
A Code-based Group Signature Scheme with Shorter Public Key Length
Hafsa Assidi, Edoukou Berenger Ayebie and El Mamoun Souidi
Mohammed V University in Rabat, Faculty of Sciences, Laboratory of Mathematics,
Computer Science and Applications, BP 1014 RP, Rabat, Morocco
Keywords:
Code-based Group Signature, Quasi-cyclic Moderate Density Parity-Check (QC-MDPC) Codes, McEliece
Cryptosystem, Syndrome Decoding.
Abstract:
Group signatures allow members to sign on behalf of a group while maintaining signer’s identity anonymous.
In this paper, we show that it is possible to reduce the public key length of the first provably secure group
signature scheme from code-based assumptions without losing the security properties. More precisely, the
public key can be 466 times shorter than the original scheme, typically for a group of 16 users when the public
key length is 1.34 kilo-bytes, while the size is 625 kilo-bytes in the original scheme (Ezerman et al., 2015).
Our technic consist in using a Quasi-cyclic Moderate Density Parity-Check McEliece variant for encrypting
user identity and a random double circulant matrix for the Underlying Zero Knowledge Argument System.
1 INTRODUCTION
A fundamental cryptographic primitive which allows
group users to anonymously sign documents on be-
half of the whole group is called group signature,
but in case of abuse, an administrator can revoke the
anonymity of the signer. Group signature was intro-
duced in (Chaum and van Heyst, 1991). Since then,
many works have been proposed in this area [(Ate-
niese et al., 2000), (Boneh et al., 2004), (Camenisch
et al., 2012), (Gordon et al., 2010)]. For anonymity
and traceability properties of these schemes, group
signatures are highly useful in various real-life sce-
narios such as controlled anonymous printing ser-
vices, digital right management systems, e-bidding
and e-voting schemes. The majority of group signa-
ture schemes are based on number theory assumptions
[(Libert et al., 2012), (Camenisch and Stadler, 1997),
(Boyen and Waters, 2006),(Boneh et al., 2004)], but
number-theoretic based cryptography will not resist
to the quantum computing. Recently, the research
for post-quantum group signatures is quite active as
shows these publications (Laguillaumie et al., 2013),
(Langlois et al., 2014), (Ling et al., 2015), (Alam
´
elou
et al., ), (Gordon et al., 2010). The majority of these
works are based on lattice assumptions, while in code-
based cryptography we denote two group signature
schemes: the first one is based on BSZ model (Bellare
et al., 2005) and it is presented in (Alam
´
elou et al.,
). The second one is based on BMW model (Bel-
lare et al., 2003) and is presented in (Ezerman et al.,
2015), this scheme satisfies the CPA-anonymity and
traceability requirements in the random oracle model.
But the size of the signature and the public key makes
this scheme impractical.
In this article, we propose a new provably secure
group signature scheme based on code assumptions
presented in (Ezerman et al., 2015). In this construc-
tion we replace the original McEliece cryptosystem
used to encrypt the signer identity by the Quasi-cyclic
Moderate Density Parity-Check (QC-MDPC) version
of McEliece. The advantage of QC-MDPC codes
is that for the same security level, the QC-MDPC
version of McEliece has very short public key size
than the original version. For example, for 80 bits
security level, the QC-MDPC public key is 4801
bits unlike the original McEliece public key which
is around 500000 bits. The second improvement
consist in using a random double circulant matrix for
the Underlying Zero Knowledge Argument System
as proposed in (Gaborit and Girault, 2007), we
suggest to replace a random matrix used by Stern
(Stern, 1996) in the Zero-Knowledge identification
scheme by a random double circulant matrix. This
construction allows to have a very short public key,
only 349 bits to obtain 2
83
of security level in the
Zero-Knowledge identification scheme. These two
improvements reduce dramatically the public key
size of the group signature scheme without impacting
the security level. For instance, in the case of 16
users we achieve a public key size of 1.34 KB, while
432
Assidi, H., Ayebie, E. and Souidi, E.
A Code-based Group Signature Scheme with Shorter Public Key Length.
DOI: 10.5220/0005969204320439
In Proceedings of the 13th International Joint Conference on e-Business and Telecommunications (ICETE 2016) - Volume 4: SECRYPT, pages 432-439
ISBN: 978-989-758-196-0
Copyright
c
2016 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

the size is around 625 KB in the original scheme
(Ezerman et al., 2015). Moreover, the structure of
these matrices makes the implementation easier and
efficient, since the product of a circulant matrix and
a vector can be obtained by multiplying only the first
row of the circulant matrix with shifts of the vector.
The organization of this paper is as follows: in
Section 2 we recall the main tools of code-based cryp-
tography, then we explain in Section 3 how to de-
crease the size of the public key by using the QC-
MDPC version of McEliece cryptosystem and double
circulant matrices. In Section 4, we consider the se-
curity of this new construction, while Section 5 com-
pares the performances of the new provably secure
group signature with the previous one. Section 6 is
devoted for conclusion.
