
On the Security of Linear Sketch Schemes against Recovering Attacks
Takahiro Matsuda
1
, Kenta Takahashi
2
and Goichiro Hanaoka
1
1
National Institute of Advanced Industrial Science and Technology (AIST), Tokyo, Japan
2
Hitachi Ltd., Yokohama, Japan
Keywords:
Fuzzy Signature, Linear Sketch, Recovering Attacks.
Abstract:
Recently, the notion of fuzzy signature was introduced by Takahashi et al. (ACNS 2015, ACNS 2016, ePrint
2017). It is a signature scheme in which signatures can be generated using “fuzzy data” (i.e. noisy data such
as biometric features) as a signing key, without using any additional user-specific data (such as a helper string
in the context of fuzzy extractors). One of the main building blocks in the existing fuzzy signature schemes, is
a primitive called linear sketch, which can be interpreted as a certain form of (one-way) encoding with which
fuzzy data is encoded, and is used in combination with an ordinary signature scheme with certain functional
and security properties, to construct a fuzzy signature scheme. Although the security of the underlying linear
sketch scheme is very important for the security of the constructed fuzzy signature schemes, a linear sketch
scheme is a relatively new primitive, and what security properties its definition and the existing constructions
satisfy, has not been understood well. In order to deepen our understanding of this primitive, in this paper we
clarify the security properties achieved by the existing linear sketch schemes. More specifically, we formalize
security of a linear sketch scheme against “recovering” attacks, and then clarify that the existing linear sketch
schemes achieve sufficiently strong security against them.
1 INTRODUCTION
1.1 Background and Motivation
Motivated mainly by application scenarios of biomet-
ric authentication, Takahashi et al. (Takahashi et al.,
2015; Matsuda et al., 2016; Takahashi et al., 2017)
recently introduced a special kind of digital signature
called fuzzy signature. In a fuzzy signature scheme,
signatures can be generated using “fuzzy data” (i.e.
noisy data such as biometric features) as a signing
key. There have been some approaches that achieve
a similar feature, and perhaps the most well-known
(and nowadays standard) approach would be to com-
bine an ordinary signature scheme with a fuzzy ex-
tractor (Dodis et al., 2008). However, as pointed
out by Takahashi et al., the fuzzy-extractor-based ap-
proach requires (public but) user-specific auxiliary
data to be present at the time of signing. Hence,
for example, a user has to carry it himself/herself,
or the device executing the signing algorithm has to
be on-line to retrieve the auxiliary data from some
(public) repository. What distinguishes a fuzzy signa-
ture scheme from the fuzzy-extractor-based approach,
is that the signing algorithm does not require user-
specific data (other than his/her own biometric fea-
ture) at the time of signing, and hence for example a
user can generate a signature even if he/she is com-
pletely empty-handed. This is quite attractive, and
fuzzy signatures are expected to be applied to various
applications.
We briefly review the results by Takahashi et al.
(Takahashi et al., 2015; Matsuda et al., 2016; Taka-
hashi et al., 2017).
1
In (Takahashi et al., 2017), in
addition to formally define fuzzy signatures, they in-
troduced what they call a fuzzy key setting, which for-
malizes some necessary information about the setting
over which fuzzy data is considered, e.g. the met-
ric space to which fuzzy data belongs, the threshold
with which two sampled data are considered to be
measured from the same object, the distribution from
which each fuzzy data is assumed to be drawn, how
the fluctuation of fuzzy data is modeled, etc. A fuzzy
signature scheme is associated with such a fuzzy key
setting. (Takahashi et al., 2017) also introduced a tool
that they call linear sketch, which is also a crypto-
1
Since (Takahashi et al., 2017) is the merged full version
of (Takahashi et al., 2015) and (Matsuda et al., 2016), from
here on, by “Takahashi et al.” we mean (Takahashi et al.,
2017) unless indicated.
76
Matsuda, T., Takahashi, K. and Hanaoka, G.
On the Security of Linear Sketch Schemes against Recovering Attacks.
DOI: 10.5220/0006847100760087
In Proceedings of the 15th International Joint Conference on e-Business and Telecommunications (ICETE 2018) - Volume 2: SECRYPT, pages 76-87
ISBN: 978-989-758-319-3
Copyright © 2018 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

graphic primitive associated with a fuzzy key setting,
and is a kind of a pair of linear encoding and error
correction methods that we will detail later. (Taka-
hashi et al., 2017) then gave a generic construction of
a fuzzy signature scheme for a fuzzy key setting from
the combination of a linear sketch scheme (that is as-
sociated with the same fuzzy key setting) and an or-
dinary signature scheme that has some homomorphic
properties regarding signing/verification keys. They
then gave two instantiations of concrete fuzzy signa-
ture schemes via their generic construction, where for
each construction, they specified a fuzzy key setting,
constructed a linear sketch scheme, and then com-
bined it with (a modified variant of) an existing or-
dinary signature scheme.
Linear Sketch. The main focus in this paper is on
a linear sketch scheme. As mentioned earlier, this
primitive can be understood as a pair of linear en-
coding and error correction methods. It is associated
with a fuzzy key setting and an abelian group K , and
consists of two algorithms
2
: “Sketch” and “DiffRec”
(where the second algorithm stands for “difference re-
construction”). The first algorithm can be used to gen-
erate a “sketch” c of an element s ∈ K using a fuzzy
data x as a “key” (or a “mask”). The second algorithm
takes as input two sketches c and c
0
, where c (resp.
c
0
) is supposedly a sketch of an element s ∈ K (resp.
s
0
∈ K ) generated by using fuzzy data x (resp. x
0
),
and outputs the difference ∆s = s −s
0
if the two fuzzy
data x and x
0
are “close” (according to the threshold
t specified in the fuzzy key setting). In (Takahashi
et al., 2017), it is required that a linear sketch scheme
satisfies additional “linearity” and “weak simulatabil-
ity” properties that are used in the security proof for
the generic construction.
Our Motivation. Although the security of the un-
derlying linear sketch scheme is very important for
the security of the fuzzy signature schemes con-
structed from the generic construction of Takahashi
et al., a linear sketch scheme is a relatively new prim-
itive, and what security properties its definition and
the existing constructions satisfy, has not been well
understood. As mentioned above, in the formaliza-
tion in (Takahashi et al., 2017), a linear sketch scheme
is associated with a fuzzy key setting, which in turn
specifies the underlying metric space and distribution
of fuzzy data. So far, we only have two concrete con-
structions of linear sketch schemes: the first scheme
2
A linear sketch scheme actually also has the setup al-
gorithm Setup that outputs a public parameter used by the
other algorithms, but we omit them in the explanation in the
introduction. The formal definition appears in Section 3.
(denoted by “S
CRT
”) is based on the Chinese remain-
der theorem, and the second one (denoted by “S
Hash
”)
is based on a universal hash function family, and the
fuzzy data space for these constructions is the space
[0,1)
n
with the L
∞
-distance. Since the constructions
S
CRT
and S
Hash
seem tailored to this specific metric
space, they have to inherently deal with non-integer
numbers and furthermore they cannot be used with
fuzzy key settings with other natural metrics for bio-
metric authentication such as the edit distance and
Hamming distance over bit strings.
In fact, the earlier papers (Takahashi et al., 2015;
Matsuda et al., 2016) left the treatment of real num-
bers somewhat ambiguous, and Yasuda et al. (Yasuda
et al., 2017) showed that the linear sketch schemes
S
CRT
and S
Hash
could be vulnerable to so-called “re-
covering attacks” (which recover fuzzy data x and an
element s from a sketch c = Sketch(s,x)), if the real
numbers in these schemes are treated in an inappro-
priate way. Concurrently to (Yasuda et al., 2017), the
treatment of real numbers was unambiguously speci-
fied in (Takahashi et al., 2017), and with their treat-
ment the attacks by (Yasuda et al., 2017) were shown
to no longer work. However, this situation suggests
that care must be taken in the definition of linear
sketch schemes.
The main motivation of this paper is to contribute
to deepening our understanding of this primitive, so
that we can come up with better constructions and ap-
plications, which potentially could lead to future new
constructions of fuzzy signatures (with fuzzy key set-
tings that are different from the existing schemes).
1.2 Our Contributions
In order to deepen our understanding of a linear
sketch scheme, in this paper we clarify a new aspect
of the security properties achieved by the existing lin-
ear sketch schemes.
