
Evaluating Security, Privacy and Usability Features of QR Code Readers
Heider A. M. Wahsheh and Flaminia L. Luccio
University Ca’ Foscari, Venice, Italy
Keywords:
QR Codes, Barcode Scanners, Android Security, QR Code Security, QR Code Privacy.
Abstract:
The widespread of smartphones with advanced capabilities has motivated developers to design new mobile
applications that are used as barcode scanners. Although several barcode readers are available, they still have
security and privacy limitations. In this paper, we first present a comprehensive and systematic review of bar-
code reader applications by analyzing their security, privacy and usability features. We categorize these apps
into four groups depending on their properties: URLs security, Crypto-based security, Popular applications,
and Save-privacy. We also highlight their weaknesses and present design recommendations for usable, secure
and privacy-guaranteed scanner applications. Based on our recommendations, we have developed BarSec
Driod a proof-of-concept secure barcode reader Android app that exploits some features of other applications
and at the same time overcomes their limitations. We have performed a user usability and security survey, on
BarSec Driod and two other popular QR code readers, KasperSky and QR Droid Private. The results show that
BarSec Driod is easy to use, satisfies the expectations of the users and is secure. Moreover, we have observed
that following the design tips, user’s security awareness and usability increase.
1 INTRODUCTION
Barcodes are low cost and easy-to-process data hold-
ers that in the last decades have become very popular
and widely used. Barcodes can hold products’ iden-
tification numbers, contact information, Uniform Re-
source Locators (URLs) and maps’ coordinates (Fo-
cardi et al., 2018b). A barcode scanner is an opti-
cal machine that has imaging and processing capabil-
ities (camera and processor), and is used to extract
data from a barcode image (Denso Wave, 2017). The
widespread of smartphone devices with high resolu-
tion cameras has motivated developers to create mo-
bile applications that can decode barcode images, and
can provide additional features such as: sharing con-
tacts, messages and URLs. Quick Response (QR)
codes are the most popular barcode types, with the
highest data capacity.
Barcodes can represent a source of attacks that in-
fect scanner devices with viruses and malware. At-
tackers may trigger vulnerabilities in the scanner’s
software, which can result in taking full control of the
user’s device and resources. These applications can
violate users’ privacy by accessing their private infor-
mation (Focardi et al., 2018b).
Multiple studies were dedicated to address QR
codes threats and solutions, while the practical side
needs more analysis (Focardi et al., 2018b; Yao and
Shin, 2013). Hundreds of barcode scanners are avail-
able for smartphone devices, some of them claim
of being ”secure” or ”privacy friendly” (Dudheria,
2017; Google Inc, 2018). These applications need
to be investigated and evaluated from security, us-
ability and privacy perspectives. In this study, we
present a comprehensive review of barcode scanner
applications. We analyze the features of barcode
readers, classify them into groups and highlight their
limitations. Then, we present a set of design tips
and recommendations for usable, secure and privacy-
guaranteed reader application. Based on our rec-
ommendations, we have implemented BarSec Driod,
a proof-of-concept Android application that exploits
some features of other applications and at the same
time overcomes their limitations. We have performed
a user usability and security survey on BarSec Driod
and two other popular QR code readers: Kasper-
Sky and QR Droid Private (KasperSky Lab, 2018;
DroidLa, 2016). Our results show that following the
design tips user’s security awareness and usability in-
crease.
Paper Structure: The rest of this study is organized
as follows: Section 2 presents a brief summary of
the related work. Section 3 explores QR code reader
applications and classifies them based on their fea-
tures. In Section 4 we present our design tips and rec-
ommendations for secure, usable and privacy-friendly
266
Wahsheh, H. and Luccio, F.
Evaluating Security, Privacy and Usability Features of QR Code Readers.
DOI: 10.5220/0007346202660273
In Proceedings of the 5th International Conference on Information Systems Security and Privacy (ICISSP 2019), pages 266-273
ISBN: 978-989-758-359-9
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

QR code readers, then we present BarSec Driod, our
recommended reader application. Section 5 explores
the users’ experiment and results of usability and se-
curity. Finally, in Section 6 we present the conclusion
and future work.
2 RELATED WORK
In this section we recall the studies that evaluate some
of the available QR code readers. However, w.r.t. our
work, these studies take into consideration a limited
number of applications (we have checked 28 of them),
and none of them focuses on all the possible features,
i.e., security, privacy and usability.
The study of (Dudheria, 2017) explores the avail-
able Android secure QR code readers, highlights their
security properties and evaluates their capabilities in
detecting malicious QR codes. According to the con-
ducted analysis, many QR code readers claim to be
secure scanners, however, they do not provide the ba-
sic security aspects and require enhancements. The
study addresses the potential weaknesses and limi-
tations of secure scanners applications, and provides
recommendations to improve the security level. How-
ever, this analysis does not take into consideration the
usability of barcode scanners.
The study of (Yao and Shin, 2013) explores the
security capabilities for the 31 most popular QR code
Android readers. Only 2 out of 31 applications have
security warning capabilities, but extended experi-
ments show that the threat detection mechanisms for
phishing and malware attacks are very weak. Thus,
the researchers propose a new QR code reader called
SafeQR, which depends on two existing security
APIs: Google safe browsing and phishtank (Google,
site; Phishtank, site). However, the authors do not
give any empirical evidence that the scanner is able
to enhance the detection rates of malicious URLs.
Moreover, the study does not take into consideration
QR codes’ offline threats such as SQL and command
injections, privacy and usability features.
