
Towards a Self-adaptive Trust Management Model for VANETs
Ilhem Souissi
1
, Nadia Ben Azzouna
1
and Tahar Berradia
2
1
Strategies for Modelling and ARtificial inTelligence research Laboratory (SMART Lab),
Institut Superieur de Gestion de Tunis, Universite de Tunis, Le Bardo, Tunis, Tunisia
2
Institut de Recherche en Systmes Electroniques Embarques (IRSEEM Lab),ESIGELEC, Rouen, France
Keywords:
Self-adaptive, Trust Management, Decision-making, VANET.
Abstract:
The vehicular ad hoc networks (VANETs) aim basically to enhance the traffic safety performance, improve
the traffic efficiency and achieve a comfortable driving experience. To reach these purposes, it is crucial to
ensure the security of this network. Trust is one of the key challenges for VANET security enhancement. Trust
management aims to investigate the relationship between the different entities in the network in order to ensure
that only trustworthy messages are delivered to drivers. Solutions for trust evaluation are not self-adaptively
adjusted to discriminate between the requirements of each class of applications. Moreover, most of these
solutions stand on the reputation to determine the trustworthiness of vehicles. However, reputation is not well-
suited in VANET due to the absence of social connections between fast moving and distributed entities. In this
paper, we present a self-adaptive trust management model that copes with the specifications of each class of
applications in a different way in order to enhance the decision-making process, minimize both time and energy
consumption for decision-making and improve the network’s security. In addition to reputation, similarity and
behavior assessment, our model uses the correlation between the event and contextual information and further
the risk assessment for decision-making.
1 INTRODUCTION
Vehicular ad hoc network (VANET) is a distributed
and highly dynamic network that mainly includes
fast moving entities (vehicles) and Road Side Units
(RSUs) (Campolo et al., 2015). VANET supports
both Vehicle-to-Vehicle communications (V2V) and
Vehicle-to-Infrastructure communications (V2I) in
order to exchange real time traffic information. It
presents a variety of applications that can be catego-
rized into three main classes: (1) Safety applications
that aim to enhance the traffic safety, (2) Traffic man-
agement applications that aim to improve the traffic
efficiency and (3) Comfort applications that intend to
achieve a comfortable driving experience.
However, VANET is vulnerable to many security
threats that can disturb the decision-making process
(La Vinh and Cavalli, 2014). Therefore, the secu-
rity of the exchanged messages is critical. Obviously,
cryptography is the best-known technique to guaran-
tee the authenticity, the privacy protection and the
confidentiality. Nonetheless, the cryptographic ma-
terials cannot cope with some issues such as authen-
ticated selfish vehicles, high dynamicity of the net-
work topology, sensor failures, etc. Recently, many
researches have been interested in the trust manage-
ment in VANETs to (1) support the cooperation be-
tween entities, (2) detect the selfish and misbehaving
ones, (3) ensure a reliable data delivery and (4) en-
hance the decision-making process.
The existing trust models handle with all of the
provided applications by the same way. However,
we notice that some of these applications are time-
critical and they require high security level such as
accident warning applications while the others are not
restrictive at all such as restaurant finder applications.
Besides, these models rely basically on the reputa-
tion, the similarity and the utility assessment (Wei
et al., 2014) (Yang, 2013) (Yao et al., 2017). Each
kind of these methodologies presents some limita-
tions. First, reputation is not well-suited due to the
absence of social connections between fast moving
entities. Second, similarity incorporates very simple
attributes such as time, location and speed. Only these
attributes are not enough to enable a vehicle to find
similarities with the other encountering vehicles. Fi-
nally, the utility stands on simple and predefined val-
ues that cannot ensure an accurate trust evaluation.
Unlike the existing solutions we present a self-
adaptive trust model that copes with the requirements
Souissi, I., Azzouna, N. and Berradia, T.
Towards a Self-adaptive Trust Management Model for VANETs.
