
CCA SECURE CERTIFICATELESS ENCRYPTION SCHEMES
BASED ON RSA
S. Sree Vivek
∗
, S. Sharmila Deva Selvi and C. Pandu Rangan
⋆
Theoretical Computer Science Lab, Department of Computer Science and Engineering
Indian Institute of Technology Madras, Chennai, India
Keywords:
Certificateless encryption, Adaptive chosen ciphertext secure (CCA2), RSA assumption, Random Oracle
model.
Abstract:
Certificateless cryptography, introduced by Al-Riyami and Paterson eliminates the key escrow problem inher-
ent in identity based cryptosystem. In this paper, we present two novel and completely different RSA based
adaptive chosen ciphertext secure (CCA2) certificateless encryption schemes. For the first scheme, the se-
curity against Type-I adversary is reduced to RSA problem, while the security against Type-II adversary is
reduced to the CCDH problem. For teh second scheme both Type-I and Type-II security is related to the RSA
problem. The new schemes are efficient when compared to other existing certificatless encryption schemes
that are based on the costly bilinear pairing operation and are quite comparable with the certificateless en-
cryption scheme based on multiplicative groups (without bilinear pairing) by Sun et al. (Sun et al., 2007) and
the RSA based CPA secure certificateless encryption scheme by Lai et al. (Lai et al., 2009). We consider a
slightly stronger security model than the ones considered in (Lai et al., 2009) and (Sun et al., 2007) to prove
the security of our schemes.
1 INTRODUCTION
Cryptosystem based on Public Key Infrastructure
(PKI) allows any user to choose his own private key
and the corresponding public key. The public key
is submitted to a certification authority (CA), which
verifies the identity of the user and issues certificates
linking his identity and the public key. Thus, a PKI
based system needs digital certificate management
that is too cumbersome to maintain and manage. Adi
Shamir introduced the notion of Identity Based Cryp-
tography (IBC) (Shamir, 1984) to reduce the burden
of a PKI due to digital certificate management. In
IBC, the private key of a user is not chosen by him,
instead it is generated and issued by a trusted author-
ity called the Private Key Generator (PKG) or Trust
Authority (TA). This private key corresponds to the
user’s public key which is generated from strings that
represent the user’s identity, avoiding the need for cer-
tificates altogether. The PKG is responsible for gen-
erating the private keys of all the users in the sys-
tem and it knows the private keys of all the users in
∗
Work supported by Project No. CSE/05-06/076/
DITX/CPAN on Protocols for Secure Communication and
Computation sponsored by Department of Information
Technology, Government of India
the system. This inherent weakness of IBC is called
as the key escrow problem. Certificateless Cryptog-
raphy (CLC) introduced by Al-Riyami and Paterson
(Al-Riyami and Paterson, 2003) addresses this issue
to some extent, while avoiding the use of certificates
and the need for CA. The principle behind CLC is
to partition the private key of a user into two compo-
nents: an identity based partial private key (generated
by the PKG) and a non-certified private key (which
is chosen by the user and not known to the PKG).
This technique potentially combines the best features
of IBC and PKI.
CLC also uses identities that uniquely identify a
user in the system as in IBC but the public key of
a user is not his identity alone but it is a combina-
tion of his identity and the public key corresponding
to the non-certified private key chosen by the user.
CLC involves a trusted third party as in IBC, named
as the Key Generation Center (KGC), who generates
partial private keys for the users registered with it.
Each user selects his own secret value and a combi-
nation of the partial private key and the secret value
acts as the full private key of the user. The authors
of (Al-Riyami and Paterson, 2003) have shown real-
ization for certificateless encryption (CLE), signature
(CLS) and key exchange (CLK) schemes in their pa-
208
Sree Vivek S., Sharmila Deva Selvi S. and Pandu Rangan C..
CCA SECURE CERTIFICATELESS ENCRYPTION SCHEMES BASED ON RSA.
DOI: 10.5220/0003529502080217
In Proceedings of the International Conference on Security and Cryptography (SECRYPT-2011), pages 208-217
ISBN: 978-989-8425-71-3
Copyright
c
2011 SCITEPRESS (Science and Technology Publications, Lda.)

per. Huang et al. (Huang et al., 2005) and Castro et
al. (Castro and Dahab, 2007) independently showed
that the signature scheme in (Al-Riyami and Pater-
son, 2003) is not secure against Type-I adversary (ex-
plained in later sections), i.e. it is possible to launch
a key replacement attack on the scheme and they also
gave a new certificateless signature scheme. Many
CLE schemes were proposed, whose security were
proved both in the random oracle model (Baek et al.,
2005; Cheng and Comley, 2005; Shi and Li, 2005;
Sun et al., 2007) and standard model (Liu et al., 2007;
Park et al., 2007). Recently, Dent (Dent, 2008) has
given a survey on the various security models for CLE
schemes, mentioning the subtle difference in the level
of security offeredby each model. Dent has also given
the generic construct and an efficient construction for
CLE. The initial constructs for certificateless cryp-
tosystem were all based on bilinear pairing (Cheng
and Comley, 2005; Shi and Li, 2005; Liu et al., 2007;
Park et al., 2007). Baek et al. (Baek et al., 2005)
were the first to propose a CLE scheme without bi-
linear pairing. Certificateless cryptosystem are prone
to key replacement attack because the public keys are
not certified and anyone can replace the public key
of any legitimate user in the system. The challenging
task in the design of certificateless cryptosystem is to
come up with schemes which resists key replacement
attacks. The CLE in (Baek et al., 2005) did not with-
stand key replacement attack, which was pointed out
by Sun et al. in (Sun et al., 2007). Sun et al. fixed
the problem by changing the partial key extract and
setting public key procedures.
Related Works. Both the aforementioned schemes,
namely (Baek et al., 2005) and (Sun et al., 2007) were
based on multiplicativegroups. Lai et al. in (Lai et al.,
2009) proposed the first RSA-based CLE scheme.
They have proved their scheme secure against cho-
sen plaintext attack (CPA). In fact they left the de-
sign of a CCA secure system based on RSA as open.
One may be tempted to think that the CPA secure
scheme of Lai et al. in (Lai et al., 2009) can be made
CCA secure by using any well known transformations
like (Fujisaki and Okamoto, 1999b), (Fujisaki and
Okamoto, 1999a) but giving access to the secret value
of the target identity and strong decryption oracle to
the Type-I adversary makes the resulting scheme in-
secure. Moreover, the scheme in (Lai et al., 2009)
cannot be directly extended to a CLE scheme, whose
Type-I and Type-II security relies on RSA assumption
without making considerable changes in the scheme,
hence we design a totally new scheme from scratch.
