
Practical Applications of Homomorphic Encryption
Michael Brenner, Henning Perl and Matthew Smith
Distributed Computing Security Group, Leibniz Universitt Hannover, Hannover, Germany
Keywords:
Homomorphic Encryption, Private Information Retrieval, Encrypted Search.
Abstract:
Homomorphic cryptography has been one of the most interesting topics of mathematics and computer security
since Gentry presented the first construction of a fully homomorphic encryption (FHE) scheme in 2009. Since
then, a number of different schemes have been found, that follow the approach of bootstrapping a fully homo-
morphic scheme from a somewhat homomorphic foundation. All existing implementations of these systems
clearly proved, that fully homomorphic encryption is not yet practical, due to significant performance limita-
tions. However, there are many applications in the area of secure methods for cloud computing, distributed
computing and delegation of computation in general, that can be implemented with homomorphic encryption
schemes of limited depth. We discuss a simple algebraically homomorphic scheme over the integers that is
based on the factorization of an approximate semiprime integer. We analyze the properties of the scheme and
provide a couple of known protocols that can be implemented with it. We also provide a detailed discussion on
searching with encrypted search terms and present implementations and performance figures for the solutions
discussed in this paper.
1 INTRODUCTION
Fully homomorphic encryption fired many people’s
imagination in the field of distributed computing se-
curity. Architectures have been proposed and many
application scenarios have been identified that can
benefit from FHE. Encrypted online storage, secure
delegation of confidential computation and even pri-
vacy for searching the web: the Cloud was about to
turn secure. Unfortunately, all implementations of
fully homomorphic encryption schemes showed, that
this technique is still much too slow for practical ap-
plications.
The most important property of FHE is un-
limited chaining of algebraic operations in the ci-
pherspace, which means that an arbitrary number of
additions and multiplications can be applied to en-
crypted operands. To achieve this, an FHE scheme
must provide a mechanism to reduce the noise of ci-
pher values, because these schemes are based on a
slightly inaccurate representation of the plaintext val-
ues. Every single operation on a ciphertext causes
even lower accuracy and eventually, the ciphertext can
no longer be properly decrypted.
This paper focuses on somewhat homomorphic
encryption, where no re-encryption is required but
only a limited number of operations is possible. We
discuss an algebraically homomorphic scheme and
show for a couple of problems of practical relevance,
how these can be solved by a surprisingly small num-
ber of operations on encrypted values. We exem-
plarily discuss solutions to the Millionaires’ Problem,
one-round Oblivious Transfer and oblivious memory
access based on the homomorphic scheme. We also
discuss searching over encrypted data with encrypted
search terms. Since this is a very important opera-
tion in distributed environments, we present our so-
lution to this in more detail in a separate section. We
showa delegation scheme, where the remote party op-
erates with encrypted arguments on public data and
generates encrypted results.This is useful when pos-
ing search requests to a public database while main-
taining confidentiality of request and response.
The paper is structured as follows: Section 2 gives
a summary of the current status of homomorphic
cryptography. Section 3 outlines a somewhat homo-
morphic encryption scheme and analyses its proper-
ties in detail. Section 4 introduces a selection of algo-
rithmic primitives that can be secured using our ho-
momorphic scheme. Section 5 introduces a constant-
depth approach to encrypted searching. In Section 6
we present details and performance figures of our im-
plementation. Section 7 concludes the paper.
5
Brenner M., Perl H. and Smith M..
Practical Applications of Homomorphic Encryption.
DOI: 10.5220/0003969400050014
In Proceedings of the International Conference on Security and Cryptography (SECRYPT-2012), pages 5-14
ISBN: 978-989-8565-24-2
Copyright
c
2012 SCITEPRESS (Science and Technology Publications, Lda.)

2 RELATED WORK
Since the breakthrough work of (Gentry, 2009), a
number of similar approaches to fully homomorphic
encryption appeared, like (Smart and Vercauteren,
2010) or slightly different approaches like (Braker-
ski and Vaikuntanathan, 2011). Performance figures
of actual implementations (Brenner et al., 2011) and
applications of FHE show that these systems can be
used for small problems only. Due to the computa-
tional overhead of current FHE schemes, the ques-
tion arises, if the underlying SHE schemes can also be
used for more practical homomorphicencryption. Re-
cent proposals, like (Naehrig et al., 2011) follow this
approach. However, the fully homomorphic encryp-
tion is still subject to progress in terms of new consid-
erations of hardness assumptions (Stehl and Steinfeld,
2010) or conceptual simplicity (Coron et al., 2011).
There are different paradigms for secure delega-
tion of computation like secure function evaluation
(SFE) mostly based on Yao's Garbled Circuits (Yao,
1982) and extensions by (Malkhi et al., 2004) or
(Kolesnikov et al., 2009b). Garbled circuits have
also been combined with homomorphicencryption by
(Gentry et al., 2010) and (Kolesnikov et al., 2009a) to
overcome their inherent disadvantage of of being lim-
ited to static one-pass boolean circuits.
A theoretical approach to achieveprivacyof mem-
ory access patterns and algorithm execution in a spe-
cial type of Turing Machines is the Oblivious Random
Access Machine (ORAM) by (Goldreich, 1987) (Gol-
dreich and Ostrovsky, 1996). There are recent propos-
als to reduce the complexity of ORAMs by Pinkas et
al. (Pinkas and Reinman, 2010) and further devel-
opments towards practical applications by (Damgrd
et al., 2011) and (Goodrich and Mitzenmacher, 2011).
Section 4 outlines how to achieve oblivious memory
access with our scheme.
3 A SOMEWHAT
HOMOMORPHIC
ENCRYPTION SCHEME
This section describes the encryption scheme and its
propertiescorrectness, security and compactness. Our
somewhat homomorphic encryption scheme E de-
pends on the following parameters:
• the security parameter λ,
• the bit length η of a cipher’s initial noise,
• the modulus p which is a large prime integer of
order 2
λ
,
• the bit length ρ of the message space, defined as
λ− η.
