
Investigation of IT Sourcing, Relationship Management and
Contractual Governance Approaches
State of the Art Literature Review
Matthias Wißotzki, Felix Timm,
Jörn Wiebring and Hasan Koç
Institute of Computer Sciences, University of Rostock, Albert-Einstein-Str. 22, 18059, Rostock, Germany
Keywords: IT Sourcing, IT Outsourcing, Vendor Management, Relationship Management, Multisourcing, Contract
Management, EAM.
Abstract: The field of IT sourcing and its related management disciplines like supplier and contract management
increasingly gains attention from research around the world regarding to the development of research
activity. Influence factors as well as vital competences in relation to the IT sourcing success are
investigated. This analysis intends to give a transparent and comprehensive overview about recent research
topics like relationship management, reveals limitations and analyses new research phenomena like
multisourcing.
1 INTRODUCTION
Information technology (IT) sourcing is the
management discipline that defines the enterprise’s
procurement strategy of IT resources, capabilities
and functions. In short-term, enterprises want to
increase its IT capabilities in order to provide better
services for internal and external customers.
Extended to the long-term view, IT sourcing aims to
raise business value and enhance the enterprise’s
competitive edge.
Regarding to Deloitte’s Global Outsourcing and
Insourcing Survey from 2012 76% of the attended
companies outsource IT and this proportion seems to
rise to 81 percent. This development leads to the
fact, that IT outsourcing is a common practice in the
22 considered industries. The IT functions that can
be outsourced are assigned to three characteristics.
Firstly, systems planning and management processes
(IT governance or architecture) belong to IT
management functions. While secondly, outsourcing
application development and its maintenance is
primarily project-driven, thirdly, IT systems
operations, telecommunications and end-user
support have an operational character. (Herz et al.
2012a)
Next to IT outsourcing two different
categorizations can be distinguished in the
Procurement of IT processes: location-dependent
and location-independent terms. Location-dependent
strategies are defined by the distance, from where an
enterprise sources its IT. This dimensions ranges
from foreign IT vendors with long distance
(Offshoring) over foreign vendors with medial
distance (Nearshoring) up to domestic vendors
(Onshoring). (Bergqvist & Fredriksson 2008) In
contrast, the location-independent categorization is
characterized by the level of integration of the IT
vendor. Using IT Outsourcing the client enterprise is
contracting with an external IT vendor. IT
Insourcing is the integration of new IT capabilities
and human capital into the enterprise, while IT
backsourcing integrates IT processes back in-house
that were outsourced beforehand. (Bergqvist &
Fredriksson 2008)
This literature review intends to give
comprehensive insights into the state of affairs in IT
sourcing. After presenting the used research
approach in chapter 2, chapters 3 and 4 define used
research questions, explain the literature selection
process and present findings with the aim to give a
conclusion of results in chapter 5.
2 RESEARCH APPROACH
The research approach used by this paper is a
systematic analysis of published papers on the topic
of IT Sourcing, Supplier and Contract Management.
The used approach is transparent, repeatable and
280
Wißotzki M., Timm F., Wiebring J. and Koç H..
Investigation of IT Sourcing, Relationship Management and Contractual Governance Approaches - State of the Art Literature Review.
DOI: 10.5220/0004865502800287
In Proceedings of the 16th International Conference on Enterprise Information Systems (ICEIS-2014), pages 280-287
ISBN: 978-989-758-029-1
Copyright
c
2014 SCITEPRESS (Science and Technology Publications, Lda.)

provides a conclusive research review of the
presented topic.
By summarizing mature IT sourcing research
fields and analysing recent research trends, this
literature review tries to give advanced insights into
the state of research in the areas of IT (Out-)
Sourcing, Backsourcing, Offshoring, Relationship
Management and Sourcing Governance. Likewise
future research expectations and challenges will be
derived. Therefore a systematic literature review has
been conducted, based on the guidelines in
(Kitchenham et al., 2009). A preliminary literature
search has underscored a lack of literature work
regarding IT sourcing since the AMCIS submission
in (Willcocks, Lacity & Cullen 2007) in 2007.
Taking into account the vast recent occurrence of
new subfields in this topic, the need for a review
analysing the latest state of the art in IT sourcing
was recognized.
Considering the purposes of this work to be
transparent, conclusive and give a comprehensive
latest state of the art, the following research
questions had to deal with the topics of research
activity, research methods and statistics of the
selected literature.
1. How much activity in the field of IT Sourcing,
Supplier & Contract Management has there been
since 2005?
2. What research topics are being investigated?
3. What research methods are being used?
4. What IT Sourcing & Supplier Management
approaches can be distinguished?
