
Performance Analysis of Fountain Codes in Wireless Body Area
Networks
Nabila Samouni
1
, Abdelillah Jilbab
2
and Driss Aboutajdine
1
1
LRIT, Associated Unit to CNRST (URAC No 29) - Faculty of Sciences, Mohammed V University in Rabat,
B.P.1014 RP, Rabat, Morocco
2
ENSET, Mohammed V University, Rabat, Morocco
Keywords:
Wireless Body Area Networks, FEC, Fountain Codes, ARQ, Energy Consumption, BER, Reliability.
Abstract:
Wireless Body area network (WBAN) has emerged in recent years as a special case of wireless sensor network
(WSN) targeted at monitoring physiological human beings. One of the major challenges in this network is to
prolong the network and node lifetime. The data transmitted from the sensors are vulnerable to corruption
by noisy channels, reflections and distortions. This paper investigates the reliability of transmissions within
WBAN and compares the performance provide by Automatic Repeat reQuest (ARQ) scheme and Luby Trans-
form code (LT). The Theoretical and practical results presented in this paper show that the use of LT codes in
WBAN has a better performance not only in BER, but also in resources and energy consumption.
1 INTRODUCTION
The increase of life expectancy in most countries of
the world is one of the major challenges in recent
decades. In Morocco, life expectancy has increased
significantly from 47 years in 1960 to 71 years in
2014. This fact implies an overload on the health
care system. In this context and with the appearance
of physiological intelligent micro-components, which
can be integrated into the human body; new solutions
are being considered to allow remote medical moni-
toring. Imagine a set of small electronic devices, au-
tonomous, placed on the patient’s bodies and make
them able to communicate with each other wirelessly.
Together they form a network named wireless body
area network (WBAN)(Movassaghi and Abolhasan,
2014).
Furthermore, in such applications, the network
must deliver reports and patient health alerts in a per-
fect manner, in which delay or loss is not tolerated.
The application of these micro-components in a med-
ical context requires:
• A sensor network where the majority of nodes are
always active.
• A particular attention to errors made in the trans-
mission channel, which is not-reliable.
• A sensor has only limited energy resources.
This causes loss of information and energy, to deal
with these two problems of instability of the radio
channel and energy consumption, several solutions
have been proposed in the literature, and that they can
be grouped into two major error control modes: ARQ
(Automatic Repeat reQuest) and FEC (Forward Error
correction).
This work investigates the reliability of transmis-
sions and energy consumption within WBAN. We in-
deed focus on ARQ (Roshanzadeh and Saqaeeyan,
2012)(Automatic Repeat reQuest) and FEC(Oskar,
2009) (Forward Error correction), especialy on the
fountain codes that derives from the FEC.
The rest of the paper is divided into 5 sections.
In Section 2, we provide an introduction of WBAN.
In section 3 we review the two most widely used er-
ror correction techniques, ARQ and FEC, in particu-
lar the LT process. Section 4 discusses a simulation
results using IEEE 802.15.6 standard. We finally state
our conclusion and future work in Section 5.
2 WBAN
Wireless Body Area Network (WBAN) is a special
case of wireless sensor networks (WSNs) that is a col-
lection of small and intelligent wireless medical sen-
sors which are attached to or implanted into a human
body(see figure 1). These sensors have wireless sense
capability and transmission biological informations;
Samouni N., Jilbab A. and Aboutajdine D.
Performance Analysis of Fountain Codes in Wireless Body Area Networks.
