
PRIVACY-PRESERVING IN-NETWORK AGGREGATION
IN WIRELESS SENSOR NETWORK
Wei Zha and Wee Keong Ng
School of Computer Engineering, Nanyang Technological University, 639798 Singapore, Singapore
Keywords:
Privacy-preserving, Wireless Sensor Network, In-network Processing.
Abstract:
Ubiquitously deployed wireless sensor networks provide grate conveniences for environment monitoring.
However, it also brings the risk of violating privacy. Sensitive sensor data disclosed to malicious part may
cause unexpected lost. In this paper, we propose a privacy-preserving in-network aggregation protocol for
wireless sensor network based on the concept of data slicing, mixing and merging with a novel share key man-
agement scheme. Our protocol allows performing in-network aggregation in sensor network while keeps the
privacy of participates. Although we only study additive aggregation in this paper, our protocol can be easily
extended to other aggregation functions, including average, count and many other functions based on aggre-
gation as long as these aggregation functions can be reduced to additive aggregation function. Performance
evaluation yields the efficiency and effectiveness of our protocol.
1 INTRODUCTION
Wireless sensor networks are gaining more momen-
tum due to its widely military and civilian usages.
Major sensor network applications include object
tracking, environment surveillance and animal habi-
tats monitoring. Wireless sensor networks may thor-
oughly change the way people interact with their en-
vironments.
Sensor nodes are usually resource constrained to
archive low cost. Therefore, it is necessary to max-
imally utilize the existing resource of each sensor
node, such as performing in-network data aggregation
to reduce communication and energy cost. In practi-
cal, many sensor network applications concern aggre-
gated data readings of a certain region rather than in-
dividual sensor reading. Thus, the ability of perform-
ing in-network aggregation has received substantial
attention. Unless otherwise stated, we use the term
“aggregation” stands for both general “aggregation”
and “in-network additive aggregation” for brevity.
Usually, a data aggregation function is defined as
f =
∑
N
i=1
d
i
(t), where d
i
(t) is the sensor reading of
node i at time t. A simple aggregation in sensor net-
work could be that each sensor node sends back their
readings to sink node upon receiving query; and sink
node calculates the sum off-line. It is easy but not
efficient. To address this issue, aggregation methods
have been proposed (Madden et al., 2002; Deshpande
et al., 2003; Solis and Obraczka, 2004; Tang and Xu,
2006).
On the other hand, as sensor network applications
grow, privacy becomes one of the most challenging is-
sues. Many sensor network applications include sen-
sitive measurements of people daily life. People may
not allow that sensor network to be deployed if they
find their private information may be disclosed to oth-
ers. In the following, we brief a motivating appli-
cation that require privacy-preserving aggregation in
wireless sensor networks.
Scenario: Assume National Institute of Health
(NIH) wants to measure the average weight of
teenagers to analyze the health level of the young gen-
eration. Individual weight information can be easily
collected by the sensor mounted in their shoes and
sent back to NIH. However, selected participants may
not wish to disclose their weight information. On
the other hand, it is also not necessarily for NIH to
know each individual weight information. The sum
of participants’ weight and the number of participants
would be enough. A solution which can satisfy the
needs of both NIH and participants are desirable.
From aforementioned scenario, we see the impor-
tance of preserving individual privacy. A feasible so-
lution to obtain accurate aggregation while preserving
the privacy of individual is desirable. An add-on ben-
efit of private-preserving aggregation includes com-
munication bandwidth and energy conserving as well
223
Zha W. and Keong Ng W..
PRIVACY-PRESERVING IN-NETWORK AGGREGATION IN WIRELESS SENSOR NETWORK.
DOI: 10.5220/0003806602230228
In Proceedings of the 1st International Conference on Sensor Networks (SENSORNETS-2012), pages 223-228
ISBN: 978-989-8565-01-3
Copyright
c
2012 SCITEPRESS (Science and Technology Publications, Lda.)

as enhanced security.