2 PRELIMINARIES
In this section, we first provide the notations that will
be used all along this work, secondly we give back-
ground in code-based cryptography and finally we de-
fine the group signature.
2.1 Notations
Let λ denotes the security parameter and negl(λ) de-
notes a negligible function in λ. We denote by a
$
← S
if a is chosen uniformly at random from the finite
set S. The symmetric group of all permutations of
k elements is denoted by S
k
. We use bold capital
letters, (e.g., A), to denote matrices, and bold low-
ercase letters, (e.g., x), to denote row vectors. We
use x
>
to denote the transpose of x and wt(x) to de-
note the Hamming weight of x. We denote by B(m, ω)
the set of all vectors x ∈ F
m
2
(x is a vector of m bits)
of hamming weight ω: wt(x) = ω. Throughout the
paper, we define a function I2B which takes a non-
negative integer a as an input, and outputs the binary
representation (a
0
,··· ,a
`−1
) ∈ {0,1}
`
of a such that
a =
∑
`−1
i=0
a
i
2
`−1−i
, and a function B2I which takes
as an input the binary representation (a
0
,··· ,a
`−1
) ∈
{0,1}
`
of a, and outputs a. All logarithms are of base
2. By 1
λ
we denote the string of N ones. We denote
by ⊕ the bitwise XOR operator.
2.2 Code-based Cryptography
Background
Now we give some necessary notions in code-based
cryptography for the well understanding of our work.
Double Circulant Matrices.
We say that H is a double circulant matrix if H =
[I
p
|A] where I
p
is the identity matrix of size p and A
is a circulant matrix of length p, which means a p × p
matrix generated from its first row a = (a
0
,...,a
p−1
)
A =
a
0
a
1
. . . a
p−1
a
p−1
a
0
. . . a
p−2
. . . . . .
. . . . . .
. . . . . .
a
1
a
2
. . . a
0
(1)
(n,q,w)-QC-MDPC Code Construction.
We are specially interested in (n,q,w)-QC-MDPC
codes where n = n
0
q. This means that the parity-
check matrix has the form H = [H
0
|H
1
|...|H
n
0
−1
],
where H
i
is a q × q circulant block.
We define the first row of H picking a random vector
of length n = n
0
q and weight w. The other q − 1 rows
are obtained from the q − 1 quasi-cyclic shifts of this
first row. Each block H
i
will have a row weight w
i
,
such that w =
∑
n
0
−1
i=0
w
i
.
A generator matrix G in row reduced echelon
form can be easily derived from the H
i
’s blocks. As-
suming the rightmost block H
n
0
−1
is non-singular
(which particularly implies w
n
0
−1
is odd, otherwise
the rows of H
n
0
−1
would sum up to 0), we construct a
generator-matrix as follows.
G =
I
n−q
(H
−1
n
0
−1
.H
0
)
T
(H
−1
n
0
−1
.H
1
)
T
.
.
.
(H
−1
n
0
−1
.H
n
0
−2
)
T
(2)
Remark 2.1. Since we work in F
2
, we notice that
generating a double circulant matrix H = [I
p
|A] of
length p require only p bits corresponding to the first
row a = (a
0
,a
1
,...,a
p−1
) of A (1). On the other hand,
the generator matrix of a (n,q,w) QC-MDPC code
can be deduced only from a n − q bits corresponding
to the first row of each block H
i
.
Syndrome Decoding Problem.
The Syndrome Decoding problem is a problem based
on coding theory proved to be NP-complete in
(Berlekamp et al., 1978) .
Definition 2.1. The SD(m, k,ω) problem is formu-
lated as follows: given a uniformly random matrix
H ∈ F
k×m
2
and a uniformly random syndrome y ∈ F
k
2
,
find a vector s ∈ B(m, ω) such that H · s
>
= y
>
.
When m, k and ω are chosen based on λ, we say that
A Code-based Group Signature Scheme with Shorter Public Key Length
433

the SD(m,k,ω) problem is hard, if the success prob-
ability of any probabilistic polynomial time (PPT) al-
gorithm in solving the problem is at most negl(λ).
Syndrome Decoding Problem for Random
Double Circulant Codes.
We define a new problem, which adapts the syndrome
decoding problem to the case of random double circu-
lant codes:
Definition 2.2. The SD(2p, p, ω) problem is formu-
lated as follows:
Instance: given a random double circulant matrix
H ∈ F
p×2p
2
and a vector y ∈ F
p
2
.
Question:find a vector s ∈ B(2p,ω) such that H ·s
>
=
y
>
.
It is not known whether this problem is NP-
complete, but the problem is probably as hard as
syndrome decoding problem, and on practical point
of view (see (Gaborit and Girault, 2007)) the practical
security is almost the same for the best known attack
that syndrome decoding for random matrices.
The Randomized QC-MDPC McEliece Encryp-
tion Scheme.
