
Clustering-based Approach for Anomaly Detection in XACML Policies
Maryem Ait El Hadj
1
, Meryeme Ayache
1
, Yahya Benkaouz
2
, Ahmed Khoumsi
3
and Mohammed Erradi
1
1
NDSR Group, ENSIAS, Mohammed V University in Rabat, Morocco
2
Conception and Systems Laboratory, FSR, Mohammed V University in Rabat, Morocco
3
Dept. Electrical & Comp. Eng., University of Sherbrooke, Sherbrooke, Canada
Keywords:
ABAC, XACML Policies, Clustering, Similarity Computation, Anomaly Detection.
Abstract:
The development of distributed applications arises multiple security issues such as access control. Attribute-
Based Access Control has been proposed as a generic access control model, which provides more flexibility
and promotes information and security sharing. eXtensible Access Control Markup Language (XACML) is
the most convenient way to express ABAC policies. However, in distributed environments, XACML policies
become more complex and hard to manage. In fact, an XACML policy in distributed applications may be
aggregated from multiple parties and can be managed by more than one administrator. Therefore, it may
contain several anomalies such as conflicts and redundancies, which may affect the performance of the policy
execution. In this paper, we propose an anomaly detection method based on the decomposition of a policy into
clusters before searching anomalies within each cluster. Our evaluation results demonstrate the efficiency of
the suggested approach.
1 INTRODUCTION
Attribute-Based Access Control model (ABAC)
(Yuan and Tong, 2005) has been suggested as a
generic access control model. ABAC considers a set
of attributes, based on which access decisions should
be taken. The attributes are any information that can
be assigned to a subject (i.e. the user or the process
that takes action on a resource), a resource (i.e. the
entity that is acted upon by a subject) and an envi-
ronment (i.e. the operational and technical context in
which the information access occurs).
eXtensible Access Control Markup Language
(XACML) (Anderson et al., 2003) is the most conve-
nient way to express ABAC model. In fact, XACML
defines an XML schema that supports the ABAC
model. Each XACML policy contains a set of rules,
each rule being composed of attributes and a decision
effect (deny/permit), that decides over a given request
to access a given resource. XACML policy represen-
tation is more expressive and fine-grained. However,
in large collaborative platforms, processing and ana-
lyzing XACML policies might be very hard and com-
plicated. This is due to the massive amount of infor-
mation that should be considered as attributes. There-
fore, XACML policies may contain several anoma-
lies, such as redundancies and conflicting rules, which
may affect the performance of the policy execution.
Detecting automatically such anomalies in large sets
of complex policies is primordial.
In this paper, we propose an approach to detect
anomalies within an XACML policy. Inspired by
(Benkaouz et al., 2016), the suggested approach is
based on decomposing the policy into clusters before
searching anomalies within each cluster. More pre-
cisely, given an XACML policy, we proceed as fol-
lows: (1) extract the rules of the XACML policy, (2)
compute a similarity score for each pair of rules, (3)
regroup similar rules into clusters. Finally, (4) de-
tect anomalies within each cluster. In this paper, we
consider three main categories of anomalies, redun-
dancy, conflict of modality and conflict of fraction
permission. The evaluation results demonstrate the
efficiency of the suggested approach.
The rest of the paper is organized as follows: Sec-
tion 2 present related work. In section 3 we present
how rules are expressed and the similarity measure
adopted. The clustering algorithm is presented in sec-
tion 4. Section 5 describes the policy anomaly detec-
tion method. Section 6 reports experimental results.
548
Hadj, M., Ayache, M., Benkaouz, Y., Khoumsi, A. and Erradi, M.
Clustering-based Approach for Anomaly Detection in XACML Policies.
DOI: 10.5220/0006471205480553
In Proceedings of the 14th International Joint Conference on e-Business and Telecommunications (ICETE 2017) - Volume 4: SECRYPT, pages 548-553
ISBN: 978-989-758-259-2
Copyright © 2017 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

Finally, the conclusion and expected future work are
drawn in section 7.
2 RELATED WORK
Regarding anomalies classification, Khoumsi et al.
(Khoumsi et al., 2016) categorize the anomalies into
two categories: a conflicting anomaly and a noncon-
flicting anomaly. On the other hand, Jonathan et al.
