
Why and How People Use Location Sharing Services on Social
Networking Platforms in China
Shang Gao
1
and Xuemei Zhang
2
1
Department of Computer and Information Science, Norwegian University of Science and Technology, Trondheim, Norway
2
School of Business Administration, Zhongnan University of Economics and Law, Wuhan, China
Keywords: Location Sharing Services, Social Networking Platforms, Check-in, Privacy, Contextual Integrity.
Abstract: Along with the development of information communication technology, there are more and more location
sharing services on social networking platforms. Although China has the largest number of internet users in
the world, users just started to use location sharing services in the last three years. This study aims to
investigate why and how people use location sharing services on social networking platforms in China. To
address this, four research questions are presented and 43 in-depth face-to-face interviews are carried out in
China. Our results indicated that most users were concerned about privacy issues when they were using
location sharing services on social networking platforms. Somewhat surprisingly, some of the interviewees
indicated that they were not aware of the availability of the location sharing services on social networking
platforms and they did not know how to use location sharing services. Furthermore, with respect to privacy
protection, most interviewees indicated that WeChat did a better job than Weibo in China. Lastly, the results
revealed that users wanted to use authority management to deal with private issues raised by the shared
location information on social networking platforms.
1 INTRODUCTION
Along with the development of information
communication technology, location based services
on mobile devices are getting more and more
popular ((Gao, et al. 2014) (Gao, et al. 2015)). There
are an increasing number of mobile applications on
social networking platforms that can sense and share
users’ location information with others. We have
seen a significant amount of research conducted to
understand users’ location sharing privacy
preferences when they are using location sharing
services on social networking platforms (Lin et al.
2013). For example, Lindqvist et al. (2011) has
studied why people use the location sharing
application Foursquare. Zhu (2012) has investigated
the privacy have social effects of location sharing.
However, we found that the usage of location
sharing services has been mainly studied in
developed countries in the last few years. The usage
of location sharing services in developing countries
is still an open research question. Thus, we aim to
investigate why and how people use location sharing
services on social networking platforms in China.
Social networking services are getting more and
more popular in China. Weibo (a Twitter-alike
service in China) and WeChat (one of the most
popular instant messaging services in China) are the
two of most popular social networking services in
China. Unlike the service of automated tracking (Li
et al., 2013), users can choose whether to attach their
location information with the messages or photos on
social networking platforms. According to the 2013
annual report from China Internet Network
Information Center, the users of Weibo and Wechat
reached a penetration rate of 43.6% and 65% at the
end of 2013 in China respectively.
The objective of this study is to examine why
and how users use location sharing services on
social networking platforms (e.g., Weibo and
Wechat) in China. To address this, four research
questions are presented and 43 in-depth face-to-face
interviews are carried out in China. The remainder
of this paper is organized as follows: the literature
review is provided in Section 2. Section 3 proposes
the research questions. This is followed by the
illustration of the research method in section 4. The
research findings are presented in Section 5. In
section 6, we conclude this study with a discussion
on the research findings and an outline for future
203
Gao S. and Zhang X..
Why and How People Use Location Sharing Services on Social Networking Platforms in China.
DOI: 10.5220/0005571902030208
In Proceedings of the 12th International Conference on e-Business (ICE-B-2015), pages 203-208
ISBN: 978-989-758-113-7
Copyright
c
2015 SCITEPRESS (Science and Technology Publications, Lda.)

research directions.
2 LITERATURE REVIEW
The related literature is discussed in this section.
2.1 Contextual Integrity
In order to investigated how people use location
sharing services in social networking platforms and
how people concern about private issues in the
process, the theory contextual integrity is used. The
contextual integrity proposed by Nissenbaum (2004)
is based on two principles. Firstly, people are living
in various social contexts; and secondly, every
context has a set of social norms matching with it.
Moreover, Nissenbaum (2004) identified two types
of information norms. The first norm is
appropriateness, which measures whether the
disclosure of information is proper in a certain
context. The information type (Barth et al., 2006) is
a factor to judge appropriateness. The second norm
is distribution, which decides whether the
distribution of information is allowed under the
conditions and restrictions in the flow of
information. The contextual integrity asserted that
the reason for privacy issues is the violation of
appropriateness or distribution principles.
In this study, the contextual integrity is used to
clarify the privacy concern on the location sharing
service on the social networks by exploring whether
the violation of the appropriateness or distribution
principles has accrued and how do people deal with
private concerns.
