
A Risk Analysis Method for Selecting Service Providers
in P2P Service Overlay Networks
Rafael Giordano Vieira, Omir Correia Alves Junior and Adriano Fiorese
Dept. of Computer Science, Santa Catarina State University, Joinville, Brazil
Keywords:
Virtual Organization, P2P SON, Risk Analysis.
Abstract:
In an increasingly competitive market place, the development of collaborative networked environments has
become a key factor to companies successfully leverage their business activities. Nevertheless, when these
companies get involved in more volatile strategic networks, it is necessary to deal with additional risks that
need to be identified, measured, and mitigated through a well defined process. In this sense, this paper aims
to specify a method for risk analysis comprising a set of service providers (SPs) in a P2P Service Overlay
Network (SON). In this applied, qualitative and essentially exploratory work, the proposed method assesses
the level of risk present in a set of previously selected SPs using key performance indicators (KPIs), and
measures the viability of a Virtual Organization (VO) formation using those selected SPs. A computational
prototype was also specified and used to execute a set of tests to assess the proposed risk analysis method.
1 INTRODUCTION
Services are becoming a major source of revenue on
the Internet. Fundamental developments in network
technologies, particularly the advent of Peer-to-Peer
Service Overlay Networks (P2P SON) (Duan et al.,
2003; Fiorese et al., 2012), are providing an advan-
tageous environment for companies make their ser-
vices available to the global user community. The
joining of the SON and P2P fields offers a high po-
tential for handling services, by creating dynamic and
adaptive value chain networks across multiple Ser-
vice Providers (SPs). Moreover, a wide range of ser-
vices can be made available, as well as an environ-
ment where price and quality can be competitive dif-
ferentials (Zhou et al., 2005).
The P2P SON concept applies to a broad range
of network architectures. This paper deals particu-
larly with the Virtual Organization (VO) type of net-
work. A VO is a temporary and dynamic strategic
alliance of autonomous, heterogeneous and usually
geographically dispersed companies created to attend
very particular business opportunities (Mowshowitz,
1997; Camarinha-Matos and Afsarmanesh, 2008). In
this sense, the P2P SON acts as infrastructure that
provides an environment for VO formation and, addi-
tionally, enhances benefits to SPs, i.e. sharing costs,
bandwidth and others (Fiorese et al., 2010).
Although the mentioned advantages of using P2P
SON can improve the VO formation process, the nat-
ural VO networked structure faces additional risks
than other general forms of organization (Alawamleh
and Popplewell, 2010). For this reason, the service
provisioning is not guaranteed and needs the sup-
port of methods that encompass one or more crite-
ria, supporting a set of key performance indicators
(KPIs). These methods seem well suited especially
when dealing with complex service chain networks
(Junior and Rabelo, 2013).
In a previous work, the same authors designed a
three-layer architecture for services management in
P2P SONs, named OMAN (Fiorese et al., 2010). The
OMAN offers an efficient search and selection pro-
cess of most suitable SPs in a multi-provider envi-
ronment. Authors also presented results of SP selec-
tion by using a geographical location criteria (Fiorese
et al., 2012). However, the VO risk aspects in the con-
text of P2P SONs were not addressed.
This paper presents an exploratory work, which
complements the proposals of (Fiorese et al., 2012)
and (Junior and Rabelo, 2013), and looks for answer-
ing how SPs can be properly selected when consider-
ing risks. This work consists in adding an additional
risk management level in the search and selection pro-
cess, conceiving a new risk analysis method, named
MARTP (Multi criteria Risk Analysis Method applied
to P2P Service Overlay Networks). In the proposed
method, the SPs are two-stage evaluated, both indi-
477
Giordano Vieira R., Correia Alves Junior O. and Fiorese A..
A Risk Analysis Method for Selecting Service Providers in P2P Service Overlay Networks.
DOI: 10.5220/0004865804770488
In Proceedings of the 16th International Conference on Enterprise Information Systems (ICEIS-2014), pages 477-488
ISBN: 978-989-758-028-4
Copyright
c
2014 SCITEPRESS (Science and Technology Publications, Lda.)
vidually and collectively. The goal of the method is
to measure the level of risk and identify which SPs
are most risky for the VO formation. This will al-
low decision-makers to decide wisely about which
SPs should be effectively discarded for a given busi-
ness collaboration opportunity, and additionally, the
identified risks can be managed and hence mitigated
throughout the VO formation process.
The remainder of this paper is organized as fol-
lows: Section 2 addresses the problem of SPs search
and selection in P2P SONs and contextualizes it
within the VO risk analysis proposal. Section 3 de-
scribes the proposed method for VO risk analysis.
Section 4 provides a numerical example to illustrate
the proposed method. Section 5 presents the set of ex-
periments conducted to evaluate the proposed method
and also presents the final results. Finally, Section 6
concludes and discusses future directions.
2 BACKGROUND
2.1 Service Provider Integration
As cited in Section 1, different SPs can be grouped
in a given VO in order to accomplish a mutual goal,
also referred to as Collaboration Opportunity (CO).
These SPs might range from non-governmental orga-
nizations to autonomous software entities, by sharing
costs, benefits and risks, acting as they were one sin-
gle enterprise (Camarinha-Matos and Afsarmanesh,
2008). Regarding to the classical main phases of a VO
life cycle (creation, operation, evolution and disso-
lution phases) (Camarinha-Matos and Afsarmanesh,
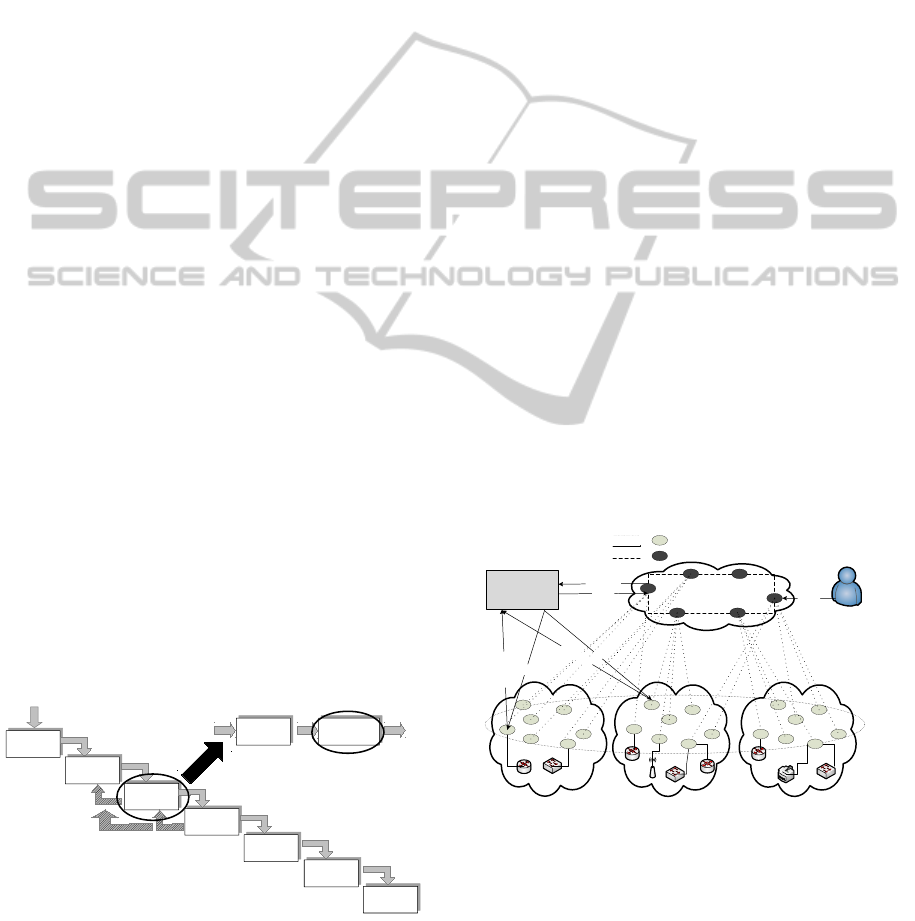
2005), this paper focuses on the creation (or forma-
tion) phase, which is seen in Figure 1. Within the
creation phase, this analysis is carried out during the
Partner’s Search and Selection step (left circle).
