
Multi-level De-anonymisation for Initially Anonymous Discussion
Systems in a Self-regulated Learning Environment
Tenshi Hara
1
, Anne Schumacher
2,∗
, Karina Hara
3
, Iris Braun
1
, Felix Kapp
4
and Alexander Schill
1
1
Chair of Computer Networks, School of Engineering Sciences, Technische Universit
¨
at Dresden, Dresden, Germany
2
Technische Universit
¨
at Dresden, Dresden, Germany
3
Blue Pumpkin LLC, Kailua-Kona, HI, U.S.A.
4
Chair of Learning and Instruction, School of Science, Technische Universit
¨
at Dresden, Dresden, Germany
Keywords:
Self-regulated Learning, Discussion Systems, Forums, Anonymity, De-anonymisation.
Abstract:
Discussion systems are a valuable asset in attaining self-regulated learning. Beyond the limitations of on-
campus classroom settings, they enable internal feedback, peer feedback as well as external feedback. A
motivating factor to continued and frequent utilisation of such systems is anonymity. However, anonymity is
a double-edged sword. On one side, it provides strong incentives to use discussion systems, on the other side
it invites destructive behaviour such as trolling. Furthermore, strong students are discouraged from contin-
ued utilisation if they cannot attribute their contribution to themselves. We propose an initially anonymous
discussion system, which enables retroactive de-anonymisation on multiple levels, namely with respect to the
identity degree as well as the attribution dimension.
1 INTRODUCTION
Modern teaching methods such as Peer Instruction
(Mazur, 1999; Crouch and Mazur, 2001; Mazur,
2017) aim at helping students achieve self-regulated
learning (Zimmerman et al., 2000). Commonly, such
methods rely on peer interactions amongst the stu-
dents. For example, Peer Instruction includes an ex-
plicit Peer Discussion phase. In general, these peer in-
teractions provide students with valuable feedback on
their knowledge and learning progress. They can ask
questions, provide answers, discuss their understand-
ing of knowledge, or simply receive feedback from
their teachers. Of course, these aspects involve self
reflection (internal feedback), comprehension of oth-
ers’ concepts (peer feedback) as well as corrections
(external feedback).
Peer interactions can be transferred outside of the
classroom into online media such as forums and dis-
cussion systems. One example for that is our graph-
ical discussion system Graphicuss which we presen-
ted at last year’s CSEdu (Chen, 2016; Hara et al.,
2017). This allows students to continue learning
activities outside of the classroom. However, interac-
tions are accessible to all peers online, rather than the
∗
Graduate student
few directly involved in the classroom. Therefore, an-
onymity is an imperative motivating factor for utilisa-
tion of online discussion systems (summarised in e.g.,
(Hara, 2016)), allowing students to make mistakes or
ask ‘stupid questions’ without fear of exposure due to
the entirely documented and available history of inter-
actions. Nevertheless, at some point in time, motiva-
tion may be further fostered by attribution rather than
anonymity. In general, anonymous systems do not
have a de-anonymisation concept allowing students
to attribute their contributions to themselves retroact-
ively. For example, if students provide a very good
contribution to a discussion which is well received by
their peers, the students may want to attribute the con-
tribution by attaching their name to it. This in return
allows their peers to actively seek the students in the
classroom (i.e., offline).
In this position paper, we present a multi-level de-
anonymisation concept for discussion systems. Stu-
dents’ contributions are initially entirely anonym-
ous. Peers are unable to correlate two contribu-
tions of the same student to each other. In a first
de-anonymisation step, pseudonyms are attached to
a student’s contribution. Such pseudonyms can be
either the same system-wide, or attached to a discus-
sion thread. In a final step, the pseudonyms can be
302
Hara, T., Schumacher, A., Hara, K., Braun, I., Kapp, F. and Schill, A.
Multi-level De-anonymisation for Initially Anonymous Discussion Systems in a Self-regulated Learning Environment.
DOI: 10.5220/0006760403020307
In Proceedings of the 10th International Conference on Computer Supported Education (CSEDU 2018), pages 302-307
ISBN: 978-989-758-291-2
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
replaced by the student’s actual identity; e.g., their
name. These three levels of identity obfuscation are
met by three degrees of attribution, namely individual
contributions, threads, and topics (sets of threads).