(Moffett and Sloman, 1994) have classified the poli-
cies conflicts into four different categories: conflict of
modality (permit/deny), conflict between imperative
and authority policy (obliged/deny), conflict of prior-
ities occurs when the resources are limited to meet
the demands upon them, and conflict of duties when a
subject has two tasks and maintains them simultane-
ously.
In the context of XACML, Mourad et al. (Mourad
et al., 2015) use UML to offer model-driven specifi-
cation of XACML policies in order to detect conflict-
ing and redundant rules. Hu et al (Hu et al., 2013)
consider representing XACML policies as decision
trees to detect conflicts and redundancies. Another
representation of XACML policies was proposed by
Stepien et al. (Stepien and Felty, 2016). They repre-
sent XACML policies using Prolog’s built-in power-
ful indexing system.
Contrary to the works discussed above, our work
takes into account a large set of attributes. It proposes
an anomaly detection method performed in each clus-
ter of rules, instead of the whole policy set, which
implies less processing time. An advantage of our
anomaly detection method is that it is performed be-
fore even enforcing the policy in the system, which
offers the ability to correct the anomalies and gain a
significant improvement in policy decision time.
3 RULES EXPRESSION AND
SIMILARITY COMPUTATION
3.1 Rules Expression
In an XACML policy, each rule has three categories of
attributes (subject, resource and environment). Each
of the 3 categories is indicated by x = s, r or e. A
rule is specified by an action decision to be taken if
the attributes satisfy a given condition (or profile).
The action decision is noted in the form X
act
, where
X is Permit or Deny to indicate that the action act
is permitted or denied, respectively. Permit
read
and
Deny
write
are two examples of action decisions.
The profile of a rule is specified by assigning a
set of values to all attributes. We use the expres-
sion attr
name ∈ attr values to assign a set of val-
ues attr values to an attribute identified by attr name.
The assignments corresponding to the same category
are separated by a comma ”,”, while a semicolon ”;”
means the passing to the next category. The seman-
tics of the rule is that its action decision is taken if
for each assignment attr
name ∈ attr values, the at-
tribute attr name takes one of the values belonging to
attr
values. The formal expression of a rule profile is
therefore as follows:
X
act
(attr
name
1
∈ attr values
1
,...;attr name
i
=
attr
values
i
,...)
Example : Permit
read
(position ∈ {doc}, spe-
cialist ∈{generalist} , team ∈ {oncology}, experi-
ence ∈ {+10} , grade ∈ {Registrar} , department
∈ {oncology}; type ∈ {PR/CAT} , formatType ∈
{AST} , degreeOfConfidentiality ∈ {Secret} ; Orga-
nization ∈ {EMS} , time ∈ {8-12}).
The attributes of the Subject category are: posi-
tion, specialist, team, experience, grade, department.
The attributes of the Resource category are: type, for-
matType, degreeOfConfidentiality. The attributes of
the Environment category are: Organization, time.
3.2 Similarity Computation
The rule similarity measure is a function S
rule
that as-
signs a similarity score S
rule
(r
i
,r
j
) to any two given
rules r
i
and r
j
. Such a score reflects the degree of
similarity between r
i
and r
j
, with respect to their sub-
ject, resource and environment attributes values.
The formal definition of the similarity score
S
rule
(r
i
,r
j
) is given in Equation 1, which is the sum
of the three similarity scores S
s
(r
i
,r
j
), S
r
(r
i
,r
j
) and
S
e
(r
i
,r
j
) related to the three attribute categories (sub-
ject, resource and environment), which are weighted
by values W
s
, W
r
and W
e
respectively. W
s
, W
r
and W
e
can be chosen to reflect the relative importance to be
given to the similarity computation. The weight val-
ues must satisfy the constraint: W
s
+W
r
+W
e
= 1.
S
rule
(r
i
,r
j
) = W
s
S
s
(r
i
,r
j
) +W
r
S
r
(r
i
,r
j
) +W
e
S
e
(r
i
,r
j
)
(1)
The assignment of weights relies on user needs
(i.e., the weight values can be specified depending on
a specific application). For example, if a user would
like to compute the similarity score of Subject at-
tributes regardless of Resource and Environment at-
tributes, he can set W
s
to 1, and W
r
and W
s
to 0. In
this paper, the same value
1
3
is assigned to the three
weights by default.