We derive from the QC-MDPC McEliece encryption
scheme (Misoczki et al., 2013) a randomized vari-
ant as it is suggested in (Nojima et al., 2008) for the
original version (McEliece, 1978) with Goppa codes,
where a uniformly random vector is concatenated to
the plaintext. We describe the scheme as follows:
• Let S(1
λ
) be the setup algorithm, it selects pa-
rameters n, q, t and w which are chosen based
on λ for a binary t-error-correcting (n,q, w)-QC-
MDPC code. Choose integers q
1
, q
2
such that
n − q = q
1
+ q
2
. Set the plaintext space as F
q
2
2
.
• Let K (n, q, w,t) be the algorithm that generate the
keys, it performs in two steps:
1. Generate a parity-check matrix H ∈ F
q×n
2
of a
t-error-correcting (n,q, w)-QC-MDPC code.
2. Generate its corresponding generator matrix
G ∈ F
(n−q)×n
2
in row reduced echelon form.
Output encrypting key pk
ME
= G and decrypting
key sk
ME
= H.
• Let E(pk
ME
,m) be the encryption algorithm, it
encrypts a message m ∈ F
q
2
2
, sample u
$
← F
q
1
2
and
e
$
← B(n,t), then output the ciphertext
c = (u k m) · G ⊕ e ∈ F
n
2
.
• Let D(sk
ME
,c) be the decryption algorithm and
let R
H
be a t-error correcting Low-Density Parity
Check (LDPC) decoding algorithm equipped with
the knowledge of H. To decrypt c ∈ F
n
2
:
1. compute y = R
H
(c)
2. get the plaintext m as follow: extract (ukm)
from the first (n − q) positions of y.
Definition 2.3 (Codeword Finding Problem). The
CwF(n,k, w) problem is as follows: given a ma-
trix H ∈ F
k×n
2
and an integer w, the problem is to
find a codeword of weight at most w in the code of
generator-matrix H.
Definition 2.4 (The Decisional McEliece Problem).
The DMcE(n, k,t) problem is as follows: given a ma-
trix G ∈ F
k×n
2
, distinguish whether G is a uniformly
random matrix over F
k×n
2
or it is generated by algo-
rithm K (n, q, w,t) described above.
When n, q, t are chosen based on λ and k = n −q, we
say that the DMcE(n,k,t) problem is hard, if the suc-
cess probability of any probabilistic polynomial time
(PPT) distinguisher is at most
1
2
+ negl(λ).
Definition 2.5 (The Decisional Learning Par-
ity with (Fixed-weight) Noise Problem). The
DLPN(k, n, B(n,t)) problem is as follows: given a
pair (A,v) ∈ F
k×n
2
× F
n
2
, distinguish whether (A,v)
is a uniformly random pair over F
k×n
2
×F
n
2
or it is ob-
tained by choosing A
$
← F
k×n
2
, u
$
← F
k
2
, e
$
← B(n,t)
and outputting (A,u · A ⊕ e). When n, k, t are cho-
sen based on λ, we say that the DLPN(k,n,B(n,t))
problem is hard, if the success probability of any PPT
distinguisher is at most
1
2
+ negl(λ).
We recall the following proposition from (Mis-
oczki et al., 2013).
Proposition 2.1. Given the hardness of Codeword
finding problem from MDPC and QC-MDPC codes:
• Breaking the MDPC variant of McEliece or
Niederreiter is not easier than solving the syn-
drome decoding problem for a random code.
• Breaking the QC-MDPC variant of McEliece or
Niederreiter is not easier than solving the syn-
drome decoding problem for a random quasi-
cyclic linear code.
Proof. The proof is given in (Misoczki et al., 2013).
Remark 2.2. The Proposition 2.1 shows that DMcE
and DLPN problems from (n, q, w)-QC-MDPC code
are both very hard as the random case of these prob-
lems.
In the standard model assuming the hard-
ness of the DMcE(n,k,t) problem and the
DLPN(q
1
,n,B(n,t)) problem described in [(D
¨
ottling,
2014), (Nojima et al., 2008)] and assuming the Re-
mark 2.2, the scheme described above is CPA-Secure.
SECRYPT 2016 - International Conference on Security and Cryptography
434

The Underlying Zero-knowledge Argument Sys-
tem.
We recall the Underlying Zero Knowledge Argument
System used by Ezerman and al in (Ezerman et al.,
2015) which is based on Stern Zero Knowledge Proto-
col (Stern, 1996) using random double circulant ma-
trix instead of random matrix .
