
Novel IoT Applications Enabled by TCNet: Trellis Coded Network
Diogo F. Lima Filho
1
and José Roberto Amazonas
2,3
1
Universidade Paulista – UNIP, Rua Dr. Bacelar, 1212, Vila Clementino, São Paulo, Brazil
2
Escola Politécnica da Universidade de São Paulo, Av. Prof. Luciano Gualberto – Tr. 3, 158, São Paulo, Brazil
3
Technical University of Catalonia – UPC, Department of Computer Architecture, Barcelona, Spain
Keywords: Internet of Things (IoT), Wireless Sensor Networks, Finite State Machine, Convolutional Codes, Trellis
Coded Network, Routing Algorithm.
Abstract: This work presents new results in routing in Wireless Sensor Networks, an important Infrastructure for the
Internet of Things architecture, using the new concept of Trellis Coded Network - TCNet. The TCNet is
based on the concept of convolutional codes and trellis decoder, that allow routing of data collected by
randomly distributed micro sensors in ad hoc networks scenarios. This model uses Mealy Machines or low
complexity Finite State Machines network nodes (“XOR” gates and shift registers), eliminating the use of
any routing tables enabling the implementation of important IoT applications as Sensor Network
Virtualization and in scenarios where clusters of nodes allow covering large areas of interest where the
sensors are distributed. The application of TCNet algorithm concepts in cases as VSNs and clustering is
facilitated due to the flexibility of TCNet to implement route management, becoming a tool to be adopted
by Sensor Infrastructure Providers aiming to deploy, for example, QoS-aware end-to-end services.
1 INTRODUCTION
Routing remains a challenge in today’s networks. It
is recognized that the major contributing factors are
the routing tables growth, constraints in the routers
technology and the limitations of today’s Internet
addressing architecture. Routing tables are populated
in routers and indicate the best next hop(s) for each
reachable destination along a route.
Considering that Wireless Sensor Networks
(WSNs) are an important infrastructure for the
Internet of Things (IoT) architecture, the interest in
using sensor networks in the same universe as IP
networks, although the sensor nodes have limited
hardware resources, this work explores an
innovative approach based on the concept of a
“Trellis Coded Network”- (TCNet), where the
foundations were introduced in previous works: (i)
“Implementation of QoS-aware routing protocols in
WSNs using the TCNet” (Lima and Amazonas
2012), where the network nodes are associated to the
states of a low complexity Finite State Machine
(FSM) and the links of a route are coded as the
transition of states of a convolutional code. The
routing discovery corresponds to finding the best
path in the convolutional code’s trellis; (ii) “A
Trellis Coded Networks-based approach to solve the
hidden and exposed nodes problems in WSN” (Lima
and Amazonas 2014), where it is explained how
TCNet innovates the decision making process of the
node itself, without the need for signaling messages
such as “Route Request”, “Route Reply” or the
“Request to Send (RTS)” and “Clear to Send (CTS)
to solve the hidden node problem that is known to
degrade the throughput of ad hoc networks due to
collisions, and the exposed node problem that results
in poor performance by wasting transmission
opportunities.
1.1 Related Work
Although some classic protocols as the Border
Gateway Protocol (BGP) (Rekhter et al. 2006),
Routing Information Protocol (RIP) (Hendrick,
1988), Ad-hoc On Demand Vector Routing (AODV)
(Perkins et al. 2003) and Open Shortest Path First
OSPF (Moy, 1988) address the scalability of today's
Internet routing system to consider the large number
of nodes that may be present in Low-Power and
Lossy Networks (LLNs) and IoT applications (IETF
620
Filho, D. and Roberto Amazonas, J.
Novel IoT Applications Enabled by TCNet: Trellis Coded Network.
DOI: 10.5220/0006772406200626
In Proceedings of the 20th International Conference on Enterprise Information Systems (ICEIS 2018), pages 620-626
ISBN: 978-989-758-298-1
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
ROLL 2009), a Working Group formed by the
Internet Engineering Task Force (IETF) in charge of
standardization and specifying the IP protocol
recognizes that factors like the routing tables
growth, constraints in routers technology and the
limitations of today's Internet addressing architecture
have driven the efforts in researching new
paradigms. Attempts to adapt the routing protocols
of infra-structured networks to cases of ad-hoc
networks are often inconsistent to address issues as:
frequent changes in topologies, poor link quality,
restricted bandwidth, and constraints on energy
resources. On the other hand, the ad-hoc and sensor
networks tend to proliferate as the number of smart
objects-based services on the Internet increase.
