
A New Enterprise Security Pattern: Secure Software as a
Service (SaaS)
Santiago Moral-García
1
, Santiago Moral-Rubio
2
, Eduardo B. Fernández
3
and Eduardo Fernández-Medina
4
1
Kybele Research Group, Dept. of Computer Languages & Systems II,
Rey Juan Carlos University, Madrid, Spain
2
Chief Information Security Officer, BBVA Group, Madrid, Spain
3
Secure Systems Research Group, Dept. of Comp. and Elect. Eng. and Comp. Science,
Florida Atlantic University, Boca Raton, FL, U.S.A.
4
GSyA Research Group, Dept. of Information Technologies and Systems,
University of Castilla-La Mancha, Ciudad Real, Spain
Abstract. In recent years, the hiring of Software as a Service (SaaS) from cloud
providers has become very popular. The advantages of using these services
seem to be many, but organizations need to know and handle a variety of
threats. Before using SaaS, organizations should check the security measures
offered by the service provider and the defense mechanisms included in their
enterprise security architectures. Security patterns are a good way to build and
test new security mechanisms, but they have some limitations related to their
usability. In order to improve the usability of security patterns, we have defined
a new type of security pattern called Enterprise Security Pattern. In this paper,
we show a brief description of enterprise security patterns, and document a new
pattern that the organizations could apply to protect their information assets
when using SaaS.
1 Introduction
The practice of outsourcing business functions has been around for decades. In recent
years, its realization as online software service has become very popular [1]. Online
software delivery is now conceived and defined as Software as a Service (SaaS). SaaS
focuses on separating the possession and ownership of software from its use [2]. The
advantages to using SaaS seem to be many, because this online service model may
prove cheaper than owning and maintaining an in-house IT system [3]. Companies
expect to save money on support and upgrade costs, IT infrastructure, IT personnel,
and implementation. However, this new environment has some threats that
organizations should handle, in order to protect their information assets.
Before using SaaS, organizations should check the security measures offered by
the service provider, and the defense mechanisms included in their enterprise security
architectures. Security patterns provide the guidelines to support the construction and
Moral-Garcia S., Moral-Rubio S., B. Fernández E. and Fernández-Medina E..
A New Enterprise Security Pattern: Secure Software as a Service (SaaS).
DOI: 10.5220/0004088500140026
In Proceedings of the 9th International Workshop on Security in Information Systems (WOSIS-2012), pages 14-26
ISBN: 978-989-8565-15-0
Copyright
c
2012 SCITEPRESS (Science and Technology Publications, Lda.)

evaluation of new security mechanisms [4]. The use of security patterns helps to
incorporate security principles when building secure systems [5]. However, they have
some limitations:
• They are small units of defense. They can only handle one (or a few) threats.
Considering the number of threats that can affect current information systems, a
security designer should tailor an extensive set of security patterns when building
secure systems.
• There are different versions of the same pattern for each architectural level. As the
building of secure systems need an extensive set of security patterns, this fact increases
the complexity when a security designer is trying to select a pattern.
• Several instantiations of a pattern may have common aspects but the designer has
to find them. This fact may cause unnecessary redundancies.
Because of these limitations, we have defined a new type of security pattern called
Enterprise Security Pattern. This new type of pattern tries to improve the usability of
security patterns by incorporating them in a more comprehensive pattern that can
handle more threats. In this paper, we document a new enterprise security pattern that
organizations could apply to protect their information assets when using SaaS.
Companies which have already hired SaaS could also consult this pattern, in order to
verify if they are correctly protecting their assets.
The remainder of this paper is organized as follows. Section 2 provides a brief
description of enterprise security patterns, including their assets, context and solutions
models. Section 3 documents a new enterprise security pattern called Secure Software
as a Service (SaaS). Finally, Section 4 presents some conclusions and future work.
2 Enterprise Security Patterns
An enterprise security pattern is described by four models describing generic enterprise
security architectures that provide some security properties for a set of information
assets in a specific context. These patterns combine in one cohesive pattern: (i) the
information assets to be protected, including their sensitivity level, (ii) the context in
which these assets are found, (iii) the threats associated with the assets, (iv) the security
policies, patterns, mechanisms and technologies used to stop these threats, and (v) the
stakeholders and systems involved in the solution. Here, we show the assets, context
and solution models used by these patterns.