3 REVIEW DESIGN
3.1 Literature Sources
After an initial search on several online databases
(Wiley Online Library, EconLit, IEEE and AISel), it
became obvious to populate papers published in
common conferences proceedings. Therefore a list
of potential conferences (AMCIS, CAiSE, ICIS,
ECIS, INCOM, PACIS) was compiled. With the
intention to work on conferences with highest
contribution to the paper’s purpose it was decided to
formulate several criterions, which were of critical
importance for the selection. According to these
criterions, the selected conference had to be
established, had to publish papers on a regular basis
these days in order to cover recent research topics
and trends, had to publish papers, which are written
by contributors of different nationalities and cultures
for avoiding bounded ways of thinking and has to
publish their papers in German or English papers
due to the authors’ language qualifications as well.
Moreover, the selected conference had to provide
their publications on databases which are freely
accessible with the possibilities given by the
University of Rostock. Furthermore these databases
had to allow the formulation of user-defined search-
strings and the published papers had to be freely
available.
Finally a group of conferences which fulfil all of
the given criterions has been identified. All of these
conferences reached a good result in a ranking of 58
conferences, proceedings and lecture notes, which
was published by the German journal
“Wirtschaftsinformatik” in 2008 (Wirtsch. Inform.
2008).
The proceedings of these conferences are
available via the database “AISeL”. With the
account of the University of Rostock it was
accessible and is capable of interpreting customized
search-strings. Furthermore these conferences
published a high amount of data on a regular basis in
the defined period of time.
3.2 Paper Selection
As mentioned above it was decided to cover the
years from 2005 to 2012 inclusive within this
research. This attribute of the search-string was used
in the initial search as well as in all further searches.
Because of the use of “AISeL” as the storage for all
papers of the selected conferences it was possible to
use the same search-string for all conferences.
The first search-string was used as well for an
exploration of the amount of data which was
published in the given period of time as for the
identification of relevant conferences. Therefore a
simple construct without any constraints or
specifications was chosen. The exact used string was
“IT Sourcing”. After overviewing the resulting huge
amount of data, the search-string was developed by
testing various terms and establishing synonyms.
Accordingly, the final search process resulted in the
following search-string:
(Sourcing OR Outsourcing OR Insourcing OR Backsourcing OR
Multisourcing) AND (“IT” OR “IS” OR “Information
Technology” OR “Information System”) AND (Supplier
Management OR Vendor Management) AND Contract AND
(Capabilities OR KPI OR "Key Performance Indicator" OR
Scope)
This string delivered a much smaller amount of
possibly relevant data, which was decided to be used
as the basis of further analysis.
After reading some of the selected paper an
InvestigationofITSourcing,RelationshipManagementandContractualGovernanceApproaches-StateoftheArt
LiteratureReview
281

existing room for improvement in the amount of
delivered results became clear. Thus, it was decided
to analyse the abstracts of all papers for certain
keywords, topics and criterions to exclude them
from our actual analysis. Papers which were
excluded from the analysis had to fulfil at least one
of the following criterions in their abstracts; a) not
focused on Information Technology Sourcing, b)
focused on Software as a Service field, c) focused on
Knowledge Process Outsourcing, d) focused on
Business Process Outsourcing, e) Contract
Management regarding employees in sourcing
projects, f) focused on Human Capital. After the
selection process, a total amount of 52 relevant
papers were provided the basis for this work.
3.3 Data Collection
In order to answer the identified research questions
data from the remaining relevant papers was
extracted. The collected meta-data comprises of
Title, Conference, Publication Year, Author(s),
Participating Institute, Country of Institute, Explicit
Topic, Research Method, Management Approach.
By analysing the collected data the next part of this
paper will deal with answering the prior defined
research questions.
4 DATA ANALYSIS
4.1 Activity in the Field IT Sourcing,
Supplier & Contract Management
(RQ1)
The research activity in 2012 (11 relevant papers)
increased about three times in comparison to 2005 (3
relevant papers). Furthermore, two significant peaks
can be identified. In 2007 especially the AMCIS
published noticeable amount of work regarding
relationship management and governance aspects in
the IT sourcing area. While the volume of
publication only remarkably changed in the AMCIS,
a present trend towards new research fields with
respect to IT sourcing seems to emerge, especially
seen in the development of ICIS publications
regarding the topic.
4.2 Research Topics (RQ2)
Although IT sourcing can be divided into several
types varying in terms of strategy and direction (see
Introduction), IT outsourcing definitely is the most
used basis for IT sourcing research. Three out of
four selected papers worked on this IT sourcing
type. This paper’s intention was either to investigate
in IT outsourcing or IT offshoring. The other fourth
of the papers considered IT insourcing (Reynolds &
Seddon 2010), backsourcing (Wong 2006) or
crowdsourcing (Nevo, Kotlarsky & Nevo 2012). It
can be said, that IT outsourcing is considered as the
most important type of IT sourcing because of its
commonness in practical use. In addition it seems
that most insights of IT sourcing can be transferred
to other sourcing types. Therefore, this section
summarizes research topics and investigated IT
sourcing competences referring to IT sourcing in
general.
