
EFFECTIVE INTERFERENCE REDUCTION METHOD FOR
SPREAD SPECTRUM FINGERPRINTING
Minoru Kuribayashi
Graduate School of Engineering, Kobe University, 1-1, Rokkodai-cho, Nada, Kobe, 657-8501, Hyogo, Japan
Keywords:
Spread spectrum fingerprinting, Collusion attack, Removal operation, Iterative detection.
Abstract:
The iterative detection method was proposed in IH2008 specified for the CDMA-based fingerprinting scheme
which embedding procedure was additive watermarking method. Such a detection method is applicable for
the multiplicative watermarking method that modulates a fingerprint using the characteristic of a content. In
this study, we study the interference among fingerprints embedded in a content in the hierarchical version of
Cox’s scheme, and propose the effective detection method that iteratively detects colluders combined with a
removal operation. By introducing two kinds of thresholds, the removal operation is adaptively performed to
reduce the interference without causing serious false detection.
1 INTRODUCTION
A growing number of techniques have been proposed
to provide collusion resistance in multimedia finger-
printing systems. Many of them can be categorized
into two approaches; the orthogonal sequence and fin-
gerprinting code. Orthogonal fingerprinting is a typ-
ical example of designing fingerprint signals. It as-
signs a spread spectrum sequence to each user and
the sequences among users are mutually orthogonal.
The design of collusion-resistant fingerprint codes
was presented by Boneh ans Shaw (Boneh and Shaw,
1998) for generic data. This fingerprinting scheme
is further improved in (Yacobi, 2001) by combining
a spread spectrum watermarking like Cox’s scheme
(Cox et al., 1997) with the Boneh-Shaw’s code. Such
a two-layered fingerprinting scheme is intensively
studied to improve the collusion resistance and the
required computational resource points of view. It is
worth mentioning that most of the variants of the two-
layered scheme use the Cox’s scheme in some man-
ner.
In Cox’s scheme (Cox et al., 1997), a spread spec-
trum sequence following an i.i.d. Gaussian distribu-
tion with zero mean and variance 1, N(0,1) is embed-
ded into the frequency components of a digital image.
Since normally distributed values allow the theoret-
ical and statistical analysis of the method, modeling
of a variety of attacks has been studied. Studies in
(Zhao et al., 2005) have shown that a number of non-
linear collusions such as an interleaving attack can be
well approximated by averaging collusion plus addi-
tive noise. One of the drawbacks of Cox’s scheme
is the amount of computational resources required for
the detection that is linearly increased with the num-
ber of users in the fingerprinting system. Wang et al.
(Wang et al., 2004) reduced the computational costs
by introducing the idea of grouping. This concept
of grouping has been applied to variants of spread
spectrum fingerprinting (He and Wu, 2006), (Hayashi
et al., 2007) and to the construction of a collusion se-
cure code (Lin et al., 2007). In (Hayashi et al., 2007),
a fingerprint sequence was designed using DCT ba-
sic vectors modulated by PN sequences such as the
M-sequence and Gold sequence in order to further re-
duce the computational costs. In (Kuribayashi and
Morii, 2008), the traceability of the fingerprinting
scheme whose embedding operation is additivewater-
marking was improved by the iterative detection with
the removal operation. By introducing two kinds of
thresholds, an adaptive detection for both group and
user IDs is performed.
In this paper, we study the characteristic of multi-
plicative watermarking method and present the itera-
tive detection method combined with the removal op-
eration for the hierarchical version of Cox’s scheme.
The amount of fingerprint signals can be detected
from the extracted signal from a pirated copy using
the similarity measurement. However, the similar-
ity function presented in Cox’s scheme is normalized
167
Kuribayashi M..
EFFECTIVE INTERFERENCE REDUCTION METHOD FOR SPREAD SPECTRUM FINGERPRINTING.