After this brief Introduction, Section 2 describes
the concept of a “Trellis Coded Network”- (TCNet)
to define the routing datagrams generated by each of
the nodes network, Section 3 presents the
performance of TCNet in terms of latency and
energy efficiency, Section 4 describes the
application of TCNet to the Sensor Network
Virtualization (SNV) and clustering scenarios and
Section 5 summarizes the conclusions and future
works.
2 TRELLIS CODED NETWORKS
The concept of a “Trellis Coded Network”- (TCNet)
changes conventional routing paradigms to enable
the development of QoS-aware packet forwarding
protocols in WSNs that are used to determine the
routing datagrams generated by each of the
network’s nodes offering the following advantages
that are compatible with the limited resources of
WSNs:
Elimination of routing tables;
Reduced latency by eliminating the route
request (RREQ) and route reply (RReply)
signaling packets employed, for example,
in AODV;
Implicit self-recovery mechanism in case
of failure.
The model is based on finite automata (Hopcroft
and Ulman 1955) or FSMs defined by a ''cross''
function (k
n
/ out
n
) where a sequence of input
symbols {k
n
} generates a sequence of output codes
{out
n
} as shown in Figure 1. The k
n
(t) is the input
symbol received at time t and generates the output
code out
n
(t). It is also assumed that at time t, a
transition occurs at the FSM from state i to state j. In
TCNet each state represents a network node and the
transition state indicates that the frame information
must be sent from node i to node j.
It is then possible to generate a specific route
along a set of nodes, defined by a desired
optimization criterion (latency, packet loss,
throughput, cost), by shifting an input sequence {k
n
}
in the FSM of the route’s first node, and informed in
the frame as a TCNet label.
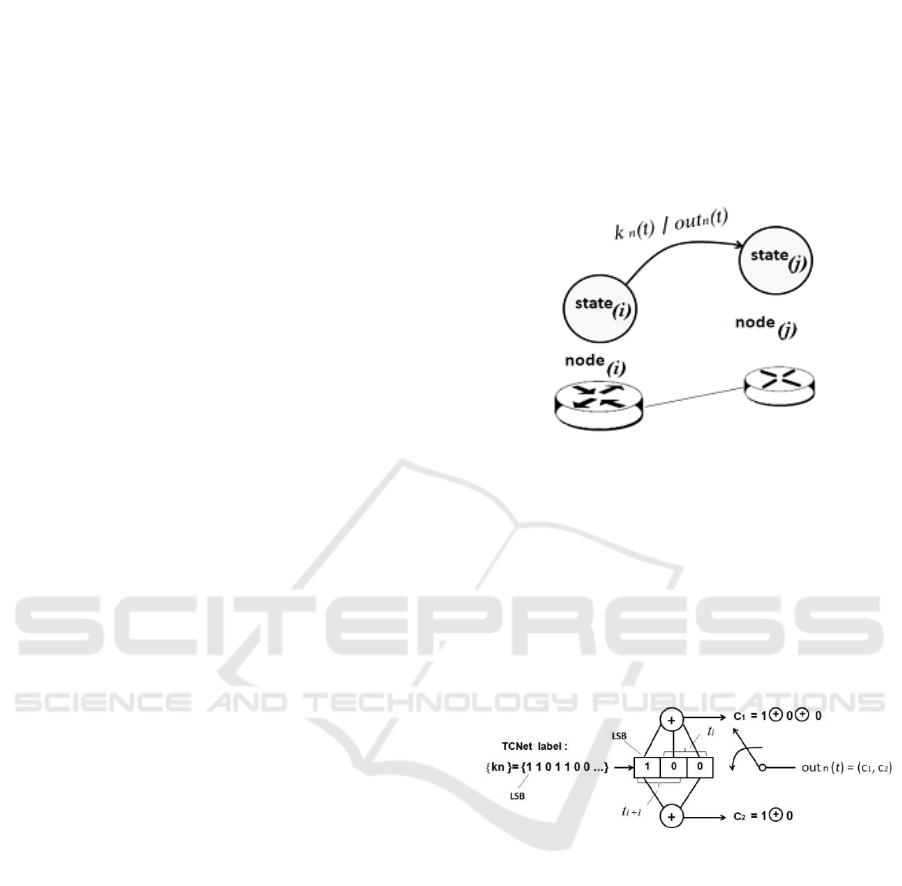
Figure 1: Network node modeled by a state of a FSM.
A network node modeled as a state allows the
application of FSM principles in order to exploit the
analogy between networks and state diagrams to
define paths between nodes. This enables each node
to have full knowledge of the network by
implementing a paths generator machine (MM) of
low complexity (''XOR'' gates and shift registers) as
shown in Figure 2.
Figure 2: Example of a MM with the input sequence {k
n
}
generating an output sequence out
n
(t) = (c
1
,c
2
).
