Customer Tracking Systems based on Identifiers of Mobile Phones
D. M. Mikhaylov
1
, A. V. Zuykov
1
, S. M. Kharkov
1
, S. V. Ponomarev
1
, S. V. Dvoryankin
2
and A. M. Tolstaya
1
1
National Research Nuclear University MEPhI (Moscow Engineering Physics Institute),
Kashirskoe highway 31, 115409, Moscow, Russia
2
Concern Radio-Electronic Technology, Ltd, Moscow, Russia
Keywords: Non-Functioning Communication Cell, Counting Users by Mobile Phone Ids, Collection of Visit Statistics.
Abstract: Gathering statistics about visitors finds more and more applications in various fields of business and
commerce. This paper describes the system of impersonal counting of unique visitors by their mobile
identifiers. Counting is carried out using a non-functioning communication cell (the system does not provide
communication services to users of mobile networks). The system masks itself as the base station of a
mobile operator. Mobile devices automatically connect to the system even in case of a strong signal from
the towers of mobile operators. Once connected, the user identification data is received. The proposed
solution allows to compare data about the number of visits to a particular site in various periods of time and
to identify the re-occurrence of the visitors. The system is inexpensive and shows 99% accuracy in the
identification of users (compared to the real data about the visitors).
1 INTRODUCTION
It is well known in the industry of online shopping,
that collecting statistical data with further data
mining procedures can help in marketing of
products. In online shopping business it is quite easy
for a programmer with certain skills to store
information about pages that users of the shop
visited, how long did they stay on these pages, what
they actually purchased, etc. All these data are used
in analytics, the main task of which is to transform
the page, site navigation and functionality to
increase the sales.
At the same time, much more products are still
sold "offline" – in shops, malls, hypermarkets and
other places where data collecting is limited. In
digital form, the shop usually receives only
information about what was sold, how much goods
was sold on a specific day at a specific time, etc.
Therefore, the collection of statistics about
visitors finds more and more applications in various
fields of business. Many companies seek to obtain
reliable statistics on the number of visitors, duration
of eye contact with the product or advertising signs
and other indicators. These statistics can be used, for
example, to increase the efficiency of an advertising
campaign or to encourage the consumption of a
certain type of goods or services (Positioning 2015,
Mikhaylov 2014a).
Many scientific papers focus on the issue of
tracking visitors (Cai 2013, Mikhaylov 2014b,
Samoylov 2015, Wang 2014, Wang 2013).
However, a significant number of systems is aimed
at counting the number of people staying in the
room. (Types of counting systems 2015) There are
also powerful systems for analyzing the faces of
visitors, but the processing is carried out on a remote
server, or requires the use of a separate powerful
server (Audience Engagement 2015, Erns 2009).
For example, there is a well-known system
RetailNext (2015), which uses sensor technology
(cameras and radio frequency identification) for
counting visitors and traffic. DVR CountBOX
(2015) is designed to count visitors; it includes a
calculation STB-1 unit and a video camera. Counter
MC-Ethernet (2015) combines traffic to two
different channels – considers entrance and exit of
the visitors separately, which allows watching the
dynamics of entry and exiting traffic of the site.
Another system – Statistics Dome (2015) – is a
professional tool for counting visitors through
surveillance algorithms of Orwell 2k computer
vision. Video counter Statistics Dome effects a bi-
directional people counting with the help of built-in
video analytics.
Mikhaylov, D., Zuykov, A., Kharkov, S., Ponomarev, S., Dvoryankin, S. and Tolstaya, A..
Customer Tracking Systems based on Identifiers of Mobile Phones.
In Proceedings of the 7th International Joint Conference on Knowledge Discovery, Knowledge Engineering and Knowledge Management (IC3K 2015) - Volume 1: KDIR, pages 451-455
ISBN: 978-989-758-158-8
Copyright
c
2015 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
451
The disadvantage of such systems is the
omission of such problems as visiting of malls by
family customers, as well as a constant entry and
exit of buyers from the room several times. They are
also expensive and often inaccurate.
Therefore, it is proposed to use the system for
counting the identifiers of mobile phones to improve
the efficiency of the resulting statistics on the
number of unique visitors, for example, in the mall.
