
Achieving Lightweight and Fine-grained Access Control in
Mobile Cloud Computing
Heng He
1, 2
, Chuan Tian
1, 2
, Yu Jin
1, 2
, Wei Xia
1, 2
and Yadan Wang
1, 2
1
College of Computer Science and Technology, Wuhan University of Science and Technology, Wuhan, China
2
Hubei Province Key Laboratory of Intelligent Information Processing and Real-time Industrial System, Wuhan, China
{heheng, jinyu}@wust.edu.cn, {tianchzx, wydwust}@163.com, xiawei137hao@sina.com
Keywords: Access Control, Attribute-based Encryption, Mobile Cloud Computing.
Abstract: Mobile cloud computing has emerged as one of the most promising technologies, which can greatly enlarge
the application range of mobile devices by moving data storage and processing to powerful and centralized
computing platforms located in clouds. However, how to keep data security and data privacy is an important
and challenging issue when users outsource their sensitive data to mobile cloud for sharing. In this paper,
we present a novel lightweight and fine-grained data access control scheme based on attribute-based
encryption for mobile cloud computing. The analysis shows that the proposed scheme can meet the security
requirement of mobile cloud computing, and provide flexible and expressive data access control policy.
Furthermore, it has less computation cost compared with other schemes.
1 INTRODUCTION
With the fast development of wireless network and
cloud computing (Mell and Grance, 2011)
technology, mobile cloud has become the primary
computing platform for many users because of the
widely used mobile devices. However, security
issues have been the top concern when users store
sensitive data (such as photos, videos and app data)
in the mobile cloud. Maintaining confidentiality and
privacy of the data becomes a challenging task
(Chen and Zhao, 2012). Since cloud servers are
operated by commercial providers who are usually
outside of the trusted domain of users, they are not
entitled to access the confidential data. Furthermore,
there are cases in which users (i.e. data owners)
publish data in the cloud for sharing and need fine-
grained data access control in terms of which users
(i.e. data consumers) have the access privilege to
which types of data (Yu et al., 2010).
Data access control has been well studied and
various techniques have been developed to specify
differential access rights for individual users.
Traditional access control schemes assume that the
servers are fully trusted by data owners and let the
servers enforce all access control policies
(Kallahalla et al., 2003), (Di Vimercati et al., 2007).
However, this assumption no longer holds in cloud
computing. To achieve access control of data stored
on untrusted cloud servers, a feasible solution would
be storing encrypted data.
A recently proposed access control model, based
on Ciphertext-Policy Attribute-Based Encryption
(CP-ABE), defines access control policies based on
the attributes of the user (Bethencourt et al., 2007).
CP-ABE is a public-key cryptography primitive that
was proposed to achieve the attribute-based access
control on untrusted storage. Compared to previous
works, CP-ABE can achieve the fine-grainedness of
data access control and meanwhile be efficient. In
CP-ABE, the complexity of encryption and key
management are independent from the number of
system users, and is just related to the number of
system attributes. There are some related schemes
which exploit CP-ABE to enforce fine-grained data
access control in cloud systems (Hur and Noh, 2011),
(Ibraimi et al., 2009), (Wang et al., 2010). However,
most of these schemes are designed for traditional
cloud computing and they cannot be directly applied
in mobile cloud computing, which will bring heavy
computation overheads to mobile devices.
In this paper, we propose a secure and
lightweight data access control scheme for mobile
cloud computing. In the following of the paper we
refer to our scheme as LF-ABE. By greatly reducing
the computation overheads in the process of
encryption and decryption, LF-ABE can achieve
510
510
He H., Jin Y., Tian C., Wang Y. and Xia W.
Achieving Lightweight and Fine-grained Access Control in Mobile Cloud Computing.
DOI: 10.5220/0006029605100515
In Proceedings of the Information Science and Management Engineering III (ISME 2015), pages 510-515
ISBN: 978-989-758-163-2
Copyright
c
2015 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

high efficiency of the system compared with the
previous related schemes. Meanwhile, it provides
flexible and expressive data access control policy.
Furthermore, most of the computing cost are
outsourced to the cloud, which can greatly decrease
the computing overhead on mobile devices.