DOI: 10.5220/0006463305130518
In Proceedings of the 14th International Joint Conference on e-Business and Telecommunications (ICETE 2017) - Volume 4: SECRYPT, pages 513-518
ISBN: 978-989-758-259-2
Copyright © 2017 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
513

of each class of applications in a different way. Ac-
cordingly, the contribution of this paper is to enhance
the decision-making process that may differ from one
situation to another according to the available infor-
mation. We show that this model can identify multiple
kinds of threats such as selfish, dishonest and misbe-
having vehicles. It may minimize the required time
for trust evaluation and reduce the energy consump-
tion. This model incorporates many concepts such
as reputation assessment, similarity between mes-
sages and between the recent and the previous sensed
events, behavior assessment, correlation between the
event and the contextual information and further the
risk assessment.
The paper is structured in the following way. In
section 2, we present a brief description of the existent
trust models as well as the adopted methodologies
and their limits. In section 3, the scheme overview is
presented. We show the benefit of the proposed self-
adaptive trust model through a real life case in section
4. Finally, in section 5, we conclude the paper and we
present future directions.
2 RELATED WORK
Trust management has undergone a spectacular evo-
lution in vehicular ad hoc networks for many years to
enhance the security and the robustness of such net-
work. Many methods for trust assessment have been
proposed in the literature (Zhang, 2011) (Soleymani
et al., 2015) (Dwivedi and Dubey, 2016). These so-
lutions depend on prominent methodologies such as
reputation, similarity, behavior, etc.
Regarding the reputation-based trust models, the
researchers have been focused on the vehicle’s trust-
worthiness to assess the progress of its trust value over
the time based on past experiences, direct interactions
and recommendations. In (Wei et al., 2014), a trust
based framework has been proposed to cope with the
security issue in VANETs. Wei et al have incorpo-
rated the direct interactions and recommendations to
evaluate and update the trust level of vehicles. An-
other similar trust based scheme for location finding
has been proposed in (Soni et al., 2015). This scheme
stands also on direct interactions and recommenda-
tions to validate or deny the presence of a desired lo-
cation.
Other models have incorporated both of the repu-
tation and similarity to assess the vehicle’s trustwor-
thiness. In (Hu et al., 2015), Hu et al have proposed
the VTrust model to ensure a robust relay selection
in VANETs. This framework stands on the global
reputation value, direct previous experiences, recom-
mendations and similarity score between the target
and the message. However, Hu et al have not de-
tailed the adopted method for the similarity assess-
ment. Differently, Yang and Al Falasi et al have been
more interested by the similarity assessment (Yang,
2013)(Al Falasi and Mohamed, 2015). Yang has pre-
sumed that the reputation of a new vehicle depends on
the reputation of similar vehicles that have reported
the same event and the similarity level between the
reporter and these vehicles. Besides, he has supposed
that evidences should be structured according to the
reputation of both of the recommender and the sender
and further on the similarity level between the evalu-
ator and the recommender. Al Falasi et al have also
adopted the similarity to evaluate the trust relation-
ship between vehicles. They have assumed that the
more vehicles behave similarly, the more they trust
each other. Additionally, they have focused on the be-
havior assessment to supervise the vehicle’s attitude
in regard to the expected one. Li and Song have been
also interested in the behavior assessment in order to
build the entity’s reputation and to detect the misbe-
having nodes (Li and Song, 2016).
Many other models have adopted the similarity
notion between messages instead of the similarity
between the groups of vehicles to detect the wrong
events. Mazilu et al have used similarity to find out
the coincidence between the received trust index (en-
capsulated on the received message) and the previous
ones (locally stored) that are related to messages re-
porting the same event (Mazilu et al., 2011). Zaidi et
al have adopted the similarity to compare their own
measurements with the others’ detections in term of
the speed, density and flow (Zaidi et al., 2014). The
correlation between these criterions enables a vehicle
to estimate the real traffic state and to detect the emer-
gent situations. A framework for smart signal traffic
control has been presented in (Płaczek and Bernas,
2016). It intends to detect the malicious data by incor-
porating the behavior and the similarity assessment.