Rough VO
Planning
Rough VO
Planning
Detailed
VO Planning
Detailed
VO Planning
Negotiation
Negotiation
VO
Lauching
VO
Lauching
Contracting
Contracting
CO Identif. &
Characteriz.
CO Identif. &
Characteriz.
Collaboration
Opportunity
Partners
Search &
Selection
Preparatory
Planning
VO
Finalization
Consortia Formation
BPSS
BPSS
Risk Analysis
Risk Analysis
Figure 1: Framework for the VO Formation Process. Ex-
tended from (Camarinha-Matos and Afsarmanesh, 2005).
The process of collaboration among the SPs in
a VO is accomplished through interactions between
their business processes, which are usually supported
by a network infrastructure. Particularly, this work
addresses the use of P2P SON to organize all the SPs
committed with the eventual VO formation. A P2P
SON is an infrastructure designed to provide services
and, in the context of this work, it can be seen as a par-
ticular Virtual Breeding Environment (VBE) (Afsar-
manesh and Camarinha-Matos, 2005). It is also con-
sidered that the SP’s search and selection procedures
is performed by the OMAN (Fiorese et al., 2010) ser-
vice management architecture, with particular empha-
sis on its specific module (named BPSS), which is
responsible for performing the selection of the most
appropriate SPs in a P2P SON.
Figure 2 details the BPSS module. P2P SON,
shown as the elliptic curve, is created covering do-
mains (clouds in Figure 2) that contain SPs. Every
peer in the P2P SON runs service(s) from the corre-
sponding SPs. The AgS is created in a higher level in-
side the P2P SON, where each AgS peer maintains an
aggregation of services published by the SON peers
(providers at the P2P SON level). In order to se-
lect a SP (peer), the BPSS sends a service request to
the AgS, which forwards the request to the peers in
the aggregation overlay. In the context of this work,
this means the begin of a new Collaboration Oppor-
tunity (CO) that will trigger the formation of a new
VO (Camarinha-Matos and Afsarmanesh, 2005). The
result of this request is a list of all SPs that fulfill a
required service according a particular, or a set of ap-
plication metrics.
Domain CDomain BDomain A
Provider/User
Aggregation Service (AgS)
SON peer
Aggregation peer
Aggregation links
Physical links
Overlay links
Q
u
e
r
y
SON
Best Peer
Selection Service
(BPSS)
Q
u
e
r
y
S
e
l
e
c
t
B
P
B
P
L
i
s
t
o
f
B
P
S
e
l
e
c
t
B
P
B
P
Figure 2: BPSS Model (Fiorese et al., 2012).
2.2 VO Formation Risk Analysis
The problem in choosing the most appropriate SPs to
compose a VO is critical. The concept of risk can
be handled at a number of perspectives. (March and
Shapira, 1987) provide an overview of risk defini-
tion, as a variation in the distribution of possible out-
ICEIS2014-16thInternationalConferenceonEnterpriseInformationSystems
478

comes, their probabilities, and their subjective values.
(Moskowitz and Bunn, 1987) associate risk with the
likelihood of an unfavorable outcome. When applied
on this research context, the risk can then be viewed
as a composition of three basic elements: the gen-
eral environment where it can happens; its occurrence
probability; and the scope of its impact in the case of
its occurrence (Vose, 2008).
In the state of the art review, some works related
to risk analysis for VOs have been identified. In
(Alawamleh and Popplewell, 2012; Alawamleh and
Popplewell, 2010), thirteen KPIs were identified as
general risk sources in VOs, further identifying the
importance of each one. In (Grabowski and Roberts,
1998), the problem of risk mitigation in VO was dis-
cussed, and four processes were identified to improve
the level of VOs performance reliability. In (Li and
Liao, 2007) two sources of risks were specified (ex-
ternal and internal), and risk occurrence likelihood in
the life span of a VO was calculated based on them.
(Min et al., 2007) and (Fei and Zhixue, 2010) consid-
ered the fuzzy characteristics and the project organi-
zation mode of VOs to propose Multi Strategy Multi
Choice (MSMC) risk programming models.
In spite of these reviewed works and the insights
we have been taken from them, none have somehow
formalized how the proposed KPIs should be used nor
provided means to quantity VO partners risks before
the VO formation. Moreover, from the best of our
knowledge, it was not identified proposals that specify
a method or procedure that aims to systematize the
process of risk qualification/quantification involved in
the SP’s Search and Selection for the VO formation.
Therefore, this paper presents as a contribution a way
to specify KPIs together with a mathematic method
that enable measuring the risk in the VO formation.
In this sense, the VO formation process depicted
in Figure 1 was extended by proposing two sub-steps
in the Partner’s Search and Selection step. The first
sub-step comprises the BPSS model (as seen in Sec-
tion 2.1). It is used to provide an environment for SP’s
search and selection. Next, the second sub-step intro-
duces an additional process in order to embrace also
risk analysis (right circle in Figure 1). Thus, given
a VO in formation (composed by SPs), a set of ade-
quate performance indicators are firstly used and, ul-
timately the SP selection also considers the risk per-
spective.