The TCNet architecture employs the Viterbi
algorithm (Proakis and Salehi 2008) proposed in
1967 for decoding convolutional codes based on the
trellis diagram to decide a sequence of branches to
be followed. The Viterbi algorithm decodes a
received sequence by evaluating the distance
between the sequence of received source symbols
and the weight of the path in the trellis, and
identifies the best sequence of branches as the one
that provides the minimum distance. This is done by
associating each branch with a number called branch
metrics, and looking for the path whose metrics sum
is minimum. This can be accomplished by means of
evaluating the maximum-likelihood (Gratzer, 1978)
and to produce an estimate of the received sequence
Novel IoT Applications Enabled by TCNet: Trellis Coded Network
621
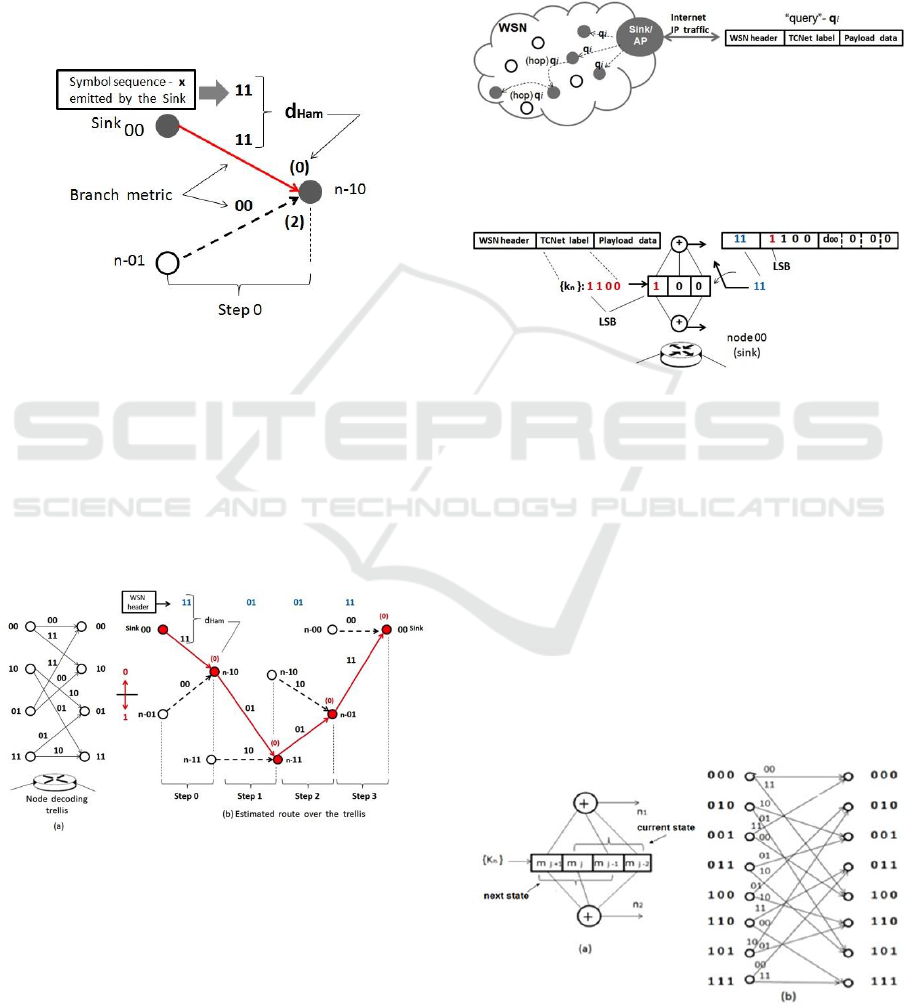
of symbols.
Figure 3 shows how node-10 recognizes the
origin of the emitted sequence to establish a survivor
branch (probable partial route). Using the concepts
of the Viterbi Algorithm, the node in question
analyses the adjacent branches and, using the
Hamming-distance between the emitted sequence
and the respective weights of the branches, decides
in favor of the branch with minimum Hamming-
distance (hard decision-operation), node-00 (Haykin
and Moher 2009).
Figure 3: Example of the hard decision taken by node-10
when the sink node-00 emits the sequence out
n
(t)=(c
1
, c
2
)
= (1,1).
Using the described procedure, Figure 4 shows
the route established by the TCNet label using {k
n
}
= {1 1 0 0} and the MM depicted in Figure 2. It can
be observed that every node in the network is visited
in the order {(10), (11), (01), (00)}, i.e., at the end,
the frame returns to the sink node with the
information collected from every other node.
Figure 4: (a) Decoding trellis; (b) Route established by the
input sequence {k
n
} = {1 1 0 0} and the MM depicted in
Figure 2.
