
BTG-RKASE: Privacy Preserving Revocable Key Aggregate Searchable
Encryption with Fine-grained Multi-delegation & Break-The-Glass
Access Control
Mukti Padhya
1 a
and Devesh C. Jinwala
2
1
Department of Computer Engineering, Sardar Vallabhbhai National Institute of Technology (SVNIT), Surat, India
2
Department of Computer Science and Engineering, Indian Institute of Technology, Jammu, India
Keywords:
Searchable Encryption, Data Sharing, Data Retrieval, Cloud Server, Multi-keyword Search, Multi-delegation,
Revocation, Break-The-Glass Access.
Abstract:
Delegation is the technique of sharing the available rights from the delegator to the delegatee for the purpose
data sharing. The Key Aggregate Searchable Encryption (KASE) scheme supports delegation of search rights
for any set of ciphertexts using a key of constant-size. However, three critical issues still need to be consid-
ered. Firstly, the existing KASE schemes only discuss delegation of rights from the data owner to other user.
However, if a subject receiving a delegation cannot perform time-critical task on the shared data, it becomes
necessary for the delegatee to further delegate their received rights to another user. Secondly, the existing
delegation mechanisms tend to rely on manual processes initiated by end-users. If no authorized user exists
to perform (or to delegate) a time-critical task, in such exceptional case, we require mechanism that flexi-
bly handles emergency situations by breaking or by controlled overriding of the standard access permissions.
Thirdly, the access of user in the system changes dynamically and it requires KASE to support user revocation
securely while not affecting the legitimate users’ access to the shared files. To address all of the above issues,
we propose Revocable KASE with Break-The-Glass access control (BTG-RKASE) to provide (i)fine-grained
multi-delegation of available rights from the delegatee to another user,(ii)break-the-glass access mechanism
when no authorized user exists to perform (or to delegate) a time-critical task,(iii)revocation of delegated rights
(even in case of multi-delegation). The security and empirical analysis shows that BTG-RKASE performs bet-
ter than the existing KASE schemes.
1 INTRODUCTION
The cryptography-based access control (Sandhu et al.,
1996; Sahai et al., 2005) is designed to prevent
unauthorized access of data stored on the untrusted
cloud server. However, in some exceptional situa-
tions the tight access policies of traditional access
control schemes (such as Role-Based Access Control
(RBAC) (Sandhu et al., 1996), Attribute-Based Ac-
cess Control (ABAC) (Sahai et al., 2005)) prevent the
data accessibility. Let us consider the following ex-
ample from a healthcare application to clarify the is-
sues we aim to address in this paper.
The E-Healthcare Record (EHR) storage system
allows patients to store their health-related informa-
tion on the cloud server. The EHR records contain
the patient’s personal information and his health in-
a
https://orcid.org/0000-0002-0498-4188
formation such as the patient’s blood pressure, heart-
beats etc. However, the privacy and confidentiality
of that patient’s medical records cannot be neglected.
Therefore, to prevent unauthorized access of medical
records, patient (Alice) use cryptography-based ac-
cess control and define access policy for the health
records (Figure 1a). For example, the access policy
(Doctor =’Bob’ and Hospital=’ABC’) or Lab=’XYZ’
allows doctor Bob from ’ABC’ hospital or manager
of ’XYZ’ laboratory to access Alice’s data. Suppose,
Bob is away from work for some particular reason,
such as sickness or on holiday, who has the right to ac-
cess Alice’s medical records in order to evaluate and
treat her appropriately? As per the access policy de-
fined by Alice, other doctors or nurses from the emer-
gency ward can not access Alice’s medical record. If
we consider the sickness of the patient, data accessi-
bility is needed to give timely treatment, at the same
time we cannot ignore the privacy of patient’s med-
Padhya, M. and Jinwala, D.
BTG-RKASE: Privacy Preserving Revocable Key Aggregate Searchable Encryption with Fine-grained Multi-delegation Break-The-Glass Access Control.
DOI: 10.5220/0007919901090124
In Proceedings of the 16th International Joint Conference on e-Business and Telecommunications (ICETE 2019), pages 109-124
ISBN: 978-989-758-378-0
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
109
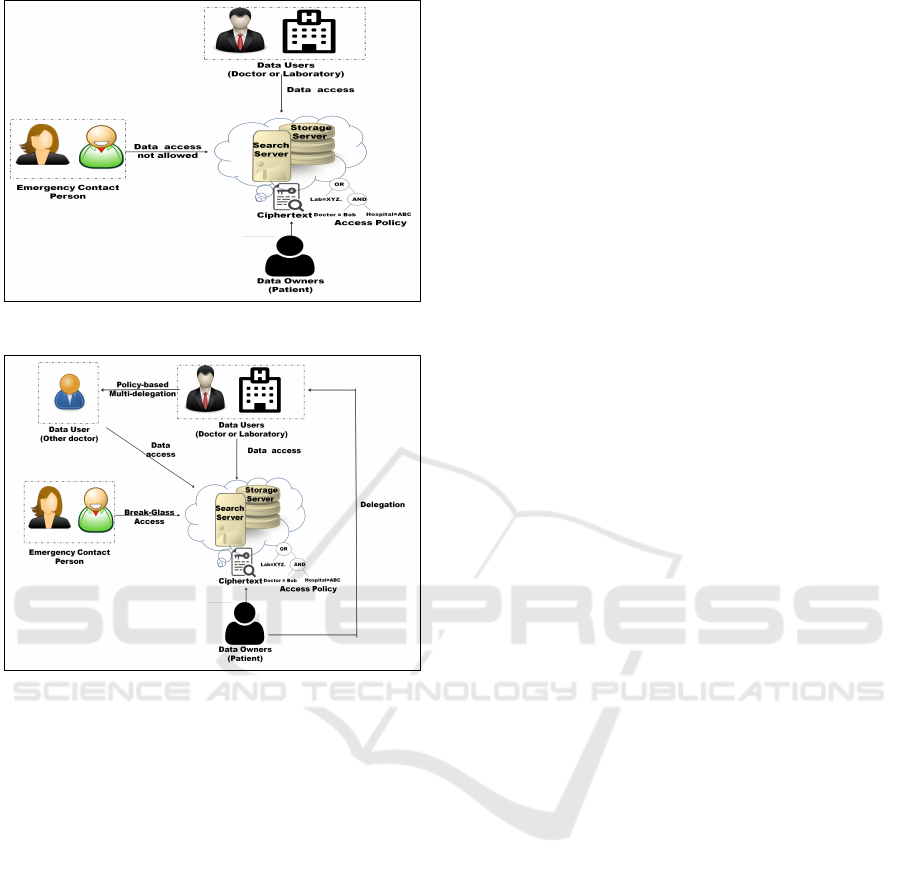
(a) Traditional approach of access control using the existing cryptography-
based schemes (Sandhu et al., 1996; Sahai et al., 2005)
(b) The proposed approach using fine-grained multi-delegation and break-
the-glass access control
Figure 1: Access control and data security in EHR System.
ical record and information? The question is, how
can we design an access control model to provide pri-
vacy, confidentiality and availability at the same time?
The possible solution to provide flexible access con-
trol and also maintaining data security is delegation of
rights over Alice’s medical records from Bob to other
doctor.
Delegation mechanism (Crampton and Khamb-
hammettu, 2008; Schaad and Moffett, 2002) allow
subjects to transfer their available rights (data access
and search), roles, tasks, or duties to another subject.
Subsequently, a subject receiving a delegation (the
delegatee) will act on behalf of the delegating sub-
ject (the delegator). Recent attempts at Key Aggre-
gate Searchable Encryption (KASE) (Cui et al., 2016)
allows a data owner to delegate keyword search rights
on a set S of files. KASE inherits the property of Key
Aggregate Encryption (KAE) (Chu et al., 2014), i.e.,
to delegate search rights on |S| number of files, the
data owner is required to share a single aggregate key
with a user. In addition, a user is required to sub-
mit a single aggregate trapdoor (instead of a group of
trapdoors) to the cloud to perform a keyword search
across |S| number of shared files. However, the limi-
tation of the existing delegation schemes (Chu et al.,
2014; Banu, 2015; Dang et al., 2016; Mahalle and
Pawade, ; Patranabis et al., 2015; Cui et al., 2016; Li
et al., 2016; Li et al., 2018; Zhou et al., 2018; Pad-
hya and Jinwala, 2018) is that they only discuss del-
egation of rights from the data owner to other user.
On the other hand, if a subject receiving a delegation
cannot perform time-critical task on the shared data,
it becomes necessary to further delegate the received
rights from the delegatee to another user. We define
such transitive delegation of rights from the delegatee
to another user a multi-delegation. For example, in
above discussed scenario of EHR system Alice can
delegate search and access rights of her records to
Bob using the existing delegation schemes (Chu et al.,
2014; Banu, 2015; Dang et al., 2016; Mahalle and
Pawade, ; Patranabis et al., 2015; Cui et al., 2016; Li
et al., 2016; Li et al., 2018; Zhou et al., 2018; Pad-
hya and Jinwala, 2018). However, multi-delegation
from Bob to other doctors is not possible in the ex-
isting delegation schemes. In the existing delegation
schemes (Chu et al., 2014; Banu, 2015; Dang et al.,
2016; Mahalle and Pawade, ; Patranabis et al., 2015;
Cui et al., 2016; Li et al., 2016; Li et al., 2018; Zhou
et al., 2018; Padhya and Jinwala, 2018), the possi-
ble way to do multi-delegation is that the delegatee
can share his received key having rights for dataset
S with other users. However, this solution is infea-
sible and insecure in case of delegatee wants to share
selected dataset S
0
⊂ S with other user. Further, multi-
delegation can temporarily change the access control
state so as to allow a subject to use another subject’s
privileges. It may be possible that the data owner does
not want to reveal his data to any user other than the
delegatee.