The way the risk is represented should be aligned
with the organization’s goals so that the most im-
portant ones can be determined for further and more
proper management. Identifying risk sources is the
first and most important step in risk management
(Vose, 2008). Therefore, there are four main sources
of risks regarding VOs: trust, communication, col-
laboration and commitment (Alawamleh and Pop-
plewell, 2010). In this work they are modeled as KPIs
and their values are calculated and provided by the
methodology developed in (Junior and Rabelo, 2013):
• Trust: SPs who are going to compose a VO do
not necessarily have prior knowledge about each
other before starting collaborating. Thus, trust is
crucial to bear in mind, which in turn involves
commitment in doing the planned tasks. When
trust among providers is not enough established
there is a hesitation to share risks and so the VO
can be jeopardized;
• Communication: Communication among VO’s
SPs is a key factor for its proper operation. They
should provide correct information about parts,
products and services, collaborating in solving
conflicts, sharing practices, etc. However, this
can be complicated by the fact SPs are heteroge-
neous, independent, geographically dispersed and
usually have distinct working cultures. The insuf-
ficient communication can put a VO on risk;
• Collaboration: Collaboration is characterized
when the sharing of risks, costs and benefits of
doing business are agreed and fairly distributed
among partners. However, when a collaboration
agreement is not clearly defined, i.e., when there
is no clear definition of its main objectives, the
VO risk increases;
• Commitment: Commitment is related to the atti-
tude of VO members with each other, i.e., it con-
siders the contributions and agreements made by
and among them for a business. This is important
as partners have complementary skills and so it is
important they feed the whole environment with
the right and timely information. The VO risk gets
higher when partners fail in that attitude.
3 THE PROPOSED METHOD
This section aims at describing the proposed method,
named MARTP (Multi criteria Risk Analysis method
applied to P2P Service Overlay Networks).
3.1 MARTP Overview
The devised method for risk analysis is generally
presented in Figure 3. It starts having as input a
pre-selected and ranked list of most adequate SPs
(through BPSS simulation) registered in a P2P SON
environment. The main goal of the proposed risk
analysis method is to add another support dimension
ARiskAnalysisMethodforSelectingServiceProvidersinP2PServiceOverlayNetworks
479

for decision-making, identifying and measuring how
risky is each of those SP candidates involved in the
VO formation process. In this work, considering VO
reference theoretical foundations (Camarinha-Matos
and Afsarmanesh, 2008), the so-called VO Manager
is seen as the main decision-maker.
The method splits the problem into two stages. In
the first stage, it starts measuring the risks individu-
ally, for each possible SP, and after and based on that,
collectively, for the entire SP team for the given VO.
In this context, VO manager has the following role:
quantifies the level of risk (acceptable range) for VOs
before creating them. There is also a risk specialist,
who is in charge of auditing the SPs historical KPI
metrics. The risk techniques and criteria are applied
to assess the risk according to the VO manager guide-
lines.
VO Manager
Pre-selected
SPs (BPSS)
Risk Analysis Process
Individual Risk
Analysis
Collective Risk
Analysis
Level of
Risk
Risk
Techniques
and Criterias
Risk Analysis Flow
Interactivity between the user and the method
Risk
Specialist
Selection Process
Selection
Techniques
and Criterias
Figure 3: Overview of MARTP.
3.2 MARTP Architecture
The MARTP method itself is illustrated in Figure 4.
Inspired in (Mosleh et al., 2004), it divides the prob-
lem into two phases: the first phase does the indi-
vidual risk analysis applying the Event Tree Analy-
sis (ETA) method for that. The second phase does
the risk analysis taking the group of SPs as a whole
into account, applying the Fault Tree Analysis (FTA)
method (Ericson, 2005; Vose, 2008).
3.2.1 Individual Risk Analysis
In the first phase of MARTP, it is performed an indi-
vidual risk analysis for pre-selected SPs. ETA is par-
ticularly suitable for risk analysis of systems where
there are interactions between several types of proba-
bilistic events, whether dependent or independent (Er-
icson, 2005). It uses a visual representation based on
a logical binary tree structure, known as Event Tree
(ET), as shown in Stage 1 of Figure 4.
An ET is a probability tree, which provides two
possible conditions: success and failure. It also has
three basic components: initial event; intermediary
events; and outcomes. The initial event begins the ET
creation process. In this work, it corresponds to one
pre-selected SP, and the assigned probability (P
IE
) is
always 1 (or 100%) in the beginning (Ericson, 2005).
Next step consists in specifying the (four) intermedi-
ary events, which are represented by the (four) KPIs:
trust, communication, collaboration and commitment.
These events are used to quantify the effectiveness
of a particular SP, i.e., if it is able or not to compose a
VO, and to generate an ET by assigning success and
failure probabilities to each of them as shown in Stage
1 of Figure 4. The criterion to assign the KPI success
probability to each SP takes the historical values anal-
ysis of the KPI that were assigned to it in past VOs
participations (Pidduck, 2006; Goranson, 1999). This
analysis is fundamentally based on statistical infer-
ences by quantifying both the central trend and vari-
ability of historical values.
The central trend analysis is performed by cal-
culating an exponentially weighted average index
(EWA) for each set of historical KPI values of a
given SP. The EWA is currently used in financial risk
analysis and supply chain management being popular
in practice due to its simplicity, computational effi-
ciency and reasonable accuracy (giving more impor-
tance for the most recent values in an exponential fac-
tor) (Montgomery and Runger, 2011). The EWA is
formally defined by Equation 1:
¯
X =
∑
n
i=1
x
i
w
i
∑
n
i=1
w
i
(1)
where x =
{
x
1
,x
2
,...,x
n
}
means a non-empty set of
historical KPI values and w represents a normalized
exponential decay constant (note that this paper aims
to calculate a success probability by KPI historical
analysis; the determination of optimal values for cen-
tral trend analysis is not within its scope). After cal-
culating the EWA for each SP, the Maximum Qual-
ity Index (MQI) value is assigned as the higher value
among all EWA results. The MQI is used as a per-
formance reference (threshold) for all others SPs that
will be assessed. In this sense, considering i the num-
ber of used KPIs (four) and n the number of SPs as-
sociated for each KPI (three), Equation 2 shows the
MQI calculation procedure:
MQI
i
= max
i
(
¯
X
n
) (2)
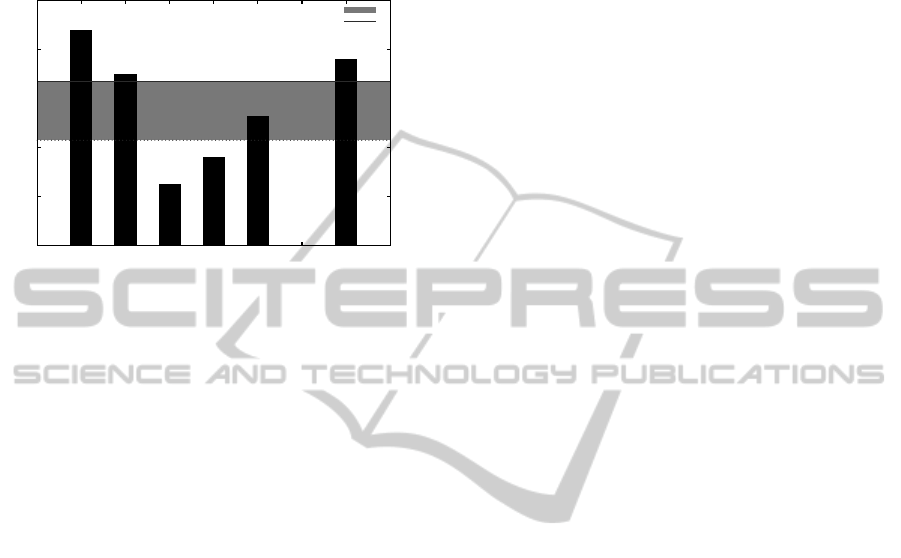
For instance, Figure 5 shows a graph with hy-
pothetical KPI values about trust (intermediate event
KPI
1
according to Stage 1 of Figure 4) associated to
a SP.