In (Krombholz et al., 2015) the authors present a
comprehensive analysis of QR code security and pri-
vacy issues. The obtained results show that most of
reader applications cannot detect malicious URLs. In
addition, these applications violate the users’ privacy,
by getting extra permissions and accessing users’ per-
sonal information. The study presents design recom-
mendations for usable and secure reader applications,
and proposes a prototype that employs Base64 digital
signatures and URL checking. Results show that fol-
lowing the design recommendations can effectively
protect users from malicious QR codes. However, the
study is limited to 12 applications and it neither dis-
cusses the size and time overhead of applying digital
signature protection, nor the implemented algorithms.
3 QR CODE READERS
Our analysis includes 28 reader applications that are
popular or claim to provide security and privacy fea-
tures.
Table 1 shows the details of the tested applica-
tions, such as: app developer, current version, num-
ber of installs from Google Play (Google Inc, 2018),
category, rate (a 5 point scale users’ evaluation of an
application from Google Play), 1D/2D (ability of the
reader to read general one dimensional (1D)/ two di-
mensional (2D) barcodes or only QR codes), and for-
mat (the reader displays the barcode type it has iden-
tified, e.g., QR code, etc.).
3.1 URLs Security Applications
Online protection includes checking URLs that are
encoded inside QR codes, which can be used to
launch phishing, malware and XSS attacks. The pro-
tection technique is simple and aims at alerting users
about malicious links.
G Data QR code scanner (G Data Software AG,
2018) is a simple, free Android application, designed
for QR code protection. This app checks the encoded
URLs, in order to detect phishing and malicious links,
it retrieves the full destination web address, even if it
was embedded as a shortened URL (Dudheria, 2017).
KasperSky QR Scanner is a free app that validates
the QR code links against malware and phishing Web
pages (KasperSky Lab, 2018). The main limitation
of KasperSky QR Scanner is that it opens URLs, de-
tected as safe, directly in the browser without asking
for user confirmation (Dudheria, 2017).
The Norton Snap QR code scanner (Norton-
Mobile, 2016) alerts users against unsafe/untrusted
URLs, shows the full expansion of the website ad-
dress and blocks the malicious online content before
being loaded on the user’s browser.
Barcode Reader for CM browser (Browser Exten-
sion, 2018) is a lightweight QR code scanner that re-
quires CM browser and automatically opens URLs.
The CM browser performs the security protection that
includes: Advertising blocker, malicious Web pages
checking and download protection.
TeaCapps (TeaCapps, 2018) barcode scanner of-
fers URL checking by using Chrome Custom Tabs,
which employs Google Safe Browsing technology
Evaluating Security, Privacy and Usability Features of QR Code Readers
267
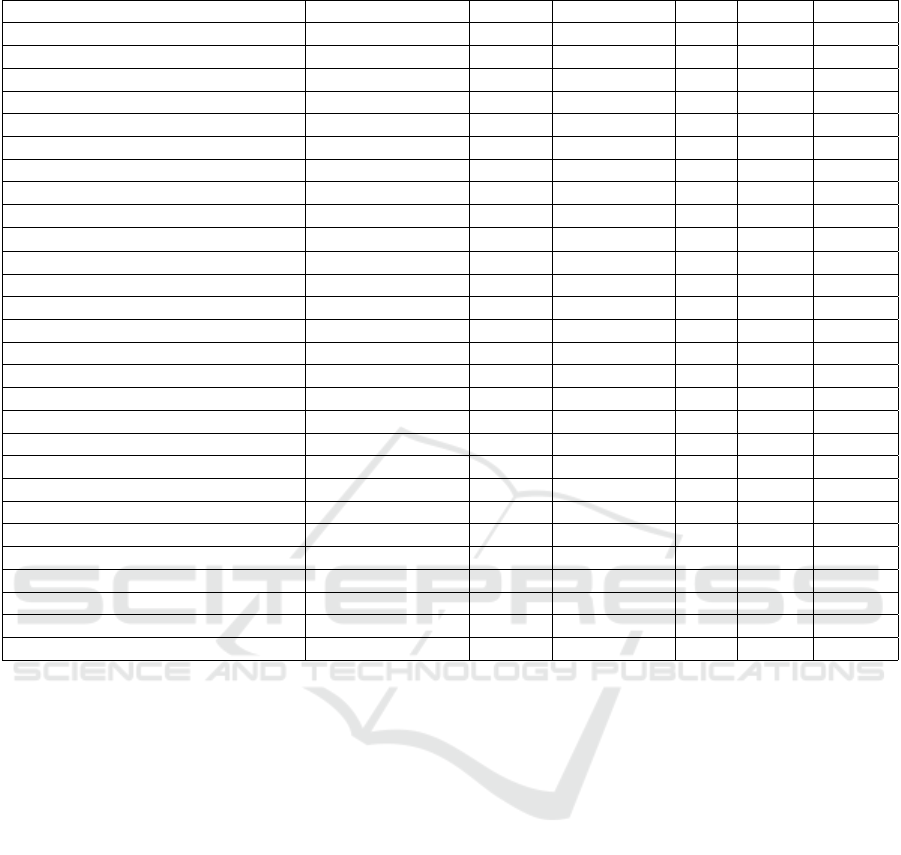
Table 1: Details of tested QR Code readers.