Before continuing, we need to define the follow-
ing notation:
Clustering-based Approach for Anomaly Detection in XACML Policies
549

- ATT
x
(r
i
) is the set of attribute names of category
x in rule r
i
.
- S
att
(r
i
,r
j
) is a score reflecting the similarity of r
i
and r
j
based uniquely on att which is a common
attribute of r
i
and r
j
.
- W
att
(r
i
,r
j
) is a nonnegative value that reflects the
relative importance of an attribute att among all
the common attributes of r
i
and r
j
of the same
category as att. The sum of all these weights is
equal to 1, i.e.,
∑
att∈ATT
x
(r
i
)∩ATT
x
(r
j
)
W
att
= 1 for
each category x.
- V
att
(r
i
) is the set of values assigned to the attribute
att in the rule r
i
.
- | X | denotes the number of elements belonging to
a set X.
Each similarity score S
x
(r
i
,r j) (for x = s, r, e) of
Eq. 1 is computed based on Eq. 2. This latter consists
in summing the scores S
att
(r
i
,r
j
) for every attribute
att of category x that is common to r
i
and r
j
. Besides,
every S
att
(r
i
,r
j
) is weighted by W
att
(r
i
,r
j
).
S
x
(r
i
,r
j
) =
∑
att∈ATT
x
(r
i
)∩ATT
x
(r
j
)
W
att
(r
i
,r
j
)S
att
(r
i
,r
j
)
(2)
Equation 3 shows how each similarity S
att
(r
i
,r
j
)
is computed is computed. This equation consists in
estimating the number of elements that are common
to V
att
(r
i
) and V
att
(r
j
) relatively to the total number
of elements in V
att
(r
i
) ∪V
att
(r
j
).
S
att
(r
i
,r
j
) =
| V
att
(r
i
) ∩V
att
(r
j
) |
| V
att
(r
i
) ∪V
att
(r
j
) |
(3)
Example:
r
1
: Permit
read
(Group ∈ IBM, Designation
∈ {Professor, PostDoc, TechStaff}; File-Type ∈
{Source, Documentation, Executable}; Time ∈ [8:00,
18:00]).
r
2
: Permit
read
(Group ∈ IBM, Designation ∈
{Student, TechStaff}; File-Type ∈ {Source, Docu-
mentation}; Time ∈ [12:00, 16:00]).
For the Sub ject category, we have two
attributes, Group (g) and Designation (d).
For r
1
, V
g
(r
1
) = {IBM} and V
d
(r
1
) =
{Professor,PostDoc,TechStaf f}. While for r
2
,
V
g
(r
2
) = {IBM} and V
d
(r
2
) = {Student,TechStaf f}.
For the Resource category, we have the at-
tribute File-Type (ft). Where for r
1
V
ft
(r
1
) =
{Source,Documentation,Executable} and for r
2
,
V
ft
(r
2
) = {Source,Documentation}.
For the Environment category, we have the at-
tribute Time (t). For r
1
, V
t
(r
1
) = [8:00, 18:00]. And
for r
2
, V
t
(r
2
) = [12:00, 16:00].