More specifically, in Section 4, we introduce se-
curity of a linear sketch scheme against “recovering”
attacks, which directly captures the resistance against
the attacks of (Yasuda et al., 2017). Namely, it re-
quires that recovering fuzzy data x from a sketch c
(and a public parameter pp) is hard. Our formaliza-
tion uses the notion of average min-entropy (Dodis
et al., 2008), which naturally corresponds to the hard-
ness of guessing a secret given some leakage. Then,
as our main technical results, we show that the two
linear sketch schemes in (Takahashi et al., 2017), S
CRT
and S
Hash
, satisfy sufficient level of security against
recovering attacks (when the treatment of real num-
bers in (Takahashi et al., 2017) is taken into account),
which are respectively shown in Sections 5 and 6.
On the Security of Linear Sketch Schemes against Recovering Attacks
77

These results directly imply that the attacks of (Ya-
suda et al., 2017) do not apply to the linear sketch
schemes in (Takahashi et al., 2017).
We remark that if a linear sketch scheme is vulner-
able to recovering attacks and is used in the generic
construction of (Takahashi et al., 2017), then the re-
sulting fuzzy signature scheme is also not secure. (In
this sense, security against recovering attacks can be
interpreted as a guideline for future designs of linear
sketch schemes.) Since (Takahashi et al., 2017) gives
security proofs for their fuzzy signature schemes, it
implies that the linear sketch schemes in (Takahashi
et al., 2017) are known to be secure against recover-
ing attacks. Our results show this fact more directly.
To show the security of the linear sketch schemes
against recovering attacks, we introduce the notion of
decomposability and partial hiding property of a lin-
ear sketch scheme. Informally speaking, the decom-
posability property requires that the computation of
c = Sketch(s,x) can be decomposed into two parts
f
1
and f
2
, where f
2
is independent of s, so that the
computation c = Sketch(s,x) is equivalent to c =
(c
1
,c
2
) = ( f
1
(s,x), f
2
(x)). The partial hiding prop-
erty requires that c
1
= f
1
(s,x) does not contain any in-
formation of x if s is chosen uniformly at random. We
will show that if a linear sketch scheme satisfies these
properties, then its security against recovering attacks
can be reduced to the hardness of recovering fuzzy
data x given only the leakage from the second com-
ponent f
2
(x), which means that the security against
recovering attacks can be analyzed by analyzing only
the distribution of x and f
2
. These properties make it
easier to show the security of linear sketch schemes
against recovering attacks, and we believe that their
formalizations are useful for future designs of linear
sketch schemes. We will show that the linear sketch
schemes S
CRT
and S
Hash
satisfy these properties in Sec-
tions 5.4 and 6.3, respectively. For the formal defini-
tions and the more details on how they are useful, see
Section 4.
1.3 Paper Organization
The rest of this paper is organized as follows: In Sec-
tion 2, we review some basic notation, basic defini-
tions and facts, and the treatment of real numbers. In
Section 3, we review the necessary definitions for lin-
ear sketch. In Section 4, we introduce security against
recovering attacks for a linear sketch scheme. There,
we also introduce decomposability and the partial hid-
ing property of a linear sketch scheme, and show a
useful lemma that is used in the subsequent sections.
In Section 5, we show how strong the first linear
sketch scheme S
CRT
is against recovering attacks. In
Section 6, we do the same for the second linear sketch
scheme S
Hash
.
2 PRELIMINARIES
In this section, we review the basic notation, basic
definitions and facts, and the treatment of real num-
bers in this paper.
2.1 Basic Notation
N, Z, and R denote the sets of all natural numbers, all
integers, and all real numbers, respectively. If n ∈ N,
then we define [n] := {1, . . .,n}. If a,b ∈ N, then
“GCD(a,b)” denotes the greatest common divisor of a
and b. If a ∈ R, then “bac” denotes the maximum inte-
ger which does not exceed a (i.e. the rounding-down
operation), and “bae” denotes the integer that is the
nearest to a (i.e. the rounding operation). Through-
out the paper, we use the bold font to denote a vector
(such as x and a). We extend the definition of “b·e” to
allow it to take a real vector a = (a
1
,a
2
,...) as input,
by bae := (ba
1
e,ba
2
e,...).
“x ← y” denotes that y is (deterministically) as-
signed to x. If S is a finite set, then “|S|” denotes its
size, and “x ←
R
S” denotes that x is chosen uniformly
at random from S. If Φ is a distribution (over some
set), then x ←
R
Φ denotes that x is chosen accord-
ing to the distribution Φ. If x and y are bit-strings,
then |x| denotes the bit-length of x, and “(x||y)” de-
notes the concatenation of x and y. “(P)PTA” denotes
a (probabilistic) polynomial time algorithm. If A is a
probabilistic algorithm, then “y ←
R
A(x)” denote that
A computes y by taking x as input and using an inter-
nal randomness that is chosen uniformly at random.
Throughout the paper, “k” denotes a security parame-
ter. A function f (·) : N → [0, 1] is said to be negligible
if for all positive polynomials p(·) and all sufficiently
large k, we have f (k) < 1/p(k).
2.2 Treatment of Real Numbers
Here, we recall the treatment of real numbers in
(Takahashi et al., 2017). The following explanations
are mostly taken verbatim from the “On the Treat-
ment of Real Numbers” paragraph in (Takahashi et al.,
2017, Section 6).
We assume that the significand of all real num-
bers is expressed in an a-priori fixed length (in bits)
λ, where λ is some natural number that is a polyno-
mial of a security parameter k. That is, a real num-
ber is expressed in the form
m
2
γ
, where m is a λ-bit
integer that represents the significand and −γ ∈ Z is
SECRYPT 2018 - International Conference on Security and Cryptography
78

the exponent.
3
Furthermore, if real numbers are in-
volved in some arithmetic operations such as addition
and multiplication, then the rounding-down operation
is naturally applied to the significand of the result-
ing number, so that the result is always expressed in
the above form (i.e. its significand is expressed with
λ bits). We stress that this setting is natural, taking
computer implementations into account.
For example, if we multiply a real number x =
m
2
γ
(where m is a λ-bit integer and 0 ≤ γ ≤ λ) with an n-
bit integer a (where n ≤ γ), then the resulting number
x · a of the multiplication of x and a is treated as
j
m · a
2
n
k
· 2
−(γ−n)
. (1)
That is, its significand is a λ-bit integer b
m·a
2
n
c and its
exponent is −(γ− n). This might not look straightfor-
ward at first glance, but note that the significand b
m·a
2
n
c
is the result of the multiplication m · a rounded down
to have a λ-bit precision (the denominator 2
n
is due
to the fact that a is an n-bit integer). The exponent is
correspondingly “shifted” to take into account that a
is an n-bit integer. See Figure 1 for an illustration for
the calculation of x · a.
2.3 Basic Definitions on Entropy
Here, we recall several basic definitions and a fact re-
lated to entropy used in this paper.
Definition 1. Let X be a distribution defined over a
set X. The min-entropy of X , denoted by H
∞
(X ), is
defined by H
∞
(X ) := −log
2
max
x
0
∈X
Pr[X = x
0
].
Definition 2 ((Dodis et al., 2008)). Let (X ,Y ) be a
joint distribution defined over the direct product of
sets X ×Y . The average min-entropy of X given Y ,
denoted by
e
H
∞
(X |Y ), is defined by
e
H
∞
(X |Y ) := −log
2
E
y←
R
Y
h
max
x
0
∈X
Pr[X = x
0
|Y = y]
i
.
Note that the average min-entropy
e
H
∞
(X |Y ) nat-
urally captures the hardness of recovering a “secret”
x from a “leakage” y when (x,y) is sampled ac-
cording to (X ,Y ). More specifically, the defini-
tion of average min-entropy
e
H
∞
(X |Y ) implies that
if (x,y) ←
R
(X , Y ), then given y, even a computa-
tionally unbounded algorithm can succeed in finding
x with probability at most 2
−
e
H
∞
(X |Y )
.
We will use the following simple fact formally
shown in (Dodis et al., 2008).
Lemma 1. Let (X ,Y ) be a joint distribution defined
over the direct product of sets X ×Y . If |Y | ≤ 2
t
for
some t ∈ N, then
e
H
∞
(X |Y ) ≥ H
∞
(X ) − t.
3
For ease of treatment of decimal numbers, we use the
convention that a positive γ implies a negative exponent.
2.4 Universal Hash Function Family
Here, we first recall the definition of a universal hash
function family, then the existence of a universal hash
function family with linearity.
Definition 3. Let H = {h
z
: D → R}
z∈Z
be a fam-
ily of hash functions, where Z denotes the seed space
of H . We say that H is a universal hash function
family if for all x,x
0
∈ D such that x 6= x
0
, we have
Pr
z←
R
Z
[h
z
(x) = h
z
(x
0
)] ≤ 1/|R|.