Let n,q,t, w, p, ω, ` be positive integers, and N =
2
`
. In this protocol, the public input consists of
matrices G ∈ F
(n−q)×n
2
, H ∈ F
p×2p
2
; N syndromes
y
0
,··· ,y
N−1
∈ F
p
2
; and a vector c ∈ F
n
2
. It al-
lows prover P to simultaneously convince verifier
V in Zero Knowledge that P possesses a vector
s ∈ B(2p,ω) corresponding to certain syndrome y
j
∈
{y
0
,··· ,y
N−1
} with hidden index j, and that c is a
correct encryption of I2B( j) via the randomized QC-
MDPC McEliece encryption. Specifically, the secret
witness of P is a tuple ( j, s, u, e) ∈ [0, N −1] × F
2p
2
×
F
n−q−`
2
× F
n
2
such that:
H · s
>
= y
>
j
and (u k I2B( j)) · G ⊕ e = c where s ∈
B(2p,ω) and e ∈ B(n,t).
2.3 Group Signature Scheme
In this paper, we are interested in the static group sig-
nature case. For that, we will follow the definitions
presented in the BMW model (Bellare et al., 2003).
Definition 2.6. A group signature scheme GS
is a tuple of four polynomial time algorithms
(KeyGen,Sign,Veri f y, Open). The description of
these algorithms is as follows:
1. KeyGen : this randomized algorithm takes as in-
put (1
λ
;1
N
), where N ∈ N
?
is the number of group
users, and outputs (gpk, gmsk, gsk), where gpk is
the group public key, gmsk is the group manager’s
secret key and gsk = {gsk[ j]}
j∈[0,N−1]
with gsk[ j]
being the secret key for the group user of index j.
2. Sign : it is a randomized algorithm, it takes as
input a secret signing key gsk[ j] for some j ∈
[0,N − 1] and a message M and returns a group
signature Σ on M.
3. Verify : it is a deterministic algorithm that takes
as input the group public key gpk, a message M,
a signature Σ on M, and returns either 1 (Accept)
or 0 (Reject).
4. Open : this deterministic algorithm takes as in-
put the group manager’s secret key gmsk, a mes-
sage M, a signature Σ on M and returns an index
j ∈ [0,N − 1] associated with a particular user, or
False indicating failure.
A group signature scheme as described in BMW
model (Bellare et al., 2003) must verify three security
requirements:
• Correctness: for all integers λ and
N, all (gpk, gmsk, gsk) obtained from
KeyGen algorithm with (1
λ
;1
N
) as in-
put, all j ∈ {0, ..,N − 1} and M ∈ {0,1}
∗
Veri f y(gpk,M, Sign(gpk,gsk[ j], M)) = 1 and
Open(gpk,gmsk, M,Sign(gpk,gsk[ j], M)) = j
• Traceability: requires that all signatures, even
those produced by a coalition of group users and
the group manager, can be traced back to a mem-
ber of the coalition.
• Anonymity: requires that, signatures generated by
two distinct group users are computationally in-
distinguishable to an adversary knowing all the
user secret keys.
Formal definitions of these properties are de-
scribed in the following definitions:
Definition 2.7 (CPA anonymity). We say that a group
signature GS = (KeyGen, Sign,Veri f y,Open) is CPA-
anonymous if for all polynomial N(·) and any PPT
adversaries A, the advantage of A in the following
experiment is negligible in λ:
1. Run (gpk,gmsk, gsk) ← KeyGen(1
λ
,1
N
) and send
(gpk, gsk) to A.
2. A outputs two identities j
0
, j
1
∈ [0, N − 1] with
a message M. Choose a random bit b and give
Sign(gsk[ j
b
],M) to A. Then, A outputs a bit b
0
.
A succeeds if b
0
= b, and the advantage of A is
defined to |Pr[A suceeds]−
1
2
|.
Definition 2.8 (Traceability). We say that a group sig-
nature GS = (KeyGen,Sign,Veri f y,Open) is trace-
able if for all polynomial N(·) and any PPT adver-
saries A, the advantage of A in the following experi-
ment is negligible in λ:
1. Run (gpk,gmsk, gsk) ← KeyGen(1
λ
,1
N
) and send
(gpk, gmsk) to A.
2. A may query the following oracles adaptively and
in any order:
• A O
Corrupt
oracle that on input j ∈ [0,N − 1],
outputs gsk[ j].
• A O
Sign
oracle that on input j, a message M,
returns Sign(gsk[ j],M).
Let CU be the set of identities queried to O
Corrupt
.
3. Finally, A outputs a message M
∗
and a signature
Σ
∗
.
A succeeds if (1) Veri f y(gpk, M
∗
,Σ
∗
) = 1 and (2)
Sign(gsk[ j], M
∗
) was never queried for j /∈ CU, yet
(3) Open(gmsk, M
∗
,Σ
∗
) /∈ CU.
A Code-based Group Signature Scheme with Shorter Public Key Length
435

3 OUR PROPOSED GROUP
SIGNATURE SCHEME
In this section, we present our improved group sig-
nature scheme of (Ezerman et al., 2015). The im-
provement concern the KeyGen algorithm which is
responsible to generate group public key gpk, group
manager secret key gmsk and group secret key gsk.
We aim to reduce the group signature public key’s
length, for that, we proceed in two steps: first we
use a generator matrix G of QC-MDPC code, as de-
scribed in (Misoczki et al., 2013), to run the ran-
domised QC-MDPC McEliece cryptosystem variant
in order to have a reduced length of public key for
the same security level achieved using Goppa codes.