2 RELATED WORK
It is imperative for students to receive feedback on
their understanding of knowledge as well as their
learning progress. This can be achieved through
formative assessment in means of internal feedback,
peer feedback and external feedback (Peters et al.,
2017). This in return helps students achieve self-
regulation (Winne and Hadwin, 1998; Zimmerman
et al., 2000). The process of internal feedback can
be fostered by asking students to reflect on their own
understanding of knowledge. Explicitly asking them
to write a summary or explain a topic to their peers
forces them to evaluate and order their own know-
ledge. Also, asking questions in an understandable
fashion requires some preceding internal feedback.
Similarly, it should be easy for lecturers to provide
students with external feedback
1
. Therefore, we ar-
gue that the challenge lies in providing a system with
attributes of useful, feasible and suitable peer feed-
back. The interesting question then is, how can peer
feedback be fostered and perceived as a motivating
experience for feedback providers and receivers?
2.1 Self-regulated Learning
Self-regulation unfolds over four more or less flexibly
sequenced phases of recursive cognition (Winne and
Hadwin, 1998), namely task perception, planning, en-
acting, and adaptation. During task perception, stu-
dents gather information about the task and classify it
based on their motivational state, their self-efficacy, as
well as their environment, especially in means of peer
performance. Next, during planning, students define
goals to be achieved and rewards to be obtained by
fulfilling the task. For that, they plan how to achieve
the goals and determine a reward importance. The
strategy can vary depending on explicit behaviours,
cognitive engagement, and motivation. After surpass-
ing a threshold volition, students enact their plan. Fi-
nally, students evaluate their performance and adapt
their strategy for increased (or at least maintained)
success in future repetitions of the same or similar
tasks. The success in achieving the defined goals as
1
Providing external feedback individually and at the
best moment is a topic of its own and shall not be discussed
in this position paper.
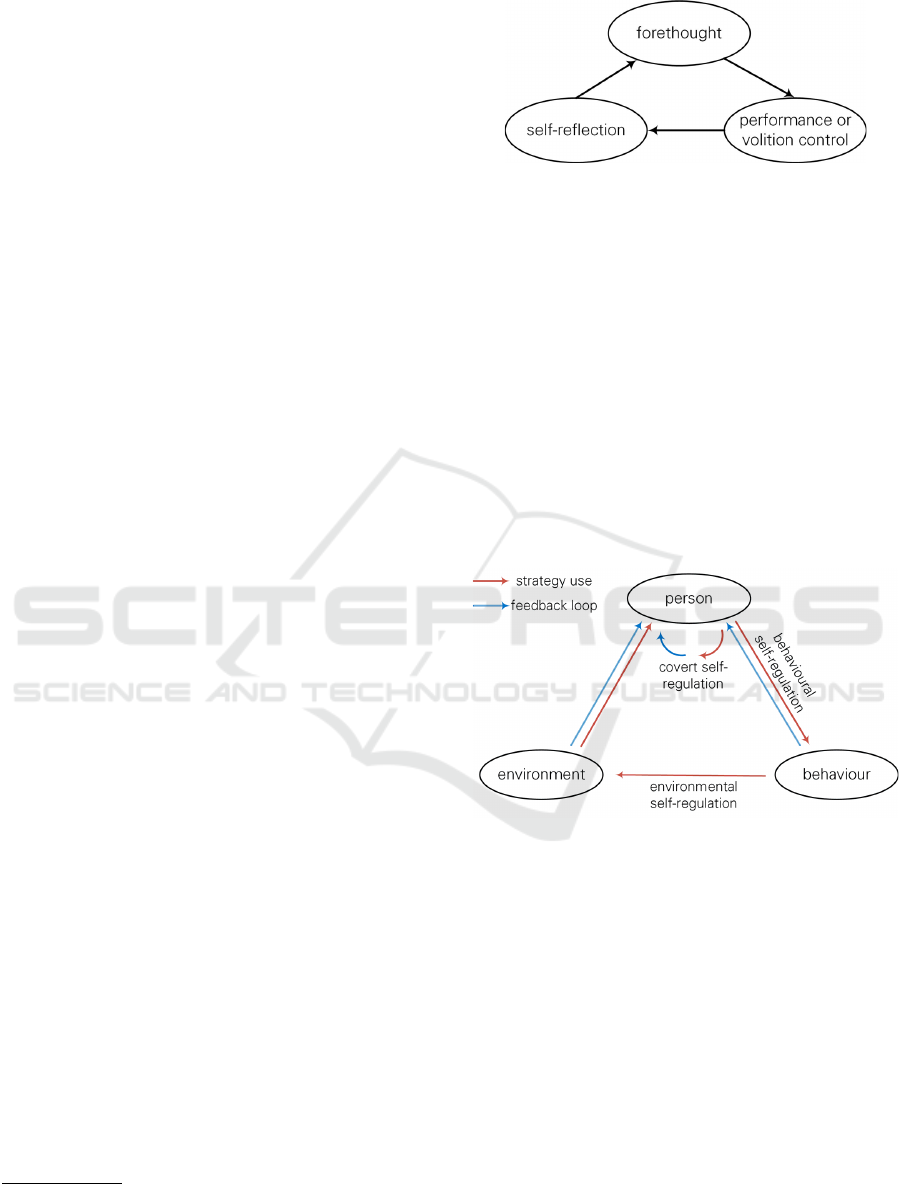
Figure 1: Cyclic transition states of self-regulation.
well as the perceived value of the obtained rewards
gravely influence the adaptation process.
The four phases defined by (Winne and Hadwin,
1998) are inter-connected by three transition states as
defined by (Zimmerman et al., 2000), namely fore-
thought, performance or volition control, and self-
reflection (cf. Figure 1). The latter two are influ-