2.1 Assets and Context Model
When building secure systems, organizations should use an information assets
classification, in order to facilitate the security designer’s work. The information assets
should be classified in groups, according to their sensitivity levels, which depend on
the relative value of the asset for the organization. This value may depend on several
aspects or factors. For this reason, when classifying assets, the organizations should
seek support from a risk analysis methodology.
The organizations’ information assets may be classified into three large groups:
15

data, applications, and code and configuration. A common characteristic for all
information assets is that they have to be stored in and may be transported through one
or more components in security realms.
A security realm can be defined as a logical and discrete entity that partitions the
enterprise network. The main purpose of these realms is to standardize enterprise
security in order to reduce cost, users’ delay, and administrative overhead of redundant
security procedures [6]. The main characteristic of security realms is that they have in
common the same security policies.
Policies are management instructions indicating a predetermined course of action,
or a way to handle a problem or situation [7]. Without policies it is impossible to build
secure systems, we don’t know what we should protect and how much effort we should
put on this protection [8]. A specific system uses a combination of security policies
according to its goals and environment. When building secure systems, designers have
to consider many security policies of different types, such as confidentiality policies,
integrity policies, availability policies, etc.
When classifying the security realms, we take into account the Types of Realms
(TR) that can be found in an enterprise network, and who manages each of those
realms, i.e., a Characteristic of the Realm (CR). The classification of Security Realms
(SR) that we propose here can be defined as SR: TR x CR. The specific realms can be
adjusted to fit different types of applications; what matters here is that we use a
classification of this type. Table 1 shows with an “X” the security realms provided in
our classification.
Table 1. Classification of security realm.
Characteristic of the Realm
Managed Externally Managed Public
Types of Realms
Customer X X X
Employee X X X
Technical User X X X
Development X X -
Data X X -
Bastion X X -
Transport X X X
The security level of the policies applied when protecting the confidentiality of an
asset can vary, depending on the security realm in which the asset is found, so its
integrity, availability, and auditability should be protected in all the realms. For these
reasons, we have defined a group of security policies that the enterprise security
patterns will use to define the sensitivity level of an information asset. To achieve this,
we have combined the answer of four dependent questions related to the following
security aspects: access authorization, encryption, and storage authorization. The four
questions are:
1. Can the information asset A be transported through the security realm SR?
2. If it is so, should A be encrypted?
16

3. Can A be stored in SR?
4. If it is so, should A be stored in hidden form?
Table 2 shows the possible answers, the security policies associated to each
combination, and a number that denotes the Security Level (SL) provided by each
policy (1 is the lowest and 6 the highest). SL will help us when designing the solutions
of the enterprise security patterns.
Table 2. Security policies of the sensitivity level.
Answers Combinations
SL Security Policies
1 2 3 4
4 Secure Channel (SC) & Hidden Storage (HS) Yes Yes Yes Yes
3 Secure Channel (SC) & Clear Storage (CS) Yes Yes Yes No
5 Secure Channel (SC) & Blocked Storage (BS) Yes Yes No -
- Clear Channel (CC) & Hidden Storage (HS) Yes No Yes Yes
1 Clear Channel (CC) & Clear Storage (CS) Yes No Yes No
2 Clear Channel (CC) & Blocked Storage (BS) Yes No No -
6 Blocked Channel (BC) No - - -
After removing the policy Clear Channel & Hidden Storage (CC & HS), shadowed
row, we obtain six different security policies. The policy CC & HS has been removed,
because it is not usual find a security policy in which the information assets require
encrypted storage and may be transported in clear way. When protecting the
information assets, enterprise security patterns may use additional security policies,
such as integrity policies, availability policies, auditability policies, etc.
Different organizations could apply different sensitivity levels to the same asset.
For example, when classifying the customers’ account, a food industry organization
could decide to apply security policies with low or medium security level in all its
security realms. However, a banking organization could decide to apply throughout
security policies with high or very high security level. Due to this, enterprise security
patterns do not try to protect single information assets. They intend to protect
information assets that have the same sensitivity level.
2.2 Solution Models
The four complementary models or viewpoints included in the solutions of enterprise
security patterns are: the Computationally Independent Model (CIM), the Platform
Independent Model (PIM), the Platform Specific Model (PSM), and the Product
Dependent Model (PDM). We discuss below each of them.