Second, we act at the choice of the matrix H used
in the Zero Knowledge interactive protocol by using
random double circulant matrix than a random one as
presented in (Gaborit and Girault, 2007). The algo-
rithms Sign, Veri f y and Open remain unchanged.
Our scheme is as follows:
KeyGen(1
λ
,1
N
) : takes as input a security param-
eter λ and the number of group users N = 2
`
. Outputs:
the group public key gpk, group manager secret key
gmsk and the group secret keys gsk.
Then, we select:
- Parameters: n = n(λ), q = q(λ), w = w(t) for the
(n,q,w)-QC-MDPC code.
- Parameters: p = p(λ), ω = ω(λ) for the syndrome
decoding problem.
- A collision-resistant hash function
H : {0,1}
∗
→ {1,2,3}
k
(where k = ω(log(λ))) used
in the Fiat Schamir paradigm (Fiat and Shamir, 1987).
Let G be the public key of QC-MDPC variant of
McEliece cryptosystem, G ∈ F
(n−q)×n
2
is the gener-
ator matrix of a (n,q,w) QC-MDPC code. As de-
scribed in Remark 2.1, to generate the matrix G we
need only (n − q) bits. Unlike the original scheme
where G ∈ F
(n−q)×n
2
(of length (n −q)×n) is a gener-
ator matrix of (n,k,t) Goppa code.
Let H = [I
p
| A] ∈ F
p×2p
2
be a random double circu-
lant matrix, where I
p
is the identity matrix and A is
a p × p circulant matrix of length p . Therefore, we
need only p bits (corresponding to the first row of A)
to generate H which is not the case in the original
scheme where H is chosen uniformly random. The
KeyGen algorithm proceeds as follows:
1. Run K (n,q,w,t) to obtain a key pair (pk
ME
=
G ∈ F
(n−q)×n
2
;sk
ME
) for the QC-MDPC variant of
McEliece encryption scheme.
2. Choose a random double circulant matrix
H = [I
p
| A].
3. For each j ∈ [0, N − 1], pick s
j
$
← B(2p,ω) , and
let y
j
∈ F
p
2
be its syndrome, i.e., y
>
j
= H · s
>
j
.
4. The keys are as follows:
gpk = (G, H, y
0
,··· ,y
N−1
), gmsk = sk
ME
, gsk =
(s
0
,··· ,s
N−1
).
Sign(gsk[ j],M) : the user j sign a message M ∈
{0,1}
∗
under gpk using his secret key s = gsk[ j] by
following these steps:
1. Encrypt the binary representation of j, i.e., vec-
tor I2B( j) ∈ F
`
2
using the QC-MDPC randomised
McEliece public key G. The cipher text is
c = (u k I2B( j)) · G ⊕ e ∈ F
n
2
where u
$
← F
n−q−`
2
and e
$
← B(n,t)
2. Generate the signature Π by running the Zero
Knowledge variant of Stern in order to prove
the possession of s
$
← B(2p,ω) corresponding
to a certain syndrome y
j
∈ {y
0
,··· ,y
N−1
} with
hidden index j, and that c is a correct QC-
MDPC McEliece encryption of I2B( j). This
is done by employing the Underlying Interac-
tive Zero Knowledge Protocol with public in-
put (G,H,y
0
,··· ,y
N−1
,c) and prover’s witness
( j, s, u, e) that satisfies:
(
H · s
>
= y
j
∧ s ∈ B(2p,ω)
(u k I2B( j)) ·G ⊕ e = c ∧ e ∈ B(n,t)
(3)
3. The protocol is repeated k = ω(log(λ)) times
to achieve negligible soundness error, and then
apply the Fiat-schamir heuristic (Fiat and Shamir,
1987) to transform it in a signature.
Let Π be a non-interactive zero-knowledge
arguments of knowledge
Π = (CMT
(1)
,··· ,CMT
(k)
;(Ch
(1)
,··· ,Ch
(k)
);
RSP
(1)
,··· ,RSP
(k)
) where CMT
i
and RSP
i
are respectively the commitment and the
response for the i
th
iteration in the in-
teractive protocol and (Ch
(1)
··· ,Ch
(k)
) =
H (M;CMT
(1)
,··· ,CMT
(k)
;gpk,c) ∈ {1, 2, 3}
k
.
4. The signature is Σ = (c,Π).
Verify(gpk,M,Σ) : since Σ = (c,Π) and
Π = (CMT
(1)
,··· ,CMT
(k)
;(Ch
(1)
,··· ,Ch
(k)
);
RSP
(1)
,··· ,RSP
(k)
), the verification occur in two
steps:
1. If
(Ch
(1)
,··· ,Ch
(k)
) 6= H (M;CMT
(1)
,··· ,CMT
(k)
;
gpk, c), then return 0.
