
Signaling Game-based Approach to Improve
Security in Vehicular Networks
Abdelfettah Mabrouk, Abdellatif Kobbane and Mohammed EL Koutbi
MIS/SIME Lab, ENSIAS, Mohammed V University of Rabat, Rabat, Morocco
Keywords:
Vehicular Ad-hoc Networks, Signaling Game, Intrusion Detection Game.
Abstract:
Secure communication between vehicle nodes is significant in Vehicular Ad Hoc Networks (VANETs). To
guarantee public safety on the roads, vehicular networks need an appropriate security mechanism to protect
them from various malici ous attacks. In this paper we present an intrusion detection system available to
detect internal malicious nodes. When an accident appear on the road, the vehicles must have information
about this, but the existence of malici ous nodes, the information will be deleted fr om the network. Because
of this, we have adopted a mathematical model based on coalition and signaling game theory to design an
Intrusion Detection Game (IDG) modeling the interaction between malicious nodes and the Coalition Head
that equipped with Intrusion Detection System (CH-IDS) agent and seek its Bayesian Nash Equilibrium (BNE)
for the optimal detection st rategy.
1 INTRODUCTION
One special type of Mobile Ad hoc Networks (MA-
NETs) is the network among moving vehicles, which
is known as Vehicular Ad hoc Network (VANET). In
such network, vehicles communicate with each other
on the road or with equipment placed a long the ro-
ads. This type of network is currently receiving in-
creased attention from manufacturers and researchers
to impr ove safety on the roads or proposed aid to dri-
vers. VANETs differ MANETs in several ways: the
high node mobility, large-scale networks, geog raphi-
cal constraints of topology, highly dynamic topology,
the high stress of real-time, sporadic network con-
nectivity, slow deployment, unreliab le communica-
tion chann e ls, etc.
Securing co mmunications in wireless networks as
in wired networks requires the implementation of me-
chanisms to achieve a number of general security ob-
jectives. These objectives include:
1. Au thentication: allows network members to ens-
ure the prop e r identity of the m e mbers with whom
they comm unicate.
2. No n-repudiation: ensures that no issuer can not
deny being the source of a message. This ob-
jective is essential in electronic transactions and
all sensitive communications.
3. Confidentiality: guaran tees that only authorized
nodes that can access the data which transmitted
across the network. These data may concern the
application layer or the lower layers.
4. Integrity: ensures tha t the data exchange d are not
subject to voluntary or accidenta l alteration. So
it allows recipients to detect data tampering by
unauthorized entities and reject the pa ckages.
5. Availability: assure the entities authorized to
access network resources w ith an adequate qua-
lity of services.
The mobility of nodes ma kes the topology of VA-
NETs unstable. It is not easy for vehicle to know cor-
rectly the neighborhood. A ttac kers can thus forge a nd
disseminate false topology information to build roads
that pass thro ugh them and re alize attacks designed to
cause accidents or congestion of roads. By this me-
ans, an ad hoc non-secure routing p rotocol can be ea-
sily attacked. In addition, the mobility of attackers
can also make them more difficult to detect or loca te.
The nature of radio tra nsmission in the air, allowing a
hacker to listen passively all messages exchanged in
the emission z one, operating in “promiscuous mode”
and using software that allows capturing transmitted
packets (sniffer). The opponent will have access to
the network and can easily inter cept the data trans-
mitted, without the issuer has knowledge of the in-
trusion. The intruder, being potentially invisible, can
jam the radio channel to block the transmissions, in-
Mabrouk, A., Kobbane, A. and EL Koutbi, M.
Signaling Game-based Approach to Improve Security in Vehicular Networks.
DOI: 10.5220/0006784004950500
In Proceedings of the 4th International Conference on Vehicle Technology and Intelligent Transport Systems (VEHITS 2018), pages 495-500
ISBN: 978-989-758-293-6
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
495

jected massive packets to exhaust the resources of no-
des, save, ed it, and then re-transmit packets as if they
had been sent by a user legitimate. In ad- hoc net-
works there are some very sophisticated attacks, such
as the wormhole attack, can only be co mmitted by
compromised nodes and are hard to avoid. The use of
cryptography does not solve the problem of these no-
des compromised by a simple authentication because
these nodes are legitimate participants in the routing
process prior to being controlled by the attacker, so
we have to especially considering other solutions to
this problem like detection approaches.
