
Opportunistic Software Composition: Benefits and Requirements
Charles Triboulot
1,2
, Sylvie Trouilhet
2,3
, Jean-Paul Arcangeli
2
and Fabrice Robert
1
1
Sogeti High Tech, Aeropark 3 Ch. Laporte 31300 Toulouse, France
2
Université de Toulouse, UPS, IRIT, 118 route de Narbonne 31062 Toulouse, France
3
IUT A, Av. G. Pompidou CS 20258 81104 Castres, France
Keywords:
Opportunism, Software Component, Automatic Bottom-up Composition, Ambient Systems.
Abstract:
Traditional software development relies on building and assembling pieces of software in order to satisfy ex-
plicit requirements. Component-based software engineering simplifies composition and reuse, but software
adaptation to the environment remains a challenge. Opportunistic composition is a new approach for building
and re-building software in open and dynamic contexts. It is based on the ability to compose software com-
ponents in a bottom-up manner, merely because they are available at a point and not because the construction
of a specific software has been demanded. In this way, software emerges from the environment. This paper
analyzes the advantages of such an approach in terms of flexibility and reuse, along with the requirements that
an infrastructure supporting opportunistic composition should satisfy: it should be decentralized, autonomic,
and dynamically adaptive. The state of the art of automatic software composition shows that few solutions are
actually bottom-up, and that none of them fully satisfies the requirements of opportunistic composition.
1 INTRODUCTION
When rationalizing software development, two major
points should be considered: productivity and reuse
on the one hand, capability of evolution on the other
hand. Regarding these points, component-based soft-
ware engineering improves object-based software en-
gineering, mainly due to the explicitation of the re-
quired interfaces at the same level as the provided
ones.
In traditional software engineering, composition
is triggered when a need is made explicit and when the
building of the software is demanded. Components
are identified, then selected among existing ones or
developed one by one, in order to compose the appli-
cation. This approach is called top-down because the
development is driven by the satisfaction of explicit
requirements. In a general way, meeting requirements
is a constant challenge for software engineers.
Once developed, applications are deployed in so-
cial and technical contexts that are changing. There-
fore requirements change, thus applications must be
flexible enough and adapt. But, even if pieces of so-
lution exist, developers generally struggle to guess
possible evolutions and to design points of variabil-
ity in software. Because stakeholders’ requirements
are considered as a foundation at the early steps of
traditional software engineering and architectural de-
sign processes, considering changes remains a major
challenge in software engineering and software archi-
tecture.
Composition and adaptation issues are particu-
larly crucial for ambient, ubiquitous and mobile sys-
tems. Given the large number of networked devices
that populate ambient environments, as each of them
may host software components, there are possibly nu-
merous applications and services that can be built and
provided to people in order to enrich their environ-
ment. Ambient intelligence can be measured in the
yielded additional value while limiting the active par-
ticipation of users. Ambient systems, with their dy-
namics, must be proactive and intelligent enough to
adapt according to the context in order to react to
some situations, anticipate user needs, or go further
than the predefined behavior.
1.1 Opportunistic Composition
Our work aims to explore a new approach for the
engineering of component-based software applica-
tions. Our approach, called “opportunistic composi-
tion”, differs from the traditional one because com-
position is no longer driven by explicit requirements
but opportunity-driven. Opportunistic composition is
426
Triboulot C., Trouilhet S., Arcangeli J. and Robert F..
Opportunistic Software Composition: Benefits and Requirements.
DOI: 10.5220/0005558404260431
In Proceedings of the 10th International Conference on Software Engineering and Applications (ICSOFT-EA-2015), pages 426-431
ISBN: 978-989-758-114-4
Copyright
c
2015 SCITEPRESS (Science and Technology Publications, Lda.)

the ability to assemble software components merely
because they are available in the surrounding envi-
ronment. In this way, composition is directed by the
execution context and by the opportunity to assemble
components that are ready for composition (but which
have not been developed specifically for the applica-
tion under construction), and no longer by the neces-
sity of satisfying explicit requirements. Thus, appli-
cations emerge from the environment and can evolve
afterwards by dynamic (re)composition based on new
opportunities.
