
Lean and Fast Secure Multi-party Computation:
Minimizing Communication and Local Computation using a Helper
Johannes Schneider
ABB Corporate Research, Baden-Daettwil, Switzerland
Keywords:
Client-server Computation, Secure Cloud Computing, Secure Multi-party Computation, Privacy Preserving
Data Mining.
Abstract:
A client wishes to outsource computation on confidential data to a network of servers. He does not trust a
single server, but believes that multiple servers do not collude. To solve this problem we introduce a new
scheme called JOS for perfect security in the semi-honest model that naturally requires at least three parties.
It differs from classical secure multi-party computation (MPC) through three points: (i) a client-server setting,
where all inputs and outputs are only known to the client; (ii) the use of three parties, where one party serves
merely as “helper” for computation, but does not store any shares of a secret; (iii) distinct use of the distributive
and associative nature of well-known linear encryption schemes to derive our protocols. We improve on the
total amount of communication needed to compute both an AND and a multiplication compared to all prior
schemes (even two party protocols), while matching round complexity or requiring only one more round.
For big-data analysis, network bandwidth is often the most severe limitation, thus minimizing the amount of
communication is essential. Therefore, we make an important step towards making MPC more practical. We
also reduce the total amount of storage needed (eg. in a database setting) compared to all prior schemes using
three parties. Our local computation requirements lag behind non-encrypted computation by less than an order
of magnitude per party, while improving on other schemes, ie. GRR, by several orders of magnitude.
1 INTRODUCTION
Cloud computing has boosted the need for methods
to compute on encrypted data. Secure multi-party
computation (MPC) is a computationally efficient
approach that allows a client to outsource computa-
tion to a group of servers, relying on the assumption
that servers do not collude (to retrieve confidential
information). In the semi-honest model, a curious but
passive attacker can monitor a server completely, eg.
its memory, disc or CPU registers.
Our effort to minimize communication and local
computation is essential to improve acceptance of
MPC in industry. All modern schemes for data
analysis, such as Hadoop or Spark, rely on data-
parallelism, ie. performing the same computation for
different parts of the data. Computation is done in
a distributed fashion, which requires moving large
amounts of data between computers (as is needed for
MPC, in particular for big data). For this essential
scenario of privacy preserving data mining, the
bottleneck becomes bandwidth (ie. the amount of
information that can be transmitted) and not network
latency (ie. number of communication rounds). We
address this concern by minimizing the number of
exchanged bits in our protocols. Thus, we believe
that our work is an important step towards making
MPC more practical.
Our scheme called JOS requires at least three par-
ties, where each party can be thought of having a
dedicated role: a keyholder (KH), an encrypted value
holder (EVH) and a helper. The keyholder stores keys
but it has no access to ciphertexts. The encrypted
value holder stores encrypted values but no keys.
THE helper assists computations. It might obtain keys
and encrypted values that do not match, ie. none of its
keys can be used to decrypt any of its encrypted val-
ues. The helper does not hold any shares per se, which
is a key conceptual feature of our method. For exam-
ple, assume the servers should store a large amount
of data. Since all other methods require shares (of at
least the same size as ours) being held by all parties,
each party must store its shares somewhere, whereas
in our case only the EVH and the KH need to store
data. Thus, we improve on the amount of storage
needed for three party protocols and match those of
two party protocols. The (mathematical) motivation
to use a helper is that the AND of two numbers can
be computed by combining four parts consisting only
of encrypted values and keys. Each part can be com-
puted by one party, re-encrypted and combined by
Schneider, J.
Lean and Fast Secure Multi-party Computation: Minimizing Communication and Local Computation using a Helper.
DOI: 10.5220/0005954202230230
In Proceedings of the 13th International Joint Conference on e-Business and Telecommunications (ICETE 2016) - Volume 4: SECRYPT, pages 223-230
ISBN: 978-989-758-196-0
Copyright
c
2016 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
223

the KH and EVH to yield an encrypted AND of the
two numbers. This would yield a total of four parties.
Through double encryption of values, we can reduce
the number of parties to three. The derivation of the
protocols uses the associative and distributive proper-
ties of linear secret sharing. Our scheme is illustrated
for three encryption schemes based on XOR and ad-
dition. We were able to design protocols that perform
efficient Boolean operations (AND, XOR) and arith-
metic operations (addition, multiplication). Linear se-
cret sharing also strikes through little computational
overhead – in particular, when compared to protocols
that require cryptographic primitives, eg. we do not
need to generate prime numbers or exponentiations of
large numbers. Aside from random numbers secure
operations only need a few additions and multiplica-
tions of numbers, which are only of the same length
as the plaintext.
In summary, we make the following contributions:
• We present a new scheme for MPC in the semi-
honest model for Boolean circuits as well as for
arithmetic expressions using n ≥ 3 parties. To the
best of our knowledge, we improve on the amount
of communication needed to compute an AND or
to conduct a multiplication compared to all prior
schemes (see Table 2). The round complexity of
JOS matches other schemes or lags behind by at
most one round more. We require less storage
than all prior three party protocols, while match-
ing storage requirements for two party protocols.