Furthermore, in the critical system such as health-
care industry and disaster management, even if the
set of authorized entities are unavailable, the task on
the shared dataset is expected to be done in reason-
able time. In the healthcare industry, patients are ex-
pected to be treated in reasonable time. In case of
Bob delegates his rights over Alice’s medical records
to John and John meets medical emergency, then how
to access the patient’s data?. Therefore, we solicit the
answer to an interesting research question as how to
handle exceptional situation when no authorized user
exists to perform (or to delegate) a time-critical task?
Motivated by use cases from the disaster management
domain, the break-the-glass principle (Joint, 2004)
was introduced as one approach to flexibly handle
emergency situations by breaking or overriding the
SECRYPT 2019 - 16th International Conference on Security and Cryptography
110

standard access permissions in a controlled manner.
In essence, break-the-glass policies (Ferreira et al.,
2006; Ardagna et al., 2008; Ardagna et al., 2010;
Marinovic et al., 2011) allow a subject to perform an
action under certain conditions (e.g., life-threatening
situation of patient) even though he/she was not pre-
viously authorized to do so. Usually, such override
accesses are monitored and documented for later re-
views and audits.
However, the break-glass policies do not take into
account the existence or availability of authorized
users. In essence, a break-glass policy extend the set
of authorized accesses for the duration of emergency
and possibly allowing a unauthorized user to access
the data (or resource), even though authorized sub-
jects are available. It is difficult to address the above
violations in an access control policy for the health-
care application because an overly loose policy might
permit access to inappropriate users, but an overly
tight policy might prevent access from the appropriate
users. A potential research direction would be to find
ways to the controlled overriding of access control re-
strictions.
Envisioning these specific requirements in KASE,
we present a KASE scheme with fine-grained multi-
delegation and break-the-glass access policy. A no-
tion of subject availability is also introduced, and the
proposed scheme allows searchable group data shar-
ing, flexible access control and data security in the
following ways (Figure 1b): in normal situations, the
authorized user with the delegated key can access and
search over the shared dataset, provided ciphertext
class is within the range of aggregate key. For the
fine-grained multi-delegation, if the attributes of the
delegatee satisfy the hidden access policy (defined
by the data owner), the delegatee can delegate his
received rights to another user. In exceptional situ-
ation (when the authorized users are not available),
the break-glass access mechanism allow timely ac-
cess to the data, provided the attributes of the user
satisfy the break-the-glass policy. Additionally, the
proposed scheme also allows revocation of delegated
rights even in case of multi-delegation. The revoca-
tion refers to the process of taking away the delegated
privileges. If the receiver of delegated rights leaves
the system, or if the data is used differently than the
data owner agreed, then data owner or delegator re-
quires to revoke the delegated rights. Additionally,
the revocation in the proposed scheme does not af-
fects the non-revoked users, as they do not require
to update their corresponding delegated keys, which
greatly reduces the expensive cost of key update and
the overhead of key delegate authority.
1.1 Related Work
The KASE scheme (Cui et al., 2016), derives its roots
from the seminal work on Key Aggregate Encryption
(KAE) by Chu et.al. (Chu et al., 2014). In KASE, a
data owner delegates search rights on a dataset using
an aggregate key and the user can search over shared
data by submitting a single aggregate trapdoor to the
cloud. Despite the advantage of the secure delegation
of search rights using a constant size key, KASE (Cui
et al., 2016; Li et al., 2016; Li et al., 2018; Zhou et al.,
2018; Padhya and Jinwala, 2018) also brings the se-
curity issues and challenges.
The KASE schemes proposed in (Cui et al., 2016;
Zhou et al., 2018) do not support searching over
multi-owner data using a single key of constant size.
Therefore, Li et al. (Li et al., 2016) propose KASE
to support multi-owner search using a single trapdoor
and also provide verification of search results using
an aggregate key. However, security proof against
chosen keyword attack is not discussed for the KASE
schemes (Cui et al., 2016; Li et al., 2016). Moreover,
the existing KASE schemes (Cui et al., 2016; Li et al.,
2016) do not provide data and trapdoor privacy, as dis-
cussed in (Kiayias et al., 2016). Zhou et al. show the
possible insider attack on the KASE (Cui et al., 2016)
scheme in (Zhou et al., 2018). Further, the KASE
(Cui et al., 2016; Li et al., 2016) schemes consider the
security assumption of Bilinear Diffie-Hellman Expo-
nent (BDHE). However, SDH or its variants such as
the BDHE do not guarantee the security for specific
parameters, as discussed in (Cheon, 2006). In (Pad-
hya and Jinwala, 2018), the authors proposed KASE
that supports search over multi-owner data using a
single aggregate key and also overcomes other secu-
rity issues of the existing KASE schemes (Cui et al.,
2016; Li et al., 2016; Li et al., 2018). However,
the KASE scheme proposed in (Padhya and Jinwala,
2018) does not supports conjunctive keyword search
and key leakage resiliency. In (Zhou et al., 2018),
the authors consider Industrial IoT (IIoT) applications
and propose a KASE scheme in the file-centric frame-
work for IIoT applications. However, this approach
suffers from low performance. In this scheme, each
user’s public key has 3n + 1 elements and secret has
n + 3 elements. Here, n is the maximum number of
documents held by a data owner.
In the existing KASE (Cui et al., 2016; Li et al.,
2016; Li et al., 2018; Zhou et al., 2018; Padhya
and Jinwala, 2018) schemes if the delegatee needs to
share his received rights on the shared dataset with
another user, then he must carry out the following
steps (Figure 2a): (i) first download the selected data,
(ii) retrieve the plaintext through decryption, (iii) re-
BTG-RKASE: Privacy Preserving Revocable Key Aggregate Searchable Encryption with Fine-grained Multi-delegation Break-The-Glass
Access Control
111

(a) Traditional approach using the existing KASE (Cui et al., 2016; Li et al., 2016; Li et al., 2018; Zhou et al., 2018; Padhya and Jinwala,
2018) schemes
(b) The proposed approach
Figure 2: Multi-Delegation.
encrypt the selected dataset using his own keys (iv)
outsource the re-encrypted data to the cloud server,
and (v) share the keys with the user (to whom the dele-
gatee wants to delegate his received rights). However,
this solution seems secure but such retrieval, as well
as the re-encryption process, become infeasible for
real-time use. Another possible solution to do multi-
delegation in the existing KASE (Cui et al., 2016; Li
et al., 2016; Li et al., 2018; Zhou et al., 2018; Padhya
and Jinwala, 2018) schemes is as follows: the dele-
gate can ask the data owner to generate a new aggre-
gate key k
0
agg
for selected dataset S
0
= {1,..,n
0
} and
share it with the user. However, this solution requires
both data owner and the delegatee to be involved in
the delegation process and later on it may result in
the tedious task for the data owner. Additionally, the
delegatee cannot directly share his aggregate key k
agg
having search rights for dataset S with other users.
Therefore, to minimize the overhead required for
multi-delegation (especially the expensive cost of re-
encryption of selected dataset) at the user sides, a bet-
ter approach is to outsource the computation of re-
encryption to the third party. We observe that Proxy
Re-Encryption (PRE) (Blaze et al., 1998) can solve
the issue of multi-delegation of rights with minimal
required overhead at user sides. PRE allows an un-
trusted proxy to re-encrypt a ciphertext from being en-
crypted under one key to another key, without learn-
ing anything about the underlying plaintext. Further-
more, the re-encrypted ciphertext can be decrypted
by the delegatee using his own key (Figure 2b). In
the proposed scheme, if the attributes of the delega-
tee satisfy the hidden access policy (defined by the
data owner), the delegatee can further delegate their
received rights to other user(s) by requesting a proxy
server to re-encrypt the selected data from the shared
dataset.
To the best of our knowledge, ours is the first
KASE scheme that meets all the following require-
ments all together viz.: fine-grained multi-delegation,
break-the-glass access control, revocation and pri-
vacy preservation simultaneously.
1.2 Our Contributions
The characteristics and contributions of the BTG-
RKASE are as follows:
• Fine-grained multi-delegation: The proposal al-
lows a data owner to delegate access and search
rights of any set of ciphertexts by sharing an ag-
gregate key with the delegatee. In addition, BTG-
RKASE support transitive delegation of rights
from the delegatee to other user(s) in a fine-
grained manner. Further, the expensive computa-
tion of re-encryption required for multi-delegation
is outsourced to proxy server.