2. For i = 1 to k, run the verification step of the
interactive protocol in Section 2 with public in-
put (G,H,y
0
,··· ,y
N−1
,c) to check the validity of
SECRYPT 2016 - International Conference on Security and Cryptography
436

RSP
(i)
with respect to CMT
(i)
and Ch
(i)
. If any
of the verification conditions does not hold, then
return 0 else return 1.
Open(gmsk, M,Σ) : Parse Σ as (c,Π) and run
D(gmsk, c) to decrypt c. If decryption fails, then re-
turn False. If decryption outputs g ∈ F
`
2
then return
j = B2I(g) ∈ [0,N − 1].
Theorem 3.1. The group signature scheme is correct,
CPA anonymous, traceable and the public key has size
of ((n − q) + (N + 1)p) bits.
A sketch of proof of this theorem is in Section 4.
4 SECURITY ANALYSIS
Our code-based group signature scheme satisfies all
the security properties listed in Subsection 2.3.
It is clear that the size of the public key is
((n − q) + (N + 1)p) bits, since G and H have size
of (n − q) bits and p bits respectively and for all j ∈
[0,N − 1] y
j
is of length p bits.
• Correctness
Let j ∈ [0,N − 1] be a honest user. Consequently,
there exists a tuple ( j,s,u,e) that satisfy Equation
3. Π is a valid signature thanks to the perfect com-
pleteness of the underlying Zero Knowledge Pro-
tocol, then the algorithm Verify(gpk,M, Σ) always
outputs 1 for all M ∈ {0, 1}
∗
. On the other hand,
let c be a ciphertext of the form c = (u k I2B( j)) ·
G ⊕ e. If we run the algorithm D(gmsk,c), the
output will be I2B( j) by the correctness of the
randomised QC-MDPC variant of McEliece. Fi-
nally, Veri f y and Open are correct which implies
the correctness of the signature scheme.
• Anonymity
Since we use a randomized version of QC-MDPC
McEliece and given the hardness of DMcE(n,k,t)
problem and the DLPN(q
1
,n,B(n,t)) probleme
in the QC-MDPC case (Remark 2.2), the CPA
anonymity proof will be the same as (Ezerman
et al., 2015).
• Traceability
We consider A a PPT adversary against the trace-
ability of the scheme with success probability
equal to ε. We construct a PPT adversary F that
is able to solve a SD(2p, p,ω) problem with suc-
cess probability polynomially related to ε. Al-
gorithm F receives a challenge SD(2p, p.ω) in-
stance (
b
H,
b
y) ∈ F
p×2p
2
×F
p
2
with
b
H a random dou-
ble circulant matrix.
The goal of F is to find a vector s ∈ B(2p,ω) such
that
b
Hs
T
= y
T
. It then proceeds as follows:
1. Pick a guess j
∗
∈ [0,N − 1] and set y
j
∗
=
b
y.
2. Set H =
b
H. For each j ∈ [0,N − 1] such that
j 6= j
∗
, sample s
j
$
← B(2p, ω) and set y
j
∈ F
p
2
be its syndrome, i.e., y
T
j
= Hs
T
j
.
3. Run K (n, q, w,t) to obtain a key pair (pk
ME
=
G ∈ F
(n−q)×n
2
, sk
ME
).
4. Sent gpk = (G,H,y
0
,...,y
N−1
), gmsk = sk
ME
to A.
The forger F then initializes a set CU = ∅ and
handles the queries from A as follows:
– Queries to the random oracle H are handled by
consistently returning uniformly random values
in {1,2,3}
k
– O
Corrupt( j)
, for any j ∈ [0, N − 1] : if j 6= j
∗
,
then F sets CU = CU ∪ j and gives s
j
to A; If
j = j
∗
, then F aborts.
– O
Sign( j,M)
, for any j ∈ [0, N − 1] and any mes-
sage M : if j 6= j
∗
, then F honestly computes
a signature since it has s
j
; If j = j
∗
, then F re-
turns a simulated signature Σ
∗
.
The adversary A give a forged signature Σ
∗
on
a message M
∗
. The requirements of the trace-
ability experiment implies that:
Veri f y(gpk,M
∗
,Σ
∗
) = 1 and
Open(gmsk, M
∗
,Σ
∗
) = j
∗
.
By applying the same technics used in the trace-
ability proof (Ezerman et al., 2015), F is able
to solve the SD(2p, p,ω) with non negligible
probability which contradicted the hardness of
SD(2p, p,ω) problem.
5 RESULTS
In Table 1, we compare our results with the original
scheme one (Ezerman et al., 2015) for different size
of group users and for 80 bits security level.
We use a (n, q, w,t) QC-MDPC code of parameters
n = 9602, q = 4801, w = 90, t = 84 the size of the
matrix G is n − q = 4801 bits (parameters for 80 bits
security). It is shown in (Misoczki et al., 2013) that
for this parameters the QC-MDPC McEliece cryp-
tosystem is secure against the best attacks (Key dis-
tinguishing attack, Key recovery attack and Decoding
attack).