• Our protocols are efficient in terms of local com-
putation. A secure addition requires adding shares
only. A secure multiplication requires in total 6
multiplications of numbers of the same size as
well as a few additions and random keys (analo-
gously for AND, XOR). In particular, our evalua-
tion shows that local computation overhead is low.
We lag behind computation on non-encrypted data
by a factor less than 10. Compared to GRR we
achieve improvements in run-time measured in
terms of local computation of 3 to 4 orders of
magnitude for encryption and decryption and a
factor of more than 20 for addition and multipli-
cation.
• The scheme is very flexible, ie. it can be ex-
tended to compute unbounded fan-in gates in con-
stant rounds as well as to more than three par-
ties (Schneider, 2016) and for efficient numeri-
cal computation such as trigonometric functions
(Schneider, 2015).
2 RELATED WORK
Helpers as trusted entities are not uncommon in MPC,
eg. (Boneh and Franklin, 1997; Du and Atallah,
2001). In the setting of (Du and Atallah, 2001) a
client wants to know if a value held by the server
matches her secret string. A “helper” assists in an-
swering the query. The result of the query should also
remain secret to the server.
Three parties are commonly used, eg. (Mohas-
sel et al., 2015; Bogdanov et al., 2008; Launchbury
et al., 2014). The work (Mohassel et al., 2015) builds
upon garbled circuits, essentially showing that gar-
bled circuits can be made robust against corruption
of one party. Sharemind (Bogdanov et al., 2008) uses
three parties and additive secret sharing, ie. for a se-
cret x each party P
i
obtains a share x
i
such that
∑
x
i
mod 2
32
= x. To perform a multiplication they com-
pute all 6 shares x
i
· x
j
using (Du and Atallah, 2001).
A multiplication requires 3 rounds and 27 messages
each containing a 32-bit value. We require at most 2
rounds and 4 messages. The paper (Bogdanov et al.,
2008) also discusses why Shamir’s secret sharing fails
on the ring of 2
32
(and needs more messages on the
ring Z
p
). The work (Du and Atallah, 2001) uses also
an untrusted third party, which assists in the compu-
tation of approximate distances (eg. of strings) using
various metrics. The system of (Launchbury et al.,
2014) uses three parties and linear secret sharing to
compute all nine shares for evaluation of multiplica-
tion as (Bogdanov et al., 2008).
An unbounded fan-in AND gate can be simulated
(Bar-Ilan and Beaver, 1989) in (expected) constant
number of rounds for arithmetic gates. They encrypt
a number a
i
held by party i as ENC(a
i
) = R
i
· a
i
· R
−1
i−1
with R
i
being a matrix of random elements. The prod-
uct of all terms a
i
is one element in the matrix being
the product of all encryptions.
The BenOr-Goldwasser-Wigderson (BGW) (Ben-
Or et al., 1988; Asharov and Lindell, 2011) gives
several fundamental MPC protocols. Genaro-Rabin-
Rabin (GRR) (Gennaro et al., 1998) simplifies BGW.
GRR requires n ≥ 2 · t + 1 ≥ 3 parties tolerating col-
lusion of t parties, BGW can handle collusion of
t < n/3 parties. GRR and BGW use Shamir’s secret
sharing to derive a protocol for multiplication. For
a performance-based comparison showing the prac-
tical gains of JOS, consult Tables 1 and 2. Scaling
up to n parties multiplying k bit numbers GRR needs
O(n
2
k logn) or O(nk
2
) bit operations (Lory, 2009).
This matches our complexity asymptotically. The
multiplication protocol Simple-Mult in GRR takes
two secrets α and β shared by two polynomials f
α
(x)
and f
β
(x) to compute α · β. Party i computes the
SECRYPT 2016 - International Conference on Security and Cryptography
224

value f
α
(i) · f
β
(i) using a random polynomial. Then
each party aggregates the input of other parties and
reduces the size of the polynomial through interpola-
tion to compute his share of α· β. A protocol for mul-
tiplication and addition using similar ideas as GRR
but using additive secret sharing (without modulo) is
given in (Maurer, 2006). In the case of three parties
a secret a is split into three parts a
0
,a
1
,a
2
such that
the sum equals a. In (Maurer, 2006) each party gets
two distinct parts. Multiplication of two secrets a and
b is analogous to GRR by computing all nine pairs
a
i
· b
j
, aggregating them locally and sharing the result
using independent randomness. A party then aggre-
gates all received numbers to obtain the result a · b.
To compute (a · b) · c each party would send its share
of a · b to one other party, such that each party again
holds two shares of the result. A key disadvantage
of (Maurer, 2006) is that shares double in size after
every multiplication, making it impractical for even a
modest number of multiplications. This is in contrast
to GRR which reduces the size of shares (using com-
putationally costly interpolation) and to our scheme,
which also does not grow the size of shares.