3.1 The Basic Construction
Our scheme E is defined as a tuple {P,C, K, E, D, ⊕, ⊗}
where the elements denote the following:
P is the plaintext space and contains elements
from N
+
limited by the prime integer p of order 2
λ
such that for two plaintext operands a, b ∈ N
P
, a· b < p
and N
P
:= {x|x < 2
η
}.
C is the ciphertext space and contains elements
from N
+
.
K is the key generator. The secret key is a large
prime integer p, the auxiliary compression argument
is d with d ← 2s+ rp with r ∈ N
+
and s ∈ N
C
with ∀x ∈
N
C
, ∀y ∈ N
P
, 2x < y (see compactness).
E is the encryption function. We encrypt a bit
value b by picking an integer a with a ≡ b mod 2 and
adding a random even or odd multiple of the prime
modulus, such that a
′
= a + (rp). If r is composite, it
must contain at least one large prime factor of order
2
λ
. It is mandatory that a ∈ N
+
, i.e. the encryption
must add noise (see below).
D is the decryption function. The decrypted result
is the remainder of a ciphertext modulo the prime key
p: a = a
′
mod p.
⊕ is the addition in ciphertext space. Due to the
cipher structure, the addition is performed as an ordi-
nary arithmetic addition. The scheme is mixed addi-
tive.
⊗ is the multiplication in ciphertext space. Like
the addition, the multiplication is performed as an
ordinary arithmetic multiplication. The scheme is
mixed multiplicative.
In this scheme, the positive plaintext value is also
the noise for the ciphertext because it additively in-
terferes with the product of the prime factors that en-
crypt it. In order to obtain a probabilistic encryption
scheme, we perform parity (mod 2) arithmetics, i.e.
a plaintext bit is encoded in a random integer of the
same parity. Notice that the encryption does not re-
veal the parity of the plaintext integer, because the
encryption function E picks at random even or odd
multiples r of the key p. This effectively allows us to
hide the parity of the plaintext and to encode binary
information.
3.2 Correctness
We show the correctness of the encryption and de-
cryption, as well as the homomorphic operations in
the following lemmas, assuming that p ∈ N
+
be a
SECRYPT2012-InternationalConferenceonSecurityandCryptography
6

large prime integer as a secret key and a and b be two
arbitrary positive integers with a, b ≪ p ∈ N
+
.
Lemma 1. The encryption scheme E is mixed additive
and the addition is correct if a+b < p.
Proof. We perform the encrypted addition as (a
′
⊕
b
′
) which extends to (a
′
⊕ b
′
) = (a+ r
1
p) + (b+ r
2
p) =
a + b + (r
1
+ r
2
)p and decrypted mod p yields (a + b).
The mixed additive operation is defined as a
′
⊕ b =
(a+ rp) + b = a+ rp+ b mod p = a+ b.
Lemma 2. The encryption scheme E is mixed multi-
plicative and the multiplication is correct if a∗ b < p.
Proof. We perform an encrypted multiplication
as a
′
⊗ b
′
= (a+ r
1
p)(b+ r
2
p) = ab + a(r
2
p) + b(r
1
p) +
(r
1
r
2
)p
2
mod p = (ab). The mixed multiplicative oper-
ation is defined as a
′
⊗b = (a+rp)b = ab+brp mod p =
ab.
Lemma 3. The encryption scheme E is capable of
computing a sequence of at least log
2
ρ − log
2
η arith-
metic operations.
Proof. The choice of the factors r and p also de-
fines the message space, such that the bit length of
the message space ρ is λ − η. The noise of a cipher
grows by at most one bit per addition (the carry), so
the minimum number of additions is ρ. The mini-
mum number of subsequent multiplications is defined
as log
2
ρ− log
2
η, assuming that ciphers with the max-
imum noise are multiplied, since this can produce at
most η2
n
bits of noise after n multiplications.
3.3 Security
As shown above, our simple encryption scheme is al-
gebraically correct. This subsection discusses con-
fidentiality of the encrypted data and the security of
the encryption scheme. The results of this subsection
lead to the choice of appropriate parameters. The at-
tack model focuses an attacker who is in possession
of a ciphertext. Since we apply symmetric encryption
only, the attacker has no public key. By reduction to
integer factorization we show the security of the en-
cryption scheme against the computation of the secret
key from a ciphertext.
Lemma 4. Let the parameters (p, q) ∈ N
+
be of or-
der 2
λ
. Any Attack A running in time polynomial in λ
against the encryption scheme can be converted into
an algorithm B for solving the integer factorization
of any composite integer number (pq) running in time
polynomial in λ.
Proof. Consider a poly(λ) time function A
ex
p ← A
ex
(a
′
)
that efficiently computes p from any cipher a
′
.
That means, that A
ex
is able to extract p from any inte-
ger computed by a term of the form a+ pq for arbitrary
a, p, q and thus can be applied in a function
B
fac
(i) : p ← A
ex
(0+ i)
to factorize arbitrary composite integers (pq) that
can be trivially expressed as 0+ pq.
Now we show the security of the encryption
scheme against an attempt of A to compute the plain-
text value of a cipher. We achieve this by showing in
addition to Lemma 4 an IND-CPA equivalent prop-
erty of the scheme, which means that any two cipher-
texts are computationally indistinguishable by A.
Lemma 5. The security of the encryption scheme
is IND-CPA equivalent and the success probability
|Pr[Exp
ind−cpa
= 1] −
1
2
| is negligible in λ for any A
from PPT (probabilistic polynomial time) function.
Proof. Since A has no public key for encryption,
we provide a probabilistic encryption oracle O
Enc
that
takes a plaintext as input and generates a ciphertext
under the secret key. Consider the following experi-
ment in the message space M :
Exp
λ
ind−cpa
= {
{m
0
, m
1
} ← M
i
R
← {0, 1}
c ← O
Enc
(m
i
)
i
A
← A
ind−cpa
(c, {m
0
, m
1
})
return
1 if i = i
A
0 otherwise
}
The encryption function equivalent oracle O
Enc
is
defined as follows:
O
λ,p
Enc
(m)= {
a
R
← 2[2
η
]
r
R
← [2
λ
]
c ← (m mod 2) + a+ rp
return c
}
The parity of the output of the oracle O
Enc
(m) has a
discrete uniform distribution, such that Pr[O
Enc
(m) ≡
2
0] = Pr[O
Enc
(m) ≡
2
1] =
1
2
for any integer m ∈ N
+
, i.e.
the encryption function does not leak any parity infor-
mation. It is sufficient to show that Pr[O
Enc
(m) ≡
2
1] =
1
2
.