Raya et al have also assessed the similarity be-
tween messages reporting the same event in order to
distinguish between false and real events (Raya et al.,
2008). They have focused on the data trust establish-
ment in ephemeral ad hoc networks. To assess each
message’s trustworthiness, they have incorporated (1)
the correlative trustworthiness of the event and its re-
porter, (2) the security status to discriminate between
legitimate and illegitimate entities and (3) the prox-
imity in terms of the time and location. As well, Yao
et al have been based on the utility theory to combine
the correlative trustworthiness of the event and its re-
porter and both of the time and location (Yao et al.,
2017). Besides, they have further focused on the rep-
SECRYPT 2017 - 14th International Conference on Security and Cryptography
514

utation of the entity that has reported the message.
Similarly, (Oluoch, 2015), Oluoch has almost adopted
the same methodology to assess the data trustworthi-
ness. He has assumed that the message value depends
on the role and the reputation of its reporter, time and
location.
The discussed trust management models are not
self-adaptivelyadjusted to cope with the requirements
of each kind of application. Some of them have been
proposed to deal with the overall applications’ classes
by the same way while the others have been restricted
to a particular type of application such as location
finding, traffic jams, etc. Moreover, it is obvious
that trust cannot only stand on the reputation assess-
ment especially in ephemeral networks due to the high
dynamicity of the network topology. Therefore, un-
like other solutions, we propose a self-adaptive trust
model that assumes that the decision-making differs
not only from one application to another but also from
one situation to another. Our aim is to enhance the se-
curity of the provided information, reduce the energy
consumption and ensure a fast deliveryof the reported
event message.
3 OVERVIEW
VANET is a highly dynamic network that includes
fast moving vehicles. These vehicles can meet only
once to exchange information during a limited pe-
riod. Accordingly, trust evaluation cannot only stand
on the reputation assessment. It has to consider other
concepts such as behavior and similarity assessment.
Figure 1 depicts concepts and attributes that may in-
terfere to ensure an effective and accurate decision-
based trust assessment.
In this paper, we propose a self-adaptive trust
model that aim to improve the decision making pro-
cess. The next conceptual diagram (2) depicts the dif-
ferent processes that allow a vehicle to make its deci-
sion. We assume that it is not always required to ex-
ecute all of these processes. Therefore, the decision-
making may differ from one situation to another de-
pending to the available information.
Whenever a vehicle or RSU receives a message it
starts by checking its validity. Each event may last for
a limited period. Thus, if the received message is not
valid anymore, then it will be discarded. Otherwise,
the establishment of the decision-making will depend
on the next processes.
Reputation Assessment. Whenever a vehicle V
i
receives a message from a nearby vehicle V
j
, it can
firstly check its reputation either locally (due to past
interactions between them) or from an RSU. How-
Figure 1: Representation of the required concepts and at-
tributes for trust assessment.
ever, in highly dynamic networks, past interactions do
not always exist. Therefore, if V
i
have no past interac-
tions with V
j
(strange) then, we suppose that the type
of this latter (e.g. police car, bus, etc.) may reflect its
trust level. Nonetheless, if V
i
has enough information
on the reputation of V
j
(familiar) then, it may decide
whether to trust the received message or not.
Similarity Assessment between Recent and
Previous Sensed Events. V
i
can compare the recent
received event with the previous sensed ones at the
same position. In VANET, some events may last for
a long period (days up to weeks) such as a working
zone whereas other events have a short validity such
as an accident. Based on the validity, the position and
the number of similar previous events, V
i
may esti-
mate the feasibility of the recent received one.