In contrast, we encrypt a using a single randomly
chosen key, yielding two shares a + k and k. This
leaves one party (the helper) without a share, which
is not the case for any other discussed protocols.
The paper by Yao (Yao, 1986) from the late
80ies still forms the underpinning for many works
evaluating Boolean circuits using garbled circuits.
The original scheme allowed for a circuit only to
be evaluated once without revealing information
about the circuit. A lot of improvements have
been made of several aspects of the protocol, eg.
(Gentry et al., 2013; Bellare et al., 2013). Reusable
circuits come only with additive overhead in the
form of a polynomial in the security parameter and
circuit depth (Gentry et al., 2013). Our advantage
compared to (Gentry et al., 2013) is that we ensure
perfect security and encryption is much simpler (and
faster). Additionally, our communication complexity
does not depend on a polynomial depending on the
security parameter as well as the circuit depth, which
can easily dominate the communication costs. Yao’s
scheme has been generalized to multiple parties
by computing a common garbled circuit in BMR
(Beaver et al., 1990).
Goldreich-Micali-Widgerson (GMW) (Goldreich
et al., 1987) uses oblivious transfer to compute any
Boolean circuit. Values are encrypted such that each
party holds parts of the non-encrypted value. The
GMW protocol has round complexity linear in the
depth of the circuit. Oblivious transfer has been con-
tinuously optimized, eg. (Asharov et al., 2013) uses
symmetric cryptography. Still, using (Asharov et al.,
2013) for an oblivious transfer requires (as a lower
bound) at least the size of the security parameter,
which is significantly more than our total communi-
cation for an AND.
There is a vast number of secret sharing schemes,
eg. for a survey see (Beimel, 2011). Our linear en-
cryption schemes are known. For instance, (Ito et al.,
1989) encrypts a secret using XOR. Additive encryp-
tion as done in JOS roughly corresponds to (Ben-Or
et al., 1988) and has been also employed by (Catrina
and De Hoogh, 2010). Whereas prior work shared a
secret with all parties, we use a dedicated helper to
support computation and use the properties of the en-
cryption schemes to derive novel protocols.
Lately, also several systems and languages have been
developed, eg. (Demmler et al., 2015; Laud and
Randmets, 2015).
3 MODEL AND NETWORK
ARCHITECTURE
A client holds an arbitrary amount of secret values
and wishes to evaluate a function using n servers,
ie. parties, such that no party learns anything about
the input or the output.
1
Thus, typically, a client en-
crypts its secrets and distributes the shares among the
servers, the servers compute the function and return
their shares to the client. The client itself does not
participate in the computation and, therefore, does
not count as party. This differs from the classical
MPC model, where each party holds a secret (or at
least a share) and the output should be known by (at
least) one party. We can emulate the classical model:
The parties can always obtain the secret value of an
output through collusion (rather than transmitting all
their shares to the client) and, in case each party has
a secret, each party can execute the same protocol for
encryption and distribution of shares of its secret as
a client having all secrets. Thus, the extension to us-
ing several clients (each having some secret value) is
obvious.
We consider the semi-honest model with n = 3
parties out of which at most n − 2 parties can be cor-
rupted by an adaptive adversary. Our simplest net-
work consists of a client, a key holder (KH) and an
encrypted value holder (EVH) and a helper. The client
communicates with the KH and EVH. Generally, the
1
Aside from unconditional security, we also discuss purely
additive encryption(without modulo) that yields statistical
security only.
Lean and Fast Secure Multi-party Computation: Minimizing Communication and Local Computation using a Helper
225

Client
Encrypted
value holder
Keyholder
0) Given a,b; f(a,b) := a ˄ b = ?
1) Choose keys Ka,Kb
2) ENC
Ka
(a) = a ⊕ Ka
ENC
Kb
(b) = b ⊕ Kb
11) f(a,b) = DEC
Kf
(ENC
Kf
(a˄b)) = a˄b
5) t0 := ENC
Ka
(a) ˄ ENC
Kb
(b)
9) ENC
Kf
(a˄b) = t0 ⊕ ENC
K3
(t1) ⊕ ENC
K4
(t2)
Helper 1
Helper 2
5) t1 := ENC
Ka
(a) ˄ Kb
6) Choose random K3
7) ENC
K3
(t1) = t1 ⊕ K3
4) Ka
8) K4
4) ENC
Ka
(a)
8) ENC
K3
(t1)
5) t2 := Ka ˄ ENC
Kb
(b)
6) Choose random K4
7) ENC
K4
(t2) = t2 ⊕ K4
5) t3 := Ka ˄ Kb
9) Kf = t3 ⊕ K3 ⊕ K4
4) ENC
Kb
(b)
8) ENC
K4
(t2)
4) Kb
8) K3
3) ENC
Ka
(a), ENC
Kb
(b)
10) ENC
Kf
(a˄b)
3) Ka, Kb
10) Kf
Figure 1: Algorithm for an AND (∧) of two bits using four parties.