As shown in Table 1, contextual integrity has
been widely used to study about the internet privacy
issues in the previous studies. Lipford et al. (2009)
investigated privacy mechanisms on social network
sites and examined privacy issues with the following
four elements: profile, photos, newsfeed and the
application platform. Grodzinsky et al. (2010)
researched personal bloggers’ privacy issues.
2.2 Privacy Concerns in Location
Sharing
Several researchers have examined the privacy
issues in location sharing services on social
networking platforms. We found that the most
studied platform was Foursquare. In-depth
interviews and surveys were most used in previous
studies (Lindqvist et al. (2011)). While people are
sharing their locations on social networking
platforms, the personal information of where you are
and what you are doing at a certain time are
disclosed. Cramer et al. (2011) examined the
conflicting norms in check-in services. The results
indicated that these norms about when and where to
check-in sometimes conflicted with each other since
people might have different motivations in using
check-in services. Furthermore, privacy attacks in
location sharing services on social networking
platforms were studied by Kostakos et al. (2011).
The result indicated that users who were most likely
to know your real location were the users who
communicated most frequently with you. Last but
not least, Tsai et al. (2010) investigated the privacy
in the perception of risks and benefits on social
networking platforms. The results revealed that
people cared about privacy control mechanism on
social networking platforms.
This research aims to complement and extend
existing research by focusing on the use of location
sharing services on social networking platforms in
China. It is a continuing effort by applying context
Table 1: Literatures used contextual integrity to study about the Internet privacy issues.
Literature Research Purpose Theory Used Findings
Lipford et al
(2009)
Investigate privacy
mechanisms on
social network sites
Contextual integrity The way to design a better privacy mechanisms
is to make the flows of information visible.
Grodzinsky et al.
(2010)
Research personal
bloggers` privacy
issues
Contextual integrity The privacy of these whose name are on the
personal bloggers of others has been violated
Shi et al. (2013) Check the privacy
concerns of
Friendship Pages
Contextual integrity Users’ interpersonal privacy concerns can arise
if contexts, actors, attributes and transmission
principles are violated or changed in context-
relative information norms
Zimmer (2008) Clarify the private
threats of google
search
Contextual integrity Google's quest for the perfect search engine has
changed personal information flows. So that
private are threatened
ICE-B2015-InternationalConferenceone-Business
204

integrity to study users’ privacy concerns in using
location sharing services on social networking
platforms in China.
3 RESEARCH QUESTIONS
The objective of this research is to understand how
users use location sharing services on social
networking platforms in China. As indicated in the
last section, previous research found that privacy is a
barrier to influence the use of location sharing
services on social networking platforms. Further, we
would like to use the theory of contextual integrate
to further investigate the norms of location
information sharing on social networking platforms
in China.
Our research questions are as follows.
1. What is the motivation for people to use
location sharing services on social networking
platforms?
2. Why do some users not use location sharing
services on social networking platforms?
3. When and where do users tend to share their
location?
4. How do people deal with the private
concerns? What is users’ preference on using
location sharing services on different social
networking platforms (e.g., WeChat, Weibo)?
4 METHODS
To address the four research questions proposed in
Section 3, we conducted a qualitative research in
terms of interviews in China. We recruited the
interview participants by posting announcements on
social networking platforms in the biggest city in the
central part of China in October 2014. Fifty users
agreed to participate in the interview. However,
some users did not appear in the scheduled interview
time slots. As a result, we had conducted 43 in-depth
face-to-face interviews with users of social
networking platforms in China. The interviews were
semi-structured and also included a set of open
questions for all interviewees. Each interview lasted
around 25 minutes. The interviews were recorded
and the notes were taken. The transcriptions and
notes were analysed by using open coding.
Among the participants, 27 (numbered as A1 to
A27), had some experience with using location
sharing services on social networking platforms. 16
(numbered as A28 to A43) of the participants were
users of social networking platforms. However, they
never used location sharing services on social
network platforms before. For this group of users,
we explored the reasons behind that by asking some
open questions. 20 of the participants were male,
and 23 were female. 3 of the participants are under
20 years old, and 40 of them are between 20 and 25.
5 RESEARCH FINDINGS
The research findings are presented in this section.
5.1 Motivations to Use Location
Sharing Services
The frequent indicated motivations during the
interviews were summarized as follows: 1).telling
friends where the interviewee has been (the most
indicated), 2).arriving at a new place or doing
something interesting, 3). being at a place where is
fun to tell his/her friends. The purpose is to inform
their friends about the change of his/her geographic
location. However, sometimes, people check-in at a
place where they are not actually in (A6),
“Sometimes, I checked-in to cheat on my boyfriend,
Actually, I was not there”. This means that the
location information can be edited by the user.