Similarity Assessment between Messages. V
i
can investigate the similarity between all of the re-
ceived messages based on a set of attributes. The time
and location denotes respectively when and where the
event has been reported. The higher the number of
similar messages in terms of time and location, the
better the decision is. Besides, the message passes
through a number of intermediate hops (NH) that may
point out the likelihood of being threatened. Accord-
ingly, the similarity assessment between messages in
term of NH allow us to identify the more risky ones.
Moreover, similarity between messages can be estab-
lished based on the signal strength of each received
message. If V
i
detects any similar signal strengths
then, it can decide that messages belong to the same
entity that may present itself under different identities
and different positions.
Towards a Self-adaptive Trust Management Model for VANETs
515

Figure 2: Conceptual Diagram for decision-making based
on reputation, behavior and similarity assessment.
Behavior Assessment. V
i
can evaluate the behav-
ior of V
j
based on a set of attributes such as speed,
Breaking Frequency (BF), etc. For example, if V
j
warns V
i
about an accident on the lane L
1
then V
i
may
supervise the behavior of V
j
versus the received alert
and with respect to its direction. If V
j
belongs to the
accident direction and it keeps moving with the same
speed or on the same lane (L
1
) thenV
i
may decide that
V
j
misbehaves. Besides, if the speed ofV
j
mismatches
with the density and the flow then, V
i
discards the re-
ceived alert. Moreover,the BF may play an important
role to supervise the behavior of V
j
. In emergent sit-
uations, this attribute may prove the existent of a risk
especially in highways where the BF is usually low.
Correlation between the Event and Contex-
tual Information. V
i
can check the correlation be-
tween the received event and any contextual infor-
mation such as vibration detection for accident alert,
the weather (foggy, snowy, etc.), the date (holidays,
weekend, etc.), lighting conditions, etc. For example,
if Vi receives the message ’slippery road’ and it de-
tects that there is a dangerous turn ahead, there is no
lights and it is raining then, it can believe the warning
message and slow down.
Risk Assessment. If the driver cannot make a de-
cision based on all of the previous alternatives then, it
can choose to assess the risk of believing or denying
the received message. On the one hand, for comfort
applications such as searching for parking packs, if
V
i
receives a message that indicates that there is no
free spaces and it cannot ensure that this alert is accu-
rate then, it may decide to look for a space by itself.
On the other hand, in critical applications such as ac-
cident warning, V
i
may analyze the consequences of
considering or denying the alert in both sides to de-
cide whether to follow the same road or to change it.
In this section, we have shown that our pro-
posal starts by locally estimating the credibility of
the reported event (reputation, similarity between re-
cent and previous sensed events). The aim behind
this scheduling is to reduce both of time and en-
ergy consumption while preserving the accuracy of
the decision-making. Moreover, this model can meet
with the specifications of each class of applications.
Safety applications require high accuracy and fast
decision-making to disseminate the alert. Therefore,
whenever a vehicle get sufficient information about
the alert trustworthiness, it may not run the remain-
ing processes and decide to broadcast the message to
nearby vehicles. Regarding the comfort applications,
they are not restrictive as the previous class. Usually,
they do not require high security and accuracy.
4 CASE STUDY
In this section, we present the following scenario to
investigate the benefit of our model in a real life case
as depicted in Figure 3. This latter does not report
real distances between different vehicles. It is only
proposed to give an overall idea about the dissemina-
tion of an alert. We have assumed that an accident
has occurred in a highway between two vehicles due
to the excessive speed (V
1
and V
2
have been entirely
damaged). Thus, the nearest vehicle V
3
can estimate
the position of the accident based on the embedded
sensors. Accordingly, the quality of these sensors has
to be assessed so as to detect any deficiency in terms
of timeliness, accuracy, etc. Subsequently, V
3
has to
evaluate its own trustworthiness by itself based on the
quality of its own measurements. Thereafter, it has to
decide whether to broadcast the alert to its adjacents
or not. In this case study, we assume that the dis-
semination of the accident warning message can be
described as follows.