KH holds keys and the EVH holds encrypted values.
Note, there are circumstances, where this distinction
has to be seen less strict, eg. for secret a there might
be two encryptions such that one encrypted value is
held by the KH. A network with three parties is shown
in Figure 2. We assume perfectly secure communica-
tion channels between parties.
4 ENCRYPTION
We use linear secret sharing, but only two out of three
parties obtain a share, ie. we generate only two shares.
We label these two shares differently, ie. key and en-
crypted value.
2
Encryption for Boolean Operations: For a given bit
m ∈ {0,1} we choose a random key K ∈ {0,1}. The
encryption ENC
K
(m) of bit m ∈ {0,1} using key K is
the XOR (⊕ symbol), ie. ENC
K
(m) := K ⊕ m. The
decryption DEC
K
(c) of a ciphertext c is DEC
K
(c) :=
c ⊕ K.
Encryption for Arithmetic Operations: For a given
number m ∈ {0,1}
l
of l bits we choose a random
key K ∈ {0,1}
b
using b ≥ l bits. The encryp-
tion ENC
K
(m) of number m using key K is then
ENC
K
(m) := (K + m) mod 2
b
. We denote inverse
elements with superscripts, eg. the inverse of K is
K
−1
:= 2
b
− K. The decryption DEC
K
(c) of a cipher-
text c is DE C
K
(c) := (c + K
−1
) mod 2
b
. Whereas
the above encryption in an arithmetic ring guaran-
2
The distinction between keys and encrypted values is
sometimes helpful, eg. for computing the sine function
(Schneider, 2015).
tees unconditional security, we also mention a vari-
ant without modulo that is only statistically secure. If
we just add the key, we have: ENC
K
(m) := K + m,
DEC
K
(ENC
K
(m)) = (m + K) + K
−1
= m + K − K =
m.
5 ADDITION, ADDITIVE
INVERSE, XOR AND NOT
We discuss the entire process ranging from encryp-
tion of plaintexts to decryption of results for a single
operation. To compute a (bitwise) XOR of two
numbers a,b the client encrypts both a and b. It sends
the two keys to the KH and the encrypted values to
the EVH. As a next step, the KH computes the XOR
of the two keys and the EVH the XOR of the two
encrypted values. Both send their results back to the
client. The client obtains a ⊕ b by decrypting the re-
sult from the EVH with the key received from the KH.
A NOT operation (denoted by ¬) corresponds to
computing an XOR of an expression and the constant
one. It can be done by the EVH by computing the
‘NOT’ of the encrypted value. More mathematically,
we have ¬a = a ⊕ 1 and ¬ENC
K
a
(a) = ¬(a ⊕ K
a
) =
(¬a) ⊕ K
a
= ENC
K
a
(¬a).
Additions of two (or more) numbers works analo-
gously to the XOR operation. To deal with negative
numbers we use the two complement.
SECRYPT 2016 - International Conference on Security and Cryptography
226

6 BASIC IDEAS FOR
MULTIPLICATION AND AND
To illustrate the main ideas, we discuss the AND and
multiplication of two numbers using two helpers aside
from the EVH and the KH. Later, we refine the algo-
rithms to require only one helper, ie. three parties.
Note, all our main results are based on the three party
protocols using one helper. Multiplication and AND
work in an analogous manner. The key idea is to ex-
press the AND of the plaintexts using several parts,
each consisting of an encrypted value and a key. Each
part can be computed on a separate party, eg. we use
(and prove) that
a ∧ b =
ENC
K
a
(a) ∧ ENC
K
b
(b)
⊕ (K
a
∧ K
b
)
⊕
K
a
∧ ENC
K
b
(b)
⊕
K
b
∧ ENC
K
a
(a)
(1)
Each of the four terms ENC
K
a
(a) ∧ ENC
K
b
(b), K
a
∧
ENC
K
b
(b), K
b
∧ ENC
K
a
(a) and K
a
∧ K
b
is computed
by one party. Each of the two helpers chooses a key to
encrypt its part before sharing the encrypted part with
the EVH and the key with the KH. The KH and EVH
combine all partial results to obtain the key and en-
crypted value of a ∧ b. The algorithm to compute the
AND of two bits is shown in Figure 1. As we focus
on a client-server setting, we minimize the effort for
the client and let the parties do secret sharing among
themselves. In traditional MPC, this task would be
performed by the client as part of Step 3. For exam-
ple, in Figure 1 Step 4 is part of the secret sharing and
could also be performed by the client. Thus, the ac-
tual computation of the multiplication consists only of
steps 5-9. No keys must be transmitted during com-
putation if keys are pre-shared.
Theorem 1. The AND protocol in Figure 1 is per-
fectly secure and the result is correct.
Proof. Since no party receives both an encrypted
value and the uniquely corresponding key the proto-
col is perfectly secure.