Sometimes doing something romantic can enable
users to share location information on social
networking platforms. A11 shared his location in a
cinema because he was with his girlfriend at that
time. He said that he tended to share the location
when he was dating with his girlfriend. Visiting
places of interest can also motivate users to use
location sharing services on social networking
platforms. Some people shared location information
to record their daily routines in their personal life.
A14 said that, “I checked-in when I wanted to share
my daily routines with my friends”.
5.2 Why People Do Not Share Their
Location Information?
There are 16 interviewees never used location
sharing services on social networking platforms
before. Six of them indicated that they never heard
of this service or did not know how to use this
location sharing service (A34, A36, A37, A40, A42,
and A43). Three interviewees indicated that they
thought sharing location is useless and meaningless
(A28, A29. A33). There were also 5 interviewees
who worried about the privacy and safety issues
raised by using location sharing service (A30, A35,
WhyandHowPeopleUseLocationSharingServicesonSocialNetworkingPlatformsinChina
205

A39, A40, A41). A30 mentioned that “I don’t like
the feeling of being watched by sharing my location
information on social networking platforms”. A35
said that, “In some cybercrime cases, location
information on WeChat or Weibo were used to find
the object”. Further, four interviewees indicated that
they were concerned about privacy issues in some
circumstance. For example, they did not want their
location information to be seen by their parents.
5.3 The Information Norms of Sharing
Location
Information norm is an important concept in the
contextual integrity theory. It represents the norm of
where and when to share location in the general
accepted way.
5.3.1 Where Do People Check-in?
Interviewees were asked to rank the types of
locations that they were likely to share according to
their past experience. The ranking scores of each
type of location were presented in Figure 1.
It can be seen from the bar chart that the users
were most likely to share their locations at tourism
scenic areas. The event scenes and entertainment
venues have the same score, both of which are the
second frequent places to check-in. The third most
likely check in location is the places for working and
studying. Home was ranked as the most unlikely
place to be shared by end users.
Figure 1: The ranking scores of each type of location.
The findings from Section 5.1 are of help to further
explain the results in Figure 1. The most indicated
motivation is to tell friends where the interviewee
has been. The tourism scenic areas are often the
places of interests. Users are interested to share this
information to their friends. Entertainment venues
and event scenes are places that are fun and
appropriate for sharing information on their daily
life. The places for working and study and home are
regarded as users’ routine places. According to the
results, it seemed that end users did not like to share
location information of their routine places.
5.3.2 When Do People Check-in?
Participants A2, A12 and A13 indicated that they
intended to share their location information on social
networking platforms when having group events. A7
and A24 tended to check-in when they felt funny
about new places. A1, A3, A4, A10, A11, A25 and
A26 shared their location information when they
arrived at a place of interest.
5.3.3 What Information Can Be Gained in
Friends’ Shared Location
Information?
Figure 2 presents the information that their friends
wanted to know by viewing the shared location. All
the participants chose the option “where my friend
has been”. 46% of the interviewees believed they
could know their friends’ opinions of the places.
15% of the interviewees chose the option “others”.
Moreover, A21 and A22 indicated that, “I can guess
what my friends are doing lately”. A5 mentioned
that “he is able to know the status of his friends
according to the location information shared on
social networking platforms”.
Figure 2: Information gained from friends’ shared location
information.
5.4 Applying Contextual Integrity to
Analyze the Privacy Concern
5.4.1 Potential Audiences
In the theory of contextual integrity, inappropriate
audience of a certain context could invade privacy
ICE-B2015-InternationalConferenceone-Business
206
(Barth et al., 2006). When the participants were
asked about potential audiences, they tended to use
authority management (A11, A13) to deal with
private issues with potential audiences. Six
interviewees said that, “If I do not want some friends
to see my location, I will block them to see my
location information”.