In the linear sketch scheme S
Hash
in (Takahashi
et al., 2017), a universal hash function family with
a linearity property is used. (See e.g. (Cheraghchi,
2011) for a concrete construction.)
Lemma 2. Let F
p
be a finite field with prime order p,
and let n ∈ N. There exists a family of universal hash
function H
lin
= {h
z
: (F
p
)
n
→ F
p
}
z∈F
p
n
such that for
all z ∈ F
p
n
, the following linearity property is satis-
fied: For all x,x
0
∈ (F
p
)
n
and α,β ∈ F
p
, it holds that
α · h
z
(x) + β · h
z
(x
0
) = h
z
(α · x + β · x
0
).
3 DEFINITIONS FOR LINEAR
SKETCH
Here, we review the definitions for a fuzzy key set-
ting in Section 3.1 and a linear sketch scheme in Sec-
tion 3.2.
In order to grasp how linear sketch schemes are
used in the constructions of a fuzzy signature scheme,
in Appendix, we review the definition of a fuzzy sig-
nature scheme as well as the two fuzzy signature
schemes proposed in (Takahashi et al., 2017).
3.1 Fuzzy Key Setting
A fuzzy key setting specifies a metric space to which
fuzzy data (such as biometric data) belongs, the
threshold with which two sampled fuzzy data are con-
sidered close/far, the distribution from which each
fuzzy data is assumed to be sampled, and the error
distribution that models “fluctuation” of fuzzy data.
The formalization of (Takahashi et al., 2017) adopts
the so-called universal error model, which assumes
that for all objects U that produce fuzzy data that we
are interested in, if U produces a data x at the first
measurement (e.g. at the registration), and the same
object is measured next time, then the measured data
x
0
follows the distribution {e ←
R
Φ; x
0
← x + e : x
0
}.
Formally, a fuzzy key setting F consists of
((d,X),t,X ,Φ,ε
e
), each of which is defined as fol-
lows:
On the Security of Linear Sketch Schemes against Recovering Attacks
79
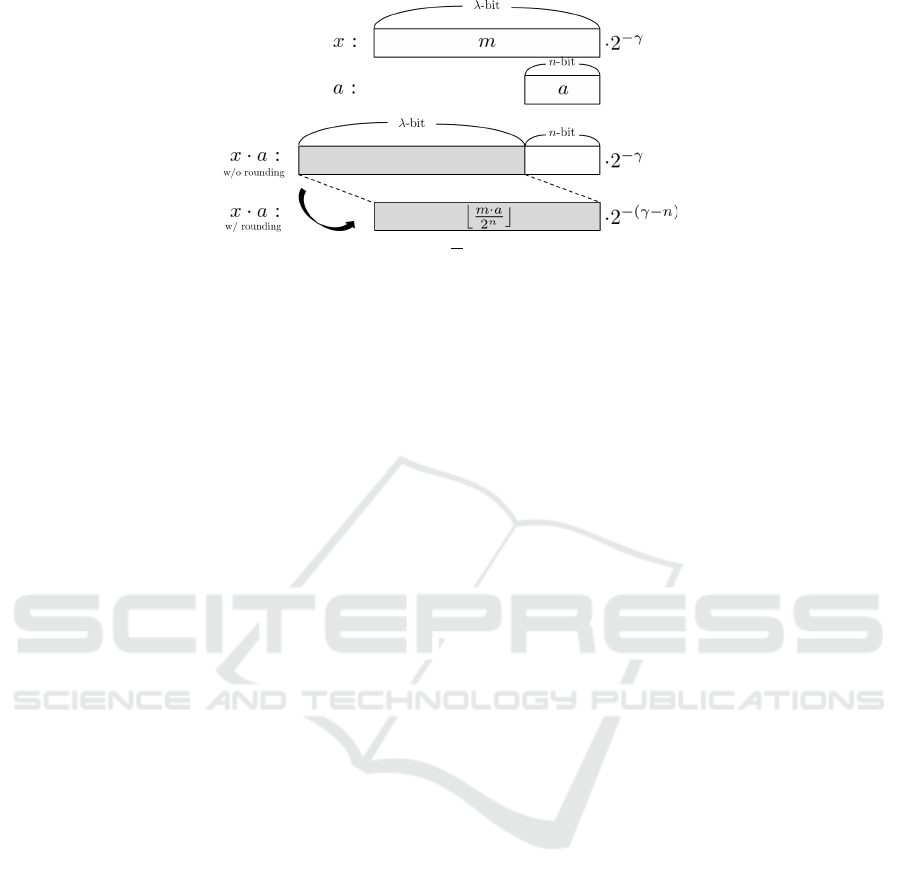
Figure 1: An illustration of multiplication of a real number x =
m
2
γ
and an n-bit integer a. (This picture is taken from (Takahashi
et al., 2017, Fig. 5).)
(d,X): This is a metric space, where X is a space
to which a possible fuzzy data x belongs, and
d : X
2
→ R is the corresponding distance func-
tion. We furthermore assume that X constitutes
an abelian group.
t: (∈ R) This is the threshold value, determined by
a security parameter k. Based on t, the false ac-
ceptance rate (FAR) and the false rejection rate
(FRR) are determined. We require that FAR :=
Pr[x,x
0
←
R
X : d(x,x
0
) < t] is negligible in k.
X : This is a distribution of fuzzy data over X .
Φ: This is an error distribution (see the above expla-
nation).
ε
e
: (∈ [0,1]) This is an error parameter that represents
FRR. We require that for all x ∈ X, FRR := Pr[e ←
R
Φ : d(x,x + e) ≥ t] ≤ ε
e
.
We remark that the false acceptance/rejection rate
FAR and FRR, the error distribution Φ, and the error
parameter ε
e
are not directly used in our paper be-
cause they do not directly affect the security of linear
sketch schemes.
3.2 Linear Sketch
Here, we review the definition of a linear sketch
scheme in (Takahashi et al., 2017).
Let F = ((d,X),t, X ,Φ,ε
e
) be a fuzzy key setting,
and let K be a finite abelian group. A linear sketch
scheme S for (F ,K ), consists of the following three
algorithms (Setup,Sketch,DiffRec):
Setup is the “setup” algorithm that takes 1
k
, and out-
puts a public parameter pp.
Sketch is the “sketching” algorithm that takes pp, an
element s ∈ K , and fuzzy data x ∈ X as input, and
outputs a “sketch” c.
DiffRec is the (deterministic) “difference reconstruc-
tion” algorithm that takes pp and two values c, c
0
(supposedly output by Sketch) as input, and out-
puts the “difference” ∆s ∈ K .
For correctness, it is required that for all k ∈
N, all x, x
0
∈ X such that d(x, x
0
) < t, all
pp output by Setup(1
k
), and all s,∆s ∈ K ,
we have DiffRec(pp,Sketch(pp, s, x), Sketch(pp,s +
∆s,x
0
)) = ∆s.
Besides, the properties called linearity and weak
simulatability are formalized in (Takahashi et al.,
2017). Informally, the linearity ensures that given
pp, a sketch value c output from Sketch(pp, s, x), and
“shift” values ∆s ∈ K and ∆x ∈ X , it is possible to
compute a sketch value c
0
that is distributed as if it is
computed from Sketch(pp,s + ∆s, x + ∆x). The weak
simulatability captures a weak form of confidentiality
that c does not leak the information of the content s
if s is chosen uniformly at random from K and x is
sampled from X . Since we do not directly use these
properties, we omit the formal definitions. See (Taka-
hashi et al., 2017) for the formal definitions.
4 DEFINING SECURITY
AGAINST RECOVERING
ATTACKS
In this section, we introduce security of a linear sketch
scheme against recovering attacks. We then introduce
structural properties of a linear sketch scheme that we
call the decomposability and partial hiding property.
Finally, we show a lemma that is useful for analyz-
ing the security of linear sketch schemes that satisfy
these properties. This lemma plays the main role in
the subsequent sections.
In the following definitions, let F = ((d,X),t,X ,
Φ,ε
e
) be a fuzzy key setting, let K be an abelian
group, and let S = (Setup,Sketch,DiffRec) be a lin-
ear sketch for (F ,K ).