An Intrusion Detection System (IDS) is a mecha-
nism tha t monito rs a network or systems to identify
abnormal or suspicious activities. It allows having in-
formation of failed or successful intrusions attempts.
Solutions are proposed by IDS for detecting internal
attacks. In order to minimize the im pact of malicious
vehicles, VANETs demand the IDS that is capable of
detecting attacks that have broken down the network.
In order to ensure their nor mal operation, VANETs
will be able to respond and isolate the intruders using
the IDS system. But bef ore the IDS c an be applied to
the VANETs practically, there is a primary issue that
has to be solved is how to select the profitable a nd
optimal detection strategy.
Game theory is a mathematical tool that studie s
situations of conflict and cooperation between se-
veral involved players. It has been widely applied in
the field of network security, preventing DoS attac k
(Mohi et a l., 2 009), and intrusion detectio n (Reddy,
2009). When a game in a system with incomplete
informa tion has many stages, the sig naling game in
which the posterior probability can be updated dyn-
amically is always considered to model the system.
Briefly, the signaling game is a dynamic gam e that
studies the situation of incomplete inf ormation and
involving two players: the first one (called th e Sen-
der) is infor med and the second one (called the Re-
ceiver) is not. The strategy set of the Sender consists
of actio ns c ontingen t on its type while the strategy set
of the Receiver consists of actions con tingent on the
Sender’s ac tions. Generally, in a signaling game, the
Sender has a private information while the Receiver
has a common inf ormation.
The intrusion detection in VANETs can be mo-
deled as a signaling game. Gener ally, a classic IDS
for guaranteeing VA NET security is compo sed of the
monitor and decision modules. The monitor module
aims to check the VANE T events while the decision
module aims to dec ide whether an event is normal or
not. This dyna mic situation is an interac tion between
malicious vehicle nodes and the IDS that is designed
and implemented to make VANETs secure. Sig na-
ling game is considered as a tool that is very profita-
ble to depict the characteristic of interactive situations
above. This approach can ac hieve the consequence
of selecting the Defend strategy optimally, which will
improve IDS’ real positive outcomes.
In this paper, our work focused on the signaling
game approach to study and ana lyze the interacti-
ons between a malicious vehicle node and a CH-
IDS agent in VAN ETs. We set up th e distributed-
centralized network model, in which each vehicle has
been equipped with an IDS agent. Not all IDS agents,
but only the IDS a gent in coalition head (CH-IDS)
will launch to to reduce channel contention and pac-
ket collisions.
The rest of this pa per is organized as follows.
Section II presents related work based on the IDS’
solutions in VANETs. The Intrusion Detection G a me
model, the stage Intrusion Detection Game, its pure
and mixed strategy BNE are introd uced in Section III.
Finally, Section IV concludes this work.
2 RELATED WORK
The security issues on VANETs have become one of
the primary concerns. Because of the high no des mo-
bility, the shared wireless medium and the absence
of centralized security services in VANET, it is in -
herently very vulnerable to attacks than wired net-
work. Cryptographic solutions, can be used as the
first line of defense for redu cing the possibilities of
attacks. However, these techniq ues have limited pre-
vention and a re not efficient in gen e ral, and th ey are
designed for a set of previously known attacks. They
are unlikely to avoid most recent malicious attacks.
For this reason, there is a need of another technique
to “detect and notify” these newer attacks, i.e . “intru-
sion detection”. This section aims to present a cur-
rent techniques of Intrusion Detection System (IDS)
aware wireless networks. In (Pattnaik a nd Pattana-
yak, 2014), the authors have focused on some cha-
racteristics of VANETs with possible types of attacks
based on intrusion detection. Also they have discus-
sed the most suitable IDS techn ique like watchdog
with their effect in VANETs. The applica tion of VA-
NETs is a rising technolo gy which can provide the fu-
ture directions of research in vehicular environment.
