
Design of Trust Model based on Cloud Computing
Ping HE, Jing QIU, Yan YI, Jianchun CAI and Zucheng DAI
Department of Physical Science and Technology, Kunming University, Kunming, China
heping0871@qq.com
Keywords: Cloud Computing, Information Security, Trust Management, Trust Level.
Abstract: Cloud computing is a kind of burgeoning new business models and infrastructure, but the characteristic of
openness, flexibility, and the public availability, to the application security has brought about many
challenges. In this paper, by analyzing the current cloud computing, trust and trust management, and other
technology, corresponding to the level of trust model based on behavior of cloud computing environment
was given. According to user's behavior dynamically and trustworthiness of value, to determine the user's
confidence level, further to control the corresponding behavior of users and permissions, it can guarantee
the safety and reliability of the cloud computing system in order to standardize management and guide
users.
1 INTRODUCTION
With the development of information technology
innovations, computer industry has become a new
variety and practical technologies, cloud computing
technology is one of them. Cloud computing is
based on Internet, using virtualization technology, a
large amount of storage resources, software and
computer resources come together, forming a giant
warehouse shares IT resources for remote cloud
provides users with information services that meet
their needs. From another perspective, cloud
computing makes IT much lower operating costs and
costs of services, and accelerating the deployment of
services and improve the convenience of the service.
Although cloud computing industry has a bright
future, now the potential risks and safety issues of
cloud computing have become the main problem
restricting the development. At present, in the
settlement of the security issues of cloud computing,
have emerged in many ways and ideas. With the
emergence of emerging trusted computing, trusted
computing is used in information security more and
more, use trusted computing to protect systems and
hardware technologies have become more
sophisticated, the traditional information security
will be further developed as a service of trust and
confidence between the parties and served on
management. This paper aims to analyze the current
technologies such as cloud computing, trust
management, presented corresponds to a cloud
computing environment based on behavior model of
trust rank, to calculate the user's trusted values
dynamically based on user behavior, which
determines that the user's trust level, to further
control user behavior and authority, to regulate and
guide the user, improve the safety and reliability of
cloud computing systems.
2 CLOUD COMPUTING
2.1 Putting Forward of Cloud
Calculation and Its Development.
After computers, Internet, cloud computing is yet
another wave of innovation in the field of
information. Although cloud computing's time is not
long, its sudden rise and network applications is
related to the transition, many of its ideas were
involved in grid computing, utility computing,
clustering technology, distributed systems
technologies are relatively mature technology.
Therefore, from the other aspects of that cloud
computing can be seen as the technology upgrades.
Then, after a series of promotional development,
mainly through mode in power plant, utility
computing, grid computing and cloud computing
four relatively mature stage of development to the
present level. After following the change of the
personal computer and the Internet, cloud computing
is seen as another wave of IT, have great market
100
100
HE P., CAI J., YI Y., QIU J. and DAI Z.
Design of Trust Model based on Cloud Computing.
DOI: 10.5220/0006019801000104
In Proceedings of the Information Science and Management Engineering III (ISME 2015), pages 100-104
ISBN: 978-989-758-163-2
Copyright
c
2015 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

prospects, it will bring people, mode of life and
fundamental change in the business model. With the
development of related technologies, cloud
computing applications in business has become a
reality. At present, the cloud computing industry is
gradually growing, and its benefits is increasing day
by day.
2.2 Information Safety of Cloud
Computing.
In the Internet, security is the eternal topic. At
present, many critical problems facing the
development of cloud computing, and security issues
first. With the growing popularity of cloud
computing development, the importance of security
issues on an escalating trend, more and more
companies because of the security issues in cloud
computing took a wait-and-see attitude. According
to the IDC report, there are more than 74% users
think the main causes of security problems is to limit
the development of cloud computing. Thus, cloud
computing security problems have been widespread
concern in the industry, and in order to better
develop cloud computing, many institutions,
research groups and standardization organizations
carry out appropriate research.
At present, cloud security products are many,
mainly dominated by traditional IT antivirus
enterprise. With the emergence of emerging trusted
computing, trusted computing is used in information
security more and more, using trusted computing
technology to guarantee the security of systems and
hardware technology is more and more mature. With
the development of cloud computing, we have
reason to believe that, in the near future, we will find
a practical and highly effective way to make sure
cloud computing security.
3 TRUST MANAGEMENT
3.1 Definition of Trust and Its Property
The definition of trust. Trust management can be
divided into two kinds, one kind is based on the
strategy of trust management, and the other is a trust
management based on behavior. M.B laze trust
management belongs to the former, it uses static
authentication mechanism to determine
authorization, the research focuses on the certificate
authentication, encryption and access strategy, etc.