App Developer Version Installs Category Rate 1D/2D Format
(G Data Software AG, 2018) 1.0.2.0643c6ef 10K+ URLs 3.3 QR
(KasperSky Lab, 2018) 1.2.4.51 1M+ URLs 4.4 QR
(NortonMobile, 2016) 2.0.0.71 1M+ URLs 4.2 3
(Trend Micro, 2018) 1.0.0 10K+ URLs 4.8 3
(FANSec Lab Apps, 2018) 1.1 10+ URLs 5 3
(Madiff Net, 2017) 1.2 100+ Crypto 5 3
(Dennings, 2018) 1.0.17 1K+ URLs 4.1 3
a
(KidControl Dev, 2018) 1.0 5K+ URLs 4.4 3 3
(DroidLa, 2016) 7.0.4 50M+ Crypto 4.2 3
(Tengler, D., 2018) Free
b
100+ Crypto 5 QR
(Avira, 2018) 2.5.0 100K+ URLs 4.3 3 3
(Browser Extension, 2018) 1.0.0 100K+ URLs 4.3 QR
(SECUSO Research Group, 2016) 1.6.1 10K+ Save-Privacy 4.4 3 3
(X and C Hi-Tech Inc, 2016) 2.4.3 500+ URLs 4.1 3
(iTechSol, 2018) 1.1 5+ URLs 3
(Red Dodo, 2014) 1.03 500K+ Save-Privacy 3.8 3 3
(Tokoware, 2016) 1.1.7 5K+ Save-Privacy 4.2 3
(FancyApp, 2018) 2.1.6 5M+ Save-Privacy 4.5 3
(TeaCapps, 2018) 1.3.1-L 1M+ URLs 4.6 3 3
(Ecrubit Consultancy Service, 2018) 1.0.2 1+ Crypto 3
(Application4u, 2018) 1.7.6 10M+ Save-Privacy 4.7 3
(Scan, 2016) 2.33 50M+ Save-Privacy 4 3
(ZXing Team, 2017) Varies with device 100M+ Popular 4.1 3 3
(Geeks.Lab.2015, 2018) 1.2.91 10M+ Popular 4.6 3 3
(Gamma Play, 2018) Varies with device 50M+ Popular 4.4 3
(Barcode Scanner, 2018) 1.25 5M+ Popular 4.4 3 3
(EZ to Use, 2018) 0.92 10M+ Popular 4.6 3
(I-Plex Technology, 2018) 1.0.5 1K+ Crypto 5 3
a
Always display QR code;
b
Free version to test functionality.
(Google, site). Table 2 presents a comparison of bar-
code scanners that provide security by checking QR
codes’ online contents (URLs).
The main limitation of these apps is that URL-
checking readers can protect users from malicious
URLs only, while other offline attacks such as SQL
and command injections can still be performed with-
out detection. In addition, these applications require
Internet connection to check URLs. Note that in this
work, we evaluate the applications’ features, not the
database/model that checks the URL (e.g., Google
Safe Browsing, etc.).
3.2 Crypto-based Security Applications
Cryptographic techniques can be used to encrypt,
sign and control the access to QR code contents.
Choosing the suitable algorithm, key size and struc-
ture are discussed in multiple studies (European
Union Agency for Network and Information Security
(ENISA), 2014; Focardi et al., 2018a), but the key
factor on barcode usability is the size overhead (Fo-
cardi et al., 2018b). However, there are few applica-
tions that offer generating and reading cryptographic
QR codes.
Madiff Net (Madiff Net, 2017) scanner applica-
tion offers reading and creating password-protected
QR codes, and the contents are encrypted using a
shared password-based key between the generator and
the barcode reader. The application is free, contains
advertisements and available with three languages:
English, Vietnamese and Chinese. As a limitation,
we highlight that being the algorithm unavailable we
cannot evaluate its strength.
QR Droid Private (DroidLa, 2016) is a full-
featured and multi-language application, which offers
reading and creating QR codes. The application sup-
ports URL shortening, QR code sharing and contents
encryption. QR Droid is well adopted and available
in 29 languages. The app employs the Data Encryp-
tion Standard (DES) algorithm with 56 bits key length
which is considered weak and breakable.
Crypto Message (Tengler, D., 2018) is a secu-
rity application that offers encrypting any type of
ICISSP 2019 - 5th International Conference on Information Systems Security and Privacy
268
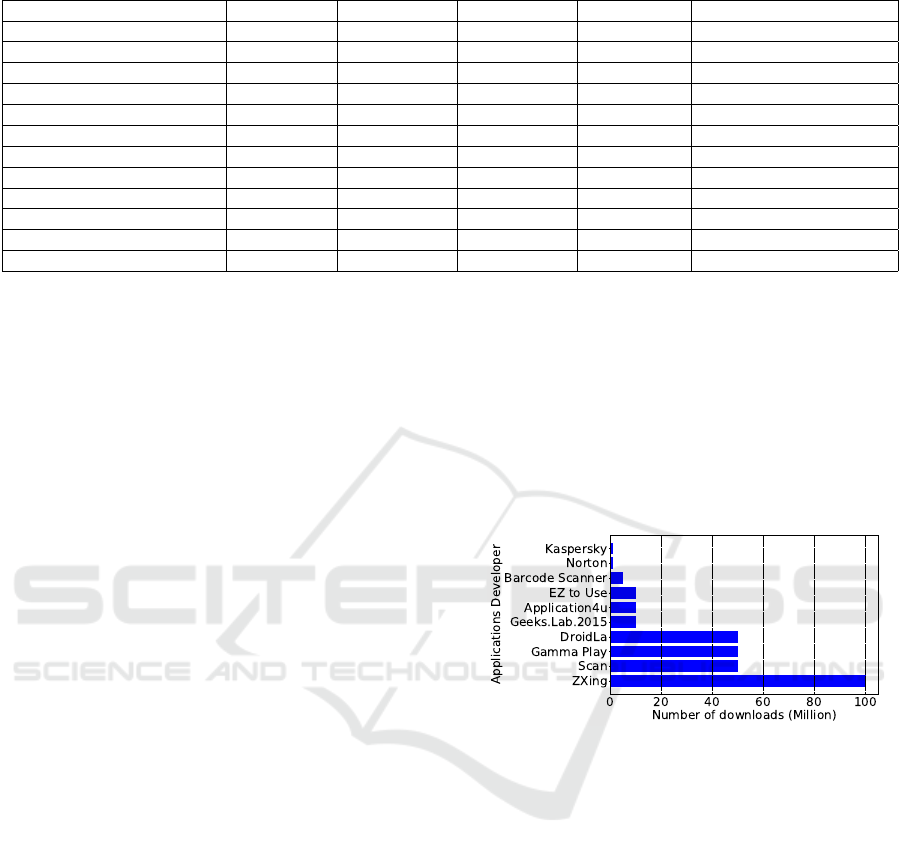
Table 2: Barcode scanners that check URLs contained inside QR codes.