Our Contribution. In this paper, we propose two
CLE schemes. The Type-I security of the first scheme
is based on the RSA assumption and the Type-II se-
curity is based on the composite computational Diffie
Hellman assumption (CCDH). Both Type-I and Type-
II securities of our second scheme are based on the
RSA assumption. Thus, we provide a scheme which
is partially RSA based (like (Lai et al., 2009), but
CCA2 secure) and another scheme which is fully
RSA based. We formally prove both our schemes
to be Type-I and Type-II secure under adaptive cho-
sen ciphertext attack (CCA2) in the random oracle
model. This is the strongest security notion for any
encryption scheme. One of the striking features of
our schemes is the novel key construction algorithm,
which is completely new and different from other key
constructs used so far in designing CLE. Moreover,
our security model is stronger than the security mod-
els considered in the two existing secure schemes,
(Lai et al., 2009) and (Sun et al., 2007). First, the
existing schemes do not provide access to the secret
value corresponding to the target identity during the
Type-I confidentiality game, while we provide the se-
cret value to the adversary. Second, we provide the
strong decryption oracle for Type-I adversary. Strong
decryption oracle means the decryption correspond-
ing to a ciphertext is provided by the challenger even
if the public key of a user is replaced after the gen-
eration of the ciphertext (Dent, 2008). We provide
these oracle queries to the Type-I adversary of both
the schemes and prove the security of our schemes
in this stronger model. We stress that our second
scheme is the major contribution in this paper and
the first scheme is a stepping stone towards our fully
RSA secure scheme. Even though computation of bi-
linear pairing has become efficient, finding out pair-
ing friendly curves are difficult (Freeman et al., 2010)
and most of the efficient curves and means of com-
pressing are patented. Thus, we have only a hand full
of elliptic curves that support pairing for designing
cryptosystem. Besides, since the RSA patent expired
in the year 2000, designing cryptographic schemes
based on RSA assumption gets more attention these
days. Hence, the research in pairing free protocol is a
very important and worthwhile effort.
We use the following well known hard problems to
establish the security of our new schemes:
Definition 1.1 (The RSA Problem). Given an RSA
public key (n, e), where n = pq, p, q, (p − 1)/2 and
(q−1)/2 are large prime numbers, e is an odd integer
such that gcd(e,φ(n)) = 1 and b ∈
R
Z
∗
n
, finding a ∈
Z
∗
n
such that a
e
≡ b (modn) is referred as the RSA
problem.
An RSA problem solver with ε advantage is
a probabilistic polynomial algorithm A
RSA
which
solves the RSA problem and ε = Prob[a ←
CCA SECURE CERTIFICATELESS ENCRYPTION SCHEMES BASED ON RSA
209

A
RSA
(n,e,b = a
e
)].
Definition 1.2 (The Composite Computational
Diffie Hellman Problem (CCDH). (Shmuely, 1985),
(McCurley, 1988)) Given p,q, n,hg,g
a
,g
b
i ∈ Z
∗
n
,
where n is a composite number with two big prime
factors p and q, also (p − 1)/2 and (q − 1)/2 are
prime numbers, finding g
ab
mod n is the Composite
Computational Diffie Hellman Problem in Z
∗
n
, where
a,b ∈ Z
odd
n
.
The advantage of any probabilistic polynomial time
algorithm A in solving the CCDH problem in Z
∗
n
is
defined as
Adv
CCDH
A
= Pr
h
A (p,q,n, g,g
a
,g
b
) = g
ab
| a,b ∈ Z
odd
n
i
The CCDH Assumption is that, for any probabilis-
tic polynomial time algorithm A , the advantage
Adv
CCDH
A
is negligibly small.
2 FRAMEWORK AND SECURITY
MODELS
In this section, we discuss the general framework for
CLE. We adopt the definition of certificateless pub-
lic key encryption, given by Baek et al. (Baek et al.,
2005). Their definition of CLE is weaker than the
original definition by Al-Riyami and Paterson (Al-
Riyami and Paterson, 2003) because the user has to
obtain a partial public key from the KGC before he
can create his public key (While in Al-Riyami and
Paterson’s original CLE this is not the case). We also
review the notion of Type-I and Type-II adversaries
and provide the security model for CLE.
2.1 Framework for CLE
A certificateless public-key encryption scheme is de-
fined by six probabilistic, polynomial-timealgorithms
which are defined below:
Setup. This algorithm takes as input a security pa-
rameter 1
κ
and returns the master private key msk and
the system public parameters params. This algorithm
is run by the KGC in order to initialize a certificateless
system.
Partial Key Extract. This algorithm takes as input
the public parameters params, the master private key
msk and an identity ID
A
∈ {0,1}
∗
of a user A. It out-
puts the partial private key s
A
and a partial public key
PPK
A
of user A. This algorithm is run by the KGC
once for each user and the corresponding partial pri-
vate key and partial public key is given to A through a
secure and authenticated channel.
Set Private Key. This algorithm is run once by each
user. It takes the public parameters params, the user
identity ID
A
and A’s partial private key s
A
as input.
The algorithm generates a secret value y
A
∈ S , where
S is the secret value space. Now, the full private key
D
A
is a combination of the secret value y
A
and the
partial private key s
A
of A.
Set Public Key. This algorithm run by the user, takes
as input the public parameters params, a user, say A’s
partial public key PPK
A
and the full private key D
A
.
It outputs a public key PK
A
for A. This algorithm is
run once by the user and the resulting full public key
is widely and freely distributed. The full public key
of user A consists of PK
A
and ID
A
.
Encryption. This algorithm takes as input the public
parameters params, a user A’s identity ID
A
, the user
public key PK
A
and a message m ∈ M . The output of
this algorithm is the ciphertext σ ∈ C S . Note that M
is the message space and C S is the ciphertext space.
Decryption. This algorithm takes as input the public
parameters params, a user, say A’s private key D
A
and
a ciphertext σ ∈ C . It returns either a message m ∈ M
- if the ciphertext is valid, or Invalid - otherwise.
2.2 Security Model for CLE
The confidentiality of any CLE scheme is proved by
means of an interactive game between a challenger
C and an adversary. In the confidentiality game for
certificateless encryption (IND-CLE-CCA2) the ad-
versary is given access to the following five oracles.
These oracles are simulated by C :
Partial Key Extract for ID
A
. C responds by return-
ing the partial private key s
A
and the partial public key
PPK
A
of the user A.
Extract Secret Value for ID
A
. If A’s public key has
not been replaced then C responds with the secret
value y
A
for user A. If the adversary has already re-
placed A’s public key, then C does not provide the
corresponding private key to the adversary.