SECRYPT 2017 - 14th International Conference on Security and Cryptography
516
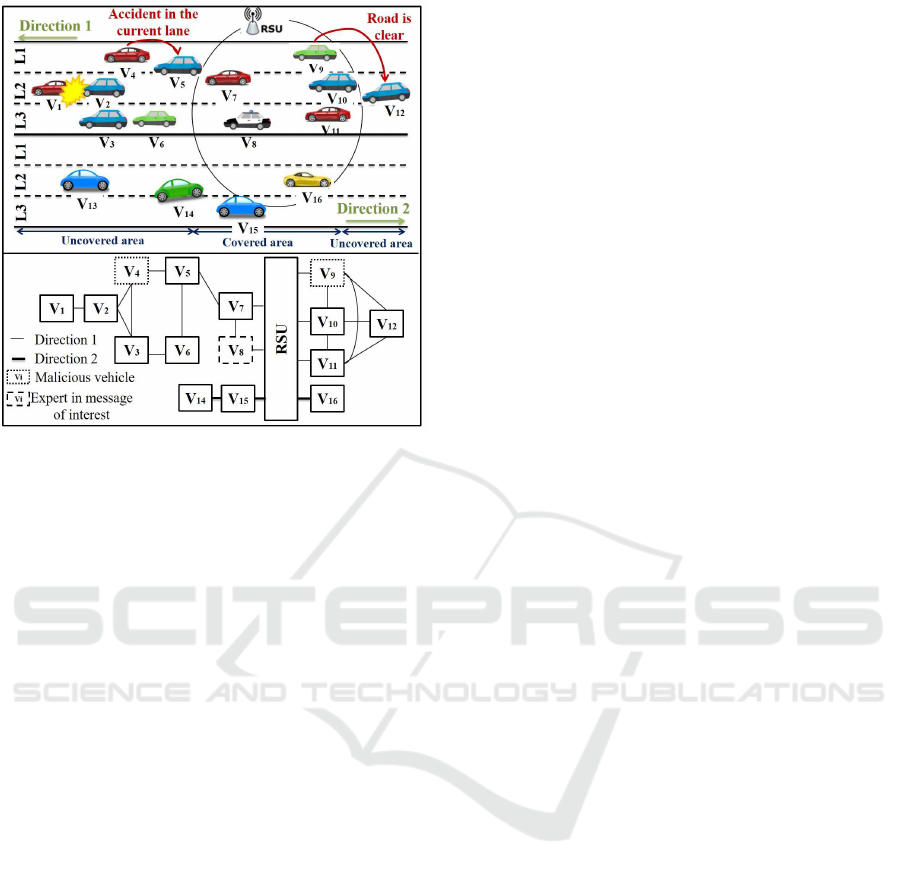
Figure 3: Graphic representation of the dissemination of an
accident warning in a highway.
1. When V
4
receives the alert from V
3
, it perceives
that it also belongs to the transmission range of
V
2
but it did not receive any alert from its side.
According to our proposal, V
4
starts by check-
ing if it has any previous interactions with V
2
and V
3
. However, these vehicles are met for the
first time. Thus, reputation assessment is not
enough to make the appropriate decision. There-
after, V
4
verifies if it has detected any similar pre-
vious events for the same position. Nonetheless,
an accident remains valid only for a short period.
Moreover, V
4
cannot stand on the similarity as-
sessment between messages given that it has re-
ceived only one message. Afterwards, V
4
can su-
pervise the behavior of both of V
2
and V
3
. It real-
izes thatV
2
is not moving anymore whileV
3
slows
down due to the existence of some broken glass in
its lane. Consequently, V
4
may ensure that the re-
ceived alert is trustworthy. It decides to broadcast
the alert but to lie about the lane of the accident.
Similarly, V
6
decides to accept the warning mes-
sage based only on the behavior assessment ofV
3
.