In (Sen, 2010), th e authors have proposed a cluster-
based semi-centralized ap proach that integrates a lo-
cal intrusion detection in a node or in a cluster. In
the network architecture pr oposed in th is work, the
nodes are grouped into clusters which are monitored
by cluster head while the inter-cluster communication
takes place thro ugh gateways by using mobile agents
VEHITS 2018 - 4th International Conference on Vehicle Technology and Intelligent Transport Systems
496

and every node maintains a database of known at-
tack for sig nature based detection. In (Ghosh et al. ,
2009), a security system is pr oposed to d etect the in-
truder that generates a false Post Cra sh Notification
alert. While the vehicle that nea r a crash ar ea issues
this notification later. In (Zhang and Lee, 2000), the
authors have proposed a cooperative distributed a rchi-
tecture where each node is responsible for detecting
signs of intrusion locally using IDS agent. While the
IDS agent is responsib le for data collection and de-
tection of malicious nodes, the neighbor s IDS agents
cooper a te with each other for global intrusion de-
tection. The model of the IDS agent is composed of
six module s, then one amo ng them called local data
collection module, is re sponsible to collect real-time
data. From data co llec te d, the local module detec tion
engine can decide if th e system is attacked or n ot, and
it c an initiate a response if an attack is detected w ith
specific evidence. T his response can be executed by
the lo c al module response (local alert) or by the g lo-
bal module response (global alert). When an abnor-
mality is detected with weak evidence, the coopera-
tive detection engine module is executed and requests
the coo peration of the other network nodes through
another secured communication module called secure
communication. In (Misra et al. , 2011), a stochas-
tic learning solution for intrusion detection (SLAID)
is proposed to identify the current attacks that occur
in VANET. In this re search, the attacker tha t disse-
minates false information is detec te d. According to
their experimental result, their system exhibits a high
detection rate. However, the main weakness of this
system lies in the fact that it generates a high over-
head since such heavy learning is embedded at every
vehicle. I n addition, this system is not applicable f or
real-time applications because the learning algorithm
requires a ce rtain time to model a normal pattern of
a target node. In (Ruj et al., 20 11), a data-centric de -
tection system (DCMD) is proposed to iden tify the
cyber-attacks that disseminate the false message alert,
e.g. Post-Crash Notification (PCN) alert. The au thors
proposed in this work a rule-based detection techni-
que to mo del the normal behavior of a target vehicle.
In case, whe n the action that a monitored veh icle per-
forms does not match this mode le d behavior, it will
be suspected as a node that disseminates a false alert
message. The simulation r esults show that their sy-
stem requires a low commun ic ation overhea d to de-
tect these cyber-attacks. However, the security perfor-
mance is not evaluated when such attack occurs, e.g.
detection rate. In (Sedjelmaci et al., 2016), an intru-
sion detection and prediction scheme has proposed to
detect and especially predict the future misbehavior of
a malicious vehicle. Th e attack prediction technique
proposed in this work is based on a game theory to
prevent the occurrence of malicious vehicles. Moreo-
ver, the detection scheme detects the most dangerous
attacks that target a VANET su ch as false alerts and
Sybil attacks.
Our work is distinguishable in terms of game type
and equilibrium. We model the interactions between
a vehicle and a CH-ID S agent with signa ling g a me.
In additio n, we seek the pure and mixed strategy
BNE for the stage game. These equilibriums deter-
mine when and how the CH-IDS agent takes a Defend
action. Finally, we get different equilibrium equations
as a result. Besides, our work is focused on the signa-
ling game to decide the optimal strategy of intrusion
detection in VANETs. In addition, we think that our
network model is profitable to make the IDS agent
reside in every vehicle, but only the IDS agent in co-
alition head (CH) performs intrusion detection based
on the signaling game.
3 SYSTEM MODEL
3.1 Network Model
The use of techniques such as cryptography does no t
offer the ab ility to detect new attacks or even defend
the network against internal nodes compromise. Ho-
wever, this type of system is used as fir st line of de-
fense while the secon d line of defense is occupied by
Intrusion Detec tion Systems commonly known by its
acronym IDS. An IDS operates in three p hases: a data
collection phase followed by an analysis phase and fi-
nally a response phase to prevent or minimize the im-
pact on the system. Generally, IDS is implanted in
certain special nodes c a lled monitors or m onitoring
nodes.
IDS can be classified as detection techniques as
follow:
• Fault d etection system: the system detects any
behavior that deviates the preset normal behavior
and triggers a response.
• Sign a ture-based system: the system has a data-
base of some attacks which are com pared with
the data co llected. An attack is detected if the
collected data coincide with an already registered
malicious behavior.
