence=0; //
ps=conn.prepareStatement(cquery);
outer2: for(int j=0;j<2;j++)
{
ps.setString(1,t_son_id);
rs=ps.executeQuery();
if(rs.next()){
t_son_id=rs.getString("parent_id");
//scm_line=scm_line+"---"+t_son_id;
ftotal=ftotal+rs.getFloat("total_we
ight");
j=0;
continue outer2;
}else{
ototal[i]=ftotal;
continue outer1;
}
}
}
for( int m=0;m<oleaf.length;m++)
{
if(ototal[m]>Max)
Max=ototal[m];
}
ICEIS 2011 - 13th International Conference on Enterprise Information Systems
202