The value of the MQI (left circle in Figure 5) as-
signed for this KPI would have been set up as 6.7 (this
ICEIS2014-16thInternationalConferenceonEnterpriseInformationSystems
480

Figure 4: MARTP Architecture.
value is the highest EWA value calculated for SPs us-
ing the KPI trust). Nevertheless, it is obvious that,
when taking into account only the highest MQI value,
a few KPIs will reach an acceptable success probabil-
ity. For this reason, a variability metric is well-suited
in this scope. The metric used is the standard devia-
tion (SD) of MQI. Therefore, the acceptable interval
will range not only values above 6.7, but also includes
the SD interval, which are 2.4 (right circle in Figure
5). So, the acceptable range turn to 6.7 − 2.4 = 4.3.
The values assigned to each KPI can vary from
0 to 10 and are associated with a probability success
rate which varies from 0 to 1, respectively. Assum-
ing that each SP has participated in n
PA
past VOs and
since that n
R
represents the number of SP’s previous
participation in VOs where its KPIs values are higher
than MQI − SD (with an * in Figure 5), Equation 3
calculates the KPI success probability for the current
participation.
Pr (K) =
n
R
n
PA
(3)
The failure rate for a given KPI is represented as
Pr (
¯
K) by the following equation:
Pr (
¯
K) = 1 − Pr (K) (4)
According to Figure 4, the success and failure
probability rates are calculated for all KPIs that com-
pose the ET of a SP, which are presented by the
four intermediate (and independent from each other)
ARiskAnalysisMethodforSelectingServiceProvidersinP2PServiceOverlayNetworks
481
events KPI
1:4
that populate the ET. Event KPI
2
, for
instance, would be related to KPI communication,
with success and failure values of 0.90 and 0.10, re-
spectively.
0
2
4
6
8
10
VO
1
VO
2
VO
3
VO
4
VO
5
...
VO
n
KPI value
Previous participations in VOs
MQI = 6.7
SD = 2.4
Standard Deviation considered interval
8.8
7.0
2.5
3.6(*)
5.3(*)
7.6
Maximum Quality Index (MQI)
Figure 5: Trust KPI historical values for a given SP.
After assigning all probabilities for all ET
branches, it is necessary to identify if the SPs are min-
imally qualified to compose a VO. For this, a calcula-
tion is performed to obtain the final probabilities for
all event combinations composing the ET. They are
determined for each of the 2
|
K
|
branches of ET and
are got by multiplying the probabilities of events that
compose each path. The results greater than a Level
of Excellence (LE) are then selected to be part of the
Stage 2 of MARTP. LE is set by the VO manager and
corresponds to a minimum acceptable probability that
qualifies/enables a SP to compose a VO. The LE val-
ues can be classified as follows: [0.0; 0.2] : regret-
table; [0.2; 0.4] : bad; [0.4; 0.6] : regular; [0.6; 0.8] :
good; [0.8;1.0] : superior.
The presented concepts can be formalized as fol-
lows:
Let SP =
{
SP
1
,SP
2
,...,SP
n
}
be a set of n SPs
previously selected, where each element in this set
is associated with a different type of service activ-
ity that is being requested in a business. Let K =
{
K
1
,K
2
,...,K
m
}
be a set of m KPIs associated to a
SP
n
, and ρ(K) the probability function associated
with each event in K (as defined in Equation 3). ETA
events occur independently, i.e., where the occurrence
of an event does not affect the occurrence of other
event. This situation can be represented by the equal-
ities defined in Equation 5 and Equation 6:
ρ(K
m
|K
m−1
|...|K
1
) = ρ(K
m
) (5)
ρ(K
1
∩ ··· ∩ K
m
) = ρ(K
1
) · ρ (K
2
)···ρ(K
m
) (6)
Now consider P =
P
1
,P
2
,...,P
|
K
|
as a set of all
possible outcomes from the 2
|
K
|
ET events combina-
tions. The procedure for obtaining this set was per-
formed using a Binary Search Tree (BST) (Bentley,
1975), which travels 2
|
K
|
different paths and assigns a
value to each element of P, as shown in Equation 7:
P =
2
|
K
|
[
k=1
"
P
IE
∗
|
K
|
∏
l=1
ω(i, j,k, l)
#
(7)
where P
ie
is the initial probability of the SP. The func-
tion ω, as shown in Equation 8, corresponds to a 4-
dimensional vector which performs a binary search in
the tree, returning a path element from each iteration.
Values i and j correspond, respectively, to the begin-
ning and ending of the search, and have i = 0 and
j = 2
|
K
|
as initial values. The value k corresponds to
the index of the sought element (an element of P) and
l, the current level of the tree. The sequence of events
can be viewed in Stage 1 of Figure 4.
ω(i, j,k, l) =
Pr (K
l
); j = c, k ≤ c
1 − Pr (K
l
);i = c, k > c
(8)
where c = (i + j)/2. After defined all possible out-
puts P for a SP and calculated their probabilities, the
method applies a constraint variable Q, which checks,
for each element of P, whether its value is greater than
or equal to LE. Only the results that are greater than
LE are considered, and the other are discarded. Thus,
Q =
{
Q
1
,Q
2
,...,Q
n
}
is a subset of P:
Q =
{
q ∈ P | q ≥ LE
}
(9)
The final probability values obtained by Equation
9 will be used to measure and analyze the SP’s risk
collectively.
3.2.2 Collective Risk Analysis
The second phase of the MARTP method aggregates
the results provided by the first phase (i.e., the risk
level of each pre-selected SPs) to calculate the VO
success probability as a whole (if the VO formation
can succeed or not).
This phase applies FTA (Fault Tree Analysis)
method (Ericson, 2005). FTA uses a logical diagram
called Fault Tree (FT) - which is a graphical repre-
sentation of failure logical events that can occur in a
system among all other possible event combinations.