• System based on specifications: the system defi-
nes a set o f conditions that a protocol m ust meet.
An attack is detected in the case w here the pr o-
gram or protocol d oes no t me et the established re-
quirements of the operation.
Signaling Game-based Approach to Improve Security in Vehicular Networks
497
IDS can also be classified according to the archi-
tecture into three categories :
• Purely distributed : the IDS checks the abnormal
behavior of neigh boring nodes locally.
• Purely centralized : the IDS is installed in the base
station, which requires an additional rou ting pro-
tocol that collects data from nodes to analyze the
behavior of each node.
• Distributed-centr alized: the IDS is on ly installed
in special nodes that play two roles at the same
time, performing activities like normal nodes and
checking for intrusion detection.
Our network model adopt the distributed-
centralized approach in which IDS agents are
deployed in each vehicle instead of installing it in the
monitors’ vehicles only. At the same time, coalition
is used to organize our network into a connected
hierarchy. By using coalitional g ame, vehicles are
organized into co a litions. Each coalition has a
coordinator, called the Coalition Head (CH), and a
number of member vehicles. Coalition results form a
two-tier hierarchy in which CHs represent the highe r
tier while member vehicles represent the lower tier.
In this hiera rchy, member vehicles send their data to
the responsible CH while this latter aggregates the
data and sends them to the Base Station (BS).
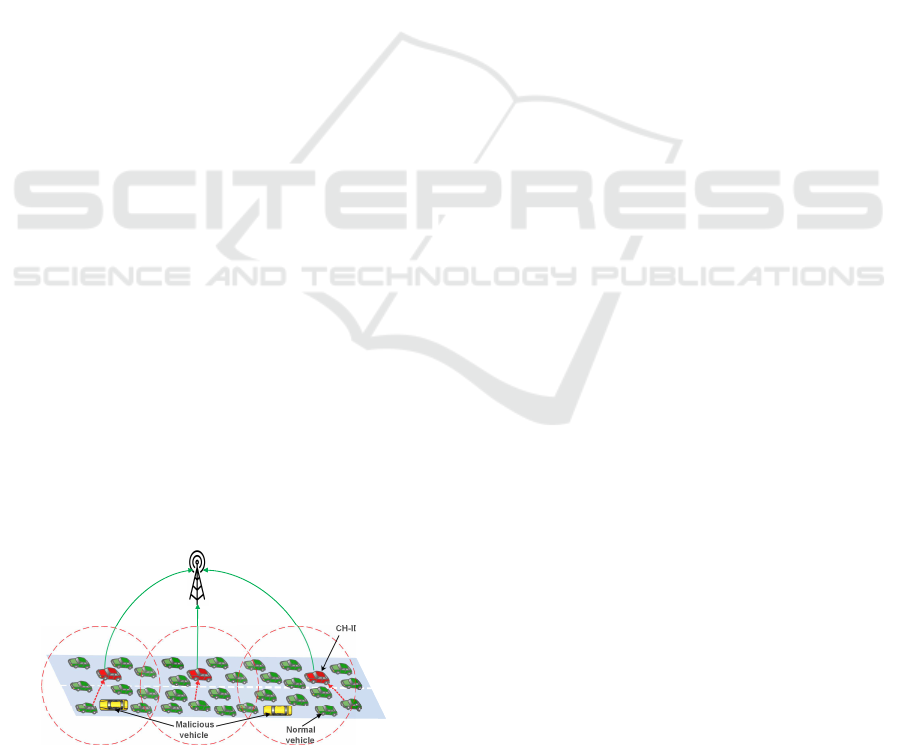
The vehicular network depicted in Fig. 1 consist
of N vehicles and M gateways. The vehicles can form
coalitions and the gateways can cooperate the trans-
mission of the vehicles when they are in the same coa-
lition. Let V = {1, 2...,N} and G = {1,2...,M} repre-
sent the set of gateways (coalition head), respectively.
We assume that :
1. All vehicles are equipped with GPS r e ceivers.
2. Eac h vehicle uses GPS capabilities to obtain its
current location and speed.
3. Vehicles’ coalition are formed dynamically acco r-
ding to our previous work presented in (Mabrouk
et al., 2015).
Base
station
Coalition 3Coalition 1 Coalition 2
CH-IDS
Figure 1: Network Model.
