
IBSC System for Victims Management in Emergency Scenarios
Alexandra Rivero-Garc
´
ıa, Iv
´
an Santos-Gonz
´
alez, Candelaria Hern
´
andez-Goya and Pino Caballero-Gil
Departamento de Ingenier
´
ıa Inform
´
atica y de Sistemas, Universidad de La Laguna, Tenerife, Spain
Keywords:
Identity-based Signcryption, Keyed-Hash Message Authentication Code, Security, Triage, Emergency.
Abstract:
This work describes an optimized system designed to help the greatest number of injured people in emergency
situations, using the shortest possible time and cost. It is composed of a mobile application (assigned to
medical staff and helpers), a web service and Near Field Communication wristbands assigned to victims.
The mobile application is devoted to providing medical staff with the geolocation of victims as well as with
an assistant indicating the best route to follow in order to take care of them based on the severity of their
conditions and based on a triage method. Resolution of the routes is solved based on a classical problem, a
Travelling Salesman Problem, using a k-parition algorithm to divide the huge number of victims in different
clusters. Thus, each doctor has a specific area to assist victims. Besides, doctors can use a functionality
of the application to contact their peers through a video call when additional help is needed. The proposal
combines an keyed-Hash Message Authentication Code scheme to protect Near Field Communication tags and
an IDentity-Based Cryptosystem to the wireless communication. Specifically an IDentity-Based Signcryption
is used for communication confidentiality, authenticity and integrity, both among peers, and between server
and medical staff.
1 INTRODUCTION
The communication technologies used in smartpho-
nes and the power of these devices can help in many
complex scenarios. Smartphones are used to support
different daily tasks, their small size and high perfor-
mance is a huge advantage. This paper presents a plat-
form for improving logistics of medical staff in emer-
gency situations in a distributed way. In particular, it
is based on data obtained from a triage application de-
veloped in (Rivero-Garcıa et al., 2014), where a mo-
bile system for victim classification in emergency si-
tuations was implemented.
The definition of triage can be described as fol-
lows. A simple, complete, objective and fast pro-
cess to obtain an initial clinical assessment of people
with the objective of evaluating their immediate sur-
vival capacities and prioritizing them according their
severity is a triage. In order to achieve the classifi-
cation, all triage systems distinguish two steps. The
first triage or simple triage is used for the generation
of a classification based on the severity of injuries of
the victims evaluating their survival skills in some se-
conds. The second triage is where medical staff ana-
lyses each patient’s state: bruises, wounds and inju-
ries. Specifically, in this work, Simple Triage and Ra-
pid Treatment Algorithm (START) method is used as
first triage. Its output is the victim’s classification ba-
sed on coloured tags, where each colour defines the
priority of the victim: black, dead or irrecoverable
victims; red, victims requiring immediate care; yel-
low, victims requiring urgent care but who can wait
for treatment from half an hour to one hour; green,
victims who are not seriously injured. They can wait
for treatment more than an hour. Here the use of Near
Field Communication (NFC) is proposed to deal with
the triage result. NFC stickers are used to save triage
results based on the generation of a keyed-Hash Mes-
sage Authentication Code (HMAC) scheme. Further-
more, the route to attend victims for each doctor is
shown through a map in their smartphones based on
the priorities of victims and they can share informa-
tion peer-to-peer with their colleagues in the affected
area. All these communications are protected through
an IDentity-based (ID-based) cryptography, specifi-
cally a ID-Based Signcryption scheme (IBSC).
This work is organized as follows. Section 2 pro-
vides some preliminaries while Section 3 gives a glo-
bal view of the proposal. Then, Section 4 sketches
the system that is used to make decisions. The topic
of victim identification through NFC tags and HMAC
schemes is dealt in Section 5. The protection of se-
curity related to the medical staff through an IBSC
scheme is proposed in Section 6. A brief security ana-
276
Rivero-García, A., Santos-González, I., Hernández-Goya, C. and Caballero-Gil, P.
IBSC System for Victims Management in Emergency Scenarios.
DOI: 10.5220/0006298702760283
In Proceedings of the 2nd International Conference on Internet of Things, Big Data and Security (IoTBDS 2017), pages 276-283
ISBN: 978-989-758-245-5
Copyright © 2017 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

lysis is provided in Section 7. Finally, a few conclusi-
ons and future works close the paper.
2 PRELIMINARIES
There are still some weaknesses in emergencies ma-
nagement. The integration of new technologies into
emergency situations management and medical care
has allowed the development of tools that help to the
coordination between medical staff in emergency sce-
narios. There are different proposals designed to help
to find missing persons after a large-scale disaster.
Such as People Locator and ReUnite (of Medicine at
NIH, 2017), Google person finder (Google, 2017) and
Safety Check of Facebook (Facebook, 2017). All
these systems try to verify and share the status of pe-
ople after some disaster, specifically the proposal of
Facebook share all the information with the victim’s
friends in this social network.