The graphical model can be translated into boolean
logic using logic gates to calculate failures. Events
are associated with input lines from the logic gates
ICEIS2014-16thInternationalConferenceonEnterpriseInformationSystems
482

(0-failure, 1-success) and must be analyzed to deter-
mine the logical connection between underlying fail-
ure events that might cause them. On the other hand,
FTA also performs probabilistic analysis for the un-
derlying failure events, by calculating the probability
of the top event (VO overall risk), given the FT and
the probability of occurrence of the basic events (risk
level of SPs) (Ericson, 2005).
This paper performs both qualitative risk analysis
(boolean values) and quantitative analysis (probabil-
ity associated to the boolean values). To make this
possible, first is considered that the risk level of each
SP is defined by a pair
h
R,S
i
. R represents a condi-
tion of the SP to compose a VO (using boolean logic),
while S represents the success probability of the SP
associated with the condition R. So SP
i
=
h
R
i
,S
i
i
for
the i-th selected SP and the i-th S associated with the
i-th R. The R value is calculated checking if the set
Q has some element (Equation 10), i.e., if there is at
least one outcome value greater than LE. A value 1
corresponds to the presence of elements, so enabling
the SP to compose a VO. The S value (Equation 11) is
calculated summing all elements of Q, obtaining the
success probability rate for a SP.
R
i
=
0 ,
|
Q
|
= 0
1 ,
|
Q
|
6= 0
(10)
S
i
=
|
Q
|
∑
i=1
q
i
, q
i
∈ Q (11)
In this sense, next step consists of taking all the re-
sults from ETA (first phase) and set them as the input
(see Figure 4) of the FTA method. A logic gate OR
with 2
|
K
|
entries is associated with each SP, meaning
that the number of logic gates OR changes according
to the number of SPs. In this case, the OR operation
among all inputs will result in a pair
h
R
i
,S
i
i
for each
SP.
Resulting values from logic gates OR are then ag-
gregated to an AND logic gate, which verifies if all
SPs are able to compose the VO. This gate returns
a pair
h
R
F
,S
F
i
where R
F
= 1 means success, i.e.,
the VO formation is considered feasible from the risk
analysis point of view, and R
F
= 0 means failure, i.e.,
VO is discarded and the procedure is restarted with
other SPs (with the other possible VO compositions).
If all members are considered able to, the VO as a
whole is considered able to go for operation. It is nec-
essary to mention that S
F
quantifies the value of R
F
,
i.e., even though the R
F
determines the criterion to
assigned success or failure in a given VO, the S
F
will
show how risky is the VO formation process itself.
The calculation for R
F
with all SPs is performed
aggregating all R
i
in order to verify if each SPs is able
to compose the VO. This process is formalized as fol-
lows (Equation 12):
R
F
=
|
SP
|
^
i=1
SP
h
R
i
i
(12)
The quantitative risk can be also found by S
F
,
which shows the final success VO probability. In this
case, the logic port AND presented in FTA acts mul-
tiplying all S
i
results acquired in the OR logic gate, as
seen in Equation 13.
S
F
=
|
SP
|
∏
i=1
SP
h
S
i
i
(13)
4 A NUMERICAL EXAMPLE
This section presents a numerical example to bet-
ter understand the proposed method operation. Sup-
pose that a CO was created and three SPs (SP =
{
SP
1
,SP
2
,SP
3
}
were selected (using the SPs selec-
tion method developed in a previous work (Fiorese
et al., 2012)). Therefore, the goal is to measure the
risk of every pre-selected possible SP for the given
VO. Following the proposed method, the individual
risk of every SP is measured and the overall VO risk
is calculated.
The assessment criteria K of each SP are defined
by a set of four KPIs: Trust (K
1
), Communication
(K
2
), Collaboration (K
3
) and Commitment (K
4
). Ta-
ble 1 shows hypothetical historical values assigned to
KPIs of SP
1
, SP
2
and SP
3
for its participations in the
last four VOs (V ). Equation 3 (see Section 3) calcu-
lates the success probability of these KPIs. The MQI
value for KPIs
1:4
are also computed and subtracted of
their respective SDs values, based on the procedures
presented in Equations 1 and 2.
In order to individually measure the risk level of
the SP
1
, SP
2
and SP
3
, they are submitted to the first
stage of MARTP, applying ETA method. It should
also consider the success and failure probabilities of
each KPI that composes the intermediate events so to
add them as parameters in the ET. The ET graphical
representation can be viewed in Stage 1 of Figure 4.
According to Table 1 and using Equations 3 and 4,
the success and failure probabilities associated with
all KPIs of each SP are calculated (Table 2) and the
respective ETs are formed.
Now, let P
i
=
{
P
1
,P
2
,...,P
16
}
a set of all combi-
nations among K
1
, K
2
, K
3
, K
4
for each SP
i
and, for
example, LE = 0.4 (a regular level). Table 3 presents
this result after applying Equation 7. It represents
ARiskAnalysisMethodforSelectingServiceProvidersinP2PServiceOverlayNetworks
483

Table 1: Quantitative values of KPIs according historical values of SP
1
, SP
2
and SP
3
in VOs.
K Service Providers (Past VOs)
SP
1
SP
2
SP
3
MQI−SD
V
1
V
2
V
3
V
4
V
1
V
2
V
3
V
4
V
1
V
2
V
3
V
4
K
1
0.50 0.74
∗
0.89
∗
0.82
∗
0.84
∗
0.85
∗
0.93
∗
0.86
∗
0.48 0.90
∗
0.81
∗
0.96
∗
0.71(SP
3
)
K
2
0.84
∗
0.90
∗
0.96
∗
0.70 0.94
∗
0.80
∗
1.00
∗
0.79
∗
0.85
∗
0.77
∗
0.90
∗
0.78
∗
0.75(SP
2
)
K
3
0.87
∗
0.95
∗
0.91
∗
0.77
∗
0.57 0.80
∗
0.96
∗
0.85
∗
0.75
∗
0.98
∗
0.85
∗
0.74
∗
0.72(SP
2
)
K
4
0.99
∗
1.00
∗
0.95
∗
0.73 0.99
∗
0.97
∗
0.89
∗
0.69 1.00
∗
0.89
∗
0.94
∗
0.77
∗
0.74(SP
3
)
∗
KPI values greater than (MQI − SD)
i
are considered in the risk analysis
Table 2: Success and failure probabilities for SP
1
, SP
2
, SP
3
.
K Service Providers
SP
1
SP
2
SP
3
Suc Fail Suc Fail Suc Fail
K
1
0.75 0.25 1.00 0.00 0.75 0.25
K
2
0.75 0.25 1.00 0.00 1.00 0.00
K
3
1.00 0.00 0.75 0.25 1.00 0.00
K
4
0.75 0.25 0.75 0.25 1.00 0.00
Table 3: Results from event combinations for SP
1
, SP
2
, SP
3
.