To show correctness, ie. that we indeed compute
a ∧ b, we must prove that the decryption done by the
client yields the correct result. From Figure 1 we see
that the final key delivered to the client is K f = t3 ⊕
K3 ⊕ K4. Thus, it remains to show that for the EVH
holds the claimed equation in Step 9:
ENC
K f
(a ∧ b) = ENC
t3⊕K3⊕K4
(a ∧ b)
= t0 ⊕ ENC
K3
(t1) ⊕ ENC
K4
(t2) (2)
We prove Equation (1) first. It can be derived us-
ing basic laws such as distributiveness and associa-
tiveness, x ⊕ x = 0 and x ⊕ 0 = x:
a ∧ b =(a ⊕ K
a
⊕ K
a
) ∧ b
=
(a ⊕ K
a
) ∧ b
⊕
K
a
∧ b
=
(a ⊕ K
a
) ∧ (b ⊕ K
b
⊕ K
b
)
⊕
K
a
∧ (b ⊕ K
b
⊕ K
b
)
=
(a ⊕ K
a
) ∧ (b ⊕ K
b
)
⊕
(a ⊕ K
a
) ∧ K
b
⊕
K
a
∧ (b ⊕ K
b
)
⊕
K
a
∧ K
b
(3)
Note, by using the definition of the encryption
ENC
K
(m) = m ⊕ K we obtain Equation (1) from (3).
Starting from ENC
K f
(a ∧ b) substituting the final key
K f = t3⊕ K3 ⊕K4 we prove the initial Equation (2):
EN C
K f
(a ∧ b)
=ENC
t3⊕K3⊕K4
(a ∧ b) ( Step 9, KH, Figure 1)
=(a ∧ b) ⊕ (t3 ⊕ K3 ⊕ K4)
=(a ∧ b) ⊕ (K
a
∧ K
b
) ⊕ K3 ⊕ K4 (Using t3 := K
a
∧ K
b
)
=
(a ⊕ K
a
) ∧ (b ⊕ K
b
)
⊕
K
a
∧ (b ⊕ K
b
)
⊕
K
b
∧ (a ⊕ K
a
)
⊕ (K
a
∧ K
b
) ⊕ (K
a
∧ K
b
)
⊕ K3 ⊕ K4 (Using Eq. (3))
=
(a ⊕ K
a
) ∧ (b ⊕ K
b
)
⊕
K
a
∧ (b ⊕ K
b
)
⊕ K4
⊕
K
b
∧ (a ⊕ K
a
)
⊕ K3 (Using a ⊕ (x ⊕ x) = a)
=
EN C
K
a
(a) ∧ ENC
K
b
(b)
⊕ ENC
K4
(K
a
∧ ENC
K
b
(b))
⊕ ENC
K3
(ENC
K
a
(a) ∧ K
b
) (Using ENC
K
(m) = m ⊕ K)
=t0 ⊕ ENC
K3
(t1) ⊕ ENC
K4
(t2)
6.1 Three Parties
It is possible to use only one helper, ie. three par-
ties, for multiplication and AND. Let us show how
to remove Helper 2. For an AND of two secrets
a,b encrypted with K
a
and K
b
Helper 2 computes
ENC
K
b
(b) ∧ K
a
(see Figure 1). None of the other
three parties can compute this expression using both
ENC
K
b
(b) and K
a
since all parties hold at least one of
the two K
b
,ENC
K
a
(a) and therefore they could reveal
a secret. However, the remaining helper (ie. Helper
1) can compute on encrypted values, ie. the EVH can
encrypt ENC
K
b
(b) with a randomly chosen K
2
to ob-
tain ENC
K
b
⊕K
2
(b). The helper can use ENC
K
b
⊕K
2
(b)
instead of ENC
K
b
(b). In particular, the EVH can dou-
ble encrypt b and it can share ENC
K
b
⊕K
2
(b) with the
KH (as long as it does not obtain K
2
) and the key K2
with the helper. This allows the KH to compute K
a
∧
ENC
K
b
⊕K
2
(b), leaving to compute K
a
∧(K
b
⊕K
2
): We
encrypt both values, ie. K
a
with K6 and K
b
⊕ K
2
with
K5 and compute using Equation (3):
Lean and Fast Secure Multi-party Computation: Minimizing Communication and Local Computation using a Helper
227

Client
Encrypted
value
holder
Keyholder
0) Given a,b; f(a,b) := a ˄ b = ?