DOI: 10.5220/0005672000450049
In Proceedings of the 5th International Confererence on Sensor Networks (SENSORNETS 2016), pages 45-49
ISBN: 978-989-758-169-4
Copyright
c
2016 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
45
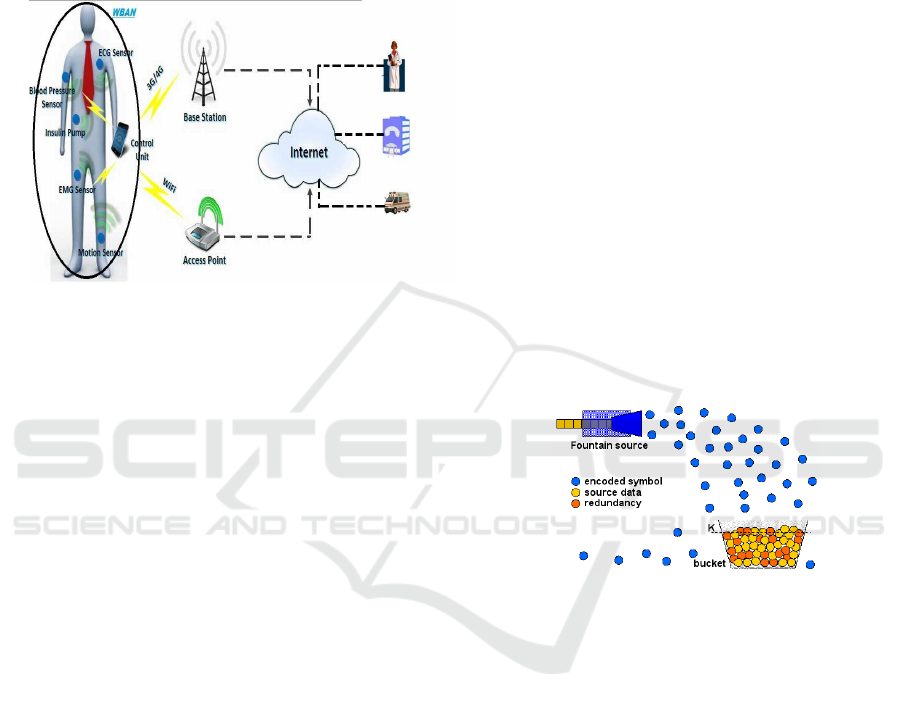
such as electrocardiogram (ECG), photoplethysmo-
gram (PPG), electroencephalography (EEG), pulse
rate, blood flow, pressure and temperature; to one
or more collection points. These information will be
transmitted wirelessly to an external processing unit.
This device will instantly transmit all information in
real time to the doctors throughout the world.
Figure 1: WBAN : Wireless Body Area Networks.
For the realization of the international standard-
ization for WBAN, a study group of IEEE called
IEEE 802.15.6, has been launched in November 2007
to work on the WBAN standardization. This last es-
tablished the first draft of the communicationstandard
of WBANs in April 2010, optimized for low power
devices and operation on, in or around the human
body (Ullah and Ullah, 2010). The approved version
of the IEEE 802.15.6 standard was ratified in Febru-
ary 2012. The purpose of this group is to establish
a communication standard optimized for low power,
high reliability.
3 ERROR CONTROL CODING
(ECC)
In general, the error control mechanisms can be cate-
gorized into two main approaches:
• Automatic Repeat reQuest (ARQ): The main
idea is that the transmitter after sending the packet
waits for a specific time (time out) to receive an
acknowledgment. If it receives positive acknowl-
edgment (ACK), it sends the next packet, while
if it receives negative acknowledgment (NAC) or
timed out before receiving any acknowledgment,
then it retransmits the same packet. The process
keeps repeating until the transmitter receives an
ACK, or a specific number of retransmission is
reached.
• Forward Error Correction (FEC): In FEC
source node encodes data using some error cor-
recting code which lets the receiver node to cor-
rect errors in data packet if it existed. Thus, mak-
ing retransmission outdated. Error control cod-
ing also provides coding gain, which lowers re-
quired transmitting power for specific bit error
rate (BER). Several codes have been investigated
for error correction in WSN, including fountain
codes, turbo codes, BCH codes and LDPC codes.
In our study, we considered FEC schemes employ-
ing fountain codes due to its low encoding/decoding
complexity, and its adaptation with all channels, con-
trast to other families (such as LDPC which is dedi-
cated just for erasure channels).
3.1 Fountain Code
The main idea of a Digital Fountain (DF) is analogous
to the case of a water fountain. To fill a drink at the
fountain (Figure 2) we focus only on the amount of
water needed to fill the glass without considering the
scheduling water drops or those that fall outside of
the glass. This idea leads to the achievement of codes
with that characteristic.
Figure 2: Analogy code fountain with filling a glass with a
water fountain.