2. V
5
receives an accident warning message from V
4
and V
6
. It detects that there is a conflict regarding
the lane of the accident. Similarly, we assume that
(1) the reputation assessment, (2) the short valid-
ity of the event and (3) the similarity assessment
between messages do not allow V
5
to identify the
malicious vehicle. Afterwards, V
5
remarks that
V
6
and V
4
keep moving respectively in L
3
and L
1
andV
6
slows down (becauseV
3
, the vehicle ahead,
slowsdown) whileV
4
keeps moving with the same
speed. Consequently, it may deduce that V
4
is ma-
licious because it did not slow down and further it
did not change the lane if L
2
is really free. There-
fore, V
5
decides to keep moving in the same lane,
and to broadcast the message received from V
6
.
3. V
7
receives the alert only from V
5
. V
7
belongs to
the transmission range of the RSU. It requests the
reputation of V
5
from the RSU. We assume that
the (1) recovered reputation, (2) the similarity be-
tween recent and local previous events and (3) the
similarity between other received messages do not
allow V
7
to decide whether to trust the alert or
not. Thereafter, V
7
tries to inspect the behavior
of V
5
. It detects that V
5
keeps moving with the
same speed and on the same lane which is differ-
ent from the lane of the accident. Based only on
these information,V
7
cannot believe that the acci-
dent exists. Afterwards, V
7
looks for any contex-
tual information that can prove the accident alert.
We assume that V
7
cannot observe any contextual
information. Therefore, it decides to assess the
consequences of believing in the received warn-
ing or not based on the event type. Therefore, it
decides to trust the alert and to move from L
2
.
4. V
7
and V
8
have high reputation values (V
8
is expert
in message of interest). Thus, the RSU trust the
warning message reported by V
7
and V
8
and it de-
cides to broadcast it to the other covered vehicles
(V
9
, V
10
and V
11
). All of these vehicles trust the
alert. However, V
9
decides to lie about the traffic
state. The RSU may perceive that V
9
is malicious
and it decides to reduce its reputation value.
5. V
12
belongs to the transmission range of V
9
, V
10
and V
11
. It receives three warning messages at
near time. V
9
says that the road is clear whereas
V
10
and V
11
say that there is an accident. We as-
sume that V
12
has no past experiences with the
three previous vehicles. As well, it cannot rely
on the similarity assessment between the recent
and the previous sensed events. Thereafter, V
12
checks the similarity between all of the received
messages. It realizes that both of V
10
and V
11
re-
port the same time and the same location of the
accident. Besides, V
10
and V
11
have different sig-
nal strengths which mean that there is no Sybil
attack. Accordingly, V
12
decides to accept the ac-
cident warning message.
This scenario shows that our proposed adaptive
trust model may perform well to identify vehicles that
misbehave such as fake information attack, drop mes-
sage attack, Sybil attack and collusion attack. Be-
sides, this model can reduce the energy consumption
since it does not require recommendations from third
Towards a Self-adaptive Trust Management Model for VANETs
517

parties. We have also shown that whenever a vehicle
get sufficient information about the alert trustworthi-
ness, it may not run the remaining processes. This
fact may accelerate the decision-making process es-
pecially for time-critical applications.
5 CONCLUSIONS
This paper proposes a self-adaptive trust model for
VANETs. This model intends to handle with the spec-
ifications of each class of applications in a different
manner. The aim of our proposal is to enhance the
decision-making process, minimize both time and en-
ergy for decision-making and improve the network’s
security. We have applied this model on a real life
case to evaluate its performance and to show its ben-
efits. In the future, we plan to detail this proposal
and further to identify the appropriate techniques to
estimate the accurate trust value. Besides, we plan to
pay more attention to the quality of raw sensed data
in order to preserve the quality of the provided appli-
cations. Finally, we have to investigate and validate
the efficiency, scalability, robustness and overhead of
this model.
ACKNOWLEDGEMENTS
This work was supported by the PHC Utique pro-
gram of the French Ministry of Foreign Affairs and
Ministry of higher education and research and the
Tunisian Ministry of higher education and scientific
research in the CMCU project number 16G1404.