Some organizations are working to provide diffe-
rent solutions related to emergency situations. One of
then is Sahana foundation (Foundation, 2017) project
aims to provide a set of modular, web-based disas-
ter management applications. This project includes
tools for synchronization between multiple instances:
a Missing Person Registry, Request and Pledge Ma-
nagement System and Volunteer coordination. Since
this proposal is a web-based framework, it has the
problem of relying on communication to the centra-
lized web-server, and thus cannot take advantage of
mobile nodes. There are no solutions to the identi-
fication of victims. The unique identification of af-
fected people is a requirement for any emergency
triage. Barcodes are a possibility because they fa-
cilitate mechanical reading (Neuenschwander et al.,
2003). Barcodes are cheap and easy to create, they
can be generated just using a standard printer. But in
an emergency situation having a printer in the affected
zone is not realistic. Radio Frequency IDentification
(RFID) is a very useful technology for victim identi-
fication as it is explained in (Inoue et al., 2006) and
in (Baracoda, 2017). Two types of tags exists, pas-
sive tags, that use the energy received from the reader
to send the identifier, and active tags, that include a
battery to increase its distance range. The problem of
this kind of communication is that a RFID reader is
needed and no security tools were provided. In (Gao
et al., 2007) a specific triage tag technology is pro-
posed. These electronic triage tags use noninvasive
biomedical sensors to continuously monitor the vital
signs of a patient and deliver pertinent information to
first responders. These are not triage tag for emer-
gency situations.
The use of NFC (Near Field Communica-
tion)(Want, 2011a) is one of the bases of the propo-
sed system, specifically NFC stickers, for automatic
patient identification. Unlike other technologies as
RFID (Zou et al., 2014), Bluetooth or Wi-Fi (Lee
et al., 2007), NFC is not oriented to the continuous
data transmission. It is necessary a temporally con-
tact between the devices that interact to allow the ex-
change of information in a quick and timely way. Alt-
hough, at first, the distance factor for transmitting in-
formation may seem a limitation it is actually the key
in this technology. The need for proximity between
devices limits the types of attacks to develop. Besi-
des, not requiring pairing between devices facilitates
its use by health staff. NFC devices may operate in
two different modes. On the one hand, in the active
mode each device generates its own electromagnetic
field (emulating the communication paradigm peer-
to-peer). On the other hand, in the passive mode
one device generates the electromagnetic field with its
own power supply. In this way, it enables that other
device starts the connection taking energy from the
field generated to power its circuit. Then the passive
device generates the response signal and transfers the
data. This mode of operation matches with the RFID
communication model and it is the one used in this
proposal.
3 GLOBAL VIEW
The main objective of the proposal is to generate a
tool to save as many time as possible in emergency
situations. Therefore, doctors have a map in their mo-
bile phones that helps them in every moment to de-
cide the route to patients. This route is based on the
severity of the injuries. Thus, collisions of doctors to