Computationally Independent Model: this model provides a description of the
security policies that the system should enforce, independently of its functional and
technological characteristics. The security policies should be applied to the information
assets and security realms.
17

Platform Independent Model: this model provides a conceptual description of the
security mechanisms that should be incorporated into the system and the relationships
that exist among them, independently of its technological characteristics and
implementation details. The same CIM could be instantiated N times in this model,
since a security policy may correspond to different security patterns. A good guideline
which can be used as a basis to select the security patterns needed is the guideline
developed by Schumacher et al. in [9] or Fernandez in [10].
Platform Specific Model: this model defines the architectural components included in
the enterprise security architecture, independently of the technology used to solve the
problem. The PSM should take into account how to place the security mechanisms
within the architecture. The same PIM can be instantiated N times in this model, since
a security mechanism may be placed in different architectural components. The
security patterns described in the PIM are included within architectural security
components. Two good guidelines which can be used as a basis to select the
architectural component are the ISO/IEC-27000-series [11] and the IT Baseline
Protection Manual [12].
Product Dependent Model: it is necessary to install the PSM in a specific
technological architecture in this model. The same PSM could be instantiated N
times, since the same architectural component may correspond to different
technological products. The technological products must be reliable products made by
known manufacturers in the security industry. The final solution may vary
significantly depending on the technologies used.
3 An Enterprise Security Pattern: Secure Software as a Service
We document here an enterprise security pattern which could be used by
organizations, in order to protect the information assets when using outsourced online
applications, for example, Google Apps for business. We discuss below each of
sections included in the pattern template. This template includes sections of the
template provided by Buschmann et al. [13], and some new sections that we consider
necessary when designing enterprise security architectures.
3.1 Intent
This pattern attempts to protect the confidentiality of the data included in the
outsourced online applications of an organization.
3.2 Context
Employees of an organization access from home (Public Employee realm, P-E)
outsourced online applications. The service provider has placed the applications in a
data center (Externally Managed Data realm, EM-D). Employees access the service
provider through Internet (Public Transport realm, P-T). The service provider has an
applications gateway (Externally Managed Bastion realm, EM-B) between Internet
18

and its d
a
In or
d
their org
a
p
rovider
Bastion
r
organiza
t
p
rovider.
Figure 1
s
The
s
p
attern a
t
E
x
Ext
e
As s
h
b
e store
d
could st
o
applicati
o
leave th
e
organiza
t
not relat
e
This
outsourc
e
level. Or
higher se
n
a
ta center.
d
er to allow
e
a
nization, wh
e
redirects the
r
ealm, M-B).
t
ion’s system
s
Once the em
p
s
hows the co
n
s
ensitivity le
v
t
tempts to pro
T
a
Security Real
m
x
ternally Manage
d
e
rnally Managed
Public Transp
o
Public Employ
M
anaged Bast
i
M
anaged Da
t
h
own in Tabl
e
d
in clear for
m
o
re the data i
n
o
ns. The rest
o
e
service pro
v
t
ion’s data ce
n
e
d to the outso
pattern shou
l
e
d online ap
p
ganizations s
h
n
sitivity leve
l
mployees co
n
e
n an employ
e
employee’s
b
In that mo
m
s
(
M
anaged
D
p
loyee has th
e
n
text diagram
o
Fig.
v
el (see Sect
i
t
ect are show
n
a
ble 3. Sensitiv
i
m
s
d
Data
Bastion
o
r
t
ee
i
on
a
3, the data i
n
m
b
y the empl
o
n
clea
r
form,
o
f realms sho
u
v
ider, but the
n
ter (M-Da) c
o
u
rced applica
t
l
d only
b
e u
s
p
lications to
s
h
ould ensure
l
s.
n
tinue using t
h
e
e tries to acc
e
b
rowser to t
h
m
ent, employ
e
D
ata realm,
M
e
ticket s/he
c
of this patter
n
1. Context dia
g
i
on 3) of th
e
n
in Table 3.
i
ty level of the
i
S
e
Secure Channe
l
Secure Channe
l
Secure Channe
l
Secure Chann
e
Secure Channe
l
Clear Channe
l
n
cluded in th
e
o
yee (P-E). T
h
but these d
a
u
ld store the
d
communicat
o
uld transpor
t
t
ions.
