
On the Efficacy of New Privacy Attacks against 5G AKA
Haibat Khan
a
and Keith M. Martin
Information Security Group, Royal Holloway, University of London, U.K.
Keywords:
5G AKA, Mobile Telephony, Privacy, Unlinkability.
Abstract:
The AKA protocol is the primary mechanism in mobile telephony for establishment of a secure channel be-
tween mobile subscribers and their service providers. In addition to the requisite security guarantees, provi-
sioning subscription privacy is an essential requirement for AKA. A recent paper by Borgaonkar et al. has
uncovered a new vulnerability in one of the associated mechanisms of the AKA protocol. Based upon this
vulnerability, Borgaonkar et al. have presented two privacy attacks; namely, activity monitoring attack and
location confidentiality attack. In this paper, we analyze these attacks for their effectiveness, practicability and
potency against 5G. Our analysis reveal that the activity monitoring attack is not as effective against 5G as it
is against the previous generations (3G/4G). The analysis also bring to light the fact that the location confi-
dentiality attack is a direct extension of an existing privacy vulnerability that affects all generations (including
5G) of mobile telephony in a much severe manner. In this paper we also establish that any countermeasure
introduced to fix this existing vulnerability will also render these two new attacks ineffective.
1 INTRODUCTION
More than half of the world’s population uses mobile
telephony services as an integral part of their daily
life. Considering the ubiquity of mobile telephony,
it is imperative that appropriate security and privacy
guarantees be provisioned to the end-users of these
services. The latest generation of mobile telephony
services operating on a commercial basis is 4G/LTE.
The first phase of the next generation technology (5G
Release 15) has already been standardized and is cur-
rently undergoing field trials (Geelen, 2019). The
international body responsible for standardization of
mobile telephony technologies is the 3rd Generation
Partnership Project (3GPP). The 3GPP standard
for 3G/4G mobile telephony security (3
rd
Genera-
tion Partnership Project, 2017) provisions an Authen-
ticated Key Agreement (AKA) protocol for establish-
ment of a secure channel between mobile subscribers
and their service providers. The AKA protocol for
4G networks is essentially similar to that of 3G with
slight differences in identifier and key management.
For 5G, an enhanced version of this AKA protocol
called the 5G AKA was introduced by 3GPP (3
rd
Generation Partnership Project, 2018c). Apart from
typical security requirements, an important consid-
eration for AKA (and its associated mechanisms) is
a
https://orcid.org/0000-0002-2948-4964
end-user privacy. 3GPP has specified the following
privacy requirements for mobile telephony users (3
rd
Generation Partnership Project, 2018a):
• User Identity Confidentiality. The permanent
identity of a user to whom a service is delivered
cannot be eavesdropped on the radio access link.
• User Location Confidentiality. The presence or
arrival of a user in a certain area cannot be deter-
mined by eavesdropping on the radio access link.
• User Untraceability. An intruder cannot deduce
whether different services are delivered to the
same user by eavesdropping on the radio access
link.
A recent paper (Borgaonkar et al., 2019) has
revealed a new logical vulnerability in one of
the associated mechanisms (sequence number re-
synchronization) of the AKA protocol. Based upon
this vulnerability, this paper presented two privacy at-
tacks; namely, activity monitoring attack and location
confidentiality attack. The activity monitoring attack
allows an attacker to learn subscribers’ mobile service
consumption patterns while the location confidential-
ity attack allows tracking of mobile subscribers, thus
breaking location confidentiality. The paper claimed
that these attacks adversely affect all generations of
mobile telecommunications, including 5G. More im-
portantly, the authors of (Borgaonkar et al., 2019)
Khan, H. and Martin, K.
On the Efficacy of New Privacy Attacks against 5G AKA.
DOI: 10.5220/0007919704310438
In Proceedings of the 16th International Joint Conference on e-Business and Telecommunications (ICETE 2019), pages 431-438
ISBN: 978-989-758-378-0
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
431

stated that these attacks have been acknowledged by
the requisite standardization bodies and that remedial
actions are underway for the future 5G specifications.
In this paper, we analyze the efficacy of these new
privacy attacks against 5G. The reason for confin-
ing this analysis to 5G is due to the fact that rela-
tively facile attacks (IMSI-catching (Fox, 2002), link-
ability via failure messages (Arapinis et al., 2012)
1
)
provisioning more disastrous breaches of subscriber
privacy already exist for the previous generations
(2G/3G/4G). Effective countermeasures for these ex-
isting attacks were not incorporated in the already de-
ployed standards because of the high upgrade costs
involved. It is thus too late to propose any amend-
ments for the 2G/3G/4G specifications. The findings
of our analysis contradict some of the claims made
in (Borgaonkar et al., 2019). Specifically, we show
the following:
• The activity monitoring attack is infeasible to ex-
ecute in 5G networks.
• The location confidentiality attack is a direct ex-
tension of an existing privacy vulnerability (Ara-
pinis et al., 2012) that exploits linkability of the
AKA failure messages. Moreover, we demon-
strate that the results obtained with this extension
attack are less effective than those achieved via
the existing vulnerability.
• Contrary to (Borgaonkar et al., 2019) which
claims dedicated fixes are required for their at-
tacks, we establish that in case of effectual coun-
termeasures introduced against the existing vul-
nerability of (Arapinis et al., 2012), both activity
monitoring attack and location confidentiality at-
tack will be rendered futile.