• Break-the-glass access control: In exceptional sit-
uation (when the authorized users are not avail-
able), the break-glass access mechanism allow
timely access to the data, provided the attributes
of the user satisfy the break-the-glass policy.
• Revocation in multi-delegation: The subject who
delegated the rights remains accountable for the
SECRYPT 2019 - 16th International Conference on Security and Cryptography
112

outcome of the delegated privileges. Therefore,
the proposed scheme allows the data owner and
the delegator (in case of multi-delegation) to re-
voke any user’s delegated rights in case delegatee
behaves maliciously or leaves the system.
• Multi-keyword Search. We enhance the existing
KASE schemes and improve its query expressive-
ness by supporting multi-keyword search over the
shared dataset using a trapdoor of constant size.
• Privacy preservation: The proposed BTG-
RKASE scheme preserves the privacy, as the hid-
den access policy defined by the data owner, the
attribute token, keyword ciphertext and the query
trapdoor do not reveal any information about re-
lated attributes or keywords.
• Improve Query Performance. The proposed
KASE scheme allows searching over the shared
dataset S using a single trapdoor Tr, that a query
requester submits to the cloud server. The exiting
KASE schemes (Cui et al., 2016; Li et al., 2016;
Li et al., 2018; Zhou et al., 2018) require |S| num-
ber of trapdoor to search over shared dataset S,
as the existing KASE schemes generate adjusted
trapdoors Tr
l
to search over doc
l
for each l ∈ S
using the given trapdoor Tr.
1.3 Outline of the Paper
The rest of the paper is organized as follows: The pre-
liminaries are given in Section 2. The system archi-
tecture and security model are defined in Section 3.
We give a concrete construction of the proposed BTG-
RKASE scheme in Section 4. The security analysis of
the BTG-RKASE is discussed in Section 5. The em-
pirical evaluation of the proposed scheme is discussed
in Section 6. Conclusion and future extensions are
provided in Section 7. References are at the end.
2 PRELIMINARIES
In this section, we introduce computational problems,
hardness assumptions and notations used throughout
this paper. We rely on the standard definitions used
for security of cryptographic schemes.
2.1 Computational Assumption
Definition 1 DDH Assumption: The DDH prob-
lem in group G of prime order p (according to
the security parameter) is a problem for input of
a tuple (g,g
a
,g
b
,g
c
,R) where, a, b,c ∈ Z
p
be cho-
sen at random and g be a generator of G,then to
Table 1: Notations used in the proposed BTG-RKASE
scheme.
Term Meaning
λ Security parameter
n Number of documents held by a data owner
B Bilinear map group system
SP System parameter
doc
l
l
th
document
PubK Public parameters
pk Public key
msk Master secret key
sk Secret key
K
l
Break-glass key of document doc
l
BK
l
Encrypted break-glass key of document doc
l
rk re-encryption key
SK Attribute token
Attr Set of user’s attributes used to generate attribute token SK
l Index of document or file
S Subset S ⊆ {1, .....,n} contains the indices of documents
KS Keyword space that involves m different keywords in the system
w
i
i
th
keyword
w
i, j
j
th
value of keyword w
i
from it’s N
i
different possible values
−→
Q Set of query keywords attached with the query trapdoor Tr
−−→
KW Set of keywords attached with the ciphertext C
−−→
KW
M Message or Plaintext
C Ciphertext
C
−−→
KW
Keyword ciphertext
C
M
Data ciphertext
δ
l
Public information related to ciphertext of l
th
document
i.e. parameters C
1
and C
2
C
R
Re-encrypted ciphertext
A
l
Access policy attached with ciphertext C
l
and defined by data owner
BT G
l
Break-the-glass access policy attached with ciphertext C
l
and defined by data owner
k
agg
Aggregate key
Tr Trapdoor used to search query keyword(s) within set
−→
Q
R Search result
RL
l
Revocation list of l
th
document
U
l
The set of revoked users’ identity for l
th
document
U
QR
User id of query requester
Π Multiplicative notation
AV
att
i
Set of all possible values for attribute att
i
av
atr
i, j
j
th
value of attribute att
i
in the set AV
att
i
Available
i
The status of availability of user having id U
i
(Available = 1, Not available =0)
decide whether R= g
abc
or not. An algorithm A
has advantage ε in solving DDH problem in G if
Adv
DDH
(A):=|Pr[A(g,g
a
,g
b
,g
c
,g
abc
) = 0]−
Pr[A(g,g
a
,g
b
,g
c
,R) = 0]| ≥ ε(κ). We say that the
DDH assumption holds in G if no Probabilistic Poly-
nomial Time (PPT) algorithm has an advantage of at
least ε in solving the DDH problem in G.
2.2 Notations
The list of notations used throughout the paper is
given in the Table 1.
3 SYSTEM ARCHITECTURE
AND SECURITY MODEL
In this section we present the formal definition of the
proposed BTG-RKASE scheme and formalize a secu-
rity model for it.
3.1 Framework
The proposed BTG-RKASE scheme is an ensemble
of randomized polynomial-time algorithms, as dis-
cussed further, here. The data owner first sets up an
account on the cloud server and establishes the public
system parameter via Setup(). At the time of register-
ing in the system, the Trusted Authority (TA) assigns
BTG-RKASE: Privacy Preserving Revocable Key Aggregate Searchable Encryption with Fine-grained Multi-delegation Break-The-Glass
Access Control
113

a unique id to the user. TA manages users in the sys-
tem and it is fully trusted by entities in the system.
The data owner generates a public, secret and master-
secret keys via Keygen(). The data owner securely
send secret key to the TA. The TA constructs attribute
token via AttrGen(). Messages can be encrypted via
Encrypt() algorithm. The data owner generates key
for break-the-glass access via KeyGen BTG(). To
delegate the search and access rights to a specific sub-
set of data classes, the data owner uses the master-
secret to generate a constant size aggregate key via
Extract(). The generated key can be passed to dele-
gatees securely (via secure e-mails or secure device).
The data owner or delegator can take away the del-
egated privileges via Revocation() algorithm. For
multi-delegation of received data rights, the delega-
tee can generate re-encryption key via ReKeygen()
algorithm. The generated key can be passed to proxy
server, using which the proxy server can re-encrypt
the requested set of data via ReEncrypt(). Finally,
any user with an aggregate key can search over shared
dataset by generating query trapdoor via Trapdoor-
Gen(). On receiving the query trapdoor from the user,
the cloud server runs the Test() algorithm to retrieve
matching documents and send it further to the query
requester. The user can access the ciphertext via De-
crypt() algorithm, provided ciphertext class is within
the range of aggregate key. For the break-the-glass ac-
cess, the user run BTG Access() algorithm, provided
the attributes of the user satisfy the break-the-glass
policy.
Furthermore, in the following discussion of the
proposed scheme, the keyword space contains m dif-
ferent keywords, i.e., KS = {w
1
,w
2
,....,w
m
}. Each
keyword w
i
contains N
i
possible values and w
i, j
rep-
resents the j
th
value of keyword w
i
. Let assume
that there are total X users in the system and U =
{U
1
,...,U
X
} is a set of all users’ identities. There-
fore, each cloud user can be uniquely identified by
his assigned identity U
id
∈ U. Additionally, U
l
⊂ U
represents the set of revoked users’ identities for l
th
document, where U
l
i
∈ U
l
represents an identity of
user whose delegated rights needs to be revoked over
l
th
document. The revocation list U
l
may be empty,
which means there is no user needs to be revoked for
l
th
document.
• SP ←Setup(1
λ
, n): Takes as input the security pa-
rameter λ and the number of documents held by a
data owner n. Outputs the public system param-
eters SP, which is omitted from the input of the
other algorithms for brevity.
• (pk, sk,msk) ←KeyGen(): Outputs a public, se-
cret and master-secret key pair (pk, sk,msk) for a
data owner registering in the system.
• SK ←AttrGen(sk,Attr): Takes as input the secret
key sk and the set of attributes Attr of user. Out-
puts the attribute token SK.
• C
l
←Encrypt(pk,sk,l,M,KW, A): Takes as input
the the public key pk, secret key sk, document in-
dex l, message M, set of related keyword(s) KW ,
and the hidden access policy A. Outputs the corre-
sponding ciphertext C
l
= (δ
l
,C
M
,C
KW
,C
A
), where
C
M
is data-ciphertext, C
KW
keyword-ciphertext, δ
l
public information, C
A
ciphertext with the hidden
access policy.
• BK
l
←KeyGen
BTG(sk, msk,l,BT G): , Takes as
input the master-secret key msk, secret key sk,
document index l, and the break-the-glass policy
BT G. Generates a break-glass key K
l
for docu-
ment doc
l
and then encrypt it using given break-
the-glass policy BT G. The algorithm outputs en-
crypted key BK
l
. If user’s attribute token SK satis-
fies break-glass policy BT G then user can recover
break-glass key K
l
to access document doc
l
.
• k
agg
←Extract(msk, S): Takes as input the master-
secret key msk of data owner and subset of data
classes S ⊆ {1,2, ...,n}. Outputs the aggregate
key k
agg
which aggregates the search and access
rights of all encrypted messages within set S.