P Service Providers (Outcomes)
SP
1
SP
2
SP
3
P
1
0.422
∗
→ 1 0.562
∗
→ 1 0.750
∗
→ 1
P
2
0.141 → 0 0.187 → 0 0.000 → 0
P
3
0.000 → 0 0.187 → 0 0.000 → 0
P
4
0.000 → 0 0.062 → 0 0.000 → 0
P
5
0.141 → 0 0.000 → 0 0.000 → 0
P
6
0.047 → 0 0.000 → 0 0.000 → 0
P
7
0.000 → 0 0.000 → 0 0.000 → 0
P
8
0.000 → 0 0.000 → 0 0.000 → 0
P
9
0.141 → 0 0.000 → 0 0.250 → 0
P
10
0.047 → 0 0.000 → 0 0.000 → 0
P
11
0.000 → 0 0.000 → 0 0.000 → 0
P
12
0.000 → 0 0.000 → 0 0.000 → 0
P
13
0.047 → 0 0.000 → 0 0.000 → 0
P
14
0.012 → 0 0.000 → 0 0.000 → 0
P
15
0.000 → 0 0.000 → 0 0.000 → 0
P
16
0.000 → 0 0.000 → 0 0.000 → 0
∗
Values greater than LE = 0.4
the 2
|K|
combinations of K, corresponding to all the
probabilities (sixteen) associated with each event. For
each value of P, the respective binary representation
are added (1 – values equal to or greater than LE; 0 –
values less than LE) as seen in Stage 1 of Figure 4.
The second stage of the method consists in to ag-
gregate all the individual results from the SP team and
to analyze them as a whole. This is done using ET re-
sults (the set with P
1
, P
2
, ..., P
16
) as input to verify
whether that VO coalition, collectively, is feasible or
not. So, it will be firstly assigned a S
i
score and a
R
i
boolean result for each SP (Equations 11 and 10)
that are calculated through a logic gate OR present
in FTA method. For each SP is also defined a con-
straint Q
i
(Equation 9), corresponding a set with the
values greater than LE (these procedures are seen as
follows):
Q
1
= {0.422}
Q
2
= {0.562}
Q
3
= {0.750}
Note that the number of elements in all Q are equal
to 1. It happens because only one value of P asso-
ciated with both SP
1
, SP
2
and SP
3
was reached 0.4.
Therefore, applying the values of constraint Q, Table
4 summarizes all these informations:
Table 4: Values of
h
R,S
i
associated with SP
1
, SP
2
, SP
3
.
h
R,S
i
Service Providers
SP
1
SP
2
SP
3
R 1 1 1
S 0.422 0.562 0.750
Given the values of R and S for all three SPs,
Equations 12 and 13 are applied considering the
provided values (Table 4) using the SP
i
(R) and SP
i
(S)
as follows:
R
F
= SP
1
(R) ∧SP
2
(R) ∧SP
3
(R) = 1 ∧ 1 ∧ 1 = 1
S
F
= SP
1
(S) ∗ SP
2
(S) ∗ SP
3
(S) =
0.422 ∗ 0.562 ∗ 0.750 = 0.177
ICEIS2014-16thInternationalConferenceonEnterpriseInformationSystems
484

As explained in Section 3, considering R
F
= 1
would mean that the combination of those three SPs
has an acceptable level of risk. Hence, they could be-
come members of the VO, i.e., the VO could be cre-
ated. Considering quantitative levels (calculated by
S
F
), the VO as a whole has 17.7% chance of success.
5 EVALUATION FRAMEWORK
This section presents results of an ongoing and ex-
ploratory research, through MARTP method evalua-
tion. A computational simulation is conducted based
on the preliminary results of (Fiorese et al., 2012) re-
search, in order to add the risk analysis context. Next
subsections present the results obtained.
5.1 Computational Prototype
The developed prototype was split into two modules:
BPSS (Best Peer Selection Service) (Fiorese et al.,
2012) and DFRA (Decision Framework for Risk
Analysis). The first module implements the BPSS
model developed by (Fiorese et al., 2012; Fiorese
et al., 2010) (view Section 2.1) by using the Peer-
FactSim.KOM discrete event simulator (Stingl et al.,
2011) to support the creation of the P2P SON infras-
tructure and additionally make available the process
for SPs search and selection. On the other hand, the
DFRA module focuses specifically on the risk anal-
ysis methods simulation. This model was integrated
with BPSS in order to group the pre-selected SPs into
a new potential VOs and to perform a MARTP evalu-
ation (see Figure 3).
Regarding technical system specifications, the
prototype was built and the tests were developed in a
computer Intel Core i5 3.1GHz, 4.0GB of RAM and
Linux Mint 14.1 64-bit distribution.
5.2 Simulations Setup
The initial configuration for the risk scenario follows
the same rules used for the SP’s selection. The data
was taken from the CAIDA project and MaxMind
GeoIP database (Caida, 2013). The SPs are repre-
sented by a set of pre-selected SON peers whose iden-
tifiers (IPs addresses) belong to five geographical do-
mains, corresponding to the five countries (Portugal,
Spain, France, Italy and Germany). They are also
equally distributed between the five domains.
Taking into account the risk analysis data setup,
the KPIs values assigned to each SP follows a linear
distribution (varying from 0 to 1) during the simula-
tion. The linear distribution strategy for generating
the KPIs values is primarily used firstly because com-
panies are often very variable and the implementa-
tion of the four chosen KPIs (trust, communication,
collaboration and commitment) in real scenarios to
cope with risks in VO also depends on the culture and
working methods currently applied by the involved
organizations. In the same way, it is also considered
that each SP has participated at 10 previous VOs (in
average) when it was selected. The LE (Level of Ex-
cellence) is defined as 0.6, which represents a good
level of quality, as seen in Section 3.
5.3 Results
5.3.1 VO Risk Analysis
The results presented in this section aims to evalu-
ate the efficiency of MARTP (regarding the number
of VO formed) in choosing SPs when comparing the
selection process. The overall procedures for obtain-
ing the selection and risk results are divided into two
different phases as follows:
• The first phase basically performs the process of
SP’s search and selection through the BPSS model
(Fiorese et al., 2012). In this paper, the process
for VO formation will take into account a set of
three distinct SPs that will provide the following
services: VPN (SP
1
), Billing (SP
2
) and Video-
Streaming (SP
3
). For this reason, the BPSS model
should be used three-times in order to provide the
three different SPs, each of them providing its par-
ticular service.
• The second phase take emphasis on the risk anal-
ysis process (MARTP). Thus, this phase uses as
input the three SPs acquired at the first phase (SP
1
,
SP
2
and SP
3
) to group them into a consortia to
measure the risk of their collaboration in compos-
ing a new VO.