The similarity between r
1
and r
2
is computed us-
ing Eqs (1, 2, 3) as follows:
Use of Eq. (1). Assuming that W
s
= W
r
= W
e
=
1
3
:
S
rule
(r
1
,r
2
) =
1
3
S
s
(r
1
,r
2
) +
1
3
S
r
(r
1
,r
2
) +
1
3
S
e
(r
1
,r
2
)
Use of Eq. (2). Each of the above S
s
(r
1
,r
2
),
S
r
(r
1
,r
2
) and S
e
(r
1
,r
2
) is computed as follows, as-
suming that W
g
(r
1
,r
2
) = W
d
(r
1
,r
2
) =
1
2
, W
ft
(r
1
,r
2
) =
W
t
(r
1
,r
2
) = 1:
- S
s
(r
1
,r
2
) =
1
2
S
g
(r
1
,r
2
) +
1
2
S
d
(r
1
,r
2
)
- S
r
(r
1
,r
2
) = S
ft
(r
1
,r
2
)
- S
e
(r
1
,r
2
) = S
t
(r
1
,r
2
)
Use of Eq. (3). Each of the above S
g
(r
1
,r
2
),
S
d
(r
1
,r
2
), S
ft
(r
1
,r
2
) and S
t
(r
1
,r
2
) is computed as fol-
lows:
- S
g
(r
1
,r
2
) =
|V
g
(r
i
)∩V
g
(r
j
)|
|V
g
(r
i
)∪V
g
(r
j
)|
=
|{IBM}|
|{IBM}|
= 1
- S
d
(r
1
,r
2
) =
|V
d
(r
i
)∩V
d
(r
j
)|
|V
d
(r
i
)∪V
d
(r
j
)|
=
|{TechSta f f }|
|{Prof essor,PostDoc,TechSta f f,Student}|
=
1
4
- S
ft
(r
1
,r
2
) =
|V
ft
(r
i
)∩V
ft
(r
j
)|
|V
ft
(r
i
)∪V
ft
(r
j
)|
=
|{Source,Documentation}|
|{Source,Documentation,Executable}|
=
2
3
- S
t
(r
1
,r
2
) =
|V
t
(r
i
)∩V
t
(r
j
)|
|V
t
(r
i
)∪V
t
(r
j
)|
=
|[12:00,16:00]|
|[8:00,18:00]|
=
4
10
By combining all these equations, we obtain:
- S
s
(r
1
,r
2
) =
1
2
S
g
(r
1
,r
2
) +
1
2
S
d
(r
1
,r
2
) =
1
2
+
1
2
×
1
4
= 0.62
- S
r
(r
1
,r
2
) = S
ft
(r
1
,r
2
) =
2
3
- S
e
(r
1
,r
2
) = S
t
(r
1
,r
2
) =
4
10
- S
rule
(r
1
,r
2
) =
1
3
S
s
(r
1
,r
2
) +
1
3
S
r
(r
1
,r
2
) +
1
3
S
e
(r
1
,r
2
) =
1
3
× 0.62+
1
3
×
2
3
+
1
3
×
4
10
= 0.56
4 POLICY CLUSTERING
Given a set S of objects, clustering S consisting in
regrouping the objects of S into several subsets of
S : C
1
,C
2
,..., where each C
i
contains objects that are
similar, based on a given similarity metric. There ex-
ist many clustering algorithms, such as the K-nearest
neigbors (KNN) algorithm (Bhatia et al., 2010). We
propose a clustering algorithm that regroups the rules
of the policy into clusters, based on the similarity
score presented in Section 3. Let us say that two rules
are similar if their similarity score is greater than a
given threshold. Based on previous works (Lin et al.,
2013; Guo, 2014), the considered threshold is 0.8.
Our clustering method has been developed so that for
SECRYPT 2017 - 14th International Conference on Security and Cryptography
550

every obtained cluster C, every rule in C is similar to
at least another rule of C. That is: for every rule r
i
in
a cluster C, there exists another rule r
j
in C such that
S
rule
(r
i
,r
j
) ≥ threshold.
The inputs of our clustering algorithm are:
- a policy P which is a set of rules
- a list S
1
, S
2
, ... , where each S
k
is the set of simi-
larity scores depending on the rule r
k
.
The algorithm proceeds iteratively as follows:
For k = 1,2, ... : by analyzing S
k
, we construct a
new cluster consisting of r
k
and all the other rules that
are similar to r
k
.
Then, when all S
k
are treated (by the above loop),
we remove every cluster that is included or equal to
another cluster.
Note that the clusters resulting from our algorithm
satisfy the following two properties:
- Each cluster contains at least one rule;
- Every rule is contained in one or more clusters.