While analysing the selected literature it
appeared that assessing both motivations for IT
sourcing and as a consequence thereof possible risks
belong to the oldest research disciplines. Reducing
costs, gain access to expertise knowledge or the
ability to focus on IT core competencies are still
counted as the main motivators for IT sourcing
projects. (Gröh, Gewald & Stuska 2012), (Li & Li
2009), (Herz et al. 2012b) Likewise the challenges
of detecting hidden transaction costs, hazardous
dependency on the vendor, intransparent project
performance or cultural discrepancies are not met
completely, too. (Gröh, Gewald & Stuska 2012),
(Gellrich and Gewald 2005) In terms of relationship
management the first and most exhaustively
investigated phenomena is the dyadic interaction
between a client and a vendor. (Herz et al. 2012a),
(Lee, Heng and Lee 2009) Therefore research also
built frameworks to differentiate between different
archetypes depending on the client’s strategic aim,
its expectations from the vendor and major
motivations. (Jahner, Böhmemann and Krcmar
2006) Initially, this research discipline focused on
the client’s perspective (Gröh, Gewald and Stuska
2012) and investigated the measurements that
mitigate potential project risks (Méndez, Mendoza
and Perez 2006), what IT capabilities to outsource
(Amber, Schroeder and Weiner 2005), (Willcocks,
Lacity and Cullen 2007) or what a client enterprise
should keep in-house (Willcocks, Lacity and Cullen
2007).
Starting with extended work from the client
perspective, clients can be clustered into different
types depending on their IT sourcing intention –
scaled by the dimensions cost, technology
improvement, business facilitation and innovation.
(Leimeister and Krcmar 2009) Furthermore, the
correlation between IT sourcing performance and
innovation processes on the client’s site seems to be
ICEIS2014-16thInternationalConferenceonEnterpriseInformationSystems
282

of current interest. (Yuanyue and Heng 2010),
(Oshry, Kotlarsky and Gerbasi 2011) Primarily in IT
sourcing projects with long distance vendors,
boundary spanning influences on IT sourcing
success are investigated. (Krishnan and Ranganathan
2008) Equally, (Gannon and Wilson 2007) identifies
vendor types in order to derive guidelines for vendor
strategies. Thus, research also considers the
perspective of the vendor recently. Likewise to the
client perspective, competences are identified
(Willcocks, Lacity and Cullen 2007) and how the
supplier becomes able to adapt frequent changes of
needs. (Plugge and Bowman 2008) An increasing
research field here is the global delivery model that
defines support for vendors by using an international
supplier network itself. (Su 2008), (Nöhren and
Heinzl 2012), (Ahuja, Sinclair and Sarker 2011)
The topic that gained most attention in the
selected literature since 2009 is multisourcing. This
phenomenon is registered in industry more and
more. Next to an extended benefit of cost reduction
and increasing expertise sources, primarily the
independency of clients towards single vendors and
better agility on the market motivate enterprises to
implement multisourcing in their sourcing strategies.
(Herz et al. 2012a) Consequently, this leads to an
individual and complex strategy development, more
governance expenditures as well as higher data
management costs for steering this plethora of
projects. (Herz et al. 2012b) Current research
categorizes multisourcing relationships into different
categories in order to assign various success factors.
While (Lee, Heng and Lee 2009) differentiate
between single-vendor and multi-vendor dominant
multisourcing relations, (Jin and Kotlarsky 2012)
additionally characterize them by depth (level of
investment in single relationship) and breadth
(number of vendors for IT function). (Herz et al.
2012a) identified differences in the vendor selection
process between multisourcing and single-sourcing.
Because of the effect of risk reduction in
multisourcing strategies, especially pricing aspects
are of greatest interest in contrast to the vendor’s
risk level in single IT sourcing relationships.
Investigated competences for multisourcing
relationships are implementing strong social ties
between acting parties, organizational capabilities
and an increased accountability integrated in
contracting processes. (Jin and Kotlarsky 2012)
Hence, the impact of organizational learning (Lee,
Heng and Lee 2009) and knowledge transfer
(Westner 2009) on multisourcing success is
measured in this regard. Next to the integration of
external knowledge between client and vendor
(Bugajska 2007), also knowledge transfer processes
are vital between the different vendors. (Schott
2011)
The next emerging phenomenon in IT sourcing is
relationship dynamics. Recently, literature studies
the influence of flexibility competences between
client and vendor (Karimi-Alaghehband and Rivard
2012) with the aim that contracting partners can take
advantage of changes in business circumstances.
(Jahner, Böhmann & Krcmar 2006) In this context
collaboration processes (Krishnan and Ranganathan
2008), (Schott 2011) and enhanced social
environments (Li and Li 2009) are investigated, e.g.
considering cultural influences. (Chen and Kishore
2007), (Heumann, Wiener and Remus 2012)
Although risks of IT sourcing are extensively
researched, new aspects in risk management arise.