Opportunism in software construction is a new
idea, which has been little, if at all, studied. A paper
on this subject has been presented at the French con-
ference UBIMOB (Ubiquity and Mobility) in 2011
(Vergoni et al., 2011). In (Conti and Kumar, 2010),
opportunistic computing has been defined as a new
computing paradigm derived from ad hoc and oppor-
tunistic networking tightly coupled with social net-
working, which aims at exploiting available resources
in an environment to provide distributed collabora-
tive computing services and applications; the main
challenges that are stated concern networking: inter-
mittent connectivity, delay tolerance, protocol hetero-
geneity.
Of course, opportunistic composition raises sev-
eral issues. The main ones relate to what can be com-
posed (heterogeneity, composability...), what should
be composed and how combinatorial complexity can
be controled, context-awareness, the semantics of the
resulting application, its quality attributes (security,
reliablility, efficiency...), its viability and usefulness,
and how to automatically perform opportunistic com-
position.
1.2 Contents and Plan
This paper presents an analysis of the opportunistic
composition approach. It discusses its advantages in
terms of flexibility and reuse, and focuses on the fea-
sibility and on the requirements that an infrastruc-
ture should satisfy in order to support opportunistic
composition and allow the emergence of component-
based software systems. Finally, the state of the art of
automatic composition is analyzed in relation to these
requirements. However, the paper does not present
any architecture or experimental results. The con-
tribution sets in the analysis of the opportunistic ap-
proach, in the identification of the requirements of its
realization, and in the analysis of the state of the art.
The paper is organized as follows. Section 2
presents a real-world illustrating scenario which is
useful for highlighting different situations of compo-
sition. In Section 3, opportunistic composition is de-
fined more formally and the requirements for its re-
alization are exposed. Section 4 analyzes the state of
the art of automatic composition. To conclude, in Sec-
tion 5, we give some directions for the realization of
opportunistic composition.
2 SCENARIO
This section presents a scenario in which opportunis-
tic composition assists users in their life and their job,
and provides applications depending on the context.
Here is Plip, an engineer who works in a secured ex-
periment room of her company. She uses a robotic
arm and a laser to project rays on a flat surface.
The scenario consists of four acts and shows sev-
eral situations of opportunistic composition. It sup-
ports an analysis presented in Section 3. It underlines
how an opportunistic composition system can react to
some situations when they occur in a dynamic envi-
ronment. Only the system’s behavior is described, not
its implementation. It is worth pointing out that com-
positions become possible without the necessity to ex-
plicitly specify user needs. They are realized merely
because the components are available in the environ-
ment and because assembling them may be relevant.
Plip does have requirements, but not necessarily ex-
plicited, and nevertheless the system provides an an-
swer to them in a proactive way.
To carry out this scenario, we assume that the
components are interoperable. Issues, such as secu-
rity or privacy, are set aside in this work.
Act I - Plip is working in her office, on a new
experimental model stored on her PC. Once the
model is completed, she runs an application on
her tablet computer that provides estimated results
according to the model. This application detects that
a component implements Plip’s model, thanks to a
Wi-Fi connection between Plip’s PC and the tablet,
and proposes the use of this component. Since it
matches her requirement, she accepts. Then, the
application runs.
Act II - Since the estimated results are satisfactory,
Plip is ready to perform the genuine experiment and
compare the estimated results to the real ones. She
goes to the experiment room with her tablet. The
experiment room has been secured recently: it is
isolated from Wi-Fi signals, but Plip does not know
that. She enters the room with her tablet which is
still connected by Wi-Fi with her PC. As the Wi-Fi
component of the tablet is no longer working, a new
composition is done, which involves a Bluetooth
OpportunisticSoftwareComposition:BenefitsandRequirements
427

component which radio waves cross the walls of the
secured room. This automatic composition preserves
the communication link between the tablet and the
outside PC. Thus, the application is still running and
connectivity issues are imperceptible for Plip.
Act III - Plip starts the experiment. She turns on
the different devices, oscilloscopes and screens, in
the experimental room. She also turns on the central
PC to control the experiment. The different devices
are assembled automatically in order to propose an
adequate experimental environment (see Figure 1).
This is possible because the opportunistic composi-
tion system has learned, from previous experiments,
the context in which such a configuration is relevant.