3 TCNet SIMULATION
EVALUATION
Consider the WSN scenario illustrated in Figure 5,
where the sink node initiates a query through a set of
sensor nodes in a predetermined order and also has
the function of Access Point to IP infra-structured
networks. The sink node initializes a frame loading
the WSN header field with the information
generated by the MM generator (out
n
(t)=(c
1
, c
2
)) and
transfers the input sequence ({k
n
}) to the TCNet
label field as shown in the Figure 6.
Figure 5: Illustration of a WSN in which the sink node
queries a set of sensor nodes. On the right, the TCNet
frame is shown.
Figure 6: Initialization of the TCNet frame by the sink
node: the input sequence {k
n
} is loaded on the TCNet label
field and the output sequence out
n
(t)=(c
1
, c
2
) is loaded on
the WSN header field.
The simulation environment used in this work is
the OMNeT++ based on C ++ (Varga, 2011) and
object oriented. This simulator is widely accepted by
the research community for being open software, has
been applied to the modeling of network traffic, and
as reference for comparisons with other available
frameworks.
Tests were done with an 8-node network, where
the sink node sends a query with CBR traffic to
verify the reachability of the nodes. Figure 7 shows
the used node’s model, configured by a MM with
rate k / n = 1/2 and the respective trellis decoder.
Figure 7: (a) MM with k/n=1/2, resulting output words
(n1, n2); (b) Trellis diagram corresponding to the MM.
ICEIS 2018 - 20th International Conference on Enterprise Information Systems
622
3.1 The TCNet Performance Analysis
The same conditions of parameters and number of
nodes of the network were considered in order to
perform measurements of latency and energy
consumed by the network, as shown in Table 1. The
simulations considered a static scenario and the
worst-case where the performances for the most
physically remote and the most critical nodes of the
route were measured.
Table 1: Definition of the simulation scenario.
TCNet
AODV
Topology: 8 nodes
randomly positioned in an
area (1000m x 1000m) and
the sink node initiates
communication with the
other nodes by queries in
the network
Topology: 8 nodes randomly
positioned in an area (1000m
x 1000m) and the host (0) as
source node initiates
communication with the