Especially forecasting risks and an integrated
proactive risk framework are of great interest in
latest work. (Gröh, Gewald and Stuska 2012)
Furthermore research on vendor-oriented risk
management increase. (Thalmann, Bachlechner and
Maier 2012) Likewise technological risk aspects are
considered, primarily information confidentiality
and maintainability. (Ackermann et al. 2011)
The second identified management discipline in
the field of IT sourcing is contractual governance.
Different types of contracts were defined and most
included clauses were investigated, e.g. costs, length
or service level agreements. (Willcocks, Lacity and
Cullen 2007) In general two different approaches
can be distinguished regarding contracting: formal
and relational contracting. Formal Contracts define
legal bindings between client and vendor regarding
business obligations, accountabilities, penalties for
non-performance of one side and other business
obligations. (Chou, Hsu and Lee 2012), (Willcocks,
Lacity and Cullen 2007) Owing to a high amount of
possibilities in contract design, the coherence
between contract configuration, intended business
goals and the type of relationship is investigated.
(Oshry, Kotlarsky and Gerbasi 2011), (Cullen,
Seddon and Willcocks 2007) The quintessence of
formal contracting is to bilaterally retain a clear and
stable business arrangement. (Tan, Sia and Kuan
2006)
In most recent work it was clarified, that these
clear legal bindings do not positively influence IT
sourcing success but are indispensable for IT
sourcing projects. (Chou, Hsu and Lee 2012)
Therefore, relational governance is investigated as
an influencing factor on project success. It includes
the integration of inter-organizational coordination
and social norms into the defined legal bindings and
InvestigationofITSourcing,RelationshipManagementandContractualGovernanceApproaches-StateoftheArt
LiteratureReview
283

aims to bilateral encouragement of responsibilities
and commitments. (Chou, Hsu and Lee 2012) By
dint of social mechanisms contract flexibility and the
ability to adapt changed needs or resources of the
business partner are facilitated. (Chandrasekaran,
Tayeh and Nagoore 2007) Several publications state
relational governance as a positively influencing
factor if IT sourcing success. (Ren, Ngai and Cho
2008), (Chou, Hsu and Lee 2012) In this context the
phenomena trust, collaboration, information
transparency and authorities were studied. (Chen and
Kishore 2007), (Lioliou and Willcocks 2009)
Another identified research field in contractual
governance is the process of monitoring and steering
IT sourcing relationships. Therefore, (Urbach and
Würz 2011) propose a reference framework, which
monitors project indicators like performance, service
improvement and communication processes.
Besides, research tries to identify causes that trigger
the termination of contract from both sides (Heng,
Wenyu and Yuanyue 2009) and refer to supporting
software tools for monitoring support. (Fischer
2012)
Summarizing this section, the identified research
work tries to analyse coherences between potential
influence factors and IT sourcing success and
potential reactions of the client and vendor.
4.3 Research Approaches (RQ3)
In accordance with the analysis results, it is possible
to distinguish basically four different research
approaches that can be categorized into purely
scientific works as well as the works, which are
based on practical experiences. Occasionally there
are papers which use a mixture of these two
categories. The category of purely scientific work
contains the approaches of literature review and
theoretical work. Literature reviews are relatively
weak in proving a hypothesis, therefore they are
primarily used to distinguish different approaches of
a topic, identify existing definitions and illustrate the
current stage of work. Theoretical work whereas is
used as an approach to developing new hypotheses
on how to solve a problem as well. Based on
preceding literature reviews they concentrate the
existing stage of knowledge and derive new
hypotheses. Results of theoretical work can be
methodologies too. Theoretical Work is often not
further tested. The category of work which is based
on practical experiences contains surveys and case
studies. Surveys gather information by questioning
stakeholders of the specific topic of the research.
Out of this data theories which will be tested in
further research are developed and derived. A case
study is an empirical inquiry that investigates a
problem within its practical context. In a case study
for example a methodology is tested in a real life
situation. Case studies prove or disprove theories
which are derived from purely scientific work or
surveys. Literature reviews are the least used
research approach. Most of the analysed literature
reviews are specific to a certain topic, for example
the impact of IT outsourcing on innovation
(Yuanyue and Heng 2010), and lay the foundation of
future research on this topic. Therefore the work in
hand fits in the gap of almost periodic reviews of the
topic. The distribution of research approaches shows
that IT sourcing is of immense practical relevance,
because about 58% of the research was done using a
practical approach. Nevertheless there is a big
scientific basis, as the huge amount of theoretical
work indicates.