• RL ←Revocation(U
l
,msk,l): Takes as input the
set of revoked users’ identities U
l
, master-secret
key msk, and document index l. Outputs the revo-
cation list RL
l
= (RL
1
,RL
2
).
• rk←ReKeygen(pk, pk
0
): Takes as input the pub-
lic key pk of data owner and public key pk
0
of del-
egatee (who wants to delegate his received rights
further to other user(s)). The algorithm generates
re-encryption key rk.
• (C
R
l
|∀l ∈ S
0
) ←ReEncrypt(rk, SK, S
0
): Takes as
input the re-encryption key rk, the attribute token
SK and set S
0
of encrypted documents’ indices.
Outputs re-encrypted ciphertexts C
R
l
iff SK A
l
∀l ∈ S
0
.
• Tr ←TrapdoorGen(k
agg
,
−→
Q ): Takes as input an
aggregate key k
agg
and a set of query keywords
−→
Q . Outputs a single trapdoor Tr.
• R ←Test(Tr, S,l,U
QR
): Takes as input a query
trapdoor Tr, a set of shared documents’ indices
S, document index l, and identity of the query re-
quester U
QR
∈ U. If U
QR
is not the revoked user
and l ∈ S, Test algorithm returns the search result
R ∈ {0,1} by following the rules shown below:
R =
(
1,If
−→
Q
−−→
KW
0,Otherwise
Otherwise, the algorithm returns NULL.
SECRYPT 2019 - 16th International Conference on Security and Cryptography
114

• M ←Decrypt(k
agg
, S,l, C
l
): Takes as input the
ciphertext C
l
, the data class l, and the aggregate
key k
agg
corresponding to the set S. The algorithm
outputs the decrypted result M if l ∈ S.
• M ←BTG Access(SK,l, U
QR
): Takes as input the
attribute token SK, an identity of the query re-
quester U
QR
, and the data class l. The algorithm
outputs the decrypted result M iff SK BTG
l
and
U
QR
is not the revoked user.
3.2 Security Model
We consider the cloud servers and data users to be
honest but curious, i.e., they follow the given proto-
cols honestly, but try to get some additional informa-
tion beyond their authorization. However, the capac-
ity of the data user in the system is limited by both
storage space and computing power. Moreover, com-
munication channels involving the server are assumed
to be insecure.
It is required that the ciphertext does not reveal
any information about the corresponding keyword(s)
to an adversary. We prove this claim by the secu-
rity of Indistinguishability against Chosen Keyword
Attack (IND-CKA) model. Moreover, given a valid
search token, the adversary can only gain information
whether the search is successful by Indistinguisha-
bility against Keyword Guessing Attack (IND-KGA)
model. We use the static corruption model, that means
the set of corrupted users has to be defined in the ini-
tialization phase. In addition, the adversary is not al-
lowed to ask for re-encryption key from uncorrupted
users to corrupted users or vice versa. We introduce
the games between an attack algorithm A and a chal-
lenger, both of whom are given input of n, the to-
tal number of documents. In the following games,
F(L, T ) is a binary relation, where L is the set of at-
tributes labeled with user’s attribute token SK and T
is the hidden access policy attached with ciphertext.
F(L, T ) = 1, if the attributes in L satisfy the access
policy specified in T i.e. L T ; else, F(L,T ) = 0.
3.2.1 IND-CKA Model
Init Phase. The adversary A selects a set of cor-
rupted users denoted by CoList sends it to the chal-
lenger. The adversary also commits two ciphertext
access policies T
∗
0
and T
∗
1
and challenge index i
c
for
which he wishes to be challenged upon.
Setup. The challenger runs Setup(1
λ
,n) to generate
system parameters. The setup algorithm also defines
a keyword space ks and attribute set AT T R.
Query Phase 1. The adversary A adaptively queries
q
1
,...., q
n
to following oracles and oracle answers in
polynomial time.
• Uncorrupted Key Generation Oracle O
pk
: Out-
puts a new key pair (pk,sk,msk) ←Keygen() and
give pk to A.
• Corrupted Key Generation Oracle O
msk
: Gen-
erates (pk, sk,msk) ←Keygen() and issues key
pair (pk,sk,msk) to A
• Attribute Token Generation Oracle O
SK
: The
adversary is allowed to request for polynomially
bounded number of attribute token on attributes L
with the restriction that F(L, T
∗
0
) = F(L,T
∗
1
) = 1
or F(L, T
∗
0
) = F(L,T
∗
1
) = 0
• Aggregate Key Generation Oracle O
k
agg
: On
giving input of (msk, S) by the adversary, where
msk is master secret key corresponding to pk and
pk is from O
msk
, then oracle returns an aggregate
key k
agg
← Extract(msk,S). The restriction is that
an adversary can not ask for the aggregate key for
challenge index, i.e., if i
c
∈ S, then O
k
agg
returns
null.
• Re-encryption Key Generation Oracle O
rk
: On
giving input of (pk, pk
0
) by the adversary, where
pk, pk
0
are from O
pk
or O
msk
, then oracle gen-
erates re-encryption key rk ←ReKeygen(pk, pk
0
).
Here, one constraint is required that both the pub-
lic key pk, pk
0
are either corrupted or both are un-
corrupted, i.e. pk and pk
0
both are from O
pk
or
O
msk
. The adversary is not allowed to ask for
re-encryption key from uncorrupted users to cor-
rupted users or vice versa.
• Re-encryption Oracle O
re
: On giving in-
put of (rk,S
0
), where re-encryption key
rk ←ReKeygen(pk, pk
0
) and pk, pk
0
are from
O
pk
or O
msk
, then oracle generates re-encrypted
ciphertext (C
R
l
|∀l ∈ S
0
) ←ReEncrypt(rk,SK,S
0
)
• Trapdoor Generation Oracle O
Tr
: It runs
Tr ←TrapdoorGen(k
agg
,
−→
Q ), and returns the trap-
door Tr for
−→
Q to A.
• Test Oracle O
test
: On giving input of trapdoor
Tr, set S and document index l ∈ S, the chal-
lenger checks k
agg
corresponding to set S occurs
in table T
k
agg
, if yes, the oracle returns output of
Test(Tr,S,l,U
QR
) to the adversary. Otherwise, it
returns null.
Challenge Phase.
The attacker A sends the challenger two equal length
set of keywords
−−→
KW
0
;
−−→
KW
1
on which it wishes to be
challenged along with an index i
c
, a message M from
message space, a public key pk, secret key sk, and
BTG-RKASE: Privacy Preserving Revocable Key Aggregate Searchable Encryption with Fine-grained Multi-delegation Break-The-Glass
Access Control
115

the challenge access policy T
∗
0
and T
∗
1
. Here, the
restriction is that if for any attribute token gener-
ated by oracle O
SK
in Phase 1 on an attribute list L,
F(L, T
∗
0
) = F(L,T
∗
1
) = 1 then
−−→
KW
0
=
−−→
KW
1
. Addi-
tionally, the attacker had not previously asked for the
query trapdoor corresponding to keywords
−−→
KW
0
;
−−→
KW
1
to the oracle O
Tr
and pk is from the O
pk
. The
challenger chooses β randomly from {0,1} and runs
Encrypt(pk,sk,i
c
,M,
−−→
KW
β
,T
∗
β
) and returns keyword
ciphertext C
∗
β
to the adversary.
Query Phase 2. Identical to that in phase 1., the ad-
versary asks for more queries q
n+1
,....., q
n
2
except the
following oracles:
• Trapdoor Generation Oracle O
Tr
: On giving in-
put of (k
agg
,
−→
Q ) by the adversary, the challenger
answers same as that in phase 1, except the fol-
lowing cases:
– The adversary had previously ask for the trap-
door corresponding to a set of keywords
−−→
KW
0
or
−−→
KW
1
–
−→
Q =
−−→
KW
0
or
−→
Q =
−−→
KW
1
If one of the above condition holds, then chal-
lenger returns null.
• Test Oracle O
test
: On input of Test(Tr,S,l,U
QR
),
if i
c
= l or i
c
∈ S, then the challenger returns null.
Otherwise the challenger responds as that in phase
1.
Guess. The adversary A outputs its guess β
0
∈ {0,1}
for β and wins the game if β = β
0
.
The advantage of the adversary in this game is de-
fined as ADV
BTG-RKASE
A,K
= |Pr[β = β
0
]−
1
2
|, where the
probability is taken over the random bits used by the
challenger and the adversary.
Definition 2 (IND-CKA Security): We say that the
proposed BTG-RKASE scheme hold the privacy for
keyword if ADV
BTG-RKASE
A,K
is negligible with respect
to the security parameter for any polynomial time ad-
versary.
3.2.2 IND-KGA Model
Init Phase. The adversary A selects a set of cor-
rupted users denoted by CoList sends it to the chal-
lenger. The adversary also commits two set of query
keywords
−→
Q
0
and
−→
Q
1
and challenge index i
c
for which
he wishes to be challenged upon.
Setup. The challenger runs Setup(1
λ
,n) to generate
system parameters. The setup algorithm also defines
a keyword space ks and attribute set AT T R.