• The associated security and privacy analysis of
the modified 5G AKA, carried out in a sym-
bolic model, is inaccurate and error prone due to
omission of important aspects specified within the
3GPP standard.
2 BACKGROUND
Before considering the details of the privacy attacks,
we outline the 5G AKA upon which these attacks are
based.
2.1 The 5G AKA
The mobile telephony security architecture consists of
three main entities. Subscribers carry User Equip-
1
This linkability attack is also valid for 5G Release 15.
ment (UE) which is typically a mobile phone (Mo-
bile Equipment (ME) in 3GPP terminology) equipped
with a Universal Integrated Circuit Card (UICC).
While the phones are treated as dumb hosts, the UICC
acts as a Hardware Security Module (HSM) (Sustek,
2011) which hosts the Universal Subscriber Identity
Module (USIM) application. USIM securely stores
and processes the subscriber’s secret information.
The Home Network (HN) is a mobile operator with
whom the user’s subscription is registered. Home
Networks maintain databases about their subscribers
and are responsible for their authentication. UE and
HN are trusted entities which share secret data such as
a subscriber’s long-term identity Subscription Perma-
nent Identifier (SUPI), long-term symmetric key K,
48-bit monotonically increasing counters called Se-
quence Numbers (SQN) used for replay protection,
etc. Sometimes a subscriber is not in the coverage
area of its HN. In such scenarios, the UE is serviced
by another semi-trusted mobile operator called Serv-
ing Network (SN). The SN is semi-trusted in the sense
that while the subscription’s SUPI gets shared with
the SN after a successful secure channel establishment
(this is essential for billing and Lawful Interception
(LI)
2
purposes), the same is not true for other secret
parameters like key K and SQN.
In addition to the requirements of mutual authen-
tication and data confidentiality, it is crucial that SQN
is protected from an eavesdropper during the estab-
lishment of a secure channel between the UE and SN
as its exposure may lead to the compromise of the
identity and location of a user (3
rd
Generation Part-
nership Project, 2018a). In 5G, these requirements
are achieved by the 5G AKA. Figure 1 shows details
of the 5G AKA and its associated failure mechanisms.
In Figure 1 functions f
1
,. . ., f
5
, f
1
∗
and f
5
∗
are unre-
lated symmetric key algorithms, f
1
, f
2
and f
1
∗
act as
message authentication functions, while f
3
, f
4
, f
5
and
f
5
∗
are used as key derivation functions. Key deriva-
tion is performed using the Key Derivation Function
(KDF) specified in 3GPP TS 33.220 (3
rd
Generation
Partnership Project, 2018b) and SN
name
is the global
identity of the SN. A successful 5G AKA culminates
in the derivation of the anchor key K
SEAF
by the SN
and UE from which further keys for securing various
layers of communication are derived. The two cases
of authentication failure for the 5G AKA are as below:
1. MAC Failure: As the first step in authentication
confirmation, the UE checks whether the received
MAC value is correct or not. In case of a fail-
2
Lawful Interception (LI) refers to the facilities in