DOI: 10.5220/0003497101670172
In Proceedings of the International Conference on Signal Processing and Multimedia Applications (SIGMAP-2011), pages 167-172
ISBN: 978-989-8425-72-0
Copyright
c
2011 SCITEPRESS (Science and Technology Publications, Lda.)

correlation score, which is not the amount of energy.
By calculating the energy from the similarity mea-
surement, the corresponding fingerprint signals can
be removed from the extracted signal in order to re-
duce the interference among fingerprint signals. We
consider the interference among detected fingerprint
signals and propose a specific removal operation to
further improve the traceability.
2 PRELIMINARIES
2.1 Spread Spectrum Watermarking
In Cox’s scheme (Cox et al., 1997), a spread spec-
trum sequence following an i.i.d. Gaussian distribu-
tion with zero mean and variance 1, N(0,1) is embed-
ded into the frequency components of a digital image.
Let v = {v
0
,...,v
ℓ−1
} be the frequency compo-
nents of a digital image and w = {w
0
,..., w
ℓ−1
} be
the fingerprint sequence. We insert w into v to obtain
a watermarked sequence v
∗
. At the detector side, we
determine which SS sequences are present in a pirated
copy by evaluating the similarity of sequences. When
a sequence ˜w is extracted by calculating the difference
between an original copy and pirated one, and its sim-
ilarity with w is obtained as follows.
sim(w, ˜w) =
w· ˜w
√
˜w· ˜w
, (1)
If the value exceeds a threshold, the embedded se-
quence is regarded as w.
When we insert a watermark w into v, we spec-
ify a scaling parameter α and select one of the three
embedding formulas for computing v
∗
.
v
∗
t
= v
t
+ αw
t
(2)
v
∗
t
= v
t
(1+ αw
t
) (3)
v
∗
t
= v
t
(e
αw
t
) (4)
Specifically, the watermarking scheme that use Eq.(2)
is called additive and the scheme that use Eq.(3) is
called multiplicative. In this paper, we employ Eq.(3)
to embed fingerprints.
In a fingerprinting scheme, each watermarked
copy is slightly different; hence, malicious users can
collect c copies D
1
,...,D
c
with respective water-
marks w
1
,...,w
c
in order to remove/alter the water-
marks. A simple, yet effective way is to average
them because when c copies are averaged,
˜
D = (D
1
+
... + D
c
)/c, the similarity value calculated by Eq.(1)
is reduced by a factor of c. Studies in (Zhao et al.,
2005) have shown that a number of nonlinear collu-
sions such as interleaving attack can be well approxi-
mated by averaging collusion plus additive noise.
2.2 Grouping
There is a common disadvantage in Cox’s scheme and
its variants such that high computational resources are
required for the detection because the correlation val-
ues of all spread spectrum sequences must be calcu-
lated. For the reduction of computational costs, hier-
archical spread spectrum fingerprinting schemes have
been proposed. The motivation of the scheme pro-
posed by Wang et al. (Wang et al., 2004) is to divide
a set of users into different subset and assign each sub-
set to a specific group whose members are more likely
to collude with each other than with members from
other groups. With the assumption that the users in
the same group are equally likely to collude with each
other, the fingerprints in one group have equal cor-
relation. At the detection, the independency among
groups limits the amount of innocent users falsely
placed under suspicion within a group, because the
probability of accusing another group is very large.
We assume that the number of groups is ℓ and that
of users in individual group is also ℓ for simplicity.
Thus, the total number of users is ℓ ×ℓ. The finger-
print sequence w
(i, j)
assigned to the j-th user within
the i-th group consists of two components.
w
(i, j)
= w
(i)
g
+ w
(i, j)
u
, (5)
where w
(i)
g
is the spread spectrum sequence for the i-
th group and w
(i, j)
u
is that for the j-th user. Because
of the presence of the common vector w
(i)
g
, when col-
luders from the same group average their copies, the
energy of the vector is not attenuated; hence, the de-
tector can accurately identify the group. The detec-
tion algorithm consists of two stages; one involves the
identification of groups containing colluders, and the
other, the identification of colluders within each sus-
picious group.