assist the same patient are avoided and decisions are
taken based on priority.
Two stages in the route generation are made. The
first one consists in the evaluation of the affected area
applying START triage method to obtain a victims’
classification based on coloured tags. This is genera-
ted by the first aid team, where there are medical staff,
firefighters or even rescue services.
As we mentioned previously, each colour defines
the priority of the victim: black, dead or irrecoverable
victims; red, victims requiring immediate care; yel-
low, victims requiring urgent care but who can wait
for treatment from half an hour to one hour; green,
victims who are not seriously injured. They can wait
for treatment more than an hour. This colour result is
stored on tags. In this case NFC (Want, 2011b) tags,
specifically NFC stickers are used to save the triage
IBSC System for Victims Management in Emergency Scenarios
277
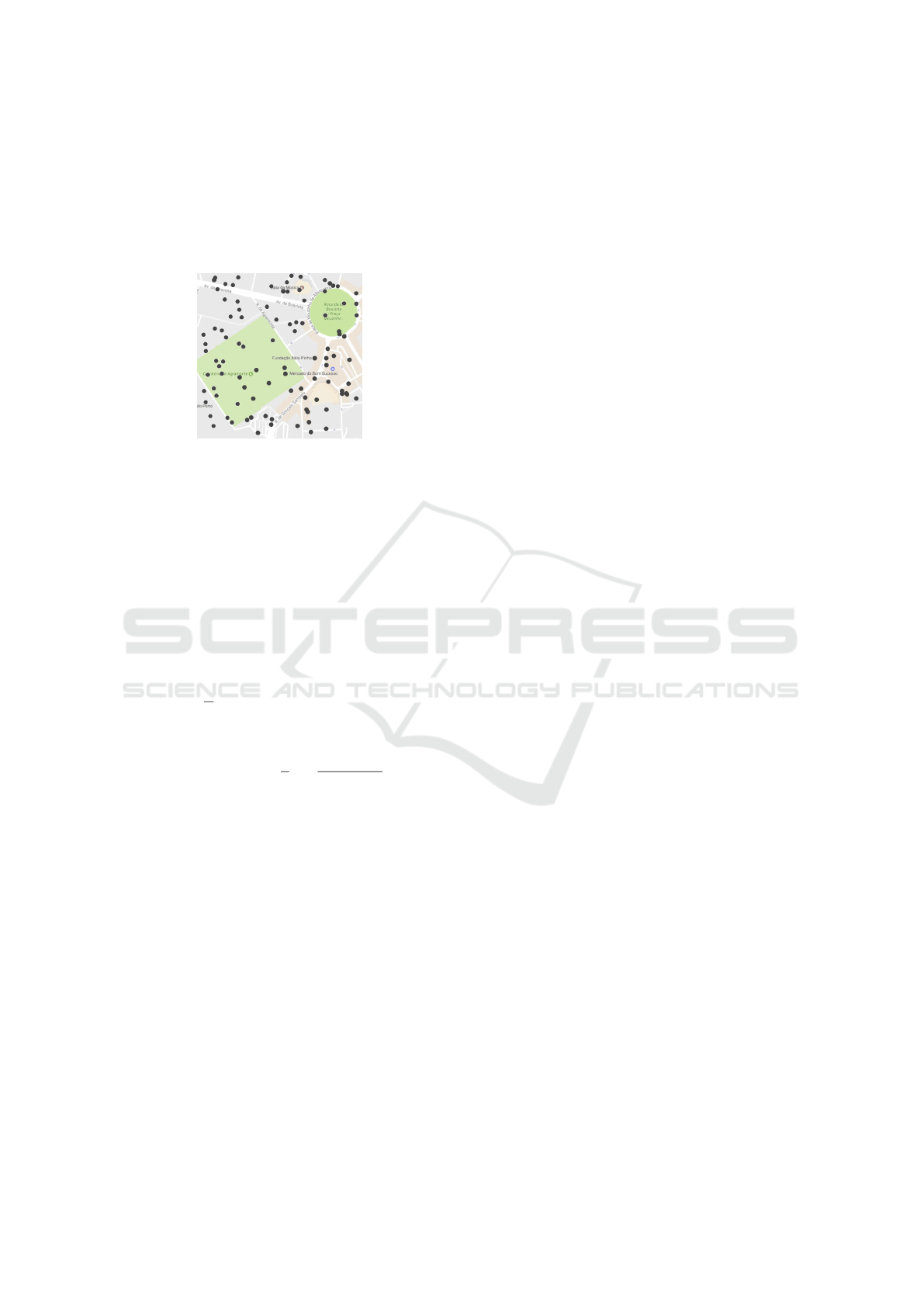
result. Note the proposed work uses NFC stickers but
multiple kind of NFC tags can be used, depending on
the emergency and the victims state. Each triage has
a location in the central server. At the end of this step
the system has a map with the location of each victim
and their triage like in figure1.
Figure 1: Victims’ location.
The second stage is based on the victim’s attention
taking into account the results of the triage priorities.
In this step the victims’ locations given by the first
triage is essential being the starting point. A graph of
each colour is generated based on the victim’s loca-
tion in a map. Victims represent nodes and the rou-
tes to reach them are de edges. Each edge has a cost.
This cost is the distance between two nodes calculated
through the Haversine Formula (Knox, 2015), where
cos
γ
AB∆λ
= cos(γ
A
) · cos(γ
B
) · hvsin(∆λ), then:
hvsin(
d
R
) = hvsin(γ
A
− γ
B
) + cos
γ
AB∆λ
(1)
Where hvsin is the haversine function:
hvsin(θ) = sen
2
(
θ
2
) =
1 − cos(θ)
2
(2)
d is the distance between two points (over the big-
ger circle of the sphere), R is the sphere radio, in our
case the Earths radio, γ
A
is the latitude of the point A,
γ
B
is the latitude of the point B and ∆λ is the diffe-
rence of the longitudes.
Finally, if sen
γ
AB
= sen(γ
A
) · sen(γ
B
) and cos
γ
AB
=
cos(γ
A
) · cos(γ
B
), the distance (d) is:
d(A, B) = R ∗ arccos(sen
γ
AB
+ cos
γ
AB
∗ cos(∆λ)) (3)
All information related to the patients who must
be attended by a doctor is done through a mobile ap-
plication. It indicates to the medical staff through a
map his/her current location and the next patient to
assist.
The application has enabled a feature called
“emergency support”. With this function when a doc-
tor or nurse requires additional help from peers he/she
can activate this mode. When they activate this fea-
ture all health personnel in the affected area receives
the notification and simply by clicking on it, they can
start a video call or a chat to help his/her colleague.
This functionality was designed to support healthcare
workers and improve the use of time in transfers be-
tween patients. Note that this feature opens a com-
munication channel between two partners through a
video streaming. Due to the high amount of infor-
mation exchanged the connection will take place by
Long Term Evolution (LTE)(Sesia et al., 2009), spe-
cifically LTE-Direct to ensure adequate and secure
communication between nodes that connect.