Furthermore, one of the oscilloscope in the room has
been upgraded, and now proposes a greater quality of
service than the other oscilloscopes. Consequently, it
is used in the assembly.
Act IV - While the experiment is running, the cen-
tral PC suddenly breaks down. Unfortunately, it em-
beds several indispensable components for the exper-
imental assembly, and plays an essential role in the
command of the robotic arm ("Exp Leader" compo-
nent). The PC is also used to collect the results of
the experiment, and then analyze them. To allow the
experiment to go on without waiting for repairs, the
opportunistic composition system searches for other
suitable components. In this case, the system may
have several choices and must efficiently select and
perform the most relevant ones (for instance an older
“Exp Leader” component and a “Stock” component
embedded in another device), with the help of context
information.
3 ANALYSIS OF THE APPROACH
From this scenario, we extract three main advantages
of the opportunistic approach compared to top-down
and traditional approaches: proactiveness, flexibility
and genericity. Then, we enumerate the functional
and extrafunctional requirements which seem to be
fundamentalfor an opportunistic composition system.
3.1 Benefits
Proactiveness - While Plip carries on her daily tasks,
she never expresses explicitly her needs. However,
the system proposesand maintains useful applications
according to the current situation without relying on
explicit user needs (explicit request of a component
by the user is possible but not mandatory).
The final assembly is characterized as emergent,
because neither the developer, the user, the system
nor the components have a knowledge of it before
its bottom-up fabrication. The key is to select useful
compositions with methods related to learning or con-
text awareness. The development of a proactive sys-
tem, which does not demand requirement formaliza-
tion and proposes relevant compositions, is promis-
ing in an ambient scope: in such undetermined and
unpredictable environments, it is hard to express, or
even identify, what the user needs can be.
Flexibility - Several adaptive reactions of the sys-
tem can be observed in the scenario. Thanks to oppor-
tunistic composition, applications using appropriate
components may replace ineffective and useless ones.
The adaptive reactions are not explicitly expressed,
but are the result of bottom-up decisions. On the one
hand, this approach supports openness (components
may appear or disappear from the local environment).
On the other hand, applications are resilient (they are
continually maintained and enhanced). Here, initial
composition and resilience are supported by the same
opportunistic approach.
Genericity - No hypothesis is made on the pres-
ence of certain components, their business domain,
their type or number. Most of all, the system can
work without the knowledge of the user needs. So, an
opportunistic composition system can be generic and
useful in any (dynamic) environment. The system as-
sisting Plip could also be used in various contexts (e.g.
smart-home, guidance, monitoring...).
However, these benefits are guaranteed only if
several open problems are resolved. How is the rel-
evance of a composition precisely evaluated? How
is the usability of an emergent application guaranteed
without formalization of needs? How is the seman-
tics of the application presented to the user? How
is the combinatorial complexity mastered? The next
sections will identify requirements for the realization
of opportunistic composition. Meeting these require-
ments should bring answers to those questions.
3.2 Functional Requirements
From the different composition situations underlined
in the scenario, five functional requirements can be
extracted. In the following enumeration, each of them
is presented through the event that triggers the new
composition.