1.1 Related Work
End to end encryption is a well known method in
computer network to guarantee private communi-
cation as long as the two participates have agree-
ment on public/private keys. However, it is not a
good candidate because in-network aggregation can-
not be applied. There are some works about privacy-
preserving aggregation in sensor network have al-
ready be done (Girao et al., 2005; Castelluccia et al.,
2005; He et al., 2007; Feng et al., 2008; Zhang et al.,
2008; Westhoff et al., 2006; Roy et al., 2006; Shi
et al., 2010). Due to space limitation, we only briefly
review two works, PDA and PriSense, which are most
close to our work. Some details of their works are ex-
plained in next section.
PDA (He et al., 2007) proposes a scheme
called Slice-Mix-aggRegaTe (SMART) for privacy-
preserving aggregation using a random key distribu-
tion mechanism. Before sensor nodes deployment,
PDA generates a large key-pool and randomly draw
k keys for each sensor node. Upon deployment, only
the sensor nodes hold the same key can establish a
link. When a sensor i is going to send its read-
ing data d
i
, it slices d
i
into m + 1 pieces, d
i, j
where
j ∈ [1,m + 1]. It keeps one data slice, encrypts and
sends out the rest of data slices to those nodes which
share the same key. Every node with a data to report
performs this process. When this process is finished,
each node holds may encrypted date slices. It then de-
crypts them and adds them together. Now, each node
holds a mixed data which does not present any real in-
formation. These mixed data can be sent to sink node
by using any existing aggregation methods (Yao, Y.
and Gehrke, 2002; Krishnamachari, L. and Estrin, D.
and Wicker, 2002; Fasolo, E. and Rossi, M. and Wid-
mer, J. and Zorzi, 2007; Madden et al., 2002).
PriSense (Shi et al., 2010) is based on the same
slicing, mixing and merging idea but different in share
key generating and management. In their scenario,
sensor nodes are with mobile ability. Only sensor
nodes registered with base-station can report their
readings. When a node registers at a base-station, that
base-station assigns an ID to that node and it peri-
odically broadcasts the active node IDs of this net-
work. When node A with ID
A
wishes to send a data
slice to node B with ID
B
, it calculates a share key
key
A,B
= F(H(ID
A
),H(ID
B
)), where H(∗) is prede-
fined good hash function and F(∗) is predefined map-
ping function. Before sending the real data slice,
node A sends a test message to node B which is a
random number r encrypted by their share key de-
noted as hri
key
A,B
. If node B can successfully return
hr + 1i
key
A,B
, A considers this link is secure and send a
data slice to node B. The rest of steps are exactly the
same as in PDA.
1.2 Our Contribution
In this paper, we propose a privacy-preserving in-
network aggregation protocol which shares the sim-
ilar idea as PDA and PriSense on data slicing, mix-
ing and merging concept, but differs significantly in
the key generating and management. PDA randomly
draws k share keys into sensor node from a large key-
pool. Due to memory constrain, value of k cannot be
too large. While small k value increases the possi-
bility of network disconnection. PriSense generates
share keys on demands. However, malicious parties
can easily decrypt encrypted data slices since active
node IDs are known to all.
In our protocol, we hire a well known algo-
rithm, Diffie Hellman Key Exchange scheme (Hell-
man, 2002), to generate share keys on demands. Thus,
it is impossible for malicious part to decrypts en-
crypted data slices without the knowledge of share
key. Because two nodes always can make agreement
on share key, network disconnection will never hap-
pen in our protocol. Our work is more secure than
PriSense and more reliable than PDA.
The rest of this paper is organized as follows. In
Section 2, we recall the concept of data slicing, mix-
ing and merging and introduce our protocol. Then,
we theoretically analyze our protocol and compare it
with PDA and PriSense in terms of efficiency and se-
curity in section 3. In section 4, experimental results
are given. In section 5, we summarize this work and
point out some future work.