Pr[O
Enc
(m) =
2
1] = Pr[(a+ r · p ≡
2
1]
Pr[a ≡
2
1] · Pr[r · p ≡
2
0]
|
{z }
=0.5
+Pr[a ≡
2
0]
| {z }
=0
·Pr[r· p ≡
2
1]
|
{z }
=0.5
1
2
(Pr[a ≡
2
1])
|
{z }
=1
=
1
2
This leads to the conclusion that ciphertexts are in-
distinguishable by A, even if he is allowed to provide
known plaintext to the encryption function.
PracticalApplicationsofHomomorphicEncryption
7

3.4 Compactness
The length of a ciphertext grows exponential in the
number of multiplications applied to it. In order to
obtain compact ciphertexts, i.e. the length of a cipher-
text is independent from the number of operations, we
suggest generating an encryption of 0 as an auxiliary
compression argument d that can be used in a reduc-
tion procedure to limit the size of a ciphertext. The
security of this delimiter is subject to Lemma 4.
Lemma 6. The operation a
′′
← a
′
mod (2s + rp) re-
duces the bit length of the ciphertext a
′
. The reduction
is correct for any 2s ∈ N
+
< a, i.e. the parity of the
original plaintext a encrypted in a
′
is preserved in a
′′
.
The length of a reduced cipher is |2s+ rp| = 2λ.
Proof. a
′′
← a
′
mod d ⇔ a
′′
← a
′
−⌊
a
′
d
⌋·d, d = 2s+rp
⇒ a
′′
= a
′
− ⌊
a+r
1
p
2s+r
2
p
⌋ · (2s + r
2
p); I : a + r
1
p < 2s + r
2
p
⇒ a
′′
= a
′
; II : a+ r
1
p ≥ 2s+ r
2
p ⇒ n = ⌊
a+r
1
p
2s+r
2
p
⌋, n ≥ 1;
δ = n· (2s+ r
2
p) = 2ns+ nr
2
p
⇒ a
′′
← a+ r
1
p
|{z}
mod p=0
|
{z }
a
′
− 2ns
|{z}
even
− nr
2
p
|
{z}
mod p=0
| {z }
δ
mod p ≡
2
a
The reduced result a
′′
decrypted mod p has the same
parity as a.
3.5 Choice of Parameters
As we showed above, the security of our scheme is
essentially based on the common assumption, that the
factorization of a large integer is hard. So the product
of the prime key p and the factor r must be sufficiently
large. Taking the results of the former RSA-challenge
into account, we suggest factors with a size ¿512 bits.
A reasonable configuration with a factor size of λ =
1024 bits and an initial noise of η = 8 bits would allow
for a sequence of log
2
λ− log
2
η = 7 multiplications.
Small factors. The encryption function must not
issue a ciphertext with a = 0 in order to avoid small
factors: if it generated two different representations
of 0 with a
′
1
= 0 + r
1
p and a
′
2
= 0 + r
2
p, the adver-
sary could easily generate a positive composite inte-
ger b
′
= |(a
′
1
− a
′
2
)| = |(r
1
− r
2
)|p, with |(r
1
− r
2
)| likely
containing a small factor, assumed that r
1
and r
2
are
in a similar range.
4 SIMPLE APPLICATIONS
This section describes a selection of algorithms that
can be encrypted by applying the scheme E.
4.1 One-round k-Bit Oblivious Transfer
Bob has two arguments and wants to share one of
them with Alice. Alice is allowed to pick one ar-
gument but doesn’t want to reveal to Bob which one
she chooses. On the other hand, Bob wants to keep
the other argument secret. Using our homomorphic
scheme, we can solve this problem for arbitrary k-bit
Strings in a single request-reply interaction. This is
the protocol:
1. Alice has a ∈ {0, 1} and the secret key SK
2. Bob has m
0,1
∈ {0, 1}
k
, two k-bit strings
3. Alice picks at random a η-bit integer t ∈ N
+
such
that t ≡ a mod 2 and encrypts a
′
← E(t)
SK
4. Bob picks at random η-bit integers m
′
i
j
∈ N
+
such
that m
′
i
j
≡ m
i
j
mod 2 for i ∈ {0, 1} and 0 ≤ j ≤ (k−1).
He computes the (selected) output bits s
j
← ((m
0
j
·
(a
′
+ 1)) + (m
1
j
· a
′
)) for 0 ≤ j ≤ (k − 1)
5. Alice decrypts the selected bit string by comput-
ing s
j
← D(s
′
j
)
SK
mod 2 for 0 ≤ j ≤ (k − 1)
The multiplicative depth of this protocol is 1. Bob
determines the result value by applying a binary se-
lector over the two bit strings, addressed by Alice’s
binary selection argument. He computes s ← (m
0
∧
¬a)⊕ (m
1
∧a) by evaluating logic AND-operations af-
ter transferring them into an arithmetic representation.
4.2 Oblivious Memory Access
In this scenario, we have a larger number of mes-
sages to choose from, so this problem can be solved
by applying a log
2
n-bit demultiplexer for n messages.
