
IMPROVING THE SECURITY OF SMS-BASED SERVICES
USING ELECTRONIC SIGNATURES
Towards SMS-based Processing of Transactional m-Government Services
Thomas Zefferer, Arne Tauber and Bernd Zwattendorfer
E-Government Innovation Center Austria, Inffeldgasse 16a, 8010 Graz, Austria
Keywords:
SMS, m-Government, Electronic Signatures, SMS based Services, Austrian Mobile-phone Signature, Security
Analysis.
Abstract:
SMS is still one of the most popular mobile communication technologies. Simplicity, cost efficiency, and low
bandwidth requirements account for the SMS technology’s continuing success. Besides the private sector,
also public sector organisations aim to take advantage of SMS technology’s current popularity. In numer-
ous countries all over the world, governments and public administrations already offer citizens SMS based
m-Government services. However, most of these services are rather simple and do not include security en-
hancing mechanisms such as cryptographic methods. This renders the use of SMS based approaches for
complex transactional m-Government services with higher security requirements difficult. We tackle this is-
sue by proposing the use of electronic signatures in SMS based services. The technical feasibility of our
approach is demonstrated by means of a prototypical application. This application allows citizens to generate,
electronically sign, and deliver electronic documents by sending well-defined SMS messages. The proposed
method’s capability to meet given security requirements of transactional m-Government services is assessed
in the course of a detailed security discussion.
1 INTRODUCTION
During the past years, mobile computing and commu-
nication technologies have significantly gained popu-
larity. Especially mobile phones have become an in-
tegral part of our daily life. The popularity of mobile
technologies has resulted in various mobile services
offered by both the private and the public sector. The
public sector mainly makes use of mobile technolo-
gies to enhance existing e-Government solutions and
to offer citizens an additional communication channel
to public administrations. These attempts have be-
come commonly known under the terms mobile gov-
ernment and m-Government.
M-Government solutions can be found all over the
world in both developing and developed countries.
Recent surveys on m-Government (Mobi Solutions
Ltd, 2010) (Zefferer, 2011) have revealed that a ma-
jority of current m-Government services rely on the
rather simple SMS (short message service) technol-
ogy. The popularity of SMS technology has several
reasons. First, the sending of SMS messages is often
very cheap compared to other more powerful mobile
data transmission technologies. In various countries,
a certain number of messages can even be sent for
free each month. Secondly, SMS technology is sup-
ported by virtually every mobile phone and does not
require mobile data networks. Thus, SMS based ser-
vices are not limited to certain end-user devices but
can rather be accessed by all users possessing a mo-
bile phone. This is of special relevance in developing
countries in which the market penetration of smart-
phones in comparison to mobile phones is still low
and broadband mobile networks are often not avail-
able. Another advantage of SMS technology is its
simplicity. Even technically inexperienced users are
able to send and receive SMS messages. Furthermore,
no set-up or configuration is required. SMS technol-
ogy can be used out of the box similarly to telephony.
The various advantages of SMS technology
account for the wide range of SMS based m-
Government services. However, there are also draw-
backs of SMS based solutions. For instance, due to
given technological limitations, SMS based services
are usually very simple. In most cases, these ser-
vices are used to broadcast certain information to cit-
izens or to collect data from citizens. Few SMS based
applications actually implement complete transaction
743
Zefferer T., Tauber A. and Zwattendorfer B..
IMPROVING THE SECURITY OF SMS-BASED SERVICES USING ELECTRONIC SIGNATURES - Towards SMS-based Processing of Transactional
m-Government Services.
DOI: 10.5220/0003909207430752
In Proceedings of the 8th International Conference on Web Information Systems and Technologies (WEBIST-2012), pages 743-752
ISBN: 978-989-8565-08-2
Copyright
c
2012 SCITEPRESS (Science and Technology Publications, Lda.)

based services. Depending on the use case, transac-
tion based services may have security requirements
that can only be met by applying cryptographic meth-
ods. This is problematic in the context of SMS based
services, for which the capabilities of end-user de-
vices are basically limited to sending and receiving
of text messages only.
In this paper we present an application allow-
ing users to securely carry out complete signature-
based transactional services by sending SMS mes-
sages. The services supported by our application
include creation, signing, and delivery of electronic
documents. Security requirements such as integrity
of digital data and non-repudiation of origin are met
by integrating both advanced and qualified electronic
signatures. The remainder of this paper is structured
as follows. Section 2 discusses related work on SMS
based m-Government services and concludes that cur-
rently most of these services do not include advanced
cryptographic methods such as electronic signatures.
We introduce basic concepts of electronic signatures
in Section 3. In this section, we also introduce several
approved core components, which our application is
partly based on. In Section 4 we discuss architectural
and implementation details of our solution and show
how it works in practice by means of a case study. Se-
curity issues of our approach are discussed in Section
5. In Section 6 an outlook to future work is given and
final conclusions are drawn.
2 RELATED WORK
Although modern smartphones provide users a variety
of different communication capabilities, SMS tech-
nology is still favoured all over the world (MBAON-
LINE, 2011). The popularity of SMS technology
has led to a plethora of SMS based services. Also
the public sector tries to make use of SMS technol-
ogy’s popularity. SMS based m-Government services
can already be found in various countries around the
world. Comprehensive overviews of existing SMS
based projects and initiatives are given in (Mobi So-
lutions Ltd, 2010) and (Zefferer, 2011).