2 SYSTEM MODEL
Our protocol is based the concept of data slicing, mix-
ing and merging but with a more secure and efficient
key management strategy. In this section, we first re-
view this concept, then introduce a different key man-
agement scheme.
2.1 Data Slicing, Mixing and Merging
Approach
In wireless sensor networks, a data aggregation func-
tion is defined as: f =
∑
N
i=1
d
i
, where d
i
is individual
sensor reading and N is the number of sensor nodes.
Generally, there are 3 steps in data slicing, mixing
and merging approach:
SENSORNETS 2012 - International Conference on Sensor Networks
224

Step 1: Assume node i is going to send a data d
i
, it
first slices d
i
into m + 1 pieces, d
i
=
∑
m+1
j=1
d
i, j
, where
m + 1 ≤ J. J is the number of neighbors of node i.
Step 2: Node i keeps one data slice and sends the
rest m pieces to its neighbors. Note that, node i sends
data slice to its neighbor only if they share the same
key. In PDA, each node randomly select m nodes
as its receiving nodes from its one-hop neighbors.
PriSense has studied different receiving nodes selec-
tion strategies, e.g., one-hop, h-hops and random.
Their results show that selecting one-hop neighbors
as receiving nodes is the most simple and efficient
one. In this work, we also randomly choose receiv-
ing nodes from one-hop neighbors.
Step 3: Each node waits for a long enough period to
make sure there is no more data slice to receive. Then,
each node sums all the data slices it has received to-
gether with its own data slice (if any), denoted as d
0
i
,
and sends it to sink node. In this step, data is usually
sent by a tree structure to perform aggregation. Many
existing algorithms can be apply. In this paper, we
omit the detail of this step for brevity.
This approach is based on the fact that:
f =
N
∑
i=1
d
i
=
N
∑
i=1
m+1
∑
j=1
d
i, j
=
N
∑
i=1
d
0
i
An example is shown in Figure 1. Node 1, 3 and
5 have data satisfies a coming query, denoted by gray
nodes. Each sensor reading is sliced into 3 pieces.
One piece is kept by itself, the rest two pieces are
sent to randomly selected one-hop neighbors as illus-
trated by Figure 1(a). Each node waits for a while
to make sure there is no more data slice to receive.
Then, each node decrypts received data and mix them
with its own data (if any) as illustrated by Figure 1(b).
Although the mixed data does not represent individ-
ual sensor reading any more, mixed data are still en-
crypted before sending out for secure purpose. On
the way to sink node, medium node can perform ag-
gregation to reduce communication. Take node 5 for
instance, instead of sending d
0
3
, d
0
4
and d
0
5
to node 6
separately, node 5 sends the sum d
0
3
+ d
0
4
+ d
0
5
to node
6. One possible data merging and aggregation way is
shown in Figure 1(c). The final sum at sink node is
exactly the sum of d
1
+ d
3
+ d
5
because:
d
1
+ d
3
+ d
5
=
∑
i∈[1,3,5]
3
∑
j=1
d
i, j
=
6
∑
i=1
d
0
i
2.2 Share Key Set Up and Management
In our protocol, there is a link between node A and
B only if they have the same share key Key
A,B
. Data
transmitted through this link is encrypted by Key
A,B
and decrypted by the same key upon receiving. In an-
other words, node A sends out hd
i, j
i
Key
A,B
. Upon re-
ceiving, node B decrypts hd
i, j
i
Key
AB
with Key
AB
. The
motivation of using symmetric encryption is based on
the report of Matt (Eschenauer and Gligor, 2002). For
a sensor node such as Motorola MC68328, a 1024bit
RSA encryption operation costs 42mJ energy. While
a 1024bit AES encryption costs only 0.104mJ energy.
PDA and PriSense both adopted symmetric encryp-
tion in their works.