Definition 4. Let ε
r
= ε
r
(k) ∈ [0, 1]. We say that a
linear sketch scheme S for (F , K ) is ε
r
-secure against
recovering attacks if Adv
recover
S
(k) := 2
−
e
H
∞
(X |P ,C )
≤
ε
r
holds, where (P ,C ) is the joint distribution defined
SECRYPT 2018 - International Conference on Security and Cryptography
80

as follows:
(P , C ) := { pp ←
R
Setup(1
k
); x ←
R
X ;
s ←
R
K ; c ←
R
Sketch(pp,s,x) : (pp,c) }. (2)
(Note that (X , P ,C ) forms a joint distribution.)
As mentioned earlier, the average min-entropy
e
H
∞
(X |P ,C ) (in the form of 2
−
e
H
∞
(X |P ,C )
) gives an up-
per bound of the best (computationally unbounded)
adversary’s advantage in guessing x given (pp,c),
when (x, pp, c) is sampled according to the joint dis-
tribution (X ,P ,C ). Hence, if ε
r
is (negligibly) small,
ε
r
-security against recovering attacks guarantees that
recovering x from (pp,c) is hard.
Next, we introduce a structural property for a
linear sketch scheme that we call decomposability,
which means that an execution of Sketch(pp,s, x) can
be decomposed into computing two sub-functions f
1
and f
2
, where f
1
is a (possibly probabilistic) func-
tion whose output depends on (pp,s, x), while f
2
is
a deterministic function whose output depends only
on (pp,x) (and independent of s), so that a sketch
c consists of the outputs from f
1
and f
2
, i.e., c =
( f
1
(pp,s,x), f
2
(pp,x)). We also require the prop-
erty that we call partial hiding, which requires that
the first function f
1
hides the information of x from
its output c
1
if the input s is chosen randomly. (We
do not require the same for f
2
, and hence the name
“partial”.) The usefulness of the decomposability and
partial-hiding property will be evident later.
Definition 5. We say that a linear sketch scheme S for
(F ,K ) is decomposable, if there exist the following
two efficiently computable functions f
1
, f
2
:
• f
1
is a (possibly probabilistic) function that takes
pp (output by Setup), s ∈ K , and x ∈ X as input,
and outputs some value c
1
.
• f
2
is a deterministic function that takes pp (output
by Setup) and x ∈ X as input, and outputs some
value c
2
.
It is required that for all pp output by Setup, x ∈ X ,
and s ∈ K , the following two distributions D
1
and D
2
are identically distributed:
D
1
:= {c = (c
1
,c
2
) ←
R
Sketch(pp,s,x) : c },
D
2
:= {c
1
←
R
f
1
(pp,s,x); c
2
← f
2
(pp,x) : (c
1
,c
2
)}
f
1
and f
2
are called the decomposed functions of
Sketch.
Furthermore, we say that a decomposable linear
sketch scheme S (with the decomposed functions f
1
and f
2
) is partially hiding if for all pp output by
Setup, the distribution {x ←
R
X ; s ←
R
K ; c
1
←
R
f
1
(pp,x,s) : c
1
} is independent of the original fuzzy
data distribution X .
We now show that any decomposable linear sketch
scheme S = (Setup, Sketch,DiffRec) with partial hid-
ing property, satisfies a convenient property that its se-
curity against recovering attacks can be analyzed only
from X and f
2
(irrelevantly to f
1
, s, or c).
Lemma 3. Let S = (Setup,Sketch,DiffRec) be a lin-
ear sketch scheme S for (F , K ). Assume that S sat-
isfies decomposability (with decomposed functions f
1
and f
2
) and the partial hiding property. Then, it holds
that Adv
recover
S
(k) = 2
−
e
H
∞
(X |P , f
2
(P ,X ))
.
Proof of Lemma 3. Consider the following distribu-
tion that outputs (pp,c
1
,c
2
):
{ pp ←
R
Setup(1
k
); x ←
R
X ; s ←
R
K ;
c
1
←
R
f
1
(pp,s,x); c
2
← f
2
(pp,x) : (pp,c
1
,c
2
) }.
Let P , C
1
, and C
2
be the distributions that correspond
to computing and outputting pp, c
1
and c
2
in the
above distribution, respectively. Note that (P ,C
1
,C
2
)
forms a joint distribution, and furthermore we have
C
2
= f
2
(P , X ) by definition. Due to the decompos-
ability of S, the joint distribution (P ,C ) (defined
in Eq. (2)) and the joint distribution (P ,C
1
,C
2
) are
equivalent, and thus it holds that
e
H
∞
(X |P ,C ) =
e
H
∞
(X |P ,C
1
,C
2
)
=
e
H
∞
(X |P ,C
1
, f
2
(P , X )).
Furthermore, by the partial hiding property and
the fact that X is independent of the generation
of a public parameter, X and C
1
are guaranteed
to be independent, which means that we have
e
H
∞
(X |P ,C
1
, f
2
(P , X )) =
e
H
∞
(X |P , f
2
(P , X )).
Combining the above arguments, we obtain
Adv
recover
S
(k) = 2
−
e
H
∞
(X |P ,C )
= 2
−
e
H
∞
(X |P , f
2
(P ,X ))
.
This completes the proof of Lemma 3.
5 RECOVERING ATTACK
SECURITY OF LINEAR
SKETCH SCHEME S
CRT
In this and next sections, we show our main results:
security of the linear sketch schemes in (Takahashi
et al., 2017) against recovering attacks. In this sec-
tion, we do this for the first linear sketch scheme S
CRT
.
This section is organized as follows: In Sec-
tion 5.1, we recall a concrete fuzzy key setting F
1
with which the linear sketch scheme S
CRT
is associ-
ated. Then, in Section 5.2, we review some math-
ematical background for describing S
CRT
. In Sec-
tion 5.3, we give the description of S
CRT
. Finally, in
Section 5.4, we show how secure the linear sketch
scheme S
CRT
is against recovering attacks.
On the Security of Linear Sketch Schemes against Recovering Attacks
81

A large part of Sections 5.1, 5.2, and 5.3 is taken
verbatim from Sections 6.1, 6.2, and 6.3 of (Takahashi
et al., 2017), respectively.
5.1 Specific Fuzzy Key Setting F
1
Here, we recall a concrete fuzzy key setting F
1
=
((d,X),t,X ,Φ,ε
e
) for which the linear sketch scheme
S
CRT
is constructed.
Metric space (d,X): We define the space X by X :=
[0,1)
n
⊂ R
n
, where n is a parameter specified by
the context (e.g. an object from which we mea-
sure fuzzy data). We use the L
∞
-distance as the
distance function d : X × X → R. Namely, for
x = (x
1
,...,x
n
) ∈ X and x
0
= (x
0
1
,...,x
0
n
) ∈ X , we
define d(x,x
0
) := kx − x
0
k
∞
:= max
i∈[n]
|x
i
− x
0
i
|.
Note that X forms an abelian group with respect
to coordinate-wise addition (modulo 1).
Threshold t: For a security parameter k, we define
the threshold t ∈ R so that
k = b−n log
2
(2t)c. (3)
Furthermore, we require that n = O(log
2
k), so
that 2
n
can be considered to be upper-bounded by
some polynomial of k. This property was used in
(Takahashi et al., 2017) to show the weak simu-
latability of the linear sketch scheme S
CRT
.
Distribution X : The uniform distribution over a
“discretized” version of X = [0,1)
n
. Specifically,
let λ ∈ N be the natural number that denotes the
representation length of a real number (see Sec-
tion 2.2). We require that each coordinate x
i
of a data x = (x
1
,...,x
n
) ∈ X be distributed as
{ j
i
←
R
Z
2
λ
:
j
i
2
λ
}. Furthermore, we require λ to
be sufficiently large (at least dk/ne).
Error distribution Φ and Error parameter ε
e
: Φ
is any efficiently samplable distribution over X
such that FRR ≤ ε
e
for all x ∈ X.
5.2 Mathematical Preliminaries
We recall some mathematical background that is nec-
essary for describing the first linear sketch scheme
S
CRT
in (Takahashi et al., 2017).
Let n ∈ N, and w
1
,...,w
n
∈ N be positive inte-
gers with the same bit length (i.e. dlog
2
w
1
e = ·· · =
dlog
2
w
n
e), such that
∀i ∈ [n] : w
i
≤
1
2t
, and ∀i 6= j ∈ [n] : GCD(w
i
,w
j
) = 1,
(4)
and W =
∏
i∈[n]
w
i
= Θ(2
k
), where k is defined as in
Eq. (3). Note that Eqs. (3) and (4) imply that we have
w
i
≤ 2
dk/ne
for all i ∈ [n]. We assume that there exists
a deterministic algorithm WGen that on input (t, n)
outputs w = (w
1
,...,w
n
) satisfying the above.