sed when th
e
s
tore informa
t
that no emp
l
h
e access cre
d
e
ss the online
a
h
e organizatio
n
e
es validate
t
M
-Da) to ge
t
an access his
/
n
.
g
ram.
e
information
i
nformation as
s
e
curity Policies
l
(SC) & Hidden
S
l
(SC) & Hidden
S
l
(SC) &
H
idden
S
e
l (SC) & Clear
S
l
(SC) & Hidden
S
l
(CC) & Clear S
t
e
outsourced
a
h
e organizati
o
a
ta are not re
l
d
ata in a hid
d
i
on channels
t
data in clea
r
e
organizatio
n
t
ion assets th
l
oyee stores
i
d
entials that t
h
a
pplications,
t
n
’s gateway
(
t
heir credenti
a
t
a ticket to
a
/
her online ap
p
assets (data
)
s
ets.
S
torage (HS)
S
torage (HS)
S
torage (HS)
t
orage (HS)
S
torage (BS)
t
orage (CS)
a
pplications s
h
o
n’s data cent
e
l
ated to the
o
en way. The
d
should be s
e
form, but the
s
n
’s employe
e
a
t meet this
s
i
nformation a
h
ey use in
t
he service
(Managed
i
als in the
a
ccess the
plications.
)
that this
SL
4
4
4
3
4
1
h
ould only
t
er (M-Da)
o
utsourced
d
ata could
e
cure. The
s
e data are
e
s use the
sensitivity
a
ssets with
19

3.3 Problem
In the past, mailbox and collaboration applications used by the organizations were
placed within the organization. Employees accessed them from their home through the
Internet. This context provoked a set of threats that the organizations had to handle.
Some threats related to the confidentiality of data in this environment are (threats
related to integrity and availability should also be handled):
• An attacker may read the accessed data by the employee via Internet. To prevent
this, the organizations need to ensure that the communications between the employee
and the data center are secure.
• An attacker may steal an employee’s identity and access his/her applications. To
prevent this, organizations need to ensure that the employee is who s/he claims to be.
• An attacker may take advantage of a vulnerability to access an employee’s
applications. To prevent this, organizations need to patch constantly the applications
and the servers where the applications are hosted.
• A technical user who performs application maintenance may leak information. To
prevent this, organizations need to ensure that the data are stored in a hidden way.
Once the cloud computing paradigm was born, the context for accessing the
organizations’ applications has changed significantly. In addition, some companies
have as main objective providing and maintaining online applications of other
organizations. The threats that the organizations have to handle in these contexts are
similar to those of the context in which the employees accessed the organization’s
systems (listed previously), but how to handle them is different.
3.4 Known Incidents
Daily, there are many incidents of identity thefts. The main objective of these thefts is
to obtain relevant information from the person (or company) attacked or steal his/her
(or its) identity. One of the most notorious incidents was the case when hackers stole
the access credentials of Fox News’ Twitter account, and then they published that
President Barack Obama was dead [14].
All companies are exposed to this type of theft. By using the pattern that we are
describing here, companies could prevent that hackers can access the employees’
online applications, even if they steal their identity. This is because the solution
provided by the pattern ensures that the employee is who s/he claims to be (more
detail in the next section).
3.5 Solution
We discuss below each of the models included in the solution:
Computationally Independent Model: we need to apply here the security policies
included in the sensitivity level of the information assets. As shown in the diagram of
the CIM (Figure 2), we could prevent that an attacker may intercept the applications’
data, encrypting the channels and storing the data in a hidden way.
20

Platfor
m
security
p
Security
L
describe
d
unauthor
i
denoted
a
are: clea
r
channels
type of
m
line), an
d
We d
i
1) The e
applicati
o
2) The
s
b
rowser
t
employe
e
3) The
e
systems
(
4) The
(
I
dentific
5) The
(
A
uthent
i
to access
6) The
(Authent
i
to access
7) The
p
rovider’
signed ti
c
8) If the
9) The
a
(
H
idden
S
10) Befo
r
m
Independe
n
p
atterns. All s
L
ogger/Audit
o
d
yet. The s
i
zed can read
a
s P_1, P_2,
e
r
channel (si
n
show a logic
a
m
essages that
d
record mess
a
Fig
.