SMS has played an essential role in developing
countries for many years. Especially in rural areas,
reliable fixed-line communication networks are often
not available. Contrary, mobile communication net-
works are often well evolved even in underdeveloped
regions. Yet, they are limited to GSM technology
most of the time. The consequent restriction to tele-
phony and text messaging has led to the development
of various useful SMS based services. For instance,
the FrontlineSMS project
1
aims to improve commu-
nication capabilities in regions with underdeveloped
infrastructures. FrontlineSMS allows data exchange
between remote entities (PCs, Laptop, etc.) based on
SMS messages. Another example for an SMS based
service is Kenya’s BloodBank-SMS project
2
. Due to
missing reliable fixed-line communication networks,
statuses of blood banks are exchanged via an SMS
based service between different hospitals.
There are various other SMS based services from
the health sector available in developing countries. In
South Africa, citizens can request location informa-
tion on HIV testing centres via SMS. Text to Change
3
is a health education initiative that aims to inform
people in developing countries about diseases such as
malaria or AIDS using text messaging technologies.
In developed countries, reliable fixed-line com-
munication networks are usually well evolved. Mo-
bile communication networks are thus just one out
of multiple communication and information alterna-
tives and mainly used to satisfy demands of the typical
western always-on society. Hence, SMS based ser-
vices in developed regions differ from those of devel-
oping countries in various aspects. In fact, most exist-
ing SMS based services aim to improve convenience.
For instance, in various European cities parking fees
can be paid via text messages
4
. In Norway, also tax
declarations can be done with the help of SMS mes-
sages
5
, which has significantly eased the entire tax
declaration process for citizens.
Various countries in both developing and devel-
oped regions make use of SMS to broadcast relevant
information to their citizens. For instance, in Venice,
Italy, citizens are supplied with flood warnings per
SMS
6
. In London, UK, the Metropolitan police for-
ward bomb alerts and similar security warnings to
registered citizens via SMS
7
.
Due to given limitations of SMS technology, most
SMS based services are rather informational than
transactional. This is reasonable since transactional
services can have higher security requirements that
are difficult to meet with SMS based approaches.
Therefore, transactional services are traditionally pro-
vided through web based approaches, which allow an
1
http://www.frontlinesms.com/
2
http://www.media.mit.edu/ventures/EPROM/research.
html
3
http://www.texttochange.org/
4
http://www.handyparken.at/handyparken/home.seam
5
http://www.textually.org/textually/archives/2003/04/00
0349.htm
6
http://www.textually.org/textually/archives/2008/06/02
0298.htm
7
http://www.emergencysms.org.uk/
WEBIST2012-8thInternationalConferenceonWebInformationSystemsandTechnologies
744

easier integration of cryptographic methods such as
electronic signatures. Unfortunately, there are sce-
narios in which web access is not available and web
based services cannot be accessed. In such scenar-
ios, SMS based transactional services can be useful.
The approach introduced in this paper implements
transactional services on SMS basis and incorporates
electronic signatures to meet security requirements of
such services.
3 BACKGROUND
Electronic signatures are perfectly suitable to meet
the requirements for integrity and non-repudiation of
transactional e-Government and m-Government ser-
vices. Hence, in this section we discuss basic princi-
ples of electronic signatures and related legal aspects.
As the application presented in this paper relies on
several components of the Austrian e-Government in-
frastructure, this section also emphasises the role of
electronic signatures in the Austrian e-Government.
3.1 Electronic Signatures
Electronic signatures are a crucial element of e-
Government infrastructures and services. Electronic
signatures rely on asymmetric cryptography and pro-
vide integrity of digital data and non-repudiation of
origin. To harmonize legal aspects of electronic sig-
natures throughout the European Union, the so-called
EU Signature Directive (European Union, 1999) has
been enacted in 1999. The EU Signature Directive
defines in detail the following two kinds of electronic
signatures.
• Advanced Electronic Signature ”means an elec-
tronic signature which meets the following re-
quirements:
– It is uniquely linked to the signatory
– It is capable of identifying the signatory
– It is created using means that the signatory can
maintain under his sole control; and
– It is linked to the data to which it relates in
such a manner that any subsequent change of
the data is detectable”
• Qualified Electronic Signatures are advanced
electronic signatures that are based on qualified
certificates and are created by a secure signature
creation device. Requirements for qualified cer-
tificates and secure signature creation devices are
also defined in detail in the annex of this directive.
The EU Signature Directive assures legal equiv-
alence between qualified electronic signatures and
handwritten signatures and their mutual recognition
throughout the European Union. Enabling citizens
to apply legally valid signatures, qualified electronic
signatures are an important component of many e-
Government services. Citizens usually use smart
cards or similar hardware tokens as secure signature
creation devices according to the directive. However,
some countries provide their citizens also alternative
approaches. For instance, Austrian
8
or Estonian
9
cit-
izens can use their mobile phones to create qualified
electronic signatures.
In the scope of e-Government, electronic signa-
tures are not only used by citizens. Electronic signa-
tures are also an important tool for public administra-
tions to avoid media breaks and to facilitate the pro-
cessing of administrative procedures. In many coun-
tries, administrative rulings are for instance electron-
ically signed before being delivered to citizens. De-
pending on the underlying technology, different kinds
of electronic signatures according to the EU Signature
Directive are used for this purpose.
In order to be suitable for different use cases, our
solution supports both advanced and qualified elec-
tronic signatures. Calling on many years of experi-
ence, the Austrian e-Government initiative provides
several core components that ease an integration of
electronic signatures into e-Government infrastruc-
tures. In the following we introduce some of these
components, which our application partly relies on.