4.4 IT Sourcing & Supplier
Management Approaches (RQ4)
After the analysis of the relevant papers we
identified several approaches and governance
structures which are presented in this section. Most
of these approaches served as a direct basis for one
or more specific papers, whilst others were only
taken into account. Sometimes there was more than
one approach used in a paper, often serving as
component of a synthesis of this approaches. There
were also papers which didn’t use any existent
approach. Transaction Cost Economics (TCE) was
identified as the most often used approach. TCE is
basically the theory about the different cost factors
which are incurred when two or more business
partners make an economic exchange. Besides costs
which are caused by an extensive search for the right
business partner there are contractual costs which
are caused by creating and enforcing the terms of
business between the partners. TCE in IT Sourcing
is mostly used to determine whether to outsource or
to insource business-critical IT, but is used for
describing relationships and forms of contracting as
well. Besides this general usage trails of the use of
TCE in all distinguished research topics except
multisourcing were detected. This shows that TCE is
a very adaptable approach which can be transferred
to almost every given topic. Examples for papers
which used this approach: (Willcocks, Lacity and
Cullen 2007), (Yuanyue and Heng 2010), (Tebboune
2010), (Heng, Wenyu and Yuanyue 2009),
(Whitaker, Mithas and Krishnan 2005) The second
most often used approach is called Resource-Based
ICEIS2014-16thInternationalConferenceonEnterpriseInformationSystems
284
View/Theory (RBV/RBT). Using this approach in IT
sourcing often describes sourcing capabilities as
resources which are important success factors of IT
sourcing projects on provider site as well as on client
site. A part of these resources is used to maintain
good performance, whilst another part is used to
improve services and thereby creating competitive
advantages.(Wunnava et al. 2008) The major
amount of papers which use this approach is located
in the clusters of the topic “Success Factors” and
“Supplier and Relationship Management”. Examples
for papers which used this approach: (Willcocks,
Lacity and Cullen 2007), (Krishnan and
Ranganathan 2008), (Plugge and Bowman 2008),
(Wunnava et al. 2008), (Nöhren and Heinzl 2012)
Social Exchange Theory (SET) is the third most
often used approach. SET is the continuation of
Exchange Theory in a more social context since SET
defines exchange mostly as communication between
the market and actors. SET is also about the
exchange of resources between market actors. This
includes the exchange of resources in a network as
well as in a dyadic relationship, possibly making
SET a suitable approach for the topic of “Multi-
Sourcing” in the future. At the time SET is mostly
used to describe the nature of the relationship
between vendor and client and to make assumptions
about possible reactions of the business partner.
(Ahuja, Sinclair and Sarker 2011), (Heng, Wenyu
and Yuanyue 2009) Examples for papers which used
this approach: (Heng, Wenyu and Yuanyue 2009),
(Ahuja, Sinclair and Sarker 2011), (Ren, Ngai and
Cho 2008), (Chandrasekaran, Tayeh and Nagoore
2007), (Chen and Kishore 2007) Formal Contracts
(FCs) are not a consistent approach per se. This
cluster consists mostly of Service Level Agreements
(SLAs) which are alike to the ITIL framework.
Formal contracts strive after avoiding risks mostly
through the definition of goals or the implementation
of measures for incidents and problems. The
relationship between vendor and client is well
defined and measurable but allows almost no space
for innovation. Nevertheless FCs can’t be seen as the
opposite of Relational Contracts (RCs). RCs aim for
flexibility and collaboration through only loose
definitions of goals and a much broader room for
innovation. This is achieved for example in IT
sourcing joint ventures, which motivate the vendor
to improve their services in order to maximize its
profit shares. In practical context there often exists a
mixture between these approaches. In the topic of
“Multi-Sourcing” there was no use of RCs
distinguished. This might be because of the
enormous complexity which comes with the
management of several providers and requires
stricter defined relationships. Examples for papers
which used these approaches: (Gellings and
Wuellenweber 2006), (Jin and Kotlarsky 2012),
(Lee, Heng and Lee 2009), (Chou, Hsu and Lee
2012), (Chandrasekaran, Tayeh and Nagoore 2007).