i
scuss below
t
mployee req
u
o
ns (Secure
C
s
ervice provi
d
t
o the organi
z
e
.
e
mployee’s b
r
(
Secure Chan
n
employee p
r
ation_2).
organization
i
cation). If th
e
his/her onlin
e
organization
i
cation). If th
e
his/her onlin
e
organization’
s
s systems, i
n
c
ket is the sa
m
access ticket
a
p
plications
m
S
torage).
r
e showing t
h
n
t Model: w
e
e
curity patter
n
or
described
ecurity patte
r
the informati
e
tc. The type
s
n
gle line), an
d
a
l representat
i
could be tra
n
a
ge (dashed li
n
.
2. Computati
o
t
he sequence
o
u
ests a secure
C
hannel_1).
d
er checks t
h
z
ation’s syste
m
r
owser reque
s
n
el_2).
r
ovides his/
h
checks tha
t
e
validation is
e
applications
checks tha
t
e
validation is
e
applications
s
systems r
e
cluding the s
i
m
e that the tic
k
is valid, the e
m
m
ust make cle
a
h
e online ap
p
e
realize here
n
s included i
n
in [15] and
H
r
n
H
idden
S
i
on stored. In
s
s
of channels
d
secure cha
n
i
on of the typ
e
n
sported are:
n
e).
o
nally indepen
d
o
f actions sho
w
channel thro
u
h
e employee’
m
s, includin
g
s
ts a secure
c
h
er credenti
a
t
the empl
o
successful, t
h
.
t
the empl
o
s
successful, t
h
.
e
direc
t
the
e
igned access
k
et generated
e
mployee cou
l
a
r the data so
t
p
lications to
the security
n
the PIM are
H
idden Stora
g
S
torage shou
l
s
tantiations o
f
that we may
n
nel (double
l
e
of message
request or r
e
d
ent model dia
g
w
n in the PI
M
u
gh a browser
s
organizatio
n
an access ti
c
c
hannel to ac
a
ls in the
o
o
yee is wh
o
h
e employee
o
o
yee is wh
o
h
e employee
o
mployee’s b
r
ticket.
A
cces
s
previously.
l
d access his/
h
t
hat they can
b
the employe
e
p
olicies of t
h
described in
[
g
e which has
d ensure th
a
f
the same pa
t
find within o
l
ine). In addi
t
that they tran
e
sponse mess
a
g
ram.
M
diagram (Fi
g
to access his/
n
and redire
c
c
ke
t
associate
d
c
ess the org
a
o
rganization’
s
o
s/he clai
m
o
btains the si
g
o
s/he clai
m
o
btains the si
g
r
owser to t
h
s
Control ch
e
h
er applicatio
n
b
e shown the
e
, the servic
e
h
e CIM as
[
9], except
s
not been
a
t nobody
t
tern P are
o
f the PIM
t
ion,
t
hese
n
sport. The
age (solid
g
ure 3):
/
her online
c
ts his/her
d
with the
a
nization’s
s
systems
m
s to be
g
ned ticket
m
s to be
g
ned ticket
h
e service
e
cks if the
n
s.
employee
e
provider
21
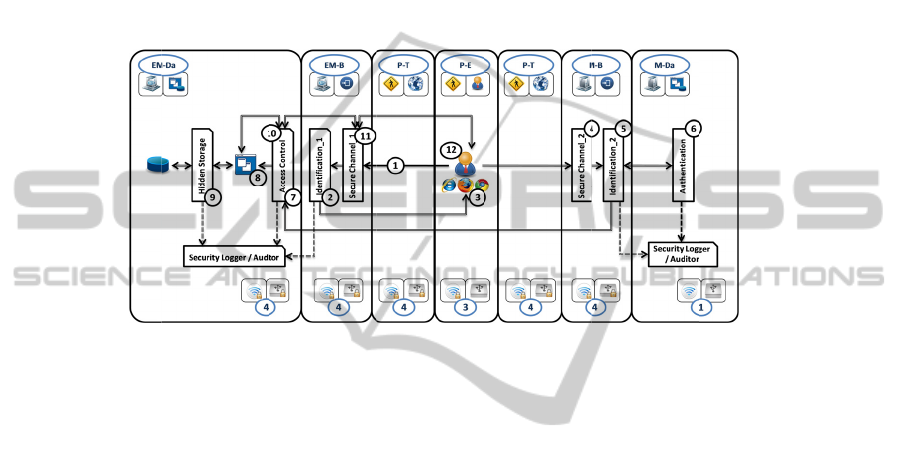
rechecks
(
A
ccess
C
11) The
s
Secure
C
12) The s
p
oint, th
e
In order
access c
o
Security
L
Platfor
m
architect
u
p
attern i
n
Web Ser
v
are tran
s
Logger/
A
A
ccess
C
Finally, t
h
transfor
m
In or
d
stealing
h
To do t
h
(somethi
n
include
widespre
a
of strong
Product
into tec
h
technolo
g
selected
t
b
y many
that the em
p
C
ontrol).