Query Phase 1. The adversary A adaptively queries
q
1
,...., q
n
to oracles and oracle answers in polynomial
time. The oracles are identical to that in the IND-
CKA security model except the following:
• Ciphertext Generation Oracle O
C
: The attacker
A sends the challenger set of keywords
−−→
KW along
with an index l, a message M from message
space, a public key pk, secret key sk, and ac-
cess policy A. If l 6= i
c
, then the challenger runs
Encrypt(pk,sk,l,M,
−−→
KW ,A) and returns ciphertext
C
l
to the adversary.
Challenge Phase. The attacker A sends the chal-
lenger two equal length set of keywords
−→
Q
0
;
−→
Q
1
on
which it wishes to be challenged along with an index
i
c
, and an aggregate key k
c−agg
corresponding to a set
S which includes an index i
c
. Here, the restriction
is that the attacker had not previously asked for the
ciphertext corresponding to keywords
−→
Q
0
;
−→
Q
1
to the
oracle O
C
. The challenger chooses β randomly from
{0,1} and runs TrapdoorGen(k
c−agg
,
−→
Q
β
) and returns
query trapdoor Tr
∗
β
to the adversary.
Query Phase 2. Identical to that in phase 1, the adver-
sary asks for more queries q
n+1
,....., q
n
2
except that
• The adversary A cannot ask for the aggregate key
corresponding to a set S which includes an index
i
c
• Ciphertext query on keyword set
−→
Q
0
or
−→
Q
1
under
challenge index i
c
is not allowed
Guess. The adversary A outputs its guess β
0
∈ {0,1}
for β and wins the game if β = β
0
.
The advantage of the adversary in this game is de-
fined as ADV
BT G−RKASE
A,KG
= |Pr[β = β
0
]−
1
2
|, where the
probability is taken over the random bits used by the
challenger and the adversary.
Definition 3 (IND-KGA Security): We say that the
proposed BTG − RKASE method hold the privacy for
trapdoor if ADV
BT G−RKASE
A,KG
is negligible with respect
to the security parameter for any polynomial time ad-
versary.
3.3 Availability of Subjects
The proposed scheme BTG-RKASE makes break-
the-glass access decisions based on the availability
of subjects. The definition of availability will be
application-specific. In the context of a hospital,
a doctor may have access to the patient’s data, but
may not be physically present in the hospital and un-
able to respond to any emergency situation of his pa-
tient. In the military setting, availability may simply
be whether the corresponding user is still alive and
present on battlefield.
SECRYPT 2019 - 16th International Conference on Security and Cryptography
116

To identify a set of available authorized subjects at
request evaluation time, the proposed scheme main-
tain a set denoted by Au
l
⊂ U represents the set of
users’ identities who has access right for document
doc
l
, where Au
l
i
∈ Au
l
represents an identity of the
delegatee who has received the access rights over l
th
document. The proposed scheme achieves the set Au
l
updating through the cloud servers to save the com-
putational overhead of data owner. In case of multi-
delegation, the user who further delegates his avail-
able rights for doc
l
, updates the set Au
l
. Further-
more, the proposed scheme also use one more nota-
tion Available
i
to represent the status of availability
of user having id U
i
. If Available
i
= 1, user hav-
ing id U
i
is available, otherwise he is not available
(Available
i
= 0). Therefore, if Available
i
= 0|∀Au
l
i
∈
Au
l
, then break-the-glass access on doc
l
is possible,
provided user’s attributes satisfy the break-the-glass
policy
4 THE PROPOSED METHOD:
BTG-RKASE
In this section, we discuss the construction of the
proposed scheme. The attribute space to define ac-
cess policy A is ATT R = {att
1
,att
2
,.., att
κ
}. Assume
AV
att
i
={av
1
,av
2
,...av
η
i
} be the set of all possible val-
ues of attribute att
i
, where η
i
denotes the maximum
number of values for i
th
attribute. Here, av
attr
i, j
rep-
resents the j
th
value of attribute attr
i
. The other no-
tations used in the forthcoming discussion are already
introduced in Section 2. The detailed construction of
the proposed BTG-RKASE scheme is as follows:
1. Setup (1
λ
, n): The data owner runs this algo-
rithm and publish the system parameters SP = (B,
PubK,H
1
,H
2
). In the following discussion, bilin-
ear map group system B=(p,G,G
T
,e(., .)), where
p is the order of G and 2
λ
≤ p ≤ 2
λ+1
. g is a gen-
erator of group G. n is the number of documents
D= (doc
1
, doc
2
, ..., doc
n
) that belongs to a data
owner. The random element α ∈ Z
p
. Algorithm 1
gives a formal description of Setup operation.
2 Keygen: The data owner runs this algorithm to
generate a key pair (pk,sk,msk)
pk = v= g
γ
; sk = ρ; msk = γ, where γ∈ Z
p
and
ρ∈ Z
p
Algorithm 1: Setup (1
λ
, n) → SP.
1: B=(p, G,G
T
,e(., .))
2: PubK ← (g, g
1
, ..,g
n
,g
n+2
, ...,g
2n
)
3: g
l
← g
α
l
∈ G| ∀l ∈ {1,2,..,n, n + 2,...,2n}
4: Select two one-way, collision resistant hash func-
tions H
1
: {0, 1}
∗
× {0,1}
∗
→ G, H
2
: {0, 1}
∗
×
{0,1}
∗
→ G
5: SP ← (B, PubK,H
1
,H
2
)
6: ks ←
m
{0,1}
∗
3 AttrGen(sk, Attr) : The attribute token genera-
tion algorithms takes as input the secret key sk,
a set Attr of attributes and generates a attribute to-
ken of constant size. Algorithm 2 gives a formal
description of AttrGen operation:
Algorithm 2: AttrGen(sk,Attr) → SK.
1: Select r ∈
R
Z
p
2: S
0
← g
r
3: for all av
attr
i, j
∈ Attr do
4: S
1
← g
ρ
(Π(H
2
(av
attr
i, j
)))
r
5: Return SK =< S
0
,S
1
>
4 Encrypt(pk,sk,l,M,
−−→
KW ,A): The data owner
gives public key, secret key sk, message M, docu-
ment index l, keywords set
−−→
KW , and access policy
A as input. The data owner generates the cipher-
text by following the steps as shown in Algorithm
3. Algorithm 3 gives a formal description of En-
crypt operation.
Algorithm 3: Encrypt (pk, sk,l, M, KW, A) → C
l
.
1: Select t ∈ Z
p
2: if l ∈ {1,2,...,n} then
3: C
1
← g
t
4: C
2
← (v · g
l
)
t
5: C
3
= C
−−→
KW
← Π(H
1
(w
i, j
))
t
|∀w
i, j
∈
−−→
KW
6: C
4
= C
M
← M · e(g
1
,g
n
)
t
|M ∈ G
T
7: for all av
attr
i, j
∈ A do
8: C
5
= (Π(H
2
(av
attr
i, j
)))
t
9: C
6
= l · e(g
t
,g
ρ
)
10: C
A
= (C
5
,C
6
)
11: C
l
= (δ
l
,C
−−→
KW
,C
M
,C
A
) = (C
1
,C
2
,C
3
,C
4
,C
5
,C
6
)
12: Data owner stores ciphertext C
l
on the cloud
server.
5. KeyGen BTG(sk, msk,l,BT G): The data owner
generates the break-glass key by following the
steps as shown in Algorithm 4. Algorithm 4 gives
a formal description of KeyGen BTG operation.
BTG-RKASE: Privacy Preserving Revocable Key Aggregate Searchable Encryption with Fine-grained Multi-delegation Break-The-Glass
Access Control
117

Algorithm 4: KeyGen BTG(sk,msk, l,BT G) → BK
l
.
1: Select β ∈ Z
p
2: if l ∈ {1,2,...,n} then
3: K
l
← g
γ
l
4: bk
1
= g
β
5: for all av
attr
i, j
∈ BT G do
6: bk
2
= (Π(H
2
(av
attr
i, j
)))
β
7: bk
3
= K
l
· e(g
β
,g
ρ
)
8: BK
l
← (bk
1
,bk
2
,bk
3
)
6. Extract (msk,S): For any subset S ⊆ {1,...,n}
which contains all the indices of document sets,
the algorithm outputs aggregate key k
agg
by com-
puting:
k
agg
= Π
j∈S
g
γ
j
The data owner securely sends k
agg
and a set S to
the user, to delegate the keyword search and data
access rights of the ciphertexts within set S.
7. Revocation(U
l
,msk,l): The algorithm outputs re-
vocation list RL
l
for document l, on giving input
of master-secret key and a set of revoked users’
identities U
l
whose delegate rights needs to be
revoked over document doc
l
. The l
th
document
must not be either accessed or searched by any
user U
l
i
∈ U
l
. The cloud server checks the user’s
authorization using RL
l
at the time of receiving
any request for document l (such as access or
search request). Algorithm 4 gives a formal de-
scription of Revocation operation.
Algorithm 5: Revocation(U
l
,msk,l) → RL
l
.
1: Select r ∈ Z
p
2: RL
1
← g
rγ
l
3: RL
2
←(Π
U
l
i
∈U
l
U
γ
l
i
)
r
4: RL
l
← (RL
1
,RL
2
)
5: Data owner stores revocation list RL
l
on the cloud
server.