Example: We consider a 4-rule policy whose simi-
larity scores are shown in Table 1. The sets S
k
are
therefore:
- S
1
= {S
rule
(r
1
,r
2
),S
rule
(r
1
,r
3
),S
rule
(r
1
,r
4
)}
- S
2
= {S
rule
(r
1
,r
2
),S
rule
(r
2
,r
3
),S
rule
(r
2
,r
4
)}
- S
3
= {S
rule
(r
1
,r
3
),S
rule
(r
2
,r
3
),S
rule
(r
3
,r
4
)}
- S
4
= {S
rule
(r
1
,r
4
),S
rule
(r
2
,r
4
),S
rule
(r
3
,r
4
)}
Iteration 1: We obtain the cluster C
1
= {r
1
,r
3
},
because S
rule
(r
1
,r
3
) is the only score in S
1
which is ≥
0.8. Iteration 2: We obtain the cluster C
2
= {r
2
,r
4
},
because S
rule
(r
2
,r
4
) is the only score in S
2
which is ≥
0.8. Iteration 3: We obtain the cluster C
3
= {r
1
,r
3
},
because S
rule
(r1, r3) is the only score in S
3
which is ≥
0.8. Iteration 4: We obtain the cluster C
4
= {r
2
,r
4
},
because S
rule
(r
2
,r
4
) is the only score in S
4
which is
≥ 0.8. Then, the clusters C
3
and C
4
are removed, be-
cause they are identical to the clusters C
1
and C
2
, re-
spectively. The constructed clusters are : C
1
= {r
1
,r
3
}
and C
2
= {r
2
,r
4
}.
Table 1: Example of computed similarity scores for 4 rules.
Pairs of rules similarity score
(r
1
,r
2
) 0.041
(r
1
,r
3
) 0.811
(r
1
,r
4
) 0.111
(r
2
,r
3
) 0.166
(r
2
,r
4
) 0.866
(r
3
,r
4
) 0.5
5 ANOMALY DETECTION
Let an access request denotes a subject that tries to
have a specific access to a resource under certain con-
ditions (Bonatti et al., 2002; De Capitani Di Vimercati
et al., 2007). Formally, an access request R is speci-
fied by an action (e.g., read, write ...) and a value
for each attribute att; such value is denoted v
att
(R).
We say that R matches a rule r
i
(we may also say: r
i
matches R), if for every attribute att of r
i
, we have
v
att
(R) ∈ V
att
(r
i
). An anomaly in a policy P is defined
as the existence of access request matching several
rules of P.
Statistically, the probability of anomalies between
rules increases with the similarity between rules. In
Section 4, the threshold of 0.8 has been used to de-
compose a policy into clusters, because it is estimated
that most anomalies are between rules whose similar-
ity score is ≥ 0.8 (Bhatia et al., 2010). For this rea-
son, we propose to detect anomalies within the same
cluster. We propose to classify anomalies in two cat-
egories as presented in (Khoumsi et al., 2016):
- An Anomaly without Conflict: occurs when
there exists an access request that matches two (or
more) rules that have the same action decision (i.e.
X
act
, where X is Permit or Deny to indicate that
the action act is permitted or denied).
- An Anomaly with Conflict: occurs when there
exists an access request that matches two (or
more) rules that have different action decisions.
We consider : conflict of modalities and conflict of
fraction permissions. The first type occurs when
two rules matched by the same access request
have contradictory action decisions. The second
type occurs when two rules matched by the same
access request have ambiguous action decisions
(e.g., Permit
read
and Permit
read,write
represent a
conflict of fraction permissions).
Regarding anomalies detection, we consider the
following notions:
- r
i
is included in r
j
(noted r
i
⊆ r
j
), if they have the
same attributes, and for every of their attributes
att, we have: V
att
(r
i
) ⊆ V
att
(r
j
).
- r
i
is said compatible with r
j
(noted r
i
∩ r
j
6=
/
0),
if they have the same attributes, and for every of
their attributes att, we have: V
att
(r
i
)∩V
att
(r
j
) 6=
/
0.
Note that if r
i
and r
j
are identical (which implies
S
rule
(r
i
,r
j
) = 1), then they are compatible and each
one is included in the other one.
Clustering-based Approach for Anomaly Detection in XACML Policies
551
5.1 Detecting Redundancy Anomaly
Consider two rules r
i
and r
j
in a cluster C. We say
that r
i
is redundant to r
j
, if removing r
i
from C (while
keeping r
j
in C) does not change the global effect of
the rules of C. Redundancies may affect the perfor-
mance of a policy as well as slow down the system,
because verifying if an access request respects a pol-
icy depends on the size (i.e. the number of rules) of
the policy. For this reason, we consider redundancy
as anomaly.