The algorithm for this purpose is quite similar to a
memory circuit: the switching function of the demux
that selects a memory item m ∈ {m
0
, m
1
, m
2
, m
3
} ad-
dressed by a ∈ {(00), (01), (10), (11)} is given as m =
(¬a
0
∧ ¬a
1
∧ m
0
) ∨ (a
0
∧ ¬a
1
∧ m
1
) ∨ (¬a
0
∧ a
1
∧ m
2
) ∨
(a
0
∧ a
1
∧ m
3
). Consider the following protocol:
1. Bob has 4 items m
0
..m
3
∈ {0, 1}
2. Alice has an argument a ∈ {0, 1}
2
and the secret
key SK
3. Alice picks at random η-bit integers t
i
∈ N
+
such
that t
i
≡ a
i
mod 2 for 0 ≤ i ≤ 2 and encrypts each
a
′
i
← E(t
i
)
SK
4. Bob picks at random η-bit integers m
′
i
∈ N
+
such
that m
′
i
≡ m
i
mod 2 for 0 ≤ i ≤ 3. He computes s
′
←
((a
′
0
+ 1) · (a
′
1
+ 1) · m
′
0
) + (a
′
0
· (a
′
1
+ 1) · m
′
1
) + ((a
′
0
+
1) · a
′
1
· m
′
2
) + (a
′
0
· a
′
1
· m
′
3
)
5. Alice decrypts the selected value s ← D(s
′
)
SK
.
SECRYPT2012-InternationalConferenceonSecurityandCryptography
8

This protocol has a multiplicative depth of 2 for a
range of 4 items. The number of selectable items
(i.e. the memory size) can be extended by a wider
address range which leads to a higher multiplicative
depth given as log
2
n. It can be extended to select k-bit
items by arranging k instances in parallel.
4.3 The Millionaires’ Problem
Alice and Bob want to know who is richer but don’t
want to reveal the amounts of their respective capi-
tals. This paragraph depicts a solution to this problem
using homomorphicallyencrypted binary adders. The
protocol is as follows:
1. Alice has a ∈ {0, 1}
k
, containing a (k-1)-bit little-
endian binary representation of her capital in
a
0
..a
k−2
, a
k−1
← 0 and the secret key SK.
2. Bob has b ∈ {0, 1}
k
, like a, b
k−1
← 0
3. Alice picks at random η-bit integers t
i
∈ N
+
such
that t
i
≡ a
i
mod 2 and encrypts a
′
i
← E(t
i
)
SK
for 0 ≤
i ≤ (k− 1)
4. Bob picks at random η-bit integers b
′
i
∈ N
+
such
that b
′
i
≡ b
i
mod 2 for 0 ≤ i ≤ (k− 1). He computes
b
′
i
← b
′
i
+ 1 for 0 ≤ i ≤ (k− 1), picks at random an
η-bit integer t
′
∈ N
+
with t
′
≡ 1 mod 2, computes
u
′
0
← b
′
0
+ t
′
and c
′
0
← b
′
0
· t
′
and further u
′
i
← b
′
i
+
c
′
i−1
, c
′
i
← b
′
i
· c
i−1
for 1 ≤ i ≤ (k − 1). Now he has
the two’s complement of b
′
in u
′
. He computes
s
′
0
← a
′
0
+ u
′
0
and c
′
0
← a
′
0
· u
′
0
. Finally, he computes
s
′
i
← a
′
i
+ u
′
i
+ c
′
i−1
and c
i
← (a
′
i
· u
′
i
) + (c
′
i−1
· (a
′
i
+ u
′
i
))
for 1 ≤ i ≤ (k − 1).
5. Alice decrypts s ← D(s
′
k−1
)
SK
and concludes for
both parties that a < b if s ≡ 1 mod 2 and a ≥ b
otherwise.
Bob first computes the two’s complement of his argu-
ment and adds Alice’s a. The most significant bit of
the solution (the sign) indicates the relation between a
and b: if the solution is negative, i.e. the sign bit is 1,
then obviously b is greater then a. As stated in Section
3.2, Bob injects his data unencryptedly. However, af-
ter an operation with an encrypted operand, the result
contains the implicitly encrypted plaintext argument.
The multiplicative depth of the protocol is 2.
5 SEARCH USING
CONSTANT-DEPTH CIRCUITS
This section introduces an approach to encrypted
searching using circuits of constant depth that oper-
ate on encrypted queries and data. This application
of homomorphic encryption is described in more de-
tail than the simple use cases in Section 4, because
remote encrypted search is one the basic operations
in a distributed setting with a wide range of possible
applications. Therefore we split the search scenario
in the subtypes exact search and fuzzy search.
5.1 General Approach
The following components are part of the system: The
Input This can be a list of words or a stream of data.
The Encrypted circuit For each word in the input data,
an encrypted homomorphic circuit is executed, which
calculates one element in the output vector, based on
the encrypted search term. An Encrypted search term
The search term is encrypted and used by the homo-
morphic circuit. The Output indicator vector In the
case of an exact search, the output vector is a bit-
vector containing a 1 if the search term matches and
a 0 else. Yet, it is also possible to do an inexact fuzzy
search with this approach. In this case, the output vec-
tor would contain the rank of the match. Formally,
one cell of the output vector can be written as the
value of a function
ϕ :
Σ
∗
× C
∗
→ C
∗
(word, searchterm) 7→ C (word,searchterm)
(1)
Since the definition of ϕ is independent of the other
words in the database, the output can efficiently be
computed in parallel. Another advantage is that the
circuit C depends only on the encrypted search term.
Especially, the depth is constant with respect to the
size of a database entry. See 5.2.3 for a reduction of
the output size.
5.2 Exact-match Search
Building on the general approach for searching intro-
duced above, one can easily generate a circuit which
executes an exact-match search. The circuit should
have the following property:
ϕ(word, searchterm) =
(
1 word == searchterm
0 else
(2)
which translates to a character-level comparison
ϕ(word, searchterm) =
|searchterm|−1
^
i=0
(word
i
=
c
searchterm
i
)
(3)
The two things that need further specification are
a) the concrete implementation of the character-level
comparison =
c
and b) the (common) case when
|searchterm| 6= |word|.
PracticalApplicationsofHomomorphicEncryption
9

5.2.1 Character-level Comparison
Let Σ be the finite alphabet for the word database as
well as the search term. Then there exists a strict total
order < on Σ. In case of Σ = {a, . . . , z, A, . . . , Z} this
may for example be the dictionary order. The bijec-
tive funciton bin(σ) then returns the binary value of
the positon of σ and is defined as
bin :
Σ → {0, 1}
⌈log
2
Σ⌉
σ 7→
(
0 if σ = min(Σ)
max
σ
′
<σ
{bin(σ
′
)} + 1
2
else.