App Developer Check URL Display URL Get full URL Direct Open URL checking technique
(G Data Software AG, 2018) 3 3 3 N/A
(KasperSky Lab, 2018) 3 3
a
KasperSky Virusdesk
(NortonMobile, 2016) 3 3 3 3
a
Norton Safe Web
(Trend Micro, 2018) 3 3 N/A
(FANSec Lab Apps, 2018) 3 3 N/A
(Dennings, 2018) 3 3 Google Safe Browsing
(KidControl Dev, 2018) 3 3 N/A
(Avira, 2018) 3 3 N/A
(Browser Extension, 2018) 3 3 CM browser
(TeaCapps, 2018) 3 3 Google Safe Browsing
(iTechSol, 2018) 3 3 N/A
(X and C Hi-Tech Inc, 2016) 3 3
a
N/A
a
Open URL directly if it is safe.
text message, and allows encoding ciphertexts in QR
codes. Advanced Encryption Standard (AES) is avail-
able with four modes: Electronic Codebook (ECB),
Cipher Block Chaining (CBC), Counter (CTR), and
Output Feedback (OFB) modes. Note that, the em-
bedded scanner cannot decode ordinary QR codes
(generated by other applications). Crypto Message
usage is non-straightforward and assumes the knowl-
edge of some basic cryptographic concepts.
EC QR (Ecrubit Consultancy Service, 2018) is a
QR code reader and generator application. The en-
cryption algorithm, the key size and the structure of
this app are not available and cannot be evaluated.
Observe that, all the above mentioned applications
have some limitations: 1) They assume no standard
way of encoding cryptographic data in QR codes, i.e.,
each application uses its own structure. Thus, in order
to decode a crypto-barcode, the user will need to use
the same generating application, while, on the other
hand, the study of (Focardi et al., 2018b) proposes
the use of the standard JavaScript Object Notation
(JSON) as a general structure to be used with crypto-
QR codes. 2) All these applications adopt weak cryp-
tographic mechanisms such as: DES and AES-ECB.
3) These applications employ base64 and hexadeci-
mal strings to represent ciphertexts, which leads to
size overhead.
The password-protected QR codes achieve con-
fidentiality and access control, and only authorized
users (who have the password) can retrieve the en-
coded data. However, encrypting the contents is not
enough to protect users who scan the QR code, since
even encrypted data may contain malicious links or
offline attacks. Generator authentication, data in-
tegrity and non-repudiation can be useful in protect-
ing the users, and can be achieved using digital sig-
natures (Focardi et al., 2018b). Table 3 presents a
summary of crypto-based QR code scanners and it
includes the app developer, encryption, digital signa-
ture (DS), algorithm (Alg), Key length (KL), encod-
ing scheme (EncS) and structure (Str).
3.3 Popular Applications
In this section we present popular QR code reader ap-
plications that have been downloaded by more than 1
million users (see Figure 1).
Figure 1: Popular QR code scanners.
ZXing Barcode Scanner (ZXing Team, 2017) is
one of the most popular applications, with more than
100 million downloads. It is compatible with vari-
ous 1D and 2D barcodes, displays the barcode type
and retrieves additional information about URLs such
as title and redirections. The ZXing library (GitHub,
2018) is a core Java source for multiple popular ap-
plications such as Barcode Scanner Pro (10M down-
loads) (Geeks.Lab.2015, 2018), and Barcode Scanner
(Barcode Scanner, 2018) (5M downloads).
QR & Barcode Scanner by (Gamma Play, 2018)
which recorded more than 50M downloads, and the
free QR Scanners Bar Code Scanner & QR Code
Reader (EZ to Use, 2018) recorded more than 10M
downloads.
Figure 1 shows the tested applications that have
more than one million downloads. Note that, being
popular is not enough to be usable and secure, so we
have investigated these applications also from privacy
perspective.
Evaluating Security, Privacy and Usability Features of QR Code Readers
269

Table 3: Crypto-based QR code scanners.
App Developer Encryption DS Alg KL (bits) EncS Str
(Madiff Net, 2017) 3 N/A 48 Base64 N/A
(DroidLa, 2016) 3 DES 56 Base64 Keyword
(Tengler, D., 2018) 3 AES 128,192 & 256 Base64 & hex N/A
(I-Plex Technology, 2018) 3 N/A N/A Base64 N/A
(Ecrubit Consultancy Service, 2018) 3 N/A N/A Base64 N/A
3.4 Save-privacy Applications
The applications we will illustrate in this section
claim to protect the users’ privacy, as they do not
require access to personal information details. Ob-
taining permissions enables direct access to the infor-
mation without users’ interaction, which means easier
and faster tasks. On the other hand, some applications
may exploit these permissions and send user’s private
data to a third party (Krombholz et al., 2015).
A privacy-violating QR code scanner may ac-
cess private images, videos, contacts, call history and
user’s location. Therefore, we need to balance the
ease-of-use (getting the permissions) and protecting
the users’ privacy. Usually, minimal permissions in-
clude accessing the camera (to scan the barcode) and
the network (if there is a need to check URLs). Ob-
taining other permissions can be extremely danger-
ous, and may result in information leakage attacks.