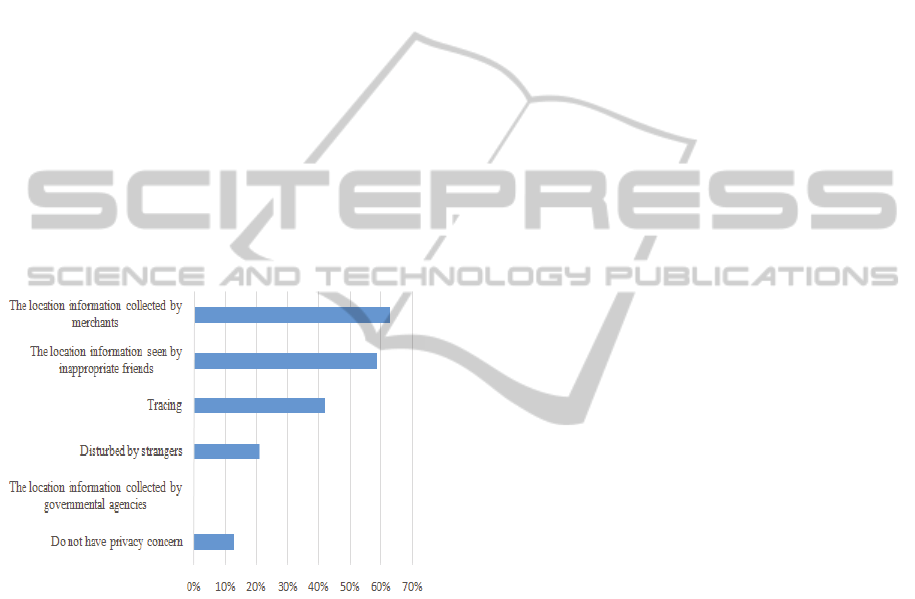
Figure 3 presents the privacy concerns of the
interviewees who have used the location sharing
service. Three of them said that they did not have
privacy concerns on using location sharing services
on social networking platforms. 63% of the
interviewees indicated that they were worried about
the issue that the shared location information could
be accessed by some unknown merchants. 58% of
the interviewees were afraid that the location
information could be seen by some unwanted
friends. 42% of the interviewees were concerned
about tracing by others, while 21% of the
interviewees were concerned about possible security
issues raised by strangers on social networking
platforms.
Figure 3: Privacy concerns of the interviewees who have
used the location sharing service.
5.4.2 Violation of Appropriateness
According to the previous research (Barth et al
(2006)), the type of information can influence
people`s judgment on whether the appropriateness
principle has been violated. When the users’ current
location is regarded as private, they are less likely to
discourse the location information to others.
When it comes to the appropriateness,
interviewees were asked to compare the difference
between WeChat and Weibo. Most interviewees
believed that WeChat did a better job than Weibo
with respect to the privacy issue (A2, A5). The
message posted on WeChat can only be seen by
verified friends, while the message posted on Weibo
can be seen by anyone. The number of interviewees
who tended to check-in on WeChat (44.4%) is more
than the number of interviewees who tended to
check-in on Weibo (18.5%).
5.4.3 Violation of Distribution
The principle of distribution is another important
concept in the contextual integrity theory. According
to the interviews, 13 users indicated that they did not
have private concerns when they were using location
sharing services on social networking platforms. A1
said, “I don’t have privacy concerns because I never
shared private location information on social
networking platforms”. Some interviewees who
have privacy concern said that they would ask his
friends to not re-post his massages any more or
delete the massage (A3, A12, A13, A15, A19, A21).
Other interviewees (A10, A18, and A23) chose to
limit their check-in behaviour because of possible
distribution of the shared private location
information.
6 CONCLUSION AND FUTURE
WORK
Our interviews with 43 users shed interesting
insights into how and why users use of location
sharing services on social networking platforms in
China. Four research questions were addressed in
this study. The key findings from this study were
summarized as follows. Firstly, our findings
indicated that most users were concerned about
privacy issues when they were using location
sharing services on social networking platforms.
This is in line with the previous research (e.g.,
Lindqvist et al. 2011). It suggests that the service
providers need to setup clear interpretations on how
users’ privacy concerns are protected in using
location sharing services on social networking
platforms. Secondly, we found many motivations as
to why users use location sharing services, including
fun, connecting with best friends, remembering daily
routines in peoples’ life. Thirdly, somewhat
surprisingly, some of the interviewees did not know
the location sharing services on social networking
platforms and did not know how to use them. The
social networking services providers need to have
some marketing campaigns to further promote
location sharing services to the end users. Fourthly,
with respect to privacy protection, most interviewees
indicated that WeChat did a better job than Weibo in
China. Last but not least, we found that users wanted
WhyandHowPeopleUseLocationSharingServicesonSocialNetworkingPlatformsinChina
207

to use authority management (A11, A13) to deal
with private issues raised by the shared location
information on social networking platforms.