Proposition 1. Consider a cluster C
k
and two of its
rules r
i
and r
j
whose action decisions are X
a
and Y
b
,
respectively. r
i
is redundant to r
j
iff :
1. r
i
is included in r
j
, and
2. X
a
= Y
b
.
Example: Consider the following rules r
1
and r
2
:
- r
1
: Permit
read
(Position ∈ {Doctor, Nurse};
File
Type∈ {Source, Documentation}; time ∈
[8:00, 18:00])
- r
2
: Permit
read
(Position ∈ {Nurse}; File
Type∈
{Documentation}; time ∈ [8:00, 18:00])
Since r
2
is included in r
1
and the two rules have
the same action decision (Permit
read
), then r
2
is re-
dundant to r
1
.
5.2 Detecting Anomalies with Conflict
Consider a policy P, two rules r
i
and r
j
are conflicting
if they can match the same profile and have different
access decisions.
Proposition 2. Given a cluster C
k
and two of its rules
r
i
and r
j
whose action decisions are X
a
and Y
b
, re-
spectively. r
i
and r
j
are conflicting iff :
1. r
i
and r
j
are compatible, and
2. X
a
6= Y
b
.
In this paper, we consider two types of anoma-
lies with conflict: conflict of fraction permissions and
conflict of modalities.
5.2.1 Conflict of Fraction Permissions
We have a conflict of fraction permissions when in
Point 2 of Proposition 2, we have a 6= b and X = Y, i.e.
the two rules permit or deny different actions. Con-
sider the following example:
- r
1
: Permit
read
(Position ∈ {Doctor, Nurse};
File
Type∈ {Source, Documentation}; time ∈
[8:00, 18:00])
- r
2
: Permit
read/write
(Position ∈ {Nurse};
File
Type∈ {Documentation}; time ∈ [10:00,
18:00])
There is a conflict of fraction permissions between
r
1
and r
2
, because r
1
and r
2
are compatible and permit
different actions (read for r
1
, and read/write for r
2
).
5.2.2 Conflict of Modalities
We have a conflict of modalities when in Point 2 of
Proposition 2, we have a = b and X 6= Y, i.e. an action
is permitted by a rule and forbidden by the other rule.