1) Choose keys Ka,Kb
2) ENC
Ka
(a) = a⊕Ka
ENC
Kb
(b) = b⊕Kb
13) f(a,b) = DEC
Kf
(ENC
Kf
a˄b)) = a˄b
3) Choose random K2
4) ENC
Kb⊕K2
(b) = ENC
Kb
(b) ⊕ K2
6) t0 := ENC
Ka
(a) ˄ ENC
Kb⊕K2
(b)
10) ENC
Kf
(a˄b) = t0 ⊕ ENC
K7
(p7) ⊕ (K5 ˄ K6)
Helper
3) Choose random K5,K7
6) ENC
K5
(Kb⊕K2) = Kb ⊕ K2 ⊕ K5
7) t1 := ENC
Ka
(a) ˄ (Kb ⊕ K2)
8) ENC
K7
(p7) = t1 ⊕ (ENC
K6
(Ka) ˄ (Kb⊕K2)) ⊕ K7
5) ENC
Ka
(a),K2
9) ENC
K7
(p7),K5
3) Choose random K6
4) ENC
K6
(Ka) = Ka ⊕ K6
6) t2 := Ka ˄ ENC
Kb⊕K2
(b)
10) t3 := K6 ˄ ENC
K5
(Kb ⊕ K2)
11) Kf = t2 ⊕ t3 ⊕ K7
5) ENC
Kb⊕K2
(b)
8) K6
5) Kb, ENC
K6
(Ka)
9) ENC
K5
(Kb⊕K2), K7
3) ENC
Ka
(a), ENC
Kb
(b)
11) ENC
Kf
(a˄b)
3) Ka,Kb
12) Kf
Figure 2: Algorithm for an AND (∧) operation of two bits using three parties.
K
a
∧ (K
b
⊕ K2) = (4)
ENC
K6
(K
a
) ∧ ENC
K5
(K
b
⊕ K
2
)
⊕ K5 ∧ ENC
K6
(K
a
)
⊕ K6 ∧ ENC
K5
(K
b
⊕ K
2
) ⊕ (K5 ∧ K6)
In this case, we do not need to distribute all four terms
to (four) different parties. In our scenario the (remain-
ing) helper holds K
b
⊕K
2
, K5 and ENC
K6
(K
a
). Thus,
it can compute two terms, namely ENC
K6
(K
a
) ∧
ENC
K5
(K
b
⊕ K
2
) and K5 ∧ ENC
K6
(K
a
). We can even
simplify for the helper: ENC
K6
(K
a
) ∧ ENC
K5
(K
b
⊕
K
2
) ⊕ K5 ∧ ENC
K6
(K
a
) = ENC
K6
(K
a
) ∧ (K
b
⊕ K
2
).
This idea is realized in the protocol shown in Fig-
ure 2. The message complexity can be reduced by
pre-sharing of keys. If, in addition, the client shares
keys and secrets with all parties directly (rather than
forwarding them using the KV and EVH), the helper
receives all its messages in Step 5 directly from the
client. Furthermore, the client is also assumed to
have computed the second encryption of b, and a
second encryption of K
b
and shared it with KV, ie.
ENC
K
b
⊕K2
(b), ENC
K5
(K
b
⊕ K2). In this case only
one communication round is necessary for a single
multiplication, ie. only the helper must send a mes-
sage to the EVH.
Theorem 2. The AND protocol in Figure 2 is per-
fectly secure and correct.
Proof. Analogously to the proof of Theorem 1, we
show that decrypting encrypted result (Step 10 for the
EVH) with the key (Step 11 for KH) in Figure 2 gives
a ∧ b. We start by transforming a ∧ b as shown below
(see separate box).
Multiplication works analogously (Schneider,
2016).
7 EVALUATION
The paper focuses on the foundations of the JOS
scheme. But we provide a small evaluation with the
intention to measure the overhead for encryptions, de-
cryptions, additions and multiplications of 32bit un-
signed integers compared to GRR in terms of com-
putation and communication. We implemented GRR
relying on Shamir’s Secret Sharing (Lory and Wenzl,
2011) in C++ using the NTL lib. We ran our experi-
ments on an Intel Core i5. For GRR we used a 65 bit
prime, since to support multiplications of two 32 bit
numbers, GRR needs at least a prime of 65 bits.
To assess computational performance we com-
puted the average time per operation per party in
microseconds using 10 million operations, denoted
by ‘[ys/op/party]’ in Table 1. Whereas for GRR
all parties perform the same computations, in our
scheme there are differences. We used the slowest
party to make the comparison fair. Our scheme
outperforms GRR due to several reasons. Our
scheme does not require the use of the NTL lib and
needs only additions and multiplications. GRR needs
also more expensive operations such as modulo, ie.