Let ˜v = {˜v
0
,..., ˜v
ℓ−1
} be the frequency compo-
nents extracted from a pirated copy. Since a finger-
print sequence is embedded by the formula in Eq.(3),
the sequence ˜w = { ˜w
0
,..., ˜w
ℓ−1
} is calculated by re-
moving the frequency components of original image
from ˜v as follows.
˜w
t
=
˜v
t
−v
t
αv
t
(6)
Using the original sequences w
(i)
g
assigned for groups,
the detection of group ID is performed as follows.
1. Calculate the similarity values S
(i)
g
of all groups.
S
(i)
g
= sim( ˜w,w
(i)
g
) (7)
2. Calculate the variance σ
2
g
of S
(i)
g
by considering
the property of its distribution and determine a
SIGMAP 2011 - International Conference on Signal Processing and Multimedia Applications
168

threshold T
g
from a given false-positive probabil-
ity P
g
.
T
g
=
q
2σ
2
g
erfc
−1
(2P
g
) (8)
3. If S
(i)
g
≥ T
g
, the i-th group is judged guilty group.
If a pirated copy is generated from multiple finger-
printed copies, the number of the guilty group is equal
or more than 1.
For each guilty group, the detection of colluders
involved in the group is performed as follows.
1. Calculate the similarity values S
(i, j)
u
of all users in
the i-th group.
S
(i, j)
u
= sim( ˜w,w
(i, j)
u
) (9)
2. Calculate the variance σ
2
u
of S
(i, j)
u
by considering
the property of its distribution and determine a
threshold T
u
from a given false-positive probabil-
ity P
u
.
T
u
=
q
2σ
2
u
erfc
−1
(2P
u
) (10)
3. If S
(i, j)
u
≥ T
u
, the j-th user in the i-th group is
judged guilty.
2.3 Iterative Detection
In (Hayashi et al., 2007), the fingerprint sequences
are designed by DCT basic vectors modulated by PN
sequences such as M-sequence and Gold-sequence in
order to further reduce the computational costs. Be-
cause of the assistance of fast DCT algorithm, the
computation of correlation values at the detector is
droppedto logarithmic scale. The embedding formula
used in (Hayashi et al., 2007) is Eq.(2), and hence, it
is additive watermarking. The detection procedure is
further improved in (Kuribayashi and Morii, 2008) to
catch more colluders without increasing the probabil-
ity of false-positiveby introducing the idea of iterative
detection and removal operation.
Because the sequence extracted from a pirated
copy will contain some colluders’ fingerprint signals,
they work as an interference at the detection of each
objectivesignal. For example, once a certain group ID
is detected, its signal is merely a noise at the detection
of user ID. Thus, if a detected fingerprint signal is re-
moved from the extracted sequence, the traceability
can be improved. In (Kuribayashi and Morii, 2008),
the removal operation is performed sequentially for
the detected signals and the detection procedure using
removal operation is performed iteratively. However,
due to the increase of the number of colluders, wrong
signals will be accidentally detected because the ef-
fects of interference are increased with respect to the
number. In such a case, the undetected fingerprint sig-
nal is attenuated by the removal operation.
For the detection of group ID, the false-negative
detection of fingerprinted signals is much serious be-
cause the following detection of the user ID is not
conducted. Even if the false-positive detection of
group ID is increased, the actual false-positive detec-
tion is bounded to the detection of the user ID. When
the threshold T
g
for group ID goes down, the num-
ber of detected group ID is increased. It provides the
chance for mining the corresponding user ID from
a detection sequence. If all detected signals are re-
moved as an interference, wrongly detected signals at
the detection of group ID are also removedand the de-
tection operation is performed again with the thresh-
old which goes down after the removal under a con-
stantly designed false-positive rate. Hence, the repeat
of detection operation provides the chance, regret-
fully, to detect wrong ID by mistake, which causes the
increase of the false detection. In order not to remove
too much, two kinds of thresholds both for group ID
and user ID are introduced in (Kuribayashi and Morii,
2008).