1) Request of a Component (fRC) (Act I). A com-
ponent is requested by a user or the system itself, for
being a part of an application. Thus, this component
tries to compose itself as a priority and properly fulfill
its functionality. This is a way to implicitly express a
ICSOFT-EA2015-10thInternationalConferenceonSoftwareEngineeringandApplications
428
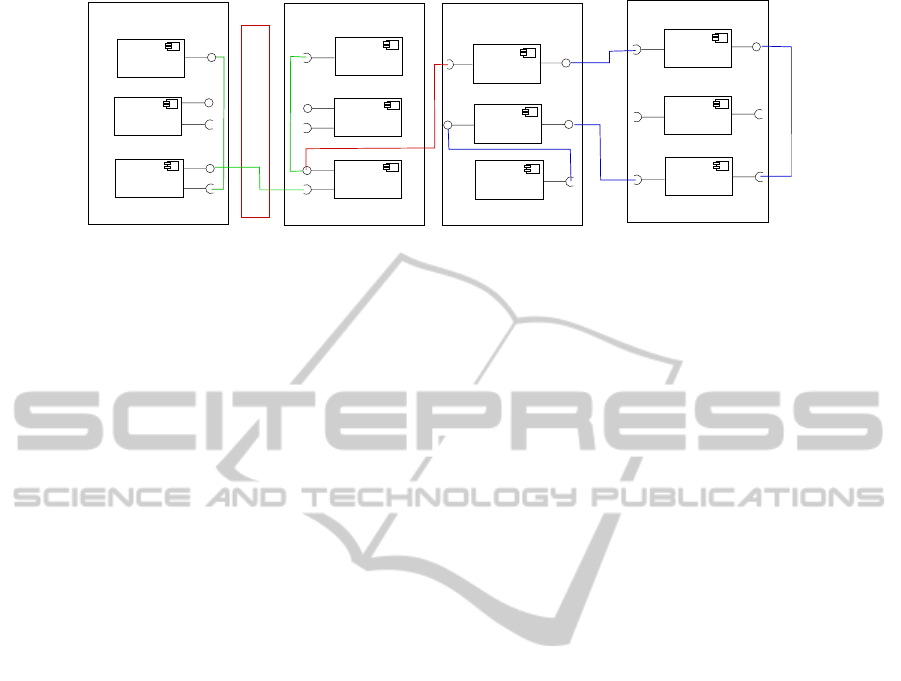
Central PC
Labo
Stock
Analysis
Robot Arm
Oscilllo 1.0
Exp Leader
Oscilllo 3.0
Mod
Cmd
Cmd
T
T
Res
X
X
Res
Res
T
Model
Plip's PC
Mod
Tablet
Mod Estim
Mod
X
X
X
X
X
X
X
X
Anti-Wi-Fi
Wall
I/O Wi-Fi
I/O BlueTooth
I/O BlueTooth
I/O Wi-Fi
Figure 1: Component view of Act III.
user need without formalizing it.
2) Context Evolution (fCE) (Act III and Act IV).
Some external situations may trigger a system reac-
tion. Context awareness allows the system to detect
these situations, while learning capabilities allow to
memorize them. So, the system can properly react to
environment evolution with the proper responses.
3) Appearance of a Component (fAC) (Act III). Due
to the high dynamics of the environment, one or sev-
eral components may be discovered by other compo-
nents. This event can follow the start-up of a device
or a mobility situation. The appearing component can
be included in an existing assembly or trigger a new
composition.
4) Disappearance of a Component (fDC) (Act II
and Act IV). A component may disappear from the
environment, in case of mobility, obsolescence or fail-
ure. The system should detect this situation and main-
tain the applications which were using the missing
component by proposing new efficient compositions.
Note that the disappearance of a component may be
progressive and can be detected and anticipated be-
fore it actually happens, especially during a situation
of mobility.
5) Upgrade (fU)(Act III). Some intrinsic properties
of components may also dynamically evolve. For ex-
ample, quality of service or interface profiles may be
modified at runtime, further to an upgrade. These
modifications are most likely to trigger new compo-
sitions. An opportunistic composition system should
be able to identify any of these situations and react
accordingly. It must also take into account that they
can occur in any quantity and in any order. Previous
situations are therefore considered as functional re-
quirements for an opportunistic composition system.
3.3 Extrafunctional Requirements
The aim of this section is to identify the extrafunc-
tional requirements for the design of a system able to
perform opportunistic composition. They represent
generic issues the opportunistic system has to deal
with, but do not make any assumptions on the meth-
ods and/or technologies used.
Seven requirements can be extracted and formal-
ized. They can be used for the evaluation of different
composition systems.
1) Decentralization (efDc): Ability to propose a de-
centralized process in which each task is attributed
to an autonomous entity in a synchronous or asyn-
chronous way. Indeed, the system must work at a lo-
cal level and consider the local neighborhood of com-
ponents but not the whole environment. Furthermore,
a local view is the natural way to perform bottom-up
composition and obtain emergent results. The rele-
vance of decentralized design is confirmed by the in-
ability for a central entity to handle high dynamics,
bottlenecks and/or failures.