The disadvantages of it can not be timely and
effective way of dealing with entities trust
relationship changes. Once the entity is endowed
with a certain identity and authority, the entity in the
process of access will have the authority, suddenly
broken entity can use the authority to make illegal
behavior, is not able to make a timely response
system.
3.2 Content and Classification of Trust
Managements
3.2.1 Contents of Trust Managements
Trust management (TM) this concept was started by
M.Blaze and others for open distributed systems,
distribution and dynamic characteristics, link
between the trust and access control, used to resolve
credibility, uncertain security in your environment.
Trust management is defined as: adopt a unified
method to describe and explain the security policy,
security trust certificates and trust relationship . Its
basic principle is to use scientific methods to
describe, handling systems complex trust
relationships. Common trust models are Sun'S
model,Claudiu'S model .
3.2.2 Classifications of Trust Managements
Trust management can be divided into two kinds,
one is policy based management, another is based on
the behavior of trust management.
Submitted by M.Blaze trust management belong
to the former, it uses static verification mechanism
to determine authorization, whose research is
focused on certificate authentication, encryption, and
access policies. Its disadvantage is that you cannot
trust relationships of the entities to respond
effectively to changes in a timely manner. Once the
entity has been endowed with a certain identity and
permissions, then the entity during his visit will have
that authority, suddenly broken entities may use this
authority to make illegal, and the system is unable to
make timely responses.
Behavior-based trust-management will be based
on the entity's historical behavior dynamically
adjusts its trust, trust relationships between two
entities is updated in real time, to better adapt to the
changing environment of cloud computing.
Therefore, by using a trust model based on behavior
to solve access issues between the entities in cloud
computing.
Design of Trust Model based on Cloud Computing
101
Design of Trust Model based on Cloud Computing
101

4 TRUST HIERARCHY BASED
ON BEHAVIOR MODELING
4.1 The Basic Idea of Trust Model
based on Behavior
Trust hierarchy based on behavior model's basic idea
is through behavior, or is the result of an entity
arising out of acts, the trusted values obtained from
the General computing entity, and on this basis to
determine or change the trust level of an entity,
further changes to the current entity roles and
permissions, in order to achieve a single entity or
even the whole cloud computing systems are
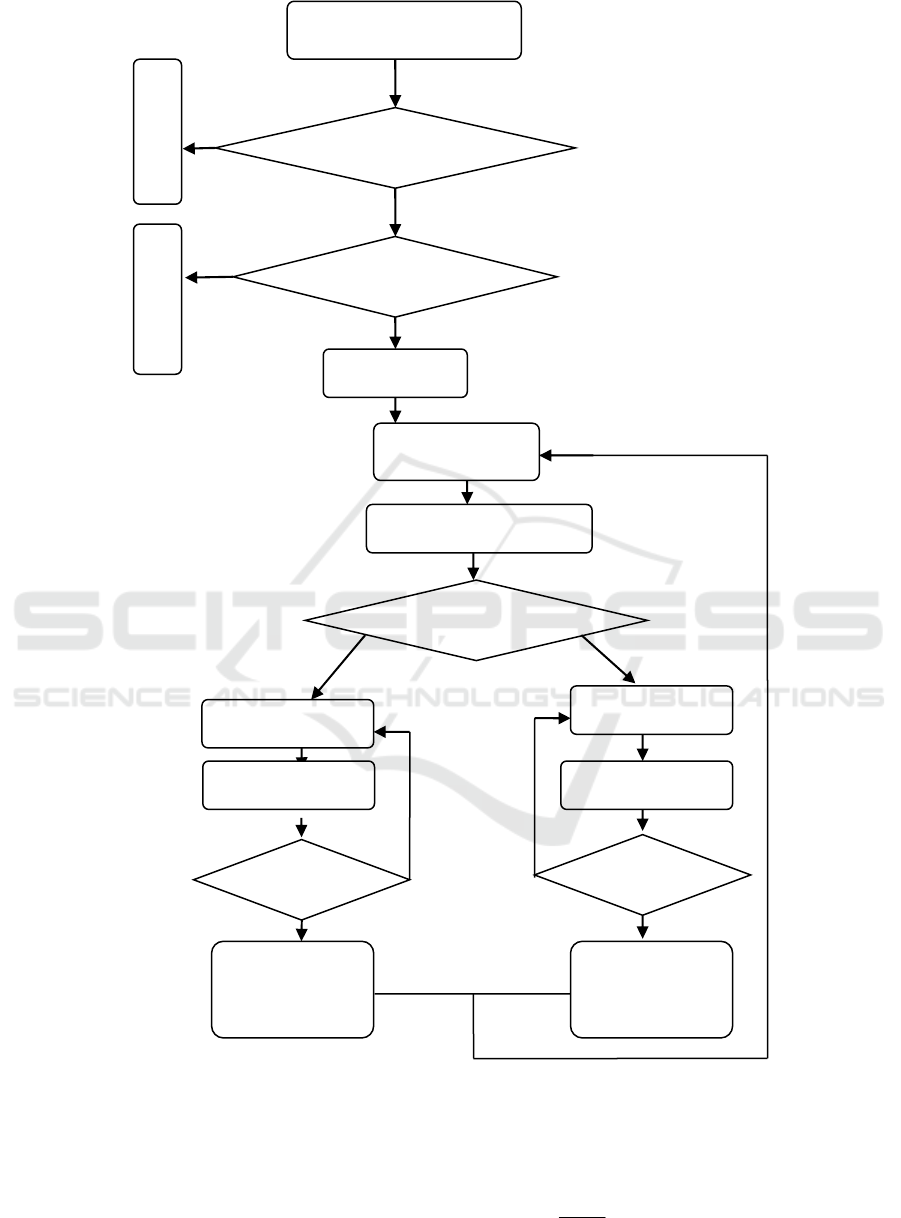
monitored and protected. Principle is shown in
Figure 1.