Fountain codes (Mitzenmacher and Rege, 1998)
are universal i.e they are simultaneously near optimal
for every erasure channel. Regardless of the statis-
tics of the erasure events on the channel, we can send
as many encoded packets as are needed in order for
the decoder to recover the source data. It follows that
such codes are optimal for any channel because it is
only necessary to receive enough symbols to decode
with high probability the source information. There
are three main category of fountain codes: Random
Linear Fountain (RLF)(MacKay and David, 2005),
Luby Transform (LT), and Raptor codes(Shokrollahi,
2006). In this work, we consider an LT code because
of its lower decoding complexity.
3.2 Luby Transform (LT)
LT codes proposed by Luby (Luby, 2002) in 1998,
they are the first practical realization of Fountain
SENSORNETS 2016 - 5th International Conference on Sensor Networks
46

codes. LT codes are rateless, i.e., the number of gen-
erated encoded packets are potentially limitless, and
encoded symbols are generated on the fly. This means
that the encoder is capable of producing as many sym-
bols as needed by the decoder to recover the original
k input symbols, no matter where the channel exists.
3.2.1 Encoding
The encoding LT principle is :
1. Divide the information transmitted in K fragments
of the same size,
2. To select randomly a degree d
m
∈ {1, ...,k} ac-
cording to the distribution Ω(x),
3. To select uniformly at random d
m
distinct infor-
mation symbols and set e
m
equal to their bitwise
modulo 2 sum.
3.2.2 Decoding
The decoding process uses the method Belief Prop-
agation (see Algorithm 2) that is based on the fact
that the degree of packet 1 may be considered de-
coded. Thus, using the previously decoded packet,
the decoder iteratively reduces the amount of encoded
packets, until all of the fragments are decoded. The
amount of packets needed to decode without errors
is in the order of K
′
= K + ε, where ε is the coding
redundancy rate.
4 SIMULATION
In this section, we investigate the reliability of trans-
mission and energy efficient, of LT code and ARQ
scheme, within wireless body area network (WBAN).
The simulation is carried out for a two system peer-to-
peer, the first one with LT code the other is uncoded
channel (using ARQ). The transmission chain to im-
plement is shown in figure 3 :
System with channel coding LT code
LT Encoder
Modulation DemodulationNoise
Channel
LT DecoderLT DecoderLT Decoder
Transmission without coding
Data source Data sink
X
Y
Y
′
X
′
Figure 3: Transmissions with and without coding.
The performance evaluation holds in terms of en-
ergy consumption and channel bit error rate (BER)
via extensive simulations using IEEE 802.15.6 stan-
dard with 7 medical sensor nodes implanted in the hu-
man body. The transmission is over an additive white
Gaussian noise (AWGN) channel, with variance N0/2
and zero mean, using BPSK modulation for all en-
coded bits. The following simulation parameters were
considered.
Table 1: Simulation parameters.
Parameter Type or Value
P
t
Transmit power 10 dBm
N
0
white noise -111 dBm/Hz
R Transmission
rate
20Kbit/s
F Frequency car-
rier
868 MHz
N
b
number of bits
per packet
100octets (uncoded channel)
105 octets (with LT coding)
E
Ele
50 nJ
E
amp
0.013 pJ
4.1 Results and Analysis
4.1.1 BER Test
This section discuss the BER performance versus
SNR for a transmission with LT code, compared to
uncoded channel (ARQ).
Fig. 4 and fig. 5 show the relationship between
the SNR and BER, as we increase the SNR, BER de-
creases respectively.
Figure 4: Performance in terms of BER versus SNR for
coding channel with LT code.
From this figures, it can be observed that the cod-
ing channel of the LT codes (between 10
−0.79
and
10
−0.788
) have a less BER than that uncoded channel
(between 10
−6
and 10
0
).
Performance Analysis of Fountain Codes in Wireless Body Area Networks
47

Figure 5: Performance in terms of BER versus SNR for
coding channel with LT code.
4.1.2 Energy Consumption
Initially we presented a theoretical comparison of en-
ergy consumed in a transmission with fountain code
and without coding. According to (Marie and Katia,
2008), the energy consumed for the transmission of
one packet can be decomposed as:
E
p
= E
T
(s,d) + E
R
(s) + E
ack
(1)
Where :
• E
T
is the energy consumed in transmission :
E
T
(s, d) = E
Telec
(s) + E
Tamp
(s, d)
= (E
elec
∗ s) + (E
amp
∗ s∗ d
2
)
• E
R
is the energy consumed in receiver :
E
R
= E
Rele
(s) = E
elec
∗ s
• E
ack
is the energy consumed in acknowledgement.
