
USING FACEBOOK ACTIVITY TO INFER SOCIAL TIES
∗
Sandra Servia Rodr´ıguez, Rebeca P. D´ıaz Redondo, Ana Fern´andez Vilas and Jos´e J. Pazos Arias
Department of Telematics Engineering, Escuela de Ingenier´ıa de Telecomunicaci´on, University of Vigo, Vigo, Spain
Keywords:
Social Networks, Facebook, Tie Signs, Tie Strength, Social Sphere.
Abstract:
Clearly there is a growing omnipresence of social networking sites in particular and social services in general.
Given this translation of social relations into the cloud, services are facing the problem of deciding, for every
user, what are the really relevant links to provide a social-sensitive response. For this, we postulate that
users’ interaction is a real sign of social relationships which can supplement the topological connections in
social sites. To this end, this paper provides a model for calculating the strength of social ties based on
interaction information collected from various social APIs in the cloud. From this general model, we detail
the deployment of an interaction network for the Facebook case.
1 INTRODUCTION
Social networks have become increasingly popular,
turning into an important mean of communication
among people of all ages. Although they do not ex-
pect to supply traditional communication, they are
an important complement to it, allowing users to
keep their contact list, share information and in-
teract with others through cross-posting, messaging,
games, social events and applications. Recently, sev-
eral researches on online social networks have came
up as consequence of their importance among Inter-
net users. A plentiful number of them is focused
on improving users’ social experience by means of
enhanced-social applications using, for this purpose,
information from their profiles and links in these net-
works, as in (Wilson et al., 2009)’s and (Chen and
Fong, 2010)’s case. The former suggests improv-
ing a white-listing system for email using social ties
strength that allows emails between friends to bypass
standard spam filters or detecting Sybil identities
2
in
an online community to protect distributed applica-
tions. The latter, in turn, proposes a framework of col-
laborative filtering on social network, for which study
∗
Work funded by the Ministerio de Educaci´on y Cien-
cia (Gobierno de Espa˜na) research project TIN2010-20797
(partly financed with FEDER funds), and by the Con-
seller´ıa de Educaci´on e Ordenaci´on Universitaria (Xunta de
Galicia) incentives file CN 2011/023 (partly financed with
FEDER funds).
2
Sybil attacks happens when a malicious user pretends
to have multiple identities -Sybil identities- to get to control
a peer-to-peer system.
the contribution of trust, similarity between profiles,
relation between users and reputation.
These applications, as others recently developed,
assume that social ties between users and their friends
have not the same strength, i.e. the more interaction
they have, the more relevant their tie will be. So,
improving the effectiveness of these applications re-
quires distinguishing strong ties from weak ties in so-
cial networks. With this aim, we have developed an
approach to infer social ties between users from their
interactions on Facebook. We have selected Facebook
to put into practice our approach of gathering users’
interaction activity because it is the largest social net-
work with over 800 million active users (Facebook,
2011). Besides considering different tie signs (which
denote interaction) on Facebook, we take into account
aspects such as that relationships change over time
and that they are more intense when less people are
involved in them.
This paper is organised as follows. The following
section provides a selection of works related to our
proposal. Section 3 describes the context in which our
application is included. Before detailing our method
to infer ties strength indexes from Facebook in Sec-
tion 5, in next section (Section 4) Facebook signs that
imply interaction between users are indicated. In Sec-
tion 6, we provide an experimental evaluation that
shows how our application works properly. Finally,
in Section 7, a discussion in this field is provided.
325
Servia Rodríguez S., P. Díaz Redondo R., Fernández Vilas A. and J. Pazos Arias J..
USING FACEBOOK ACTIVITY TO INFER SOCIAL TIES.
DOI: 10.5220/0003907803250333
In Proceedings of the 2nd International Conference on Cloud Computing and Services Science (CLOSER-2012), pages 325-333
ISBN: 978-989-8565-05-1
Copyright
c
2012 SCITEPRESS (Science and Technology Publications, Lda.)

2 RELATED WORK
The concept of tie strength was introduced by (Gra-
novetter, 1973), who defines it as a function of dura-
tion, emotional intensity, intimacy and exchange of
services from which ties are split into ’strong’ and
’weak’ ties. Although this work, as well as many
others about this subject, are included in the field of
social science, there are also several studies related
to the same topic in computer science. For exam-
ple, (Mutton, 2004) describes a method of inferring
a social network by monitoring an IRC channel in
which, to obtain the network, an IRC bot observes
the messages exchanged between users in the channel
and, from this information, infer the social network in
which they are involved. Other example is the case of
(Tyler et al., 2005), who propose a method for identi-
fying communities using e-mail data.
In the case of online social networks, they already
provide users’ social graphs, which are made of links
between users and their contacts in these networks.
However, initial studies on interaction networks (net-
works made up of ties among users who often interact
through social networks) have brought great insights
into how an interaction network is structurally differ-
ent from the social network. Examples of these works
are (Wilson et al., 2009), (Viswanath et al., 2009) or
(Backstrom et al., 2011), which study users’ activity
on Facebook to built on the interaction network, tak-
ing into account different interaction signs. In (Wil-
son et al., 2009) case, for each user, these signs are
the social graph (they only consider interactions be-
tween Facebook friends), wall-posts and photo com-
ments, whereas (Viswanath et al., 2009) only take
into account wall-posts to study the varying patterns
of interaction over time affect the overall structure of
the interaction network. Finally, (Backstrom et al.,
2011) study how Facebook users allocate attention
across friends, taking into account, as well as mes-
sages, comments and wall-posts, information about
how many times one user views another’s profile page
or photos posted by another user. Both (Wilson
et al., 2009) and (Viswanath et al., 2009) use Face-
book data obtained using crawlers otherwise, (Back-
strom et al., 2011) retrieve data directly from Face-
book, since information about users’ passive inter-
actions such as browsing updates, photos or profiles
from their friends through homepage, is not available.