Knowledge Integration and Knowledge Transfer
(KI/ KT) are not consistently defined. In general
literature KI is for example described as a series of
processes, which revolve around the transfer,
translation and transformation of knowledge. In the
context of Multi-Sourcing Knowledge Integration
can be seen as a process which deals with the
synthesis of specialized knowledge into situation-
specific knowledge to obtain an objective. Vendors
as well as clients are parts of this process. (Jin &
Kotlarsky 2012) Knowledge Transfer is described in
a 4-stage model which includes the transfer of basic
and advanced technical and practical knowledge,
learning and multiplying the knowledge. (Schott
2011) The use of this vendor-vendor-specific model
as a model in a client-multivendor-relationship is
imaginable. Examples for papers which use this
approach: (Jin and Kotlarsky 2012), (Lee, Heng and
Lee 2009), (Schott 2011), (Méndez, Mendoza and
Perez 2006)
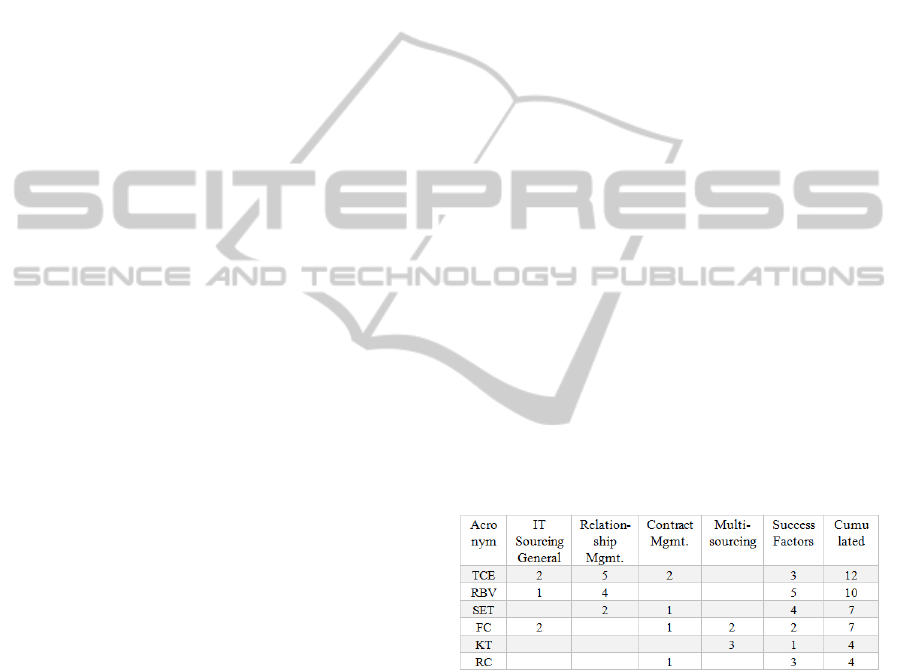
Table 1 shows the quantity in which the most
used approaches were used, mapped to the main
topics which were distinguished in RQ2.
Table 1: Quantity of Most Used Approaches – Topic
Specific and Cumulated.
The topics “Multisourcing” and “Contract
Management and Contractual Governance” use the
smallest amount of existent approaches since these
are at least investigated topics because of their
emerging importance in business. As an example,
multisourcing research starts from in 2009 (Lee,
Heng and Lee 2009), only a small amount of models
and frameworks has been developed so far.
5 CONCLUSIONS
With this paper a transparent, repeatable and
systematic literature review on the topic of IT
InvestigationofITSourcing,RelationshipManagementandContractualGovernanceApproaches-StateoftheArt
LiteratureReview
285

sourcing, relationship management and contractual
governance has been provided. The process of
literature and paper selection has been illustrated and
the four formulated research questions have been
answered as well. Furthermore several main topics
and management approaches have been described
more detailed. In accordance with the Kitchenham et
al.’s guidelines, the review was conducted based on
four conferences that published a high amount of
data on a regular basis in the defined period of time
and was available to the University of Rostock
network. Number of the relevant papers should rise
when taking other resources into account such
journals and books into account. This also would
require an extension of Kitchenham et al.’s
methodology. IT sourcing is a young discipline from
a scientific point of view. Although the concept of
outsourcing is used in practical environment for a
long time, research has only begun relatively
recently. Nevertheless there is already a certain
amount of topics which are investigated extensively,
as shown in RQ2. On the other side there is a
plethora of topics which are being investigated right
now and at least the same amount of topics, which
needs to be researched. This list of future topics is
partially already on the research agenda of some
authors or at least suggested as a topic of future
interest. Although the basics of IT sourcing are
already researched there is still a demand for the
standardization of IT sourcing-specific concepts and
terminology (Willcocks, Lacity and Cullen 2007).
As shown in RQ4 there is need for the development
of frameworks, theories and models which are
specific to a particular research field of IT sourcing
as well. It can be derived that generally used
management approaches like the ones described
above will serve as a basis for far more topic-
specific approaches.
The trend of multisourcing is mentioned by
many authors and will be of growing interest for the
next research periods. Specific topics are for
example experience-based research ((Herz et al.
2012b), (Chou, Hsu and Lee 2012)), governance
mechanisms ((Gröh, Gewald and Stuska 2012)) and
vendor-vendor-relationships ((Schott 2011), (Nevo,
Kotlarsky and Nevo 2012)). IT sourcing specific risk
management, especially vendor- and client-based
security management ((Thalmann, Bachlechner and
Maier 2012), (Ackermann et al. 2011)) will be of
interest as well. Furthermore there is a plethora of
further topics which will be more important in the
future as well, for example the influence of social
factors ((Li and Li 2009)), cloud computing ((Gröh,
Gewald and Stuska 2012)) and organizational
learning ((Willcocks, Lacity and Cullen 2007),
(Cunden 2008)) on the success of IT sourcing. It has
been discovered that the point of view of the vendor
in an IT sourcing project is typically less researched
than the point of view of the client. It can be
assumed that the vendors point of view will be an
interesting topic in future research.