2 PRELIMINARIES
2.1 CP-ABE
CP-ABE is proposed by Bethencourt, Sahai and
Waters. It is a variant of Attribute-Based Encryption
(ABE) (Sahai and Waters, 2005). In CP-ABE, each
user is identified with a set of attributes, and users
need to register with the Trust Authority (TA), who
is responsible for publishing the universe attributes
and generating the related keys (including public
key, master key and users’ secret keys). An attribute
can be any descriptive string that defines, classifies,
or annotates the user, to which it is assigned. Each
user’s Secret Key (SK) is associated with his
attributes. When Data Owner (DO) encrypts a
message, he specifies an associated access policy
tree over attributes, which is embedded into the
ciphertext in the process of encryption. The access
tree is used to descript an access policy that specifies
which combination of attributes can decrypt the
ciphertext. Let tree T whose root node is r represent
the access policy. Each inner node of T is a logic
operator, such as “AND”, “OR” and “OF”, while
each leaf node represents an attribute. According to
the idea of secret sharing, each node of the access
tree represents a secret. In the encryption phase, we
need to top-down recursively assign a secret to each
node. While in the decryption phase, we need to
bottom-up recover the secret of the root node. A user
will only be able to decrypt a ciphertext if that user’s
attributes pass through the ciphertext’s access tree.
2.2 Bilinear Map
Let G
0
and G
1
be two multiplicative groups of prime
order p, Q is a generator of G
0
. Map e: G
0
G
0
G
1
is a bilinear map with the following properties:
Bilinear: for all a, b
*
p
Z
and R, S G
0
, we have
e(R
a
, S
b
) = e(R, S)
ab
.
Non-degenerate: e(Q, Q) 1.
Computable: the group operation in
G
0
and the
bilinear map e are both efficiently computable.
In addition, the map
e is symmetric:
e(g
a
, g
b
) = e(g, g)
ab
= e(g
b
, g
a
).
2.3 Shamir's Secret Sharing Scheme
In Shamir's secret sharing technique (Shamir, 1979),
a secret s is divided into n shares in such a way that
any subset of
t shares, where t n, can together
reconstruct the secret; no subset smaller than t can
reconstruct the secret. The technique is based on
polynomial interpolation where a polynomial
y = f (x)
of degree t-1 is uniquely defined by t points (x
i
, y
i
).
The details of the scheme are as follows:
1. Setup. The dealer
D wants to distribute the
secret
s > 0 among t users.
1)
D chooses a prime p > max (s, n), and defines
a
0
= s.
2)
D selects t-1 random coefficients a
1
, ..., a
t-1
, 0
a
j
p-1, and defines the random
polynomial over
Z
p
,
1
0
()
t
j
j
j
f
xax
.
3)
D computes s
i
= f(i) mod p, and sends
securely the share s
i
to user p
i
, together with
the public index i.
2. Pooling of Shares. Any group of
t or more users
pool their distinct shares (
x, y) = (i, s
i
) allowing
computation of the coefficients a
j
of f(x) by
Lagrange interpolation,
1
0
() ()
t
j
i
f
xlx
,
where
1,
()
j
j
jtji
ij
x
x
lx
x
x
. The secret is f
(0) = a
0
= s.
3 LF-ABE
3.1 Scheme Overview
As it is known, due to the differences in hardware
and platforms, computing capabilities of the mobile
device is far weaker than the desktop PC. It is
difficult for lightweight mobile devices to finish the
encryption and decryption operations of CP-ABE on
their own. To reduce the computation overheads at
mobile client, we take consideration of securely
outsourcing computation intensive CP-ABE
operations to Encryption Cloud Service (ECS) and
Decryption Cloud Service (DCS) located in cloud.