other nodes of the network
using routes obtained
through flooding
Protocol: owner
Protocol: MAC 802.11g
Traffic: CBR with 512-byte
packets
Traffic: CBR with 512-byte
packets
Simulation time: 1 query
Simulation time: The 1st
flooding in the network, with
the negotiations (RREQ and
RRep) and the ACK
confirmation by the host (0)
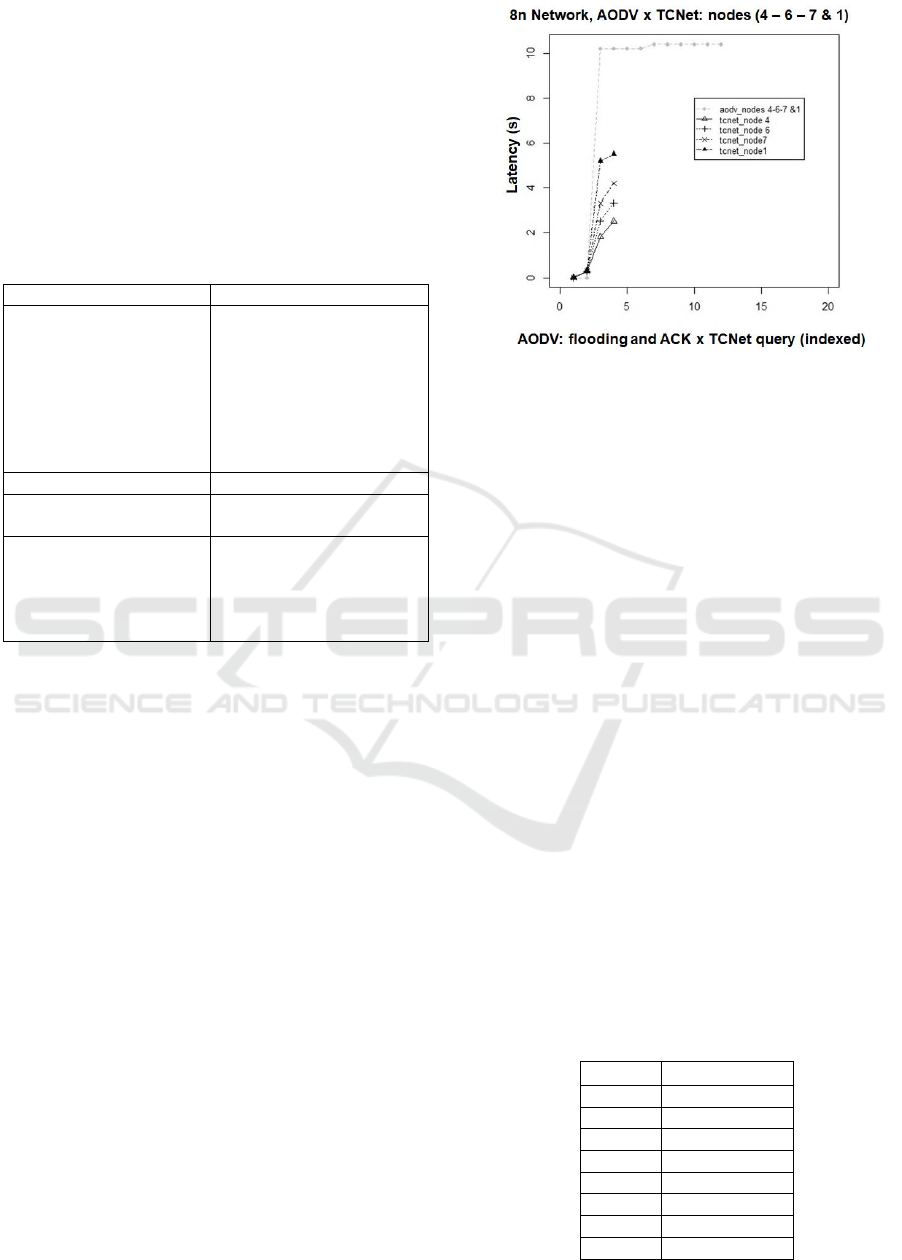
3.1.1 Latency Efficiency
Figure 8 shows the results of the latency of different
nodes of the TCNet network in comparison with a
similar route for the AODV case. The latency has
been evaluated for the TCNet queries of the most
critical nodes (4, 6, 7 and 1), and the same nodes for
AODV route establishment mechanism. It can be
observed:
In TCNet the latency increases as the
nodes correspond to the last positions of
the sequence k
n
(t), resulting a longer
processing time of the MM during the
decision making process of the target node.
In AODV there is an initial delay in
establishing the route and a temporary
stabilization of the latency.
In TCNet the worst-case latency
corresponds to 50% of the AODV latency,
in the considered scenario of an 8-node
network.
Figure 8: Comparison of TCNet and AODV latency for an
8-node network.
3.1.2 Energy Efficiency
The energy consumed in a WSN is a fundamental
parameter due to the limitations of the sources
(batteries) that are most often non-replaceable. This
work considered the energy consumed by the nodes
in the case of the TCNet algorithm, taking into
account the power distribution in the following
situations: Transmission (tx), Reception (rx),
Processing (proc) and Guard band (gb). The
following power values were adopted according to
the IEEE 802.11b standard:
Transmission Power (P
tx
): 2 mW;
Reception Power (P
rx
): 1 mW;
Processing Power (P
proc
): 1 mW;
Guard band (P
gb
): not considered
The energy consumed by the node is given by
(1), which corresponds to the contribution of the
node to the total consumption of the network.
ΣE
(n)
=E
tx
+E
rx
+E
proc
+E
gb
(1)
Table 2 shows the energy values for an 8 nodes
route considered in the simulation of TCNet
network.
Table 2: Individual contribution to the energy ΣE
(n)
consumed by the nodes of the TCNet network.
ΣE
(n)
Energy (Joule)
ΣE
(0)
4. 10
-4
J
ΣE
(4)
5. 10
-4
J
ΣE
(2)
6. 10
-4
J
ΣE
(5)
7. 10
-4
J
ΣE
(6)
8. 10