In the moment in which a doctor has just treat
a victim, he/she can take his/her mobile and read
the tag, mark the point as completed and check next
victim status. When the doctor arrives to the location
of the new victim, the node is automatically marked
on the map as being in the care process but he/she can
read the sticker to be sure of the authenticity of the
node. The period devoted to reach a new node is cal-
led “travelling time”. Doctors can receive notificati-
ons called “emergency support” when they are in this
“travelling time” to avoid constant notifications that
may mislead the staff in the middle of an assistance.
4 DECISION-MAKING SYSTEM
First of all, in the generation of doctors’ routes, an un-
directed graph is created from the points defined du-
ring the triage. There are as many points as patients
on the map, these are the vertices of our graph. The
edges will be defined undirected between the vertices.
This distance between points will be the cost of the
edge. The system generates one graph for each triage
colour, the main objective is treating patients based on
their injuries. First of all, the patients with red triage
are care, then patients with yellow triage and finally
the ones with green triage. Once each graph is genera-
ted, the amount of resources and the place where they
are needed. In this case resources are doctors (number
of doctors #d) that will assist patients. Their position
at all time is known. Specifically a graph based on
the Delaunay Triangulation (de Berg et al., 2008) is
created (as in figure 2) .
Initially, the system divides into clusters the red
graph. At the end, there are as many subgraphs as
doctors in the emergency area. Specifically our sy-
stem generates a k − partition based on (Hespanha,
2004), where k is the number of doctors (#d). The
system assigns to each doctor, depending on the loca-
tion, the node that is the highest priority and closest to
the coloration performed. That is, the nearest doctor
IoTBDS 2017 - 2nd International Conference on Internet of Things, Big Data and Security
278
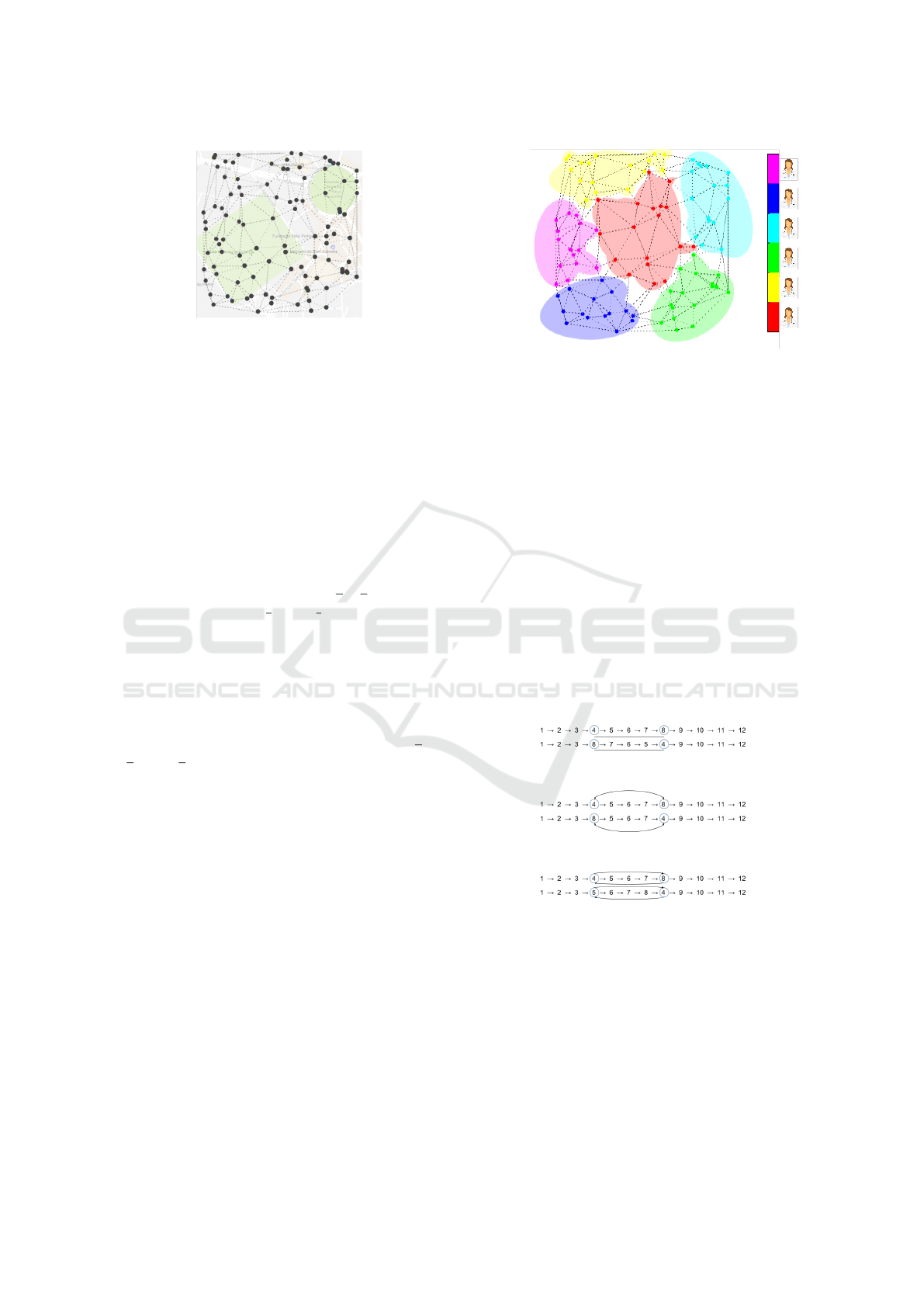
Figure 2: Graph based on Delaunay Triangulation.