Using those two kinds of thresholds, the finger-
print signals are detected adaptively as follows. We
first detect as many suspicious group IDs as possi-
ble using a lower threshold, and the detected signals
that exceed a higher threshold are removed from the
detection sequence. Then, for the detected suspi-
cious groups, we attempt to detect the corresponding
users. The detected signals as the user ID are removed
from the detection sequence, and if the fingerprint sig-
nals of group IDs corresponding the detected user IDs
have not been removed, they are also removed. Such
operations are repeatedly performed until no user ID
is detected. Finally, some candidates of user ID are
judged using a higher threshold, and guilty users are
identified.
3 PROPOSED SCHEME
Our goal is to identify as many colluders as possible
from the sequence ˜w with small and constant false-
positiveprobability for the group-based fingerprinting
scheme that embeds spread spectrum sequences by a
multiplicative watermarking method.
For the detection of group ID, the false negative
detection of fingerprinted signals is much serious be-
cause the following detection of the user ID is not
conducted. In order to mining more colluders without
removing too much signals by the removal operation,
two kinds of thresholds both for group ID and user ID
are introduced. These thresholds and related parame-
EFFECTIVE INTERFERENCE REDUCTION METHOD FOR SPREAD SPECTRUM FINGERPRINTING
169

ters are classified into high and low using the capitals
“H” and “L”.
1. Calculate the similarity values S
(i)
g
of all groups.
2. Calculate the variance σ
2
g
of S
(i)
g
by considering
the property of its distribution and determine two
thresholds T
L
g
and T
H
g
by Eq.(8) from given false-
positive probabilities P
L
g
and P
H
g
, respectively.
3. If S
(i)
g
≥ T
L
g
, the i-th group is judged suspicious
group.
4. If S
(i)
g
≥ T
H
g
, then the corresponding fingerprint
signals are removed from ˜w,
˜w ← ˜w−
∑
S
(i)
g
≥T
H
g
S
(i)
g
√
ℓ
w
(i)
g
, (11)
and the values S
(i)
g
are stored in
ˆ
S
(i)
g
.
5. For each suspicious group, if no user has been
judged suspect yet, the detection of colluders in-
volved in the group is performed as follows.
5-1 Calculate the similarity values S
(i, j)
u
of all users
in the i-th group.
5-2 Calculate the variance σ
2
u
of S
(i, j)
u
by consid-
ering the property of its distribution and deter-
mine a threshold T
L
u
from a given false-positive
probability P
L
u
.
5-3 If S
(i, j)
u
≥ T
L
u
, the j-th user in the i-th group is
judged suspect, and the corresponding finger-
print signals are removed from ˜w.
˜w ← ˜w−
∑
S
(i, j)
u
≥T
L
u
S
(i, j)
u
√
ℓ
w
(i, j)
u
(12)
The values S
(i, j)
u
are stored in
ˆ
S
(i, j)
u
.
5-4 For the i-th group such that the i-th user is
judged suspect, if S
(i)
g
6≥ T
H
g
at Step.4, re-
calculate S
(i)
g
and remove the corresponding fin-
gerprint signal from ˜w.
˜w ← ˜w−
S
(i)
g
√
ℓ
w
(i)
g
(13)
The value S
(i)
g
is stored in
ˆ
S
(i)
g
.
6. For the groups and users judged suspects, re-
calculate S
(i)
g
and S
(i, j)
u
, and remove the corre-
sponding fingerprint signals from ˜w. The stored
values
ˆ
S
(i)
g
and
ˆ
S
(i, j)
u
are incremented as follows.
ˆ
S
(i)
g
←
ˆ
S
(i)
g
+ S
(i)
g
(14)
ˆ
S
(i, j)
u
←
ˆ
S
(i, j)
u
+ S
(i, j)
u
(15)
7. At least one suspect user ID is detected by Step 5,
go to Step 1; otherwise, go to Step 8.