The process for comparison between the number
of formed VOs without risk analysis (i.e., only group-
ing the three SPs acquired in the first phase into a con-
sortia for forming a new VO) and with risk analysis
(analyzing the risk of the previous formed consortia)
for the best SPs is depicted in Figure 6a. The simula-
tion comprises 11 sets of individual scenarios divided
into clusters that range [50,300] SPs. For each of the
eleven scenarios (50 SPs, 75 SPs, ···, 300 SPs), the
first and second phase early mentioned are performed
100 times, which will result in eleven 2-bar clusters,
which one varying from 0 to 100. This scale are rep-
resented by the vertical axis and shows, in percentage,
the number of formed VOs regarding the two bars.
ARiskAnalysisMethodforSelectingServiceProvidersinP2PServiceOverlayNetworks
485

0
20
40
60
80
100
50 75 100 125 150 175 200 225 250 275 300
Formed VOs
Number of SPs
Without Risk
With Risk
(a)
0
20
40
60
80
100
50 75 100 125 150 175 200 225 250 275 300
Formed VOs
Number of SPs
Without Risk
With Risk
(b)
Figure 6: Clustering VO Formation for: (a) Best SPs; (b) Second Best SPs.
It is worth mentioning that the selected SPs in the
first phase (i.e., without risk analysis; first-bar clus-
ter), will form VOs (since if does not have other cri-
teria to block the formation). Nevertheless, there is
a significant decrease on the percentage of VOs for-
mation under risk analysis (MARTP) results. The
method is primarily behaving just as a filter, where
from selected SPs, it checks whose are able to com-
pose VOs, regardless of whether they have been rated
as the best or the worst according to other criteria.
The comparison between VO formation also took
into account the second best SPs (selected by the
BPSS), as shown in Figure 6b. This comparison can
aids the validation of the MARTP method by measur-
ing the average improvement of two distinct scenarios
(in this case, the difference of the best SPs over the
second-best SPs).
Considering average results (and based on a con-
fidence interval of 95%), the reduction in the num-
ber of formed VOs when adding the risk filter for the
“best” SPs was 80.54%, and for the second offering
better services, the reducing dropped 80.81%. The
results show that there was not significant variations
between the average of percentage reductions of the
best and second best SPs.
It is important noting that forming the VO based
on choosing only the best SPs accordingly the best
rates of KPIs is not a very good choice. A wiser deci-
sion is to submit the chosen SPs to a risk evaluation.
This is what MARTP does. More importantly, it does
it considering also the odds of SPs working together.
This is the reason of the high drops in the number of
VOs formed after the risk analysis.
5.3.2 Estimation of VO Acceptance Rate
The results presented in Section 5.3.1 showed the
amount of formed VOs when considering LE = 0.6.
However, it is necessary to consider that such results
are calculated based on static values of LE, i.e., that
were previously defined by VO manager and give
only a partial view of the method functionality.
Accordingly, there was performed an evaluation
regarding the relation between the amounts of formed
VOs while LE varies. This evaluation aims to show
how the LE variation can impact in the number of
formed VOs, and additionally, to obtain an equation
that best define this behavior.
The evaluation was carried out by a regression
analysis, where equations were found that describe
how the number of formed VOs behaves in accor-
dance with the increase in LE for 100 simulated sce-
narios (each scenario represents a simulation per-
formed with LE varying from 0.00 to 1.00, with in-
tervals of 0.01). Figure 7 presents two curves, each
one generated by applying a regression calculation in
the dataset obtained through the 100 simulated sce-
narios. The minimum and maximum ranges [0,100]
represented on the vertical axis was defined accord-
ing to the limit in the number of formed VOs. This
means that for values lower or higher than the adopted
Table 5: Polynomial coefficients for the best and becond-best SPs regression analysis.
a b c d e f g h
Eq 1 1.008e+2 -7.312e+1 9.128e+2 -2.912e+3 -2.534e+3 1.581e+4 -1.727e+4 5.972e+3
Eq 2 9.976e+1 -5.416e+1 7.972e+2 -3.161e+3 4.502e+1 1.011e+4 -1.211e+4 4.273e+3
ICEIS2014-16thInternationalConferenceonEnterpriseInformationSystems
486

range, the number of VOs formed remains constant at
0 or 100. In contrast, the horizontal axis represents
the variation in the LE value. It ranges from 0 to 1
with intervals of 0.01 (100 possible results), accord-
ing defined in Section 3.
0
20
40
60
80
100
0 0.2 0.4 0.6 0.8 1
Formed VOs in Average (%)
Value of LE
Best SPs Fitted Curve
Second Best SPs Fitted Curve
Figure 7: Regression analysis for VO formation in relation
to LE variation.
The curve is better adjusted by a polynomial equa-
tion, where the approximate polynomial coefficients
are shown in Table 5. In the analysis performed
through Figure 7, it was found the correlation coef-
ficient (which verify the correlation degree between
LE and the VO formation percentage) r
a
= −0.999
for the best SPs and r
b
= −0.999 for the second-best
SPs scenario. It means that the LE values have a
strong negative correlation with the number of VOs
formed, i.e., the more increases the value of LE, the
smaller becomes the number of VOs, with a success
rate higher than 99.999% for both cases.
One can also see that even maintaining a lower
LE value, often the SPs cannot become able to com-
pose VOs (for instance, the results presented in Sec-
tion 5.3.1 shows that the number of formed VOs when
LE is 0.6 is approximately 20%). It primarily occurs
because how the ETA method (which makes up the in-
dividual risk analysis) in this work is designed to deal
with independent events, so it is sufficient that just
one of all KPIs present a low value for significantly
reduce the SP success probability as a whole.
In this sense, it can be concluded that the method
favors a more rigorous evaluation when is encom-
passed an increased number of indicators, what is de-
sirable when analyzing the risk in the VO as a whole.
Moreover, for all SPs that will compose a VO, it is
necessary that all their indicators have reasonably ac-
ceptable values. Otherwise, they can compromise the
proper working of the VO.
6 CONCLUSION
This paper addressed some issues related to VO risk
identification and measurement. Overall, risk analy-
sis has become a key element in VO planning since
small errors can lead them to impairment as a whole.
Therefore, it is proposed a new method to perform a
risk analysis in a set of Service Providers (SPs) that
are going to compose a Virtual Organization (VO).
The presented method, named MARTP, is com-
posed of two stages. The first stage performs an indi-
vidual risk analysis for all pre-selected SPs, by basing
it on ETA analysis. Having as input the results from
the first stage, the second stage calculates and anal-
yses the global risk considering all SPs together. It
applies FTA method to accomplish that.
In order to assess the MARTP behavior, four dis-
tinct KPIs (trust, communication, collaboration and
commitment) are assigned for each SP. Moreover,
these indicators are combined with real geographical
data in a simulation environment. The performed sim-
ulations involved sets of pre-selected SPs, which have
been taken in (Fiorese et al., 2012).