s
ervice provi
d
C
hannel.
ervice provid
e
e
employee c
o
to audit pos
s
o
ntrol, and hi
d
L
ogger/Audit
o
m
Specific M
o
u
ral compone
n
n
stantiations
S
v
e
r
. The secu
r
s
formed in
a
A
udito
r
is tra
n
C
ontrol and
t
h
e security p
a
m
ed into a Dis
s
d
er to preven
t
h
is/her identit
y
h
is, an auth
e
n
g stronger th
a
T
oken-Based
a
d, but we c
o
authenticatio
n
Dependent
M
h
nological p
r
g
ical product
s
t
hese technol
o
organization
s
p
loyee has p
e
d
er shows th
e
e
r stores a se
s
o
uld access hi
s
ible attacks,
t
d
den storage
or
.
Fig. 3. Platfor
m
o
del: we tra
n
n
ts. As show
n
S
ecure Chan
n
r
ity pat
t
ern in
s
Reverse Pr
o
n
sformed in
a
t
he applicati
o
a
ttern instanti
a
s
ociation Dat
a
t
that an atta
c
y
; we need to
e
ntication sy
s
a
n passwords
)
Authenticati
o
uld also have
n
.
M
odel: we tr
a
r
oducts. The
s
that we ha
v
o
gies, becaus
s
; but we coul
d
e
rmissions to
e
employee
h
s
sion cookie i
s
/her online a
p
t
he mechanis
m
should recor
d
m
independent
n
sform here t
h
n
in the diagra
m
n
el_1 and
I
d
e
s
tantiations S
e
r
oxy. The se
c
a
Log Syste
m
o
ns are trans
f
a
tion
H
idden
S
a
Serve
r
.
c
ker may acc
e
ensure that t
h
stem with h
i
)
. In the solut
i
o
n Serve
r
,
b
e
used biomet
r
a
nsform here
t
diagram of
v
e decided t
o
e we consid
e
d
have select
e
access thos
e
h
is/her online
n the employ
e
p
plications w
i
m
s for identi
f
d
all activity
model diagra
m
h
e security p
a
m
of the PS
M
e
ntification_1
e
cure Channe
l
c
urity patter
n
m
. The secur
i
f
ormed into
a
S
torage and t
h
e
ss an emplo
y
h
e employee i
s
i
gh security
i
on of the pat
t
b
ecause its
u
r
ic authentica
t
t
he architectu
r
the PDM
(
o
include in
e
r them reput
a
e
d another set
e
data and a
p
applications
e
e’s browser.
i
thout re-auth
e
f
ication, auth
e
in the securi
ty
.
a
tterns of the
M
(Figure 4), t
h
are transfor
m
l
_2 and
I
dent
if
n
instantiatio
n
ty pattern in
s
a
n
A
pplicati
o
h
e application
s
y
ee’s applicat
i
s
who s/he cl
a
level shoul
d
ern, we have
d
u
se is curre
n
t
ion or some
o
r
al security c
o
Figure 5), s
the solution.
a
ble and curr
e
of technologi
p
plications
through a
From this
e
nticate.
e
ntication,
t
y patterns
PIM into
h
e security
m
ed into a
if
ication_2
n
Security
stantiation
o
n Serve
r
.
s’ data are
t
ions, after
a
ims to be.
d
be used
decided to
n
tly more
other kind
o
mponents
s
hows the
We have
e
ntly used
i
es.
22

3.6 C
o
The con
s
PDM of
t
shows th
e
We c
a
of the en
t
p
art of t
h
has to
w
increase
increase;
impleme
n
o
nsiderations
s
iderations of
t
he solution.