Red Dodo (Red Dodo, 2014) description says it
does not require personal information details, by ex-
ploring the app’s permissions list we have discovered
that it has access to the storage, photos, Wi-Fi details,
media and files.
Similarly, the QR Code Reader Extreme (Fan-
cyApp, 2018) claims to require few permissions,
whereas by inspecting the app’s permissions list we
have found out that it has access to photos, media,
files, storage network and camera.
Some applications offer QR code’s online con-
tents check (URLs), alongside with less permissions.
An example is TeaCapps Scanner (TeaCapps, 2018),
which requires camera and Internet permissions but
not access to storage or files.
On the good side, Tokoware (Tokoware, 2016) a
simple 1D and 2D barcode reader application, devel-
oped based on the ZXing (GitHub, 2018) library, and
Lightning QR code Scanner (Application4u, 2018),
require access to the camera and network, while
QR Scanner (Privacy Friendly) (SECUSO Research
Group, 2016) only requires access to the camera.
Thus, all these applications are suitable for users who
aim at protecting their privacy.
Since users’ privacy is important, we have eval-
uated all the 28 tested barcode reader applications
in terms of granted permissions. Table 4 shows
the requested permissions for all our tested applica-
tions (i.e., Device & app history, Contacts, Location,
Phone, Photos/media/files, Storage, Camera, Wi-Fi
info, Device ID, Network).
4 DESIGN RECOMMENDATION
Based on our analysis for the available barcode read-
ers, and based on suggestions provided in other works
(Focardi et al., 2018b; Reeder et al., 2018) we present
design tips for secure, usable, and privacy friendly
barcode reader applications. The recommended de-
sign supports the reading of different barcode types,
so to be used it in various contexts and prevents the
execution of any encoded codes or commands. It
is important to display the barcode type, in order to
avoid wrong barcode type decoding. We should pro-
vide manuals for users to learn how to use secure
reader applications. From the security side, we have
to check any URL to avoid phishing and malware at-
tacks, and use security warnings such as: browser
warning against malicious URLs. Digital signature
services can authenticate the barcode generator and
guarantee data integrity, while encrypted contents can
achieve confidentiality and access control.
Saving the users privacy is recommended by re-
questing minimum set of permissions to prevent ac-
cessing private files. The recommended permissions
are camera (to scan the image) and Internet (to check
URLs) only. Regarding usability, we recommend pro-
viding default basic functionalities with simple inter-
face, so that non-expert users can use the app easily.
Based on these recommendations, we have imple-
mented BarSec Driod (Heider Wahsheh, 2018), an
Android mobile application that employs the ZXing
library (GitHub, 2018), and follows our design tips
to provide a secure barcode scanning service. The
application design followed the JSON structure pro-
posed by (Focardi et al., 2018b), and employed Java
standard security libraries to implement the crypto-
graphic primitives. The algorithms and key lengths
were adopted based on (Focardi et al., 2018a). Bar-
Sec Driod specifications are included in Table 5.
ICISSP 2019 - 5th International Conference on Information Systems Security and Privacy
270
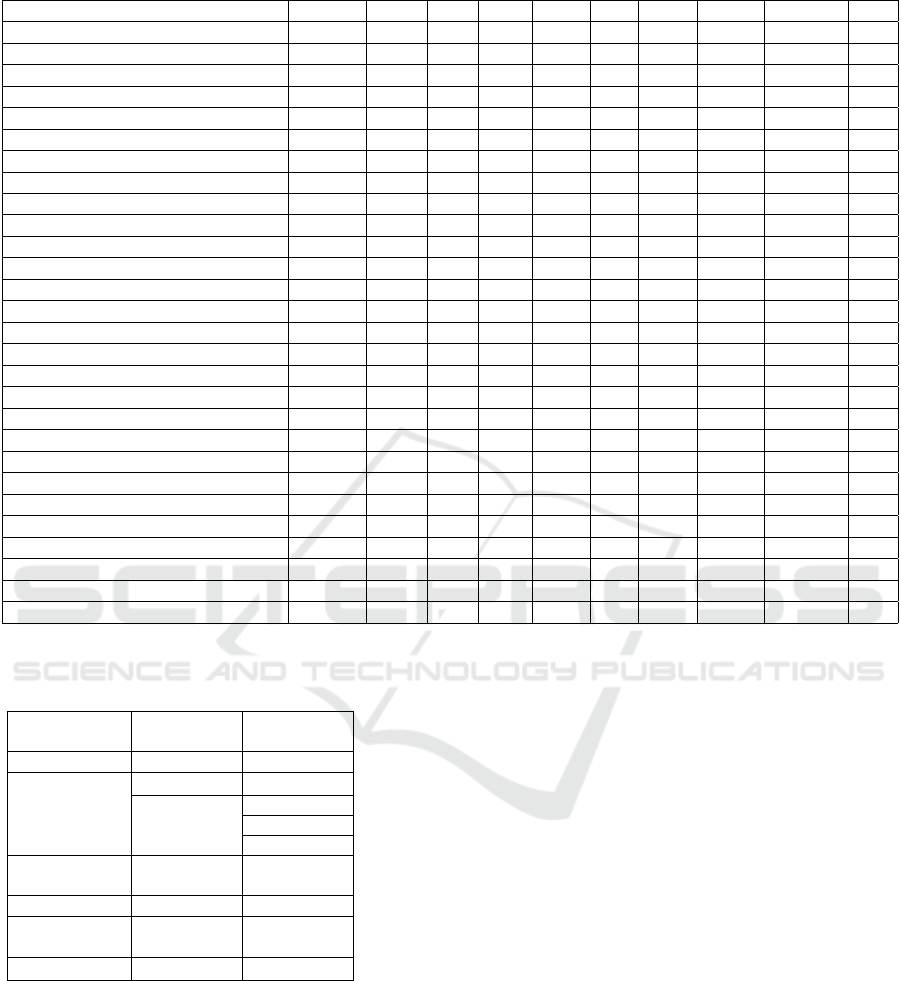
Table 4: Permissions of tested QR Code readers.