3.2 Stage Intrusion Detection Game
According to the characteristics of VANETs and IDS,
we choose some parameters for our Intrusion De-
tection Game. When the malicious vehicle makes
attacks to waste the VANETs reso urces, the net-
work will be disrupted and gradually crashed during
the communication between two vehicles which can
cause unexpected events. This process gives malici-
ous vehicle a payoff from their attacks; at the same
time, they pay a cost of consumption due to their at-
tacks. Therefore, for a malicious vehicle, we intro-
duce g
A
and c
A
to de note attack gain and cost respecti-
vely. A member vehicle is available to communicate
when it selects the action Cooperate, the packet th en
can be forwarded successfully. The normal member
vehicle will bene fit from this g ood network while the
malicious vehicle will also get payoff for its disguise.
In order to simplify, we supp ose that both the normal
and malicious nodes pa y the same cost as well as get
the same payoff. Therefore, for a member vehicle, we
introdu ce c
C
and g
C
to denote cooperation cost and
gain respectively. The CH-IDS agent ge ts the g ain
g
D
, when it selects the Defend strategy, fo r having
successfully d etected the malicious member vehicle
node. At the same time, it should pay for the cost, c
D
,
for energy consumption. Obviously, in the CH-IDS
agent like any gen eral IDS, there exist the detection
rate and the false alarm rate denoted by α and β r e-
spectively. The false alarm mean s that the CH-IDS
agent detec ts a member vehicle in normal communi-
cation in error, wh ic h will lead to a loss l
F
.
Hence, we consider in our stage Intrusion De-
tection Game (IDG) two players: mem ber vehicle as
a Sender S denoted by θ
S
, and CH-IDS agent as a Re-
ceiver R dented by θ
R
. Member vehicle S may be
Normal or Malicious, and its type is private infor-
mation to CH-IDS agent R. At each time slot, the
players choose their actions from their actions spa ces.
Because it wants to disguise itself, a malicious mem-
ber vehicle S may attack or cooperate. When member
vehicle S is Normal, it always cooperates. The CH-
IDS agent should not always b e the action Defend,
sometimes it should be Idle. That is, the ac tion of
CH-IDS may be Defend or Idle. Table 1 presents dif-
ferent utilities of the Intrusion Detection Game (IDG).
Except IDS’ Idle, all other actions in Table 1 in-
cur costs. For the action profile (Attack, Defend), i.e.
when a malicious vehicle chooses the Attack action
and the CH-IDS agentchooses the Defend action, the
utility o f θ
S
is th e gain of being not detected minus
the loss of being detected minus the attac k cost while
the utility of θ
R
is the gain of detecting successfully
minus the loss of not detecting minus the detection
VEHITS 2018 - 4th International Conference on Vehicle Technology and Intelligent Transport Systems
498
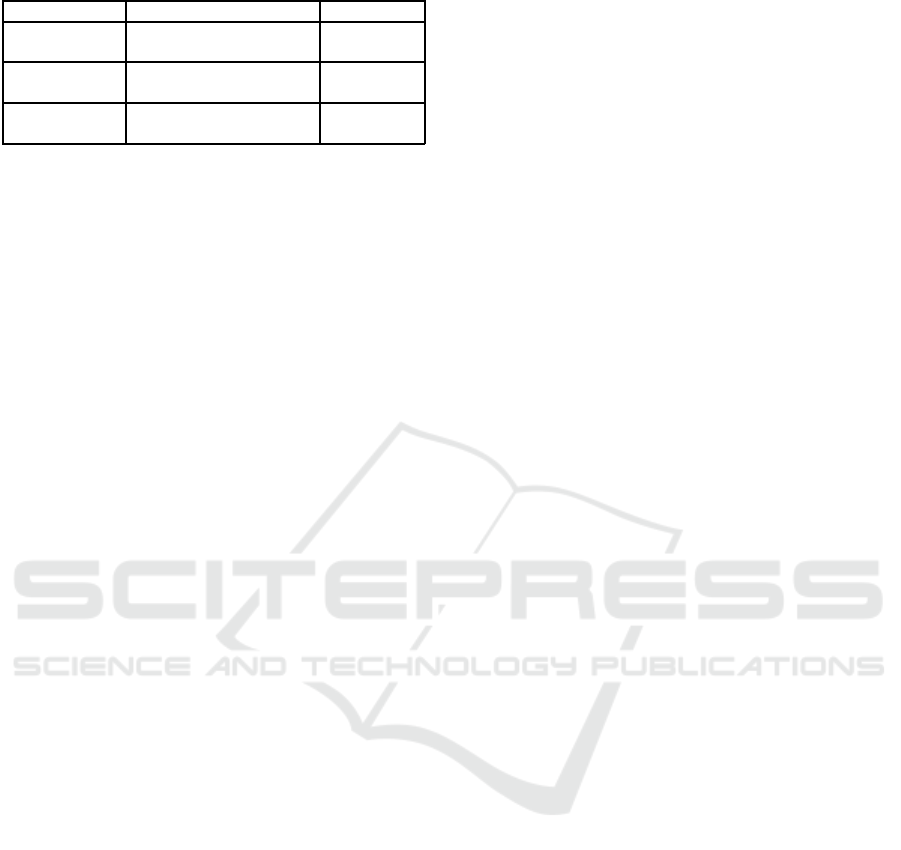
Table 1: Utilities of intrusion detection game.