8. Calculate a higher threshold T
H
u
from a given
false-positive probability P
H
u
using the variance
σ
2
u
.
9. If
ˆ
S
(i)
g
≥ T
H
u
and
ˆ
S
(i, j)
u
≥ T
H
u
, then the j-th user in
the i-th group is finally judged guilty.
The actual probability of false-positive at the de-
tection is strongly related to the final decision, and the
critical parameter is the higher threshold T
H
u
. Regret-
fully, the design in the conventional method (Kurib-
ayashi and Morii, 2008) completely ignores the num-
ber of trials for detecting user ID, denoted by N
trial
,
because the actual probability of false-positive is esti-
mated as N
trial
P
H
u
. In the above detection procedure,
N
trial
is the number of trials performing Step 5. So,
the threshold T
H
u
is calculated by the following equa-
tion:
T
H
u
=
q
2σ
2
u
erfc
−1
2P
H
u
N
trial
(16)
It is worth mentioning that the removal operation
in Step 6 adjusts properly the detected similarity val-
ues. Because of the mutual interference among fin-
gerprint sequences, the similarity values calculated at
early stage in the detection process involve large noise
term, and the amount of noise energy is, in general,
large when the number of fingerprint sequences in-
volved in ˜w is large. Therefore, the similarity values
detected at the early stage involve much noise. The
removal operation for the corresponding signals may
not reduces the interference, but rather causes further
distortion, which results in the increase of the false-
positive probability. Thus, the removal operation in
Step 6 controls the above effect in order to properly
remove the fingerprint signals. For the comparison,
the method without Step 6 is denoted by “method I”
and that with Step 6, by “method II”, and the perfor-
mance is evaluated in the next section.
4 EXPERIMENTAL RESULTS
The performance of the proposed methods is evalu-
ated by detecting colluders using different 10
4
kinds
of combination of IDs. We use a standard “lena” im-
age with a 256-levelgray scale and a size of 512×512
pixels. The scaling parameter is fixed in our sim-
ulation by α = 0.07 and the length of sequence is
ℓ = 1000. The number of groups is 10
3
and that of
users in an individual group is also 10
3
, hence, the to-
tal number of users is 10
6
in this simulation. Then,
the PSNR value of a fingerprinted image is about 35
[dB] when a fingerprint is embedded into an image
SIGMAP 2011 - International Conference on Signal Processing and Multimedia Applications
170
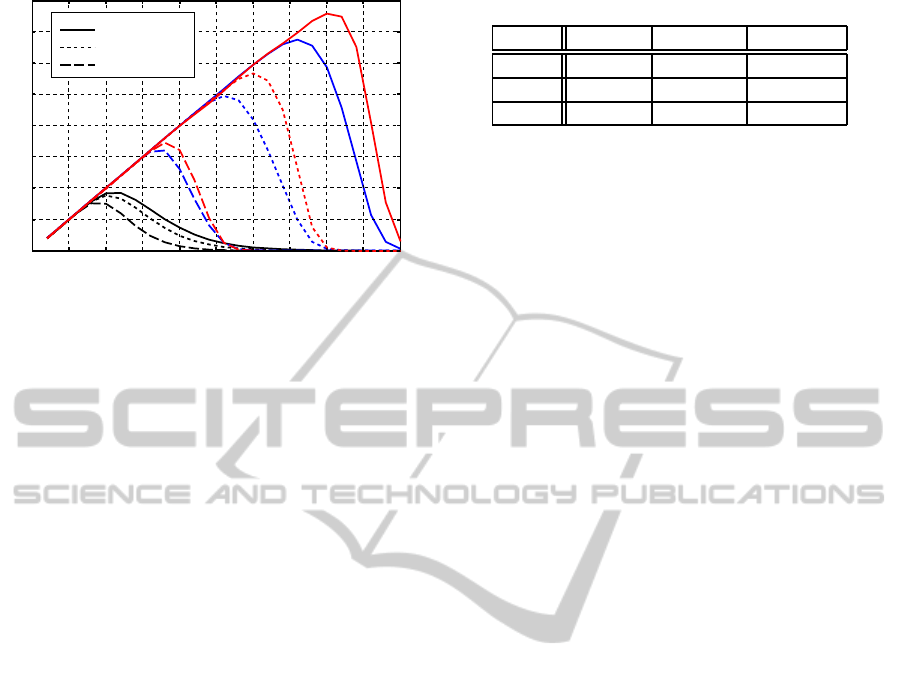
0
5
10
15
20
25
30
35
40
0 5 10 15 20 25 30 35 40 45 50
number of colluders
number of detected colluders
JPEG 100%
JPEG 75%
JPEG 50%
Figure 1: Number of detected colluders, where black, blue,
and red lines are the results using the original detection
method, method I, and method II, respectively.