4.2 Trust Model based on Behavior
Management Strategies
This model in cloud server in the of entity of trust
grade by a Trust Center to unified management,
dang user login cloud server completed identity
validation Hou, Trust Center will view user of
current trust grade, if trust grade below minimum
service grade (minimum service grade, that critical
grade, if trust grade again declined, server on
refused to the user using), is cloud server will
refused to for user through cloud service; actual
operations in the, dang user trust grade was reduced
to minimum service grade Shi will received warned
information If trust levels belonging to the service
level, Trust Center will notify the cloud continues to
provide cloud services. Cloud in cloud services to
provide users in the process also will monitor and
audit user actions, users of a variety of risk
behaviors (such as entity attempts unauthorized
operations) can be recorded, through analysis and
calculations, changing the user's trusted, and has the
potential to affect the trust level, and change the user
role properties, permissions will be reassigned.
Adoption of this model is the core of credible entity
acts as well as changes in trust level, which affects
the user permissions.
5 USER-TRUSTED VALUE
CALCULATION METHOD
5.1 User Behavioral Evidence
Acquisition
Credible terms in this article are based on entity
behaviors, or is an entity acts as a result of the entity.
Cloud services providers can be based directly on
hardware and software detection method to obtain
the user's behavior, to quantitative assessment of
consumer confidence in the overall behavior of
Foundation for cloud computing services value the
result itself is objective, does not have the subjective
characteristics of trust. Cloud computing service
provider has the right to full control over cloud
resources, trade secrets and privacy of users and
cloud-based services as well as external purposes
provided by considering the cloud service providers
must not view the user's data content, are virtually
impossible to vast amounts of data for detailed
inspection. However, the huge monitor relies on user
behavior characteristic of network traffic and find
statistics of users ' behavior. Currently available for
obtaining user behavior evidence there are main
methods of the following kinds:
(1) use network traffic monitoring and analysis
tools, such as the Bandwidthdl, each gateway
protocols are available for more lP flow, view
network status, such as: the rate of packet
transmission and reception.
(2) use intrusion detection systems currently
available, such as RealSecttr, can obtain access
times, operating failures and delays.
(3) using the audit trail system to generate system
event log and record user behavior, including system
Ft log Ft log records, applications, network
management, and audit logs capture user data
packets, and accordingly records.
(4) according to the Protocol (for example,
RMON,SNMP) of developed software.
(5) with hardware access to evidence, such as the
NetScout2 company's hardware probe
(6) not detected evidence that other methods may
be used for research, for example, can be based on
evidence of previous users reasoning and prediction.
5.2 User Behavior Trust Hierarchy
Entity representation of the result mainly in the
following three ways:
(1) percentages. Including user behavior and a
similar level expressed as a percentage of the
common attacks, less qualified, credible level
percentage greater trust levels higher.
(2) a Boolean. Only two trust levels. Exists, then
the trusted level 1 of the project; does not exist, then
the project credible level of 0.
(3) specific value within a certain range.
According to an action by a range of properties for
ranking.
ISME 2015 - Information Science and Management Engineering III
102
ISME 2015 - International Conference on Information System and Management Engineering
102
Accumulation of
suspicious behavior
Audit information analysis
real-time monitoring
Suspicious behavio
r
judgment
credit rating
downgrad Role to
redistribute
yes no
n
o
reach the
threshold
Accumulation of
safe use
Confidence value
decreases
Confidence value
increases
n
o
reach the
threshold
credit rating go up
Role to redistribute
Entity requests to connect
to the server
Server
authentication
Decides the grade of
trust
Provide service
Authentication
F
a
il
ed
succ
e
ssful validation
Not less than minimum
service levels
Under minimum
service level
access denied
denial of service
Figure 1: The level of trust model based on behavior principle diagram.