CH-IDS (Defend) CH-IDS (Idle)
Malicious vehicle u
S
= (1 − α) · g
A
− α· g
D
− c
A
u
S
= g
A
− c
A
(Attack) u
R
= α· g
D
− (1 − α) · g
A
− c
D
u
R
= −g
A
Malicious vehicle u
S
= g
C
− c
C
u
S
= g
C
− c
C
(Cooperate) u
R
= −β· l
F
− c
D
u
R
= 0
Normal vehicle u
S
= g
C
− c
C
u
S
= g
C
− c
C
(Cooperate) u
R
= −β· l
F
− c
D
u
R
= 0
cost. In case o f the action profile (Attack, Idle), the
utility of θ
S
is th e attack gain minus the attack co st
while the utility of θ
R
is the loss of being attacked. For
the action pro file (Cooperate, Defend), the utility of
θ
S
is the coopera tion gain minus the coo peration cost
while the utility of θ
R
is the loss o f false alarm minus
the defend cost. Thus, the static Intrusion Detection
Game (IDG) is defin ed as follows.
The stage Intrusion Detection Game (IDG) is de-
fined by 5-tuple (N, Θ, A, P, U) wher e :
• N = {member vehicle S, CH-IDS agen t R} is a set
of 2 players;
• Θ = Θ
S
× Θ
R
, where Θ
S
is the set of type space
(malicious or normal) of the player S and Θ
R
is
the set of type space of the player R;
• A = A
S
× A
R
, where A
S
and A
R
are the set of acti-
ons available to th e player S (Attack o r Cooperate)
and the set of actions available to the player R
(Defend or Idle) respectively;
• P : Θ 7→[0,1] is a probability distribution over ty-
pes, P = (p, 1 − p) where p denotes the probabi-
lity that a vehicle can b e malicious node and 1 − p
denotes the probability that a vehicle can be nor-
mal node;
• U = (u
S
,u
R
), wher e u
S
is the utility function for
the player S and u
R
is the utility function for the
player R, the values of u
S
and u
R
are illustrated in
Table 1.
3.3 Equilibriums of Stage Intrusion
Detection Game
As a game based on signaling game theor y, the stage
Intrusion Detection Game can attain Bayesian Nash
equilibriu m (BNE), but the CH-IDS agent R does not
know the type of the member vehicle node S. A vir-
tual player (Nature) is introduced at th e beginning of
the signaling game, and will act firstly to decid e the
type of playe r S.