Other studies to deduce the interaction network, as
in (Gilbert and Karahalios, 2009), are supported by
the information kept in users’ profiles: age, political
ideals or distance between hometowns, for instance.
However, (Kahanda and Neville, 2009) study how to
infer the nature and strength of relationships among
Facebook’s members using attribute-based features
(gender, relationship-status,...), topological features
(connectivity of the users in the friendship graph),
transactional features (Wall postings, picture posting
and groups) and network-transactional features (Wall
posting in another users Wall,...) to obtain users’ ”top-
friends”. They have concluded that the most out-
standing features to predict tie strength are network-
transactional features, followed by transactional ones.
In this paper, we propose an approach to infer
social ties between users from their interactions on
Facebook. Although studies like (Gilbert and Kara-
halios, 2009) consider information kept in users’s pro-
files (age, political ideals,...), from our point of view,
they are not as reliable as other signs left by users
in the network, mainly different modes of interaction
which we consider in our application. Apart from
other features of interaction, we consider wall-posts,
tagged photos or membership of a group as in the case
of (Kahanda and Neville, 2009). However, in our
propose, as well as using these features, we take into
account aspects such as that relationships change over
time and that they are more intense when less people
are involved in them.
Finally, aforementioned works get Facebook data
using crawlers or directly from Facebook servers.
However, as our approach is part of a large project
to provide personalized services in the cloud, we are
interested in using information obtained through so-
cial network APIs. In this paper, we propose getting
the most out Facebook API and taking into account
all users’ information available having their suitable
permissions, which is relevant from the point of view
of interaction. Anyway, the procedure can be easily
generalized to any social networking site with a pub-
lic API.
3 APPLICATION CONTEXT
Our application to infer tie strength from Facebook
interactions is part of the project CLOUDIA
3
, which
has the goal of defining a suitable ecosystem to as-
sist the users in finding existing services in the cloud
to satisfy their specific needs, and also to detect and
cater for new business opportunities in the form of
services demanded but not existing as a unique whole.
To this aim, it will use information stored in the dif-
ferent social networks in which the users may partic-
ipate.
In CLOUDIA, to find suitable services, the assis-
tance has to be personalized to each user, i.e. depend-
3
http://gssi.det.uvigo.es/index.php?option=com
content
&view=article&id=210&Itemid=439&lang=en
CLOSER2012-2ndInternationalConferenceonCloudComputingandServicesScience
326

Figure 1: Inferring social ties application.
ing on user’s interests and needs, different services
will be recommended. Last years, several collabora-
tive filtering recommender systems have been devel-
oped. All of them are based on the premise that users
who have historically had similar interests will prob-
ably continue having it into the present. An important
issue in these systems is finding a set of users, known
as neighbors, that have a history of agreeing with the
target user (having rated different services similarly,
tending to use similar set of services,...). Moreover,
several authors, like (O’Donovan and Smith, 2005),
have improved neighborhood formation taking into
account, besides similarity between profiles, social in-
fluence or trust between users. As in real life, when
we look for an advice for a service (health, commerce,
learning,...) we will often turn to our friends, on the
basis that we have similar service preferences overall.
In the case of an applications, it is necessary know-
ing who are user’s friends, i.e. users in which target
user trusts when looks for a recommendation. Like-
wise, intensity of social relationships often varies, and
recommender should be up on these changes. Since
it is not feasible that users report to the application,
we may get users’ ties from social networks sites in
which they have subscribed. However, as (Wilson
et al., 2009) shows, social network users usually tend
to interact with a few of their friends (Wilson applied
it to Facebook, but it can be generalized to the rest so-
cial networks). That is, a friendship relation on Face-
book does not necessarily indicate a real relationship
between them. So, knowing which are the real ties
between a user and his friends is essential in social
networks.
At this point, our application would come into
play, taking care of monitoring users’ social networks
activity and extracting, from this activity, users’ ties
strength. From them, the application will be able to
build the users’ social spheres and, ultimately, find the
suitable services to them. Even though in this paper
we focus on Facebook social network, our goal is to
extend the application to any social network.
In Figure 1 our proposal is shown: a social ser-
vice, mySocialSphere, which lives in the cloud and
is in charge of monitoring and processing evidences
of relationships to build up the user’s social sphere.
It builds up user’s partial social spheres using user’s
information obtained from automated queries to dif-
ferent social networks APIs, which are combined to
form the inferred global social sphere, which be used
in CLOUDIA to find suitable services to users.