For vectors v = (v
1
,...,v
n
) ∈ N
n
, we define
v mod w := (v
1
mod w
1
,...,v
n
mod w
n
). (5)
For vectors v
1
,v
2
∈ N
n
, we define the equivalence re-
lation “∼” by
v
1
∼ v
2
def
⇐⇒ v
1
mod w = v
2
mod w,
and let Z
n
w
:= Z
n
/ ∼ be the quotient set of Z
n
by ∼.
Note that (Z
n
w
,+) constitutes an abelian group, where
the addition is modulo w as defined in Eq. (5).
According to the Chinese remainder theorem
(CRT), each element in Z
W
can be uniquely repre-
sented as an element in Z
n
w
, and vice versa. Let
CRT
w
: Z
n
w
→ Z
W
be the mapping that transforms an
element in s ∈ Z
n
w
into s ∈ Z
W
via the CRT, and we
denote by CRT
−1
w
the inverse function of CRT
w
. Note
that for all v
1
,v
2
∈ Z
n
w
, it holds that
CRT
w
(v
1
+ v
2
) = CRT
w
(v
1
) + CRT
w
(v
2
) mod W.
Similarly to Z
n
w
, we define R
n
w
:= R
n
/ ∼ to be the
quotient set of real vector space R
n
by the equivalence
relation ∼, where for a real number y ∈ R, we define
r = y mod w
i
by the number such that ∃n ∈ Z : y =
nw
i
+ r and 0 ≤ r < w
i
.
Let E
w
: R
n
→ R
n
w
be the following function:
E
w
(x) := (w
1
x
1
,...,w
n
x
n
) ∈ R
n
w
,
where x = (x
1
,...,x
n
) ∈ R
n
. Note that it holds that
E
w
(x + e) = E
w
(x) + E
w
(e) (mod w). (6)
Let C
w
: R
n
w
→ Z
n
w
be the following function:
C
w
(y
1
,...,y
n
)
:=
by
1
+ 0.5c,...,by
n
+ 0,5c
.
(7)
We note that the rounding-down operation by
i
+ 0.5c
in C
w
can be regarded as a kind of error correction.
Specifically, by the conditions in Eq. (4), the fol-
lowing properties are satisfied: For any x,x
0
∈ X, if
d(x,x
0
) = |x − x
0
k
∞
< t, then we have
E
w
(x) − E
w
(x
0
)
∞
< t · max
i∈[n]
{w
i
} ≤ 0.5.
Therefore, for such x,x
0
, it always holds that
C
w
E
w
(x) − E
w
(x
0
)
= 0. (8)
Additionally, for any x ∈ R
n
and s ∈ Z
n
w
, the following
holds:
C
w
(x + s) = C
w
(x) + s (mod w). (9)
SECRYPT 2018 - International Conference on Security and Cryptography
82

5.3 Scheme Description
Let F
1
= ((d, X ),t,X , Φ, ε
e
) be the fuzzy key setting
defined in Section 5.1, and let w = (w
1
,...,w
n
) =
WGen(t,n), where n is the dimension of X , and
let W =
∏
i∈[n]
w
i
. Let CRT
w
, CRT
−1
w
, E
w
, and
C
w
be the functions defined in the previous subsec-
tion. Using these objects, the linear sketch scheme
S
CRT
= (Setup,Sketch,DiffRec) for F
1
and the addi-
tive group (Z
W
,+), is constructed as in Figure 2.
Note that the setup algorithm Setup in this lin-
ear sketch scheme actually does nothing, and the
main algorithms Sketch and DiffRec are determinis-
tic. Furthermore, recall that the rounding-down op-
eration is applied after multiplication of a real num-
ber and an integer is performed, so that the result-
ing real number has a λ-bit significand. Concretely,
let s ∈ Z
W
and s = (s
1
,...,s
n
) = CRT
−1
w
, and sup-
pose that c = (c
1
,...,c
n
) ∈ R
n
w
is a sketch output
from Sketch(pp,s, x), where x = (x
1
,...,x
n
) ←
R
X
and thus each x
i
is of the form x
i
=
j
i
2
λ
for some λ-bit
integer j
i
. Then, since each w
i
is a dk/ne-bit inte-
ger, x
0
i
= w
i
x
i
results in b
w
i
· j
i
2
dk/ne
c · 2
−(λ−dk/ne)
. Conse-
quently, each c
i
∈ R
w
i
is of the following form:
c
i
= s
i
+
j
w
i
· j
i
2
dk/ne
k
· 2
−(λ−dk/ne)
mod w
i
. (10)
It was shown in (Takahashi et al., 2017) that S
CRT
satisfies correctness, and also satisfies the linearity
and weak simulatability properties.
5.4 Security against Recovering Attacks
In this subsection, we show how secure the linear
sketch scheme S
CRT
is against recovering attacks. To
this end, we first show that S
CRT
satisfies decompos-
ability with the partial hiding property.
Lemma 4. The linear sketch scheme S
CRT
satisfies the
decomposability and partial hiding property.
Proof of Lemma 4. Let s ∈ Z
W
and s = (s
1
,...,s
n
) :=
CRT
−1
w
(s) ∈ Z
w
. Let c = (c
1
,...,c
n
) ∈ R
n
w
be
a sketch output from Sketch(pp,s,x), where x =
(x
1
,...,x
n
) ←
R
X and thus each x
i
is of the form
x
i
=
j
i
2
λ
for some λ-bit integer j
i
. As mentioned in the
previous subsection, due to the rounding-down opera-
tion performed at each multiplication w
i
· x
i
, each co-
ordinate c
i
of the sketch c is computed as in Eq. (10).
Here, we consider the “integer” part c
(i)
in
and the “dec-
imal” part c
(i)
de
of c
i
, which are as follows:
c
(i)
in
= bc
i
c = s
i
+
jj
w
i
· j
i
2
dk/ne
k
· 2
−(λ−dk/ne)
k
mod w
i
,
(11)
c
(i)
de
= c
i
mod 1 =
j
w
i
· j
i
2
dk/ne
k
· 2
−(λ−dk/ne)
mod 1.
(12)
Note that c
(i)
in
∈ Z
w
i
and c
(i)
de
∈ [0, 1). Note also that the
decimal part c
(i)
de
is independent of s
i
due to “ mod 1”.
We can make use of this fact, and define the decom-
posed functions f
1
(pp,s,x) and f
2
(pp,x) as follows:
f
1
(pp,s,x): This function outputs c
1
= (c
(1)
in
,...,
c
(n)
in
) ∈ Z
n
w
, where each c
(i)
in
is computed as in
Eq. (11).
f
2
(pp,x): This function outputs c
2
= (c
(1)
de
,...,c
(n)
de
)
∈ [0, 1)
n
, where each c
(i)
de
is computed as in
Eq. (12).
Furthermore, it is straightforward to see that f
1
satisfies the partial hiding property. Specifically, if
s ∈ Z
W
is chosen uniformly at random, then s =
(s
1
,...,s
n
) = CRT
−1
(s) is distributed uniformly over
Z
n
w
. Hence, each s
i
acts as a key for one-time pad
encryption, and thus each c
(i)
in
∈ Z
w
i
does not contain
any information of x
i
. Therefore, when s ∈ Z
W
is cho-
sen uniformly at random, the output c
1
of f
1
(pp,s,x)
becomes independent of x. This completes the proof
of Lemma 4.
We now show how secure the linear sketch scheme
S
CRT
is against recovering attacks.
Theorem 1. The linear sketch scheme S
CRT
satisfies
2
−k
-security against recovering attacks.
Proof of Theorem 1. Due to Lemmas 3 and 4, and the
fact that P does not involve any probabilistic opera-
tion, we have
Adv
recover
S
CRT
(k) = 2
−
e
H
∞
(X |P , f
2
(P ,X ))
= 2
−
e
H
∞
(X | f
2
(P ,X ))
.
Moreover, due to our treatment of real numbers,
each coordinate c
(i)
de
of the output of f
2
can have at
most 2
λ−dk/ne
values. Hence, the entire output of f
2
can take at most (2
λ−dk/ne
)
n
≤ 2
n·λ−k
values. Since
H
∞
(X ) = n · λ holds due to the assumption on the
fuzzy data distribution, by applying Lemma 1, we can
estimate
e
H
∞
(X | f
2
(P , X )) as follows:
e
H
∞
(X | f
2
(P , X )) ≥ H
∞
(X ) − (n · λ − k)
= n · λ − (n · λ − k) = k.
Combining the two inequalities, we obtain
Adv
recover
S
CRT
(k) ≤ 2
−k
, which means that S
CRT
satisfies 2
−k
-security against recovering attacks. This
completes the proof of Theorem 1.