REFERENCES
Al Falasi, H. and Mohamed, N. (2015). Similarity-based
trust management system for detecting fake safety
messages in vanets. In International Conference on
Internet of Vehicles, pages 273–284. Springer.
Campolo, C., Molinaro, A., and Scopigno, R. (2015). Ve-
hicular ad hoc networks. Standards, Solutions, and
Research.
Dwivedi, S. and Dubey, R. (2016). Review in trust and
vehicle scenario in vanet. International Journal of
Future Generation Communication and Networking,
9(5):305–314.
Hu, H., Lu, R., and Zhang, Z. (2015). Vtrust: a robust
trust framework for relay selection in hybrid vehicular
communications. In Global Communications Confer-
ence (GLOBECOM), 2015 IEEE, pages 1–6. IEEE.
La Vinh, H. and Cavalli, A. R. (2014). Security attacks
and solutions in vehicular ad hoc networks: a survey.
International journal on AdHoc networking systems
(IJANS), 4(2):1–20.
Li, W. and Song, H. (2016). Art: An attack-resistant trust
management scheme for securing vehicular ad hoc
networks. IEEE Transactions on Intelligent Trans-
portation Systems, 17(4):960–969.
Mazilu, S., Teler, M., and Dobre, C. (2011). Securing ve-
hicular networks based on data-trust computation. In
P2P, Parallel, Grid, Cloud and Internet Computing
(3PGCIC), 2011 International Conference on, pages
51–58. IEEE.
Oluoch, J. O. (2015). A unified framework for trust manage-
ment in Vehicular Ad Hoc Networks (VANET). PhD
thesis, Oakland University.
Płaczek, B. and Bernas, M. (2016). Detection of malicious
data in vehicular ad hoc networks for traffic signal
control applications. In International Conference on
Computer Networks, pages 72–82. Springer.
Raya, M., Papadimitratos, P., Gligor, V. D., and Hubaux,
J.-P. (2008). On data-centric trust establishment in
ephemeral ad hoc networks. In INFOCOM 2008.
The 27th Conference on Computer Communications.
IEEE, pages 1238–1246. IEEE.
Soleymani, S. A., Abdullah, A. H., Hassan, W. H., Anisi,
M. H., Goudarzi, S., Baee, M. A. R., and Man-
dala, S. (2015). Trust management in vehicular ad
hoc network: a systematic review. EURASIP Jour-
nal on Wireless Communications and Networking,
2015(1):146.
Soni, S., Sharma, K., and Chaurasia, B. K. (2015). Trust
based scheme for location finding in vanets. In Ad-
vances in Optical Science and Engineering, pages
425–432. Springer.
Wei, Z., Yu, F. R., and Boukerche, A. (2014). Trust based
security enhancements for vehicular ad hocnetworks.
In Proceedings of the fourth ACM international sym-
posium on Development and analysis of intelligent ve-
hicular networks and applications, pages 103–109.
ACM.
Yang, N. (2013). A similarity based trust and reputa-
tion management framework for vanets. International
Journal of Future Generation Communication and
Networking, 6(2):25–34.
Yao, X., Zhang, X., Ning, H., and Li, P. (2017). Using trust
model to ensure reliable data acquisition in vanets. Ad
Hoc Networks, 55:107–118.
Zaidi, K., Milojevic, M., Rakocevic, V., and Rajarajan, M.
(2014). Data-centric rogue node detection in vanets.
In Trust, Security and Privacy in Computing and
Communications (TrustCom), 2014 IEEE 13th Inter-
national Conference on, pages 398–405. IEEE.
Zhang, J. (2011). A survey on trust management for
vanets. In Advanced information networking and ap-
plications (AINA), 2011 IEEE international confer-
ence on, pages 105–112. IEEE.
SECRYPT 2017 - 14th International Conference on Security and Cryptography
518