divisions. Encryption and decryption are extremely
efficient in our scheme, since we require essentially
only one addition or subtraction (and generation
of the key). GRR requires generation of several
random numbers for encryption and evaluation of
SECRYPT 2016 - International Conference on Security and Cryptography
228
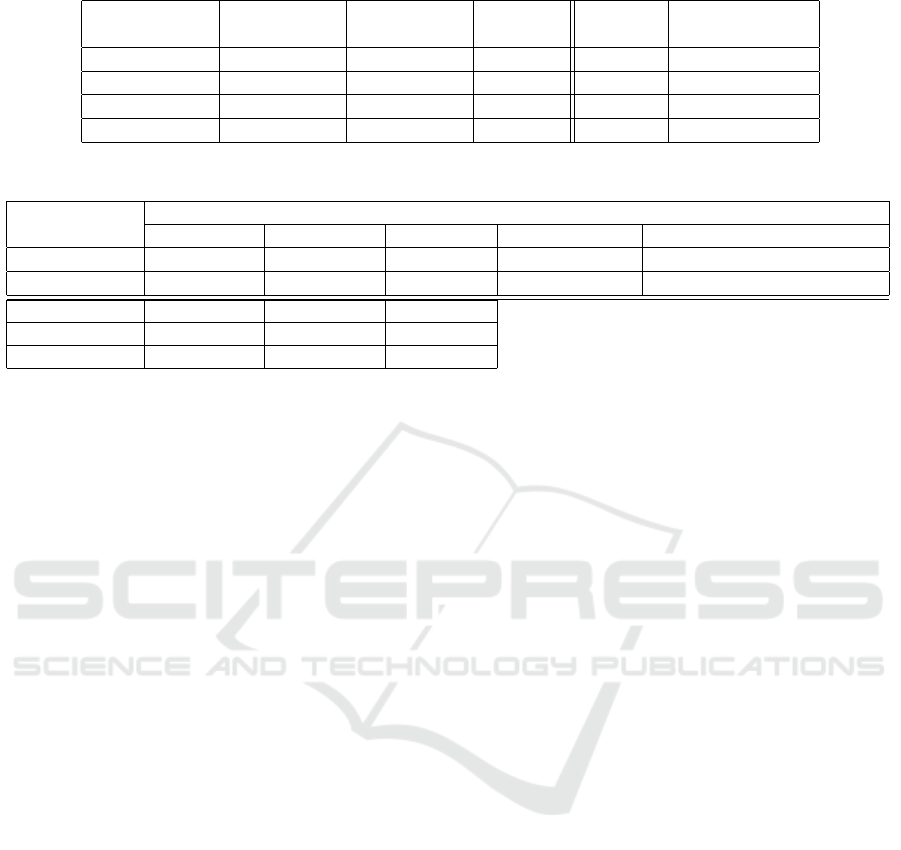
Table 1: Comparison of local computation of the slowest party.
Operation
GRR Our scheme SpeedUp Plaintext Overheadfactor
[ys/op/party] [ys/op/party] [ys/op] (of our scheme)
Encryption 6.7600 0.0078 866.7 - -
Decryption 9.7233 0.0011 9115.6 - -
Addition 0.0655 0.0015 42.3 0.0015 1
Multiplication 4.0600 0.0150 270.67 0.0031 4.84
Table 2: Comparison of total communication and rounds.
Operation
[total transmitted bits (rounds)]
Our scheme GRR, BGW Sharemind (Maurer, 2006) (Bar-Ilan and Beaver, 1989)
Addition 0 (0) 0 (0) 0 (0) 0 (0) 0 (0)
Multiplication 160 (2) 390 (1) ≥ 500 (3) 390 (1) > 300(> 2)
Our scheme GMW BMR
XOR 0 (0) 0 (0) >0 (0)
AND 5 (2) >50 (> 2) > 10 (> 2)
a polynomial (for encryption). Decryption requires
solving a system of equations.
For GRR secrets are hosted at the parties. Therefore,
we also assumed that keys and secrets are held at the
parties, ie. they do not have to be distributed by the
client to compare our protocol (Multiplication is anal-
ogous to AND in Figure 2 – see (Schneider, 2016)).
This means that all messages to and from the client
are not considered. The amount of communication to
perform one addition or one multiplication is given in
Table 2. Table 2 is based on pre-shared keys between
each pair of parties, eg. by exchanging a single
key and then using this key as input for a pseudo
random number generator. Thus, we need two rounds
and we have to transmit the analogous terms to
ENC
Ka
(a),ENC
Kb
(b),ENC
Kb⊕K2
(b),ENC
K7
(p7),
ENC
K5
(Kb ⊕ K2) in Figure 2 – see (Schneider, 2016)
(requiring 32 bits each). For GRR each party sends
two messages with 65 bits each. We also compared
against schemes that provide only statistical security,
ie. for (Maurer, 2006) we chose a keysize of size
64 bits, which is generally not enough. For GMW
(Goldreich et al., 1987) we assumed that the security
parameter used in oblivious transfer is 64 bits,
which is also very modest. For BMR (Beaver et al.,
1990) we also lower bounded the number of bits
exchanged. Table 2 indicates that our scheme uses
least exchanged bits. With respect to the number
of rounds GRR (and Maurer) do better. For the
important case, where we do big data analysis, the
bottleneck becomes bandwidth, ie. the amount of
communicated information.
8 CONCLUSIONS
We have presented a new methodology for secure-
multi party computation. It strikes through little com-
munication, storage and computational overhead, be-
ing unconditionally secure and conceptual simplic-
ity. This makes it easily implementable and a suit-
able candidate for a framework targeted towards pri-
vacy preserving data mining, where minimal amount
of communication as provided by JOS is essential.
Thus, in future work, we want to implement an in-
dustrial strength system focusing on numerical oper-
ations.
REFERENCES
Asharov, G. and Lindell, Y. (2011). A full proof of the bgw
protocol for perfectly secure multiparty computation.