We also use a double circulant matrix H of size
p = 350 bits to achieve the same security level (80
bits) as it was detailed in (Gaborit and Girault, 2007).
A Code-based Group Signature Scheme with Shorter Public Key Length
437
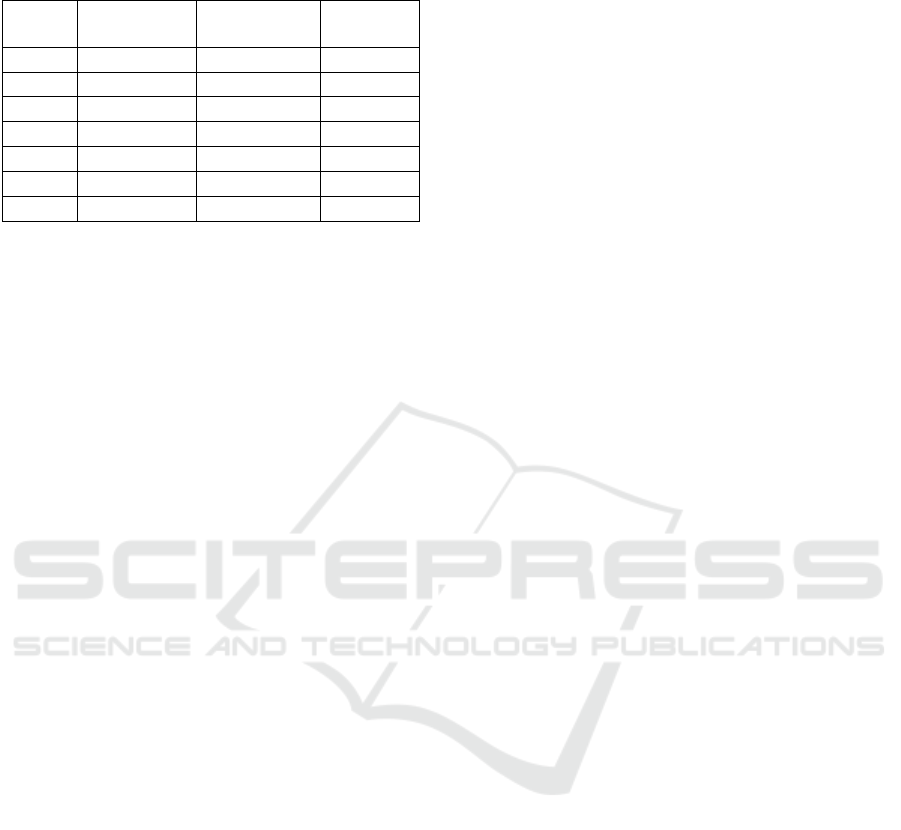
Table 1: Public keys in the original scheme case and in our
new scheme case.
N old key size Our key size factor
reduction
N=2
4
625 KB 1.34 KB 466
N=2
8
642 KB 11.84 KB 54
N=2
12
906 KB 179.84 KB 5
N=2
16
5.13 MB 2.86 MB 1.79
N=2
20
72.8 MB 45.87 MB 1.58
N=2
24
1.16 GB 0.73 GB 1.58
N=2
28
18.45 GB 11.74 GB 1.57
We notice that our results, for the public key size,
are better than ones obtained in the original scheme
especially for groups with small size. For instance,
when we have a group of N = 2
4
the size of our public
key is 466 times shorter than the previous scheme.
However when N ≥ 2
16
, the reduction factor tends to
1.57.
6 CONCLUSION
In this paper, we have proposed a provably secure
code based group signature scheme with reduced pub-
lic key length, the public keys can be 466 times
shorter than the original scheme, typically for a group
of 16 users when the public key is 1.34 kB, while the
size is 625 kB in the original scheme. The proposed
scheme also satisfies the correctness, CPA anonimity
and traceability properties which are the security re-
quirements for a static group signature scheme. In
a future work, we will try to reduce the signature
size. We can also construct a scheme achieving CCA-
anonymity and supporting revocation mechanism.
REFERENCES
Alam
´
elou, Q., Blazy, O., Cauchie, S., and Gaborit, P. A
code-based group signature scheme.
Ateniese, G., Camenisch, J., Joye, M., and Tsudik, G.
(2000). A practical and provably secure coalition-
resistant group signature scheme. In CRYPTO 2000,
Santa Barbara, California, USA, August 20-24, 2000,
Proceedings, volume 1880 of LNCS, pages 255–270.
Springer.
Bellare, M., Micciancio, D., and Warinschi, B. (2003).
Foundations of group signatures: Formal definitions,
simplified requirements, and a construction based on
general assumptions. In EUROCRYPT 2003, Warsaw,
Poland, May 4-8, 2003, Proceedings, volume 2656 of
LNCS, pages 614–629. Springer.