The objective of the system is to eliminate the above
flaws with the new system giving improved
performance.
2 COUNTING VISITORS BY
IDENTIFIERS OF MOBILE
PHONES
The proposed solution is based on non-functioning
communication cell. A non-functioning communi-
cation cell (NFCC) is an independent cell of the
cellular network, which generates a signal of a
mobile operator's base station, but it does not
provide access to communication services. NFCC
are successfully used for many civilian and military
applications.
At the same time, the real operator is an
officially registered service provider for the selected
user.
Customer tracking systems by identifiers of
mobile phones include:
non-functioning connection cell for receiving
data; wherein NFCC is associated with the
central server;
central server that analyzes received traffic,
wherein the server is connected to the central
computer of the operator;
computer of the operator, where there are reports
of new events in the system arrive.
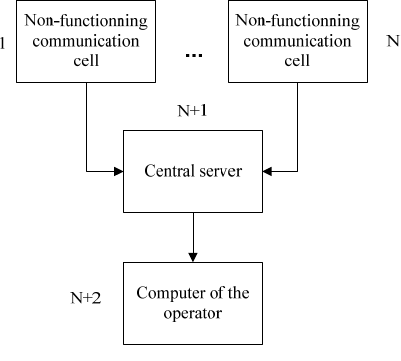
Figure 1 shows the structure of the system under
development. The number of NFCC can vary from 1
to N.
Inside the central server, to which the NFCC are
connected, an analysis of the data is carried out, but
the interim results of processing are not saved in the
memory of the equipment and the external memory.
The system is a non-functioning communication
cell, which is determined by the network as a base
station of a cellular operator, whereby the mobile
devices within the range of the complex will
automatically switch to work with it. Once
connected, there is a receipt identifying the user data
that are needed for the further calculation.
Figure 1: This caption has more than one line so it has to
be set to justify.
Further, the mobile device resumes functioning with
the network of its real operator. The central server,
when analyzing, can also identify the model of the
mobile device and the operator of the mobile device.
NFCC effects the switch of the mobile device to
collect identifying information even in case of a
good signal from the base station of the real operator
due to the high base station selection criteria (cell
selection and cell reselection criteria).
The described device does not allow any kind of
data transfer that is why the mobile devices
connected to the complex switch back to the
network of the real operator. This scheme of work
does not affect the quality of communication
services of the real service provider, so the complex
does not prevent the data transmission.
The system operates as follows: NFCC conducts
partial authentication, and after receiving the user
data for identifying the mobile device, switches back
to the base station of the operator. The system
allows keeping a record of the duration of a visit to
the selected area with up to six minutes accuracy. In
the case of inactivity, every six minutes a mobile
device of the subscriber updates its connection
status. Thus, it is possible to build the statistics
length of stay in the territory of the subscriber.
Automatic connection of mobile devices to the
NFCC within one standard connection occurs even
in the case of a strong signal from the towers of
mobile operators.
Figure 2 shows a schematic block diagram,
which can be realized by the proposed system of
counting visitors by identifiers of mobile phones.
Figure 2 shows:
1 – mobile device of the subscriber whose
identifiers are to be determined;
KDIR 2015 - 7th International Conference on Knowledge Discovery and Information Retrieval
452
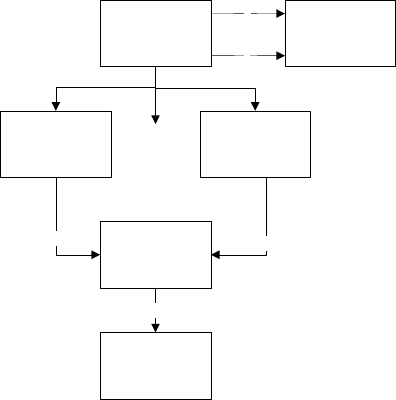
2 – base station of an operator to which the
subscriber's mobile device is connected;
3 ... N – NFCC working by standards 2G\3G\4G,
which switches the mobile device of the user (due to
better reception). It is necessary to create conditions
for switching the mobile device to the new base
station, thereby the mobile device performs a new
authentication in the network, providing the ability
to process the required IDs;
N + 1 – central server that handles the received
identifiers;
N + 2 – computer operator who receives the
anonymous analysis results.