3.2 Electronic Signatures in Austria
Electronic signatures are a key concept of the Aus-
trian e-Government. The use of electronic signa-
tures within Austrian e-Government processes is fa-
cilitated by several core components. A comprehen-
sive overview of these components is provided in
(Posch et al., 2011).
Citizens use qualified electronic signatures to au-
thenticate at e-Government services, to assure in-
tegrity of transmitted data, and to provide written con-
sent in electronic procedures. Public administrations
make use of advanced electronic signatures to im-
prove governmental back-office processes and to sign
administrative rulings. In the following we discuss
core components of the Austrian e-Government ini-
tiative dealing with the creation of electronic signa-
tures. Some of these components are used by our
SMS-based application.
8
https://www.handy-signatur.at
9
http://www.id.ee/?id=10995&&langchange=1
IMPROVINGTHESECURITYOFSMS-BASEDSERVICESUSINGELECTRONICSIGNATURES-Towards
SMS-basedProcessingofTransactionalm-GovernmentServices
745

With the Citizen Card - the national eID - Aus-
trian citizens can create qualified electronic signa-
tures. Although the term Citizen Card suggests the
use of smart cards the Citizen Card concept (Leitold
et al., 2002) is technology neutral and not limited to a
certain signature creation device. Currently, citizens
can use smart cards and mobile phones to create qual-
ified electronic signatures. While smart card based
signature creation processes are used in various coun-
tries, the mobile phone based approach followed in
Austria is novel and especially of interest in the con-
text of our SMS based application.
The Austrian Mobile Phone Signature that has
been discussed by Orthacker in (Orthacker et al.,
2010) follows a centralized approach to carry out mo-
bile phone based signatures. This means that a cen-
tral hardware security module (HSM) is in charge
of creating electronic signatures. The user’s mo-
bile phone is solely used to authorize the signature
creation process with a mobile transaction number
(mTAN). According to this approach, a central ser-
vice currently hosted by the Austrian certification au-
thority A-Trust
10
represents the core component of
the Austrian Mobile Phone Signature. A HSM is an
integral part of this central service. For security rea-
sons, all Citizen Card private keys are encrypted with
the master key of the HSM and a symmetric encryp-
tion key, which is derived from a secure password that
is only known to the user.
To start a signature creation process, users have
to transmit their mobile phone number and their se-
cure password together with the data to be signed to
the central service. This communication takes place
through a web based interface. With the secure pass-
word, the user’s personal signing key residing in the
central HSM can be decrypted. After successful veri-
fication of the secure password and decryption of the
user’s signing key, a one-time password (TAN) is gen-
erated and sent to the user’s mobile phone via SMS.
To finally initiate the signature creation process, the
user returns the obtained TAN through the web based
interface to the central service.
The security of the Mobile Phone Signature basi-
cally depends on the second, non-web based mobile
communication channel that is used to transmit a se-
cure TAN to the user. Similar to smart card based
approaches also the Austrian Mobile Phone Signature
relies on a two-factor authentication scheme. The fac-
tor ’knowledge’ is covered by the user’s secure signa-
ture password. Additionally, the factor ’possession’
is considered by sending a TAN to the user’s mobile
phone. This way, the service verifies whether the user
is the person she claims to be.
10
http://www.a-trust.at/
The Mobile Phone Signature facilitates the cre-
ation of qualified electronic signatures for Austrian
citizens. Public administrations often rely on ad-
vanced electronic signatures, which are better suited
for automated signature creation. To facilitate signa-
ture creation processes for Austrian public adminis-
trations, a server-based signature creation module has
been developed. This module is called MOA-SS
11
and enables the creation of advanced electronic sig-
natures using preconfigured software keys.
To improve security and reliability, the SMS based
m-Government application we are presenting in this
paper relies on core signature components, which are
provided as open source modules by the Austrian e-
Government initiative. Our solution incorporates both
the Mobile Phone Signature and MOA-SS to integrate
creation devices for qualified and advanced electronic
signatures. This way, our application basically sup-
ports two different levels of security, advanced and
qualified electronic signatures according to the Signa-
ture Directive. We will discuss security implications
of this approach later in this paper.
4 IMPLEMENTATION
The basic objective of our application is the imple-
mentation of SMS based transactional procedures. In
our solution, a procedure defines a process includ-
ing the generation, signing, and delivery of electronic
documents. To meet possible security requirements of
such procedures, our solution incorporates electronic
signatures. In this section we present the architec-
ture and the general process flow of our solution. To
appropriately illustrate our application’s functionality,
we finally discuss a concrete procedural use case sup-
ported by our solution.
4.1 Architecture
The limiting factor of SMS based services defines
the end-user’s device, which is basically restricted to
sending and receiving of SMS messages. Most func-
tionality of our application cannot be modelled via
SMS messages and thus has to be outsourced to an-
other component. Therefore, our solution relies on a
central web application implementing the main func-
tionality. The central web application makes use of
several external components to implement the desired
processes.