A
e
result of the
a
n see in Tab
l
t
erprise secur
i
h
e IT infrastr
u
w
ork in some
of personnel
even it
c
n
tation, and
m
Fig. 4. Platf
o
Fig. 5. Prod
u
the pattern t
a
A
nother set o
f
analysis for e
a
e 4 that, whe
n
i
ty architectur
e
u
cture would
b
cases outsid
e
in the secur
i
c
ould decre
a
m
aintenance
a
o
rm specific m
o
u
ct dependent
m
ake into acc
o
f technologie
s
ach of the rel
e
n
deploying t
h
e
does not in
c
b
e outsource
d
e
the organi
z
i
ty and log t
a
se
b
ecause
a
re outsource
d
o
del diagram.
m
odel diagram.
o
un
t
the selec
s
could chan
g
e
vant aspects.
h
e solution, th
e
c
rease; even it
d
. The securit
y
z
ation. This
f
eam. The in
s
IT infrastr
u
d
. Once the s
t
ed technolo
g
g
e this analysi
e
performanc
e
could decrea
s
y
and log ad
m
fa
ct may mea
n
s
tallation cos
t
u
cture, IT
p
o
lution is de
p
g
ies in the
i
s. Table 4
e
overhead
s
e because
m
inistrator
a
n a small
t
does not
personnel,
p
loyed the
23
residual risk is minimal. This means that the solution does not need complementary
measures to attain its initial objective.
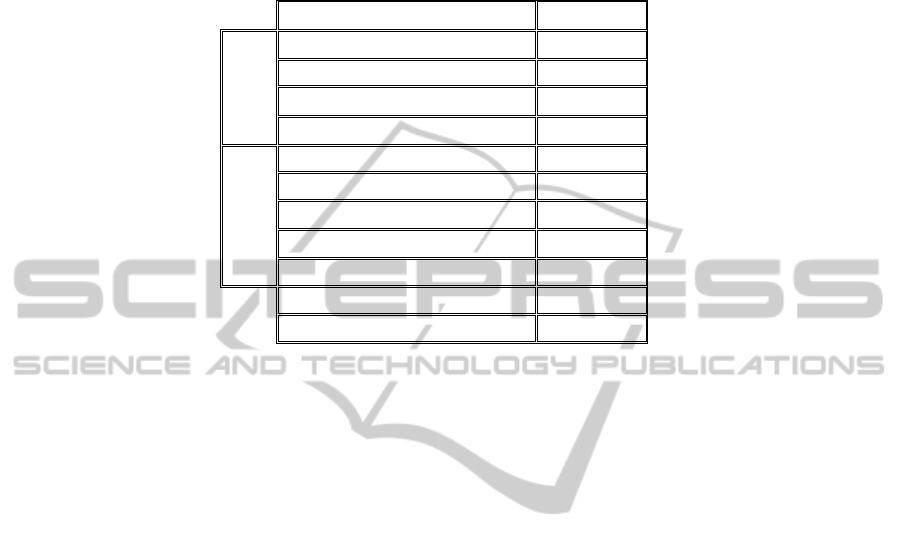
Table 4. Considerations.
Aspects to consider Analysis
Performance
overhead
Storage 0
Primary Memory 0
Processor 0
Bandwidth 0
Complexity
Security Administrator 1
Log Administrator 1
End User 0
Massive Expansion 0
System Administrator 0
Installation Cost 0
Residual Risk 0
3.7 Consequences
As we said previously, threats found in the problem are related to the confidentiality of
the assets. Integrity and availability threats could be handled in similar ways. We
discuss below the security mechanisms that we have included in the pattern, in order to
prevent or reduce the risk of the identified threats:
• An attacker may read the data accessed by the employee via Internet. The service
provider’s Web Server and the organization’s Reverse Proxy using secure channels can
prevent this.
• An attacker may access an employee’s applications, after stealing his/her identity.
To prevent this, we include a Token-based Authentication Server.
• An attacker may use a vulnerability to access an employee’s applications. To
prevent this, the service provider has to constantly patch the applications and the
servers where the applications are hosted.
• A technical user who performs the applications maintenance may leak information.
To prevent this, we include a Dissociation Data Server in the service provider.