Journal of Cryptology, pages 1–94.
Asharov, G., Lindell, Y., Schneider, T., and Zohner, M.
(2013). More efficient oblivious transfer and exten-
sions for faster secure computation. In Proceedings
of the 2013 ACM SIGSAC conference on Computer &
communications security, pages 535–548. ACM.
Bar-Ilan, J. and Beaver, D. (1989). Non-cryptographic fault-
tolerant computing in constant number of rounds of
interaction. In Proceedings of the eighth annual ACM
Symposium on Principles of distributed computing.
Beaver, D., Micali, S., and Rogaway, P. (1990). The round
complexity of secure protocols. In Proceedings of the
twenty-second annual ACM symposium on Theory of
computing, pages 503–513.
Beimel, A. (2011). Secret-sharing schemes: a survey. In
Coding and cryptology, pages 11–46. Springer.
Lean and Fast Secure Multi-party Computation: Minimizing Communication and Local Computation using a Helper
229

Bellare, M., Hoang, V. T., Keelveedhi, S., and Rogaway, P.
(2013). Efficient garbling from a fixed-key blockci-
pher. In Security and Privacy (SP), 2013 IEEE Sym-
posium on, pages 478–492. IEEE.
Ben-Or, M., Goldwasser, S., and Wigderson, A. (1988).
Completeness theorems for non-cryptographic fault-
tolerant distributed computation. In Proceedings of
the twentieth annual ACM symposium on Theory of
computing, pages 1–10.
Bogdanov, D., Laur, S., and Willemson, J. (2008). Share-
mind: A framework for fast privacy-preserving com-
putations. In Computer Security-ESORICS 2008,
pages 192–206. Springer.
Boneh, D. and Franklin, M. (1997). Efficient genera-
tion of shared rsa keys. In Advances in Cryptology
(CRYPTO), pages 425–439.
Catrina, O. and De Hoogh, S. (2010). Improved primitives
for secure multiparty integer computation. In Security
and Cryptography for Networks.
Demmler, D., Schneider, T., and Zohner, M. (2015). ABY
– A Framework for Efficient Mixed-Protocol Secure
Two-Party Computation. In Proc. Network and Dis-
tributed System Security (NDSS).
Du, W. and Atallah, M. J. (2001). Protocols for secure
remote database access with approximate matching.
In E-Commerce Security and Privacy, pages 87–111.
Springer.
Gennaro, R., Rabin, M. O., and Rabin, T. (1998). Simpli-
fied VSS and fast-track multiparty computations with
applications to threshold cryptography. In Proc. of
the 17th ACM symposium on Principles of distributed
computing, pages 101–111.
Gentry, C., Gorbunov, S., Halevi, S., Vaikuntanathan, V.,
and Vinayagamurthy, D. (2013). How to compress
(reusable) garbled circuits. IACR Cryptology ePrint
Archive, 2013:687.
Goldreich, O., Micali, S., and Wigderson, A. (1987). How
to play any mental game. In Proc. of 19th Symp. on
Theory of computing, pages 218–229.
Ito, M., Saito, A., and Nishizeki, T. (1989). Secret sharing
scheme realizing general access structure. Electronics
and Communications in Japan (Part III: Fundamental
Electronic Science), 72(9):56–64.
Laud, P. and Randmets, J. (2015). A domain-specific lan-
guage for low-level secure multiparty computation
protocols. In Proc. of the 22Nd ACM SIGSAC Con-
ference on Computer and Communications Security,
pages 1492–1503.
Launchbury, J., Archer, D., DuBuisson, T., and Mertens, E.
(2014). Application-scale secure multiparty computa-
tion. In Programming Languages and Systems, pages
8–26. Springer.
Lory, P. (2009). Secure distributed multiplication of
two polynomially shared values: Enhancing the ef-
ficiency of the protocol. In Emerging Security In-
formation, Systems and Technologies (SECURWARE),
pages 286–291.
Lory, P. and Wenzl, J. (2011). A note on secure multiparty
multiplication.
Maurer, U. (2006). Secure multi-party computation made
simple. Discrete Applied Mathematics, 154(2):370–
381.
Mohassel, P., Rosulek, M., and Zhang, Y. (2015). Fast and
secure three-party computation: The garbled circuit
approach. In Proc. of the 22nd ACM Conf. on Com-
puter and Communications Security, pages 591–602.
Schneider, J. (2015). Secure numerical and logical multi
party operations. arXiv preprint arXiv:1511.03829,
http://arxiv.org/abs/1511.03829.
Schneider, J. (2016). Lean and fast secure multi-party com-
putation: Minimizing communication and local com-
putation using a helper. SECRYPT, extended version
arXiv:1508.07690, https://arxiv.org/abs/1508.07690.
Yao, A. C.-C. (1986). How to generate and exchange se-
crets. In Foundations of Computer Science(FOCS).
SECRYPT 2016 - International Conference on Security and Cryptography
230