“lena” using the above parameters. The given false-
positive probabilities are fixed by P
L
g
= 0.5 ×10
−2
,
P
H
g
= 1.0 ×10
−4
, P
L
u
= 1.0 ×10
−5
, and P
H
u
= 1.0 ×
10
−8
. It is noted that the final false-positive proba-
bility is designed to be 1.0 ×10
−4
by Eq.(16). A pi-
rated copy is produced by averaging c copies whose
fingerprint is randomly selected from 10
6
candidates.
It implies that colluders are likely to come from dif-
ferent groups, which is the worst case in group-based
scheme.
The number of detected colluders is measured un-
der the conditions such that fingerprinted images are
averaged and compressed by JPEG algorithm. When
the quality factor is large, the additivenoise caused by
the attack is small. Figure 1 show the number of de-
tected colluders, where solid, dotted, and dashed lines
are the results using the JPEG quality factor 100%,
75% and 50%, respectively. The number of detected
colluders are considerably increased using the pro-
posed iterative detection methods. It is because the
removal operation effectively reduces the interference
term involved in ˜w, and the iteration of the detecting
operation enables us to catch more colluders from the
incremented ˜w. It is noticed that the method II de-
tects more colluders than the method I. The improve-
ment of the performance comes from the operation in
Step 6 that controls the amount of the signals removed
from ˜w.
The probability of false-positive is also measured
under the above conditions. The average probability
accusing innocent users is shown in Table 1. Com-
pared with the probabilities of original method, those
of method I are larger. The reason comes from the
wrong detection of fingerprint signals of innocent
groups and users at the early stage in the iterative de-
tection. Even if such wrongly detected innocent users
Table 1: Probability of false-positive [×10
−4
].
JPEG original method I method II
50 0.92 404.24 2.36
75 0.84 1230.04 3.84
100 0.76 2432.00 1.92
are excluded with high probability at the final judg-
ment, the distortions caused by the removal operation
further degrade ˜w and they increase the probability of
false-positive. It is noticed from the results of method
II that the control of removal operation in Step 6 also
reduce such distortions.
The performance of proposed method II is eval-
uated under averaging collusion. For simplicity, no
additional attacks for a pirated copy is done in this ex-
periment. Figure 2 show the number of detected col-
luders for images “aerial”, “baboon”, “f16”, “lena”,
“peppers”, and “tiffany”. Because the some results of
original method are almost equal, those lines lap over.
It is observed that the number of detected colluders
is drastically increased by the proposed method com-
pared with the original method. It confirms that the
iterative detection with removal operation effectively
improves the performance. However, we can see from
the figure that the performance is strongly dependent
on the characteristic of host image. It is because of
the property of the multiplicative watermarking. The
probability of false-positive is shown in Table 2. It
is observed that the probability of proposed scheme
is slightly increased from that of original one. This
comes from the removal operation that occasionally
removes wrongly detected signals. An adaptive set-
ting of the thresholds T
L
g
, T
H
g
, T
L
u
, and T
H
u
will en-
hance the performance. The detailed analysis of the
dependency among those thresholds and the number
of detected colluders is left for our future work.