is distributed for each partition, excluding the doctors
already assigned. This is a quick solution for distri-
buting to doctors in different areas. If a new node is
generated, the system automatically add it to the nea-
rest cluster, and a new doctor’s route is recalculated.
Definition 1. k-partition. Consider G = (V, E) as an
undirected graph with the set V as vertex and the set
E as edges and where the edge cost function is c :
E → [0, ∞). A k − partition of V is a collection P =
{V
1
, V
2
, ..., V
k
} of k disjoint subsets of V , whose union
equals V . The cost associated with P is defined by:
C(P) =
∑
i6= j
∑
(v,v)∈Ev∈V
i
,v∈ j
c(v, v)
The l −bounded Graph Partitioning (l −GP) pro-
blem is based on finding a k − partition P that mi-
nimizes C(P), with no more than l vertices in each
partition. The problem is based on the MAXk −
CUT problem (de Sousa et al., 2016) that find a par-
tition for F that maximizes the reward for a edge-
reward given as r : V × V → [0, ∞), where r(v, v) =
r(v, v), ∀v, v ∈ V . We considered a variation of this
problem called Hypergraph Max k-CUT (HMkC)
problem (Ageev and Sviridenko, 2000) with the sizes
of parts given and for a set of k integers s
1
, s
2
, ..., s
k
adds the constraint |V
i
| = s
i
, ∀i.
Note if there are red nodes (number of red no-
des #r) the other colours are not considered. When
these victims are attended the yellow nodes(y) are ta-
ken into account and finally green nodes(g).
When the graph is divided as in figure (figure 3)
the system assign one doctor for each zone. Then the
system analyses the path of each subgraph. This is
the problem known as the Travelling Salesman Pro-
blem (TSP) (Hoffman et al., 2013) and we solve this
through a Genetic Algorithm (Mudaliar and Modi,
2013).
These methods are adaptive and may be used to
solve optimisation and search problems. They are in-
spired by the behaviour of the species to evolve and
belong to the group of genetic algorithms.
Figure 3: k-Partition graph.
Populations are made up of different individuals.
In the problem posed here when talking about indivi-
duals we refer to victims / possible routes that can be
obtained.
A simulation has been carried out in order to vali-
date the use of this approach to build the routes. For
each subgraph a population of 100 individuals is rand-
omly generated. A selection of the best four individu-
als (the lowest cost route) is made. From them the
parts that routes have in common are selected as pa-
rents for generating the new population and children
are generated by permuting the order of the part that
does not match.
Once the new population is generated, random
mutations based on three different operations as
shown in the figure 4 are made. This iteration is repe-
ated 1000 times before getting the final result.
(a) Flip operation
(b) Swap operation
(c) Slide operation
Figure 4: Operations to generate mutations.
Finally, once the genetic algorithm is applied to
each subgraph obtained after the partition, the diffe-
rent routes for each doctor are obtained, such as it is
illustrated in figure 5.
The number of iterations and the population size
was chosen based on the results of time and costs we
obtained in different simulations. These values are
an approximation that can be adjusted at any time.
Thus, a graph of routes is generated for each doctor,
IBSC System for Victims Management in Emergency Scenarios
279

(a) Doctor #1 solution (b) Doctor #2 solution
(c) Doctor #3 solution (d) Doctor #4 solution
(e) Doctor #5 solution (f) Doctor #6 solution
Figure 5: Routes of Doctors.
based on the combination of different subgraphs that
are produced with patients of the same priority level.
At the time of generating the graph of the following
categories (colours), the last vertex added to the previ-
ous graph is the starting point of the new graph. This
generation of separated subgraphs is based on the re-
gulations when applying triage schemes because pa-
tients may be attended in order depending of the seve-
rity of injuries. If a patient walks, and a medical staff
re-triages her/him, the system updates the information
and the mobile application updates the NFC tag if it
is necessary.
The incorporation of new medical staff or new ca-
sualties does not cause any problems or additional
cost. If more nodes are added to the graph the doctors’
routes are updated paying attention to the new charac-
teristics of the affected area. The routes will be rese-
ted and each doctor can continue his/her work wit-
hout worrying about such distractions. Given a con-
straint, doctors who are in the “travelling time” will
not receive the route update until he/she has attend
next victim, this will the starting point of the route
this is never stored in the NFC tag.