REFERENCES
Ackermann, T., Miede, A., Buxmann, P., Steinmetz, R.:
Taxonomy of Technological IT Outsourcing Risks:
Support for Risk Identification and Quantification. In:
ECIS 2011 Proceedings.
Ahuja, Manju; Sinclair, Rob; and Sarker, Saone: The
Influence of Outsourcing Models on Vendor
Knowledge Integration. In: PACIS 2011 Proceedings.
Amber, A., Schroeder, M., Weiner, M.: Competence
Based IT Outsourcing - An Evaluation of Models for
Identifying and Analyzing Core Competences. In:
AMCIS 2005 Proceedings.
Barbara Kitchenham, O. Pearl Brereton, David Budgen,
Mark Turner, John Bailey and Stephen Linkman
(2009), “Systematic literature reviews in software
engineering – A systematic literature review”,
Information and Software Technology, Vol. 51 No. 1,
pp. 7–15.
Berkqvist, L., Fredriksson, O.: Outsourcing Terms: A
Literature Review from an ISD Perspective. In: ECIS
2008 Proceedings.
Bugajska, Malgorzata: Piloting Knowledge Transfer in
IT/IS Outsourcing Relationship Towards Sustainable
Knowledge Transfer Process. In: AMCIS 2007
Proceedings.
Chandrasekaran, R., Tayeh, A., Nagoore, V.:
Understanding Information System Outsourcing
Failure: Lessons of a Case Study. In: AMCIS 2007
Proceedings.
Chen, R., Kishore, R.: IT Offshore Outsourcing:
Contingency and Strategies. In: AMCIS 2007
Proceedings.
Chou, Tzu-Chuan; Hsu, Shu-Mei; and Lee, Gwo-Guang:
The Impacts of Network Governance on the
Performance of ITO: A Study of Taiwanese Firms. In:
PACIS 2012 Proceedings.
Cullen, S., Seddon, P., Willcocks, L.: IT Outsourcing
Configuration: Case Research Into Structural
Attributes and Consequences. In: ECIS 2007
Proceedings.
Cunden, M.: The Impact of the IT Outsourcing
Relationship on the Success of the Venture: A
Research Agenda. In: ECIS 2008 Proceedings.
Fischer, Thomas A.; Hirschheim, Rudy; and George,
Beena: Governance in Outsourcing Relationships –
The Role of Information Technologies. In: ICIS 2012
Proceedings.
Gannon, B., Wilson, D.: IS Offshoring: A Proposed
Maturity Model of Offshore IS Suppliers. In: ECIS
ICEIS2014-16thInternationalConferenceonEnterpriseInformationSystems
286

2007 Proceedings.
Gellings, C., Wuellenweber, K.: Successfully
implementing IT outsourcing strategy in German
Banks: the role of contract design and risk analysis. In:
ECIS 2006 Proceedings.
Gellrich, T., Gewald, H.: Sourcing, Risk and the Financial
Market. In: ECIS 2005 Proceedings.
Gröh, Andreas; Gewald, Heiko; and Stuska, Torsten: Next
Generation Outsourcing – A Research Agenda Guided
by Practice. In: PACIS 2012 Proceedings.
Heng, Cheng Suang; Wenyu, Du; and Yuanyue, Feng:
Investigating Vendors' Decision to Terminate IT
Outsourcing Contracts. In: ICIS 2009 Proceedings.
Herz, T., Hamel, F., Schoeni, M., Uebernickel, F.,
Brenner, W.: Comparing IT Supplier Selection Criteria
in Single-Versus Multi-Sourcing Constellations: An
Empirical Study. In: AMCIS 2012 Proceedings.
Herz, Thomas Ph.; Hamel, Florian; Uebernickel, Falk; and
Brenner, Walter: Global IT Multisourcing: Objectives,
Challenges and Requirements in Multinational
Insurance Companies. In: PACIS 2012 Proceedings.
Heumann, Jakob; Wiener, Martin; and Remus, Ulrich:
Power Distance in Information Systems Offshoring
Projects – A Control Theory Perspective. In: ICIS
2012 Proceedings.
Jahner, S., Böhmann, T., Krcmar, H.: Anticipating and
considering customers' flexibility demands in is
outsourcing relationships. In: ECIS 2006 Proceedings.
Jahner, S., Böhmann, T., Krcmar, H.: Relationship
Archetypes in Information Systems Outsourcing
Arrangements: An Exploratory Analysis. In: AMCIS
2006 Proceedings.
Jin, Xiaowei; and Kotlarsky, Julia: A Conceptual
Framework of Knowledge Integration in
Multisourcing Arrangements. In: ICIS 2012
Proceedings.