(4)
Finally, the relation =
c
is defined as
=
c
:
{σ
1
, σ
2
}|
⌈log
2
Σ⌉−1
^
i=0
bin(σ
1
)
i
⊕bin(σ
2
)
i
⊕1
.
(5)
The depth of the resulting circuit from Equation 5.2
combined with the circuit of =
c
from Equation 5 is
depth(ϕ(word, search)) =
2+ ⌈log
2
Σ⌉ + ⌈log
2
|search|⌉ ∈ O(log
2
n)
(6)
Note that the computation of bin is just used to trans-
form a character to its binary representationand there-
fore is not part of the circuit itself. Rather than com-
puting the implicit function given in Equation 4 one
would use a code table like ASCII for an efficient
transformation.
5.2.2 Padding
In Equation 5.2 the implicit requirement was |word| ≥
|searchterm| introduced. In a general search, however,
the lengths of the search term and the words may very
well be different.
Definition 5.1. For an alphabet Σ anda padding char-
acter with Σ ∩ =
/
0 let the alphabet with padding
be
e
Σ = Σ ∪ {}.
n
is a shorthand for ···
|
{z }
n times
, an n-
character padding.
Additionally, some random padding may be re-
quired for the searchterm, because the length of
the searchterm is a public information, even if the
searchterm itself is encrypted. Also, the length of
the searchterm is revealed in the depth of the cir-
cuit. In order to hide the actual length the client
appends a random number of padding characters to
the searchterm prior to encrypting it. The server
only evaluates the search function for database items
shorter than the searchterm. Despite this modifi-
cations, the depth of ϕ is still in O(logn), as the
only modifications made add a constant to Σ and
|searchterm| in Equation 6.
5.2.3 Reducing the Output Size
The output vector of the exact search has a linear de-
pendency in the size if the database that is operated
on. Under the assumption of a total strict order of
the database elements, we have that the search yields
at most one positive indicator (or none, if no entry
in the databases matches the search term). Following
the technique, outlined in the description of the obliv-
ious memory access in 4.2, the reduced output vec-
tor for the indicators I
0
..I
n
can be computed as
∑
n
i=0
I
i
.
This reduces the output space complexity to O(1), i.e.
to one single element which contains an encrypted
1, if the search term was found and an encrypted 0
otherwise. To indicate the position of the match in
the database, the return value can be computed as
∑
n
i=0
I
i
∗ i. The result can be returned as a log
2
n bit el-
ement with an encrypted binary representation of the
match index i. The reduction cost of the binary index
generation is a multiplicative depth which is increased
by 1.
5.3 Fuzzy Search
While Section 5.2 provided some fundamental con-
struction of a search using a homomorphiccircuit, this
section uses that principle to its full extent by allow-
ing more than just a boolean comparison (=
c
) of the
characters. This results in the ability to also compute
inexact matches. The main part that differs from the
exact search scheme is the construction of φ.
5.3.1 Counting Mismatches
The first step towards a circuit evaluating a fuzzy
search is done by counting the number of mismatches
between the search string and a given word in a
database or a substring in a character stream. To ac-
complish this the multiplicative (AND) combination
of all the character-level comparisons like in Equa-
tion 5.2 is replaced by a sum, yielding
ϕ :
Σ
∗
× C
s
→ C
⌈log
2
s⌉
(w, s) 7→
|s|−1
∑
i=0
(w
i
=
c
s
i
)
. (7)
Since the sum can be expressed as a hamming
weight of a bit vector, the application of symmet-
ric polynomials leads to a very shallow circuit, used
for example in (Smart and Vercauteren, 2010, page
15). The k-th bit of the hamming weight of a vector
SECRYPT2012-InternationalConferenceonSecurityandCryptography
10

(b
1
, . . . , b
n
) can be directly expressed by the polyno-
mial
e
2
k−1
(b
1
, . . . , b
n
) :=
∑
1≤ j
1
< j
2
··· j
2
k−1
≤n
b
j
1
···b
j
2
k−1
.
The evaluation of the polynomial translates directly
to the circuit
e
2
k−1
(b
1
, . . . , b
n
) :=
M
1≤ j
1
< j
2
··· j
2
k−1
≤n
b
j
1
··· ∧ · · · b
j
2
k−1
.
In the case that the maximum number of errors
err
max
is given beforehand, the advantage of symmet-
ric polynomials is that one can directly limit the num-
ber of evaluated polynomials to the first log
2
(err
max
)
digits of the output vector.
5.3.2 “Softer” Mismatches
Some applications of fuzzy search, for example the
mapping of short reads in genomes (Trapnell and
Salzberg, 2009), require more differentiation when
calculating the match between two characters. In this
example, a sequence where only one character (= acid
in the DNA) changed to one chemically related acid
still strongly indicates a match in the genome. Conse-
quently, if the position of the mismatch would intro-
duce a change to a completely unrelated acid, a match
of the sequence would be less likely.