App Developer DevHis Cont Loc Phn Files Stg Cam Wi-Fi DevInfo Net
(G Data Software AG, 2018) 3 3 3 3 3 3
(KasperSky Lab, 2018) 3 3 3 3 3 3 3
(NortonMobile, 2016) 3 3 3 3 3 3
(Trend Micro, 2018) 3 3 3 3 3 3
(FANSec Lab Apps, 2018) 3 3 3 3 3 3 3 3
(Madiff Net, 2017) 3 3 3 3 3 3 3 3 3
(Dennings, 2018) 3 3 3 3 3 3
(KidControl Dev, 2018) 3 3 3 3
(DroidLa, 2016) 3 3 3 3
(Tengler, D., 2018) 3 3 3 3 3
(Avira, 2018) 3 3 3 3 3 3 3
(Browser Extension, 2018) 3 3 3 3 3
(SECUSO Research Group, 2016) 3
(X and C Hi-Tech Inc, 2016) 3 3 3 3 3 3 3
(iTechSol, 2018) 3 3
(Red Dodo, 2014) 3 3 3 3 3
(Tokoware, 2016) 3 3
(FancyApp, 2018) 3 3 3 3 3
(TeaCapps, 2018) 3 3
(Ecrubit Consultancy Service, 2018) 3 3 3 3
(Application4u, 2018) 3 3
(Scan, 2016) 3 3 3 3 3 3
(ZXing Team, 2017) 3 3 3 3 3 3 3 3
(Geeks.Lab.2015, 2018) 3 3 3 3 3 3 3
(Gamma Play, 2018) 3 3 3
(Barcode Scanner, 2018) 3 3 3 3 3 3 3
(EZ to Use, 2018) 3 3 3 3 3
(I-Plex Technology, 2018) 3 3 3 3 3 3
Table 5: BarSec Droid specification.
Feature Supported
Key
length (bits)
Encryption AES
a
128
Digital
Signature
ECDSA
b
256
RSA
1,024
2,048
3,072
Encoding
Scheme
ISO-8859-1 -
Structure JSON -
URL
Checking
3
c
-
Compatibility 3
d
-
a
Cipher Block Chaining (CBC), Output Feedback (OFB),
Cipher Feedback (CFB) and Galois/Counter Mode (GCM);
b
Elliptic Curve Digital Signature Algorithm (ECDSA);
c
Norton safe web;
d
Supports legacy QR code.
BarSec Droid can also read standard QR codes
that do not include cryptographic data and not fol-
low specific structures, by getting the full URL and
checking their online content using Norton Safe Web
service (Symantec Corporation, 2018).
5 USABILITY AND SECURITY
EXPERIMENTS
We have conducted a users’ survey to get the users’
reactions about the BarSec Droid usage, and the level
of trust for the provided security information. In or-
der to compare the results with other security apps,
we have chosen two very popular apps, KasperSky
(KasperSky Lab, 2018) that belongs to the URL pro-
tection group, and QR Droid Private (DroidLa, 2016)
that belongs to the Crypto-based protection group.
We conducted our survey with the help of 30 users
who were undergraduate students from different col-
leges (volunteers). They were asked to scan two QR
codes for each reader (6 barcodes per user). Then, the
users completed a survey that was built following the
lines of (Gary Perlman, 2015), a very popular usabil-
ity survey, and (Farb et al., 2013), a usability survey
on secure mobile applications.
Our survey includes the following six points: Easy
to use, time satisfaction, support information satisfac-
tion, security of app, likely to use and visually appeal-
ing.
Evaluating Security, Privacy and Usability Features of QR Code Readers
271
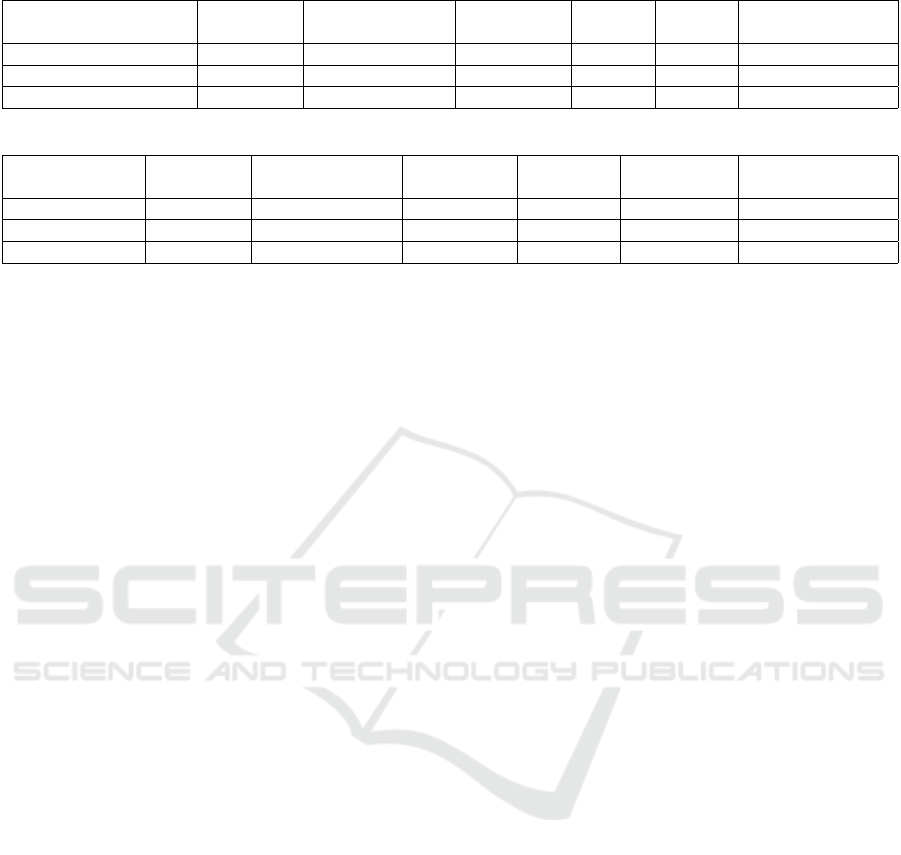
Table 6: T-test results for BarSec Droid vs. KasperSky.