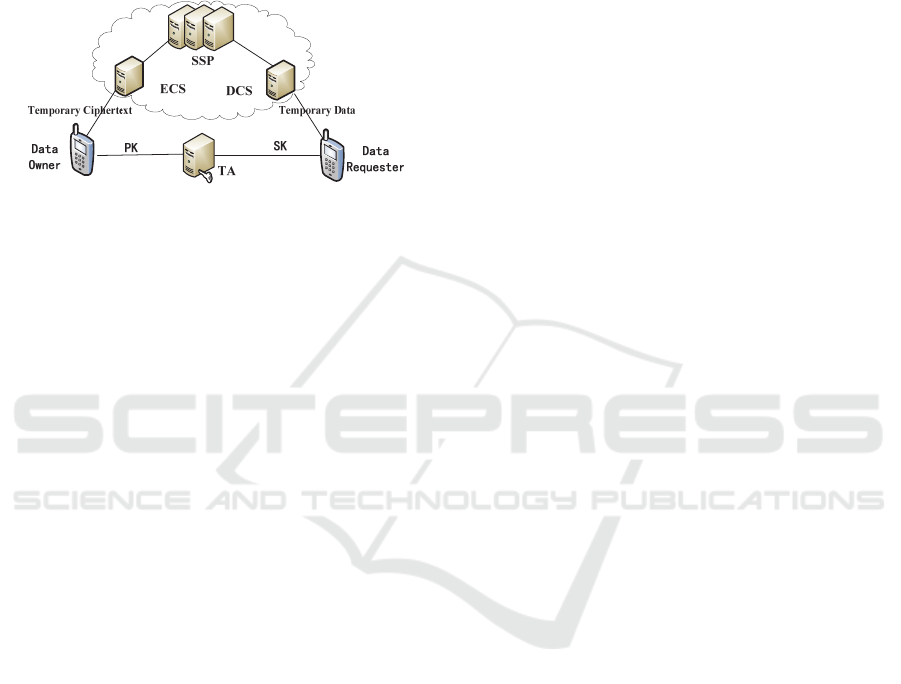
Figure 1 gives the framework of LF-ABE.
We construct our LF-ABE scheme based on
Ibraimi’s CP-ABE algorithm (EPS-ABE) (Ibraimi et
al., 2009) since it is very secure and efficient. The
encryption complexity grows linearly on the size of
Achieving Lightweight and Fine-grained Access Control in Mobile Cloud Computing
511
Achieving Lightweight and Fine-grained Access Control in Mobile Cloud Computing
511
access policy. For the purpose of outsourcing the
computation cost at mobile client, we define a
virtual attribute which is owned by every user. We
denote the virtual attribute as Att
Vir
. The access tree
T is constructed by T
Pol
and T
Vir
, and they are
connected with an “AND” operator, that is T = T
Pol
T
Vir
. T
Pol
is the real access policy, while T
Vir
only
contains Att
Vir
.
Figure 1: The framework of LF-ABE.
First, we utilize Shamir's secret sharing
technique to assign each leaf node of the access tree
a secret s
i
. Specially, denote the secret of Att
Vir
as
s
Vir
. Then, we use each leaf node’s secret to perform
a point multiplication operation which is used to
encrypt the file. The number of point multiplications
grows linearly on the number of the leaf nodes.
Apparently, the leaf nodes in T
Vir
are far less than
those in T
Pol
, so the point multiplication operations
in are far less than T
Vir
. To outsource the
computation cost of mobile client, DO sends each s
i
in T
Pol
to ECS, then ECS performs the point
multiplication operations and returns a temporary
ciphertext, while DO only needs to make use of s
Vir
to perform point multiplication operation once at
mobile client.
In the decryption phase, the bilinear pairing
operations over ciphertext and private key take
heavy overhead. Denote every secret key component
as D
i
and Data Requester (DR) sends each D
i
except
D
Vir
to DCS. Then, DCS runs the decryption
algorithm to compute a temporary data, and returns
it to DR. Finally, DR takes advantage of the
temporary data and D
Vir
to recover the real file
locally.
3.2 The Construction of LF-ABE
LF-ABE consists of four algorithms. The detailed
construction of LF-ABE is as follows:
1) Setup (k). TA runs the setup algorithm to
generate a system Public Key (PK) and a system
Master Key (MK). The input is a security
parameter k which determines the size of the
groups. This algorithm generates an elliptic
curve group G
0
of prime order p with a generator
Q, which is a point on the elliptic curve. The
bilinear map is e: G
0
G
0
G
1
. Then, generate
the universe attribute set
= {a
1
, a
2
, …, a
n
}.
Note that each user’s attribute set contains a
virtual attribute. Next, it chooses a random
elemen t
j
Z
p
for each attribute a
j
in
. Then, it
selects the last random element
Z
p
. Finally,
it generates PK and MK as follows:
PK = (G
0
, Q, e, y = e(Q, Q)
, T
j
= t
j
Q(1 j n))
MK = (
, t
j
(1 j n))
Every party can get access to PK while MK is
secretly held by TA and not published.