On the Security of Linear Sketch Schemes against Recovering Attacks
83

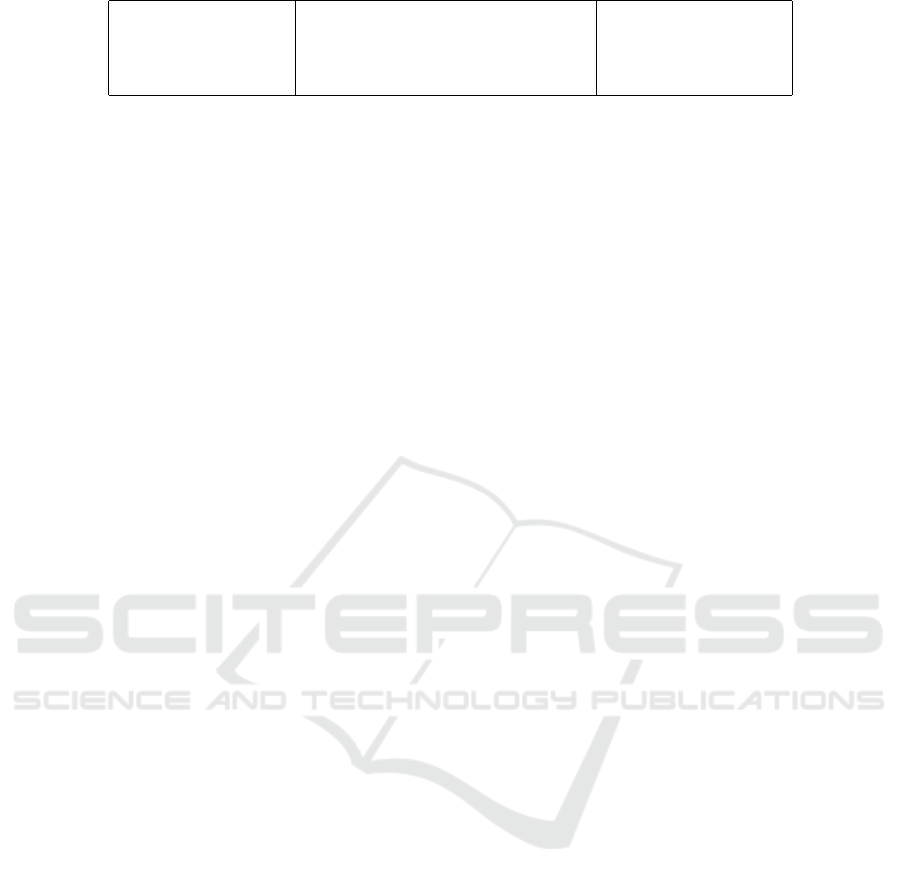
Setup(1
k
) :
Return pp ← (w
1
,...,w
n
,W).
Sketch(pp,s ∈ Z
W
,x ∈ [0, 1)
n
) :
c ← (CRT
−1
w
(s) + E
w
(x)) mod w
Return c.
DiffRec(pp,c,c
0
) :
∆s ← C
w
(c
0
− c)
∆s ← CRT
w
(∆s)
Return ∆s.
Figure 2: The linear sketch scheme S
CRT
= (Setup, Sketch,DiffRec) for the fuzzy key setting F
1
. In the figure, addi-
tions/subtractions are done in R
n
w
.
6 RECOVERING ATTACK
SECURITY OF THE LINEAR
SKETCH SCHEME S
Hash
In this section, we show the security of the second
linear sketch scheme S
Hash
in (Takahashi et al., 2017)
against recovering attacks.
This section is organized as follows: In Sec-
tion 6.1, we recall a concrete fuzzy key setting F
2
with which the linear sketch scheme S
Hash
is associ-
ated. Then in Section 6.2, we give the description of
S
Hash
. Finally, in Section 6.3, we show how secure
the linear sketch scheme S
Hash
is against recovering
attacks.
A large part of Sections 6.1 and 6.2 is taken ver-
batim from Sections 7.1 and 7.2 of (Takahashi et al.,
2017), respectively.
6.1 Specific Fuzzy Key Setting F
2
Here, we recall a concrete fuzzy key setting F
2
=
((d,X),t,X ,Φ,ε
e
) for which the linear sketch scheme
S
Hash
is constructed.
Metric space (d,X): The space X is defined by X :=
[0,1)
n
⊂ R
n
, where n ∈ N is a parameter spec-
ified by the context (e.g. an object from which
we measure fuzzy data) and a security parame-
ter k. The distance function d : X × X → R is
the L
∞
-distance. Namely, for x = (x
1
,...,x
n
) ∈ X
and x
0
= (x
0
1
,...,x
0
n
) ∈ X, we define d(x,x
0
) :=
kx − x
0
k
∞
:= max
i∈[n]
|x
i
− x
0
i
|. Note that X forms
an abelian group with respect to coordinate-wise
addition (modulo 1).
Threshold t: For a security parameter k, we require
the threshold t ∈ R to satisfy
k ≤ b−n log
2
(2t)c. (13)
For notational convenience, let T := 1/(2t).
Distribution X : An efficiently samplable distribu-
tion over a “discretized” version of X = [0,1)
n
.
That is, letting λ ∈ N denote the length of the sig-
nificand of a real number, if x = (x
1
,...,x
n
) is
sampled from X , then each x
i
is of the form
j
i
2
λ
,
where j
i
is some λ-bit integer. (See Section 2.2.)
We require T ≤ 2
λ
.
Furthermore, we require that X satisfy the as-
sumption on the average min-entropy that we state
later.
Error distribution Φ and Error parameter ε
e
: Φ
is any efficiently samplable distribution over X
such that FRR ≤ ε
e
for all x ∈ X.
The Requirement on the Distribution of Fuzzy
Data X . Let X
0
be the “scaled-up” version of X ,
namely, X
0
is the distribution obtained by multiply-
ing the value T = 1/(2t) to the outcome of the dis-
tribution X , where the rounding-down operation is
performed for each coordinate of X
0
as explained in
Section 2.2. Since X is a distribution over [0,1)
n
,
X
0
is a distribution over [0,T )
n
. Now, let us divide
X
0
into the “integer” part X
0
in
and the “decimal” part
X
0
de
. Namely, let x
0
= (x
0
1
,...,x
0
n
) be a vector pro-
duced from X
0
. Then, X
0
in
is the distribution of the
n-dimensional vector whose i-th element is the inte-
ger part of x
0
i
. Similarly, X
0
de
is the distribution of
the n-dimensional vector whose i-th element is the
decimal part of x
0
i
. Note that each coordinate of the
integer part X
0
in
is represented by dlog
2
T e bits, and
thus each coordinate of the decimal part X
0
de
will have
(λ − dlog
2
T e)-bit precision, so that the significand of
the entire x
0
i
is expressed in λ bits. Note also that the
joint distribution (X
0
in
,X
0
de
) contains the same infor-
mation as X
0
.
The requirement on the distribution X is that we
have
e
H
∞
(X
0
in
|X
0
de
) ≥ log
2
p + ω(log
2
k), (14)
where p is the order of the field over which the uni-
versal hash family H
lin
(guaranteed by Lemma 2) is
constructed.
6.2 Scheme Description
Let F
2
= ((d, X ),t,X , Φ, ε
e
) be the fuzzy key setting
as defined above. Let F
p
be a finite field with prime
order p satisfying p ≥ T = 1/(2t). Here, we iden-
tify F
p
with Z
p
, and interpret an element in the for-
mer set as an element in the latter set, and vice versa.
Let H
lin
= { h
z
: (F
p
)
n
→ F
p
}
z∈F
p
n
be the universal
hash function family with linearity as guaranteed by
Lemma 2. For each z ∈ F
p
n
and s ∈ F
p
, we define
SECRYPT 2018 - International Conference on Security and Cryptography
84

“h
−1
z
(s)” as the set of preimages of s under h
z
. That
is, h
−1
z
(s) := {a ∈ (F
p
)
n
|h
z
(a) = s}. Hence, the nota-
tion “a ←
R
h
−1
z
(s)” means that we choose a vector a
uniformly from the set h
−1
z
(s).
Then, using these ingredients, the linear sketch
scheme S
Hash
= (Setup, Sketch,DiffRec) for F
2
and
the additive group (Z
p
,+), is constructed as de-
scribed in Figure 3.