8. ReKeygen(pk, pk
0
): This algorithm outputs re-
encryption key rk by computing:
rk = pk
0
/pk = g
γ
0
/g
γ
9. ReEncrypt(rk,SK,S
0
): On receiving the re-
encryption request from DU, proxy server first
matches user attribute token SK with the hidden
access policy A
l
|∀l ∈ S
0
defined by the data owner.
If the attribute token SK satisfies the access policy
A
l
, then the cloud server re-encrypt C
l
using the
re-encryption key rk and calculates re-encrypted
ciphertext C
R
l
by following the steps as shown in
Algorithm 6. Algorithm 6 gives a formal descrip-
tion of ReEncrypt operation.
Algorithm 6: ReEncrypt (rk, SK,S
0
) → C
R
l
|∀l ∈ S
0
.
1: for all l ∈ S
0
do
2: Y
l
←
C
6
·e(S
0
,C
5
)
e(C
1
,S
1
)
3: If SK A
l
, then Y
l
= l otherwise it gets
any random value which indicates SK 2 A
l
.
4: if Y
l
= l then
5: C
R
1
← C
1
,C
R
2
← C
2
∗ rk
6: C
R
3
← C
3
, C
R
4
← C
4
7: C
R
5
← C
5
, C
R
6
← C
6
8: Stores the ciphertext C
R
l
on the cloud server
10. TrapdoorGen(k
agg
,
−→
Q ): The user who wants to
perform the keyword search over the shared data,
runs this algorithm and generates a single aggre-
gate trapdoor Tr. If the set S of documents are in
the range of an aggregate key k
agg
, then the user
having trapdoor Tr can search over any document
in the range of set S. Algorithm 7 gives a formal
description of TrapdoorGen() operation.
Algorithm 7: TrapdoorGen(k
agg
, Q)→ Tr.
1: Select b ∈ Z
p
2: Tr
0
← {k
agg
· Π(H(w
i, j
))
b
}
w
i, j
∈
−→
Q
3: Tr
1
← g
b
4: Tr ←(Tr
0
,Tr
1
)
5: The user submits (Tr,S) to the cloud server.
11. Test (Tr, S,l,U
QR
): To check if document doc
l
contains query keyword(s) within set
−→
Q or not,
the cloud server follows steps as shown in Al-
gorithm 8. Algorithm 8 gives a formal descrip-
tion of Test operation. In the following discussion
U
QR
∈ U is an identity of query requester and U
l
is a set of revoked users’ identities corresponding
to list RL
l
.
12. Decrypt (k
agg
,S,l,C
l
): If l /∈ S, Decrypt algorithm
outputs NULL. Otherwise, returns the output:
M = C
4
e(k
agg
pub
1
l
pub
2
l
, C
1
) /e(pub
3
, C
2
)
e(pub
4
, C
1
)
{pub
1
l
}
l∈S
= {Π
j∈S
g
j+l
}
l∈S
{pub
2
l
}
l∈S
= {Π
j∈S, j6=l
g
n+1− j+l
}
l∈S
pub
3
= Π
j∈S
g
j
pub
4
= Π
j∈S
g
n+1− j+l
For efficiency consideration, the parameters
({pub
1
l
, pub
2
l
}
l∈S
, pub
3
, pub
4
) for the set S is
computed only once.
SECRYPT 2019 - 16th International Conference on Security and Cryptography
118

Algorithm 8: Test (Tr,S,l,U
QR
)→ R ∈ {0,1}.
1: if Revoked(U
QR
,RL
l
,U
l
,l) 6= 1 then
2: if l ∈ S then
3: pub
0
1
= Π
j∈S
g
j+l
4: pub
0
2
= Π
j∈S
g
j
5: R = e(Tr
0
· pub
0
1
,C
1
) / e(pub
0
2
,C
2
)
e(C
KW
1
,Tr
1
)
6: if R = 1 then
7: Add doc
l
to the search result list
8: Return R
9: if l /∈ S then
10: Return Failure
11: if Revoked(U
QR
,RL
l
,U
l
,l) = 1 then
12: Return Failure
13: FUNCTION Revoked(U
QR
,RL
l
,U
l
,l)
14: pub
0
← Π
U
l
i
∈U
l
,U
l
i
6=U
QR
U
l
i
15: Y ← e(RL
l
2
,g
l
)/e(U
QR
· pub
0
,RL
l
1
)
16: Return Y
13. BTG Access(SK,l, U
QR
): On giving input of the
attribute token SK, identity of query requester
U
QR
, and the data class l, the cloud server follows
steps as shown in Algorithm 9. Algorithm 9 gives
a formal description of BTG Access operation.
Algorithm 9: BTGAccess(SK,l, U
QR
)→ M.
1: if Revoked(U
QR
,RL
l
,U
l
,l) 6= 1 then
2: if Available
i
= 0|∀Au
l
i
∈ Au
l
then
3: Take the attribute token SK = (S
0
,S
1
) of
user U
QR
and match SK with the break-glass pol-
icy of l
th
document BTG
l
.
4: if SK BTG
l
then
5: K
l
←
bk
3
·e(S
0
,bk
2
)
e(bk
1
,S
1
)
6: Using K
l
user U
QR
can access C
l
.
7: M = C
4
e(K
l
pub
1
l
pub
2
l
, C
1
)
/e(pub
3
, C
2
) e(pub
4
, C
1
)
8: Here, while computing parameters
(pub
1
l
, pub
2
l
, pub
3
, pub
4
), the set S contains only
one element, i.e., l itself.
9: elseReturn Failure
10: if Revoked(U
QR
,RL
l
,U
l
,l) = 1 then
11: Return Failure
12: FUNCTION Revoked(U
QR
,RL
l
,U
l
,l)
13: pub
0
← Π
U
l
i
∈U
l
,U
l
i
6=U
QR
U
l
i
14: Return Y ← e(RL
l
2
,g
l
)/e(U
QR
· pub
0
,RL
l
1
)
4.1 Analysis of the BTG-RKASE
The correctness of Test algorithm can be realized as
follows:
If the query requester U
QR
is revoked user, then
= e(RL
2
,g
l
)/e(U
QR
· pub
0
,RL
1
)
= e((Π
U
l
i
∈U
l
U
l
i
)
γr
,g
l
)/e(U
QR
·Π
U
l
i
∈U
l
,U
l
i
6=U
QR
U
l
i
,g
γr
l
) = 1
Therefor, if identity of query requester is within
set of revoked users then Test algorithm outputs fail-
ure. Then, user is no longer permitted to search on the
l
th
document.
Now, consider the case U
QR
/∈ U
l
, i.e., query re-
quester is not the revoked user. If the user’s query
trapdoor Tr matches with the keyword ciphertext
C
−−→
KW
, then Test algorithm outputs:
e(Tr
0
· pub
0
1
,C
1
) / e(pub
0
2
,C
2
) e(C
KW
1
,Tr
1
)
=
e(Tr
0
· pub
0
1
,C
1
)
e(pub
0
2
,C
2
) e(C
KW
1
,Tr
1
)
=
e(k
agg
· Π(H(w
i, j
))
b
· Π
j∈S
g
j+l
,g
t
)
e(Π
j∈S
g
j
,(v · g
l
)
t
) e(Π(H(w
i, j
))
t
,g
b
)
=
e(k
agg
,g
t
) e(Π(H(w
i, j
))
b
,g
t
) e(Π
j∈S
g
j+l
,g
t
)
e(Π
j∈S
g
j
,g
γt
) e(Π
j∈S
g
j
,g
t
l
) e(Π(H(w
i, j
))
t
,g
b
)
= 1
The correctness of BTG Access algorithm can be
realized as follows:
If the user’s attribute token SK satisfies the
break-glass policy BT G of the document doc
l
, then
BTG Access algorithm outputs
bk
3
· e(S
0
,bk
2
)
e(bk
1
,S
1
)
=
K
l
· e(g,g)
βρ
e(g
r
,(Π(H
2
(av
attr
i, j
)))
β
)
e(g
β
,g
ρ
(Π(H
2
(av
attr
i, j
)))
r
)
= K
l
Using K
l
user can access document doc
l
.
BTG Access outputs as follows:
C
4
e(K
l
pub
1
l
pub
2
l
, C
1
) /e(pub
3
, C
2
) e(pub
4
,
C
1
)
=
C
4
e(g
γ
l
· Π
j∈S
g
j+l
· Π
j∈S, j6=l
g
n+1− j+l
,g
t
)
e(Π
j∈S
g
j
,(v · g
l
)
t
) e(Π
j∈S
g
n+1− j+l
,g
t
)
=
C
4
e(g
γ
l
,g
t
) e(Π
j∈S
g
j+l
,g
t
) e(Π
j∈S, j6=l
g
n+1− j+l
,g
t
)
e(Π
j∈S
g
j
,g
γt
) e(Π
j∈S
g
j
,g
t
l
) e(Π
j∈S
g
n+1− j+l
,g
t
)
=
M e(g
1
,g
n
)
t
e(Π
j∈S
g
n+1− j+l
,g
t
)
e(g
n+1
,g
t
)
e(Π
j∈S
g
n+1− j+l
,g
t
)
=
M e(g
1
,g
n
)
t
e(g
n
,g
1
)
t
= M
BTG-RKASE: Privacy Preserving Revocable Key Aggregate Searchable Encryption with Fine-grained Multi-delegation Break-The-Glass
Access Control
119

5 SECURITY ANALYSIS
Theorem 1. If the decisional DDH assumption hold
in (G,G
T
), then the proposed BTG-RKASE scheme
preserves the keyword privacy in the random oracle
model.