Bellare, M., Shi, H., and Zhang, C. (2005). Foundations
of group signatures: The case of dynamic groups. In
CT-RSA 2005, San Francisco, CA, USA, February 14-
18, 2005, Proceedings, volume 3376 of LNCS, pages
136–153. Springer.
Berlekamp, E. R., McEliece, R. J., and Van Tilborg, H. C.
(1978). On the inherent intractability of certain coding
problems. IEEE Transactions on Information Theory,
24(3):384–386.
Boneh, D., Boyen, X., and Shacham, H. (2004). Short
group signatures. In CRYPTO 2004, California, USA,
August 15-19, 2004, Proceedings, volume 3152 of
LNCS, pages 41–55. Springer.
Boyen, X. and Waters, B. (2006). Compact group signatures
without random oracles. In EUROCRYPT 2006, St.
Petersburg, Russia, May 28 - June 1, 2006. Proceed-
ings, volume 4004 of LNCS, pages 427–444. Springer.
Camenisch, J., Neven, G., and R
¨
uckert, M. (2012). Fully
anonymous attribute tokens from lattices. In SCN
2012, Amalfi, Italy, September 5-7, 2012. Proceed-
ings, volume 7485 of LNCS, pages 57–75. Springer.
Camenisch, J. and Stadler, M. (1997). In CRYPTO 97, Cali-
fornia, USA August 17–21, 1997 Proceedings, volume
1294 of LNCS, pages 410–424. Springer.
Chaum, D. and van Heyst, E. (1991). Group signatures.
In EUROCRYPT ’91, Brighton, UK, April 8-11, 1991,
Proceedings, volume 547 of LNCS, pages 257–265.
Springer.
D
¨
ottling, N. M. (2014). Cryptography based on the Hard-
ness of Decoding. PhD thesis, Karlsruhe Institute of
Technology.
Ezerman, M. F., Lee, H. T., Ling, S., Nguyen, K., and
Wang, H. (2015). A provably secure group signature
scheme from code-based assumptions. In ASIACRYPT
2015,Auckland, New Zealand, November 29 – De-
cember 3, 2015, Proceedings, Part I, volume 9452 of
LNCS, pages 260–285. Springer.
Fiat, A. and Shamir, A. (1987). How to prove your-
self: Practical solutions to identification and signature
problems. In CRYPTO ’86, Santa Barbara, Califor-
nia, USA, 1986, Proceedings, volume 263 of LNCS,
pages 186–194. Springer.
Gaborit, P. and Girault, M. (2007). Lightweight code-based
identification and signature. In Information Theory,
2007. ISIT 2007. IEEE International Symposium on,
pages 191–195. IEEE.
Gordon, S. D., Katz, J., and Vaikuntanathan, V. (2010). A
group signature scheme from lattice assumptions. In
ASIACRYPT 2010, Singapore, December 5-9, 2010.
Proceedings, volume 6477 of LNCS, pages 395–412.
Springer.
Laguillaumie, F., Langlois, A., Libert, B., and Stehl
´
e, D.
(2013). Lattice-based group signatures with logarith-
mic signature size. In ASIACRYPT 2013, Bengaluru,
India, December 1-5, 2013, Proceedings, Part II, vol-
ume 8270 of LNCS, pages 41–61. Springer.
Langlois, A., Ling, S., Nguyen, K., and Wang, H. (2014).
Lattice-based group signature scheme with verifier-
local revocation. In PKC 2014, Buenos Aires, Ar-
SECRYPT 2016 - International Conference on Security and Cryptography
438

gentina, March 26-28, 2014. Proceedings, volume
8383 of LNCS, pages 345–361. Springer.
Libert, B., Peters, T., and Yung, M. (2012). Scalable group
signatures with revocation. In EUROCRYPT 2012,
Cambridge, UK, April 15-19, 2012. Proceedings, vol-
ume 7237 of LNCS, pages 609–627. Springer.
Ling, S., Nguyen, K., and Wang, H. (2015). PKC 2015,
gaithersburg, md, usa, march 30 – april 1, 2015, pro-
ceedings. volume 9020 of LNCS, pages 427–449.
Springer.
McEliece, R. (1978). A public-key cryptosystem based on
algebraic. Coding Thv, 4244:114–116.
Misoczki, R., Tillich, J.-P., Sendrier, N., and Barreto, P. S.
(2013). Mdpc-mceliece: New mceliece variants from
moderate density parity-check codes. In Information
Theory Proceedings (ISIT), 2013 IEEE International
Symposium on, pages 2069–2073. IEEE.
Nojima, R., Imai, H., Kobara, K., and Morozov, K. (2008).
Semantic security for the mceliece cryptosystem with-
out random oracles. Designs, Codes and Cryptogra-
phy, 49(1):289–305.
Stern, J. (1996). A new paradigm for public key identi-
fication. Information Theory, IEEE Transactions on,
42(6):1757–1768.
A Code-based Group Signature Scheme with Shorter Public Key Length
439
