
A Novel Beaconless Geographic Routing Protocol for Irregular
Wireless Sensor Networks
Jeongcheol Lee, Hosung Park, Seungmin Oh, Yongbin Yim and Sang-Ha Kim
Department of Computer Engineering, Chungnam National University, Daejeon, Republic of Korea
Keywords: Wireless Sensor Networks, Beaconless Routing, Geographic Routing.
Abstract: Many beaconless geographic routing protocols have been proposed in the wireless sensor networks, and
they could avoid the hidden problem by adopting restricted forwarding area, which is nested in the greedy
area and includes only mutually communicable nodes. However, these protocols are designed for uniform
sensor field, so they cannot be directly applied to practical irregular sensor fields with partial voids. If voids
or hotspots are in the restricted small area, these restricted region-based approaches would be failed to find a
forwarding node even if there exist appropriate candidates in the rest area. In this paper, we propose a
beaconless geographic routing protocol to increase forwarding opportunities for practical sensor networks.
By giving different contention priorities into the mutually communicable nodes and the rest nodes in the
greedy area, every neighbor node in the greedy area can be used for data forwarding without any packet
duplication.
1 INTRODUCTION
Geographic routing requires nodes to know positions
of their neighbors for forwarding data, so each node
periodically exchanges HELLO messages including
its position with its neighbors. To reduce the control
overhead due to these messages called beacons,
beaconless routing strategy has been studied in the
literature. Traditional beaconless routing
(Heissenbuttel, 2004); (Turau, 2005); (Fubler, 2003)
and (Sanchez, 2007) has the following process: a
sender broadcasts data to its neighbors, and only
neighbors in greedy forwarding area, closer
neighbors to a destination, are eligible to become as
next-hop forwarding candidates. Finally, only one
neighbor is selected as a next-hop forwarder by a
completely reactive method. To avoid collision
among these neighbors, the sender includes a
waiting function into the data packet which is related
to the distance between each receiving neighbor and
the destination. So, the fastest timer expiring node,
the closest node from the destination among the
neighbors, will become a next-hop forwarder by
itself and begin to send the received data by
broadcasting like the previous sender did. The rest of
neighbors overhear this message, so they could
cancel their own timer and release the received data.
However, some of neighbors in the greedy area
cannot hear the message of other neighbors because
any two nodes may be possibly out of radio range. It
might lead to a large number of packet duplications
in such overhearing-based beaconless routing
protocols due to multiple winners among these
neighbors. So, previous studies tries to adopt a
completely conservative approach, which reduces a
forwarding candidate area as a restricted region.
This approach limits the greedy forwarding area into
only mutually communicable nodes. It allows that
only the nodes in the restricted forwarding area,
which is nested in the greedy area, can be
participated in the timer-based forwarding
contention.
destination
FORWARDING
_QUERY
message from
D to sender
B
D
F
C
E
sender
A
Hidden-less area
Hidden area
DATA
BROADCAST
from A
Figure 1: Data forwarding in the proposed protocol.
237
Lee J., Park H., Oh S., Yim Y. and Kim S..
A Novel Beaconless Geographic Routing Protocol for Irregular Wireless Sensor Networks.
DOI: 10.5220/0004316002370240
In Proceedings of the 3rd International Conference on Pervasive Embedded Computing and Communication Systems (PECCS-2013), pages 237-240
ISBN: 978-989-8565-43-3
Copyright
c
2013 SCITEPRESS (Science and Technology Publications, Lda.)

This strategy is very simple and may be effective
in uniformly and densely deployed WSNs, but
forwarding opportunities can be loss in the practical
WSNs. In most of applications of WSNs, very small
and cheap sensor nodes are deployed to an interest
field by a plane in the air. Therefore, the network
commonly becomes an irregular shape that has lots
of partial network holes due to obstacles such as
buildings, lakes, or etc. If such holes are in the
restricted small forwarding area, it would be failed
to find a forwarding node even if there are
appropriate candidates in the rest area. In this case,
the sender has to send the data packet again or
change its routing mode from the greedy mode to the
recovery mode. Unfortunately, the neighbors cannot
be guaranteed to successfully receive data packet
again at the next time due to the error-prone nature
of wireless links. Also, if the routing mode is
changed, the protocol requires a number of control
messages and wastes lots of node energy because it
has to get the positions of all neighbors to detour the
holes.