Request Public Key for ID
A
. C responds by return-
ing the full public key PK
A
for user A. (First by choos-
ing a secret value if necessary).
Replace Public Key for ID
A
. The adversary can re-
peatedly replace the public key PK
A
for a user A with
any valid public key PK
′
A
of its choice. The current
value of the user’s public key is used by C in anycom-
putations or responses.
Decryption for Ciphertext σ and Identity ID
A
: The
adversary can issue a decryption query for ciphertext
σ and identity ID
A
of its choice, C decrypts σ and re-
turns the corresponding message to the adversary. C
SECRYPT 2011 - International Conference on Security and Cryptography
210

should be able to properly decrypt ciphertexts, even
for those users whose public key has been replaced,
i.e. this oracle provides the decryption of a ciphertext,
which is generated with the current valid public key.
The strong decryption oracle returns Invalid, if the ci-
phertext corresponding to any of the previous public
keys were queried. This is a strong property of the se-
curity model (Note that, C may not know the correct
private key of the user). However, this property en-
sures that the model captures the fact that changing a
user’s public key to a value of the adversary’s choice
may give the adversary an advantage in breaking the
scheme. This is called as strong decryption in (Dent,
2008). Our schemes provides strong decryption for
Type-I adversary.
There are two types of adversaries (namely Type-I
and Type-II) to be considered for any certificateless
encryption scheme. The Type-I adversary models the
attack by a third party attacker, (i.e. anyone except the
legitimate receiver or the KGC) who is trying to gain
some information about a message from the encryp-
tion. The Type-II adversary models the honest-but-
curious KGC who tries to break the confidentiality of
the scheme. Here, the attacker is allowed to have ac-
cess to master private key msk. This means that we
do not have to give the attacker explicit access to par-
tial key extraction, as the adversary is able to com-
pute these value on its own. The most important point
about Type-II security is that the adversary modeling
the KGC should not have replaced the public key for
the target identity before the challenge is issued.
Constraints for Type-I and Type-II Adversaries.
The IND-CLE-CCA2 security model distinguishes
the two types of adversary Type-I and Type-II with
the following constraints.
• Type-I adversary A
I
is allowed to change the pub-
lic keys of users at will but does not have access
to the master private key msk.
• Type-II adversary A
II
is equipped with the mas-
ter private key msk but is not allowed to replace
public keys corresponding to the target identity.
IND-CLE-CCA2 Game for Type-I Adversary. The
game is named as IND-CLE-CCA2-I. This game,
played between the challenger C and the Type-I ad-
versary A
I
, is defined below:
Setup. Challenger C runs the setup algorithm to gen-
erate master private key msk and public parameters
params. C gives params to A
I
while keeping msk se-
cret. After receiving params, A
I
interacts with C in
two phases:
Phase I. A
I
is given access to all the five oracles. A
I
adaptively queries the oracles consistent with the con-
straints for Type-I adversary described above.
Challenge. At the end of Phase I, A
I
gives two mes-
sages m
0
and m
1
of equal length to C on which it
wishes to be challenged. C randomly chooses a bit
δ ∈
R
{0,1} and encrypts m
δ
with the target identity
ID
∗
’s public key to form the challenge ciphertext σ
∗
and sends it to A
I
as the challenge. (Note that the par-
tial Private Key corresponding to ID
∗
should not be
queried by A
I
but the secret value corresponding to
ID
∗
may be queried. This makes our security model
stronger when compared to the security models of
(Lai et al., 2009) and (Sun et al., 2007).)
Phase II. A
I
adaptively queries the oracles consistent
with the constraints for Type-I adversary described
above. Besides this A
I
cannot query Decryption on
(σ
∗
,ID
∗
) and the partial private key of the receiver
should not have been queried to the Extract Partial
Private Key oracle.
Guess. A
I
outputs a bit δ
′
at the end of the game.
A
I
wins the IND-CLE-CCA2-I game if δ
′
= δ. The
advantage of A
I
is defined as -
Adv
IND−CLE−CCA2−I
A
I
= |2Pr
δ = δ
′
− 1|
IND-CLE-CCA2 Game for Type-II Adversary. The
game is named as IND-CLE-CCA2-II. This game,
played between the challenger C and the Type-II ad-
versary A
II
, is defined below:
Setup. Challenger C runs the setup algorithm to gen-
erate master private key msk and public parameters
params. C gives params and the master private key
msk to A
II
. After receiving params, A
II
interacts with
C in two phases:
Phase I. A
II
is not given access to the Extract partial
Private Key oracle because A
II
knows msk, it can gen-
erate the partial private key of any user in the system.
All other oracles are accessible by A
II
. A
II
adaptively
queries the oracles consistent with the constraints for
Type-II adversary described above.
Challenge. At the end of Phase I, A
II
gives two
messages m
0
and m
1
of equal length to C on which
it wishes to be challenged. C randomly chooses a
bit δ ∈
R
{0,1} and encrypts m
δ
with the target iden-
tity ID
∗
’s public key to form the challenge ciphertext
σ
∗
and sends it to A
II
as the challenge. (Note that
the Secret Value Corresponding to ID
∗
should not be
queried by A
II
and the public key corresponding to
ID
∗
should not be replaced during Phase I.)
Phase II. A
II
adaptivelyqueries the oracles consistent
with the constraints for Type-II adversary described
above. Besides this A
II
cannot query Decryption on
(σ
∗
,ID
∗
) and the Secret Value corresponding to the
receiver should not be queried to the Extract Secret
Value oracle and the public key corresponding to ID
∗
should not be replaced during Phase I.
CCA SECURE CERTIFICATELESS ENCRYPTION SCHEMES BASED ON RSA
211

Guess. A
II
outputs a bit δ
′
at the end of the game.
A
II
wins the IND-CLE-CCA2-II game if δ
′
= δ. The
advantage of A
II
is defined as -
Adv
IND−CLE−CCA2−II
A
II
= |2Pr
δ = δ
′
− 1|
3 BASIC RSA-BASED CLE
SCHEME (RSA-CLE
1
)
In this section, we propose the basic RSA based cer-
tificateless encryption scheme RSA-CLE
1
and also
prove the security of the scheme against both Type-
I and Type-II adversaries under adaptive chosen ci-
phertext attack (CCA2). For this scheme the Type-I
security relies on the RSA assumption and the Type-
II security is based on the composite computational
Diffie Hellman assumption (CCDH).
Notation. We use the notation Z
odd
n
to represent the
odd numbers from [0,n]. Throughout the paper, in
order to choose a random odd number from the range
[1,n], we randomly pick an element in Z
n
and check
whether it is odd, if it is odd, we accept it, else we
subtract 1 from the chosen number. These numbers
are represented as Z
odd
n
.