2) KeyGen (
, MK). TA runs the key generation
algorithm, which takes as input the master key
MK and a set of attributes that describe the
identity of the user. It outputs a private key SK.
This algorithm first chooses a random r Z
p
and
computes D
0
= (
- r)Q. Then for each attribute
a
j
in
, compute
1
()
jj
DrtQ
. For the purpose
of outsourcing the computation cost of mobile
client and preserving the data privacy, a virtual
attribute named Att
Vir
is defined. Specially,
denote the secret key component of virtual
attribute as D
Vir
. The user’s private key SK is:
SK
= (D
0
, a
j
: D
j
)
3) Encrypt (m, T, PK). The encryption algorithm
encrypts a file m under the access tree T. Att
Vir
is
attached to the access tree as the right sub-tree.
The access tree is redefined as T = T
Pol
Att
Vir
.
T
Pol
is the real access policy that not need to be
modified in any form.
The detailed encryption algorithm processes as
follows:
A)
Select a random element s Z
p
. Set the value of
the root node of T to be s, mark the root node as
assigned and all child nodes as un-assigned. For
each un-assigned non-leaf node, recursively do
the following:
If the symbol is “AND”, and its child nodes are
marked un-assigned, the secret s is divided using (t,
n) Shamir's secret sharing technique where t = n, and
n is the number of child nodes. To each child node, a
share secret s
i
= f(i) is assigned. Mark this node
assigned. If the symbol is “OF” (threshold operator),
and its child nodes are marked un-assigned, the
secret s is divided using (t, n) Shamir's secret sharing
technique where t < n, and n is the total number of
child nodes and t is the number of child nodes
necessary to reconstruct the secret. To each child
ISME 2015 - Information Science and Management Engineering III
512
ISME 2015 - International Conference on Information System and Management Engineering
512
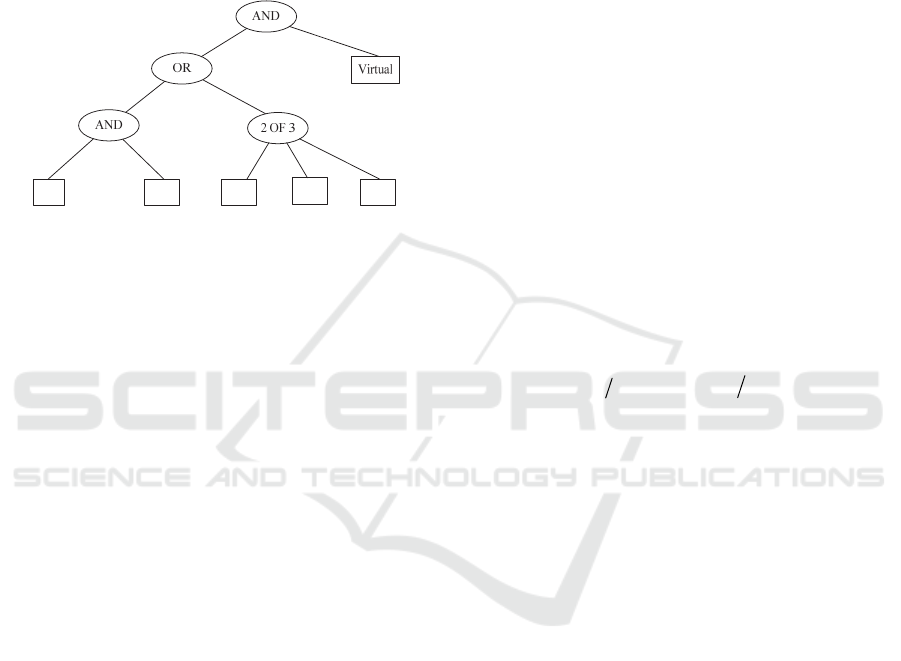
node a share secret s
i
= f(i) is assigned. Mark this
node assigned. If the symbol is “OR”, and its child
nodes are marked un-assigned, the secret s is divided
using (t, n)Shamir's secret sharing technique where t
= 1 and n is the number of child nodes. To each
child node a share secret s
i
= f(i) is assigned. Mark
this node assigned. Figure 2 describes the detailed
progress of assigning secrets to each node of the
access tree.