Figure 1 shows the basic building blocks of our
solution. The central web application defines the
11
http://egovlabs.gv.at/projects/moa-idspss/
WEBIST2012-8thInternationalConferenceonWebInformationSystemsandTechnologies
746
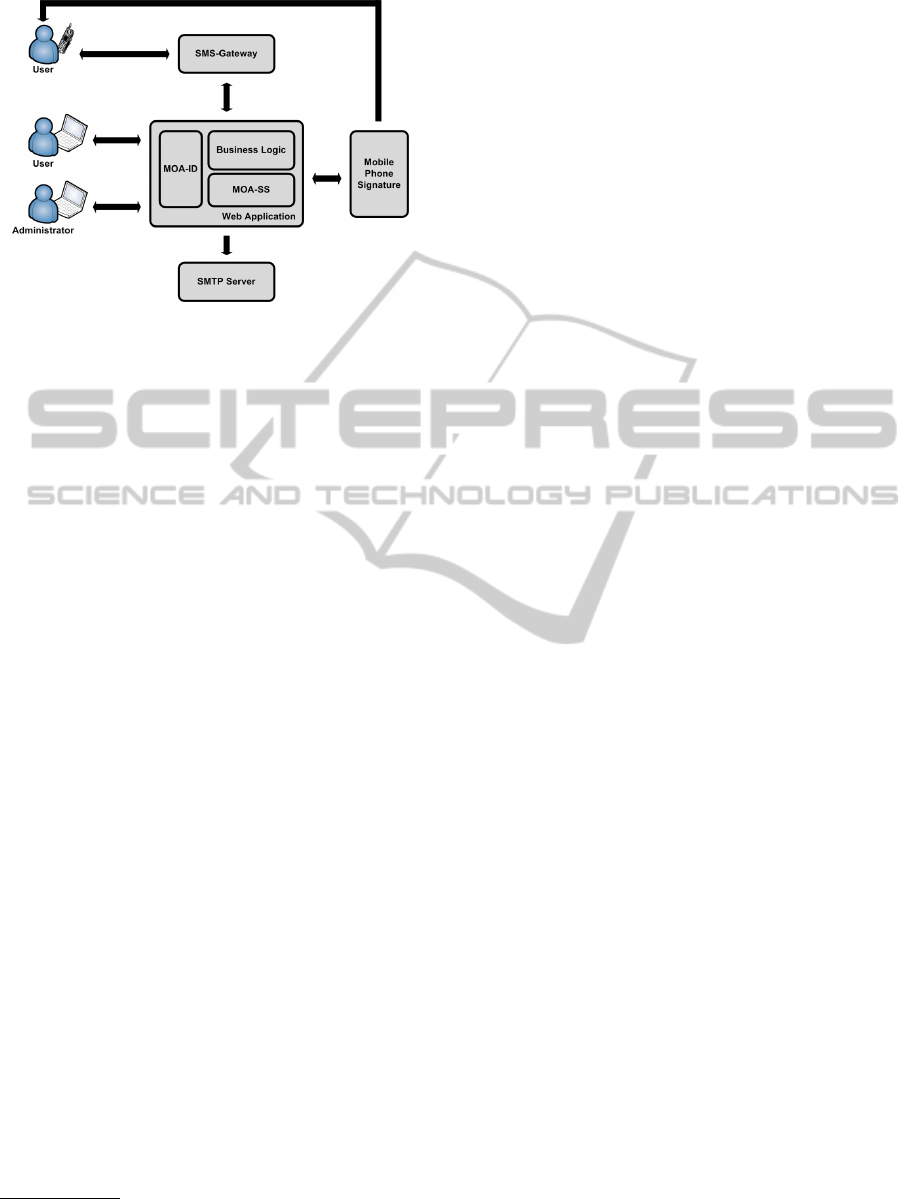
Figure 1: Architecture and basic building blocks of the pre-
sented application.
core component and basically implements all busi-
ness logic. Users interact with this web application
through an external SMS gateway that translates SMS
messages into XML based requests and vice versa.
By sending appropriate SMS messages users can elec-
tronically create, sign, and deliver documents. All this
functionality is basically covered by the web applica-
tion’s business logic.
Our solution supports two alternatives to sign
a created document
12
. Qualified electronic signa-
tures can be carried out using the Austrian Mobile
Phone Signature. Alternatively, documents can also
be signed using a central MOA-SS module being an
integral component of the central web application.
This approach allows for the creation of advanced
electronic signatures.
The web application also features a web based
user interface. Through this interface users can re-
view and inspect their documents that have been pre-
viously processed via SMS. Additionally, adminis-
trators can carry out maintenance tasks through this
interface. The web based access to the central web
application is protected by a two-factor authentica-
tion scheme. Again, we rely on an approved core
component of the Austrian e-Government landscape
to implement secure user authentication. The open
source module MOA-ID
13
encapsulates functionality
needed to securely authenticate users by means of a
two-factor authentication based on the Austrian Citi-
zen Card concept. Similar to MOA-SS, MOA-ID is
an integral component of our central web application.
To deliver signed documents, the web application
is connected to an external SMTP server. However,
the generic design of our solution guarantees that also
other types of delivery such as registered or certified
12
The documents created follow the PDF standard.
13
http://egovlabs.gv.at/projects/moa-idspss/
mail could be used.
4.2 Interfaces and Process Flows
Our application basically provides two different user
interfaces. On the one hand, users can communicate
with the application by exchanging SMS messages.
This interface is mainly used to process procedures.
On the other hand, the application can also be ac-
cessed through a web based interface. This interface
is mainly intended for document inspection and main-
tenance tasks.
The processing of procedures through the applica-
tion’s SMS based interface consists of the following
steps:
• Document Creation. A user starts a procedure by
sending a well-defined SMS message. This mes-
sage contains the unique identifier of the proce-
dure to be processed. A PDF document is cre-
ated based on a template that is assigned to the
selected procedure and on dynamic data defined
by the user. This data is transmitted to the ap-
plication via SMS together with the procedure’s
unique identifier.