Consider the following example:
- r
1
: Deny
read
(Position ∈ {Doctor, Nurse};
File
Type∈ {Source, Documentation}; time ∈
[8:00, 18:00])
- r
2
: Permit
read
(Position ∈ {Nurse}; File
Type∈
{Documentation}; time ∈ [10:00, 16:00])
There is a conflict of modality between r
1
and r
2
,
because r
1
and r
2
are compatible while action read is
permitted by r
2
and forbidden by r
1
.
6 EVALUATION RESULTS
In order to evaluate the efficiency and effectiveness
of the suggested approach, we consider synthetic
datasets. The synthetic dataset is composed of the
combination of eight subject attributes, four resource
attributes and two environment attributes. The at-
tribute values are inspired from real world (i.e., med-
ical environment).
We have implemented our approach in Java and
the experiments were performed on an Intel Core i5
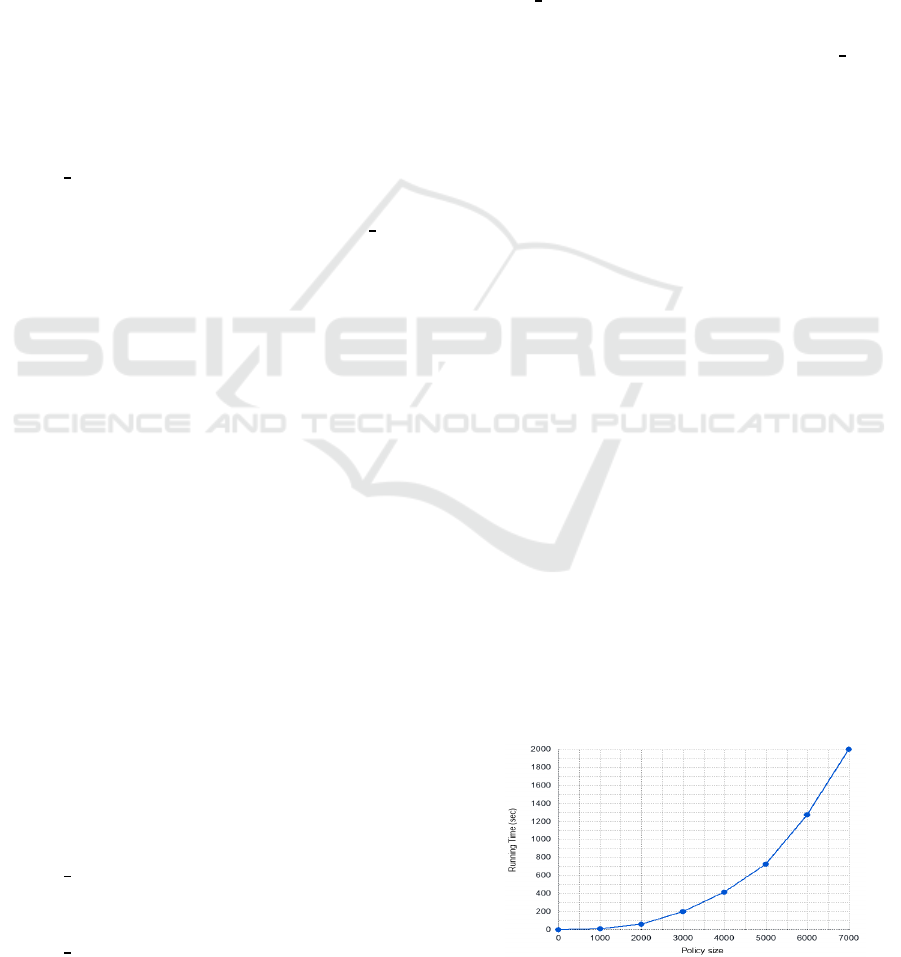
CPU 2.7 GHz with 8 GB RAM. Figure 1 shows the
running time needed to process the XACML policy
entirely and output the results. The running time in-
creases with the number of policy rules in a quadratic
way. This is due to the number of the combina-
tions being computed for policy rules during the four
steps, especially in the similarity computation where
we consider brute force technique to compute the sim-
ilarity scores. Regarding ABAC-PC algorithm com-
plexity, the computational time is in O(n
2
) where n is
the number of rules.
Figure 1: Running time.
SECRYPT 2017 - 14th International Conference on Security and Cryptography
552
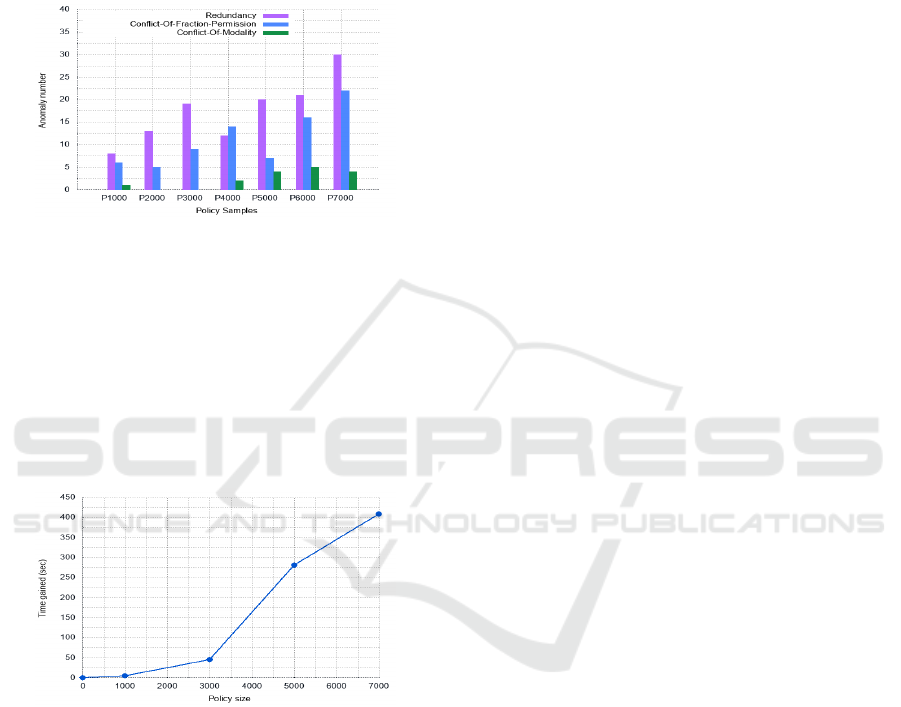
Figure 2 shows the number of anomalies detected
regarding each type (i.e. redundancy anomaly, con-
flict of fraction permissions and conflict of modal-
ities). The number of anomalies increases with the
policy size. The obtained results can be explained by
the fact that with the increase of the police size, the
probability of having anomalies increases.