For the rest of this subsection, let the alphabet
Σ = {A,C, G, T} consist of the four acids that build
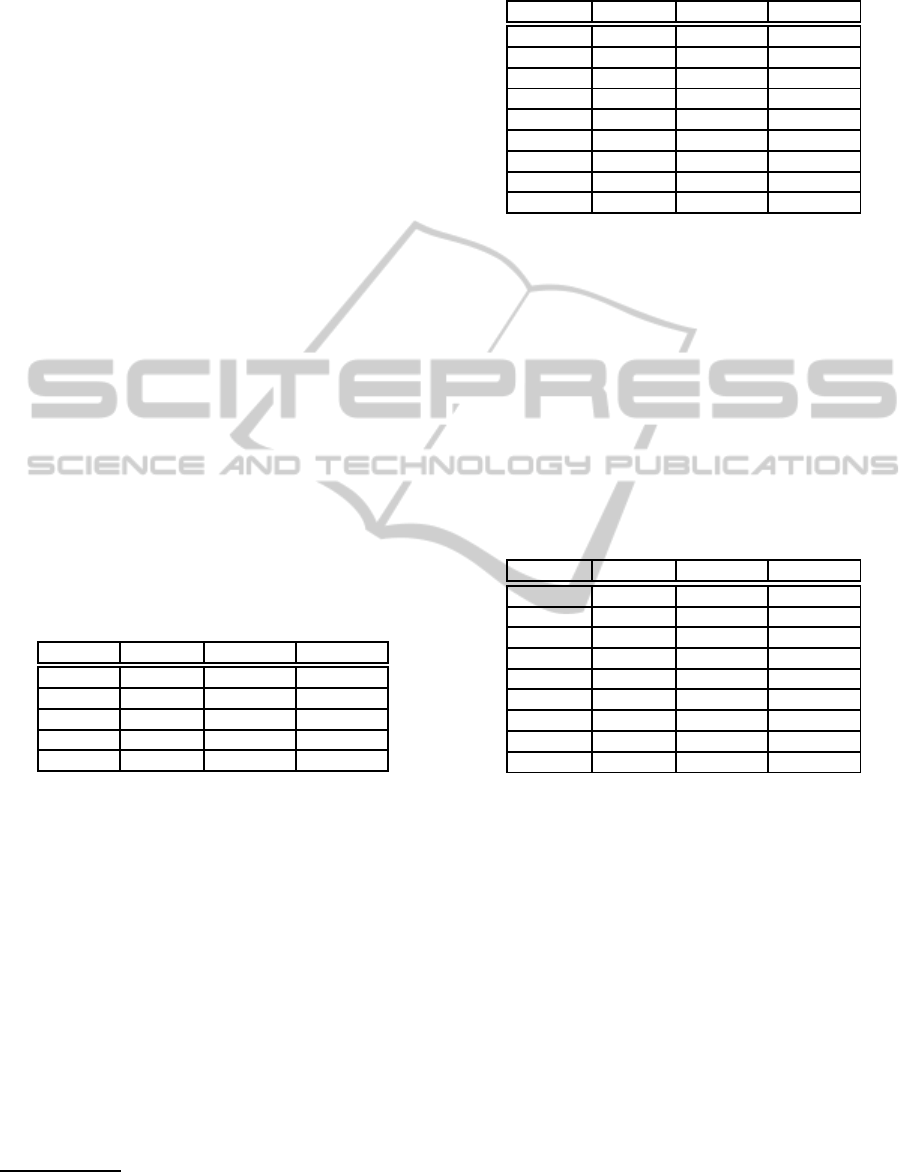
the DNA. The top table in Figure 1 lists the quan-
tified differences (penalities) between these DNA-
bases which reflect a computational metric for the ge-
netic distances between a searchterm and a processed
genome sequence.
In the circuit, a function pen : Σ×Σ → C
∗
is needed
that maps two given characters to the penalty of con-
verting one character into the other. Since this func-
tion needs to be evaluated inside the circuit, it needs
to be written as a boolean circuit itself. The necessary
steps (also see Figure 1) are:
1. For each character c in the row and column head-
ers, write bin(c). Additionally, write the penalty in
binary.
2. For each digit of the binary value of the penalty,
write one table containing only that digit.
3. For each table in the previous step, create a mini-
mal circuit evaluating this table using a Karnaugh
map.
Depth analysis of pen. Without loss of generality,
assume the resulting circuit be in conjunctive normal
form (CNF). The conjunction at the top level results
in AND-gates of depth log
2
(|Σ|). Since only XOR-
G A C T
G 0 1 3 2
A 1 0 1 3
C 3 1 0 2
T 2 3 2 0
00 01 11 10
00 00 01 11 10
01 01 00 01 11
11 11 01 00 10
10 10 11 10 00
1
00 01 11 10
00 0 0 1 1
01 0 0 0 1
11 1 0 0 1
10 1 1 1 0
2
o
1
= (a
2
∨ b
2
)
∧ (a
1
∨ b
1
)
∧ (a
2
∨ a
1
∨ b
2
∨ b1)
3
00 01 11 10
00 0 1 1 0
01 1 0 1 1
11 1 1 0 0
10 0 1 0 0
2
o
0
= (a
2
∨ b
2
)
∧ (a
0
∨ b
0
∨ b
1
)
∧ (b
0
∨ a
0
∨ a
1
)
∧ (
a
0
∨ a
1
∨ b
0
∨ b
1
)
3
bin
Figure 1: Construction of the pen function: transformation
of a penalty table to a circuit using a Karnaugh map.
and AND-gates are available in the homomorphic cir-
cuit, each binary disjunction a∨ b must be written as
compound operation (a ⊕ b) ⊕ (a ∧ b), resulting in a
factor two compared to the depth of a circuit using
OR gates. Each disjunctive term therefore has depth
log
2
(2|Σ|). The total depth of the resulting circuit for
pen is log
2
(|Σ|) + log
2
(2|Σ|) ∈ O(log|Σ|), which is the
same depth as for =
c
in Section 5.2.1.
By replacing the character comparison with a
penalty function, it is also necessary to sum up the
individual penalties from the character-level compar-
isons for a total penalty of the word match as shown
in Section 5.3.1. This results in the circuit
ϕ :
Σ
∗
× C
s
→ C
⌈log
2
s⌉
(w, s) 7→
|s|−1
∑
i=0
pen(w
i
, s
i
)
. (8)
5.4 Results
In this section we introduced an approach to mark the
position of a definitive or probable match with respect
PracticalApplicationsofHomomorphicEncryption
11
to exact or fuzzy search. The circuit ϕ that needs
to be evaluated in the homomorphic cipherspace was
shown to have a depth bound to O(log
2
|Σ|) in all cases.
This means that the depth of the circuit is known be-
forehand, and especially that it does notdepend on the
size of the database.