Theorem 1. In the stage Intrusion Detection Game,
there is a pure-strategy BNE when
p < (β· l
F
+ c
D
)/(α· g
D
+ α· g
A
+ β· l
F
) (1)
Proof. 1) When a vehicle node S selects the pure-
strategy (Attack, Cooperate) which means that vehicle
S always plays Attack if it is malicious and Coope-
rate if it is normal. Then, according to Table 1, the
expected utilities of Defend and Idle for the CH-IDS
agent R are:
u
R
(De f end) = p · (α · g
D
− (1 − α) · g
A
− c
D
)
+(1 − p) · (− β − l
F
− c
D
) (2)
and
u
R
(Idle) = −p · g
A
+ (1 − p) · 0 = −p · g
A
(3)
If u
R
(De f end) ≥ u
R
(Idle), we get
p ≥ (β · l
F
+ c
D
)/(α· g
D
+ α· g
A
+ β· l
F
) (4)
then the dominant strategy for the CH-IDS agent R is
Defend. However, if CH-IDS agent R plays Defend, is
reasonable that Attack will not be the dominant stra-
tegy for member vehicle node S because:
(1 − α) · g
A
− α· g
D
− c
A
< g
C
− c
C
(5)
Therefore, (Attack for malicious vehicle, Cooperate
for normal vehicle, Defend for CH-IDS agent) is not
a pure strategy BNE.
If u
R
(De f end) < u
R
(Idle), we get
p < (β · l
F
+ c
D
)/(α· g
D
+ α· g
A
+ β· l
F
) (6)
then the dominan t strategy for CH-IDS agent R is Idle.
Correspon dingly, Attack will be the dominan t strategy
for member vehicle node S because:
g
A
− c
A
> (1 − α) · g
A
− α· g
D
− c
A
(7)
Therefore, (Attack for malicious vehicle S, Coope-
rate for normal vehicle S, Idle for CH-IDS agent R)
is a pure-strategy BNE. 2) When vehicle S selects
the pure-strategy (Cooperate for malicious vehicle,
Cooperate for normal vehicle) which me ans it always
plays the action Cooperate regardless of its type. For
CH-IDS agent R, the best response to Cooperate of
vehicle S is Idle; and for malicious vehicle, the best
response to Idle of CH-IDS agent R is Attack. This is
contradictive to the pure-strategy ( Cooperate for ma-
licious veh ic le , Cooperate for normal vehicle), the-
refore, {Cooperate, Cooperate, Idle} is not a pure-
strategy BNE.
In summary, when
p < (β · l
F
+ c
D
)/(α· g
D
+ α· g
A
+ β· l
F
) (8)
there is a pure-strategy BNE {Attack, Cooperate,
Idle} which means the malicious vehicle always plays
Attack and the normal vehicle always plays Cooperate
while the CH-I D S agent R always plays Idle. Alt-
hough this pur e-strategy BNE is not practical because
CH-IDS agent R must take action Idle. That is, the
malicious membe r vehicle nodes will not be caught
forever. Therefore, for detecting malicious vehicle
Signaling Game-based Approach to Improve Security in Vehicular Networks
499

nodes, it is essential to find a mixed-strategy BNE.
Theorem 2. In the stage Intrusion Detection Game,
there is a mixed-strategy BNE when
p ≥ (β· l
F
+ c
D
)/(α· g
D
+ α· g
A
+ β· l
F
) (9)
Proof. Let σ
S
= (ρ, 1 − ρ) and σ
R
= (δ,1 − δ) are
the mixed strategy for the malicious vehicle S and the
mixed stra tegy for the CH-IDS agent R, respectively.
Then, according to Table 1, the expected utilities for
the vehicle S and the the CH-IDS age nt R are:
u
S
(ρ,δ) = p · ρ · δ· ((1 − α) · g
A
− α· g
D
− c
A
)
+p · ρ · (1 − δ) · (g
A
− c
A
) + p · (1 − ρ) · δ· (g
C
− c
C
)
+p ·(1− ρ)· (1 − δ)· (g
C
−c
C
)+(1− p)·δ·(g
C
−c
C
)
+(1 − p) · (1 − δ) · (g
C
− c
C
) (10)
and
u
R
(ρ,δ) = p · ρ· δ · (α· g
D
− (1 − α) · g
A
− c
D
)
+p · ρ · (1 − δ) · (−g
A
) + p · (1 − ρ) · δ· (−β· l
F
− c
D
)
+p · (1 − ρ) · (1 − δ) · 0 + (1 − p) · δ· (−β· l
F
− c
D
)
+(1 − p) · (1 − δ) · 0 (11)
then, from ∂
ρ
(u
S
(ρ,δ)) = 0 and ∂
δ
(u
R
(ρ,δ)) = 0 we
get,
ρ
∗
= (β · l
F
+ c
D
)/(p · (α· g
D
+ α· g
A
+ β· l
F
)) (12)
and
δ
∗
= (p · g
A
− p · c
A
− g
C
+ c
C
)/(p · (α· g
A
+ α· g
D
))
(13)
Since ρ
∗
≤ 1 beca use it is a probab ility, we have:
p ≥ (β· l
F
+ c
D
)/(α· g
D
+ α· g
A
+ β· l
F
) (14)
In summary, there is a mixed strategy BNE (At-
tack, Cooperate, Defend) when (14) is achieved,
which means the malicious vehicle plays Attack with
probability ρ
∗
and the normal vehicle always p lays
Cooperate while the CH-IDS agent R plays Defend
with probability δ
∗
.