Karimi-Alaghehband, Forough; and Rivard, Suzanne:
Information Technology Outsourcing Success: A
Model of Dynamic, Operational, and Learning
Capabilities. In: ICIS 2012 Proceedings.
Krishnan, P.,Ranganathan, C.: Boundary Spanning
Capabilities in Offshored Information Systems
Development Projects: A Conceptual Framework. In:
AMCIS 2008 Proceedings.
Lee, Jae-Nam; Heng, Cheng Suang; and Lee, Jung: Multi-
Vendor Outsourcing: Relational Structures and
Organizational Learning From a Social Relation
Perspective. In: ICIS 2009 Proceedings.
Leimeister, S., Krcmar, H.: Identifying Different IS
Outsourcing Client Types. In: AMCIS 2009
Proceedings.
Li, Meng; and Li, Dong: A Survey and Analysis of the
Literature on Information Systems Outsourcing. In:
PACIS 2009 Proceedings.
Lioliou, Eleni; and Willcocks, Leslie: IT Outsourcing
Governance: Illuminating on the Interplay between
Contractual and Relational Governance. In: ICIS 2009
Proceedings.
Méndez, E., Mendoza, L., M., Perez: Critical Success
Factors as a Strategy for Risk Mitigation in IT
Outsourcing Projects. In: AMCIS 2006 Proceedings.
Nevo, Dorit; Kotlarsky, Julia; and Nevo, Saggi: New
Capabilities: Can IT Service Providers Leverage
Crowdsourcing? In: ICIS 2012 Proceedings.
Nöhren, M., Heinzl, A.: Relative Efficiency of IT
Outsourcing Global Delivery Models: A Resource-
Based Perspective. In: ECIS 2012 Proceedings.
Oshri, Ilan; Kotlarsky, Julia; and Gerbasi, Alexandra: Can
Client Firms Achieve Radical Innovation in IT
Outsourcing? In: ICIS 2011 Proceedings.
Plugge, A., Bowman, H.: Fit Between IT Outsourcing
Supplier Sourcing Capabilities and Organizational
Structure: A Conceptual Model. In: AMCIS 2008
Proceedings.
Ren, Jifan; Ngai, Wang-Ting; and Cho, Wing-Sing:
Contractual and Relational Governance of Software
Outsourcing Projects: A Proposed Research Model
and Research Agenda. In: PACIS 2008 Proceedings.
Reynolds, Peter; and Seddon, Peter B.: “Betting on the
House”: Value Creation by Insourcing at Crown
Limited. In: PACIS 2010 Proceedings.
Schott, Katharina: Vendor-Vendor Knowledge Transfer in
Global ISD Outsourcing Projects: Insights from a
German Case Study. In: PACIS 2011 Proceedings.
Su, Ning: Internationalization Strategies of IT Vendors
from Emerging Economies: The Case of China. In:
ICIS 2008 Proceedings.
Tan, Chengxun; Sia, Siew-Kein; and Kuan, Christine:
Flexibility Maneuvers in Outsourcing: An Empirical
Assessment. In: ICIS 2006 Proceedings.
Tebboune, Dr. Sofiane: A Theoretical Approach to
Netsourcing Research. In: AMCIS 2010 Proceedings.
Thalmann, Stefan; Bachlechner, Daniel; and Maier,
Ronald: Security Management in Cross-
Organizational Settings: A Design Science Approach.
In: ICIS 2012 Proceedings.
Urbach, N., Würz, T.: Designing a Reference Framework
of IT/IS Outsourcing Steering Processes. In: ECIS
2011 Proceedings.
Westner, Markus: Antecendents of succes in IS offshoring
projects - Proposal for an empirical research study. In:
ECIS 2009 Proceedings.
Whitaker, Jonathan; Mithas, Sunil; and Krishnan,
Mayuram: Antecedents of Onshore and Offshore
Business Process Outsourcing. In: ICIS 2005
Proceedings.
WI- Orientierungslisten, Wirtsch. Inform, vol. 50, no. 2,
pp. 155–163, 2008.
Willcocks, L., Lacity, M., Cullen, S.: Information
Technology Sourcing Research: Critique, Lessons and
Prospects. In: AMCIS 2007 Proceedings.
Wong, Siew Fan: Bringing IT Back Home: Developing
Capacity for Change. In: ICIS 2006 Proceedings.
Wunnava, S., Ellis, S., Kroll, M., Watkins, J.: IT
Outsourcing: Examined Under the Resource-Based
View Lens. In: AMCIS 2008 Proceedings.
Yuanyue, Feng; and Heng, Cheng Suang: Helping or
Hampering: Effects of IT Service Outsourcing on
Client’s Product Innovation. In: ICIS 2010
Proceedings.
InvestigationofITSourcing,RelationshipManagementandContractualGovernanceApproaches-StateoftheArt
LiteratureReview
287