4 TIE SIGNS: THE FACEBOOK
CASE
Facebook provides its users with the typical inter-
personal communication features, although its high-
USINGFACEBOOKACTIVITYTOINFERSOCIALTIES
327
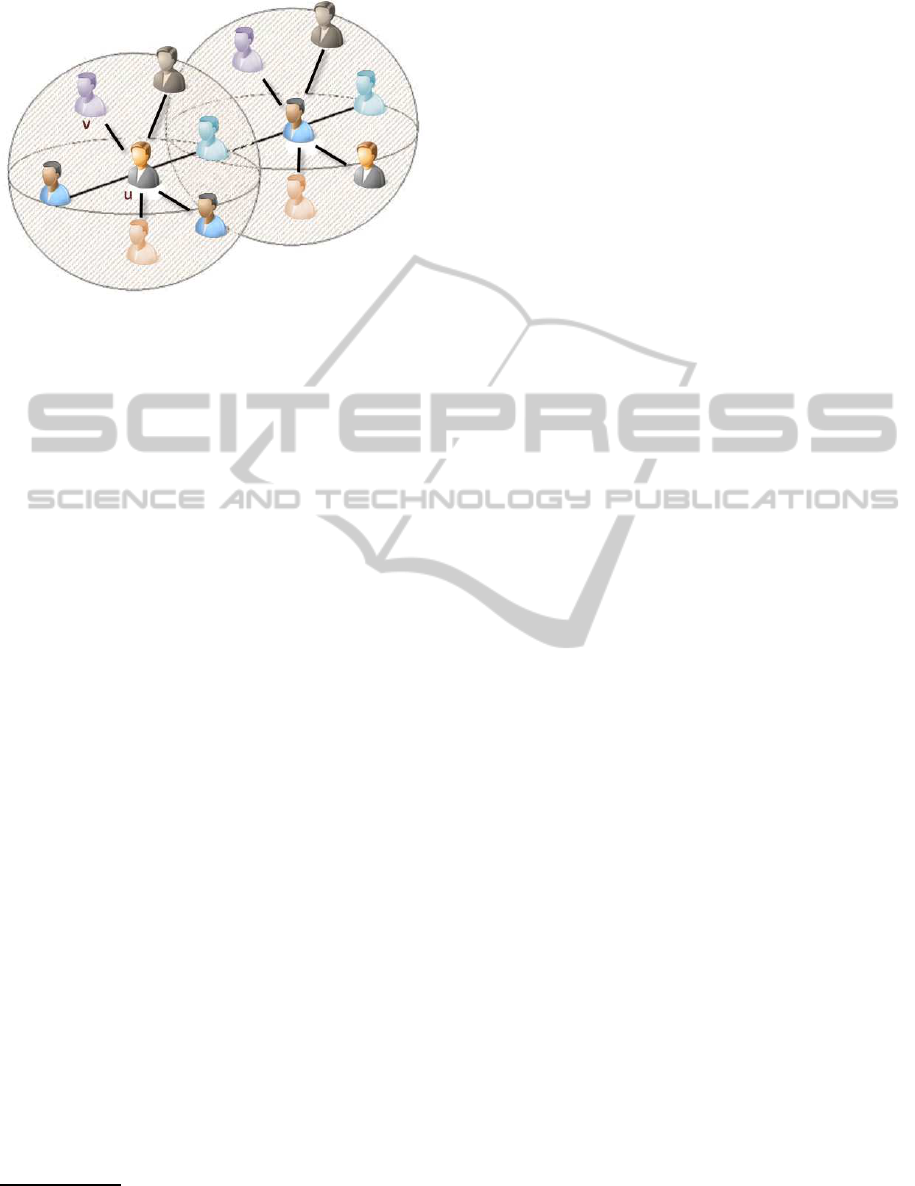
Figure 2: User’s social sphere.
light is the wall. Subscribers use the wall to post
photos, videos, links and messages that may be en-
riched with any friends’ comment. Besides, mini-
feeds provide detailed logs of each subscriber’s ac-
tions, so any friend may see at a glance how was his
evolution in Facebook over time. As in any social
network, security is a key factor and Facebook allows
their subscribers to personalize the privacy settings to
restrict access to the profile information, mini-feed,
wall posts, photos, comments, etc. only to friends,
friends-of-friends, lists of friends, no one or all.
On the premise the more interaction between two
users, the more tie strength, we have developed a
Facebook application
4
that extracts user’s activity in
Facebook and infers the closeness between a target
user, u, and one of this friends, v (Figure 2). Since u
probably takes advantage from the Facebook facilities
to communicate to v (private messages, wall-posts,
photos and videos uploads, etc.), we use all this in-
teractions as signs to built a model that calculates the
tie strength between u and v, from the u’s perspective:
TS
u
(v). Please, note that this subjective point of view
surely cause that the tie strength from the v’s perspec-
tive, TS
v
(u), is different.
After a detailed analysis of Facebook features and
how users interact and communicate, we have iden-
tified the interaction signs whose mathematical nota-
tion is as follows:
Wall-posts. Let P(x, y) = {p
1
(x, y), p
2
(x, y),. . .} be
the set of wall-posts user x has writen on y’s wall.
Thus, P
s
(x) =
S
∀y
{P(x, y)} is the set of x’s posts over
his friends’ wall and P
r
(x) =
S
∀y
{P(y, x)} is the set
of wall-posts that x has received.
4
Using the OAth2.0 protocol, our application requires
the target user grants a set of privileges that are explicitly
required when joining the application (see Section 6).
Private Messages. The set of private messages that
user x has sent to user y is denoted by PM(x, y) =
{pm
1
(x, y), pm
2
(x, y),. . .}. Consequently, PM
s
(x) =
S
∀y
{PM(x, y)} is the set of private messages x has
sent and PM
r
(x) =
S
∀y
{PM(y, x)} is the set of private
messages x has received.
Comments. Let C(x, y) = {c
1
(x, y),c
2
(x, y),. . .} be
the set of comments done by x about y’s entries (pho-
tos, wall-posts, etc.). Then, C
s
(x) =
S
∀y
{C(x, y)} is
the set of comments done by x about any Facebook
user’s entries and C
r
(x) =
S
∀y
{C(y, x)} is the set of
comments that the x’s entries have received.
Likes. Let L(x, y) = {l
1
(x, y),l
2
(x, y),. . .} be the set
of likes done by x over y’s entries. Then, L
s
(x) =
S
∀y
{L(x, y)} is the set of likes done by x and L
r
(x) =
S
∀y
{L(y, x)} is the set of likes that x’s entries have
received.