telecommunications and telephone networks that allow law
enforcement agencies with court orders or other legal au-
thorization to selectively wiretap individual subscribers.
SECRYPT 2019 - 16th International Conference on Security and Cryptography
432
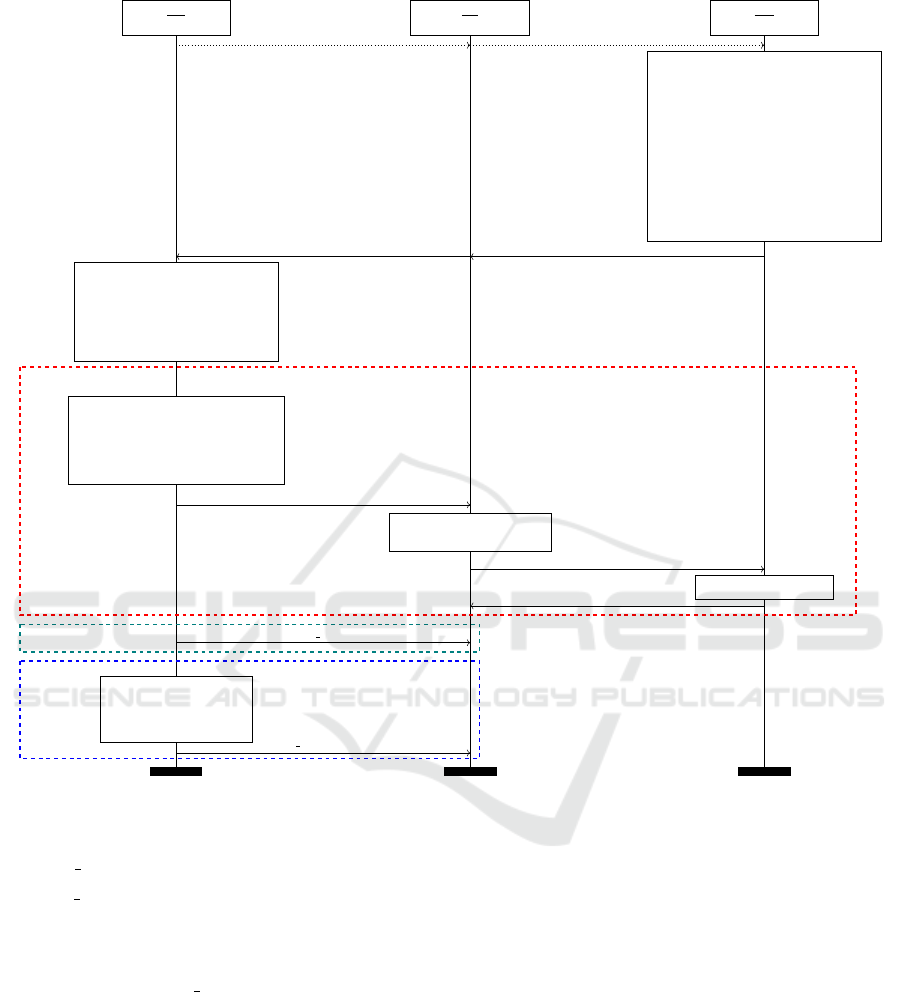
UE
(SUPI, K, SQN
UE
)
SN
(SN
name
)
HN
(SUPI, K, SQN
HN
)
R
$
← {0, 1}
128
AK ← f
5
(K, R)
MAC ← f
1
(K, SQN
HN
kR)
CONC ← SQN
HN
⊕ AK
AUT N ← CONCkMAC
CK, IK ← f
3
(K, R), f
4
(K, R)
XRES ← f
2
(K, R)
XRES
∗
← KDF(CKkIK, SN
name
kRkXRES)
HXRES
∗
← SHA256(RkXRES
∗
)
K
AU SF
← KDF(CKkIK, SN
name
kCONC)
K
SEAF
← KDF(K
AU SF
, SN
name
)
SQN
HN
← SQN
HN
+ 1
XCONCkX MAC ← AU T N
AK ← f
5
(K, R)
XSQN
HN
← XCONC ⊕ AK
MAC ← f
1
(K, X SQN
HN
kR)
CHECK (i) XMAC
?
= MAC
(ii) XSQN
HN
> SQN
UE
− 4
SQN
UE
← XSQN
HN
RES ← f
2
(K, R)
.
.
.
K
SEAF
← KDF(K
AU SF
, SN
name
)
RES
∗
← KDF(CKkIK, SN
name
kRkRES)
HRES
∗
← SHA256(RkRES
∗
)
CHECK HRES
∗
?
= HXRES
∗
CHECK RES
∗
?
= XRES
∗
MAC
∗
← f
1
∗
(K, SQN
UE
kR)
AK
∗
← f
5
∗
(K, R)
CONC
∗
← SQN
UE
⊕ AK
∗
AUT S ← CONC
∗
kMAC
∗
Temporary or Encrypted ID SUPI or Encrypted ID, SN
name
R, AUT N, HXRES
∗
, K
SEAF
R, AUT N
RES
∗
SUPI or Encrypted ID, SN
name
, RES
∗
Success
MAC Failure
Sync Failure, AU T S
If (i) and (ii) then:
If ¬(i) then:
If (i) and ¬(ii) then:
Figure 1: The 5G AKA protocol and its associated failure mechanisms.
ure [Case ¬(i) in Figure 1], the U E replies with a
MAC Failure message back to the SN.
2. Sync Failure: After MAC verification, the UE
checks the freshness of the sequence number SQN
received in the authentication challenge. In case
of this failure [Case (i) and ¬(ii) Figure 1], it re-
sponds with a Sync Failure message along with
a re-sync token AUT S. Note that in Figure 1,
the sequence number freshness check is denoted
by XSQN
HN
> SQN
UE
− 4. What this actually
means is that there is some “window” of size 4,
within which sequence numbers smaller than the
current sequence number of UE will be accepted
given they previously had not been received by
the UE. This mechanism is there to handle out-
of-order delivery of challenge messages from HN
to UE. We discuss this aspect in further detail in
Section 3.3.
2.2 The Logical Vulnerability
The logical vulnerability of (Borgaonkar et al., 2019)
affecting user privacy stems from the use of XOR
within the re-sync token AUT S, which is concatena-
tion of two parameters; CONC
∗
and MAC
∗
. The pa-
rameter CONC
∗
contains the current sequence num-
ber of the UE in a masked form as SQN
UE
⊕ AK
∗
,
where AK
∗
= f
5
∗
(K, R). Note that during calculation
of the masking key AK
∗
, the value R is extracted from
the received authentication challenge. Hence, in case
of receiving the same authentication challenge twice
at two different times t
1
and t
2
, the masked sequence
numbers in their corresponding AUT S tokens will be:
CONC
∗
1
= SQN
1
UE
⊕ AK
∗
1
where AK
∗
1
= f
5
∗
(K, R)
CONC
∗
2
= SQN
2
UE
⊕ AK
∗
2
where AK
∗
2
= f
5
∗
(K, R),
On the Efficacy of New Privacy Attacks against 5G AKA
433

where SQN
1
UE
is the sequence number of UE at time
t
1
and SQN
2
UE
is the sequence number at time t
2
.
Therefore, the adversary can compute:
CONC
∗
1
⊕CONC
∗
2
= SQN
1
UE
⊕ SQN
2
UE
.