5 VICTIMS IDENTIFICATION:
NFC TAGS AND HMAC
SCHEME
A member of the medical staff is who assign NFC tags
to victims in the system proposed. All of these tags
contain the result of the triage, that is to say the colour
of the triage classification, jointly with the location
and the result of a HMAC generated by the server, the
physical identifier of the NFC tag (idTag) and some
server data explained later in the paper. The stored
information will serve as patient identification both in
for triage as well as in the medical records generated
later on at the hospital. If some data is gathered the
system sends it to the server
The use of smartphones helps in the identification
of patients through NFC stickers by using phones as
NFC readers. Apart of this, devices send the physical
tag identifier to the server. In the server, two 64 by-
tes arrays are generated (Smart, 2016). They are ipad
and opad arrays, and they have default values defined
at the initialization stage. The new arrays are genera-
ted through a XOR operation combining the previous
values and the Master Secret Key (msk). The results
are ipadkey y opadkey arrays (figure 6). After that,
the HMAC value is generated with the physical tag
identifier and the triage colour result T
result
(it is a let-
ter for each colour: B, black; R, red; Y , yellow and
G, green), so the system applies a hash function to the
concatenation of these fields and the ipadkey. The
output of this hash concatenated with the opadkey is
the input to another hash function.
Figure 6: HMAC Keys Generation.
The global function may be described as:
H1 = HASH(ipadkey||idTag||T
result
)
HMAC(Tid, msk) = HASH((opadkey)||H1)
The hash function chosen for the implementation
is a SHA3
512
. The final output will be the identifier
that the will be saved in the NFC sticker tag, as you
can see in figure 7.
When a doctor or a member of the medical staff
want to access to the triage result of a patient, in
the affected zone, he/she has to read the NFC sticker
through the mobile application which sends the data
of the physical tag identifier and HMAC to the server.
The server is who verifies the authenticity of the tag
IoTBDS 2017 - 2nd International Conference on Internet of Things, Big Data and Security
280

Figure 7: HMAC Hash Operation.
and generates a new node. The doctors can see all the
nodes in the mobile phone, specifically the nodes on
his/her routes.
6 MEDICAL STAFF SECURITY:
IBSC SCHEME
Different communications modes are supported rela-
ted with medical staff. On the one hand, the commu-
nication with the server (to check NFC tags authenti-
city and synchronizing routes) and, on the other hand
the communication between them (video-calls and
chats). Authentication against the server and peers
and integrity of shared data is included. In both com-
munication modes an ID-Based Signcryption scheme
(IBSC) is used in order to achieve secure communica-
tions. This complex cryptosystem is a combination of
ID-Based Encryption (IBE) and ID-Based Signature
(IBS) that provides private and authenticated delivery
of information between two parties in an efficient way
with a composition of an encryption scheme with a
signature scheme (Boyen, 2010). This approach of-
fers the advantage of simplifying management by not
having to define a public key infrastructure. This type
of scheme was chosen due to its low computational
complexity, efficiency in terms of memory and its usa-
bility.
A crucial part of the proposal is a Private Key Ge-
nerator (PKG), a server in charge of generating health
staff private keys. The identifier of medical staff is
the number of registered medical practitioners and for
nurses the same (ID). Next, we describe the mathe-
matical basic tools used as well as the notation inclu-
ded in their description.
Definition 2. Considering two cycling groups (G, +)
and (V, ·) of the same prime order q. Pis a generator
of G and there is a bilinear map paring ˆe : G ×G → V
satisfying the following conditions:
• Bilinear: ∀P, Q ∈ G and ∀a, b ∈ Z, ˆe(aP, bQ) =
ˆe(P, Q)
ab
• Non-degenerate: ∃P
1
, P
2
∈ G that ˆe(P
1
, P
2
) 6= 1.
This means if P is generator of G, then ˆe(P, P) is
a generator of Q.
• Computability: there exists an algorithm to com-
pute ˆe(P, Q), ∀P, Q ∈ G
Some hash functions denoted as follows are also
needed: H
1
: {0, 1}
∗
→ G
∗
, H
2
: {0, 1}
∗
→ Z
∗
q
, H
3
:
Z
∗
q
→ {0, 1}
n
, where the size of the message is defined
by n. The signcryption scheme used is the ID-Based
Signcryption Scheme (IDSC) proposed in (Malone-
Lee, 2002). Next we describe some basic notation
used: x
r
←− S stands for an element x randomly selected
from a set S, x ← y denotes the assignation of the va-
lue y to x and || is used for concatenation.
The steps needed for the signcryption scheme are
the following:
• SETUP: The initial parameters are established
and the server generates the master public key
(mpk) and the master secret key (msk). For that
a prime q based on some private data k ∈ Z, two
groups G and V of order q and a bilinear pairing
map ˆe : G × G → V are selected. P ∈ G is selected
randomly and the hash functions H
1
, H
2
and H
3
are also chosen.
msk
r
← Z
∗
q
mpk ← msk · P
• EXTRACT (ID): In this step, the secret key for
each member of the medical staff based on their
ID is generated. The public key Q
ID
∈ G and
the secret key S
ID
∈ G are calculated taking into
account the msk. It should be pointed out that
this key exchange between server and the doctor
is performed using the stream cipher SNOW3G
(Santos-Gonz
´
alez et al., 2014) under the session
key obtained through an Elliptic Curve Diffie-
Hellman (ECDH)(Bos et al., 2014). the safety of
following connections as you can see in figure ??.