6 IMPLEMENTATION &
PERFORMANCE
This section gives a brief summary of our implemen-
tation
1
. The platform for the prototype is Java 6 SE
on a 2.4 GHz Core 2 Duo with 3 MB L2 cache and 4
GB RAM. We present performance figures for differ-
ent key and problem sizes.
6.1 Basic Operation Timings
Due to the structure of the homomorphic scheme E,
the algorithms for addition, multiplication and de-
cryption are almost atomic arithmetic operations of
the underlying library for large integer handling. The
most time consuming operations are K (Keygen) and
E (Encrypt). The timing for these and the other basic
operations is depicted in Table 1. The reason for the
Table 1: Timings for basic operations.
Op. λ = 512 λ = 1024 λ = 2048
Keygen 35ms 270ms 4242ms
Encrypt 35ms 301ms 3218ms
Decrypt ¡1ms ¡1ms ¡1ms
Add ¡1ms ¡1ms ¡1ms
Mult ¡1ms ¡1ms ¡1ms
relatively long runtime of Keygen and Encrypt is the
determination of a prime number during these opera-
tions.
6.2 Protocol Timings
Our implementation comprises the protocols outlined
in Section 4. The algorithms have been transformed
into native Java code which invokes the API of our
encryption scheme. The resulting performance is de-
picted in Table 2, which contains the time consump-
tion figures and Table 3, showing the sizes of the out-
put arguments.
1
The software can be downloaded at
http://www.hcrypt.com
Table 2: Protocol timings.
Protocol λ = 512 λ = 1024 λ = 2048
OT100 ¡1ms ¡1ms ¡1ms
OT10k 8ms 15ms 35ms
OT100k 190ms 290ms 426ms
YMP4 ¡1ms ¡1ms ¡1ms
YMP40 2ms 9ms 37ms
YMP80 10ms 34ms 132ms
OMA16 ¡1ms 1ms 4ms
OMA32 1ms 4ms 14ms
OMA64 3ms 12ms 43ms
6.3 Parameter Sizes
For the key parameters, factor sizes of λ ∈
{512, 1024, 2048} and η = 8 bits have been chosen.
There are measurements of every described protocol
for three different problem sizes. Table 3 shows the
return sizes for the Oblivious Transfer (OT) proto-
col implementation with 100, 10000 and 100000 bits
long plaintext arguments. The timing figures show the
runtime required for the determination of the result
by Bob. The output sizes of the single return argu-
Table 3: Oblivious transfer parameter sizes (Bits).
Protocol λ = 512 λ = 1024 λ = 2048
OT100 103k 205k 410k
OT10k 10.3M 20.5M 41M
OT100k 103M 205M 410M
YMP4 3k 6k 12k
YMP40 40k 80k 160k
YMP80 80k 161k 323k
OMA16 4k 8k 16k
OMA32 5k 10k 20k
OMA64 6k 12k 24k
ments of Yao's Millionaires' Problem (YMP) shown
in Table 3 are in the range from 4 to 80 plaintext bits
and therefore require between 3k and 323k bits of en-
crypted space. The runtime figures in Table 2 only
contain the computational part of Bob. The Oblivious
Memory Access (OMA) is the selection of exactly one
of 16, 32 or 64 elements (memory bits). So the re-
turn sizes are the number of bits required by a single
encrypted return bit. The calculation of the memory
circuit by Bob is shown in the runtime figures.
6.4 Search Results
We have implemented the exact search as described
in Section 5.2 with different key sizes and database
sizes, as well as two different output set reductions.
The default reduction yields a one-bit indicator con-
taining an encrypted 1 if the search term matches a
SECRYPT2012-InternationalConferenceonSecurityandCryptography
12
database entry and 0 otherwise. The second reduction
type generates an encrypted binary representation of
the matching entry’s database index. The word size
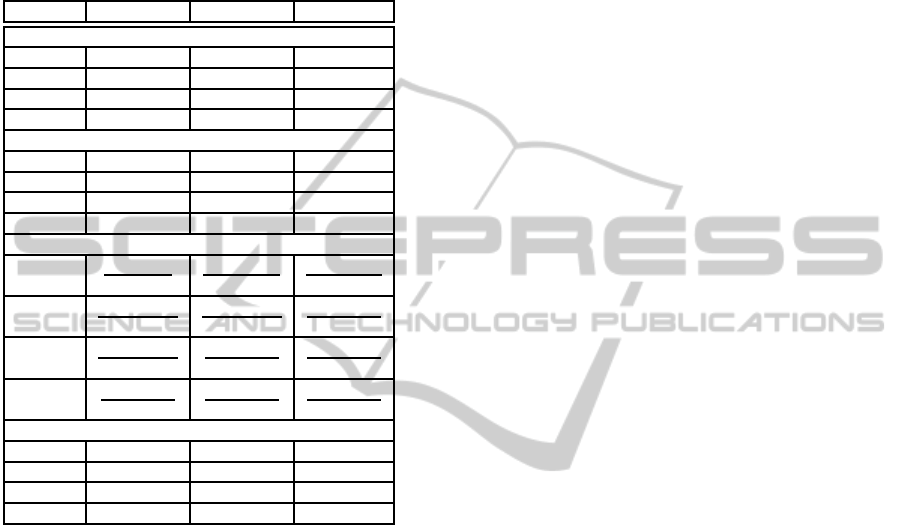
for all experiments is 5 bits. Table 4 summarizes the
result figures. The upper section of Table 4 depicts
Table 4: Exact-match search results.