4 CONCLUSION
Because of its frequently changing network topo logy
and deployed applications, the intrusion detection in
VANETs is considered as a challenging task. Every
individual wants to stay safe r and secured on the road
during driving. For this reason, we have proposed
an Intrusion Detection Game based on the signaling
game. This game simulating the interactions between
vehicles an d IDS agent indicates the characteristic of
different stage of attack and defend. The stage In tru-
sion Detection G a me has revealed the essence of VA-
NETs a t every individual slot time. At the same time,
its pure-strategy BNE and mixed-strategy BNE have
made the IDS agent choose Idle or Defend action, not
always Defend. So, the CH-IDS agent can choose its
optimal strategy for defending the malicious vehicle’s
Attack actively.
ACKNOWLEDGEMENTS
We apprec ia te and would like to than k the anonymous
referees for their construc tive comments and sugges-
tions wh ic h will improve the presentation of this work
supported by Mobile Intellige nt System (MIS) Rese-
arch Group, Laboratory of Mobile and Embedde d In-
formation System, ENSIAS, Mohammed V Univer-
sity of Rabat, Mor occo
REFERENCES
Ghosh, M., Varghese, A., Kherani, A. A., and Gupta, A.
(2009). Distributed misbehavior detection in vanets.
In Wireless Communications and Networking Confe-
rence, 2009. WCNC 2009. IEEE, pages 1–6. IEEE.
Mabrouk, A., Kobbane, A., Sabir, E., and Koutbi, M. E .
(2015). Coalitional game theory for cooperative trans-
mission in vanet: Internet access via fixed and mobile
gateways. In International Conference on Networked
Systems, pages 490–495. Springer.
Misra, S., Kr ishna, P. V., and Abraham, K. I. (2011). A sto-
chastic learning automata-based solution f or intrusion
detection in vehicular ad hoc networks. Security and
Communication Networks, 4(6):666–677.
Mohi, M., Movaghar, A., and Zadeh, P. M. (2009). A baye-
sian game approach for preventing dos attacks in wire-
less sensor networks. In Communications and Mobile
Computing, 2009. CMC’09. WRI International Con-
ference on, volume 3, pages 507–511. IEEE.
Pattnaik, O. and Pattanayak, B. K. (2014). S ecurity
in vehicular ad hoc network based on intrusion de-
tection system. American Journal of Applied Scien-
ces, 11(2):337.
Reddy, Y. B. (2009). A game theory approach to detect
malicious nodes in wireless sensor networks. In Sen-
sor Technologies and Applications, 2009. SENSOR-
COMM’09. Third International Conference on, pages
462–468. IEEE.
Ruj, S., Cavenaghi, M. A., Huang, Z., Nayak, A., and Sto-
jmenovic, I. (2011). On data-centric misbehavior de-
tection in vanets. In Vehicular technology conference
(VTC Fall), 2011 IEEE, pages 1–5. IEEE.
Sedjelmaci, H., Senouci, S. M., and Bouali, T. (2016). Pre-
dict and prevent from misbehaving intruders in hete-
rogeneous vehicular networks. Vehicular Communi-
cations.
Sen, J. (2010). A n intrusion detection architecture for clus-
tered wireless ad hoc networks. In Computational
Intelligence, Communication Systems and Networks
(CICSyN), 2010 Second International Conference on,
pages 202–207. IEEE.
Zhang, Y. and Lee, W. (2000). Intrusion detection in wire-
less ad-hoc networks. In Proceedings of the 6th an-
nual international conference on Mobile computing
and networking, pages 275–283. ACM.
VEHITS 2018 - 4th International Conference on Vehicle Technology and Intelligent Transport Systems
500