-4
J
ΣE
(7)
9. 10
-4
J
ΣE
(3)
10. 10
-4
J
ΣE
(1)
11. 10
-4
J
Novel IoT Applications Enabled by TCNet: Trellis Coded Network
623
The evaluation of the consumed energy by the
AODV considered the total time (ΣT
Lat
) taken by the
negotiations using the signaling (RREQ, RREP and
ACK) to establish the route to the destination node,
taking into account that in each AODV event energy
consumption occurs in the transmission, reception
and processing, respectively given by: E
tx
, E
rx
and
E
proc
. Thus the energy consumption for the AODV
network is given by (2):
ET
aodv
= ΣT
Lat
(P
tx
+P
rx
+P
proc
) (2)
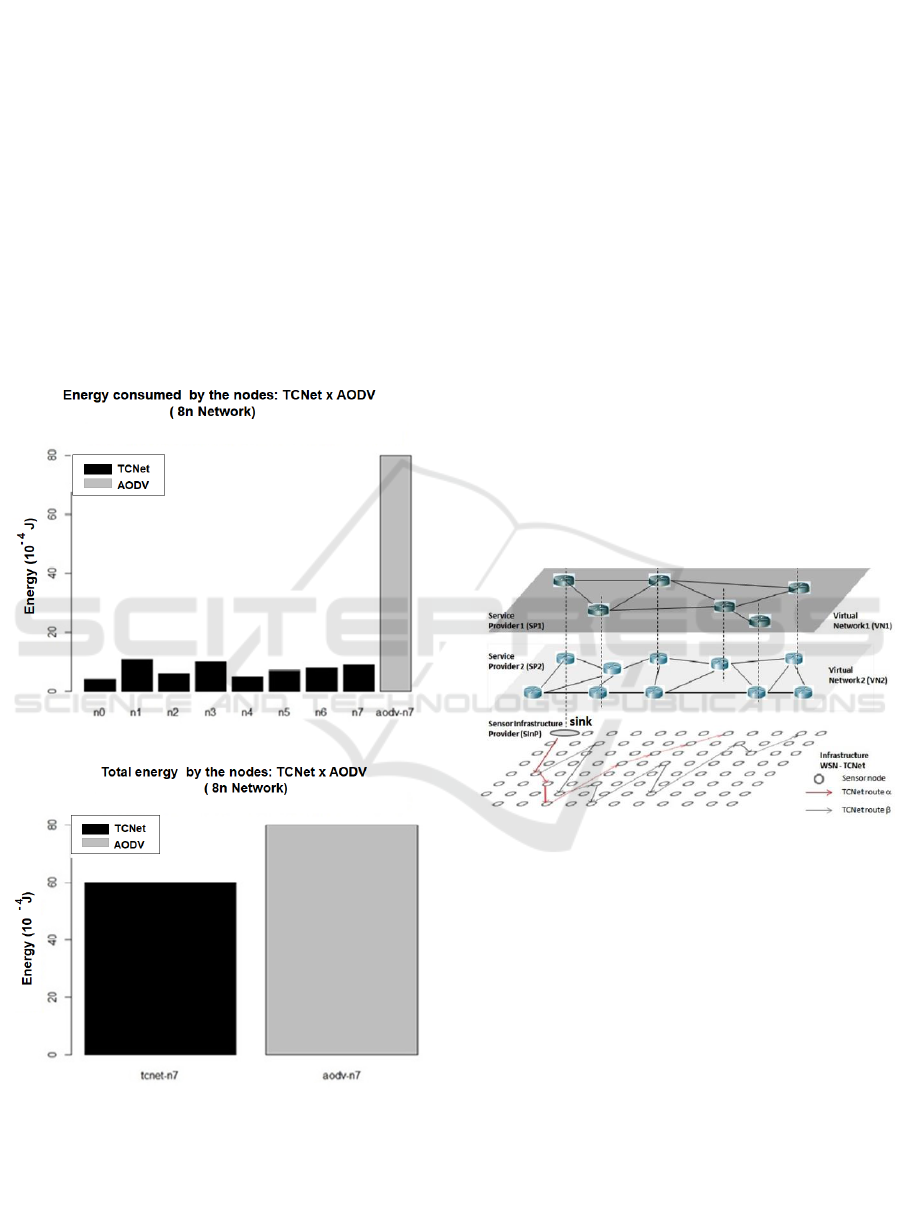
In the comparison of energy consumption,
TCNet x AODV, it was considered an 8-node
network and a route going through all nodes to reach
the most distant node, i.e., node 7. The results are
shown in Figures 9 (a) and (b).
(a)
(b)
Figure 9: (a) Energy distributed among TCNet nodes in
relation to the energy consumed by the AODV; (b)
Comparison between the total energy consumed by the
mechanisms of TCNet x AODV.
The total energy consumed by the TCNet
corresponds to 75% of the energy consumed by the
AODV.
4 APPLICATIONS OF THE TCNet
ALGORITHM
4.1 TCNet in Scenarios of Sensor
Networks Virtualization
The use of the TCNet algorithm concept in cases of
Sensor Network Virtualization (SNV) (Anderson e
al 2005), (Chowdhury, 2009) is made easier due to
the flexibility of the TCNet algorithm in route
management applications.
The TCNet concept becomes a tool that can be
adopted by distinct Sensor Infrastructure Providers
(SInPs) to establish simultaneous end-to-end
services over a same infrastructure as shown in
Figure 10.
Figure 10: WSN virtualization environment scenario
enabled by the TCNet concept where two distinct SInPs
establish two simultaneous end-to-end services over the
same infrastructure.
The scenario presented in Figures 11 (a), (b) and
(c) shows a SNV environment where the sink node
manages a heterogeneous set of sensors, over only
one infrastructure administered by a (SInP) and
controlled by a Gateway Router sensor located in the
sink. Figure 11 (c) shows an example of TCNet
managing different sets of sensors using queries
generated by different sequences corresponding to
specific quality requirements for each set of sensors.