• Document Signing. The document is signed ei-
ther by the external Mobile Phone Signature or
by the central MOA-SS signature module. De-
pending on the chosen method either a qualified
personal citizen signature or an advanced elec-
tronic server signature is created. The user se-
lects the desired signature method by SMS. If
the user chooses the Mobile Phone Signature, a
TAN is sent to the user’s mobile phone during the
signature creation process. This TAN has to be
forwarded manually to the central application via
SMS.
• Document Delivery. The document is delivered
to configured recipients. Different recipients can
be defined for each procedure. After success-
ful delivery, the document is stored in a central
database for later inspection. The user is notified
about the successful processing of the document
via SMS and e-mail.
Besides the SMS interface, the application can
also be accessed through a web based interface. The
set of functionality provided through this web inter-
face actually depends on the user’s assigned rights.
Standard users can use the application’s web interface
for the following tasks:
• Account Creation. In order to use the applica-
tion, users need to register and create a user pro-
file containing mobile phone number and e-mail
address.
IMPROVINGTHESECURITYOFSMS-BASEDSERVICESUSINGELECTRONICSIGNATURES-Towards
SMS-basedProcessingofTransactionalm-GovernmentServices
747

• Register to Procedures. The application allows
the dynamic definition of different procedures.
Users must register to defined procedures before
using them.
• Inspect Documents. Documents created during
the processing of procedures can be inspected and
downloaded through the application’s web inter-
face.
Users with assigned administrator rights can ad-
ditionally access the following functions through the
application’s web interface:
• Define Procedures. System administrators can
define new procedures by choosing an appropri-
ate identifier and a suitable PDF template. Addi-
tionally, predefined receivers can be selected to re-
ceive newly created and signed documents. Also
data that has to be provided by users during the
document creation process can be defined.
• Application Maintenance. Application main-
tenance involves for instance the activation and
deletion of user accounts.
4.3 Case Study: Sick Note
The reporting of absence from work due to sickness is
one out of many scenarios that comply with the above
mentioned general process flow. In the following we
illustrate the functionality of our application by dis-
cussing the sick note procedure in more detail. Al-
though this is no typical m-Government procedure, its
simplicity makes it perfectly suitable to demonstrate
the capabilities of our approach.
Basically, the implemented sick note procedure
allows employees to generate, sign, and deliver sick
notes to their employer. Using our applications, sick
employees can reliably report their absence simply by
sending SMS messages but still having the guarantee
and non-repudiation property of electronic signatures.
The entire procedure requires the following steps to
be carried out.
4.3.1 Definition of Procedure
Before a procedure can be used, it has to be defined
first. Procedures can be defined by users with ad-
ministrator rights through the application’s web based
maintenance interface. Once a procedure is defined,
users can register to this procedure and use it.
A procedure basically specifies a type of docu-
ment that may be generated and signed by users dur-
ing a transaction. Amongst others, a procedure is de-
fined by the following information:
• Unique identifier.
• List of key words, which have to be transmitted
by the user via SMS, and which are included in
the generated document.
• List of receivers of completely signed documents.
Considering our concrete case study, the proce-
dure that supports the SMS based generation of sick
notes comprises the following specifications:
• Unique identifier: SICK.
• List of key words: FROM.
• List of receivers: DEPARTMENT HEAD, PER-
SONNEL OFFICE.
Figure 2 shows the web interface that can be used
to define new procedures. Amongst others, this in-
terface allows the assignment of receivers and key
words. Receivers and key words can by defined via
similar web based interfaces.
4.3.2 Registration
Users must register through the web application’s web
interface in order to gain access to the application.
Therefore, users are securely authenticated using a
two-factor authentication scheme based on the Aus-
trian Citizen Card concept.
During the registration process, a user account
is created, which contains required user related data
such as user name and mobile phone number. To
avoid misuse, newly created user accounts must be or-
ganisationally verified and manually activated by sys-
tem administrators.
As soon as the user’s account is activated, she
may register to procedures that have been previously
defined by system administrators. This registration
takes place through the web interface shown in Fig-
ure 3. The registration for procedures is only required
once. After successful registration no further web
based interaction with the application is required.
4.3.3 Document Processing
The processing of procedures represents the main use
case of our application and is completely carried out
via the application’s SMS interface. To start the pro-
cess flow (i.e. to create a sick note), users send an
SMS to the web application. The SMS contains the
unique identifier of the corresponding procedure (i.e.
’SICK’) and a list of key words (i.e. ’FROM’) with
associated key values (e.g. ’2011-11-01’) that have to
be provided for this procedure.