2) Dynamic Adaptation (efDA): Ability to handle
undetermined and unpredictable environments. The
opportunistic composition system runs in highly dy-
namic and unpredictable environment: components
may appear or disappear at runtime, even context and
users’ actions can change. Thus, it should be open
and able to generic and efficient adaptation.
3) Combinatorial Optimization (efCO): Ability to
handle a fair amount of possible compositions among
available components. Ignoring this point may lead to
efficiency and speed issues for the composition pro-
cess. Thus, the system must handle this problem and
efficiently select the most useful compositions using
discriminating strategies.
4) Recomposition (efRc): Ability to dynamically
maintain and/or enhance existing compositions. In
order to support the resilience of applications, com-
ponents may be added or replaced, or the entire as-
sembly may be challenged.
5) Learning and Context Awareness (efLC): Abil-
ity to take into account past activities and context to
perform relevant compositions.
6) Utility of the Result (efUR): Ability to guaran-
tee a useful application as a result of the composition.
The emergent result must be useful and satisfy im-
plicit needs. Its utility can be automatically verified,
OpportunisticSoftwareComposition:BenefitsandRequirements
429

Table 1: Functional and extra-functional requirements.
fRC fCE fAC fDC fU efDc efDA efCO efRc efLC efUR efSUN
Vallée 2005 x x + ++ + - + + - -
Grondin 2006 x x x - - + - ++ + ++ - -
Desnos 2007 x x - - + + ++ - - - +
Bartelt 2008 x x ++ - - - - - - - +
Rouvoy 2009 x x x - ++ - - + - + -
Guidec 2010 x x x ++ ++ - - - - ++ - -
Sykes 2011 x x x + + - ++ - - -
Bonjean 2013 x x x x x ++ + ++ + + + -
in local or global scope, a posteriori by feedback on
the assembly, or a priori by identification of promis-
ing compositions.
7) Silence of User Needs (efSUN): Ability of the sys-
tem to operate without the preliminary expression of
user needs. This requirement is a main one in order
to let the system propose emergent solutions without
explicit requirements or user needs.
Next section confronts the state of the art with the
functional and extrafunctional requirements.
4 STATE OF THE ART
We analyzed eight research works on component au-
tomatic composition in order to determine if and how
they could answer the requirements of the opportunis-
tic approach (Vallée et al., 2005; Grondin et al., 2006;
Desnos et al., 2007; Bartelt et al., 2008; Rouvoy et al.,
2009; Guidec et al., 2010; Sykes et al., 2011; Bon-
jean et al., 2013). Table 1 indicates both if the solu-
tion could handle the functional requirements (if the
system could detect and then properly handle the sit-
uation, the corresponding box contains a cross) and
the extrafunctional requirements (evaluated from - -
to ++).
None of the solutions has (x) or (++) for all the
requirements. The fDC (Disappearance of a Compo-
nent) requirement is globally met. This is due to the
systematic self-adaptation aspects developed in the
reviewed works. Likewise, some extrafunctional re-
quirements, such as efDc (Decentralization) or efDA
(Dynamic Adaptation), are admitted as essential for
automatic composition and a lot of solutions exists.
However, efCO (Combinatorial Optimization) and
efLC (Learning Context), although they are extremely
important in dynamic environments, have yet to be
considered. A similar assessment can be made for
functional requirements; situations such as fU (Up-
grade) and fCE (Context Evolution) also seem to be
hardly anticipated. The last issue is the status of the
expression of user needs, many systems demanding
their formalization before making any composition
decision. This expression is not mandatory, but it can
be noted that efUR (Utility of the Result) and efSUN
(Silence of User Needs) are not satisfied together (see
Table 1).
5 CONCLUSION AND
PERSPECTIVES
In this paper, we have defined opportunism as an ap-
proach for building and re-building software by com-
posing available software components. We have il-
lustrated the advantages of this approach: flexibility
and adaptiveness. In our opinion, opportunistic soft-
ware composition is not limited to ambient systems:
for example, it could assist software engineers, which
have to compose reusable components as part of large
libraries or to adapt component-based software, by
proposing them relevant compositions.