Therefore, in order to both increase forwarding
opportunities and also prevent packet duplication
due to the hidden problem, we propose a novel
region-based beaconless routing protocol, which
gives different contention priorities into each region
in the sub-areas of the greedy forwarding area. In the
proposed protocol, nodes in high prioritized region
immediately find a next-hop forwarder in a fully
distributed manner after receiving a sender’s
broadcast data. On the other hand, nodes in low
prioritized region have to wait until contention of
high prioritized region is done. Namely, our protocol
has the two phase of contention process.
2 NETWORK MODEL
In the proposed protocol, the greedy forwarding area
is divided into two sub-areas: Hidden-less area and
the rest area, hidden area. The hidden-less area is
similar to the restricted forwarding area of the
previous protocols in the way that includes only
mutually communicable nodes. However, instead of
the previous protocols, the position of the hidden-
less area can be moved within the greedy forwarding
area by a learning mechanism. In order to switch the
hidden-less area with simple calculation, we choose
a 60’ radian area for the hidden-less area which is a
radial region that includes a 30’ radian area around
the line connecting the sender and the destination on
both sides. Except the hidden-less area, we call the
rest area as a hidden area. Note that all nodes in the
greedy forwarding area have been given data packet
from its previous sender at the same time, but their
relaying or answering times have to be different
from each other in order to prevent collisions. So,
we exploit the modified waiting function which is
based on both the distance from the destination
(closer node from the destination has lower timer)
and the priority value related to its geographic
position in the greedy forwarding area (higher
prioritized node has lower timer).
3 PROPOSED PROTOCOL
As shown in Fig. 1, a sender broadcasts its data to its
neighbors, so all nodes in the greedy forwarding area
can receive the sender’s data. The data packet
contains the original message, the position of the
sender and the destination, the maximum waiting
time, and the region information for the hidden-less
area. So, each neighbor in the greedy forwarding
area could realize whether it is in the hidden-less
area, or not. In this case, only the nodes A, B, C, D,
E, and F have been received the data successfully
among neighbors in the greedy forwarding area.
These nodes start to keep the received data into their
memories. Among these nodes, only both A and C
are in a high prioritized hidden-less area (fan-shaped
dashed region). After receiving the data, nodes in the
hidden-less area get higher priority than the hidden
area, and it immediately begins to find a next-hop
forwarder. These nodes have their own timer only
related to the distance from the destination by using
a predefined maximum time of T_max seconds. So,
in the hidden-less area, the closest node A from the
destination wake up first, becomes a next-hop
forwarder by itself, and broadcasts the received data
to its neighbors. Among all neighbors in the greedy
forwarding area, nodes that overhear this broadcast
data release its timer and received data. However, if
the node density is extremely high, this forwarding
message might be generated simultaneously among
neighbors because timers expire almost concurrently.
It might lead to lots of collisions, so the proposed
protocol exploits Distance and Angle based
Collision Avoiding Scheme, called DACAS.
On the other hand, nodes in the hidden area set
their own timer as a sum of distance-based value and
the T_max. Namely, every nodes in the hidden area
has to wait during T_max seconds first, it then
begins to start its distance-based timer. If the timer is
expired, the node in the hidden area sends a
FORWARDING_QUERY message to the sender. If
only there are no node that successfully rebroadcast
PECCS2013-InternationalConferenceonPervasiveandEmbeddedComputingandCommunicationSystems
238

the data in the hidden-less area, the sender replies
the FORWARDING_PERMIT message to the node
immediately. After that, the node becomes a next-
hop forwarding node, and broadcasts the received
data to its neighbors. Except the node, other
neighbors release their timers and received data
when they overhear the FORWARDING_PERMIT
message. In this figure, the node A in the hidden-less
area becomes a next-hop forwarding node by itself.
The other nodes B, C, and F that can overhear a
broadcast data from A, give up their contention
process for becoming the next-hop forwarder. Since
the node D and E are out of transmission range from
the A, they cannot overhear the broadcast data
message. When the timer of node D is expired, it
sends FORWARDING_QUERY messages to the
sender S. However, the sender S already overheard
the broadcast data from A, so the S ignores the
message from the node D. Also, the node E can
releases its timer when it overhears a
FORWARDING_QUERY message from the node D.