As the application supports two signature creation
alternatives, the user’s preferred signature method
must also be included in the SMS message. If the
user desires to sign the document to be generated by
WEBIST2012-8thInternationalConferenceonWebInformationSystemsandTechnologies
748
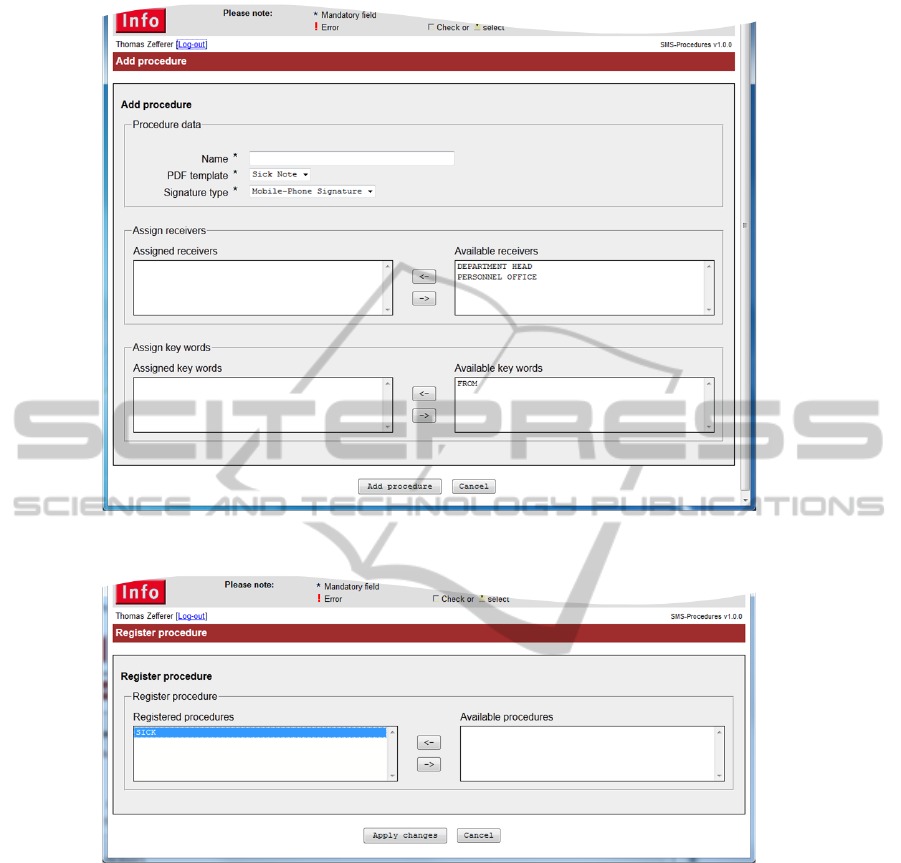
Figure 2: Web based interface for the definition of new procedures.
Figure 3: Web based interface allowing users to register to available procedures.
the Server Signature Module MOA-SS, the key word
’server’ has to be appended to the SMS message.
If the user prefers the Mobile Phone Signature ap-
proach, the user’s Mobile Phone Signature password
has to be appended instead.
Reconsidering the sick note example, a user
could send the following text message to start the
process flow and sign the document using the Server
Signature Module:
SICK*FROM:2011-11-01*server
To generate the same document (sick note)
but sign it with the Mobile Phone Signature, the
following SMS message has to be sent:
SICK*FROM:2011-11-01*<password>
In this example, ’<password>’ denotes the user’s
personal password for the Mobile Phone Signature
service. In this scenario, a signature creation request
is sent to the Mobile Phone Signature. The user re-
ceives a mobile TAN during the signature creation
process. This TAN has to be forwarded to the web
application via SMS. In order to complete the sign-
ing process, the central web application forwards the
TAN to the Mobile Phone Signature for verification.
Irrespective of the chosen signing method, the
IMPROVINGTHESECURITYOFSMS-BASEDSERVICESUSINGELECTRONICSIGNATURES-Towards
SMS-basedProcessingofTransactionalm-GovernmentServices
749

signed document is finally delivered to all configured
receivers of the procedure. According to the defi-
nition of the Sick Note procedure, the created and
signed sick note is sent to the department head and
to the personnel office. The user is notified about the
success of the document processing by SMS and e-
mail.
Figure 4 illustrate the SMS based user interaction
from the user point of view. In the shown example,
the user requests the creation of a sick note indicating
a sick leave that starts on 2011/11/21. Furthermore,
the user selects the MOA-SS based signature creation
method by adding the key word ’server’. The appli-
cation notifies the user via SMS after having created,
signed, and delivered the sick note.
Figure 4: SMS message exchange during processing of pro-
cedure.
4.3.4 Document Inspection
The whole process of document and signature cre-
ation is basically carried out by the central web ap-
plication. Since users communicate with the web
application via SMS only, created and signed docu-
ments cannot be accessed immediately. To guarantee
an appropriate degree of transparency, the application
stores the signed document in an internal database
for later inspection. Previously generated and signed
documents can be accessed via the application’s web
interface. Again, access to this interface and to own
documents is protected by a secure two-factor authen-
tication scheme.
Figure 5 shows the web based user interface. The
left area contains a list of available documents. De-
tails of the selected document are displayed in the
main area. Details include document related data and
the document’s processing log. Available PDF files
can be downloaded by clicking the displayed PDF
icons.
5 SECURITY ANALYSIS
This section discusses aspects, which may have an
impact on the security level of SMS-based proce-
dures. Security considerations have been made dur-
ing the conceptual design of the main architecture and
also during the prototypical implementation.
5.1 Omission of Communication
Channel
The traditional Austrian Mobile Phone Signature uses
a two-factor authentication mechanism based on two
communication channels. This means that on the
one hand mobile phone number and signature pass-
word entered in a web form ensure knowledge and
on the other hand the correct TAN sent by SMS en-
sures proof of possession. Hence, if the phone is
stolen, without knowing the signature password a sig-
nature creation process cannot be initiated. In con-
trast, the purely SMS based procedures proposed in
this paper have just one communication channel, the
mobile phone. Even if a pure SMS based solution
may increase usability, a single communication chan-
nel inevitably decreases the security level. In case of
malware the use of a single communication channel
may become critical as also the signature password is
transferred via the same channel. This issue is dis-
cussed in more detail in Section 5.5.
5.2 Security of Intermediary
Components
In case of the Austrian Mobile Phone Signature, the
TAN is directly exchanged between the user and the
operator. Several intermediary components are in-
volved in case of SMS based procedures. It is nec-
essary that all these components fulfil certain security
requirements to protect the TAN from disclosure. The
security of the whole system is just as strong as the
weakest link. This does not only concern the compo-
nents itself, but the inter-component communication
as well. For example, an intermediary component
using GSM may threaten the security of the whole
system due to known vulnerabilities of GSM (Barkan
et al., 2008).