We remind the reader that we are treating real
numbers as explained in Section 2.2. We remark
that as in the first linear sketch scheme S
CRT
, the
rounding-down operation is applied after the multi-
plication T · x, so that the resulting real number in
each coordinate has a λ-bit significand. Concretely,
let s ∈ Z
p
, and let a = (a
1
,...,a
n
) ∈ h
−1
z
(s), and
suppose that c = (c
1
,...,c
n
) ∈ (R
p
)
n
is output from
Sketch(pp,s,x), where x = (x
1
,...,x
n
) ←
R
X and
thus each x
i
is of the form x
i
=
j
i
2
λ
for some λ-bit in-
teger j
i
. Then, for each i ∈ [n], x
0
i
= T · x
i
results in
b
T · j
i
2
dlog
2
T e
c · 2
−(λ−dlog
2
T e)
. Consequently, each c
i
∈ R
p
is of the following form:
c
i
= a
i
+
j
T · j
i
2
dlog
2
T e
k
· 2
−(λ−dlog
2
T e)
mod p. (15)
It was shown in (Takahashi et al., 2017) that S
Hash
satisfies correctness, and also satisfies the linearity
and weak simulatability properties.
6.3 Security against Recovering Attacks
In this subsection, we show how secure the linear
sketch scheme S
Hash
is against recovering attacks. To
this end, we first show that S
Hash
satisfies decompos-
ability with the partial hiding property.
Lemma 5. The linear sketch scheme S
Hash
satisfies
the decomposability and partial hiding property.
Proof of Lemma 5. Let s ∈ Z
p
and a = (a
1
,...,a
n
) ∈
h
−1
z
(s). Let c = (c
1
,...,c
n
) ∈ (R
p
)
n
be a sketch out-
put from Sketch(pp, s, x), where x = (x
1
,...,x
n
) ←
R
X and thus each x
i
is of the form x
i
=
j
i
2
λ
for some
λ-bit integer j
i
. As mentioned in the previous subsec-
tion, due to the rounding-down operation performed
at each multiplication T · x
i
, each coordinate c
i
of the
sketch c is computed as in Eq. (15). Here, we con-
sider the “integer” part c
(i)
in
and the “decimal” part c
(i)
de
of c
i
, which are as follows:
c
(i)
in
= bc
i
c = a
i
+
jj
T · j
i
2
dlog
2
T e
k
· 2
−`
0
k
mod p, (16)
c
(i)
de
= c
i
mod 1 =
j
T · j
i
2
dlog
2
T e
k
· 2
−`
0
mod 1. (17)
where `
0
= λ − dlog
2
T e. Note that c
(i)
in
∈ Z
p
and c
(i)
de
∈
[0,1). Note also that the only component that depends
on s is a, but due to “mod 1,” the decimal part c
(i)
de
becomes independent of it. Similarly to the first linear
sketch scheme S
CRT
, we can define the decomposed
functions f
1
(pp,s,x) and f
2
(pp,x) as follows:
f
1
(pp,s,x): This function is a probabilistic function,
which first picks a = (a
1
,...,a
n
) ∈ h
−1
z
(s) uni-
formly at random, and outputs c
1
= (c
(1)
in
,...,c
(n)
in
)
∈ (Z
p
)
n
, where each c
(i)
in
is computed as Eq. (16).
f
2
(pp,x): This function outputs c
2
= (c
(1)
de
,...,c
(n)
de
)
∈ [0, 1)
n
, where each c
(i)
de
is computed as Eq. (17).
Furthermore, it is not hard to see that f
1
satisfies
the partial hiding property. Specifically, recall that
given s ∈ Z
p
, Sketch chooses a = (a
1
,...,a
n
) ∈ (Z
p
)
n
uniformly at random from the set h
−1
(s). Due to
the linearity of the underlying universal hash family
H
lin
, if s ∈ Z
p
is also chosen uniformly at random,
a is distributed uniformly in (Z
p
)
n
. Hence, each a
i
acts as a key for one-time pad encryption, and thus
each c
(i)
in
∈ Z
p
does not contain any information of x
i
.
Therefore, when s ∈ Z
p
is chosen uniformly at ran-
dom, the output c
1
of f
1
(pp,s,x) becomes indepen-
dent of x. This completes the proof of Lemma 5.
We now show how secure the linear sketch scheme
S
Hash
is against recovering attacks.
Theorem 2. The linear sketch scheme S
Hash
satisfies
(p
−1
· k
−ω(1)
)-security against recovering attacks.
Proof of Theorem 2. Due to Lemmas 3 and 5, and
the fact that f
2
does not use a public parameter pp = z
and thus independent of P , we have
Adv
recover
S
CRT
(k) = 2
−
e
H
∞
(X |P , f
2
(P ,X ))
= 2
−
e
H
∞
(X | f
2
(P ,X ))
.
Moreover, it is straightforward to see that the dis-
tribution f
2
(P , X ) is exactly the distribution X
0
de
in-
troduced in Section 6.1, namely, the distribution
of the vector of the “decimal”-part of the scaled-
up version X
0
of X . Note also that given X
0
de
,
guessing the original distribution X is a harder
task than guessing the “integer”-part X
0
in
. Hence,
we have
e
H
∞
(X | f
2
(P , X )) ≥
e
H
∞
(X
0
in
|X
0
de
) ≥ log
2
p +
ω(log
2
k). Due to Eq. (14), we can estimate
Adv
recover
S
Hash
(k) as follows:
Adv
recover
S
Hash
(k) = 2
−
e
H
∞
(X | f
2
(P ,X ))
≤ 2
−
e
H
∞
(X
0
in
|X
0
de
)
≤ 2
−(log
2
p+ω(log
2
k))
= p
−1
· k
−ω(1)
.
Hence, S
Hash
satisfies (p
−1
· k
−ω(1)
)-security against
recovering attacks. This completes the proof of The-
orem 2.
On the Security of Linear Sketch Schemes against Recovering Attacks
85
Setup(1
k
) :
z ←
R
F
p
n
Return pp ← z.
Sketch(pp,s ∈ Z
p
,x ∈ [0, 1)
n
) :
a ←
R
h
−1
z
(s)
c ← a + T · x
Return c.
DiffRec(pp,c,c
0
) :
∆c ← c
0
− c
∆s ← h
z
(b∆ce)
Return ∆s.
Figure 3: The linear sketch scheme S
Hash
= (Setup,Sketch,DiffRec) for the fuzzy key setting F
2
. In the figure, the addi-
tions/subtractions are done in (R
p
)
n
.
REFERENCES
Cheraghchi, M. (2011). Capacity achieving codes from
randomness condensers. http://arxiv.org/pdf/0901.
1866v2. pdf. Preliminary version appeared in ISIT
2009.
Dodis, Y., Ostrovsky, R., Reyzin, L., and Smith, A. (2008).
Fuzzy extractors: How to generate strong keys from
biometrics and other noisy data. SIAM J. Comput.,
38(1):97–139.
Goldwasser, S., Micali, S., and Rivest, R. (1988). A digi-
tal signature schemes secure against adaptive chosen-
message attacks. SIAM J. Computing, 17(2):281–308.
Matsuda, T., Takahashi, K., Murakami, T., and Hanaoka, G.
(2016). Fuzzy signatures: Relaxing requirements and
a new construction. In Proc. of ACNS 2016, volume
9696 of LNCS, pages 97–116. Springer.
Schnorr, C. (1990). Efficient signature generation for smart
cards. In Proc. of CRYPTO 1989, volume 435 of
LNCS, pages 239–252. Springer.
Takahashi, K., Matsuda, T., Murakami, T., Hanaoka, G.,
and Nishigaki, M. (2015). A signature scheme with
a fuzzy private key. In Proc. of ACNS 2015, volume
9092 of LNCS, pages 105–126. Springer.
Takahashi, K., Matsuda, T., Murakami, T., Hanaoka, G.,
and Nishigaki, M. (2017). Signature schemes with a
fuzzy private key. IACR Cryptology ePrint Archive:
Report 2017/1188. https://eprint.iacr.org/2017/1188.
This is the merged full version of (Takahashi et al.,
2015) and (Matsuda et al., 2016).
Waters, B. (2005). Efficient identity-based encryption with-
out random oracles. In Proc. of EUROCRYPT 2005,
volume 3494 of LNCS, pages 114–127. Springer.
Yasuda, M., Shimoyama, T., Takenaka, M., Abe, N., Ya-
mada, S., and Yamaguchi, J. (2017). Recovering at-
tacks against linear sketch in fuzzy signature schemes
of ACNS 2015 and 2016. In Proc. of ISPEC 2017,
volume 10701 of LNCS, pages 409–421. Springer.