Next we detail the two attacks presented in (Bor-
gaonkar et al., 2019) which, by exploiting this vul-
nerability, try to compromise user privacy.
2.3 Activity Monitoring Attack
In this attack the adversary tries to learn the n least
significant bits of SQN
UE
at two different time in-
stances, t
1
and t
2
. Thereafter, from the difference be-
tween the sequence numbers (corresponding to suc-
cessful authentication sessions), the attacker infers the
volume of “activity” (number of call, SMS, etc) a par-
ticular user has performed between these two time in-
stances, hence the name Activity Monitoring Attack
(AMA). As we will see shortly, to mount this at-
tack the adversary requires malicious interaction with
both U E and HN (via SN). Hence, the compromise
of both identity confidentiality and location confiden-
tiality of the target UE are prerequisites to launch
an AMA. Details of a single instance of the attack
at a particular time t are now explained. The on-
line phase of the AMA is depicted in Figure 2. Dur-
ing this phase the attacker first fetches 2
n−1
+ 1 suc-
cessive authentication challenges from the HN for
the targeted UE. The attacker then sends a partic-
ular n + 1 of these challenges to the UE each fol-
lowed by a replay instance of the initially received
authentication challenge (R
0
, AUT N
0
) and records the
corresponding n + 1 resync tokens, i.e. AUT S
‘
and
AUT S
j
( f or j = 0 to n − 1).
In the offline phase, utilizing the logical vulnera-
bility as elaborated earlier in Section 2.2, the attacker
retrieves the following values from the recorded
resync tokens:
δ
i
= SQN
0
HN
⊕ (SQN
0
HN
+ 2
i
) f or 0 ≤ i ≤ n − 1,
where SQN
0
HN
is the initial value of the HN’s se-
quence number at the start of the attack. Note that
due to receipt of the first authentication challenge
(R
0
, AUT N
0
) from the adversary, the UE will also
sync its sequence number to this value at the start of
the attack. Further, by feeding these n values into Al-
gorithm 1, the attacker extracts the n least significant
bits of SQN
0
HN
.
2.4 Location Confidentiality Attack
As an other consequence of the logical vulnerability
of Section 2.2, (Borgaonkar et al., 2019) presented
Algorithm 1: SQN inference algorithm.
Data: δ
i
f or 0 ≤ i ≤ n − 1
Result: X = n least significant bits of SQN
0
HN
X ← [0, 0, . . . , 0] // init an array of size
n
for i ← 0 to n − 1 do
// Analyze δ
i
at bit positions i, i + 1
(b
1
, b
2
) ← (δ
i
[i], δ
i
[i + 1])
if (b
1
, b
2
) ⇔ (1, 0) then
// No remainder propagates when
SQN
0
HN
+ 2
i
X [i] ← 0
else if (b
1
, b
2
) ⇔ (1, 1) then
// A remainder propagates when
SQN
0
HN
+ 2
i
X [i] ← 1
else
// Not possible
Error
end
end
return (X)
a Location Confidentiality Attack (LCA), i.e. finding
out whether some targeted UE is present in a cer-
tain location. Note that we present LCA as explained
in (Borgaonkar et al., 2019). We claim there are sev-
eral erroneous assumptions upon which this attack is
based and we will highlight these when we undertake
the corresponding analysis in Section 3.2. The LCA
proceeds as follows:
1. The attacker observes a 5G AKA session of some
targeted user
3
UE
x
and extracts the corresponding
CONC
∗
x
value by replaying the observed authenti-
cation challenge to UE
x
.
2. After some time, if the attacker wishes to check
whether another unknown 5G AKA session be-
longs to U E
x
or not, the attacker again replays the
earlier observed challenge from Step (1) to this
unknown user and obtains CONC
∗
?
.
3. Now based upon the value CONC
∗
x
⊕CONC
∗
?
, the
attacker can infer (with non-negligible probabil-
ity) whether this new user is UE
x
or not. In case of
some other user, this will be a random value, while
in case of U E
x
, it will equate SQN
old
UE
x
⊕SQN
current
UE
x
due to canceling out of the common masking key
AK
∗
. This value (dependent upon the lapsed time)
should be small in the case of user UE
x
.
3
Note that it is not necessary for the attacker to know the
SU PI of the user to launch this attack.