enced by the learner’s peers, especially by assessing
the own performance in comparison to the peers’ per-
formance as well as by reflecting on own mistakes
in comparison to the peers’ mistakes and (potentially
better/worse) solutions. Thus, supporting students in
these two transition states immediately enhances their
success in the corresponding self-regulation phases
connected through these states.
Figure 2: Triadic self-regulation.
Of course, peers’ influences on a learner’s percep-
tion of their own learning progress are also import-
ant from a triadic self-regulation perspective (Zim-
merman et al., 2000) (cf. Figure 2). From the three
aspects of triadic self-regulation, behaviour and en-
vironment are directly influenced by a learner’s peers,
especially when taking the before-mentioned trans-
itions states into consideration. Simply, peer influ-
ences have a strong impact self-regulation strategies:
interactions with peers are an imperative aspect in the
process of achieving self-regulation. Therefore, peer
interactions are a highly important part of modern
learning and teaching concepts such as Peer Instruc-
tion (Mazur, 1999; Mazur, 2017).
Multi-level De-anonymisation for Initially Anonymous Discussion Systems in a Self-regulated Learning Environment
303

2.2 Discussion Systems and Forums
Forum systems such as auditorium (Beier et al., 2014)
or our Graphicuss (Chen, 2016; Hara et al., 2017)
provide users with the possibility to discuss topics in
a linear, chronologically ordered fashion. An under-
lying tree structure consisting of the posts (partially)
ordered within threads, which again are organised by
topics or categories
2
allows for intuitive cognition of
posts belonging together as a discussion, as well as
related or unrelated post, threads, and topics. Within
a thread, users can discuss the main subject as well
as answers other users have posted before. This tree
structure can have a large number of levels if the cre-
ation of sub-threads within threads is allowed.
Forums commonly require users to register an
identity/pseudonym under which their posts are dis-
tinguished from others’. Participation of anonymous
users is generally not desired, as this invites spam and
various forms of vandalism, such as trolling.
Forum systems that support anonymous particip-
ation attribute all anonymous posts to one indistin-
guishable pseudonym, e.g. ‘anonymous’, making
it difficult to follow individual contributors’ argu-
mentations. Attribution to distinguishable anonym-
ous users, as available in other collaboration systems
like Google Docs
3
is is not implemented in any forum
system to the authors’ knowledge.