Photos and Videos. The set of x’s photos where
user y has been tagged is defined as PH(x, y) =
{ph
1
(x, y), ph
2
(x, y),. . .}. Analogously, the set of x’s
videos where user y has been tagged is defined as
VD(x, y) = {vd
1
(x, y),vd
2
(x, y),. . .}. Then, PH(x) =
S
∀y
{PH(x, y)} ( VD(x) =
S
∀y
{VD(x, y)}) is the set
of x’s photos (videos) where any of this friends is
tagged.
Belonging to the Same Groups. G
p
(x) =
{g
p
1
(x), g
p
2
(x), . . .} denotes the set of the pub-
lic groups to which x belongs and G
s
(x) =
{g
s
1
(x), g
s
2
(x), . . .} denotes the set of the private or
secret groups to which x belongs.
Event Attendance. EV
p
(x) = {ev
p
1
(x), ev
p
2
(x), . . .}
denotes the set of public events to which x
has shown intention to participate and EV
p
(x) =
{ev
p
1
(x), ev
p
2
(x), . . .} denotes the set of secret or pri-
vate events to which x has intention to go.
5 TIE STRENGTH INFERENCE
This paper only focuses on infering tie strength in-
dexes between Facebook friends, so we only analyze
how to assess the closeness u perceives about his re-
lationship with v: TS
u
(v) ∈ [0, 1]. In order to obtain
the index value, we propose the following logarithmic
function:
CLOSER2012-2ndInternationalConferenceonCloudComputingandServicesScience
328

f(x) =
0 if 0 ≤ x ≤
¯x
2
x
max
ln(
x
max
¯x
2
x)
ln(
x
max
2
¯x
2
)
if
¯x
2
x
max
< x
(1)
being
x and x
max
the mean and maximum value, re-
spectively. So, f(x) is close to 1 if x > x, close to
0 if x <
x and, finally, close to 0.5 if x ∼ x; exactly
the behavior we are looking for. With this function as
base, Section 5.1 shows our approach to calculate the
tie strength index. However, as life itself, tie strength
should be a dynamic index reflecting that old inter-
actions are progressively less important and, so, have
less influence in the index calculation. Additionally,
some signs’ influence vanishes as the number of par-
ticipants increase, so we have also add the concept of
relevance. Section 5.2 shows as time and relevance
are taken into account in the index calculation.
5.1 Tie Strength Calculation
We propose obtaining the strength index of the tie be-
tween u and v, from the u’s perspective, as a weighted
addition of three kind of interactions: (1) on-line,
TS
u
|
o
(v); (2) face-to-face, TS
u
|
p
(v); and (3) interest-
based, TS
u
|
i
(v):
TS
u
(v) =β· TS
u
|
o
(v) + γ· TS
u
|
f
(v)
+ (1− β− γ) · TS
u
|
i
(v) (2)
On-line Interactions (TS
u
|
o
(v)). Under this name
we include those signs that happen exclusively in the
Facebook world and do not require a previous face-to-
face contact: wall-posts, comments, likes and private
messages. We define two subsets: addressed-signs
and open-signs. The former draw together the inter-
actions that v explicitly sends to u –a private message,
for instance; whereas the latter are those interactions
without an explicit receiver –any like, for example.
Therefore, TS
u
|
o
(v) is obtained as follows:
TS
u
|
o
(v) = α· f(x
d
(v, u)) + (1− α) · f(x
o
(v, u)) (3)
where
x
d
(v, u) =|P(v, u)| + |P(u, v)| + |PM(v, u)|
+ |PM(u, v)|
x
o
(v, u) =|C(v, u)| + |C(u, v)| + |L(v, u)| + |L(u, v)|
are the number of addressed-signs and the number of
open-sings, respectively and f(x) is the logarithmic
function in Equation 1. Since α reflects the impor-
tance of addressed-signs, that we consider is signif-
icantly more relevant than open-signs, it should be
more than 0.5.
Face-to-Face Interactions (TS
u
|
f
(v)). This contri-
bution reflects any interactions showing a previous
physical contact between u and v. It is obtained as
follows:
TS
u
|
f
(v) = f(x(u, v)) (4)
where
x(u, v) = |PH(u, v)| + |VD(u, v)|
denotes the number of u’s photos where v is tagged
and f(x) is the logarithmic function in Equation 1.
Interest-based Interactions (TS
u
|
i
(v)). This contri-
butionassesses the common interests that u and v have
explicitely shown. In the Facebook universe this may
be done by subscribing to a group as well as accepting
an event invitation. Thus, it is obtained as follows:
TS
u
|
i
(v) = α· f(y
d
(v, u)) + (1− α) · f(y
o
(v, u)) (5)
where
y
d
(v, u) =|G
s
(u) ∩ G
s
(v)| + |EV
s
(u) ∩ EV
s
(v)|
y
o
(v, u) =|G
p
(u) ∩ G
p
(v)| + |EV
p
(u) ∩ EV
p
(v)|
are the number of addressed sings (private and se-
cret groups and events, and the number of open-signs
(public groups and events), respectively and f (x) is
the logarithmic function in Equation 1; α, since has
the same meaning than in Equation 3, should have the
same value and be always over 0.5.