3.1 The RSA-CLE
1
Scheme
The proposed scheme comprises the following six al-
gorithms. Unless stated otherwise, all computations
except those in the Setup algorithm are done mod n.
Setup. The KGC does the following to initialize the
system and to setup the public parameters.
• Chooses two primes p and q, such that p = 2p
′
+1
and q = 2q
′
+ 1 where p
′
and q
′
are also primes.
• Computes n = pq and the Euler’s totient function
φ(n) = (p− 1)(q− 1).
• It also chooses four cryptographic hash functions
H : {0,1}
∗
→ Z
∗
n
, H
1
: {0,1}
∗
× Z
∗
n
→ Z
odd
n
, H
2
:
{0,1}
l
×Z
∗
n
→ Z
odd
n
and H
3
: Z
∗
n
×Z
∗
n
×{0,1}
∗
→
{0,1}
l+|Z
odd
n
|
, where l is the size of the message.
• Now, KGC publicizes the system parameters,
params = hn,H,H
1
,H
2
,H
3
i and keeps the factors
of n, namely p and q as the master private key.
Note. Since n is a product of two strong primes, a ran-
domly chosen number in Z
odd
n
is relatively prime to
φ(n) with overwhelming probability. The RSA mod-
ulus n is set to n = pq and p, q are chosen such that
p = 2p
′
+ 1, q = 2q
′
+ 1 where both p
′
and q
′
are also
large primes. Considering φ(n) = 2
2
p
′
q
′
with only
three factors 2, p
′
,q
′
, the probability of any odd num-
ber being co-prime to φ(n) is overwhelming, because
finding a number not co-prime to 4p
′
q
′
is equivalent
to finding p
′
or q
′
or finding p or q. Thus, hardness of
factoring implies that the random odd number in Z
n
is relatively prime to φ(n) with very high probability.
Partial Key Extract. Our partial key extraction is not
a deterministic algorithm, i.e. this algorithm gives dif-
ferent partial keys for the same identity when queried
more than once. Examples for this type of key extrac-
tion can be found in (Baek et al., 2005) and (Sun et al.,
2007). This algorithm is executed by the KGC and
upon receiving the identity ID
A
of a user A the KGC
performs the following to generate the corresponding
partial private key d
A
.
• Chooses x
A
∈
R
Z
odd
n
.
• Computes g
A
= H(ID
A
).
• Computes the partial public key PPK
A
= g
x
A
A
• Computes the value e
A
= H
1
(ID
A
,PPK
A
).
• Computes d
A
such that e
A
d
A
≡ 1 mod φ(n) and
sends the partial private key s
A
= x
A
+ d
A
mod
φ(n) and the partial public key PPK
A
to the user
through a secure channel.
The validity of the partial private key can be verified
by user A by performing the following check:
(g
x
A
A
)
e
A
g
A
?
= (g
A
)
s
A
e
A
(1)
Note. However, this can be made deterministic by
obtaining the randomness used in the computation of
the partial public key through a secure MAC (Mes-
sage Authentication Code) with the identity of the
user as input and the master private key as the key
to the MAC.
Set Private Key. On receiving the partial private key
the user with identity ID
A
does the following to gen-
erate his full private key.
• Chooses y
A
∈
R
Z
odd
n
as his secret value.
• Sets the private key as D
A
= hD
(1)
A
,D
(2)
A
i =
hs
A
,y
A
i. (Note that both the KGC and the corre-
sponding user knows D
(1)
A
and the user with iden-
tity ID
A
alone knows D
(2)
A
).
Set Public Key. The user with identity ID
A
computes
the public key corresponding to his private key as de-
scribed below:
• Computes g
A
= H(ID
A
).
• Computes the value g
D
(2)
A
A
.
• Makes PK
A
= hPK
(1)
A
,PK
(2)
A
,PK
(3)
A
i =
hPPK
A
,g
D
(2)
A
A
,g
D
(1)
A
A
i public.
SECRYPT 2011 - International Conference on Security and Cryptography
212

Note that g
x
A
A
was sent by KGC to the user while
setting ID
A
’s partial private key. The validity of the
public key can be publicly verified using the follow-
ing verification test:
• Compute e
A
= H
1
(ID
A
,PK
(1)
A
).
• Check whether the following holds:
(PK
(3)
A
)
e
A
?
= (PK
(1)
A
)
e
A
g
A
(2)
Encryption. To encrypt a message m to a user with
identity ID
A
, one has to perform the following steps:
• Check the validity of the public key corresponding
to ID
A
.
• Choose r ∈
R
Z
odd
n
.
• Compute e
A
= H
1
(ID
A
,PK
(1)
A
), g
A
= H(ID
A
) and
h = H
2
(m,r).
• Compute c
1
= g
h
A
, and c
2
= (mkr) ⊕
H
3
(PK
(1)
A
)
he
A
,(PK
(2)
A
)
h
,ID
A
.
Now, σ = (c
1
,c
2
) is send as the ciphertext to the user
A.
Decryption. The receiver with identity ID
A
does the
following to decrypt a ciphertext σ = (c
1
,c
2
):
• Find (mkr) = c
2
⊕ H
3
(
(c
1
)
D
(1)
A
e
A
c
1
,(c
1
)
D
(2)
A
,ID
A
).
• Computes h
′
= H
2
(m,r) and checks whether c
1
?
=
g
h
A
.
User A accepts the message only if the above check
holds.
3.2 Security Proof
In order to prove the confidentiality of a certificate-
less encryption scheme, it is required to consider the
attacks by Type-I and Type-II adversaries. In the two
existing secure schemes (Lai et al., 2009) and (Sun
et al., 2007), the Type-I adversaryis not allowedto ex-
tract the secret value corresponding to the target iden-
tity. In order to capture the ability of the adversary
who can access the secret keys of the target identity,
we give access to the user secret value of the target
identity to the Type-I adversary. We also state that, al-
lowing the extract secret value query correspondingto
the target identity makes the security model for Type-I
adversary more stronger.
3.2.1 Confidentiality against Type-I Adversary
Theorem 3.1 Our certificateless public key encryp-
tion scheme RSA-CLE
1
is IND-RSA-CLE
1
-CCA2-I
secure in the random oracle model, if the RSA prob-
lem is intractable in Z
∗
n
, where p, q, (p − 1)/2 and
(q− 1)/2 are large prime numbers.