5.3 Signature Password Handling
When using the Austrian Mobile Phone Signature in
SMS based procedures, the application requires the
user’s password to create the signature. The only pos-
sible way is to transmit the password within an SMS
from the user to the application. This approach has
WEBIST2012-8thInternationalConferenceonWebInformationSystemsandTechnologies
750
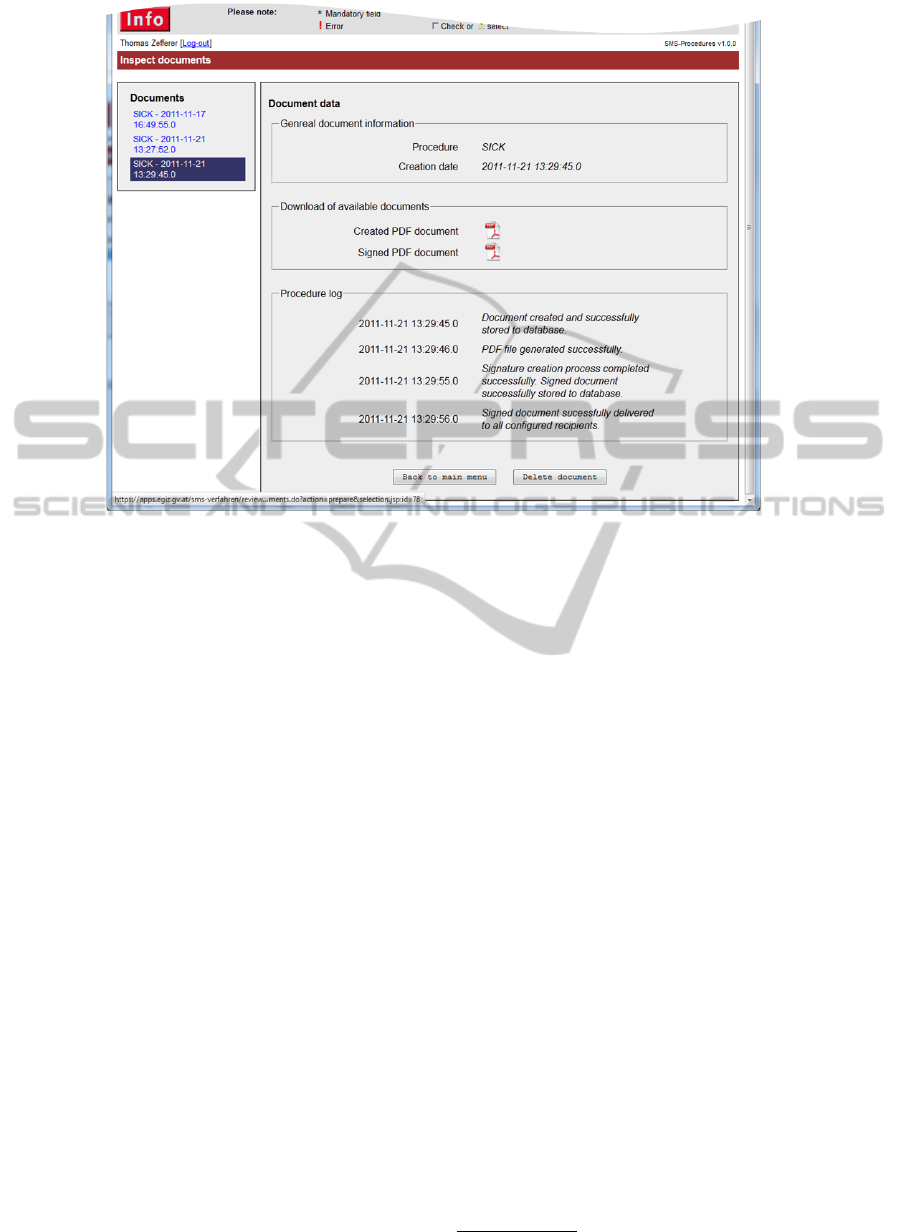
Figure 5: Web based interface allowing users to inspect documents.
two drawbacks. First, it requires full trust in the appli-
cation. A malicious SMS gateway could intercept sig-
nature passwords and exploit them in an abusive way.
A second problem is the sending of the user’s sig-
nature password over the same channel as the TAN.
This is a heightened security risk because if the chan-
nel is compromised, also the signature process might
be compromised. Users are also advised to delete
their sent SMS messages from their mobile phones
frequently. Otherwise, the secure signature password
may appear in locally stored communication histories
and get compromised if the device is lost or stolen.
5.4 Display of Signature Data
According to the Austrian Signature Act, involved
technical components must ensure that the signed
data can be displayed to the signatory upon request.
When using the Austrian Mobile Phone Signature
in the user’s web browser, this functionality is pro-
vided. Support of this feature is more difficult with
our SMS based approach as only text based data can
be displayed by SMS technology. However, this does
not render application of our approach impossible,
since our solution relies on the Austrian PDF signa-
ture standard PDF-AS (EGov-Labs, 2012). PDF-AS
allows the text based signing of PDF documents, i.e.
only the extracted text is signed. This text could also
be displayed in one or more SMS messages. This fea-
ture is not yet supported in our prototype implemen-
tation, but can be added easily if required.