DB size λ = 512 λ = 1024 λ = 2048
search
1024 31 ms 115 ms 442 ms
256 k 8.6 s 30.1 s 119 s
512 k 17.4 s 61.1 s 241 s
1 M 36.9 s 124 s 487 s
generate index
1024 11 ms 22 ms 43 ms
256 k 5.1 s 10.2 s 20.4 s
512k 12 s 24.0 s 48.1 s
1 M 29.8 s 59.5 s 119.5 s
indicator vector size(bits,
∗
compact cipher)
1024
1 M
∗
5.2 M
2 M
∗
10.5 M
4 M
∗
20.9 M
256 k
256 M
∗
1.34 G
512 M
∗
2.68 G
1 G
∗
5.37 G
512k
512 M
∗
2.68 G
1 G
∗
5.37 G
2 G
∗
10.7 G
1 M
1 G
∗
5.37 G
2 G
∗
10.7 G
4 G
∗
21.4 G
index value size (bits)
1024 5.1 k 10.2 k 20.5 k
256 k 5.1 k 10.2 k 20.5 k
512k 5.1 k 10.2 k 20.5 k
1 M 5.1 k 10.2 k 20.5 k
the timing results for different key sizes and database
sizes. The timings scale almost linearly with the size
of the database, whereas larger keys cause an expo-
nential timing behavior. The second section of the
table shows the timings of the index-reduction for the
different problem sizes. The sum of the index gen-
eration time and the basic search time is the total ex-
ecution time for an index-reduced search. Section 3
of the table summarizes the sizes in number of bits of
the returned match-indicator vectors. The lower sec-
tion of the table contains the return sized of an index-
reduced search. The returned argument contains an
encrypted binary representation of the log
2
n plaintext
index-bits.
7 SUMMARY
In this paper we discussed an algebraically homo-
morphic scheme of limited multiplicative depth that
can be used as an approach to build practical applica-
tions that operate on encrypted data. We discussed the
properties of the SHE scheme and provided a proof of
correctness. We gave a security analysis for different
attack models and stated, under what circumstances
the scheme is secure. Proof-of-concept implementa-
tions of the discussed protocols outlined the charac-
teristics of homomorphically encrypted real-life ap-
plications. A detailed formal analysis of exact-match
searching with extensions to fuzzy searching on en-
crypted data with encrypted search terms showed,
how the algorithmic primitives of the simple proto-
cols can be combined to solve a problem of higher
complexity.
REFERENCES
Brakerski, Z. and Vaikuntanathan, V. (2011). Effi-
cient fully homomorphic encryption from (standard)
lwe. Cryptology ePrint Archive, Report 2011/344.
http://eprint.iacr.org/.
Brenner, M., Wiebelitz, J., von Voigt, G., and Smith, M.
(2011). A smart-gentry based software system for se-
cret program execution. In Proc. of the International
Conference on Security and Cryptography SECRYPT.
SciTePress.
Coron, J.-S., Mandal, A., Naccache, D., and Tibouchi, M.
(2011). Fully homomorphic encryption over the inte-
gers with shorter public keys. In Advances in Cryptol-
ogy CRYPTO 2011, volume 6841 of LNCS. Springer
Berlin / Heidelberg.
Damgrd, I., Meldgaard, S., and Nielsen, J. (2011). Perfectly
secure oblivious ram without random oracles. In The-
ory of Cryptography, volume 6597 of LNCS. Springer
Berlin / Heidelberg.
Gentry, C. (2009). Fully homomorphic encryption using
ideal lattices. In Proc. of the 41st annual ACM sympo-
sium on Theory of computing, STOC ’09, New York,
NY, USA. ACM.
Gentry, C., Halevi, S., and Vaikuntanathan, V. (2010). i-
hop homomorphic encryption and rerandomizable yao
circuits. In Advances in Cryptology - CRYPTO 2010,
volume 6223 of LNCS. Springer Berlin / Heidelberg.
Goldreich, O. (1987). Towards a theory of software protec-
tion and simulation by oblivious rams. In Proc. of the
19th annual ACM symposium on Theory of comput-
ing, STOC ’87, New York, NY, USA. ACM.
Goldreich, O. and Ostrovsky, R. (1996). Software protec-
tion and simulation on oblivious rams. J. ACM, 43.
Goodrich, M. and Mitzenmacher, M. (2011). Privacy-
preserving access of outsourced data via oblivious ram
simulation. In Automata, Languages and Program-
ming, volume 6756 of LNCS. Springer Berlin / Hei-
delberg.
Kolesnikov, V., Sadeghi, A.-R., and Schneider, T. (2009a).
How to combine homomorphic encryption and gar-
bled circuits improved circuits and computing the
minimum distance efficiently.
Kolesnikov, V., Sadeghi, A.-R., and Schneider, T. (2009b).
Improved garbled circuit building blocks and appli-
PracticalApplicationsofHomomorphicEncryption
13

cations to auctions and computing minima. In Cryp-
tology and Network Security, volume 5888 of LNCS.
Springer Berlin / Heidelberg.
Malkhi, D., Nisan, N., Pinkas, B., and Sella, Y. (2004).
Fairplay - a secure two-party computation system.
In Proc. of the 13th conference on USENIX Security
Symposium - Volume 13, SSYM’04, Berkeley, CA,
USA. USENIX Association.
Naehrig, M., Lauter, K., and Vaikuntanathan, V. (2011).
Can homomorphic encryption be practical? In Proc.
of the 3rd ACM workshop on Cloud computing se-
curity workshop, CCSW ’11, New York, NY, USA.
ACM.
Pinkas, B. and Reinman, T. (2010). Oblivious ram revisited.
In Advances in Cryptology - CRYPTO 2010, volume
6223 of LNCS. Springer Berlin / Heidelberg.
Smart, N. and Vercauteren, F. (2010). Fully homomorphic
encryption with relatively small key and ciphertext
sizes. In Public Key Cryptography, PKC 2010, vol-
ume 6056 of LNCS. Springer Berlin / Heidelberg.
Stehl, D. and Steinfeld, R. (2010). Faster fully homo-
morphic encryption. In Advances in Cryptology -
ASIACRYPT 2010, volume 6477 of LNCS. Springer
Berlin / Heidelberg.
Trapnell, C. and Salzberg, S. (2009). How to map billions
of short reads onto genomes. Nature Biotechnology,
27(5).
Yao, A. C. (1982). Protocols for secure computations. In
SFCS '82: Proc. of the 23rd Annual Symposium on
Foundations of Computer Science. IEEE Computer
Society, Washington, DC, USA.
SECRYPT2012-InternationalConferenceonSecurityandCryptography
14