5.2 Impact of Time and Relevance
None all Facebook signs, even belonging to the same
kind, should have the same relevance in the index cal-
culation. For instance, being tagged together in a five-
people photo it is clearly more relevant than being
tagged together in a twenty-people photo; at least, it
may be assumed that in the first case the situation en-
tails more closeness. So, some signs’ relevance van-
ishes as the number of participants increase. For time
we adopt the same pattern: relevance vanishes as time
goes by. Thus, we propose to modify the previous
equations by using the following decreasing function:
d(x) = e
−µ·x
(6)
where µ represent the strength of the slope, i.e. the
velocity to vanish signs’ importance: µ
r
for relevance
and µ
t
for time.
USINGFACEBOOKACTIVITYTOINFERSOCIALTIES
329

Relevance Impact. This aspect only affects face-
to-face and interest-based contributions in Equation 2
(photos, videos, events and groups). Face-to-face
contribution is obtained by:
TS
u
|
f
(v) = f(x(v, u))
where
x(v, u) =
∑
∀ j∈PH(u,v)
d(|tags
j
|) +
∑
∀ j∈VD(u,v)
d(|tags
j
|)
being |tags
j
| de number of tags in the j-picture (or
video) and d(|tags
j
|) the result of applying Equa-
tion 6. To obtain interest-based index, Equation 5,
we use the following contributions:
y
d
(v, u) =
∑
∀ j∈(G
s
(u)∩G
s
(v))
d(|users
j
|)
+
∑
∀ j∈(EV
s
(u)∩EV
s
(v))
d(|users
j
|)
y
o
(v, u) =
∑
∀ j∈(G
p
(u)∩G
p
(v))
d(|users
j
|)
+
∑
∀ j∈(EV
p
(u)∩EV
p
(v))
d(|users
j
|)
being |users
j
| the number of users that are expected
to attend j-event or are subscribed in j-group, and
d(|users
j
|) the result of applying Equation 6.
Gradual Forgetting. Time, however,affects all Face-
book signs: the older an interaction is, the lower
its weight should be. Thus, applying the decreasing
function, the contributions to Equation 3 to calculate
TS
u
|
o
(v) are as follows, being d(t
j
) the result of ap-
plying Equation 6 to the time of the latest updated of
j-Facebook sign:
x
d
(v, u) =
∑
∀ j∈P(u,v)
d(t
j
) +
∑
∀ j∈P(v,u)
d(t
j
)
+
∑
∀ j∈PM(u,v)
d(t
j
) +
∑
∀ j∈PM(v,u)
d(t
j
)
x
o
(v, u) =
∑
∀ j∈C(u,v)
d(t
j
) +
∑
∀ j∈C(v,u)
d(t
j
)
+
∑
∀ j∈L(u,v)
d(t
j
) +
∑
∀ j∈L(v,u)
d(t
j
)
In the case of calculating TS
u
|
f
(v), the new con-
tribution to Equation 4 is:
x(v, u) =
∑
∀ j∈PH(u,v)
d(|tags
j
|) · d(t
j
)
+
∑
∀ j∈VD(u,v)
d(|tags
j
|) · d(t
j
)
Finally, the new contributions to Equation 5 are as
follow:
y
d
(v, u) =
∑
∀ j∈(G
s
(u)∩G
s
(v))
d(|users
j
|) · d(t
j
)
+
∑
∀ j∈(EV
s
(u)∩EV
s
(v))
d(|users
j
|) · d(t
j
)
y
o
(v, u) =
∑
∀ j∈(G
p
(u)∩G
p
(v))
d(|users
j
|) · d(t
j
)
+
∑
∀ j∈(EV
p
(u)∩EV
p
(v))
d(|users
j
|) · d(t
j
)
6 EXPERIMENTAL EVALUATION
Our evaluation is focused on three stereotyped Face-
book users: (1) users having many friends that usually
interacts with only a few (our instance is user A hav-
ing 130 friends, average Facebook user (Facebook,
2011)); (2) users having only a few close friends and
interacting with all of them (our instance is user B
having 11 friends); and (3) users having a few friends
with which hardly interact (our instance is userC hav-
ing 62 friends). With the objective of assessing the
goodness of the previous formulation, we have de-
veloped a Facebook application that uses its API to
access the available information the subscribers have
upload in their Facebook profile. OAth 2.0 is the pro-
tocol Facebook uses for authentication (users and ap-
plications) and authorization (applications). OAuth
provides a method for clients to access server re-
sources on behalf of a resource owner (such as a dif-
ferent client or an end-user). It also provides a pro-
cess for end-users to authorize third-party access to
their server resources without sharing their creden-
tials (typically, a username and password pair), using
user-agent redirections. Facebook implementation of
the OAuth 2.0 involves three different steps: user au-
thentication (users are prompted to enter their creden-
tials), application authorization (users are asked to au-
thorize the application to access some of their infor-
mation through permissions) and application authen-
tication (using the application secret, available from
the Developer Application).
Since our objective is retrieving information about
subscribers’ activity in Facebook, our application re-
quires from the following permissions (which are
explicitly asked to subscribers whenever they run
our application): (i) basic information permission
(to access name, gender, profile picture, list of
friends, networks and any other information the sub-
scriber have shared with everyone), (ii) offline per-
mission (to access the previous information any-
CLOSER2012-2ndInternationalConferenceonCloudComputingandServicesScience
330
time), (iii) permissions to access the subscriber’s
mailbox (read mailbox), wall-posts (read stream),
photos (user
photo), videos (user videos), events
(user events) and groups(user groups). Using this in-
formation, we are able to obtain the tie strength index
and all the data needed to this experimental evalua-
tion.