E
elec
and E
amp
represent the energy of electronic
transmission and amplification respectively.
The total energy used to transmit K fragments of
information for the case without coding (ARQ mech-
anism) can be expressed, in the form:
E
T
ARQ
= K.
1
γ
ack
.
1
γ
data
. (E
T
+ E
R
)
+ E
ack
The energy consumption of LT codes is given by:
E
LT
= (K + ε− 1) .
1
γ
data
. (E
T
+ E
enc
+ E
R
+ E
dec
) +
1
γ
ack
.
1
γ
data
. (E
T
+ E
enc
+ E
R
+ E
dec
) + E
ack
Where E
enc
and E
dec
represent the energy used to en-
code and decode LT respectively.
Fig. 6 show the energy consumption for two dif-
ferent schemes : the LT codes and ARQ as a func-
tion of the distance with K=100 packets. It can be
observed from the results that the uncoded channel
(ARQ) scheme has energy consumption higher than
the LT code.
Figure 6: Energy consumption as a function of the distance.
Figure 7: Energy consumption as a function of the packets
sent.
In fig 7 the energy consumption for the LT codes
and ARQ is plotted as function of the number of pack-
ets sent. We can be inferred also that transmission
using LT coding is more energy efficient than using
ARQ.
However, the LT code have lower energy con-
sumption, as can be seen in Fig. 6 and fig. 7. The
advantage of LT code is to increase the reliability of
packets without a significant increase in the energy
consumption.
Despite the number of data packets transmitted
in the case with coding (LT), amounts, it may be
noted that the energy consumption is lower than in
the case with ARQ, because the sends of acknowl-
SENSORNETS 2016 - 5th International Conference on Sensor Networks
48

edgment packets can occur for each packet, while for
LT, it is just for the last packet which can be trans-
mitted. In addition the encoding process introduces
mathematical operations XOR type, which generates
a sequence encoding complexity O(log(
K
δ
)). Con-
sumption to the calculation process is small and can
be neglected compared to the energy consumption re-
quired for the transmission radio.
5 CONCLUSIONS
In WBAN the network must deliver reports and pa-
tient health alerts in a perfect manner, in which delay
or loss is not tolerated. This paper has presented two
solutions for the problem of instability of the radio
channel and sensor lifetime: ARQ and LT code that
derives from the FEC. We simulated and verified that
LT code has a better performance not only in BER,
but also in resources and energy consumption.
In our future work, it should be compared the per-
formance provided by LT codes with the other famille
of FEC sush as LDPC code and BCH in wireless body
area Networks (WBAN).
REFERENCES
Luby, M. (2002). LT codes. Annual IEEE Symposium on
the Foundations of Computer Sciences (STOC), 43rd
edition.
MacKay and David, J. C. (2005). Fountain codes. IEEE
Communications.
Marie, Z. R. G. J. and Katia, J. R. (2008). Energy-
delay bounds analysis in wireless multi-hop net-
works with unreliable radio link. in arXiv preprint
arXiv:0807.4656.
Mitzenmacher, J. B. M. L. M. and Rege, A. (1998). A Digi-
tal Fountain Approach to Reliable Distribution of Bulk
Data. in Conference on Applications, Technologies,
Architectures, and Protocols for Computer Communi-
cation (SIGCOMM), Vancouver, BC, Canada.
Movassaghi, S. and Abolhasan, M. (2014). Wireless body
area networks: A survey. Communications Surveys &
Tutorials, IEEE 16.3 : 1658-1686.
Oskar, E. (2009). Error Control in Wireless Sensor Net-
works.
Roshanzadeh, M. and Saqaeeyan, S. (2012). Error Detec-
tion and Correction in Wireless Sensor Networks. in
MECS.
Shokrollahi, A. (2006). Raptor Codes. transaction on In-
formation Theory.
Ullah, K. K. S. and Ullah, N. (2010). An overview of IEEE
802.15.6 standard. Int. Symp. on Applied Sciences
in Biomedical and Communication Technologies (IS-
ABEL), pp. 1 6, 3rd edition.
Performance Analysis of Fountain Codes in Wireless Body Area Networks
49