The achieved results seem promising about the
suitability of the method regarding its purpose. The
level of competence required for each SP to compose
a VO is higher and it is strongly influenced by LE,
which is decisive for this choice. Thus, the VO man-
ager should increase the quality of the SPs by increas-
ing the LE value, which result in a more restrict set of
SPs that are able to compose a VO.
Likewise, the presented method contributes to a
more concrete way to express, measure, assess and
deal with the risks in VO forming, both individually
and collectively, while focusing only on SPs. Never-
theless, the use of the method in the process of risk
analysis provides an evaluation with a lower level of
subjectivity, discarding SPs or not, before composing
a VO, according to the established criteria.
Therefore, future work includes testing the
method in near-real scenarios as well as creating a
framework for risk analysis regarding VOs formation
as a whole. The next steps also include extend the
evaluation to an expert panel, in order to improve the
quality of the method as well as the comparison with
other decision support methods like Bayesian Net-
works (Heckerman, 1996), Genetic Algorithms (Hol-
land, 1973) and Data Envelopment Analysis (DEA)
(Cooper et al., 2007).
ARiskAnalysisMethodforSelectingServiceProvidersinP2PServiceOverlayNetworks
487

REFERENCES
Afsarmanesh, H. and Camarinha-Matos, L. M. (2005). A
framework for management of virtual organization
breeding environments. In Proceedings of the 6th
Working Conference on Virtual Enterprises (PRO-
VE’05), pages 35–48, Valencia, Spain.
Alawamleh, M. and Popplewell, K. (2010). Risk sources
identification in virtual organisation. In Enterprise In-
teroperability IV, pages 265–277. Springer London.
Alawamleh, M. and Popplewell, K. (2012). Analysing vir-
tual organisation risk sources: an analytical network
process approach. International Journal of Network-
ing and Virtual Organisations, 10(1):18–39.
Bentley, J. L. (1975). Multidimensional binary search trees
used for associative searching. Communications of the
ACM, 18(9):509–517.
Caida (2013). Macroscopic topology project. http://www.
caida.org/analysis/ topology/macroscopic/.
Camarinha-Matos, L. M. and Afsarmanesh, H. (2005). Col-
laborative networks: a new scientific discipline. Jour-
nal of Intelligent Manufacturing, 16(4-5):439–452.
Camarinha-Matos, L. M. and Afsarmanesh, H. (2008). On
reference models for collaborative networked orga-
nizations. International Journal of Production Re-
search, 46(9):2453–2469.
Cooper, W. W., Seiford, L. M., and Tone, K. (2007). Data
Envelopment Analysis: A Comprehensive Text with
Models, Applications, References and DEA-Solver
Software. Springer Verlag, New York, USA.
Duan, Z., Zhang, Z. L., and Hou, Y. T. (2003). Service
overlay networks: SLAs, QoS, and bandwidth pro-
visioning. IEEE/ACM Transactions on Networking,
11(6):870–883.
Ericson, C. A. (2005). Hazard analysis techniques for sys-
tem safety. John Wiley & Sons, New York, USA.
Fei, L. and Zhixue, L. (2010). A fuzzy comprehensive eval-
uation for risk of virtual enterprise. In Proceedings of
the 10th International Conference on Internet Tech-
nology and Applications, pages 1–4, Corfu, Greece.
Fiorese, A., Sim
˜
oes, P., and Boavida, F. (2010). OMAN a
management architecture for P2P service overlay net-
works. In Proceedings of the 4th international confer-
ence on Autonomous infrastructure, management and
security (AIMS’10), pages 14–25, Zurich, Switzer-
land.
Fiorese, A., Sim
˜
oes, P., and Boavida, F. (2012). Peer selec-
tion in P2P service overlays using geographical loca-
tion criteria. In Proceedings of the 12th international
conference on Computational Science and Its Applica-
tions (ICCSA’12), pages 234–248, Salvador de Bahia,
Brazil.
Goranson, H. T. (1999). The agile virtual enterprise cases,
metrics, tools. Quorum Books, Westport, CT, USA.
Grabowski, M. and Roberts, K. H. (1998). Risk mitiga-
tion in virtual organizations. Journal of Computer-
Mediated Communication, 3(4):704–721.
Heckerman, D. (1996). A tutorial on learning with bayesian
networks. Technical report, Learning in Graphical
Models.
Holland, J. H. (1973). Genetic algorithms and the optimal
allocation of trials. SIAM J. Comput., 2:88–105.
Junior, O. C. A. and Rabelo, R. J. (2013). A KPI model for
logistics partners’ search and suggestion to create vir-
tual organisations. International Journal of Network-
ing and Virtual Organisations, 12(2):149–177.
Li, Y. and Liao, X. (2007). Decision support for risk anal-
ysis on dynamic alliance. Decision Support Systems,
42(4):2043–2059.
March, J. G. and Shapira, Z. (1987). Managerial perspec-
tives on risk and risk taking. Management Science,
33(11):1404–1418.
Min, H., Xue-Jing, W., Lu, F., and Xing-Wei, W. (2007).
Multi-strategies risk programming for virtual enter-
prise based on ant colony algorithm. In Proceedings
of the 1st International Conference on Industrial En-
gineering and Engineering Management, pages 407–
411, Singapore.
Montgomery, D. C. and Runger, G. C. (2011). Applied
Statistics and Probability for Engineers. John Wiley
& Sons, New Jersey, USA.
Moskowitz, H. and Bunn, D. (1987). Decision and risk
analysis. European Journal of Operational Research,
28(3):247–260.
Mosleh, A., Dias, A., Eghbali, G., and Fazen, K. (2004).
An integrated framework for identification, classifi-
cation, and assessment of aviation systems hazards.
In Proceedings of the 6th International Conference
on Probabilistic Safety Assessment & Management
(PSAM’04), pages 2384–2390, Berlin, Germany.
Mowshowitz, A. (1997). Virtual organization. Communi-
cations of the ACM, 40(9):30–37.
Pidduck, A. B. (2006). Issues in supplier partner selec-
tion. Journal of Enterprise Information Management,
19(3):262–276.
Stingl, D., Gross, C., Ruckert, J., Nobach, L., Kovacevic,
A., and Steinmetz, R. (2011). PeerfactSim.KOM: a
simulation framework for peer-to-peer systems. In
Proceedings of the 13th International Conference
on High Performance Computing and Simulation
(HPCS’11), pages 577–584, Istanbul, Turkey.
Vose, D. (2008). Risk analysis: a quantitative guide. John
Wiley & Sons, New Jersey, USA.
Zhou, S., Hogan, M., Ardon, S., Portman, M., Hu, T., Won-
grujira, K., and Seneviratne, A. (2005). Alasa: When
service overlay networks meet peer-to-peer networks.
In Proceedings of the 11th Asia-Pacific Conference
on Communications (APCC’05), pages 1053–1057,
Perth, Australia.
ICEIS2014-16thInternationalConferenceonEnterpriseInformationSystems
488