6.1 Index Calculation
After several analysis, we have decided that the im-
portance of the directed addressed-signs (α) is 5 times
greater than the opened ones, as well as 60% is the
weight for online interactions, 25% for physical inter-
actions and 15% for interest-based interactions. Con-
cretely, we have fixed α = 0.8, β = 0.6, γ = 0.25,
µ
r
= 0.035 y µ
t
= 0.01. We established these values
because most of the users do not have many photos or,
if they have many, they are not tagged. Also, they at-
tended events and were members of groups with a lot
of attendees (members), which indicated that this type
of interaction would not be very relevant for them.
Also, we observed that online interaction was their
main type of interaction. Moreover, we consider that
the importance of the event of interaction loses half
of its value when there are about 20 users tagged in
a photo (video) or members of a group (attendees an
event) or when the event of interaction happened ap-
proximately two months before the moment in which
indexes are calculated.
0 20 40 60 80 100 120
0
0.1
0.2
0.3
0.4
0.5
0.6
0.7
0.8
0.9
1
% of friends
index
user 1
user 2
user 3
Figure 3: TS
A
(x), TS
B
(x) and TS
C
(x).
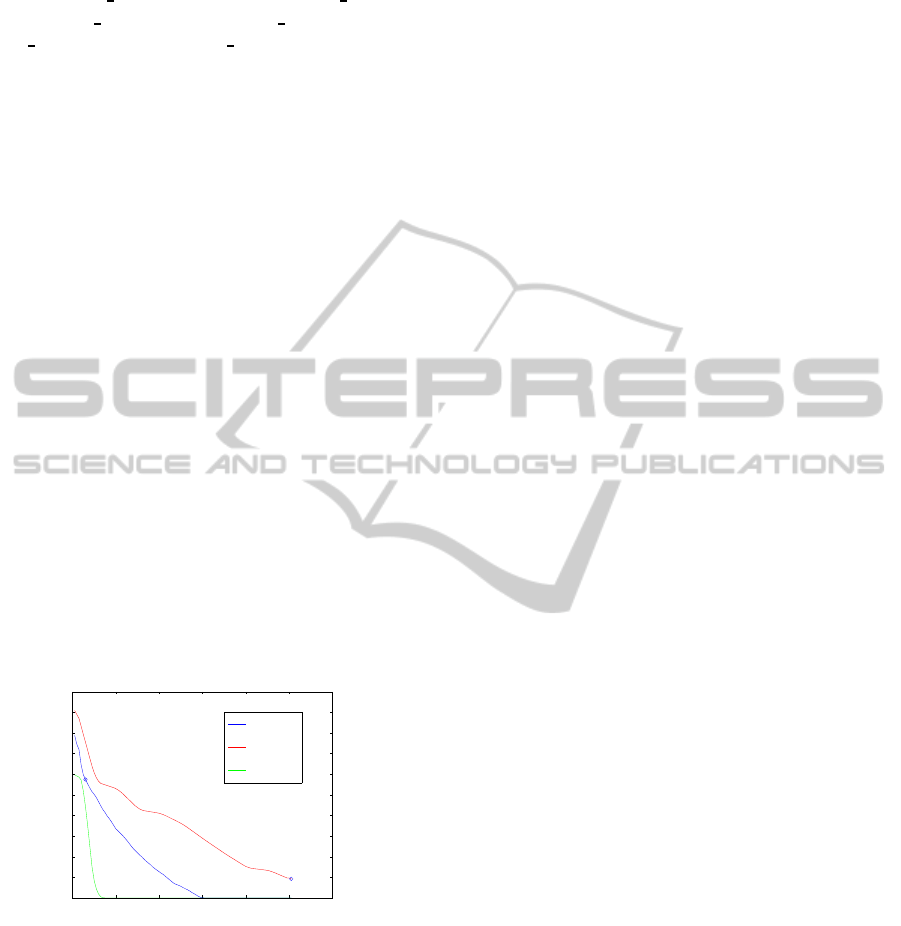
Under these conditions, Figure 3 shows the results
for each stereotyped user, A, B and C. These results
show that the value of the index is greater than 0.5
in, at most, the 23% of the considerate cases. It is
in keeping with Wilson’s article (Wilson et al., 2009),
which indicates that for most of the Facebook users,
the large majority of interactions occur only across a
small subset of their social links.
Besides, the more spread the allocation attention
across friends (or not friends) is, the more difference
exists among their indexes. For example, users B and
C, who spread their interactions among their friends
more uniformly than A, have a lower slope. For exam-
ple, X is a very active user and has the same interac-
tion signs with A and B, however TS
A
(C) = 0.58 and
TS
B
(C) = 0.009, as expected. Thus, the tie strength
index depends on how the allocation attention across
friends is: high for A (A does not pay attention to
many of his or her contacts), whereas for C is much
lower, since C spreads his or her attention more uni-
formly among them.
6.2 Relevance and Gradual Forgetting
Now, we consider an user whose Facebook social
graph is formed by 130 friends. We study how the
index varies using different values for the params that
control relevance and time (µ
r
and µ
t
). We chose this
user because is similar than the average user, who has
130 friends (Facebook, 2011).