Proof.
We consider a challenger C , a simulator S I M
and a polynomial-time adversary A. We assume
that the adversary A has a non-negligible advantage
ε(l) to break the privacy of our scheme. Then, we
can construct simulator SI M that breaks the de-
cisional DDH problem ς= (g, g
a
, g
b
, g
c
, R) with
the probability Pr|Abreaks decisional DDH| ≥ 1/2 +
ε(1−(q
re
+q
test
+q
dec
)·τ−Pr|Abreaks break-the-glass policy|
2e·q
Tr
Here, q
re
,q
test
,q
Tr
are the number of queries to
re-encryption oracle, test oracle, and trapdoor gener-
ation oracle, respectively. τ is the maximum prob-
ability that any given signature verification token is
output by G and it is assumed to be very negligible.
Moreover, Pr|Abreaks break-the-glass policy| is also
very negligible as per our assumption.
On DDH input (g,g
a
,g
b
,g
c
,R), simulator S I M
aims to decide if R = g
abc
.
The challenger C generates a,b,c,z ∈
R
Z
p
, bilin-
ear groups G,G
T
with prime order p and the mapping
G × G → G
T
. g is a generator of group G. The chal-
lenger C computes X as follows:
R =
(
g
abc
,(X = 0)
g
z
,(X = 1)
The challenger gives instance (g, g
a
, g
b
,g
c
, R)∈
G
T
to simulator SI M .
SI M interacts with A (SIM simulates the C for
A) and starts the simulation as follows.
Init Phase. The adversary A selects a set of cor-
rupted users denoted by CoList sends it to the chal-
lenger. The adversary also commits two ciphertext
access policies T
∗
0
and T
∗
1
and challenge index i
c
for
which he wishes to be challenged upon.
Setup. The simulator SI M generates system param-
eters SP=(g, g
1
,.. . ,g
n
,g
n+2
,. ..,g
2n
).
Here, g
l
= (g
a
)
α
l
∈ G for l = {1,2,.. .,n,n +
2,. ..,2n}.
Moreover, S I M simulates the hash oracles for
keyword and attribute as follows:
• O
H
1
: Given a keyword w
i
, having value w
i, j
, the
hash function proceeds as follows:
– If w
i, j
has not been queried before, then S I M
toss a random coin c
i
∈ {0,1} with the proba-
bility that Pr|c
i
= 0| = 1/(q
T
+ 1), where q
T
is
very large number. We require that q
T
should
be larger than the number of oracle queries
for O
k
agg
,O
Tr
,O
test
. If c
i
= 0, then selects
f ∈ Z
p
and computes T
∗
w
i, j
= (g
f
)
c
. Other-
wise, computes T
∗
w
i, j
= (g
f
)
bc
. Add the tuple
< w
i
,w
i, j
,c
i
,T
∗
w
i, j
> to table T
kw
and return T
∗
w
i, j
.
– Otherwise, retrieve T
∗
w
i, j
from table T
kw
with re-
spect to w
i, j
and return T
∗
w
i, j
• O
H
2
: Given a attribute value av
attr
i, j
, it proceeds
as follows:
– If av
attr
i, j
has not been queried before, then toss
a random coin c
i
∈ {0, 1}. If c
i
= 0, then selects
a random value h ∈
R
Z
p
and computes T
av
attr
i, j
= (g
h
)
c
. Otherwise, computes T
av
attr
i, j
= (g
h
)
bc
.
Add the tuple < attr,c
i
,v
i, j
,T
av
attr
i, j
> to table
T
attr
and return T
attr
.
– Otherwise, retrieve T
av
attr
i, j
from table T
attr
with
respect to attr and return T
av
attr
i, j
Query Phase 1. The simulator SI M constructs
following oracles and adversary A can adaptively
queries q
1
,...., q
n
to these oracles in polynomial for
multiple times.
• Uncorrupted Key Generation Oracle O
pk
: On
input an index i, if corrupted
i
= 1, then S I M sets
public-key pk
i
= v =g
γ
i
where γ
i
∈
R
Z
p
; otherwise,
SI M computes pk
i
= v =(g
c
)
γ
i
. Finally, S I M
records the tuple < pk
i
,γ
i
,corrupted
i
> in table
T
k
and responds A with pk
i
and sk
i
= ρ
i
where
ρ
i
∈
R
Z
p
. Table T
k
is used to records the outputs
of O
pk
and O
msk
and these records will be used in
other oracles to response the queries.
• Corrupted Key Generation Oracle O
msk
: On
input of pk
i
, S I M checks whether pk
i
oc-
curs in T
k
, if not, SI M terminates. Other-
wise, if corrupted
i
= 0, SI M terminates. If
corrupted
i
= 1, S I M responds A with (pk
i
=
g
γ
i
,msk
i
= γ
i
,sk
i
= ρ
i
), and records the tuple <
pk
i
,γ
i
,corrupted
i
> in table T
k
• Attribute Token Generation Oracle O
SK
:
Whenever A makes its i
th
attribute token gen-
eration query for the set L
i
of attributes such
that F(L
i
,T
∗
0
) = F(L
i
,T
∗
1
) = 1 or F(L
i
,T
∗
0
) =
F(L
i
,T
∗
1
) = 0, i.e., F(L
i
,T
∗
0
) = F(L
i
,T
∗
1
).
Specifically, A is allowed to issue a valid attribute
token generation query which can satisfy chal-
lenge access policy, with the restriction that the to-
ken should satisfy both the challenge access struc-
ture T
∗
0
and T
∗
1
. The simulator S I M selects a
random values r
i
∈
R
Z
p
and computes the attribute
token as follows:
SECRYPT 2019 - 16th International Conference on Security and Cryptography
120

SK =< S
0
,S
1
>= < g
r
i
,g
ρ
i
(Π(H
2
(av
attr
j,k
)))
r
i
>
|∀av
attr
j,k
∈ L
i
• Aggregate Key Generation Oracle O
k
agg
: On
giving input of (msk
i
,S) by the adversary,where
msk
i
is master secret key corresponding to pk
i
,
the simulator checks that key pair (pk
i
,msk
i
) oc-
curs in table T
k
, if not, S I M reports failure and
terminates. Otherwise, it returns an aggregate
key k
agg
i
← Extract(msk
i
,S) and add the tuple
< k
agg
i
,msk
i
,S > in table T
k
agg
. The adversary A
cannot ask for the aggregate key corresponding to
a set S that includes an index i
c
.
• Re-encryption Key Generation Oracle O
rk
: On
giving input of (pk
i
, pk
j
) by the adversary, S I M
checks whether pk
i
, pk
j
occur in T
k
,if not, S I M
terminates. Otherwise SI M does the following
operations:
– If corrupted
i
= corrupted
j
, SI M responds A
with pk
j
/pk
i
– If corrupted
i
6= corrupted
j
, SI M aborts
• Re-encryption Oracle O
re
: On giving in-
put of (rk,S
0
), where re-encryption key
rk ←ReKeygen(pk, pk
0
), SI M checks whether
pk
i
, pk
j
occur in T
k
and pk, pk
0
are from O
pk
or
O
msk
,if not, S I M terminates. Otherwise, SIM
performs as following:
– If corrupted
i
= corrupted
j
, SI M responds A
with re-encrypted ciphertext (C
R
i
|∀l ∈ S
0
) ←
ReEncrypt(rk,SK, S
0
)
– If corrupted
i
6= corrupted
j
, SI M aborts
• Trapdoor Generation Oracle O
Tr
: On input
(k
agg
i
,
−→
Q ), the simulator proceeds as follows:
– It queries O
H
1
∀w
j,k
∈
−→
Q and obtain
(w
j,k
,c
j
,w
j,k
,T
∗
w
j,k
)
– If corrupted
i
= 1, set trapdoor Tr ←
TrapdoorGen(k
agg
i
,
−→
Q )
– If corrupted
i
= 0 ∧ c
j
= 1, set trapdoor Tr ←
TrapdoorGen(k
agg
i
,
−→
Q )
– Otherwise, report failure and terminate.
• Test Oracle O
test
: On giving input of (Tr ←
TrapdoorGen(k
agg
i
,
−→
Q ),S,l), S I M checks k
agg
i
occurs in table T
k
agg
, if yes, SI M returns output
of Test(Tr,S,l,U
QR
) to the adversary. Otherwise,
SI M returns null.