Proof Sketch. The challenger C is challenged with
an instance of the RSA problem, say hn,e ∈
R
Z
odd
n
,bi
∈ Z
∗
n
, where n is a composite number with two big
prime factors p and q, (p−1)/2 and (q−1)/2 are also
primes. Let us consider that there exists an adversary
A
I
who is capable of breaking the IND-RSA-CLE
1
-
CCA2-I security of the RSA-CLE
1
scheme. C can
make use of A
I
to compute a such that a
e
≡ b mod n,
by playing the following interactive game with A
I
.
Setup. C begins the game by setting up the system
parameters as in the RSA-CLE
1
scheme. C takes n
from the instance of the RSA problem that C has re-
ceived and sends params = hni to A
I
. C also designs
the four hash functions H, H
1
, H
2
and H
3
as random
oracles O
H
, O
H
1
, O
H
2
and O
H
3
.
Phase I. A
I
performs a series of queries to the oracles
provided by C . The descriptions of the oracles and
the responses given by C to the corresponding oracle
queries by A
I
are described below:
Note. We assume that O
H
(.) oracle is queried with
ID
i
as input, before any other oracle is queried with
the corresponding identity, ID
i
as one of the inputs.
O
H
(ID
i
): We follow the proof methodology intro-
duced in (Boyen, 2003) and make a simplifying as-
sumption that A
I
queries the O
H
oracle with distinct
identities in each query. This is because, if the same
identity is repeated, by definition, the oracle consults
the list L and gives the same response. Thus, we as-
sume that A
I
asks q
H
distinct queries for q
H
distinct
identities. Among this q
H
identities, a random iden-
tity has to be selected as target identity by C . C selects
a random index γ, where 1 ≤ γ ≤ q
H
and C does not
reveal γ to A
I
. When A
I
generates the γ
th
query on
ID
γ
, C fixes ID
γ
as target identity for the challenge
phase.
For answering the O
H
query, C performs the follow-
ing, for 1 ≤ γ ≤ q
H
• If a tuple of the form hID
i
,e
i
,β
i
,g
i
i exists in the
list L then C retrieves the corresponding g
i
.
• Else,
– If i 6= γ, C performs the following:
∗ C chooses e
i
∈
R
Z
odd
n
, β
i
∈
R
Z
∗
n
and computes
g
i
= β
e
i
i
.
∗ Generates the partial private key correspond-
ing to ID
i
as follows:
· Chooses s
i
∈
R
Z
odd
n
.
· Computes
g
s
i
i
β
i
. Let
g
s
i
i
β
i
= g
x
i
i
for some x
i
.
(Note that x
i
is not known to C .)
· Chooses y
i
∈
R
Z
odd
n
and adds the tuple
hID
i
,s
i
,g
x
i
i
,y
i
i in the list L
S
.
CCA SECURE CERTIFICATELESS ENCRYPTION SCHEMES BASED ON RSA
213

∗ Adds the tuple hID
i
,g
x
i
i
,e
i
i in the list L
1
.
∗ Computes g
y
i
i
and g
s
i
i
, adds the tuple
hID
i
,g
x
i
i
,g
y
i
i
,g
s
i
i
,e
i
i into the list L
P
.
– If i = γ, C performs the following:
∗ C chooses β
i
∈
R
Z
∗
n
and ω ∈
R
Z
odd
n
and com-
putes z = ω
2
. Let z = x
−1
i
d
2
, for some x
i
. Sets
e
i
= e and computes g
i
= β
ze
2
i
i
.
Note. It is to be noted that the tuple
hID
γ
,e
γ
,β
γ
,g
γ
i in the list L is equal to
hID
γ
,e,β
γ
,β
ze
2
γ
i.
∗ Chooses y
i
∈
R
Z
odd
n
and computes PK
i
=
hPK
(1)
i
,PK
(2)
i
,PK
(3)
i
i = hβ
i
,g
y
i
i
,β
i
β
ze
i
i
i. C
now adds the tuple hID
i
,β
i
,g
y
i
i
,β
i
β
ze
i
i
,e
i
i into
the list L
P
. The public key thus generated
passes the verification test done by A
I
as
shown below:
(PK
(3)
i
)
e
i
= (β
i
β
ze
i
i
)
e
i
= (β
e
i
i
β
ze
2
i
i
)
= (PK
(1)
i
)
e
i
g
i
(Since β
ze
2
i
i
= g
i
)
∗ Adds the tuple hID
i
,g
x
i
i
= β
i
,e
i
i in the list L
1
.
• C adds the tuple hID
i
,e
i
,β
i
,g
i
i to the list L and
returns g
i
to A
I
.
O
H
1
(ID
i
,∆
i
): To respond to this query, C retrieves
the tuple that corresponds to ID
i
, which is of the form
hID
i
,g
x
i
i
,g
y
i
i
,g
s
i
i
,e
i
i from the list L
P
and performs the
following:
• If g
x
i
i
= ∆
i
, a tuple of the form hID
i
,∆
i
,e
i
i will
exist in the list L
1
, C returns the corresponding e
i
.
• If g
x
i
i
6= ∆
i
, C chooses ˆe
i
∈
R
Z
odd
n
, adds the tuple
hID
i
,∆
i
, ˆe
i
i in the list L
1
and returns ˆe
i
as the re-
sponse.
O
H
2
(m,r): To respond to this query, C checks
whether a tuple of the form hm,r,hi exists in the list
L
2
. If a tuple of this form exists, C returns the cor-
responding h, else chooses h ∈
R
Z
odd
n
, adds the tuple
hm,r,hi to the list L
2
and returns h to A
I
.
O
H
3
(k
1
,k
2
,ID
i
): To respond to this query, C checks
whether a tuple hk
1
,k
2
,ID
i
,h
3
i exists in the list L
3
. If
a tuple of this form exists, C returns the correspond-
ing h
3
else chooses h
3
∈
R
{0,1}
l+|Z
odd
n
|
, adds the tuple
hk
1
,k
2
,ID
i
,h
3
i to the list L
3
and returns h
3
to A
I
.
O
PartialKeyExtract
(ID
i
). To respond to this query, C
does the following:
• If i = γ, C aborts the game.
• If i 6= γ, C retrieves the tuple of the form
hID
i
,s
i
,g
x
i
i
,y
i
i from list L
S
and returns s
i
as the
partial private key and PPK
i
= g
x
i
i
as the partial
public key corresponding to the identity ID
i
.
O
ExtractSecretValue
(ID
i
). C retrieves a tuple of the form
hID
i
,s
i
,g
x
i
i
,y
i
i from the list L
S
and returns the corre-
sponding y
i
as the secret value corresponding to the
identity ID
i
. If the entry corresponding to y
i
in the
tuple is “−” then A
I
has replaced the private key cor-
responding to ID
i
.