We consider interaction sign’s relevance and each
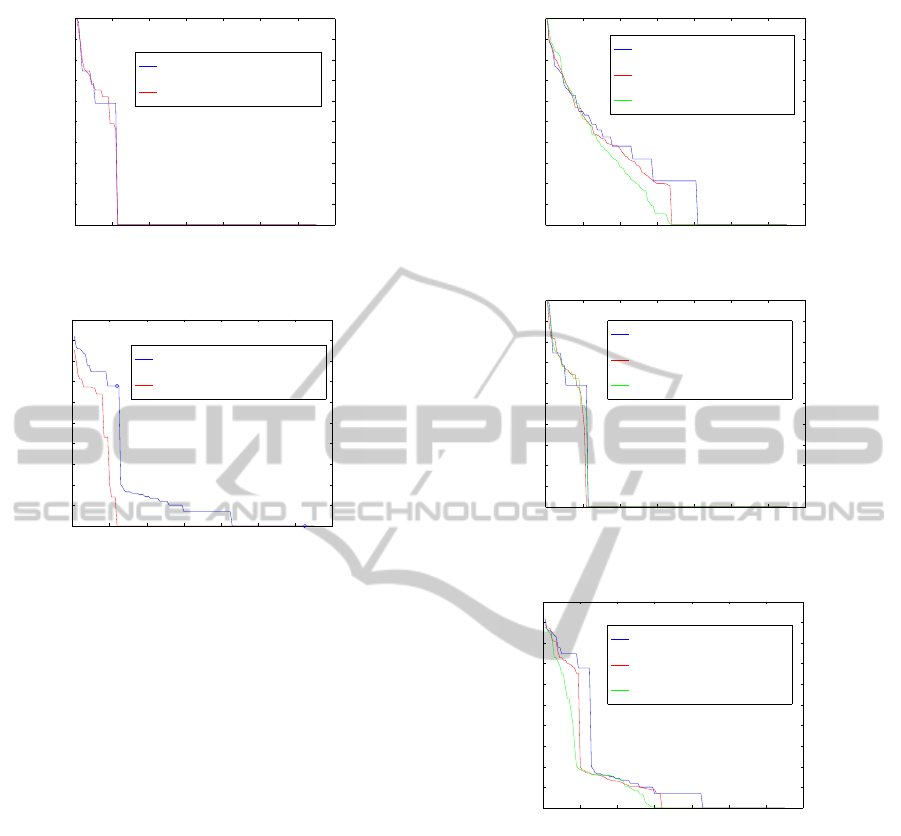
kind of interaction separately. Figures 4(a) and 4(b)
show how the index varies among the user’s friends,
taking in account only face-to-face and interest-based
interactions, respectively.
In graphic 4(a) we used µ
r
= 0.23, which means
that the importance of the interaction sign loses half
of its value when there are 3 users tagged in a photo
(video). In this case, the index is similar when we
take in account or do not take in account the relevance
of the interaction. The reason is that the user’s pho-
tos has hardly more than 3 people tagged in them.
To interest-based interaction (figure 4(b)) we fixed
µ
r
= 0.035, which means that the importance of the
interaction sign loses half of its value when there are
about 20 attendees an event (or members of a group).
In this case we observe differences if we consider or
do not consider the relevance. When we do not con-
sider it, for the 35% of the users their index is zero,
while if we consider it, this percentage rises to the
80% of the users. The main reason is because most of
the groups (events) have about 5000 members (atten-
dees), which means that the fact that the user belongs
to the group is irrelevant. For example, the user B
has an basic index of 0.68, while this value drops to 0
when the relevance is considered.
Finally, we consider the importance of the time
in each contribution to the index (online, face-to-face
and interest-based). In figures 5(a), 5(b) and 5(c), in-
dex variation over the user’s friends is shown. We
fixed µ
t
= 0.01, µ
t
= 0.002 and µ
t
= 0, which means
that the event of interaction loses half of its value
when it happened two months or a year before the
moment in which the index is calculated. The value
USINGFACEBOOKACTIVITYTOINFERSOCIALTIES
331
0 20 40 60 80 100 120 140
0
0.1
0.2
0.3
0.4
0.5
0.6
0.7
0.8
0.9
1
friends
index
basic (µ
r
= 0)
importance (µ
r
= 0.23)
(a) Tie strength index (only face-to-face interac-
tions).
0 20 40 60 80 100 120 140
0
0.1
0.2
0.3
0.4
0.5
0.6
0.7
0.8
0.9
1
friends
index
basic (µ
r
= 0)
importance (µ
r
= 0.035)
(b) Tie strength index (only interest-based inter-
actions).
Figure 4: Relevance influence in tie strength index.
µ
t
= 0 happens when time factor is not considered.
Wed use the same value for the rest of the parameters
that in previous section.
Results of this study are shown in the figures 5(a),
5(b) and 5(c). We obtain that the number of friends
with index value is equal to zero is greater when we
consider the time factor in the interaction. Also, the
lower µ
t
is, the more friends have index 0. It is keep-
ing with Wilson’s article (Wilson et al., 2009), which
indicates that the lower the size of the temporal win-
dow in which the interactions happened is, the lower
the number of friends with the user interacts is. Also
It makes sense that a friend who only is tagged in
some photos uploaded 2 or 3 years ago has an index
0 when we consider the importance of the time in the
interaction. On the other hand, a friend that is tagged
in few photos may have a greater index than another
friend tagged in many older photos when we consider
the importance of the time in interactions.
7 DISCUSSION
This paper describes an approach to infer social ties
from Facebook through its public API, which is in-
cluded in a large project to infer social ties from any
0 20 40 60 80 100 120 140
0
0.1
0.2
0.3
0.4
0.5
0.6
0.7
0.8
0.9
1
friends
index
basic (µ
t
= 0)
time decay (µ
t
= 0.002)
time decay (µ
t
= 0.01)
(a) Tie strength index (only online interactions).
0 20 40 60 80 100 120 140
0
0.1
0.2
0.3
0.4
0.5
0.6
0.7
0.8
0.9
1
friends
index
basic (µ
t
= 0)
time decay (µ
t
= 0.002)
time decay (µ
t
= 0.01)
(b) Tie strength index (only face-to-face interac-
tions).