SECRYPT 2019 - 16th International Conference on Security and Cryptography
434
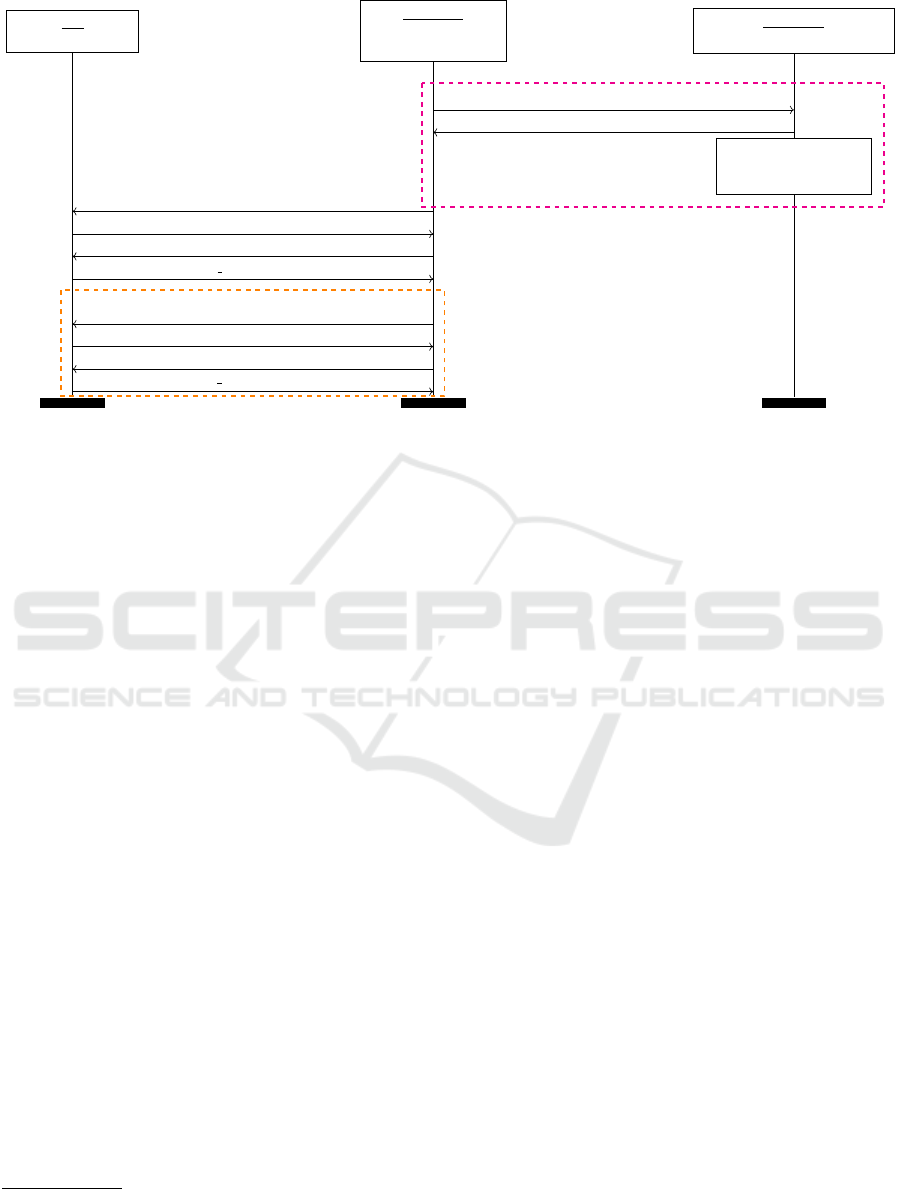
UE
(SUPI, K, SQN
UE
)
Attacker
(SUPI or
Encrypted SUPI)
SN + HN
(SUPI, K, SQN
HN
= SQN
0
HN
)
.
.
.
SQN
HN
← SQN
HN
+ 1
ID
R
i
, AUT N
i
R
0
, AUT N
0
RES
0
R
0
, AUT N
0
Sync Failure, AU T S
‘
R
2
j
, AUT N
2
j
RES
j
R
0
, AUT N
0
Sync Failure, AU T S
j
f or i = 0 to 2
n−1
:
f or j = 0 to n − 1 :
Figure 2: The online phase of the AMA.
3 ANALYSIS
3.1 AMA
3.1.1 Infeasible Prerequisites
As elaborated earlier in Section 2.3, to launch an
AMA, the adversary first needs to compromise the tar-
get’s identity and location confidentiality. While such
a compromise is easy to manage in earlier generations
(3G/4G) via IMSI-catching attacks (Fox, 2002), how
this will be achieved in 5G is not clear. With a ran-
domized public-key encryption mechanism in place to
protect direct exposure of the SUPI during the identi-
fication phase, such a compromise is highly unlikely
in 5G Release 15. In Section 5.2 of (Borgaonkar et al.,
2019), in the case of an unknown SUPI, the use of
SUCI (the randomized encryption of SUPI) is sug-
gested for fetching the requisite authentication chal-
lenges from the HN. This would require correlat-
ing the SUCI to the appropriate SUPI, which in the
case of a secure encryption scheme is not possible.
The most convincing implementation of AMA in 5G
would look something like this: the attacker follows
the victim closely
4
and observes the victim’s attach
procedure (utilizing SUCI) to the network. We stress
that all this needs to be undertaken in isolation with-
out the presence of other mobile subscribers in the
concerned attack area. Such requirement of physical
4
In this case the identity confidentiality and location
confidentiality are already compromised as the attacker can
already identify the target and is aware of its location.
tracking of the target in AMA render it unattractive
for its automated use in 5G.
The prospect of the repeated use of SUCI for
fetching of successive authentication challenges from
the HN to launch the AMA is possible because the
current identification mechanism in 5G (3
rd
Genera-
tion Partnership Project, 2018c) is susceptible to re-
play attacks. No dedicated replay prevention mech-
anism has been built into the 5G randomized en-
cryption scheme used for SUPI protection. This
was highlighted to 3GPP by the European Telecom-
munications Standards Institute Security Algorithms
Group of Experts (ETSI SAGE) during their evalua-
tion of the SUPI protection mechanism for 5G (ETSI-
SAGE, 2017). Recently, an alternative SUPI protec-
tion mechanism has been proposed for 5G which pre-
vents such SUCI replay attacks (Khan et al., 2018).