Different from PDA, our protocol only generates
share keys when a node is ready to distribute its data
slices. Well known Diffie Hellman Key Exchange
scheme (Hellman, 2002) is adopted by our work.
There are 3 steps in Diffie Hellman Key Exchange for
generating share key between two nodes. We assume
node A is going to send node B a data slice d
i, j
:
Step 1: Node A generates a prime P and a generator
G, send them to node B in clear text.
Step 2: Node A generates a random number R
A
and send the result of S
A
= Mod(G
R
A
,P) to node
B. Node B does this simultaneously and sends S
B
=
Mod(G
R
B
,P) to node A.
Step 3: Upon receiving, node A can calcu-
late the share key by Key
AB
= mod((G
R
B
)
R
A
,P).
Node B could obtain the same key by Key
AB
=
mod((G
R
A
)
R
B
,P).
Thus, share key is known by both node A and B.
Node A encrypts data slice d
i, j
and sends to B. Upon
receiving, node B is able to decrypt it correctly.
Note that, it is not necessary for two nodes to make
agreement on share key every time. Old share keys
can be reused to archive energy conservation. One
possible strategy could be every node keeps k share
keys with each one-hop neighbor. A node randomly
pick up one key from k keys to encrypt data as long as
the key is not expired. Whenever the available keys
are less than k due to key expiration or other security
purpose, it makes a new agreement on share key with
the receiving node.
3 COMPARISON AND
PERFORMANCE EVALUATION
PDA and PriSense adopt the same data slicing, mix-
ing and merging concept. We compare our work with
them in this section and evaluate the performance of
our work.
PRIVACY-PRESERVING IN-NETWORK AGGREGATION IN WIRELESS SENSOR NETWORK
225

4
6
5
3
2
1
Sink node
1,1
d
1,2
d
5,3
d
5,2
d
5,1
d
3,3
d
3,2
d
3,1
d
1,3
d
(a) Data slicing and distribution, m = 2.
4
6
5
3
2
1
Sink node
3,31,11
ddd
c
5,36
dd
c
5,14
dd
c
3,25,15
ddd
c
1,12
dd
c
1,33,13
ddd
c
(b) Data mixture.
4
6
5
3
2
1
Sink node
1
d
c
4
d
c
5
d
c
2
d
c
3
d
c
6
d
c
(c) Data merging and aggregation.
Figure 1: Data slicing, mixing and merging approach. Nodes with data to send is represented by gray nodes. For simplicity,
each node breaks its data into 3 pieces in our illustration.
3.1 Comparison with PDA
As mentioned before, key management adopted by
PDA pre-generates a large Key-pool off-line and ran-
domly assigns k keys to each node before deployment.
That means the k keys will serve that node for life-
time (Eschenauer and Gligor, 2002). One disadvan-
tage of this key management strategy is unnecessary
memory occupancy. The probability of two nodes
with the same key is not high. Two nodes usually have
a very few overlapping keys. Assume each node share
α keys with its neighbors on average, (k − α)/k% key
storage memory is wasted. For the parameters used in
PDA, (k − α)/k > 90%. Besides, there is possibility
that network is disconnected in PDA.
Another disadvantage of PDA is that once de-
tected the share keys of certain node are disclosed,
that node must be revoked, because that node is un-
able to obtain new share keys. In our work, share keys
are generated on demand. Possibly only a few keys
will be stored in memory comparing with k keys in
PDA. Besides, whenever a share key disclosure is de-
tected, new share key can be generated distributively
in real time. Considering the risk of disclosing share
key, our key management strategy is more secure.
3.2 Comparison with PriSense
PriSense targets mobile sensor network. Sensor node
may join and leave a network due to mobility. When a
node joins network, it must register with base-station
to obtain an unique active ID. That ID may be re-
signed to other node if this node leaves network.