2
a
3
a
5
a
1
a
D
p
sZ
1
s
3
s
4
s
,1 1 1j
CtsQ
,2 2 2j
CtsQ
,3 3 3j
CtsQ
,4 4 4j
CtsQ
L
s
L
s
L
s
2
s
s
4
a
5
s
,5 5 5j
CtsQ
Vir Vir Vir
CtsQ
Figure 2: The way to assign secrets.
Then DO computes C
0
, C
1
and C
Vir
at local
mobile client as following to get the temporary
ciphertext:
CT
Vir
= (C
0
= sQ, C
1
= me(Q, Q)
s
, C
Vir
= t
Vir
s
Vir
Q)
After completing the above steps, DO sends every s
i
,
and CT
Vir
to the encryption cloud service ECS, where
a
i
T
Pol
, and i denotes the index of the attribute in
the access tree. The index values are uniquely
assigned to leaf nodes in the access tree in an
ordering manner.
B) For each leaf attribute a
j,i
T
Pol
, ECS computes
C
j,i
= s
i
T
j
. By doing this, most of the computation
overheads are outsourced to ECS. Then we get
the other temporary ciphertext CT
Pol
:
CT
Pol
= (a
j,i
T: C
j,i
)
C)
ECS uses the two temporary ciphertexts to
generate the following complete ciphertext:
CT = CT
Pol
CT
Vir
= (a
j,i
T: C
j,i
, C
Vir
, C
0
, C
1
)
Finally, ECS sends CT to the Storage Service
Provider (SSP) .
4) Decrypt (CT, SK
). The decryption algorithm
decrypts the file m from the ciphertext using
user’s private key SK
. The decryption algorithm
is computationally expensive since bilinear
pairing operation over ciphertext and private key
takes heavy overhead. To reduce the
computation overheads of mobile client, we
outsource most of the computation overheads to
DCS. The decryption process is decomposed into
the following three steps:
A) DR first requires data from SSP. SSP checks
whether DR’s attribute set satisfies the access
tree T embedded in the ciphertext. If so, SSP
sends CT to DCS. Meanwhile, DR sends all of
the components of SK
except D
0
and D
Vir
to
DCS. Then DCS chooses the smallest attribute
set
that satisfies T. For each a
j
in
,
compute:
(0)
,
'
(0)
1
'
(,)
(s , )
(, )
i
j
i
j
L
l
ji j
a
l
jj j
a
rs
AeCD
et Qrt Q
eQQ
DCS then sends parameter A to DR.
B) DR computes locally:
00
1
(, )e(C, )
(,( ))( , )(,)
(,)
L
Vir Vir
rs
Vir Vir Vir
s
BeCD D A
esQ rQet s Qrt QeQQ
eQQ
C) DR performs the final step and gets the file m:
1
(,) (,)
s
s
mCBmeQQ eQQ
4 SECURITY AND
PERFOMANCE EVALUATION
4.1 Security Discussion
We now briefly discuss security properties of LF-
ABE.
In the encryption algorithm, ECS is just
responsible for dealing with the computations that
related to access control and it does not get any
direct secrets of the data content. The ciphertext
component C
1
that related to the file m is computed
by mobile device locally. According to Shamir's
secret sharing technique, recovering the master
secret requires the cooperation of all parties if the
operator is “AND”. That is to say, though ECS has
most of the secrets of the access tree, it still cannot
recover the master secret because the secret of
virtual attribute is secretly held by DO. While in the
decryption phase, sending all the secret key
components except D
0
and D
Vir
to DCS will also not
reduce security level. DCS can use these secrets to
get a temporary result, but the final setp of
Achieving Lightweight and Fine-grained Access Control in Mobile Cloud Computing
513
Achieving Lightweight and Fine-grained Access Control in Mobile Cloud Computing
513
decryption is performed by the decryptor at mobile
client.
In LF-ABE, the KeyGen algorithm generates a
different random value r for each user, this means
each user’s secret key is randomized and can not be
combined with the others’. So malicious users can
not use collusion to expand their access permission
in LF-ABE, including ECS and DCS.
4.2 Performance Evaluation
The computation operations in ABE system are
multiplication, point multiplication, exponentiation
and pairing. Due to the computation overheads of
processing multiplication is much less than that of
the other three operations, its influence on the
system performance can be neglected. So we just
take consideration of pairing, point multiplication
and exponentiation.