Verified identities, as implemented in popular so-
cial media platforms like Facebook
4
and Twitter
5
, are
uncommon. Nevertheless, verified identities, or to the
least verified pseudonyms, are imperative for a well-
structured and believable discussion culture. Access
control must be established in a privacy-respecting
fashion (P
¨
otzsch and Borcea-Pfitzmann, 2009) while
enabling effective deflection of spam and vandalism,
or sh%t-storms
6
(Rost et al., 2016). At the same time,
users’ contributions must remain trustworthy and be-
lievable, especially allowing other users to assess the
value and truthfulness of a contribution (Kartal et al.,
2011). Accordingly, product recension platforms of-
ten only allow negative feedback if the users attach
their name to their recension.
2
In general, a post is a single contribution of a user.
Multiple posts, e.g. a question and corresponding answers,
are organised in threads. Finally, multiple threads can be at-
tached to a topic spanning multiple discussions on a broader
subject.
3
https://docs.google.com/ – They use animals; e.g., ‘an-
onymous elephant’ or ‘anonymous cat’.
4
https://facebook.com/
5
https://twitter.com/
6
The four-letter word was censored at an offended re-
viewer’s request. We wish to emphasise that it is a common,
properly cited term in this context.
2.3 Anonymity
As discussed in the previous sections, self-assessment
and peer influences are an important factor for stu-
dents’ learning success. Therefore, these are amongst
the most important influence factors identified in the
Visible Learning meta-studies (Hattie, 2009; Hattie,
2013). Nevertheless, exposure should also be con-
sidered, especially if it leads to students being forced
to concede to a lack of knowledge or wrong under-
standing thereof. We identified anonymity as a strong
motivating factor to free students of fears of exposure
(Hara, 2016).
Giving students the option to contribute anonym-
ously can be desirable to lower users’ inhibitions to
contribute. However, in common systems anonym-
ity is generally only provided in regard to what other
users are presented.
The problem with anonymity is its double-edged
nature. On on hand, it provides strong incentives for
students to contribute without fear of exposure, on
the other hand it inhibits strong students from con-
tributing, as they cannot attribute their contributions
to themselves. The strong motivation for attribution
is ‘showing off’: at some point, students want their
peers to know who has authored well-received contri-
butions. Prestige is a strong motivation after all.
Another problem with anonymity is system sus-
ceptibility to trolling and other malicious activities.
Under the cover of anonymity, users loose restraint to
negatively or destructively contribute to the system.
Therefore, systems commonly store identifying meta-
data (e.g., IP address, e-mail address) in order to ret-
roactively reprimand users or revoke system access.
This in return leads to an underlying fear of exposure
as users must trust that the system does not divulge
their identifying information unnecessarily.
Regardless the problems, anonymity remains a
strong motivating factor for system utilisation. Al-
lowing students to remove the constraints of anonym-
ity retro-actively can address strong students and mo-
tivate them to contribute even more. Trust must be
established between the system and the students, only
providing (desirably strong) anonymity amongst the
students themselves.
Similar considerations apply to the relations
between students and teaching staff. Knowing that
lecturers are unable to identify students within a sys-
tem can foster ‘stupid questions’
7
, which students
would normally not dare to ask. In reverse, lectur-
ers might want to be able to identify weaker students
7
Questions students perceive to be stupid. However,
this is a common misconception: any question helps
strengthen a correct understanding of knowledge.
CSEDU 2018 - 10th International Conference on Computer Supported Education
304

in order to provide targeted help. Based on our re-
search, we strongly believe that a well designed sys-
tem should allow lecturers to provide such support
even in an anonymous setting (Hara, 2016).