Easy to use Time Satisfaction
Support info
satisfaction
Security
of app
Likely
to use
Visually appealing
BarSec Droid 4.0±0.2 3.7±0.2 3.9±0.2 4.6±0.1 3.6±0.1 3.6±0.2
(KasperSky Lab, 2018) 3.4±0.1 3.8±0.2 2.3±0.2 3.8±0.2 3.0±0.2 2.2±0.2
p-value 0.001 0.895 0.000 0.000 0.012 0.000
Table 7: T-test results for BarSec Droid vs. QR Droid Private.
Easy to use Time Satisfaction
Support info
satisfaction
Security of
app
Likely to use
Visually appealing
BarSec Droid 4.0±0.2 3.7±0.2 3.9±0.2 4.6±0.1 3.6±0.1 3.6±0.2
(DroidLa, 2016) 3.3±0.2 3.4±0.2 3.1±0.2 1.9±0.2 4.5±0.1 3.8±0.2
p-value 0.002 0.169 0.004 0.000 0.000 0.393
Each point have five-point scale, described as: (1:
very unsatisfied to 5: very satisfied). We have fol-
lowed the answers evaluation method used on (Farb
et al., 2013) by using paired T-test, which is a stan-
dard statistical method that compares the mean val-
ues of two groups. Paired T-test was used because the
survey asked the user to evaluate 2 apps at a time.
Table 6 shows the Means (the value before ±),
Mean Standard Error ((MSE), the value after ±), and
p-value results from participants’ feedback for Bar-
Sec Droid and KasperSky. Note that, in the T -Test,
when the p-value is less than 0.05, there is a statisti-
cally significant difference between two groups (Lim-
ited, 2018), and in this case the mean and MSE val-
ues are marked in bold in the table. Table 7 shows
the same results for BarSec Droid and QR Droid Pri-
vate. According to Table 6, it is clear that the users’
opinions recorded better results for BarSec Droid. For
all questions the BarSec Droid means recorded higher
values with statistical significance, except for the time
of tasks satisfaction which recorded converged values
(i.e., similar satisfaction).
According to Table 7, BarSec Droid recorded bet-
ter answers for easiness of use, support information
satisfaction and security trust. On the other hand, QR
Droid Private recorded a higher level of being likely
to use, which reflects the application excellent design
and options. The time of tasks recorded converged
values, which reflects that BarSec Droid, Kaspersky
and QR Droid Private have acceptable time delay ac-
cording to the users’ feedback.
6 CONCLUSION
This study provides a comprehensive assessment for
28 barcode scanning applications, from security, us-
ability and privacy perspectives. We have analyzed
the features of these applications and classified them
into four groups. Through the analysis, we have high-
lighted the limitations, and concluded that: Most of
these apps do not cover the users’ security and privacy
needs. We proposed design tips for usable, secure and
privacy-guaranteed barcode reader applications, and
implemented BarSec Droid, a proof-of-concept An-
droid app that utilizes other applications’ advantages
and resolves their weaknesses.
In order to evaluate our work, we have conducted
a users’ usability and security survey, for BarSec
Droid and two popular QR code readers, i.e., Kasper-
Sky and QR Droid Private. The results show that
when following the proposed design tips the user’s
security trust and awareness increases, as well as the
ease of use. Adding to that, it will enhance the
user’s behavior towards the use of security applica-
tions. As a future work, we plan to extend our analy-
sis to cover more applications, and evaluate the secu-
rity techniques that check QR code contents such as:
Google safe browsing and Norton Safe Web.
REFERENCES
Application4u (2018). Lightning QRcode Scanner. http:
//ww7.application-4u.com/.
Avira (2018). Free QR Scanner. https://www.avira.com/.
Barcode Scanner (2018). QR & Barcode Scanner. https:
//barcodescannerblog.wordpress.com/.
Browser Extension (2018). QR Code Scanner & Bar-
code Reader for CM Browser. http://www.cmcm.com/
en-us/.
Dennings (2018). Safe QR - Scanner & Generato. http:
//www.dennings.org/.
Denso Wave (2017). QRcode.com DENSO WAVE. http:
//www.qrcode.com/en.
DroidLa (2016). QR Droid Private. http://qrdroid.com/.
Dudheria, R. (2017). Evaluating Features and Effective-
ness of Secure QR Code Scanners. In Int. Conference
on Cyber-Enabled Distributed Computing and Knowl-
edge Discovery (CyberC), pages 40–49. IEEE.
Ecrubit Consultancy Service (2018). EC QR. http://www.
ecrubit.com/.