In this example:
The humidity sensors are visited by the
sequence: k
n
{1 1 0 0 0 0 0 0};
ICEIS 2018 - 20th International Conference on Enterprise Information Systems
624
The temperature sensors are visited by the
sequence: k
n
{1 0 1 0 0 0 0 0};
The light sensors are visited by the
sequence: k
n
{1 1 1 1 0 0 0 0}.
Figure 11: (a) FSM with rate k/n = ½; (b) Trellis diagram
related to the FSM; (c) SInP sensors routing sets and
sequences related to the respective routes of the sensor
sets.
4.2 TCNet in Nodes Clusters Scenarios
Scenarios with large areas of interest to be covered
by WSNs suggest the subdivision of these areas into
clusters (Murthy and Manoj 2008). The use of
TCNet in these cases increases the alternative of
connections due to the self-configuration of the
trellis, making unnecessary the use of signaling
protocols, as would be the case in ad-hoc networks
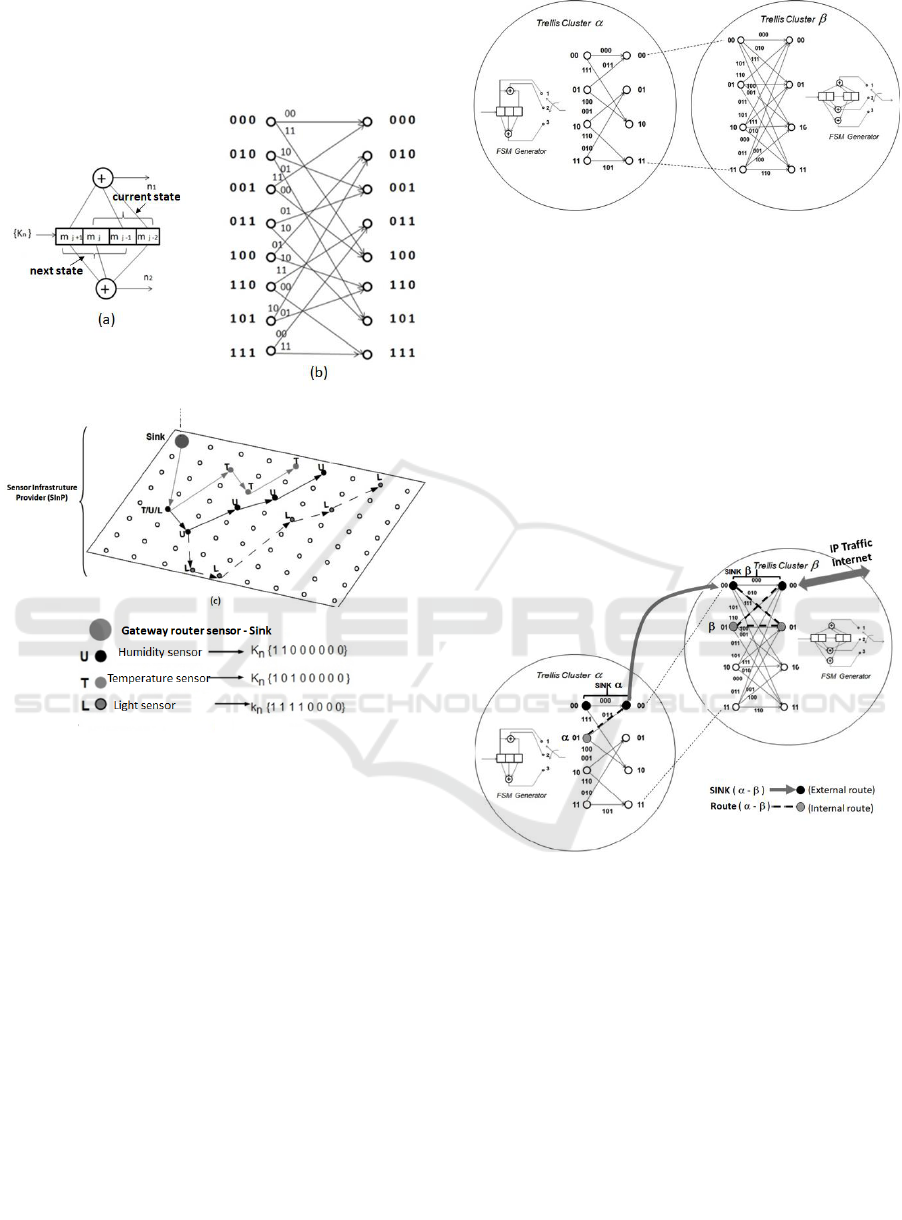
with AODV. Figure 12 shows a scenario with two
clusters based on trellis α and β and their respective
FSMs, allowing the construction of different routes.