3 DE-ANONYMISATION
Based on the existing ideas in combination with the
goals of self-regulation, we propose a multi-level
de-anonymisation approach. Initially, students shall
be totally anonymous, with only system administrat-
ors or law enforcement being able to identify stu-
dents. Hence, even teachers are initially unaware
of their students’ identities as system users. Then,
it shall allow students to ask questions, provide an-
swers, and discuss topics in three identity degrees,
namely totally anonymous (ID-0), pseudonymised
(ID-1), and identity-attributed (ID-2; also identi-
fied), as well as three attribution dimensions, namely
per post (Dim-0), per thread (Dim-1), and per topic
(Dim-2). The combination of identity degrees and at-
tribution dimensions can be described by an attribu-
tion tuple (Dim, ID); e.g., (0, 1) indicates that a stu-
dent contributes a single post under their pseudonym.
Both sets are ordered descending: ID-2 > ID-1 >
ID-0 and Dim-2 > Dim-1 > Dim-0. Furthermore, at-
tribution tuples shall hold
∀i, j ∈
{
1, 2, 3
}
:
Dim
1
ID
i
>
Dim
2
ID
j
iff Dim
1
> Dim
2
and
0
ID
1
>
0
ID
2
iff ID
1
≥ ID
2
.
A higher attribution dimension always overwrites
a lower, independent of the value of the identity de-
gree. However, this condition shall only hold for
future contribution in the discussion system. Even
though the identity degree is set in the higher attri-
bution dimension and applies to all lower attribution
dimensions, a student can always change settings for
individual posts/threads in lower attribution dimen-
sions. For example, if a thread is set to ID-1, all fu-
ture contributions of the same student in that thread
also default to ID-1. Nevertheless, the student can
choose ID-0 or ID-2 for individual posts. Therefore,
the above defined order only serves the purpose of
simplifying interactions: if a student wants to be pre-
dominantly anonymous in a thread, they can set the at-
tribution tuple (1, 0) rather than having to choose the
identity degree each time they post within the thread.
In order to have a feasible identity degree sys-
tem, the discussion system has to ensure that pseud-
onyms and identities can only be used by the author-
Table 1: Available identity degrees based on verification.
available
default ID
allowed
upgrades
verfication
{
0
}
/
0 none
{
0, 1
} {
1
}
E-Mail
{
0, 1, 2
} {
1, 2
}
IMS
ised users. We suggest allowing anonymous registra-
tions be limited to ID-0 independent of the attribution
dimension. That way, malicious users cannot incarn-
ate pseudonyms or identities. Pseudonyms should be
enabled for verified user accounts; e.g., after e-mail
verification. Then, ID-0 and ID-1 are available to
the users in all attribution dimensions. Users should
be able to choose their own pseudonyms or get ran-
dom pseudonyms assigned. In both cases, pseud-
onyms used shall only be re-usable for the users who
have first used the pseudonym. Last, ID-2 should be
made available only to users with verified identities.
For this, a trusted identity provider or identity man-
agement system (IMS) should be used. For example,
a university could provide a student’s identity based
on the matriculation records. Secure access to these
sensitive data could be realised through an authentic-
ation service like Shibboleth
8
, which is summarised
in Table 1.
As mentioned above, students should not be lim-
ited to a single pseudonym. They might want to use
a pseudonym in a discussion they are sure to con-
tribute positively, but use a different pseudonym in
a discussion they are unsure and which might reflect
negatively on them. However motivating, such flex-
ibility may open the discussion system to ‘adverse
whitewashing’. Students can simply choose a new
pseudonym as soon as they feel a pseudonym has
be attributed to too many negatively perceived con-
tributions. Additionally, ‘trolls’ could constantly use
new pseudonyms for their trolling activities. Hence,
a suitable compromise must be found to allow flex-
ible utilisation of pseudonyms on one hand, and troll
control on the other. Likewise, pseudonym manage-
ment efforts must be taken into consideration. An-
swering questions / quoting posts (in full as well as
partially) requires further considerations with respect
to the ID of the quoted post; e.g., which ID is the
answer supposed to have, or what happens to quoted
content as soon as the ID of the original posting has
been altered? Describing all considerations would
break the confines of this position paper; thus, we
wish to allude the reader to Table 2 for further de-
tails. Beyond that scope, further functions of discus-
8
https://www.shibboleth.net/
Multi-level De-anonymisation for Initially Anonymous Discussion Systems in a Self-regulated Learning Environment
305

Figure 3: Overview of lectures and their pre-set ID levels.
sion systems must also observe the boundaries of at-
tribution. For example, a personal message (PM) sys-
tem introduces relations between students. If a stu-
dent follows another student’s contributions based on
a PM-established relation of ID-1, a posting under
ID-2 should not be attributed to the given relation-
ship as the ID-2 posting would break the pseudo-
anonymity of the ID-1 PM-established relationship
(in simple term: as soon as a real identity is attached
to an initially pseudonymous post, the other end of the
relationship would be able to attribute all previously
pseudonymised posts to the student).