We stress that adoption of such a mechanism will ren-
der attacks such as AMA infeasible.
3.1.2 Requesting Batch of AVs
Unlike the previous generations, Clause 6.1.3.2.0
of (3
rd
Generation Partnership Project, 2018c) does
not support requests for issuing multiple Authentica-
tion Vectors (AVs) for 5G AKA. Also, after issuance
of each 5G AV, the HN waits for a response from
the SN after successful mutual authentication and key
agreement between UE and SN as elaborated in Fig-
ure 1. Hence, the adversary has to wait for the expira-
tion of the timeout of the currently issued AV before
the next AV issuance request can be entertained by the
HN. This considerably increases the time complexity
On the Efficacy of New Privacy Attacks against 5G AKA
435

of AMA’s online phase in 5G.
3.1.3 The Accuracy of AMA Assumptions
Essentially AMA tries to reveal the n least significant
bits of SQN
UE
at two different time frames for the
target user. Thereafter, based upon the assumption
that each sequence number increment corresponds to
a successful AKA session, it deduces that the differ-
ence between the two SQN
UE
reveals the user’s ser-
vice consumption during that time interval. The prob-
lem with this assumption is that the difference be-
tween the sequence numbers does not “fully” corre-
sponds to successful AKA sessions. Many times, due
to network failure or channel noise (bad weather, etc),
legitimate messages may get lost during transmission
and may not reach the intended destination. On the
other hand, it may be the case that a user is genuinely
under attack by some active attacker. In such cases,
the end result would be the non-utilization of the af-
fected sequence numbers. Thus, while a difference in
sequence numbers may give a rough idea about the
user’s service consumption, its efficacy is dependent
upon many other factors.
Another assumption that adversely affects
AMA’s accuracy is the inference of SQN
UE
from
SQN
HN
. Note that at the start of the AMA, SQN
UE
is
forced to update to the value SQN
0
HN
, the initial value
of the SQN
HN
. The presumption behind this step is
that the two values should be equivalent, which may
or may not be the case. It is quite possible (due to
a variety of circumstances) for SQN
HN
to be much
higher than that of SQN
UE
at the start of AMA. In
such scenarios, AMA’s accuracy about the target’s
activity gets negatively impacted.
3.1.4 Severity of AMA
In (Borgaonkar et al., 2019), it is claimed that
AMA breaches subscribers’ privacy more severely
than either location confidentiality or identity con-
fidentiality attacks. This seems to be an overstate-
ment as compromise of the permanent identity or lo-
cation is arguably a more severe breach of privacy
than the exposure of a number of voice calls or SMSs
sent by a user. Otherwise, such a breach of privacy
would have been mentioned in the official 3GPP mo-
bile subscribers’ privacy requirements (3
rd
Genera-
tion Partnership Project, 2018a). In fact, breach of
a user’s identity and location does not only violate the
user’s privacy but can lead to physical attacks. For
(a sensational) example, consider the scenario where
a bomb explosion is triggered automatically when a
high value target’s presence is detected in the near
vicinity by an IMSI-catcher (Goldman et al., 2009;
Bock, 2016).
3.2 LCA
3.2.1 No Activity Monitoring
Unlike AMA, LCA does not presume any prerequisite
compromises (such as identity and location confiden-
tiality) about the target which makes it a much easier
attack to launch in practice. Moreover, LCA targets
location confidentiality of a user instead of its service
consumption, which is a more severe breach of pri-
vacy as discussed in Section 3.1. In a way, LCA can
be considered as a more direct application of the the
logical vulnerability of Section 2.2. Though, (Bor-
gaonkar et al., 2019) have presented LCA as an exten-
sion of their primary attack AMA, we argue that LCA
is a much more significant attack than AMA as it does
not require fetching of authentication vectors from the
HN, running of the SQN Inference Algorithm and is
simple to execute. However, we stress that there is no
activity monitoring (contrary to the claim made in the
Footnote No 2 of (Borgaonkar et al., 2019)). This is
because, now, what the attacker gets after a successful
LCA is as:
CONC
∗
UE
⊕CONC
∗
?
= SQN
old
UE
⊕ SQN
current
UE
.
Note that the presumption for this is that the value
SQN
old
UE
⊕ SQN
current
UE
will be small (less than some
threshold value). So there are two aspects which hin-
der the accurate inference of activity monitoring:
1. The attacker is already operating the LCA under
the presumption of a small increase in SQN
UE
which renders the aspect of activity monitoring in-
effective.
2. Unlike AMA, in LCA the attacker is unable to ex-
tract the n least significant bits of SQN
UE
, what
the attacker actually gets are the positions of the
bits of SQN
UE
which flipped their value (either 0
to 1 or 1 to 0) hindering an accurate estimate of
the difference between the two values. Neverthe-
less, there is some leakage from a cryptographic
viewpoint.