5.5 Malware
Traditional mobile phones with limited functionality
can usually be considered as secure. This assumption
does not apply to smartphones. Since smartphones
can be extended and equipped with arbitrary addi-
tional software called Apps, they are more vulnerable
to different kinds of malware. Apps may get rights
to access various parts of the phone’s functionality,
e.g. including SMS capabilities. In this way an App
may intercept unnoticedly incoming or outgoing SMS
messages. This is the reason why it can be problem-
atic to enter the signature password on a smartphone.
Having caught the password and being able to unno-
ticedly intercept SMS, a malware could theoretically
create qualified electronic signatures with legal value
on behalf of the user.
5.6 Identity Spoofing
Another critical security target is spoofing of the
user’s identity. SMS spoofing
14
is a common and le-
gitimate technique offered by phone providers so that
SMS messages appear to originate from a particular
company (name) or a particular phone number. How-
ever, the technique can illicitly be used to imperson-
14
http://www.smsspoofing.com/
IMPROVINGTHESECURITYOFSMS-BASEDSERVICESUSINGELECTRONICSIGNATURES-Towards
SMS-basedProcessingofTransactionalm-GovernmentServices
751

ate another person or company. This way, an attacker
may trigger SMS based procedures on behalf of the
user. The issue becomes critical if the procedure does
not use any confirmation TAN, for example if the user
initially triggers the procedure via SMS and the re-
maining part is processed on the server side (includ-
ing the generation of the signature).
6 FUTURE WORK AND
CONCLUSIONS
The conducted security analysis revealed several se-
curity issues that have to be considered in future work.
Also, the use of SMS messages to transmit potentially
security sensitive data raises the question on the gen-
eral security of SMS technology. The weakness of the
encryption schemes used by the GSM protocol has al-
ready been shown (Barkan et al., 2008). Hence, data
transmissions over GSM networks cannot always be
regarded as secure.
The need for a secure exchange of SMS messages
has already been addressed by various authors. A
comprehensive overview of current approaches to en-
hance the security of SMS is given in (Medani et al.,
2011). For instance, Lisonek and Drahansk (Lisonek
and Drahansk, 2008) enhanced the security of SMS
messages by using asymmetric cryptography. An-
other method relying on both symmetric and asym-
metric encryption schemes has been proposed by An-
uar et al. (Anuar et al., 2008). Another solution fol-
lowing a hybrid cryptographic scheme has been intro-
duced in (Al-bakri and Kiah, 2010). All these meth-
ods are basically able to enhance the security of data
being exchanged via SMS. However, all these solu-
tions also add a certain amount of complexity and re-
quire the incorporation of additional components. For
our prototypical implementation we have therefore
omitted all security enhancing features. The evalu-
ation of existing approaches and their integration into
our solution to enhance its security is regarded as fu-
ture work.
In this paper we have presented an SMS based ap-
plication that makes use of advanced as well as qual-
ified electronic signatures to meet security require-
ments of transactional m-Government services. Our
application allows users to dynamically create, elec-
tronically sign, and deliver PDF documents on a pure
SMS basis. Tests have shown that our solution allows
documents to be created, singed, and deliverd within
a few seconds.
Although being fully functional, the presented ap-
plication is still in a prototypical state. The basic goal
of this prototypical implementation was to evaluate
whether an integration of electronic signatures into
SMS based services is technically feasible. Definitely,
our application shows that this is basically possible.
REFERENCES
Al-bakri, S. and Kiah, M. (2010). A novel peer-to-peer
sms security solution using a hybrid technique of
ntru and aes-rijndael. Scientific Research and Essays,
5(22):3455–3466.
Anuar, N. B., Kuen, L. N., Zakaria, O., Gani, A., and Wa-
hab, A. W. A. (2008). Gsm mobile sms/mms using
public key infrastructure: m-pki. W. Trans. on Comp.,
7:1219–1229.
Barkan, E., Biham, E., and Keller, N. (2008). Instant
Ciphertext-Only Cryptanalysis of GSM Encrypted
Communication. J. Cryptol., 21:392–429.
EGov-Labs (2012). PDF-AS. http://egovlabs.gv.at/projects/
pdf-as/.
European Union (1999). Directive 1999/93/ec of the eu-
ropean parliament and of the council of 13 december
1999 on a community framework for electronic signa-
tures.
Leitold, H., Hollosi, A., and Posch, R. (2002). Security ar-
chitecture of the austrian citizen card concept. In Pro-
ceedings of the 18th Annual Computer Security Ap-
plications Conference (ACSAC ’02). IEEE Computer
Society.
Lisonek, D. and Drahansk, M. (2008). Sms encryption for
mobile communication. International Conference on
Security Technology, pages 198–201.
MBAONLINE (2011). Planet text - how
sms messaging is changing the world.
http://www.mbaonline.com/planet-text/.
Medani, A., Gani, A., Zakaria, O., Zaidan, A. A., and
Zaidan, B. B. (2011). Review of mobile short message
service security issues and techniques towards the so-
lution. Scientific Research and Essays, 6(6):1147–
1165.
Mobi Solutions Ltd (2010). Mobile government: 2010 and
beyond.
Orthacker, C., Centner, M., and Kittl, C. (2010). Qualified
mobile server signature. In Proceedings of the 25th
TC 11 International Information Security Conference.
Posch, K.-C., Posch, R., Tauber, A., Zefferer, T., and Zwat-
tendorfer, B. (2011). Secure and provacy-preserving
egovernment - best practice austria. In Rainbow of
Computer Science. Springer.
Zefferer, T. (2011). Mobile government - e-government for
mobile societies.
WEBIST2012-8thInternationalConferenceonWebInformationSystemsandTechnologies
752