Figure 2: The number of detected anomalies.
Figure 3 shows the time gained from using clus-
tering step as a function of policy size. To compute
this metric, we run our approach without clustering.
This means that the detection step is run once on the
whole set of rules. Then, we compute the difference
in running time between the two versions of our ap-
proach (i.e., with/without clustering). As shown in
this figure, the time gained increases with the number
of policy rules.
Figure 3: Time gained from clustering step.
7 CONCLUSIONS
An XACML policy for distributed applications might
be aggregated from multiple stakeholders and could
be managed by several administrators. Therefore, it
may contain several anomalies, which may lead to
high implementation complexity. In this direction,
we have proposed an approach which is based on
decomposing the policy into clusters before search-
ing anomalies within each cluster. The evaluation re-
sults demonstrate the efficiency of the proposed ap-
proach to detect different types of anomalies. Direc-
tions for future work include the detection of other
type of anomalies, such as inconsistency and similar-
ity anomalies between two aggregated policies. As
well as the resolution of the detected anomalies.
REFERENCES
Anderson, A., Nadalin, A., Parducci, B., Engovatov, D.,
Lockhart, H., Kudo, M., Humenn, P., Godik, S., An-
derson, S., Crocker, S., et al. (2003). extensible access
control markup language (xacml) version 1.0. OASIS.
Benkaouz, Y., Erradi, M., and Freisleben, B. (2016). Work
in progress: K-nearest neighbors techniques for abac
policies clustering. In Proceedings of the 2016 ACM
International Workshop on Attribute Based Access
Control, pages 72–75. ACM.
Bhatia, N. et al. (2010). Survey of nearest neighbor tech-
niques. arXiv preprint arXiv:1007.0085.
Bonatti, P., De Capitani di Vimercati, S., and Samarati, P.
(2002). An algebra for composing access control poli-
cies. ACM Transactions on Information and System
Security (TISSEC), 5(1):1–35.
De Capitani Di Vimercati, S., Foresti, S., Samarati, P., and
Jajodia, S. (2007). Access control policies and lan-
guages. International Journal of Computational Sci-
ence and Engineering, 3(2):94–102.
Guo, S. (2014). Analysis and evaluation of similarity met-
rics in collaborative filtering recommender system.
Master’s thesis, lapland university of applied sciences.
Hu, H., Ahn, G.-J., and Kulkarni, K. (2013). Discovery and
resolution of anomalies in web access control policies.
Dependable and Secure Computing, IEEE Transac-
tions on, 10(6):341–354.
Khoumsi, A., Erradi, M., and Krombi, W. (2016). A formal
basis for the design and analysis of firewall security
policies. Journal of King Saud University-Computer
and Information Sciences.
Lin, D., Rao, P., Ferrini, R., Bertino, E., and Lobo, J.
(2013). A similarity measure for comparing xacml
policies. IEEE Transactions on Knowledge and Data
Engineering, 25(9):1946–1959.
Moffett, J. D. and Sloman, M. S. (1994). Policy conflict
analysis in distributed system management. Journal of
Organizational Computing and Electronic Commerce,
4(1):1–22.
Mourad, A., Tout, H., Talhi, C., Otrok, H., and Yahyaoui,
H. (2015). From model-driven specification to design-
level set-based analysis of xacml policies. Computers
& Electrical Engineering.
Stepien, B. and Felty, A. (2016). Using expert systems
to statically detect” dynamic” conflicts in xacml. In
Availability, Reliability and Security (ARES), 2016
11th International Conference on, pages 127–136.
IEEE.
Yuan, E. and Tong, J. (2005). Attributed based access con-
trol (abac) for web services. In IEEE International
Conference on Web Services (ICWS’05), page 569.
Clustering-based Approach for Anomaly Detection in XACML Policies
553