Independent of the challenges described above,
students require a simple visualisation of their degree
of anonymity. Simply showing the attribution tuple is
not a suitable solution. Based on user interviews and
usability tests, we recommend an icon-based visual-
isation with ‘anonymID smilies’ (cf. Figure 4), or
something similar with clearly distinguishable visu-
alisation for the ID levels.
The anonymID smilies work best in combination
with easily comprehensible colour schemes. In our
prototype we stayed true to the basic colour scheme of
our system (blue) and used shades of the basic high-
light colour (by saturation: 75% for ID-2, 50% for
ID-1, 25% for ID-0). That way, students are able
to immediately identify the pre-set identity degree for
lectures
9
(cf. Figure 3) as well as threads (cf. Fig-
ure 5). The colour coding did not work as well for
individual posts. Instead, textual representations in a
designated area should be used; in Figure 5 this can be
seen in the upper right corner of each post (‘Anonym’:
an anonymous student; ‘Pseudo1’: a pseudonymised
student; ‘Max Mustermann’: student’s verified iden-
tity (name)).
(a) ID-0 (b) ID-1 (c) ID-2
Figure 4: Suggestion for visualisation of the ID levels.
9
Topics correspond to lectures in our prototype.
Figure 5: Within a lecture view: different pre-set ID levels
for threads (left) and individual postings (right).
Of course, this can be attributed the fact that our
prototype only used shades of blue rather than differ-
ent colours. Without the other colours in visible prox-
imity, it is very hard for users to intuitively distinguish
the colours.
A justifiable question is how beneficial retroact-
ive de-anonymisation actually can be. Students may
decide to de-anonymise a contribution, but this may
remain totally unnoticed by their peers if the topic
or thread as been closed or concluded its line of dis-
cussion. However, students do tend to revisit certain
discussions in preparation of their exams. This is es-
pecially true for questions on understanding complex
course material. In order to quickly revisit how a cer-
tain understanding developed, these old discussions
are very helpful. This in return brings the argument
back full-circle to the beginning: students can attrib-
ute their contributions and become valuable learning
contacts for their peers. This in return is very mo-
tivating, and it fosters an even stronger understanding
of and confidence in their knowledge as the students
might change into the teacher role when explaining
concepts, et cetera to their peers.
4 CONCLUSION
Discussion systems are a valuable asset in attaining
self-regulation. They enable internal feedback, peer
feedback as well as external feedback beyond the
scope of on-campus lectures, namely into the online
media. A motivating factor to continued and frequent
utilisation of such systems is anonymity. In this po-
sition paper we have discussed the pros and cons of
anonymity and why it is important to enable retro-
active de-anonymisation. We presented a multi-level
de-anonymisation concept based on three identity de-
grees as well as three attribution dimensions, and an
attribution tuple (Dim, ID) to describe anonymity set-
tings within discussion systems. For some aspects we
CSEDU 2018 - 10th International Conference on Computer Supported Education
306

Table 2: Comparison of pseudonym counts.
pseudonym
availability
pseudonyms
utilised
advantages disadvantages
exactly one 1
• prevents ‘adverse whitewashing’
• easy pseudonym management
• only allows ID-0→ID-1 and
ID-0→ID-2, but not
ID-0→ID-1→ID-2
• cannot retroactively modify ID
(ID-19ID-2)
limited max
• flexibly usable • possibility of ‘adverse whitewashing’
• no best-practice for suitable max value
1/Topic
• no direct linking of pseudonyms to
topics
• good degree of ‘adverse
whitewashing’ prevention
• lack of Variability/flexibility
• no control of / influence over
pseudonyms
1/Thread
• prevents ‘adverse whitewashing’
within threads
• allows retroactive ID modification
(ID-1→ID-2 per thread)
• lack of variability/flexibility
unlimited ∞
• flexibility
• own arbitrament
• allows retroactive ID modification
(ID-1→ID-2 per post)
• simplifies ‘adverse whitewashing’
• challenging pseudonym management
outlined the utility and limitations of the so designed
anonymity management.