3.2.2 No Requirement of Dedicated Fixes
Having established that LCA is not another version of
AMA but rather an attack targeting location confiden-
tiality in its own right, we turn our attention to another
important dimension. All generations of mobile tele-
phony (including 5G Release 15) suffer from an exist-
ing location attack known in the literature as Linkabil-
ity of Failure Messages (LFM) attack (Arapinis et al.,
SECRYPT 2019 - 16th International Conference on Security and Cryptography
436

2012). The LFM attack exploits the fact that in case of
an erroneous authentication challenge, the reason of
the authentication failure gets exposed to the attacker,
i.e. either MAC Failure or Sync Failure. This allows
an attacker to link two failure messages together to
identify a target user. LFM is much simpler to execute
than LCA. In LFM, the attacker first observes an AKA
session of the target user and records the authentica-
tion challenge (R, AUT N). Later, when the attacker
wants to check whether another AKA session belongs
to the same user or not, he replays the recorded au-
thentication challenge and observes the type of fail-
ure message received. In case of MAC Failure it is
some other user, while in case of Sync Failure it is the
same user. Note that in LFM, unlike LCA, no further
computations are required and the results are precise.
Hence, it is a more devastating attack than LCA.
In (Borgaonkar et al., 2019) it is claimed that LCA
will work even if LFM attack gets patched. The rea-
son behind this claim seems to be the (erroneous) as-
sumption that a countermeasure for the LFM attack
will only hide the reason of authentication failure and
not the rest of the failure message contents (includ-
ing AUT S token) leading to the logical vulnerability
of Section 2.2. However, the solutions in the liter-
ature proposing countermeasures to the LFM attack
suggest otherwise. This is essentially because the
indistinguishability experiments proving unlinkabil-
ity in these solutions cover all aspects of unlinkabil-
ity and not only the reason of the authentication fail-
ure. As a concrete example we consider the counter-
measure proposed in (Arapinis et al., 2012). In case
of an authentication failure (due to any reason), the
whole failure message including the resync token is
encrypted by the network public key. Hence, the log-
ical vulnerability of Section 2.2 gets resolved before
it can be exploited. This leads us to the deduction
that in reality, LCA is a more complex version of the
LFM attack. Surprisingly, in Release 15 of 5G spec-
ification, no countermeasures for this potent LFM at-
tack have been adopted. Though the authors of (Bor-
gaonkar et al., 2019) present LCA as a distinct attack
from the LFM attack, suggesting that dedicated coun-
termeasures independent of existing attacks would be
required, it is not hard to see that a genuine counter-
measure against the LFM attack will also render both
AMA and LCA ineffective. This is because now the
attacker will not be able to the exploit the resync to-
kens AUT S to launch AMA or LCA.
3.3 The Curious Case of Out-of-Order
Message Delivery
Although, there has been a number of formal anal-
yses of the 5G AKA (Basin et al., 2018; Cremers
and Dehnel-Wild, 2019) in the symbolic model us-
ing tools such as Tamarin Prover (Meier et al., 2013)
and 3GPP has been using this approach for proto-
col evaluations (3
rd
Generation Partnership Project,
2001), the problem has always been the necessary ab-
straction required during the transformation from the
real world conditions to the underlying mathematical
model of the system being evaluated. As a concrete
example, consider the case of the analysis carried out
in (3
rd
Generation Partnership Project, 2001). Even
after formal analysis, a number of vulnerabilities were
later discovered in the 3G AKA. Another example
is that of (Basin et al., 2018), whose analysis of the
5G AKA failed to capture the privacy flaws pointed
out in (Borgaonkar et al., 2019). While the formal
analysis of 5G AKA undertaken in (Borgaonkar et al.,
2019) is based upon enhanced system models which
consider the AUT S tokens of the Sync Failure mes-
sages, there is an important aspect which was missed,
i.e. how the 5G AKA (and the earlier AKA proto-
cols) handle out-of-order delivery of the authentica-
tion challenges from the HN to UE.
As per 3GPP specifications (3
rd
Generation Part-
nership Project, 2018a), the mechanism in the UE for
verifying the freshness of sequence numbers should
to some extent allow the out-of-order delivery of se-
quence numbers. This is to ensure that the authenti-
cation failure rate due to synchronization failures re-
sulting from such messages is sufficiently low. The
standard requires that the UE should store in its mem-
ory the sequence numbers of a certain number of past
successful authentication events. Such a mechanism
ensures that a (stale) sequence number can still be
accepted if it is among the last 32 sequence num-
bers generated (i.e. 4 = 32 in Figure 1) and was
not previously used. Unfortunately, the formal mod-
els of (Basin et al., 2018; Borgaonkar et al., 2019)
have ignored this important aspect of sequence num-
ber freshness verification which renders their security
and privacy analysis of 5G AKA imprecise.
4 CONCLUSION AND
RECOMMENDATIONS
In this paper, we analyzed two recent attacks on 5G
subscription privacy by (Borgaonkar et al., 2019). We
established that the activity monitoring attack is in-
On the Efficacy of New Privacy Attacks against 5G AKA
437

feasible in practice to be executed in 5G networks.
We have also shown that the location confidentiality
attack is trying to achieve what previous attacks in
the literature have already done with much less ef-
fort and greater effectiveness. Moreover, we demon-
strated that both these attacks will become void if
the existing privacy vulnerability of (Arapinis et al.,
2012) is fixed. Additionally, we highlighted how the
history of the symbolic modeling of the AKA protocol
has been plagued with serious gaps that lead to vari-
ous vulnerabilities. Looking at the the results of our
analysis in hindsight, it seems that the authors of (Bor-
gaonkar et al., 2019) were overoptimistic in interpre-
tation of their results.