Opportunistic composition is a promising generic
approach, well-adapted to highly dynamic and open
environments, which disregards formalization of user
needs. However, the link between needs and compo-
nent assemblies should be considered through learn-
ing, evaluation of utility and user’s feedback, in or-
der to control the emergence. Thus, opportunistic
composition may be a basis for design of intelligent
systems, which proactively provide emergent applica-
tions adapted to (possibly unforeseen) situations, and
anticipate user needs.
Systems that support opportunistic software com-
position should meet several requirements, in partic-
ular those related to combinatorial complexity and
relevance of the emergent applications. In order to
face these challenges, we currently develop a solution
based on multi-agent systems (MAS) which offer sev-
eral advantages from an architectural point of view
(Arcangeli et al., 2014), and precisely on cooperative
MAS (Georgé et al., 2011), which support the emer-
gence of functions through local interactions between
cooperative agents. In order to select relevant compo-
ICSOFT-EA2015-10thInternationalConferenceonSoftwareEngineeringandApplications
430

sitions, agents have learning capabilities and are able
to consider user’s feedback.
REFERENCES
Arcangeli, J.-P., Noel, V., and Migeon, F. (2014). Software
Architectures and Multi-Agent Systems. In Oussalah,
M. C., editor, Software Architectures, volume 2, chap-
ter 5, pages 171–208. Wiley-ISTE.
Bartelt, C., Fischer, B., and Rausch, A. (2008). To-
wards a Decentralized Middleware for Composition
of Resource- Limited Components to Realize Dis-
tributed Applications. In 3rd Int. Conf. on Pervasive
and Embedded Computing and Communication Sys-
tems (PECCS 2013), pages 245–251.
Bonjean, N., Gleizes, M.-P., Maurel, C., and Migeon, F.
(2013). Forward Self-combined Method Fragments.
In Agent-Oriented Software Engineering XIII, number
7852 in LNCS, pages 168–178. Springer.
Conti, M. and Kumar, M. (2010). Opportunities in oppor-
tunistic computing. Computer, 43(1):42–50.
Desnos, N., Huchard, M., Urtado, C., and Vauttier, S.
(2007). Automated and Unanticipated Flexible Com-
ponent Substitution. In Proc. of 10th Int. Symp. on
Component-Based Software Engineering.
Georgé, J.-P., Gleizes, M.-P., and Camps, V. (2011). Co-
operation. In Di Marzo Serugendo, G., Gleizes,
M.-P., and Karageogos, A., editors, Self-organising
Software, Natural Computing Series, pages 7–32.
Springer.
Grondin, G., Bouraqadi, N., and Vercouter, L. (2006).
MaDcAr: An Abstract Model for Dynamic and Au-
tomatic (Re-)Assembling of Component-Based Ap-
plications. In Component-Based Software Engineer-
ing, number 4063 in LNCS, pages 360–367. Springer-
Verlag.
Guidec, F., Sommer, N. L., and Mahéo, Y. (2010). Oppor-
tunistic Software Deployment in Disconnected Mo-
bile Ad Hoc Networks. Int. Journal of Handheld Com-
puting Research, 1:24–42.
Rouvoy, R., Barone, P., Ding, Y., Eliassen, F., Hallsteinsen,
S., Lorenzo, J., Mamelli, A., and Scholz, U. (2009).
Music: Middleware support for self-adaptation in
ubiquitous and service-oriented environments. In Soft-
ware Engineering for Self-Adaptive Systems, pages
164–182. Springer-Verlag.
Sykes, D., Magee, J., and Kramer, J. (2011). FlashMob:
Distributed Adaptive Self-Assembly. In Proc. of the
6th Int. Symp. on Software Engineering for Adaptive
and Self-Managing Systems, pages 100–109.
Vallée, M., Ramparany, F., and Vercouter, L. (2005). A
Multi-Agent System for Dynamic Service Composi-
tion in Ambient Intelligence Environments. In The
3rd International Conference on Pervasive Comput-
ing (PERVASIVE 2005), pages 175–182.
Vergoni, C., Tigli, J.-Y., Rey, G., and Lavirotte, S. (2011).
Construction Bottom-up d’applications ambiantes en
environnements partiellement connus a priori. In
7èmes Journées Francophones Mobilité et Ubiquité
(UBIMOB 2011).
OpportunisticSoftwareComposition:BenefitsandRequirements
431