APPENDIX
Here, we provide a minimal definition of a fuzzy sig-
nature scheme. Then, in order to grasp how the linear
sketch schemes S
CRT
and S
Hash
are used to construct
fuzzy signature schemes, we briefly review the first
and second fuzzy signature schemes in (Takahashi
et al., 2017).
Syntax. A fuzzy signature scheme Σ
FS
for a fuzzy
key setting F = ((d,X),t,X ,Φ,ε) consists of the four
algorithms (Setup
FS
,KG
FS
,Sign
FS
,Ver
FS
):
Setup
FS
: This is the setup algorithm that takes 1
k
as
input (where k determines the threshold value t of
F ), and outputs a public parameter pp.
KG
FS
: This is the key generation algorithm that takes
pp and a fuzzy data x ∈ X as input, and outputs a
verification key vk.
Sign
FS
: This is the signing algorithm that takes pp, a
fuzzy data x
0
∈ X, and a message m as input, and
outputs a signature σ.
Ver
FS
: This is the (deterministic) verification algo-
rithm that takes pp, vk, m, and σ as input, and
outputs either > (“accept”) or ⊥ (“reject”).
Let δ = δ(k) ∈ [0,1]. A fuzzy signature scheme
Σ
FS
for a fuzzy key setting F = (d,X),t,X ,Φ,ε
e
) sat-
isfies δ-correctness if it holds that
Pr
h
pp ←
R
Setup
FS
(1
k
); x ←
R
X ;
vk ←
R
KG
FS
(pp,x); e ←
R
Φ;
σ ←
R
Sign
FS
(pp,x + e,m) :
Ver
FS
(pp,vk,m,σ) = >
i
≥ 1 − δ
for all k ∈ N and all messages m.
In (Takahashi et al., 2017), as a security require-
ment for a fuzzy signature scheme, an analogue of
the standard existential unforgeability against cho-
sen message attacks (EUF-CMA security) (Goldwasser
et al., 1988) was defined. We omit the formal defini-
tion since we do not directly deal with it in this paper.
First Scheme Σ
FS1
. This scheme is constructed for
the specific fuzzy key setting F
1
, from the combina-
tion of the linear sketch scheme S
CRT
and a variant of
the Waters scheme (Waters, 2005) (called the mod-
ified Waters signature (MWS) scheme in (Takahashi
et al., 2017)). (For the fuzzy key setting F
1
and the
linear sketch scheme S
CRT
, see Sections 5.1 and 5.3,
respectively.)
Let ` = `(k) be a positive polynomial that denotes
the length of messages. Let F
1
= ((d,X ),t,X , Φ, ε
e
)
be the fuzzy key setting defined in Section 5.1, where
SECRYPT 2018 - International Conference on Security and Cryptography
86

Setup
FS1
(1
k
) :
g,h, u
0
,u
1
,...,u
`
←
R
G
Let z be an element of Z
∗
p
of order W .
Return pp ← (g,h,u
0
,(u
i
)
i∈[`]
,z).
KG
FS1
(pp,x) :
sk ←
R
Z
W
; vk ← g
z
sk
c ← (CRT
−1
w
(sk) + E
w
(x)) mod w
Return V K ← (vk, c).
Sign
FS1
(pp,x
0
,m) :
Parse m as (m
1
k...km
`
) ∈ {0, 1}
`
.
e
sk ←
R
Z
W
;
e
vk ← g
z
e
sk
; r ←
R
Z
p
;
e
σ
2
← g
r
e
σ
1
← h
z
e
sk
· (u
0
·
∏
i∈[`]
u
m
i
i
)
r
e
c ← (CRT
−1
w
(
e
sk) + E
w
(x
0
)) mod w
Return σ ← (
e
vk,
e
σ
1
,
e
σ
2
,
e
c).
Ver
FS1
(pp,VK, m, σ) :
(vk, c) ← V K; (
e
vk,
e
σ
1
,
e
σ
2
,
e
c) ← σ
Parse m as (m
1
k...km
`
) ∈ {0, 1}
`
.
If e(
e
σ
2
,u
0
·
∏
i∈[`]
u
m
i
i
) · e(
e
vk, h)
6= e(
e
σ
1
,g) then return ⊥.
∆s ← C
w
(
e
c − c); ∆sk ← CRT
w
(∆s)
If (vk)
z
∆sk
=
e
vk then return > else return ⊥.
Setup
FS2
(1
k
) :
g ←
R
G; z ←
R
F
p
n
Let H : {0,1}
∗
→ Z
p
be a cryptographic hash function.
Return pp ← (g,z,H).
KG
FS2
(pp,x) :
sk ←
R
Z
p
; vk ← g
sk
a ←
R
h
−1
z
(sk); c ← a + T · x
Return V K ← (vk, c).
Sign
FS2
(pp,x
0
,m) :
e
sk ←
R
Z
p
;
e
vk ← g
e
sk
; r ←
R
Z
p
; R ← g
r
e
h ← H(Rkm);
e
s ← r + (
e
sk) ·
e
h mod p
a
0
←
R
h
−1
z
(
e
sk);
e
c ← a
0
+ T · x
0
Return σ ← (
e
vk,
e
h,
e
s,
e
c).
Ver
FS2
(pp,VK, m, σ) :
(vk, c) ← V K; (
e
vk,
e
h,
e
s,
e
c) ← σ
R ← g
e
s
· (
e
vk)
−
e
h
If H(Rkm) 6=
e
h then return ⊥.
∆c ←
e
c − c; ∆sk ← h
s
(b∆ce)
If vk · g
∆sk
=
e
vk then return > else return ⊥.
Figure 4: (Left) The description of the fuzzy signature scheme Σ
FS1
= (Setup
FS1
,KG
FS1
,Sign
FS1
,Ver
FS1
), and (Right) the
description of the fuzzy signature scheme Σ
FS2
= (Setup
FS2
,KG
FS2
,Sign
FS2
,Ver
FS2
). In both of the descriptions, the steps
related to the underlying linear sketch schemes are highlighted with the box .
t (and n) are determined according to the security pa-
rameter k. let w = (w
1
,...,w
n
) = WGen(t,n), where
n is the dimension of X, and let W =
∏
i∈[n]
w
i
. Let
CRT
w
, CRT
−1
w
, E
w
, and C
w
be the functions de-
fined in Section 5.2. Let (G,G
T
,e, p) be a descrip-
tion of symmetric bilinear groups with prime order
p = Ω(2
k
) such that W |p − 1, where G and G
T
are
groups of prime order p and e : G × G → G
T
is an
efficiently computable bilinear map.
4
Then, using these ingredients, the fuzzy signature
scheme Σ
FS1
= (Setup
FS1
,KG
FS1
,Sign
FS1
,Ver
FS1
)
for the fuzzy key setting F
1
is constructed as in Fig-
ure 4 (left).
It was shown in (Takahashi et al., 2017) that this
fuzzy signature scheme satisfies ε
e
-correctness, and is
secure if the computational Diffie-Hellman assump-
tion holds in G.
Second Scheme Σ
FS2
. This scheme is constructed
for the specific fuzzy key setting F
2
, from the com-
bination of the linear sketch scheme S
Hash
and the
Schnorr signature scheme (Schnorr, 1990). (For the
4
For all generators g ∈ G and a, b ∈ Z
p
, it holds that
e(g
a
,g
b
) = e(g,g)
ab
∈ G
T
.
fuzzy key setting F
2
and the linear sketch scheme
S
Hash
, see Sections 6.1 and 6.2, respectively.)
Let F
2
= ((d,X),t,X ,Φ,ε
e
) be the fuzzy key set-
ting that we specified in Section 6.1, and suppose
the dimension of the fuzzy data space is n. Let
(G, p) be the description of a group G of prime or-
der p = Ω(2
k
). Let H
lin
= {h
z
: (F
p
)
n
→ F
p
}
z∈F
p
n
be the universal hash family with linearity as guar-
anteed by Lemma 2. (We identify F
p
with Z
p
.) Let
H : {0, 1}
∗
→ Z
p
be a cryptographic hash function
(modeled as a random oracle).
Using these building blocks, the second fuzzy
signature scheme Σ
FS2
= (Setup
FS2
,KG
FS2
,Sign
FS2
,
Ver
FS2
) for the fuzzy key setting F
2
is constructed as
in Figure 4 (right).
It was shown in (Takahashi et al., 2017) that this
fuzzy signature scheme satisfies ε
e
-correctness, and is
secure in the random oracle model (where H is mod-
eled as a random oracle) if the discrete logarithm as-
sumption holds in G.
On the Security of Linear Sketch Schemes against Recovering Attacks
87