To facilitate the evaluation, we compare the
computation overheads in Desktop PC, laptop PC
and smartphone. The testing environment is Java
platform. For the convenience of elaboration, denote
as the set of attributes (except the virtual attribute)
the user owns,
is the set of attributes satisfying
the access tree where
and T is the set of
attributes in the access tree. Assume that all the
schemes use the same bilinear map e: G
0
G
0
G
1
.
C
0
denotes point multiplication on elliptic curve
group G
0
, C
1
denotes exponentiation on G
1
and C
e
denotes pairing.
Table 1: Computing time on different devices (Unit: ms).
Device CPU C
0
C
1
C
e
Desktop 3.4GHz 24.7 3.1 25.1
Laptop 2.0GHz 42.8 7.2 49.6
Smartphone 1.0GHz 159.0 48.7 314.7
We can see clearly from Table 1 that, the
computing capabilities between different devices are
very large. Consequently, running ABE system on
lightweight mobile devices will take heavy
overhead.
In Table 2, we compare the computation
overheads between our scheme and the EPS-ABE
scheme at mobile client under the assumption that
their CP-ABE algorithm is directly used to mobile
cloud and does not perform any outsourcing
operations. The key generation algorithm is
performed by TA and it has no connection with the
mobile user, so we do not describe it in Table 2.
Table 2 shows that compared with the EPS-ABE
scheme, most of the computation operations in LF-
ABE are outsourced to ECS and DCS, the
computation overheads are greatly reduced at mobile
client.
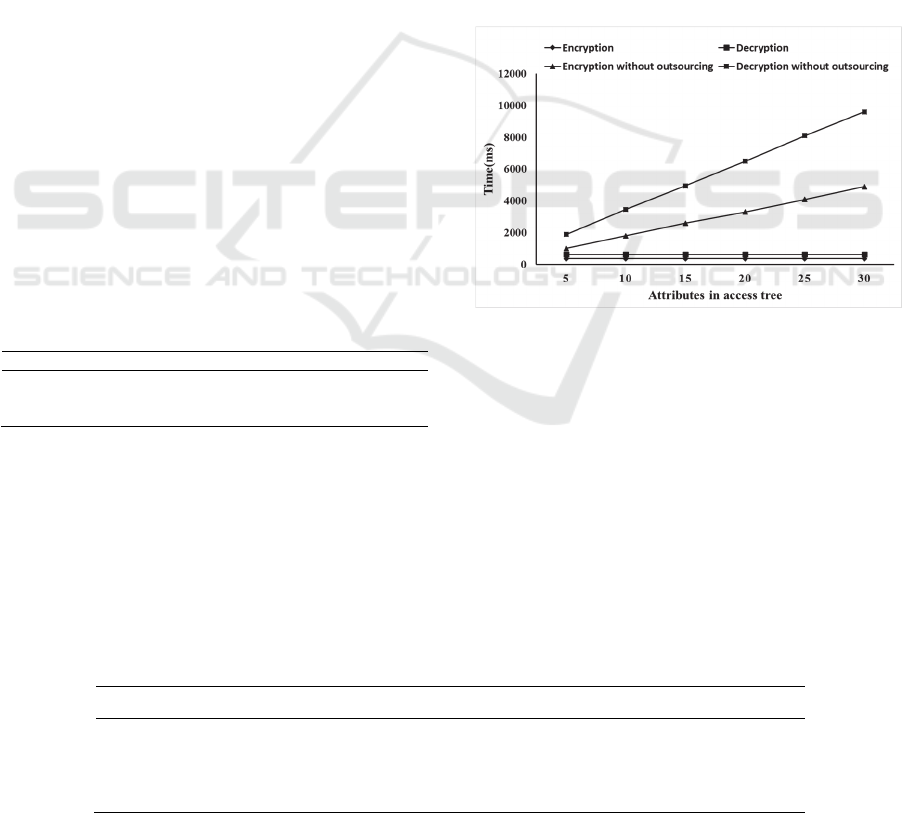
Figure 3 compares the computation time of
encryption and decryption at mobile client between
LF-ABE and EPS-ABE. The time of the two phases
in EPS-ABE scheme is linear with the number of
attributes in the access tree, while in LF-ABE the
time is constant. Figure 3 shows that if the number
of the attributes is large enough, more than 90% of
the computation overheads are outsourced to the
cloud services.