O
RequestPublicKey
(ID
i
). C retrieves the tuple of the
form hID
i
,g
x
i
i
,g
y
i
i
,g
s
i
i
,e
i
i from the list L
P
and returns
PK
i
= hβ
i
,g
y
i
i
,β
i
β
e
i
i
i as the public key corresponding
to the identity ID
i
.
O
ReplacePublicKey
(ID
i
,PK
′
i
). To replace the public
key of ID
i
with a new public key PK
′
i
= hPK
′
(1)
i
,
PK
′
(2)
i
,PK
′
(3)
i
i, chosen by A
I
, C does the following:
• Updates the corresponding tuples in the list
L
P
as hID
i
,PK
′
(1)
i
,PK
′
(2)
i
,PK
′
(3)
i
,e
i
i, only if
(PK
′
(3)
i
)
e
i
= (PK
′
(1)
i
)
e
i
g
i
, where g
i
corresponding
to ID
i
is retrieved from the list L.
• Return Invalid, otherwise.
O
StrongDecryption
(σ,ID
i
,PK
i
): C performs the follow-
ing to decrypt the ciphertext σ = hc
1
,c
2
i:
• Checks the validity of PK
i
and rejects the cipher-
text σ if this check fails, else proceeds with the
following steps.
• Retrieves the tuple hID
i
,g
x
i
i
,e
i
i from list L.
• For each hm, r,hi ∈ L
2
list performs the following:
– Checks whether g
h
i
?
= c
1
.
– If
True
, computes k
1
= (PK
(1)
i
)
e
i
h
and k
2
=
(PK
(2)
i
)
h
.
– Checks in list L
3
, for an entry corresponding
to (k
1
,k
2
,ID
i
). If a tuple exists then retrieves
the corresponding h
3
value and checks whether
c
2
⊕ h
3
?
= (mkr), where m, r are retrieved from
the list L
2
.
– If
True
, outputs m as the message.
• If no tuple satisfies all the above tests, returns
Invalid.
Challenge. At the end of Phase I, A
I
produces two
messages m
0
and m
1
of equal length and an identity
ID
∗
. C aborts the game if ID
∗
6= ID
γ
, else randomly
chooses a bit δ ∈
R
{0,1} and computes a ciphertextσ
∗
with ID
γ
as the receiver by performing the following
steps:
• Set c
∗
1
= b
z
, where b is taken from the RSA prob-
lem instance received by C and z is the value cho-
sen during the O
H
(.) oracle query corresponding
to ID
γ
.
• Choose c
∗
2
∈
R
{0,1}
l+|Z
odd
n
|
.
SECRYPT 2011 - International Conference on Security and Cryptography
214

Now, σ
∗
= hc
∗
1
,c
∗
2
i is sent to A
I
as the challenge ci-
phertext. It should be noted that with overwhelming
probability, σ
∗
is a invalid ciphertext and since A
I
is
disallowed to query the strong decryption oracle with
σ
∗
as input, A
I
will not be able to identity whether σ
∗
is valid or not.
Phase II. A
I
performs the second phase of interaction,
where it makes polynomial number of queries to the
oracles provided by C with the following conditions:
• A
I
should not have queried the Strong Decryp-
tion oracle with (σ
∗
,PK
γ
,ID
γ
) as input. (It is to
be noted that PK
γ
is the public key corresponding
to ID
γ
during the challenge phase. A
I
can query
the decryptionoracle with (σ
∗
,PK
∗
,ID
γ
) as input,
∀PK
∗
6= PK
γ
)
• A
I
should not query the partial private key corre-
sponding to ID
γ
.
• A
I
can query the secret value corresponding to
ID
γ
and PK
γ
.
Guess. At the end of Phase II, A
I
produces a bit δ
′
to C , but C ignores the response and performs the fol-
lowing to output the solution for the RSA problem
instance.
• For each tuple of the form hk
1
,k
2
,ID
i
,h
3
i in list
L
3
, C checks whether k
e
1
?
= b. (where e and b are
taken from the RSA problem instance.)
• Outputs the corresponding k
1
value for which the
above check holds as the solution (i.e, a = k
1
) for
the RSA problem instance.
3.2.2 Confidentiality against Type-II Adversary
Theorem 3.2 Our certificateless public key encryp-
tion scheme RSA-CLE
1
is IND-RSA-CLE
1
-CCA2-II
secure in the random oracle model, if the CCDH
problem is intractable in Z
∗
n
, where n = pq and p, q,
(p− 1)/2, (q − 1)/2 are large prime numbers.
Due to page limitation we present the formal proof
of this theorem in the full version of the paper (Selvi
et al., 2010).
4 FULLY RSA BASED CLE
SCHEME (RSA-CLE
2
)
In this section, we propose the fully RSA based cer-
tificateless encryption scheme RSA-CLE
2
. The Type-
I security is similar to that of the Type-I security proof
of RSA-CLE
1
. We prove the security of the scheme
against Type-II attacks under adaptive chosen cipher-
text attack (CCA2) assuming the hardness of RSA
problem.
4.1 The RSA-CLE
2
Scheme
The proposed scheme comprises the following six al-
gorithms. Unless stated otherwise all computations
except those in the setup algorithm are done mod n.
Setup. The KGC does the following to initialize the
system and to setup the public parameters.
• Chooses two primes p and q, such that p = 2p
′
+1
and q = 2q
′
+ 1 where p
′
and q
′
are also primes.
• Computes n = pq and the Euler’s totient function
φ(n) = (p− 1)(q − 1).
• It also chooses three cryptographic hash func-
tions H : {0,1}
∗
→ Z
∗
n
, H
1
: {0,1}
∗
× Z
∗
n
→ Z
odd
n
,
H
2
: {0,1}
l
× Z
∗
n
→ Z
odd
n
and H
3
: Z
∗
n
× {0,1}
∗
×
{0,1}
∗
→ {0,1}
l+|Z
∗
n
|
, where l is the size of the
message.
• Now, KGC publicizes the system parameters,
params = hn, H,H
1
,H
2
,H
3
i and keeps the factors
of n, namely p and q as the master private key.
Partial Key Extract. This algorithm is executedby the
KGC and upon receiving the identity ID
A
of a user A
the KGC performs the following to generate the cor-
responding partial private key d
A
.
• Chooses x
A
∈
R
Z
odd
n
.
• Computes g
A
= H(ID
A
).
• Computes the partial public key PPK
A
= g
x
A
A
• Computes the value e
A
= H
1
(ID
A
,PPK
A
).