When a sender broadcasts its data to its neighbors,
neighbors which is closer to the destination than the
sender (in greedy forwarding area) set their own
timer as the following equation:
() () () (),
Wc fc f c f c
(1)
where W(c) represents the total waiting time (ms) for
the current node between 0 and T_max. The greedy
area of a sender which is closer to the destination
than the sender can be divided into multiple sector
areas. Each sector is made by using the
Maximum_Radio_Range (MRR) and the sector size
given by the application. The function f represent
the waiting time for each sector, and the f’ represents
the local waiting time for each node in a sector
according to its position in the sector. The f’’
represents the priority time delay. If the node c is in
the hidden-less area or out of the greedy area, the
function f’’ returns 0. Otherwise, it returns T_max.
For the function f, it uses the following equation:
max
() ,
M
RR
fc T
MRR
(2)
where dist(a,b) represents the Euclidean distance
between the position of the node a and b.
can be
presented as the following equation:
(, ) (, )
,
dist c d dist s d
(3)
where the values s, c, and d are the geographic
location of sending node that broadcasts data packet,
the current node that successfully receives the data
packet, and the destination node, respectively.
According to the sector size
, similarly located
sensor nodes have the same waiting time for the
sector. The function f’ can be presented as the
following equation:
max
() ,
fc T
M
RR
(4)
where the value
falls between 0 and 1 according
to the angle ratio of a sensor node in a sector area.
The lower
means the node is closer to the line
which is connecting the sender and the destination.
Namely, the closest node from the source-
destination line has the shortest timer in each sector
area. Also, every sensor node has another timer
called T_interval for the adoptive collision
avoidance. After a sender node broadcasts data
packet, if the node realizes a collision among its
neighbors by MAC device or receives two or more
packets from its neighbors within T_inverval, it
determines there might be a collision among
neighbors and rebroadcast data with increased
T_max.
4 PERFORMANCE EVALUATION
We implement the three schemes by Qualnet
Network Simulator 4.0 and utilize IEEE 802.15.4 as
the MAC protocol. The model of sensor nodes are
followed by the specification of MICA2. The
transmission range of sensor nodes is set to 50 m.
The simulation scenario is a 500 x 500 m
2
area in
which a varying number of nodes (from 200 to 900
nodes) are deployed. To make a fair comparison,
each protocol sets T_max as 300 ms. For the
proposed protocol, T_inverval is set to 10 ms. For
each scenario the results presented here are average
of 10 separate simulation runs.
4.1 Path Throughputs
Figure 2 (a) shows the distribution of throughputs of
the three protocols. In this simulation, 500 sensor
nodes are randomly deployed into the sensor fields.
Each curve shows the throughput CDF of the
geographic routes for the same randomly selected 50
node pairs. A point’s x value indicates throughputs
in packets per second. The size of a packet is 100
bytes. The y value indicates what fraction of pairs
has fewer throughputs.
The left two curves are the throughput CDF
ANovelBeaconlessGeographicRoutingProtocolforIrregularWirelessSensorNetworks
239
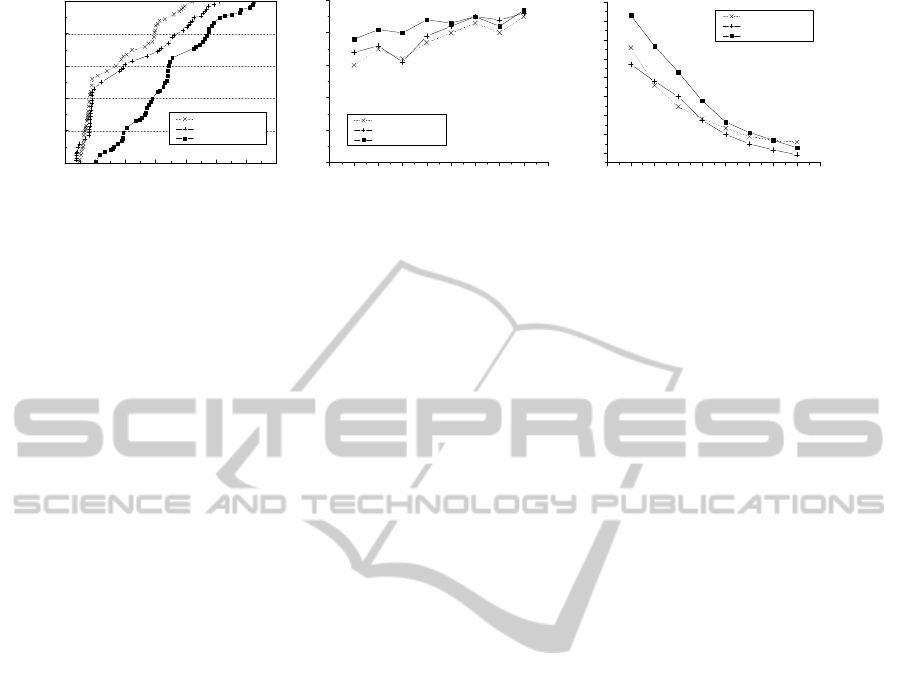
0 50 100 150 200 250 300 350
0.0
0.2
0.4
0.6
0.8
1.0
Cumulative Fraction of Node Pairs
Packets per Second Delivered
BLR
BGR
Proposed Protocol
100 200 300 400 500 600 700 800 900 1000
50
60
70
80