This pattern would also be applicable in a context where the employees access their
online applications from the organization (Managed Employee realm, M-E), rather
than from their home.
3.8 Known Uses
As shown previously, Google is one of the online applications’ providers that offer the
security measures and architecture included in the pattern’s solution. One of their most
24

popular products is Google Apps. Forty million active users and four million of
businesses are currently using it [16], including Florida Atlantic University and BBVA
Group.
4 Conclusions and Future Work
Using Software as a Service (SaaS) has currently become very popular. This popularity
is caused because companies could save money on support and upgrade costs, IT
infrastructure, IT personnel, implementation, and maintenance. However, before using
SaaS, organizations should check the security measures offered by the service
provider.
Security patterns are a good way to construct and evaluate new security
mechanisms, but they are not applied as much as they could be, because designers have
problems in selecting them and applying them in the right places. Enterprise security
patterns could improve the application of the patterns by incorporating them in a more
comprehensive pattern that may handle more threats. There will be a smaller number
enterprise security patterns, which makes their selection simpler for designers.
When adopting SaaS, organizations could consult the enterprise security pattern
that we have presented here, in order to protect the data included in the outsourced
applications from a common set of threats. Organizations which have already adopted
SaaS could also consult this pattern in order to verify if they are correctly protecting
their information assets. As future work, we will intend to document more enterprise
security patterns which can be consulted by organizations when using Platform as a
Service (PaaS) or Infrastructure as a Service (IaaS).
Acknowledgements
This research has been hosted at Florida Atlantic University (FAU) and carried out in
the framework of the following projects: MASAI (TIN2011-22618) financed by the
Spanish Ministry of Education and Science, BUSINESS (PET2008-0136) financed by
the Ministry of Science and Innovation, and SISTEMAS (PII2I09-0150-3135) and
SERENIDAD (PEII11-0327-7035), all financed by the Local Government of Castilla-
La Mancha, in Spain.
References
1. Espadas, J., Concha, D., Molina, A.: Application Development over Software-as-a-Service
platforms. In The Third International Conference on Software Engineering Advances
(2008).
2. Turner, M., Budgen, D., Brereton, P.: Turning Software into a Service. Computer, 36 (10),
pp. 38-44 (2003).
3. Ma, D.: The Business Model of Software-As-A-Service. In IEEE International Conference
on Services Computing (SCC 2007) (2007).
25

4. Fernandez, E., Washizaki, H., Yoshioka, N., Kubo, A., Fukazawa, Y.: Classifying Security
Patterns. In Progress in WWW Research and Development, pp. 342-347 (2008).
5. Hafiz, M., Adamczyk, P., Johnson, R. E.: Organizing Security Patterns. Software, IEEE,
pp. 52-60 (2007).
6. Arconati, N.: One Approach to Enterprise Security Architecture. SANS Institute(2002).
7. Wood, C. C.: Information Security Policies Made Easy. Version 7 (2000).
8. Fernandez, E. B., Gudes, E., Olivier, M.: Policies and Models. In The design of secure
systems (under contract with Addison-Wesley).
9. Schumacher, M., Fernandez-Buglioni, E., Hybertson, D., Buschmann, F., Sommerlad, P.:
Security Patterns: Integrating Security and Systems Engineering. Wiley (2006).
10. Fernandez, E. B.: Security patterns in practice: Building secure architectures using software
patterns. under contract with J. Wiley (To appear in the Wiley Series on Software Design
Patterns).
11. ISO: International Organization for Standarization. http://www.iso.org (retrieved: March,
2012).
12. BSI: IT Baseline Protection Manual. Federal Agency for Security in Information
Technology, Germany(2000).
13. Buschmann, F., Meunier, R., Rohnert, H., Sommerlad, P., Stal, M.: Pattern-oriented
software architecture: A system of patterns. Wiley, (1996).
14. GIZMODO: Fox News' Twitter Account Hacked. http://gizmodo.com/5817870/fox-news-
twitter-account-hacked-claims-barack-obama-is-dead (retrieved: March, 2012).
15. Fernandez, E. B., Mujica, S., Valenzuela, F.: Two security patterns: Least Privilege and
Security Logger/Auditor. In Asian PLoP (2011).
16. Google: Businesses share their stories - Google Apps. http://www.google.com/apps/intl/en/
customers/index.html (retrieved: March, 2012).
26