However, we were also aware of some
limitations of this research. First, the sample in this
study was quite narrow in terms of age range since
all participants in our interviews were under 25
years old. This sample might not be fully
representative of the entire population in China. For
example, the generalizability of the findings to other
groups of users (e.g., older adults) remains to be
determined. Second, the self-reporting nature of this
study is another limitation. Last but not least, we
only studied location sharing services on two
popular social networking platforms in China. This
may limit the generalizability of our findings.
Continuing with this stream of research, we plan
to test other age groups to see the generalizability of
our findings in this study. Future research is also
needed to empirically examine potential factors
influence users’ adoption of location sharing
services in terms of a research model with larger
samples in China. We also would like to record
users’ historical behaviour on using location sharing
services to further analysis users’ usage patterns.
REFERENCES
Barth, A., Datta, A., Mitchell, J. C., & Nissenbaum, H.
2006. Privacy and contextual integrity: Framework
and applications. In the proceedings of 2006 IEEE
Symposium on Security and Privacy. IEEE Press.
Cramer, H., Rost, M., & Holmquist, L. E. 2011.
Performing a check-in: emerging practices, norms
and'conflicts' in location-sharing using foursquare.
In Proceedings of the 13th International Conference
on Human Computer Interaction with Mobile Devices
and Services. ACM.
Fusco, S. J., Michael, K., Michael, M. G., & Abbas, R.
2010. Exploring the social implications of location
based social networking: an inquiry into the perceived
positive and negative impacts of using LBSN between
friends. In the proceedings of 2010 Ninth International
Conference on Mobile Business and 2010 Ninth
Global Mobility Roundtable(ICMB-GMR), IEEE
Press.
Gao, S., Krogstie, J., & Siau, K. 2014. Adoption of mobile
information services: An empirical study. Mobile
Information Systems, 10(2).
Gao, S., Krogstie, J., Thingstad, T., & Tran, H. 2015. A
mobile service using anonymous location-based data:
finding reading rooms. The International Journal of
Information and Learning Technology, 32(1).
Grodzinsky, F., & Tavani, H. T. 2010. Applying the
“Contextual Integrity” Model of Privacy to Personal
Blogs in the Blogoshere, International Journal of
Internet Research Ethics, 3(1).
Kostakos, V., Venkatanathan, J., Reynolds, B., Sadeh, N.,
Toch, E., Shaikh, S. A., & Jones, S. 2011, Who's your
best friend?: targeted privacy attacks In location-
sharing social networks, in the Proceedings of the 13th
international conference on Ubiquitous computing.
ACM.
Lindqvist, J., Cranshaw, J., Wiese, J., Hong, J., &
Zimmerman, J. 2011. I'm the mayor of my house:
examining why people use foursquare-a social-driven
location sharing application. In the Proceedings of the
SIGCHI Conference on Human Factors in Computing
Systems. ACM.
Lipford, H. R., Hull, G., Latulipe, C., Besmer, A., &
Watson, J. 2009. Visible flows: Contextual integrity
and the design of privacy mechanisms on social
network sites. In the Proceedings of International
Conference on Computational Science and
Engineering, 2009. CSE'09. IEEE Press.
Lin, J., Benisch, M., Sadeh, N., Niu, J., Hong, J., Lu, B., &
Guo, S. 2013. A comparative study of location-sharing
privacy preferences in the United States and
China. Personal and ubiquitous computing, 17(4).
Li, M., Zhu, H., Gao, Z., Chen, S., Ren, K., Yu, L., & Hu,
S. 2014. All Your Location are Belong to Us:
Breaking Mobile Social Networks for Automated User
Location Tracking. In the Proceedings of the 15th
ACM international symposium on Mobile ad hoc
networking and computing. ACM.
Nissenbaum, H. 2004. Privacy as contextual
integrity. Washington law review, 79(1).
Shi, P., Xu, H., & Chen, Y. 2013. Using contextual
integrity to examine interpersonal information
boundary on social network sites. In the Proceedings
of the SIGCHI Conference on Human Factors in
Computing Systems. ACM.
Tsai, J. Y., Kelley, P. G., Cranor, L. F., & Sadeh, N. 2010.
Location-sharing technologies: Privacy risks and
controls. ISJLP, 6, 119.
Zimmer, M. 2008. Privacy on planet Google: Using the
theory of contextual integrity to clarify the privacy
threats of Google's quest for the perfect search
engine. J. Bus. & Tech. L., 3, 109.
Zhu, C., Wat, K. K., Fang, B., & Liao, S. S. 2012. Privacy
and Social Effects in Location Sharing Services. In the
proceedings of 2012 IEEE First International
Conference on Services Economics. IEEE Press.
ICE-B2015-InternationalConferenceone-Business
208