Keeping in view the current development status
of the 5G AKA the following recommendations are
made to 3GPP:
• It is important for user privacy that 3GPP should
introduce appropriate countermeasures for the
linkability attack described in (Arapinis et al.,
2012).
• Considering the aspects of protocol analysis dis-
cussed in Section 3.3, it is imperative that an
all-encompassing comprehensive security and pri-
vacy analysis of the 5G AKA in an appropriate
computational model should be carried out by a
group of experts.
• To prevent any further future attacks, it is es-
sential that the existing vulnerability of the 5G
AKA identification phase to replay attacks be pre-
vented. The proposal of (Khan et al., 2018) is one
candidate for such a measure.
REFERENCES
3
rd
Generation Partnership Project (2001). Formal Analysis
of the 3G Authentication Protocol 3GPP TR 33.902
Version 4.0.0 (Release 4).
3
rd
Generation Partnership Project (2017). 3GPP System
Architecture Evolution (SAE); Security Architecture
(3GPP TS 33.401 version 13.5.0 Release 13).
3
rd
Generation Partnership Project (2018a). 3G Secu-
rity; Security Architecture (3GPP TS 33.102 Version
15.0.0 Release 15).
3
rd
Generation Partnership Project (2018b). Generic Au-
thentication Architecture (GAA); Generic Bootstrap-
ping Architecture (GBA)(3GPP TS 33.220 Version
15.2.0 Release 15).
3
rd
Generation Partnership Project (2018c). Security Ar-
chitecture and Procedures for 5G Systems (3GPP TS
33.501 Version 15.0.0 Release 15).
Arapinis, M., Mancini, L. I., Ritter, E., Ryan, M., Golde,
N., Redon, K., and Borgaonkar, R. (2012). New Pri-
vacy Issues in Mobile Telephony: Fix and Verifica-
tion. In Yu, T., Danezis, G., and Gligor, V. D., editors,
the ACM Conference on Computer and Communica-
tions Security, CCS’12, Raleigh, NC, USA, October
16-18, 2012, pages 205–216. ACM.
Basin, D. A., Dreier, J., Hirschi, L., Radomirovic, S., Sasse,
R., and Stettler, V. (2018). A Formal Analysis of 5G
Authentication. In Lie, D., Mannan, M., Backes, M.,
and Wang, X., editors, Proceedings of the 2018 ACM
SIGSAC Conference on Computer and Communica-
tions Security, CCS 2018, Toronto, ON, Canada, Oc-
tober 15-19, 2018, pages 1383–1396. ACM.
Bock, M. (2016). Simulation chamber and method for set-
ting off explosive charges contained in freight in a
controlled manner. US Patent No. 9335139, Filed
September 19th., 2012, Issued May. 10th., 2016.
Borgaonkar, R., Hirschi, L., Park, S., and Shaik, A. (2019).
New Privacy Threat on 3G, 4G, and Upcoming 5G
AKA Protocols. To appear in Proceedings on Privacy
Enhancing Technologies (PoPETs), Issue 3, 2019.
https://eprint.iacr.org/2018/1175.
Cremers, C. and Dehnel-Wild, M. (2019). Component-
Based Formal Analysis of 5G-AKA: Channel As-
sumptions and Session Confusion. In 26th Annual
Network and Distributed System Security Symposium,
NDSS 2019, San Diego, California, USA, February
24-27, 2019. The Internet Society.
ETSI-SAGE (2017). First response on ECIES for conceal-
ing IMSI or SUPI. https://portal.3gpp.org/ngppapp/
CreateTdoc.aspx?mode=view&contributionId=
832160.
Fox, D. (2002). Der imsi-catcher. Datenschutz und Daten-
sicherheit, 26(4).
Geelen, A. (2019). Port of Hamburg: 5G appli-
cations pass field test. https://www.telekom.
com/en/media/media-information/archive/
port-of-hamburg-5g-applications-pass-field-test-551178.
[Online; accessed 15-January-2019].
Goldman, S. O., Krock, R. E., Rauscher, K. F., and Run-
yon, J. P. (2009). Mobile forced premature detonation
of improvised explosive devices via wireless phone
signaling. US Patent No. 7552670, Filed September
22nd., 2005, Issued Jun. 30th., 2009.
Khan, H., Dowling, B., and Martin, K. M. (2018). Identity
Confidentiality in 5G Mobile Telephony Systems. In
Cremers, C. and Lehmann, A., editors, Security Stan-
dardisation Research - 4th International Conference,
SSR 2018, Darmstadt, Germany, November 26-27,
2018, Proceedings, volume 11322 of Lecture Notes
in Computer Science, pages 120–142. Springer.
Meier, S., Schmidt, B., Cremers, C., and Basin, D. A.
(2013). The TAMARIN Prover for the Symbolic
Analysis of Security Protocols. In Sharygina, N. and
Veith, H., editors, Computer Aided Verification - 25th
International Conference, CAV 2013, Saint Peters-
burg, Russia, July 13-19, 2013. Proceedings, volume
8044 of Lecture Notes in Computer Science, pages
696–701. Springer.
Sustek, L. (2011). Hardware Security Module.
https://link.springer.com/referenceworkentry/10.
1007%2F978-1-4419-5906-5 509. [Online; accessed
08-May-2019].
SECRYPT 2019 - 16th International Conference on Security and Cryptography
438