Base-station periodically broadcasts all the active IDs
in the network so that each node can get an overview
of this network. When node A with ID
A
wants to
send a data slice to node B with ID
B
, it calculates a
share key key
AB
= F(H(ID
A
),H(ID
B
)), where H(∗)
is a predefined good hash function and F(∗) is a pre-
defined mapping function (Zhang and Fang, 2006).
Before sending the actual data, node A generates a
random number r, encrypts and sends to node B. If
node B can correctly return hr + 1i
Key
AB
to node A, A
sends hd
i, j
i
Key
AB
to B.
Key management strategy in PriSense is much less
secure than PDA and our protocol. A malicious
node can calculate a share key to decrypt overheard
data as long as it knows the IDs of sender and re-
ceiver. Since base-station periodically broadcasting
active node IDs, it is easy for malicious node to cal-
culate a share key with the knowledge of predefined
hash and mapping function.
Additionally, PriSense has studied the receiving
node selection strategies, namely, one-hop, h-hop and
random selection. According to their experimental re-
sults, one-hop receiving node strategy is the most cost
efficient one. Both PDA and our work choose the one-
hop receiving node strategy by default.
3.3 Performance Evaluation
We evaluate our protocol in terms of disclosure prob-
ability and communication cost.
• P
d
(Disclosure Probability): is the probability
that adversaries obtain a node’s data.
• E
c
(Communication Cost): is the total energy
consumption for answering one query.
Disclosure Probability Analysis. Suppose a sensor
network is consist of N sensor nodes, among which
there are n malicious nodes collude to get data d
i
from
node I. The probability that a node is malicious is
P(M) = n/N. A node with data d
i
slices data into
m+1 pieces before sending. To get d
i
, malicious node
must get all the m + 1 pieces.
To get the m data slices, at least m receivers must
be malicious nodes. The probability is P(M)
m
. The
remaining one piece kept by node I can only be calcu-
lated when all the data received by I is from malicious
node and the receiver of d
0
i
is also malicious. Assume
node I receives J pieces of data before sending out
mixed data d
0
i
, the probability of obtaining that one
piece data is P(M)
J+1
(we assume the worst case that
m receiver nodes are different with J sender nodes). In
conclusion, at least m+J +1 nodes need to collude to
get d
i
.
P
d
= P(M)
m
× P(M)
J+1
= (
n
N
)
m+J+1
SENSORNETS 2012 - International Conference on Sensor Networks
226
Communication Cost Analysis. In the following of
this paper we use Φ to denote the set of nodes with
data to send and |Φ| is the number of nodes. We
generally classify communication cost E
c
into 3 parts,
E
c1
, E
c2
and E
c3
.
E
c1
represents the communication cost of dis-
tributing data slice from nodes in Φ to their one-hop
neighbors. Recall the process of Diffie Hellman Key
Exchange scheme, node A sends a Prime P and a gen-
erator G to node B. Then, A and B exchange some
information based on P and G. There are 3 messages
occurred in total. We assume these 3 messages are in
the same length, denote as l
key
, for simplicity. With
the agreement on share key, A sends B encrypted data
slice. We use l
data
to denote the length of that mes-
sage. Each node in Φ sends out m pieces of encrypted
data slice, we have
E
c1
= |Φ| × m × (3 × l
key
+ l
data
)
E
c2
represents the communication cost of submit-
ting mixed data. In this process, all the nodes in Φ
will submit its data. Due to data slice distribution,
some nodes which do not belong to Φ but received
data slices also need to submit their data. The prob-
ability that a node receiving a data slice is m/N − 1,
and the probability that a node receives at least one
data slice is 1 − (1 −
m
N − 1
)
|Φ|
. Among the N nodes,
N − |Φ| nodes are not generating any data but may
be chosen as receiving nodes. We denote this kind of
nodes by set N
s
,
|N
s
| = (N − |Φ|) × (1 − (1 −
m
N − 1
)
|Φ|
)
Nodes in Φ definitely have data to submit. For
simplicity, we assume the data to submit is also in the
length l
data
, we have
E
c2
= ((N − |Φ|) × (1 −(1−
m
N − 1
)
|Φ|
)+|Φ|)× l
data
In the process of submitting mixed data, some
medium nodes will be involved. They neither be-
long to Φ or N
s
. The number of this kind of nodes
are totally depends on the aggregation methods. It
varies when different methods apply. Since we do
not specific any particular aggregation methods in our
protocol, we leave it as E
c3
for simplicity. Thus,
we can compute the total communication cost E
c
=
E
c1
+ E
c2
+ E
c3
.