The entity behavior of above three kinds of forms
result, can set trust grade of manifestation.It is 1 to
can believe a value[0, 1] numbers, therefore, need to
pass to return one the method for turning to acquire
each trust grade to should of can letter
value.Suppose original behavior result the Di
assigned Ni reputation grade, but current behavior
result reputation grade is Mi, then Di of can believe
value Ti=
i 1
1
i
M
N
−
−
.
Design of Trust Model based on Cloud Computing
103
Design of Trust Model based on Cloud Computing
103

Can believe the calculation method of value. The
entity behavior that establishes to need an
investigation is a Dl, D2 and D3......Dn, the result of
each behavior Di assigned Ni trust grade, the
behavior result of current record is Mi:(Mi ∈ [0, Ni-
1])Each power of behavior Di heavy coefficient is a
Yi(Yi ∈ and), then can get the following calculation
the entity can believe the formula of being worth the
T:
n
11
1
1
n
i
ii i
i
ii
M
TYDY
N
==
−
==
−
∑∑
Among them, the weight coefficient of Yi can be
obtained by the analytic hierarchy process.
Hypothesis requires investigation and collecting
evidence for the Dl, D2, D3, ... ... Dn, we can use the
comparison one by one, determined that n
behavioral evidence, and any comparison of the two.
6 CONCLUSION
With the popularity of cloud computing
technologies, and the openness and flexibility of
cloud computing, virtual properties and public
availability, brought many challenges to application
security. Combining cloud computing security
problems facing the proposed trust model based on
behavior, and gives users confidence value
calculation method.
ACKNOWLEDGEMENTS
This material is based upon work supported by the
National Science Foundation of China (NSFC, grant
no.51402138), and College Students' Innovation and
Entrepreneurship Training Plan in Yunnan Province
(grant no. 201311393004). Department of Yunnan
Education:2015Y395
REFERENCE
Zhang Yunyong, Chen Qingjin, Pan Songbai, Wei Jin wu.
Cloud computing security key technology analysis [J].
Journal of telecom science, 2010 (9)
Gao Yunlu, Shen Bei army, Kong Huafeng. Cloud
computing trust model based on SLA and user
evaluation [J]. Computer engineering 36 (7), 2012 (4)
T.Dimitrakos. System Models, E-risk and E-trust towards
Bridging the Gap?In:Towards the ESociety: E-
Business, E-Commerce,and E-Government, eds.
B.Schmid, K. Stanoevska-Slabeva, V. Tschammer.
Kluwer Academic Publishers. (2001).
D.H. McKnight, N.L. Chervany, Conceptualizing Trust: A
Typology and E-Commerce Customer Relationships
Model, 34thAnnual Hawaii InternationalConference
on System Sciences (HICSS-34)-Volume 7,01 03-
01,2001,pp.7022-7031.40
T.Grandison& M.Sloman. A Survey of Trust in Internet
Applications.IEEE Commtmications Survey and
Tutorials. 2000.
R.C.Mayer, J.H.Davis, D.F.Schoorman. An Integrative
Model of Organizational Trust [J]. The Academyof
Management Review, 1995, 20(3):709-734.
Sun Y L, Yu W, Han Z, et al. Information theoretic
framework of trust modeling and evaluation for ad hoc
networks[J]. Selected Areas in Communications,
IEEE Journal on, 2006, 24(2): 305-317.
Blaze M, Feigenbaum J, Lacy J. Decentralized trust
management[C]//Security and Privacy, 1996.
Proceedings., 1996 IEEE Symposium on. IEEE, 1996:
164-173.
Kaelbling L P, Littman M L, Moore A W. Reinforcement
learning: A sur\ey[J].arXiv preprint cs/'9605103.
1996.
Yi Tieguo, Tian Liqin, Hu Zhixing,Sun Jinxia. Trusted
network a user behavior assessment based on AHP
method [J]. Computer engineering and application,
2007 lancet (19) : 123-126.
Lv Shenjuan zhang yongsheng, LouYinghong, Zhang
Yandong, Tian Ming. Credible technology research
based on cloud theory [J]. Computer application
technology, 2013, 30 (8) : 2523-2526.
Liu Liang ,Zhou Dejian ,Xie Xiaolan etc. Service trust
evaluation model based on cloud computing [J].
Journal of software Tribune, 2011, 10 (5) : 75-77.
li feng-hua, Wang Wei, Ma Jian-feng,etc. The access
control model based on behavior and its behavior
management [J]. Journal of electronics, 2008, 3 (10) :
1881-1890.
ISME 2015 - Information Science and Management Engineering III
104
ISME 2015 - International Conference on Information System and Management Engineering
104