Q
ID
← H
1
(ID)
S
ID
← msk · Q
ID
• SIGNCRYPTION (S
ID
a
, ID
b
, m): All the mes-
sages m ∈ {0, 1}
n
will be encrypted and signed.
The receiver’s public key is generated taking into
account ID
b
and then the message is signed with
S
ID
a
and encrypted with Q
ID
b
giving as result σ (a
t-uple of three components: c, T, U).
Q
ID
b
← H
1
(ID
b
)
x
r
← Z
∗
q
T ← x · P
IBSC System for Victims Management in Emergency Scenarios
281

r ← H
2
(T ||m)
W ← x · mpk
U ← r · S
ID
a
+W
y ← ˆe(W, Q
ID
b
)
k ← H
3
(y)
c ← k ⊕ m
σ ← (c, T, U)
• UNSIGNCRYPTION (ID
a
, S
ID
b
, σ): If every-
thing is right, the message m ∈ {0, 1}
n
is returned.
Otherwise, if there are some problems in the sig-
nature or in the encryption of m, ⊥ is returned.
The sender’s public key is generated taking into
account ID
a
and then the message is unencrypted
with S
ID
b
.
Q
ID
a
← H
1
(ID
a
)
split σ as (c, T, U)
y ← ˆe(S
ID
b
, T )
k ← y
m ← k ⊕ c
r ← H
2
(T ||m)
Verification:
ˆe(U, P) == ˆe(Q
ID
a
, mpk)
r
· ˆe(T, mpk)
Note: if the verification is successful m is retur-
ned, otherwise ⊥ is returned.
7 SECURITY ANALYSIS
The proposed scheme provides protection against dif-
ferent attacks. In this sections some of them are pre-
sented. On the one hand, a spoofing attack and/or
cloning of the card will be hardly successful since it
would involve the generation of the HMAC described
taking into account the master key of the server and
the ID card. Even if an outsider obtains this informa-
tion, it should be noted that the physical identifier of
a NFC tag is unique to each element. On the other
hand, if someone emulate a NFC card from an An-
droid device, in this operating system, the emulated
device goes from being passive to being active. So
the attack would be detected since the application has
the restriction that only read NFC tags that are pas-
sive. At the time of its implementation in Android are
different and completely distinguishable communica-
tions.
Attacks related to make multiple requests to the
server, called Denial of Service (DoS) attack, are re-
stricted because only requests associated with a num-
ber of legitimate members of the medical staff will
take effect. Once the corresponding private key is as-
signed, more requests of this kind will be not atten-
ded.
Finally, the typically “Man in the Middle” attack
which conveys a successful authentication to the ser-
ver with an identifier of legitimate members of the
medical staff is improbable. This false identifica-
tion would be easily detectable because the number
of members who can make requests to the server is
limited to those who are working at the time of the
request. This authentication is one of the most impor-
tant points on every cloud computing system based on
mobile phones (Alizadeh et al., 2016).
8 CONCLUSIONS AND FUTURE
WORK
In this work, a system has been presented to may to
improve logistics and attention of casualties in ex-
treme situations. The priority is to serve the greatest
number of injuries using the shortest possible time
and cost. The tool consists on a mobile application,
NFC tags and a web service. The mobile application
helps health staff to know in every moment the posi-
tion of the victim and where they must go. Specifi-
cally the system create a graph based on the Delau-
nay Triangulation and uses a k − partition to divide
it in clusters. Different subgraphs are obtained, as
many ones as doctors in the emergency area. When
the graph is divided the system assign one doctor for
each zone. Then the system analyses the path of each
subgraph through a Genetic Algorithm to solve it like
a TSP. The system has an “emergency support” tool
to contact peers through a video call when doctors re-
quire additional support. Data security is a key ob-
jective, so for this reason a HMAC scheme is used
to protect NFC tags and an ID-Based Signcryption is
used for the communications. A first approach has
been implemented in Android and Nodejs with NFC
tags. More functionalities can be added to the server,
such as statistics, a real-time map with events, etc.
Thus, this task is part of a work in progress.
ACKNOWLEDGEMENTS
Research supported by TESIS2015010102, TE-
SIS2015010106, RTC-2014-1648-8, TEC2014-
IoTBDS 2017 - 2nd International Conference on Internet of Things, Big Data and Security
282

54110-R, MTM-2015-69138-REDT and DIG02-
INSITU.
REFERENCES
Ageev, A. A. and Sviridenko, M. I. (2000). An approxima-
tion algorithm for hypergraph max k-cut with given
sizes of parts. In Algorithms-ESA 2000, pages 32–41.
Springer.