E
c
= E
c3
+ |Φ| × m × (3 × l
key
+ l
data
)
+ ((N − |Φ|) × (1 − (1 −
m
N − 1
)
|Φ|
) + |Φ|) × l
data
10 20 30 40 50 60 70 80 90
0
0.1
0.2
0.3
0.4
0.5
0.6
Number of Malicious Nodes
Disclosure Probability
m = 2
m = 3
m = 4
m = 5
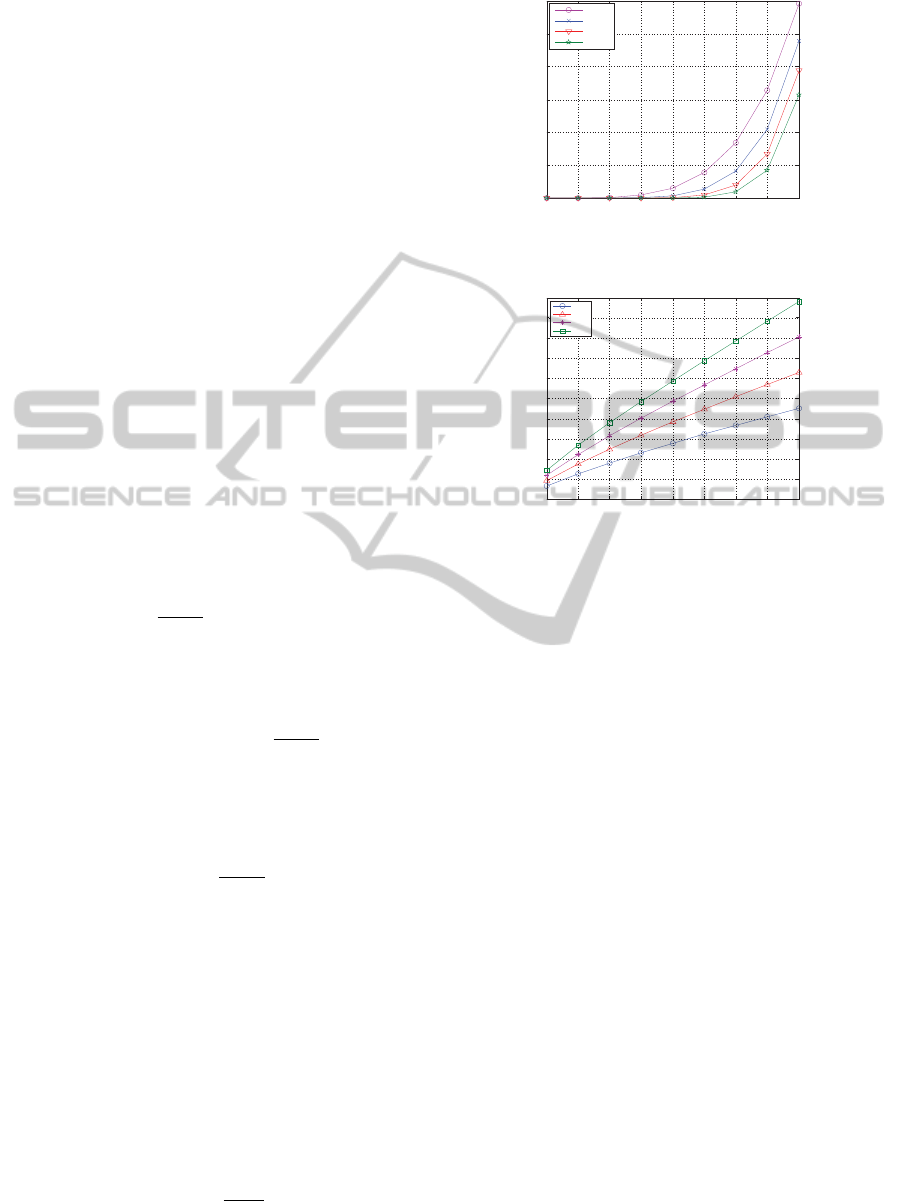
Figure 2: Impact of malicious nodes and m on disclosure
probability.