ICISSP 2019 - 5th International Conference on Information Systems Security and Privacy
272

European Union Agency for Network and Infor-
mation Security (ENISA) (2014). Algo-
rithms, Key Size and Parameters Report –
2014. https://www.enisa.europa.eu/publications/
algorithms-key-size-and-parameters-report-2014.
EZ to Use (2018). Free qr scanner: Bar code scanner
& qr code reader. https://play.google.com/store/apps/
details?id=app.qrcode.
FancyApp (2018). QR Code Reader Extreme.
https://play.google.com/store/apps/details?id=com.
fancyapp.qrcode.barcode.scanner.reader.
FANSec Lab Apps (2018). Secure QR Code Scan-
ner. https://play.google.com/store/apps/details?id=
com.fansec.lab.security.secureqrcodescanner.
Farb, M., Lin, Y.-H., Kim, T. H.-J., McCune, J., and Per-
rig, A. (2013). Safeslinger: Easy-to-Use and Secure
Public-Key Exchange. In Proceedings of the 19th an-
nual international conference on Mobile computing &
networking, pages 417–428. ACM.
Focardi, R., Luccio, F., and Wahsheh, H. A. M. (2018a).
Security Threats and Solutions for Two Dimensional
Barcodes: A Comparative Study. In K., D., edi-
tor, Computer and Network Security Essentials, pages
207–219. Springer.
Focardi, R., Luccio, F., and Wahsheh, H. A. M. (2018b).
Usable Cryptographic QR Codes. In Proceedings of
the 19th International Conference on Industrial Tech-
nology, pages 1664–1669. IEEE.
Gamma Play (2018). QR & Barcode Scanner. https://play.
google.com/store/apps/details?id=com.gamma.scan.
Gary Perlman (2015). After Scenario Questionnaire. http:
//garyperlman.com/quest/quest.cgi?form=ASQ.
G Data Software AG (2018). G data qr code scanner. https:
//www.gdata.de/.
Geeks.Lab.2015 (2018). Barcode Scanner Pro.
https://play.google.com/store/apps/details?id=com.
geekslab.qrbarcodescanner.pro.
GitHub (2018). ZXing Project Home. https://github.com/
zxing/zxing/.
Google (website). Google Safe Browsing API. https:
//developers.google.com/safe-browsing/.
Google Inc (2018). Google Play Store. https://play.google.
com/store?hl=en.
Heider Wahsheh (2018). BarSec Droid. https://play.google.
com/store/apps/details?id=barcode security.heider.
bsr.
I-Plex Technology (2018). Secure Barcode Reader & QR
Code Generator. https://play.google.com/store/apps/
details?id=com.iplextech.barcode.scanner.
iTechSol (2018). Secure QR Barcode Scanner.
https://play.google.com/store/apps/details?id=com.
scanner.qr.barcode.reader.bar.codes.
KasperSky Lab (2018). QR Code Reader and Scanner:
App for Android. https://free.kaspersky.com/?cid=
acq-gplay-lnk#mobile.
KidControl Dev (2018). Safe Geotag QR Scanner. https:
//web.facebook.com/GeoTagQR? rdc=1& rdr.
Krombholz, K., Fr
¨
uhwirt, P., Rieder, T., Kapsalis, I., Ull-
rich, J., and Weippl, E. (2015). QR Code Security–
How Secure and Usable Apps Can Protect Users
Against Malicious QR Codes. In Availability, Reli-
ability and Security (ARES), 2015 10th International
Conference on, pages 230–237. IEEE.
Limited, S. (2018). P-value. https://www.statsdirect.com/
help/basics/p values.htm.
Madiff Net (2017). QR & Barcode Security.
https://play.google.com/store/apps/details?id=com.
trustbookin.qrcodebarcodesecurity.
NortonMobile (2016). Norton Snap QR Code Reader.
https://support.norton.com/sp/en/us/home/current/
solutions/v64691018 EndUserProfile en us?client=
norton&site=nrtn en US.
Phishtank (website). Phishtank API. https://www.
phishtank.com/.
Red Dodo (2014). QR & Barcode Reader (Secure). http:
//reddodo.com/qr-barcode-scanner.php.
Reeder, R. W., Felt, A. P., Consolvo, S., Malkin, N.,
Thompson, C., and Egelman, S. (2018). An Expe-
rience Sampling Study of User Reactions to Browser
Warnings in the Field. In Proceedings of the 2018 CHI
Conference on Human Factors in Computing Systems,
page 512. ACM.
Scan (2016). QR Code Reader. https://www.scan.me/.
SECUSO Research Group (2016). QR Scanner (Privacy
Friendly). https://secuso.aifb.kit.edu/index.php.
Symantec Corporation (2018). Norton Safe Web. https:
//safeweb.norton.com/.
TeaCapps (2018). QR & Barcode Reader.
https://play.google.com/store/apps/details?id=com.
teacapps.barcodescanner.
Tengler, D. (2018). Crypto Message. https:
//play.google.com/store/apps/details?id=cz.
crypto message free.apk.
Tokoware (2016). Private QR Reader Free. http://www.
tokoware.com/.
Trend Micro (2018). QR Scanner - Free, Safe QR Code
Reader, Zero Ads. https://www.trendmicro.com/en
us/business.html.
X and C Hi-Tech Inc (2016). Scan 2d Social QR Code Scan-
ner. http://www.scan2d.com/static/index.html.
Yao, H. and Shin, D. (2013). Towards Preventing QR Code
Based for Detecting QR Code Based Attacks on An-
droid Phone Using Security Warnings. In Proc. of the
8th ACM SIGSAC ASIA CCS,, pages 341–346.
ZXing Team (2017). Barcode Scanner. https://github.com/
zxing/.
Evaluating Security, Privacy and Usability Features of QR Code Readers
273