Alizadeh, M., Abolfazli, S., Zamani, M., Baharun, S., and
Sakurai, K. (2016). Authentication in mobile cloud
computing: A survey. Journal of Network and Com-
puter Applications, 61:59–80.
Baracoda (2017). Idbluean efficient way to add rfid re-
ader/encoder to bluetooth pda and mobile phones.
Available online: http://www.baracoda.com (accessed
on 15 February 2017).
Bos, J. W., Halderman, J. A., Heninger, N., Moore, J., Na-
ehrig, M., and Wustrow, E. (2014). Elliptic curve
cryptography in practice. In International Conference
on Financial Cryptography and Data Security, pages
157–175. Springer.
Boyen, X. (2010). Identity-based signcryption. Springer.
de Berg, M., Cheong, O., van Kreveld, M., and Overmars,
M. (2008). Delaunay triangulations. Computational
Geometry: Algorithms and Applications, pages 191–
218.
de Sousa, V. J. R., Anjos, M. F., and Le Digabel, S. (2016).
Computational study of valid inequalities for the max-
imum k-cut problem.
Facebook (2017). Facebook safety check. Available on-
line: https://www.facebook.com/about/safetycheck/
(accessed on 15 February 2017).
Foundation, S. (2017). Open source disaster
management software. Available online:
https://sahanafoundation.org/ (accessed on 15
February 2017).
Gao, T., Massey, T., Selavo, L., Crawford, D., Chen, B.-
r., Lorincz, K., Shnayder, V., Hauenstein, L., Dabiri,
F., Jeng, J., et al. (2007). The advanced health and
disaster aid network: A light-weight wireless medical
system for triage. Biomedical Circuits and Systems,
IEEE Transactions on, 1(3):203–216.
Google (2017). Google person finder web page. Available
online: https://google.org/ (accessed on 15 February
2017).
Hespanha, J. P. (2004). An efficient matlab algorithm for
graph partitioning. Santa Barbara, CA, USA: Univer-
sity of California.
Hoffman, K. L., Padberg, M., and Rinaldi, G. (2013). Tra-
veling salesman problem. In Encyclopedia of opera-
tions research and management science, pages 1573–
1578. Springer.
Inoue, S., Sonoda, A., Oka, K., and Fujisaki, S. (2006).
Emergency healthcare support: Rfid-based massive
injured people management. In Proceedings of the
fourth International Workshop on Ubiquitous Com-
puting for Pervasive Healthcare Applications, Irvine,
CA.
Knox, R. W. (2015). Marcq saint-hilaire without tears. The
International Hydrographic Review, 52(2).
Lee, J.-S., Su, Y.-W., and Shen, C.-C. (2007). A compara-
tive study of wireless protocols: Bluetooth, uwb, zig-
bee, and wi-fi. In Industrial Electronics Society, 2007.
IECON 2007. 33rd Annual Conference of the IEEE,
pages 46–51. IEEE.
Malone-Lee, J. (2002). Identity-based signcryption. IACR
Cryptology ePrint Archive, 2002:98.
Mudaliar, D. N. and Modi, N. K. (2013). Unraveling travel-
ling salesman problem by genetic algorithm using m-
crossover operator. In Signal Processing Image Pro-
cessing & Pattern Recognition (ICSIPR), 2013 Inter-
national Conference on, pages 127–130. IEEE.
Neuenschwander, M., Cohen, M. R., Vaida, A. J., Pat-
chett, J. A., Kelly, J., and Trohimovich, B. (2003).
Practical guide to bar coding for patient medication
safety. AMERICAN JOURNAL OF HEALTH SYSTEM
PHARMACY, 60(8):768–779.
of Medicine at NIH, N. L. (2017). People loca-
tor and reunite web page. Available online:
https://lpf.nlm.nih.gov/ (accessed on 15 February
2017).
Rivero-Garcıa, A., Hern
´
andez-Goya, C., Santos-Gonz
´
alez,
I., and Caballero-Gil, P. (2014). Fasttriaje: A mobile
system for victim classification in emergency situati-
ons.
Santos-Gonz
´
alez, I., Rivero-Garc
´
ıa, A., Caballero-Gil, P.,
and Hern
´
andez-Goya, C. (2014). Alternative commu-
nication system for emergency situations. In WEBIST
(2), pages 397–402.
Sesia, S., Toufik, I., and Baker, M. (2009). LTE: the UMTS
long term evolution. Wiley Online Library.
Smart, N. P. (2016). Hash functions, message authentication
codes and key derivation functions. In Cryptography
Made Simple, pages 271–294. Springer.
Want, R. (2011a). Near field communication. IEEE Perva-
sive Computing, (3):4–7.
Want, R. (2011b). Near field communication. IEEE Perva-
sive Computing, (3):4–7.
Zou, Z., Chen, Q., Uysal, I., and Zheng, L. (2014). Ra-
dio frequency identification enabled wireless sensing
for intelligent food logistics. Phil. Trans. R. Soc. A,
372(2017):20130313.
IBSC System for Victims Management in Emergency Scenarios
283