• Computes d
A
such that e
A
d
A
≡ 1 mod φ(n) and
sends the partial private key s
A
= x
A
+ d
A
mod
φ(n) and the partial public key PPK
A
to the user
through a secure channel.
Set Private Key. On receiving the partial private key
the user with identity ID
A
does the following to gen-
erate his secret key.
• Chooses two primes P
A
and Q
A
, such that P
A
=
2P
′
A
+ 1 and Q
A
= 2Q
′
A
+ 1, where P
′
A
and Q
′
A
are
also primes.
• Computes N
A
= P
A
Q
A
and the Euler’s totient
function φ(N
A
) = (P
A
− 1)(Q
A
− 1).
• Chooses ˆe
A
∈
R
Z
odd
N
A
as the user public key and
computes
ˆ
d
A
≡ ˆe
−1
A
mod φ(N
A
).
• Sets the private key as D
A
=
hD
(1)
A
,D
(2)
A
,D
(3)
A
,D
(4)
A
i = hs
A
,
ˆ
d
A
,P
A
,Q
A
i.
Set Public Key. The user with identity ID
A
com-
putes the public key corresponding to his pri-
vate key as PK
A
= hPK
(1)
A
,PK
(2)
A
,PK
(3)
A
,PK
(4)
A
i =
hPPK
A
,g
D
(1)
A
A
, ˆe
A
,N
A
i and makes it public.
CCA SECURE CERTIFICATELESS ENCRYPTION SCHEMES BASED ON RSA
215
Note that g
x
A
A
was sent by KCG to the user while set-
ting ID
A
’s partial private key. The validity of the pub-
lic key can be publicly verified using the following
verification test:
• Compute e
A
= H
1
(ID
A
,PK
(1)
A
) and g
A
= H(ID
A
).
• Check whether (PK
(2)
A
)
e
A
?
= (PK
(1)
A
)
e
A
g
A
Encryption. To encrypt a message m to a user with
identity ID
A
, one has to perform the following steps:
• Check the validity of the public key corresponding
to ID
A
.
• Choose r ∈
R
Z
odd
n
and ˆg ∈
R
Z
∗
N
A
.
• Compute e
A
= H
1
(ID
A
,PK
(1)
A
), g
A
= H(ID
A
) and
h = H
2
(m,r).
• Compute c
1
= g
h
A
, c
2
= ˆg
PK
(3)
A
mod N
A
and c
3
=
(mkr) ⊕ H
3
(PK
(1)
A
)
he
A
, ˆg,ID
A
.
Now, σ = (c
1
,c
2
,c
3
) is send as the ciphertext to the
user A.
Decryption. The receiver with identity ID
A
does the
following to decrypt a ciphertext σ = (c
1
,c
2
,c
3
):
• Computes k
1
=
(c
1
)
D
(1)
A
e
A
c
1
and k
2
= (c
2
)
D
(2)
A
mod
N
A
.
• Retrieves (mkr) = H
3
(k
1
,k
2
,ID
A
) ⊕ c
3
.
• Computes h
′
= H
2
(m,r) and checks whether c
1
?
=
g
h
A
.
User A accepts the message only if the above check
holds.
4.1.1 Confidentiality against Type-I Adversary
Theorem 4.1 Our certificateless public key encryp-
tion scheme RSA-CLE
2
is IND-RSA-CLE
2
-CCA2-I
secure in the random oracle model, if the RSA prob-
lem is intractable in Z
∗
n
, where p, q, (p − 1)/2 and
(q− 1)/2 are large prime numbers.
The proof for this theorem is similar to that of the
Type-I proof of RSA-CLE
1
(IND-RSA-CLE
1
-CCA2-
I).
4.1.2 Confidentiality against Type-II Adversary
Theorem 4.2 Our certificateless public key encryp-
tion scheme RSA-CLE
2
is IND-RSA-CLE
2
-CCA2-II
secure in the random oracle model, if the RSA prob-
lem is intractable in Z
∗
N
, where N = PQ and P, Q,
(P− 1)/2, (Q− 1)/2 are large prime numbers.
Due to page limitation we present the formal proof
of this theorem in the full version of the paper (Selvi
et al., 2010).
5 COMPARISON STUDY
We compare our schemes with the two existing se-
cure schemes (Lai et al., 2009) and (Sun et al., 2007).
We compare the level of security offered by each
schemes and the assumptions used to prove the secu-
rity against the two adversaries. The Type-I security
of the scheme in (Lai et al., 2009) is based on RSA as-
sumption and thus operates on composite groups and
is CPA secure against both Type-I and Type-II adver-
saries. The Type-II security is based on the composite
computational Diffie Hellman Assumption (CCDH).
Both Type-I and Type-II securities of the scheme in
(Sun et al., 2007) are based on the CDH assump-
tion in multiplicative groups with prime order. Our
schemes are based on RSA assumption and operates
on composite groups. The major operations in all the
schemes are multiplication and exponentiation, still,
we do not consider them for the comparison due to the
fact that the security parameters are different for RSA
based schemes and schemes based on multiplicative
groups with prime order.
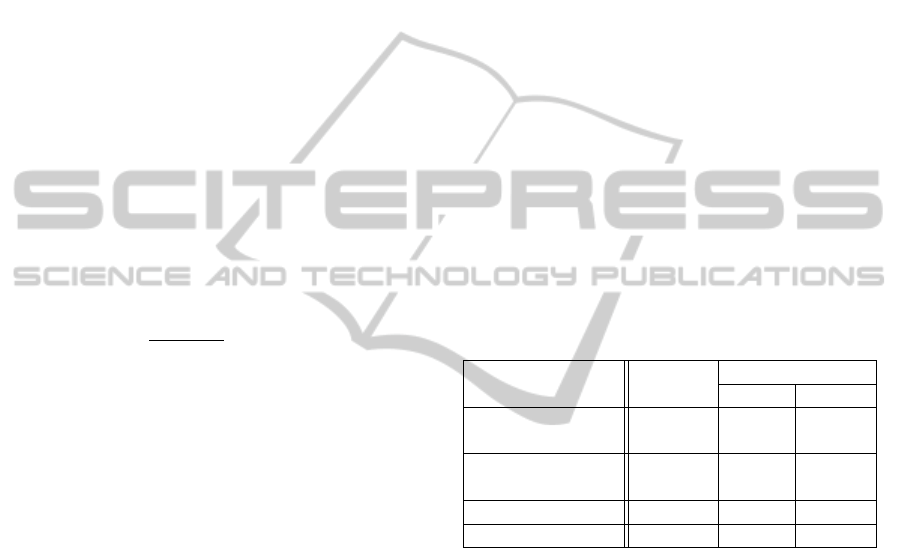
Table 1: Comparison of level of security and assumptions.