5 CONCLUSIONS
In this paper, we implemented the iterative detection
method plus the removal operation for the hierarchi-
cal version of Cox’s fingerprinting scheme. Consider-
ing the characteristic of multiplicative watermarking,
the amount of removed signals is controlled in the
detection procedure. From the experimental results,
the number of detected colluders of proposed meth-
ods is considerably increased compared with that of
the original method. Even if the false-positive proba-
bility is slightly increased in the proposed method, the
control of the amount of fingerprint signals removed
from the extracted signal effectively improve the per-
formance. If the removal operation can further clas-
EFFECTIVE INTERFERENCE REDUCTION METHOD FOR SPREAD SPECTRUM FINGERPRINTING
171

sify the innocent/guilty groups and users, the perfor-
mance of the proposed methods can be improved.
0
5
10
15
20
25
30
35
40
0 5 10 15 20 25 30 35 40 45 50
baboon
f16
lena
peppers
aerial
tiffany
number of colluders
number of detected colluders
(a) JPEG 100%
0
5
10
15
20
25
30
35
0 5 10 15 20 25 30 35 40 45 50
baboon
f16
lena
peppers
aerial
tiffany
number of colluders
number of detected colluders
(b) JPEG 75%
Figure 2: Number of detected colluders for various images,
where solid and dot lines are the results using the original
method and method II, respectively.
Table 2: Probability of false-positive [×10
−4
] for various
images.
image detector JPEG quality
100% 75% 50%
aerial original 0.64 0.64 0.60
method II 3.72 4.16 3.04
baboon original 0.56 8.80 2.56
method II 2.20 0.32 0.12
f16 original 0.52 0.68 0.80
method II 3.16 4.56 2.88
lena original 0.76 0.84 0.92
method II 1.92 3.84 2.36
peppers original 0.80 0.52 0.76
method II 0.44 0.80 1.72
tiffany original 0.80 0.40 0.60
method II 0.44 1.08 0.32
REFERENCES
Boneh, D. and Shaw, J. (1998). Collusion-secure finger-
printing for digital data. IEEE Trans. Inform. Theory,
44(5):1897–1905.
Cox, I. J., Kilian, J., Leighton, F. T., and Shamson,
T. (1997). Secure spread spectrum watermark-
ing for multimedia. IEEE Trans. Image Process.,
6(12):1673–1687.
Hayashi, N., Kuribayashi, M., and Morii, M. (2007).
Collusion-resistant fingerprinting scheme based on
the CDMA-technique. In IWSEC2007, volume 4752
of LNCS, pages 28–43. Springer, Heidelberg.
He, S. and Wu, M. (2006). Joint coding and embedding
techniques for multimedia fingerprinting. IEEE Trans.
Inf. Forensics Security, 1(2):231–247.
Kuribayashi, M. and Morii, M. (2008). Iterative detec-
tion method for CDMA-based fingerprinting scheme.
In IH2008, volume 5284 of LNCS, pages 357–371.
Springer, Heidelberg.
Lin, Y. T., Wu, J. L., and Huang, C. H. (2007). Concatenated
construction of traceability codes for multimedia fin-
gerprinting. Optical Engineering, 46(10):107202.1–
107202.15.
Wang, Z. J., Wu, M., Trappe, W., and Liu, K. J. R. (2004).
Group-oriented fingerprinting for multimedia foren-
sics. EURASIP J. Appl. Signal Process., 14:2142–
2162.
Yacobi, Y. (2001). Improved Bone-Shaw content finger-
printing. In CT-RSA2001, volume 2020 of LNCS,
pages 378–391. Springer, Heidelberg.
Zhao, H. V., Wu, M., Wang, Z. J., and Liu, K. J. R. (2005).
Forensic analysis of nonlinear collusion attacks for
multimedia fingerprinting. IEEE Trans. Image Pro-
cess., 14(5):646–661.
SIGMAP 2011 - International Conference on Signal Processing and Multimedia Applications
172