10 20 30 40 50 60 70 80 90
0
0.5
1
1.5
2
2.5
3
3.5
4
4.5
5
x 10
4
Number of Source Nodes
Communication Cost
m = 2
m = 3
m = 4
m = 5
Figure 3: Impact of Φ and m on Communication cost.
4 EXPERIMENTAL RESULTS
In this section, we simulate a wireless sensor net-
work with N = 100 nodes. Considering the value ex-
changed at the second step of negotiating share key
could be very huge, we assign 16Byte to l
key
and
50Byte to l
data
. For simplicity, we adopt the same data
aggregation method proposed in PDA for step 3 of
data slicing, mixing and merging approach. A simple
brief of the aggregation method is given here. Upon
deployment, each node has a probability p to choose
itself as cluster node and send out HELLO message.
If a node does not decide to be a cluster node, it stores
all the HELLO messages it has received. When the
cluster node selection period is over, each non-cluster
node randomly picks up one cluster node based on the
HELLO messages it has received. Thus, each node
sends mixed data to its cluster node. Each cluster
node can perform data aggregation before forwarding
data to sink node.
We first test the disclosure probability with differ-
ent number of malicious nodes, then repeat this ex-
periment with different m values. Figure 2 shows the
results. We can see that the more malicious nodes
are, the higher the disclosure probability is, and vice
versa. It is quite obvious that the more malicious
nodes, the higher chance a data would be disclosed.
We also note that, while the numbers of data slices in-
PRIVACY-PRESERVING IN-NETWORK AGGREGATION IN WIRELESS SENSOR NETWORK
227

crease, the disclosure probability decreases. It is easy
to understand that the more data slices a node made,
the lower chance for malicious nodes to collect all of
them. For all the m values, disclosure probability are
very low when the malicious nodes are less than 50%.
That indicates our method is quite secure even if half
of the network is of malicious nodes.
We further record the communication costs with
different source nodes Φ and m. The results are il-
lustrated by Figure 3. Communication costs increase
while |Φ| increase. It is intuitive that the more nodes
have data to send, the more communication cost will
be occurred in the network. It is independent of the
number of malicious nodes. Number of data slices
m does have a significant impact on communication
cost, especially when the number of source nodes Φ
is high.
5 CONCLUSIONS
In this paper, we point out the needs of performing
privacy-preserving in-network aggregation in wire-
less sensor networks. Two motivating applications are
given. Some existing works have been done. How-
ever, they are either not secure enough or overheads
of key management is too high. In our work, we reuse
their framework but with a more secure and efficient
key management methods. The security and commu-
nication cost have been thoroughly analyzed. Com-
parisons with the two most similar works have been
made. Experimental results confirmed the correctness
of our work. In the future work, we are going to ex-
tend our work to other aggregation methods, such as
Min/Max. We are also going to study other mutual au-
thentication algorithms with lower computation and
communication overhead.
REFERENCES
Castelluccia, C., Mykletun, E., and Tsudik, G. (2005). Effi-
cient Aggregation of Encrypted Data in Wireless Sen-
sor Networks. In MobiQuitous.