Mobile device
Non-functioning
communication
cell
Non-functioning
communication
cell
Base station of
the operator
Central server
Computer of the
operator
...
3
3
4
1
1
2
2
3
N
N+1
N+2
5
Figure 2: Schematic block diagram of system
implementation.
A customer tracking systems by identifiers of
mobile phones works as follows:
Step 1 – In normal mode, the mobile device of
the subscriber is connected to the access point.
Step 2 – At a pre-set time the mobile device of
the subscriber changes the connection from the
base station of the operator to one of the N
virtual base stations, thereby performing
authentication of the new network, which
provides the possibility of receiving the desired
identifiers. This is achieved by using a special
radioreceiver of signals during a new
authentication of the mobile device in the
network when switching from one base
station to
another, due to forced creation of conditions for
the best quality signal.
Step 3 – Central server that is connected to N
non-functioning communication cells, processes
the information obtained.
Step 4 – Unallocated analysis results from a
central server are transferred to the computer of
the operator.
Step 5 – Once the correct identities of mobile
devices of subscribers are gathered, they switch
the connection from one of NFCC to the base
station of the real operator.
Thus, the system of counting the identifiers of
mobile phones allows determining the number of
unique visitors, without affecting the quality of
cellular connection. The system collects anonymous
data and does not receive any personally identifiable
information of the visitors.
In terms of information security the proposed
system can:
redirect packet traffic in the data leak prevention
(DLP) system;
record all calls with copies of conversations sent
to DLP system;
control of SMS messages;
control of employees presence on the workplace;
selective blocking of subscribers;
mass dispatch of SMS notifications.
It is possible to develop the client for the mobile
operating systems Android, iOS, Windows Phone,
with integrated DLP system that will allow to block
camera, microphone and sending images.
There are several spheres of the system
application, for example:
marketing research, integration with loyalty
programs;
communication systems;
protection systems from data leakage (DLP
systems);
intelligent connection blocking with no threat to
health;
security systems, physical security of facilities.
The latter has the following advantages:
large coverage area, it is advantageous to use for
the control of remote objects and sparsely
populated areas (pipelines, electrohighways,
border, etc.);
possibility of drawing up white lists, operation in
mode “friend/foe”;
ability to identify the offender (in case of special
permissions).
3 EXPERIMENTAL DATA
To test the effectiveness of the developed system for
counting mobile phone identifiers a special territory
Customer Tracking Systems based on Identifiers of Mobile Phones
453
was allocated. It was a bandwidth monitoring area of
200 m2 and 20 employees. Control of access to the
territory was carried out by using access cards,
allowing us to conduct a comparative analysis of the
system.
As a part of the experiment, which was
conducted during five weeks, antennas and amplifier
were installed around the perimeter of the zone so as
to completely cover-control it. For ease of testing,
the system was set up for one mobile operator (the
employees who worked in the territory, used the
services of the same operator). The results of the
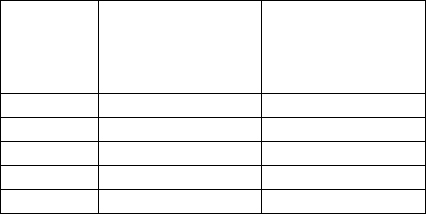
experiment are given in Table 1.
Table 1: Results of the experiment of counting visitors.
Timeline NFCC inspection
results
(entrance to the
facility)
Access cards
inspection results
(entrance to the
facility)
1 week 586 578
2 weeks 565 563
3 weeks 586 586
4 weeks 574 569
5 weeks 592 589
During the entire time of the experiment, the
system shows stable operation. The results obtained
with the help of NFCC were compared with the data,
fixed by means of electronic access cards to the
territory. The results do not differ by more than 1%.
Inaccuracy is due to the fact that some employees
had a tablet with access to the Internet or a second
cell phone while being at the controlled territory.
4 CONCLUSIONS
Thus, this paper describes a system of impersonal
counting of identifiers of mobile phones, which
would greatly increase the efficiency of counting
unique visitors in shopping malls, exhibitions and
other similar events. The system requires a small
financial cost for its installation and operation, it
does not affects the quality of services provided to
users by the operator of communication and has no
adverse impact on the information security of mobile
devices.