90
100
Packet Delivery Ratio (%)
Number of Sensor Nodes
BLR
BGR
Proposed Protocol
100 200 300 400 500 600 700 800 900 1000
200
300
400
500
600
700
800
900
1000
End-to-end Delay (ms)
Number of Sensor Nodes
BLR
BGR
Proposed Protocol
(a) (b) (c)
Figure 2: Simulation results in terms of (a) cumulative fraction of randomly selected 50 node pairs, (b) packet delivery ratio
according to node density, and (c) end-to-end delay according to node density.
achieved by using traditional beaconless routing
protocols, BLR and BGR. The right curve is the
throughput CDF achieved by the proposed protocol.
The proposed protocol provides almost three times
as much throughput as traditional beaconless routing
for the median pair. It is because that BLR and BGR
have more number of routing failures than our
protocol. In the traditional protocols, only a few
number of neighbor node could get a chance to be a
next forwarding node. Unfortunately, this routing
failure is related with the performance of the data
throughput because of unnecessary time-loss.
4.2 Impact of the Number of Sensor
Nodes
Fig. 2 (b) shows a packet delivery ratio (PDR)
among three different protocols. As the node density
increases, PDR of each protocol also increases. It is
because that each protocol has shorter path as
increasing node densities. Therefore we can find that
PDR is strongly related with the number of hops. In
general, the proposed protocol shows higher PDR
than other protocols. The reason is that our protocol
fully uses a forwarding candidate area like beacon-
based protocols; however other protocols use only
limited area that consists of mutually communicable
sensor nodes. These protocols can guarantee a
desired data throughputs by destination only when
the network has an enough sensor node.
Fig. 2 (c) shows the end-to-end delay for each
protocol. The graph shows that the density is
strongly correlated with the end-to-end delay.
Namely, the lower density shows a large amount of
end-to-end delay. In fact, routing in perimeter mode
is the main cause. In this simulation, a large part of
end-to-end delay is made by perimeter routing.
However, although the proposed protocol has
smaller perimeter packets than other protocols, we
observe that the proposed protocol has the more
delay than others with low densities.
5 CONCLUSIONS
This paper propose a novel beaconless geographic
routing protocol that can be used in irregular
wireless sensor networks, which could increases
forwarding opportunities by giving different
contention priorities into the mutually
communicable nodes and the rest nodes in the
greedy area. Our various experimental results show
that the proposed protocol has better performance
than the previous protocols.
REFERENCES
M. Heissenbuttel, T. Braun, T. Bernoulli, and M. Wachli,
BLR: Beacon-Less Routing Algorithm for Mobile Ad-
Hoc Networks, Elsevier’s Computer Communications
Journal (ECC), 27(11):1076–1086, July 2004.
M. W. V. Turau, BGR: Blind Geographic Routing for
Sensor Networks, in Proc. of the Third Workshop on
Intelligent Solutions in Embedded Systems (WISES),
Hamburg, Germany, May 2005.
H. Fußler, J. Widmer, M. Kasemann, M. Mauve, and H.
Hartenstein, Contention-Based Forwarding for Mobile
Ad Hoc Networks, Ad Hoc Networks, 1(4):351 – 369,
2003.
J. A. Sanchez, R. Marin-Perez, and P. M. Ruiz, BOSS:
beacon-less on demand strategy for geographic routing
in wireless sensor networks, in Proc. 4th IEEE Int.
Conf. on Mobile Ad-hoc and Sensor Systems (MASS),
Oct. 2007, pp. 1–10.
PECCS2013-InternationalConferenceonPervasiveandEmbeddedComputingandCommunicationSystems
240