0 20 40 60 80 100 120 140
0
0.1
0.2
0.3
0.4
0.5
0.6
0.7
0.8
0.9
1
friends
index
basic (µ
t
= 0)
time decay (µ
t
= 0.002)
time decay (µ
t
= 0.01)
(c) Tie strength index (only interest-based inter-
actions).
Figure 5: Time influence in tie strength index.
social network in the cloud. The solution goes one
step further to integrate the various links maintained
by users in all their social networks sites, the ones in
which they are registered. We are interested in sepa-
rating the sheep from the goats, i.e. separating the rel-
evant ties from these other ties which are almost fig-
urative. For instance, despite maintaining Facebook
a contact network, users are allowed to interact with
people outside their contact network (send a private
message, tag a photo with, etc.). In the same way
Twitter users can retweet any post, even if they are
not following the original poster. So, users may in-
teract frequently with users with who have not direct
link in any social network. Reversely, also it may oc-
CLOSER2012-2ndInternationalConferenceonCloudComputingandServicesScience
332

cur that a user has never interact with another user
with who shares a direct link in any social network.
Consequently, taking into account the users’ activity
and not only the figurative relation is a more effective
approach.
Our proposal is oriented to the construction of the
user’s social sphere in the cloud taking into account
two different-nature contributions. Firstly, the inter-
action network which can be computed from the for-
mulation in this paper by extending the online, face-
to-face and interest-based interactions to other social
network sites. Secondly, the topological networks, i.e.
the real links which the user maintains (and implicitly
accepts) in a plethora of social services. We make out
the topological network as a surface where social tie
strength is deployed. So, to obtain the social influence
between two users we consider (1) the tie strength in-
ferred from the interaction between them and (2) the
accumulate tie strengths of paths through, at most,
one intermediate user (in Facebook, for example, it
would be between friends and friends of friends).
Although, in this paper, the tie strength is only
based on Facebook interactions between friends, the
proposed formulation may also used to obtain the tie
strength between any two Facebook users, not nec-
essarily friends
5
. Despite of the fact that at first
sight it is expected for two Facebook friends to have
a stronger tie than two non-friends, statistics show
Facebook users only regularly relate with a small sub-
set of their 130 friends, on average (Facebook, 2011).
Thus, it is perfectly possible for them to have more
interaction with a non-friend than with one of their
friends, which must not be ignored to obtain the users’
social sphere.
Besides, and as aforementioned, users’ social
sphere should be obtained not only with the Facebook
data, but also taking into account their interactions in
other social networks. Along this line, we are cur-
rently working on extending this approach to other
social sites having a public API and adapting the inter-
actions in each social network accordinglyto our clas-
sification (online, face-to-face and interest-based in-
teractions). For instance, in Twitter, retweets, replies
or private messages would be included into the on-
line category, as well as private messages or photo
comments in Flickr, private messages in LinkedIn
or Wall-posts, comments or +1 in Google+. How-
ever, tags in photos or videos in Google+, Picasa
or Flickr would belong to the face-to-face category;
whereas interactions among users in the same group
in Google+, Flickr, LinkedIn, etc. would be catego-
5
Please, note that some of the signs, like wall-post are
only available for friends, so the absence of these contribu-
tions entails a reduction in the tie strength.
rized as interest-based. Finally, interactions among
users occur in any Web 2.0 application, even if it does
not have a declarative network as, for example, in the
case of blogs or wikis. Consequently, we bear in mind
extending our proposal to cover all the range of Web
2.0 application.
REFERENCES
Backstrom, L., Bakshy, E., Kleinberg, J., Lenton, T., and
Rosenn, I. (2011). Center of attention: How facebook
users allocate attention across friends. In Proceedings
of the 5th International AAAI Conference on Weblogs
and Social Media.
Chen, W. and Fong, S. (2010). Social network collabo-
rative filtering framework and online trust factors: a
case study on facebook. In The 5th International Con-
ference on Digital Information Management (ICDIM
2010), pages 266–273, Thunder Bay, Canada.
Facebook (2011). Facebook statistics.
Gilbert, E. and Karahalios, K. (2009). Predicting tie
strength with social media. In Proceedings of the 27th
international conference on Human factors in comput-
ing systems, pages 211–220. ACM.
Granovetter, M. (1973). The strength of weak ties. Ameri-
can journal of sociology, pages 1360–1380.
Kahanda, I. and Neville, J. (2009). Using transactional in-
formation to predict link strength in online social net-
works. In International AAAI Conference on Weblogs
and Social Media (ICWSM).
Mutton, P. (2004). Inferring and visualizing social net-
works on internet relay chat. In Information Visual-
isation, 2004. IV 2004. Proceedings. Eighth Interna-
tional Conference on, pages 35–43. IEEE.
O’Donovan, J. and Smith, B. (2005). Trust in recommender
systems. In IUI ’05: Proceedings of the 10th In-
ternational Conference on Intelligent User Interfaces,
pages 167–174, New York, NY, USA. ACM Press.
Tyler, J., Wilkinson, D., and Huberman, B. (2005). E-mail
as spectroscopy: Automated discovery of community
structure within organizations. The Information Soci-
ety, 21(2):143–153.
Viswanath, B., Mislove, A., Cha, M., and Gummadi, K.
(2009). On the evolution of user interaction in face-
book. In Proceedings of the 2nd Workshop on Online
social networks, pages 37–42, Barcelona.
Wilson, C., Boe, B., Sala, A., Puttaswamy, K. P., and Zhao,
B. Y. (2009). User interactions in social networks and
their implications. In Proceedings of the 4th ACM Eu-
ropean conference on Computer systems, Nuremberg,
Germany.
USINGFACEBOOKACTIVITYTOINFERSOCIALTIES
333