Ongoing testing of the prototype system
demonstrated its high efficiency, where the accuracy
of the results obtained by the device is 99%
compared to the actual data. In the future, this figure
will be increased to 100%.
The limitations of the study are the following:
legal difficulties as there is no regulation of use
of such devices, albeit low-power, at frequencies
of mobile operators;
the system only supports the 2G (GSM), other
cellular standards are not supported. It is
necessary to develop a system or jammers for
them. But the latter encounter legal difficulties.
Today, the system is being tested and further
developed. It is planned to conduct scientific
research to address the problem of the calculation of
several unique devices from one owner (for
example, the visitor has two mobile phones and a
tablet).
The scalability of the system described will also
be examined.
REFERENCES
Positioning (2015) Marketing tools and sales. Official site
of Development Program of the Small Business in
Saint-Petersburg. Committee for economic
development, industrial policy and trade of
Administration of St. Petersburg. URL:
http://www.spb-mb.ru/index.php?page=286.
Dmitry Mikhaylov, Timur Khabibullin, Andrey
Starikovskiy, Alexander Smirnov, Mikhail Froimson,
Maxim Aristov and Vladimir Konev (2014a) Method
and System for Gender-oriented Targeted Advertising.
ICORES 2014. Proceedings of the 3rd International
Conference on Operations Research and Enterprise
Systems. ESEO, Angers, Loire Valley, France. 6 - 8
March, 2014. Pages 153-158.
Zhaowei Cai; Longyin Wen; Dong Cao; Zhen Lei; Dong
Yi; Li, S.Z. (2013) Person-specific face tracking with
online recognition. 10th IEEE International
Conference and Workshops on Automatic Face and
Gesture Recognition (FG), 2013. Pages: 1 – 6.
Dmitry Mikhaylov, Anton Samoylov, Peter Minin and
Alexey Egorov. (2014b) Face Detection and Tracking
from Image and Statistics Gathering. Tenth
International Conference on Signal-Image Technology
& Internet-Based Systems, 2014. С 37-42.
Samoylov A.S., Mikhaylov D.M., Minin P.E., Egorov
A.D. (2015) Face Tracking for a System of Collecting
Statistics on Visitors and Quality Assessment of its
Functioning. Journal of Theoretical and Applied
Information Technology. Volume 71, Issue 3, 31
January 2015, Pages 353-366.
Guojun Wang; Alam Bhuiyan, M.Z.; Jiannong Cao; Jie
Wu. (2014) Detecting Movements of a Target Using
Face Tracking in Wireless Sensor Networks. IEEE
Transactions on Parallel and Distributed Systems,
(Volume: 25, Issue: 4). April 2014. Pages: 939 – 949.
Chao Wang; Yunhong Wang; Zhaoxiang Zhang; Yiding
Wang. (2013) Face Tracking and Recognition via
Incremental Local Sparse Representation. Seventh
KDIR 2015 - 7th International Conference on Knowledge Discovery and Information Retrieval
454
International Conference on Image and Graphics
(ICIG), 2013. Pages: 493 – 498.
Types of counting systems. (2015) Unique electronic users
accounting system. Counters of visitors. URL:
http://www.uchet.biz/vidy-sistem-podscheta-
posetitelei.php.
Audience Engagement. (2015) Intel AIM Suite. URL:
https://aimsuite.intel.com/aim-suite-work/audience-
engagement.
Ernst A., Ruf T. Kublbeck C. (2009) A modular
framework to detect and analyze faces for audience
measurement systems. Proc. GI Jahrestagung, 2009.
Pages: 3941-3953.
RetailNext (2015) Official website. URL:
http://retailnext.net.
CountBOX (2015) Official website. URL: http://count-
box.com.
The system of visitors counting MC-Ethernet (2015) "The
first BIT". URL: http://www.kkm.ru/shop/anti-
steal/sistemy-podscheta-posetiteley/sistema-
podscheta-posetiteley-megacount/44055.
Statistics Dome (2015) Official website. URL:
http://подсчет-посетителей.рф.
Customer Tracking Systems based on Identifiers of Mobile Phones
455