Scheme Security Assumption
Type-I Type II
Lai et al. CPA RSA CCDH
(Lai et al., 2009)
Sun et al. CCA2 CDH CDH
(Sun et al., 2007)
RSA-CLE
1
CCA2 RSA CCDH
RSA-CLE
2
CCA2 RSA RSA
6 CONCLUSIONS
In this paper, we have proposed two CCA2 secure cer-
tificateless encryption schemes. For the first scheme
the Type-I security is based on the RSA assumption
and Type-II security is based on the composite com-
putational Diffie Hellman assumption. Both Type-I
and Type-II securities of our second scheme are based
on the RSA assumption. Our schemes are quite novel
and based on entirely different key construct and pro-
tocol. It should be further noted that the existing
schemes (Lai et al., 2009) and (Sun et al., 2007) con-
sider a security model in which the Type-I adversary
is not provided the extract secret value oracle, for the
target identity. Our security model is stronger be-
cause we permit the extract secret value oracle cor-
responding to the target identity to the Type-I adver-
sary. In fact, the scheme in (Lai et al., 2009) is not
SECRYPT 2011 - International Conference on Security and Cryptography
216

secure with this oracle access. However, in our secu-
rity model the secret value corresponding to the target
identity is given to the Type-I adversary, which makes
it stronger. Moreover, we provide strong decryption
oracle for Type-I adversary, i.e, the decryption of a
ciphertext is provided by the challenger even if the
public key of the corresponding user is replaced af-
ter the generation of the ciphertext. Thus we provide
a CCA2 secure CLE whose security is partly based
on RSA and another scheme which is fully based on
RSA assumption. We have proved the security of our
schemes in the random oracle model. We leave it an
interesting open problem to design a CLE scheme in
the original model (Al-Riyami and Paterson, 2003)
with the security of the scheme fully based on RSA
assumption.
ACKNOWLEDGEMENTS
We would like to extend our sincere thanks to the
anonymous referees of the PROVSEC-2010 program
committee for given us insightful remarks which
helped us to improve the security proof of the
schemes.
REFERENCES
Al-Riyami, S. S. and Paterson, K. G. (2003). Certificateless
public key cryptography. In Advances in Cryptology
- ASIACRYPT 2003, volume 2894 of Lecture Notes in
Computer Science, pages 452–473. Springer.
Baek, J., Safavi-Naini, R., and Susilo, W. (2005). Cer-
tificateless public key encryption without pairing. In
Information Security - ISC 2005, volume 3650 of
Lecture Notes in Computer Science, pages 134–148.
Springer.
Boyen, X. (2003). Multipurpose identity-based signcryp-
tion (a swiss army knife for identity-based cryptog-
raphy). In Advances in Cryptology - CRYPTO 2003,
volume 2729 of Lecture Notes in Computer Science,
pages 383–399. Springer.
Castro, R. and Dahab, R. (2007). Two notes on the secu-
rity of certificateless signatures. In Provable Security -
ProvSec 2007, volume 4784 of Lecture Notes in Com-
puter Science, pages 85–102. Springer.
Cheng, Z. and Comley, R. (2005). Efficient certificateless
public key encryption. Cryptology ePrint Archive, Re-
port 2005/012. http://eprint.iacr.org/.
Dent, A. W. (2008). A survey of certificateless encryption
schemes and security models. International Journal
of Information Security, Vol-7(No-5):349–377.
Freeman, D., Scott, M., and Teske, E. (2010). A taxonomy
of pairing-friendly elliptic curves. Journal of Cryptol-
ogy, Vol-23(No-2):224–280.
Fujisaki, E. and Okamoto, T. (1999a). How to enhance the
security of public-key encryption at minimum cost.
In Public Key Cryptography, PKC ’99, volume 1560
of Lecture Notes in Computer Science, pages 53–68.
Springer.
Fujisaki, E. and Okamoto, T. (1999b). Secure integration
of asymmetric and symmetric encryption schemes. In
Advances in Cryptology - CRYPTO ’99, volume 1666
of Lecture Notes in Computer Science, pages 537–
554. Springer.
Huang, X., Susilo, W., Mu, Y., and Zhang, F. (2005). On
the security of certificateless signature schemes from
asiacrypt 2003. In Cryptology and Network Security
- CANS 2005, volume 3810 of Lecture Notes in Com-
puter Science, pages 13–25. Springer.
Lai, J., Deng, R. H., Liu, S., and Kou, W. (2009). Rsa-
based certificateless public key encryption. In In-
formation Security Practice and Experience - ISPEC
2009, volume 5451 of Lecture Notes in Computer Sci-
ence, pages 24–34. Springer.
Liu, J. K., Au, M. H., and Susilo, W. (2007). Self-generated-
certificate public key cryptography and certificateless
signature/encryption scheme in the standard model:
extended abstract. In ASIACCS 2007, Proceedings of
the 2nd ACM symposium on Information, Computer
and Communications Security, pages 273–283. ACM.
McCurley, K. S. (1988). A key distribution system equiv-
alent to factoring. Journal of Cryptology, Volume
1(Number 2):95–105.
Park, J. H., Choi, K. Y., Hwang, J. Y., and Lee, D. H.
(2007). Certificateless public key encryption in the
selective-id security model (without random oracles).
In Pairing-Based Cryptography - Pairing 2007, vol-
ume 4575 of Lecture Notes in Computer Science,
pages 60–82. Springer.
Selvi, S. D., Vivek, S., and Rangan, C. (2010). Cca2
secure certificateless encryption schemes based on
rsa. Cryptology ePrint Archive, Report 2010/459.
http://eprint.iacr.org/.
Shamir, A. (1984). Identity-based cryptosystems and signa-
ture schemes. In Advances in Cryptology, CRYPTO -
1984, volume 196 of Lecture Notes in Computer Sci-
ence, pages 47–53. Springer.
Shi, Y. and Li, J. (2005). Provable efficient certificateless
public key encryption. Cryptology ePrint Archive, Re-
port 2005/287. http://eprint.iacr.org.
Shmuely, Z. (February, 1985.). Composite diffie-hellman
public-key generating systems are hard to break.
Technical Report No. 356, Computer Science Depart-
ment, Technion-Israel Institute of Technology.
Sun, Y., Zhang, F., and Baek, J. (2007). Strongly secure
certificateless public key encryption without pairing.
In Cryptology and Network Security - CANS 2007,
volume 4856 of Lecture Notes in Computer Science,
pages 194–208. Springer.
CCA SECURE CERTIFICATELESS ENCRYPTION SCHEMES BASED ON RSA
217