Deshpande, A., Nath, S., Gibbons, P. B., and Seshan,
S. (2003). Cache-and-Query for Wide Area Sensor
Databases. In International Conference on Manage-
ment of Data, pages 503–514.
Eschenauer, L. and Gligor, V. D. (2002). A Key-
Management Scheme for Distributed Sensor Net-
works. In Proceedings of the 9th ACM Conference on
Computer and Communications Security, pages 41–
47. ACM.
Fasolo, E. and Rossi, M. and Widmer, J. and Zorzi, M.
(2007). In-network aggregation techniques for wire-
less sensor networks: a survey. In Wireless Communi-
cations, pages 70—-87.
Feng, T., Wang, C., Zhang, W., and Ruan, L. (2008). Confi-
dentiality Protection for Distributed Sensor Data Ag-
gregation. In International Conference on Computer
Communications, pages 56–60.
Girao, J., Westhoff, D., and Schneider, M. (2005). CDA:
Concealed Data Aggregation for Reverse Multicast
Traffic in Wireless Sensor Networks. In IEEE Interna-
tional Conference on Communications, pages 3044–
3049.
He, W., Liu, X., Nguyen, H., Nahrstedt, K., and Abdelzaher,
T. T. (2007). PDA: Privacy-Preserving Data Aggre-
gation in Wireless Sensor Networks. In IEEE Inter-
national Conference on Computer Communications,
pages 2045–2053.
Hellman, M. E. (2002). An Overview of Public Key Cryp-
tography. In IEEE Communications Magazine, pages
42–49.
Krishnamachari, L. and Estrin, D. and Wicker, S. (2002).
The impact of data aggregation in wireless sensor net-
works. In International Conference on Distributed
Computing Systems Workshops, pages 575—-578.
Madden, S., Franklin, M. J., Hellerstein, J. M., and Hong,
W. (2002). TAG: a Tiny AGgregation service for ad-
hoc sensor networks. In ACM SIGOPS Operating Sys-
tems Review, pages 131–146.
Roy, S., Setia, S., and Jajodia, S. (2006). Attack-Resilient
Hierarchical Data Aggregation in Sensor Networks. In
Proceedings of the fourth ACM workshop on Security
of ad hoc and sensor networks, pages 71–82. ACM.
Shi, J., Zhang, R., Liu, Y., and Zhang, Y. (2010). Prisense:
privacy-preserving data aggregation in people-centric
urban sensing systems. In INFOCOM, pages 1–9.
IEEE.
Solis, I. and Obraczka, K. (2004). The Impact of Tim-
ing in Data Aggregation for Sensor Networks. In
IEEE International Conference on Communications,
volume 6, pages 3640–3645. IEEE.
Tang, X. and Xu, J. (2006). Extending Network Lifetime for
Precision-Constrained Data Aggregation in Wireless
Sensor Networks. In IEEE International Conference
on Computer Communications, volume 6, pages 1–12.
Westhoff, D., Girao, J., and Acharya, M. (2006). Con-
cealed Data Aggregation for Reverse Multicast Traf-
fic in Sensor Networks: Encryption, Key Distribu-
tion, and Routing Adaptation. In IEEE Transactions
on Mobile Computing, pages 1417–1431. IEEE Com-
puter Society.
Yao, Y. and Gehrke, J. (2002). The cougar approach to in-
network query processing in sensor networks. In SIG-
MOD, pages 9—-18.
Zhang, W., Wang, C., and Feng, T. (2008). GP2S: Generic
Privacy-Preservation Solutions for Approximate Ag-
gregation of Sensor Data (concise contribution). In
IEEE International Conference on Pervasive Comput-
ing and Communications, pages 179–184. IEEE.
Zhang, Y. and Fang, Y. (2006). ARSA: An Attack-Resilient
Security Architecture for Multihop Wireless Mesh
Networks. In IEEE Journal on Selected Areas in Com-
munications, pages 1916–1928. IEEE.
SENSORNETS 2012 - International Conference on Sensor Networks
228