Figure 3: The comparison of computation time between
LF-ABE and EPS-ABE at mobile client.
5 CONCLUSIONS
In this paper, we propose a novel lightweight and
fine-grained access control scheme for mobile cloud
computing named LF-ABE, which meets the
requirements of data security and privacy in mobile
cloud computing. Since there are no special
restrictions on the access policy, LF-ABE provides
expressive and flexible data access control.
Table 2: The comparison of computation overheads between LF-ABE and EPS-ABE at mobile client.
Scheme LF-ABE EPS-ABE
Operation C
0
C
1
C
e
C
0
C
1
C
e
Encryption 2 1
|
|+1
1
Decryption
2
|
|+1
ISME 2015 - Information Science and Management Engineering III
514
ISME 2015 - International Conference on Information System and Management Engineering
514

Meanwhile, by outsourcing most of the computation
overheads to the encryption and decryption cloud
services, mobile devices can easily complete the
data processing operations.
ACKNOWLEDGEMENTS
This work was supported by the Youth Talent
Project of the Science and Technology Research
Program of Hubei Provincial Education Department
under Grant No. Q20151111, and Young Scientist
Foundation of Wuhan University of Science and
Technology under Grant No. 2013xz012, No.
2014xz019, and No.2015XG005.
REFERENCES
Mell, P., Grance, T., 2011. The NIST definition of cloud
computing, NIST Special Publication 800-145.
Chen, D., Zhao, H., 2012. Data security and privacy
protection issues in cloud computing. In Proceedings
of the 1st International Conference on Computer
Science and Electronics Engineering, pp. 647-651.
IEEE Computer Society.
Yu, S., Wang, C., Ren, K., Lou, W., 2010. Achieving
secure, scalable, and fine-grained data access control
in cloud computing. In Proceedings of the 29th
International Conference on Computer
Communications, pp. 1-9. IEEE Computer Society.
Kallahalla, M., Riedel, E., Swaminathan, R., Wang, Q.,
Fu, K., 2003. Plutus: scalable secure file sharing on
untrusted storage. In Proceedings of the 2nd
Conference on File and Storage Technologies, pp. 29-
42.
Di Vimercati, S. D. C., Foresti, S., Jajodia, S., Paraboschi,
S., Samarati, P., 2007. Over-encryption: management
of access control evolution on outsourced data. In
Proceedings of the 33rd International Conference on
Very Large Data Bases, pp. 123-134. VLDB
endowment.
Bethencourt, J., Sahai, A., Waters, B., 2007. Ciphertext-
policy attribute-based encryption. In Proceedings of
the 28th IEEE Symposium on Security and Privacy,
pp. 321-334. IEEE Computer Society.
Hur, J., Noh, D. K., 2011. Attribute-based access control
with efficient revocation in data outsourcing systems.
IEEE Transactions on Parallel and Distributed
Systems, 22(7), pp. 1214-1221. IEEE Computer
Society.
Ibraimi, L., Petkovic, M., Nikova, S., Hartel, P., Jonker,
W., 2009. Mediated ciphertext-policy attribute-based
encryption and its application. In Proceedings of the
International Conference on Information Security
Applications, pp. 309-323. Springer Berlin Heidelberg.
Wang, G., Liu, Q., Wu, J., 2010. Hierarchical attribute-
based encryption for fine-grained access control in
cloud storage services. In Proceedings of the 17th
ACM Conference on Computer and Communications
Security, pp. 735-737. ACM Press.
Sahai, A., Waters, B., 2005. Fuzzy identity-based
encryption. In Proceedings of the 24th Annual
International Conference on the Theory and
Applications of Cryptographic Techniques, pp. 457-
473. Springer Berlin Heidelberg.
Shamir, A., 1979. How to share a secret. Communications
of the ACM, 22(11), pp. 612-613. ACM Press.
Ibraimi, L., Tang, Q., Hartel, P., Jonker, W., 2009.
Efficient and provable secure ciphertext-policy
attribute-based encryption schemes. In Proceedings of
the 5th International Conference on Information
Security Practice and Experience, pp. 1-12. Springer
Berlin Heidelberg.
Achieving Lightweight and Fine-grained Access Control in Mobile Cloud Computing
515
Achieving Lightweight and Fine-grained Access Control in Mobile Cloud Computing
515