In the future, we want to test our de-anonymi-
sation concept outside the constraints of a simple
forum prototype: we plan to implement it into the
next version of Graphicussin order to investigate the
limitations of our concept; we are sure that different
classroom and off-campus online settings require dif-
ferent attribution settings, or to the very least some
nifty fine-tuning. Further, we want to investigate the
influence of pseudonyms externally provided through
an identity management system such as Shibboleth
8
.
Simple metrics should be ascertainable through
targeted interviews with students and teachers (e.g.,
System Usability Scale, NASA Task Load Index).
Using the prototype in actual lectures should enable
us to determine a relation between the students’ will-
ingness to de-anonymise, and their actual utilisation
of the de-anonymisation feature. This should also
help identify potential trade-offs.
REFERENCES
Beier, L., Braun, I., and Hara, T. (2014). auditorium - Frage,
Diskutiere und Teile Dein Wissen! In GeNeMe 2014
- Gemeinschaften in Neuen Medien. GeNeMe.
Chen, K. (2016). Graphical Discussion System. Master’s
thesis, Technische Universit
¨
at Dresden.
Crouch, C. H. and Mazur, E. (2001). Peer instruction: Ten
years of experience and results. American journal of
physics, 69(9):970–977.
Hara, T. (2016). Analyses on tech-enhanced and anonymous
Peer Discussion as well as anonymous Control Facil-
ities for tech-enhanced Learning. PhD thesis, Tech-
nische Universit
¨
at Dresden. https://katalogbeta.slub-
dresden.de/id/0017472650/.
Hara, T., Chen, K., Braun, I., and Kapp, F. (2017). Graph-
icuss - Proposing Graphical Discussion System. In
Proceedings of the 9th International Conference on
Computer Supported Education (CSEdu 2017).
Hattie, J. (2009). Visible learning: A synthesis of meta-
analyses in education.
Hattie, J. (2013). Visible learning: A synthesis of over 800
meta-analyses relating to achievement. Routledge.
Kartal, A., Doerfel, S., Roßnagel, A., and Stumme,
G. (2011). Privatsph
¨
aren-und Datenschutz in
Community-Plattformen: Gestaltung von Online-
Bewertungsportalen. Informatik, 412:1–15.
Mazur, E. (1999). Peer instruction: A users manual.
Mazur, E. (2017). Peer instruction. In Peer Instruction,
pages 9–19. Springer.
Peters, O., K
¨
orndle, H., and Narciss, S. (2017). Effects of
a formative assessment script on how vocational stu-
dents generate formative feedback to a peers or their
own performance. European Journal of Psychology of
Education.
P
¨
otzsch, S. and Borcea-Pfitzmann, K. (2009). Privacy-
Respecting Access Control in Collaborative Work-
spaces. In PrimeLife, pages 102–111. Springer.
Rost, K., Stahel, L., and Frey, B. S. (2016). Digital social
norm enforcement: Online firestorms in social media.
PloS one, 11(6):e0155923.
Winne, P. H. and Hadwin, A. F. (1998). Studying as self-
regulated learning. Metacognition in educational the-
ory and practice, 93:27–30.
Zimmerman, B. J., Boekarts, M., Pintrich, P., and Zeidner,
M. (2000). Attaining self-regulation: a social cognit-
ive perspective. Handbook of self-regulation, 13.
All URLs within this paper were last successfully accessed
on 19 November 2017.
Parts of this position paper are based on Anne Schumacher’s
Master’s thesis.
Multi-level De-anonymisation for Initially Anonymous Discussion Systems in a Self-regulated Learning Environment
307