Even occurring overlap of neighboring coverage
areas, the routes are independent and allows the
expansion in order to serve large areas of wireless
coverage.
Fig. 12. Clusters α and β have different settings of FSM
allowing the construction of independent routes.
The sink nodes, α-00 and β-00, allow the
interconnection of the clusters managing the routes
after the decision making process has been
performed by their respective trellis. The scenario
shown in the example of Figure 13 demonstrates
data collected from the nodes (α-01 and β-01),
belonging to the different clusters, and being
transmitted by their respective sinks to be
aggregated to the IP traffic by sink performing
its gateway function.
Figure 13: Clusters corresponding to the FSMs and
showing a concatenation of the routes between the two
clusters.
5 CONCLUSIONS
In this work we have made a review of the TCNet
concept that enables the implementation of packets
forwarding procedures in limited processing,
storage, communication and energy resources
networks, as WSNs, without using routing tables. In
addition a comparative performance evaluation
between the TCNet and the AODV was made
showing that the TCNet outperforms the AODV
both in terms of worst-case latency and total energy
Novel IoT Applications Enabled by TCNet: Trellis Coded Network
625

consumption. It has also been demonstrated the
potential of TCNet to be used to implement sensor
virtualization networks and the management of
sensors clusters. These applications are important in
the IoT domain and show TCNet as an enabling
technology to tackle scalability and to offer different
levels of QoS.
The TCNet concept is a powerful tool that can be
adopted to face very challenging problems. As
future work we will demonstrate how TCNet can be
used to implement robust networks with self-
recovery properties in the presence of failures.
ACKNOWLEDGEMENTS
This work has been partially supported by the
Spanish Ministry of Economy and Competitiveness
under contract TEC2017 – 90034 - C2 - 1 - R
(ALLIANCE project) that receives funding from
FEDER.
REFERENCES
Anderson,T., Peterson, L., Shenker, S. and Tuner, 2005.
“Overcoming the internet impasse through
virtualization. Computer”, v. 38, p. 34–41.
Chowdhury,K., Zaheer, F. and Boutada. 2009. An identity
management framework for network virtualization.
IEEE INFOCOM, p. 34–41.
Gratzer,G., 1978. “General Lattice Theory”, 1
st
ed.,
Academic Press, Inc.
Haykin, S and Moher, M, 2009. Communication Systems,
5th ed., John Wiley & Sons, Inc.
Hendrick,C. L, 1988. “Routing Information Protocol,”
RFC 1058, available for download from
http://www.rfc-editor.org/rfc/rfc1058.txt.
Hopcroft, J .E. and Ulman,J. D., 1955. “Introduction to
Automata Theory”, Languages and Computation, 1st
ed. Addison Wesley.
IETF ROLL Working Group, 2009. “IETF Roll Working
Group routing over low-power and lossy networks,”
homepage: http://www.ietf.org/dyn/wg/charter/roll-
charter.html.
Lima, D. F. and Amazonas, J. R, 2012. “TCNet: Trellis
Coded Network – Implementation of QoS – aware
routing protocols in WSNs ”, IEEE Latincom
106445, http:www.ieeelatincom.org/2012/.
Lima, D. F., Amazonas, J.R., “A Trellis Coded Networks-
based approach to solve the hidden and exposed nodes
problems in WSN,” SICOTEL2014 Seminário Taller
Latinoamericano de Instrumentación, Control y
Telecomunicaciones, April 2014,
http://www.gituq.edu.co/memorias%20sicotel2014.pdf
Moy, J., 1988. “ Open Shortest Path First,” RFC 2328,
available for download from http:www.rfc-
editor.org//rfc/rfc2328.txt.
Murthy, C. R., Manoj, B.S., 2008 “Ad Hoc Wireless
Networks – Architectures and Protocols”. 6
th. Ed.
[S.l]: Prentice Hall.
Perkins, C, Belding, E. and Das S., 2003. “Ad hoc on-
demand distance vector-(AODV) routing,” RFC 3561,
available for download from http:www.rfc-
editor.org/rfc/rfc3561.txt.
Proakis,J.G., Salehi, M., 2008. Digital Communications,
5th ed., Mc Graw Hill.
Rekhter, Y, Li T. and Hares S., 2006. “Border Gateway
Protocol”, RFC 3271, available for download from
http://www.rfceditor.org/rfc/rfc4271.txt.
Varga, A.: “OMNeT++, 2011. Discrete Event Simulation
System”,
http://www.omnetpp.org/doc/manual/usman.html.
ICEIS 2018 - 20th International Conference on Enterprise Information Systems
626