Challenge Phase. The attacker A sends the chal-
lenger two equal length set of keywords
−−→
KW
0
;
−−→
KW
1
on which it wishes to be challenged along with an in-
dex i
c
, a message M from message space, a public
key pk
∗
, secret key sk, and the challenge access pol-
icy T
∗
0
and T
∗
1
. Here, the restriction is that if for any
attribute token generated in Phase 1 on an attribute list
L, F(L, T
∗
0
) = F(L,T
∗
1
) = 1 then
−−→
KW
0
=
−−→
KW
1
. If pk
∗
is not in table T
k
or corrupted
∗
= 1, then simulator
SI M terminates. If H
1
(
−−→
KW
0
) = 1 and H
1
(
−−→
KW
1
) = 1,
then the simulator returns ’failure’ and aborts. Other-
wise, the simulator S I M chooses d ∈ {0,1} as fol-
lows:
• If H
1
(
−−→
KW
0
) = 1 and H
1
(
−−→
KW
1
) = 0, then set d = 1
• If H
1
(
−−→
KW
0
) = 0 and H
1
(
−−→
KW
1
) = 1, then set d = 0
• otherwise, let d ←
R
{0,1}
The challenger runs
Encrypt(pk,sk,i
c
,M,
−−→
KW
d
,T
∗
d
) and returns ciphertext
C
∗
d
to the adversary.
The Challenger C sets t = a and computes cipher-
text for
−−→
KW
d
and access policy T
∗
d
as follows:
C
∗
1
= g
a
; C
∗
2
= (v · g
l
)
a
C
∗
3
= C
−−→
KW
= Π(H
1
(w
i, j
))
a
|∀w
i, j
∈
−−→
KW
d
C
∗
4
= C
M
= M e(g
1
, g
n
)
a
C
∗
5
= Π(H
2
(av
attr
i, j
)))
a
|∀attr
i, j
∈ T
∗
d
C
∗
6
= i
c
· e(g
a
,g
ρ
)
Query Phase 2. Same as Phase 1, the adversary asks
for more queries q
n+1
,....., q
n
2
except the following
oracles:
• Trapdoor Generation Oracle O
Tr
: On giving in-
put of (k
agg
,
−→
Q ) by the adversary, the challenger
answers same as that in phase 1, except the fol-
lowing cases:
– The adversary had previously ask for the trap-
door corresponding to a set of keywords
−−→
KW
0
or
−−→
KW
1
–
−→
Q =
−−→
KW
0
or
−→
Q =
−−→
KW
1
If one of the above condition holds, then chal-
lenger returns null.
• Test Oracle O
test
: On input of Test(Tr,S,l,U
QR
),
if i
c
= l or i
c
∈ S, then the challenger returns null.
Otherwise the challenger responds as that in phase
1
Guess. The adversary A outputs its guess d
0
∈ {0,1}
for d.
If d
0
= d , then SI M outputs X
0
= 0 . If d
0
6= d ,
then SI M outputs X
0
= 1.
This completes the simulation.
If S I M does not report failure and it receives
DDH instances as input, the challenge ciphertext is
a valid encryption of (pk
∗
,i
c
,M,
−−→
KW
d
,T
∗
d
) and A
guesses d
0
= d with the advantage l. If SI M does
BTG-RKASE: Privacy Preserving Revocable Key Aggregate Searchable Encryption with Fine-grained Multi-delegation Break-The-Glass
Access Control
121

not receives DDH instances as input, the challenge
ciphertext does not contain information about
−−→
KW
d
since keyword ciphertext is uniformly distributed in
G
T
and independent of d. The adversary A guesses
d
0
= d with exactly 1/2 probability.
We analyze the probability that the simulator does
not report failure or abort during the simulation.
When A asks for trapdoor to oracle O
Tr
, it
happens H
1
(kv
w
j,k
) = 0 for some keyword w
j,k
and it makes simulator to respond with failure.
The probability that the simulator SI M aborts is
Pr[H
1
(kv
w
j,k
) = 0]= 1/(q
Tr
+ 1). Therefore, as A
makes at most q
Tr
oracle queries, the probability of
the simulator not reporting failure and aborting is
(1 − 1/(q
Tr
+ 1))
q
Tr
≥ 1/e
The only situation that SIM reports failure
during challenge phase is that H
1
(
−−→
KW
0
) = 1 and
H
1
(
−−→
KW
1
) = 1. Since Pr[H
1
(
−−→
KW
d
) = 0]= 1/(q
Tr
+
1) for d ∈ {0, 1} and the values of H
1
(
−−→
KW
0
) and
H
1
(
−−→
KW
1
) are independent of A. Furthermore, these
two values are independent of each other. Hence, we
have
Pr|H
1
(
−−→
KW
0
) = 1∧ H
1
(
−−→
KW
1
) = 1| = (1 −1/(q
Tr
+
1))
2
≤ 1 − 1/q
Tr
Hence, the probability that the simulator has no
failure state is at least 1/q
Tr
.
Therefore, the simulator simulates without failure
with the probability at least 1/e + 1/q
Tr
.
Let us analyze the advantage of the simulator solv-
ing DDH problem on condition that the simulation
completes perfectly.
Based on this, there will be two cases as follows:
case(i): if X = 0, then Z = g
abc
and hence challenge
ciphertext is a correct ciphertext of keyword
−−→
KW
d
.
Then, the probability of A guessing correctly d = d
0
is 1/2 + ε.
case(ii): if X = 1, then the challenge ciphertext is in-
dependent of
−−→
KW
0
and
−−→
KW
1
, so that A can not ob-
tain any information of d. Then, the probability of A
guessing correctly d = d
0
is 1/2.
From (i) and (ii), it follows that SI M ’s advantage
in this DDH game can be computed as:
=
1
2
(
1
2
+ ε) +
1
2
1
2
=
1
2
+
ε
2
Therefore, if the A has a non-negligible advan-
tage ε in the above game then we can build a simula-
tor (SI M ) which can break the DDH problem with
non negligible quantity = (
1
e
+
1
q
Tr
)
ε
2
, which is an in-
tractable problem.
Theorem 2. If the decisional DDH assumption hold
in (G,G
T
), then the proposed BTG-RKASE scheme
preserves the trapdoor privacy in the random oracle
model.
Proof. The proof of Theorem 2 is similar to the proof
of Theorem 1.
6 EMPIRICAL EVALUATION
In this section, we evaluate and analyze the compu-
tational cost of different algorithms of the proposed
scheme.
6.1 Implementation Details
In order to evaluate the performance, we implement
the prototype of our scheme and conduct the ex-
periments using Java Pairing Based Cryptographic
(JPBC) library (De Caro and Iovino, 2011). We con-
ducted experiments as follows: client implementa-
tions were executed in a personal computer with 64
bit Intel(R) Core(TM) i5 -7200U CPU @ 2.50 GHz
with Windows10 OS; server implementations were
deployed in the Amazon AWS cloud, using an EC2
M5 large instance. Communications were performed
on a 10MB/s connection, with 26.932ms round-trip
time. We used the official Medicare.gov Hospital
Compare datasets provided by the Centers for Medi-
care and Medicaid Services (Hos, 2019). Each doc-
ument is fixed to 10 KB with random words cho-
sen from a dictionary and the query is also contain-
ing some random keywords. We use Type A pairing
for evaluation and it is the fastest (symmetric) pairing
among all types of curves. Type A pairings are con-
structed on the curve y
2
= x
3
+ x over the field F
q
for
some prime q = 3 mod 4.
6.2 Experimental Results
The time cost of Setup() is linear in the maximum
number of documents belonging to the data owner
(Figure 3a). Figure 3b shows the computational cost
of KeyGen() approximate to a constant. The com-
putational cost of AttrGen() is linear in number of
attributes, as shown in Figure 3c. The results given
in Figure 3d and Figure 3e show that the compu-
tational overhead of Encrypt() is linear in the num-
ber of keywords to be attached with the ciphertext
and number of attributes in the access policy. Fig-
ure 3f show that the computational overhead of Key-
Gen BTG() is linear in the number of attributes in
the break-glass policy. Figure 3g shows the compu-
tational time of Extract() is linear in the number of
shared documents. The computational cost of Revo-
cation() is linear in the number of revoked users, as
SECRYPT 2019 - 16th International Conference on Security and Cryptography
122

(a) Time cost of Setup() (b) Time cost of KeyGen() (c) Time cost of AttrGen() (d) Time cost of Encrypt()
based on number of keywords
(e) Time cost of Encrypt()
based on number of attributes
in access policy
(f) Time cost of Key-
Gen BTG() based on number
of attributes in break-glass
policy
(g) Time cost of Extract() (h) Time cost of Revocation() (i) Time cost of TrapdoorGen() (j) Time cost of ReKeygen()
(k) Time cost of ReEncrypt() (l) Time cost of Test() based on
number of keywords
(m) Time cost of Test() based
on number of shared docu-
ments
(n) Time cost of Decrypt() (o) Time cost of BTG Access()
Figure 3: The computational cost of BTG-RKASE algorithms().
shown in Figure 3h. Figure 3i shows the computa-
tional time of TrapdoorGen() is linear in the number
of keywords within search query set. Figure 3j shows
the computational time of ReKeygen() approximate
to a constant. Figure 3k shows that the computational
time of ReEncrypt() is linear in number of documents
to be re-encrypted. The execution time of Test() is lin-
ear in the number of shared documents (Figure 3m),
whereas in case of multi-keyword search the compu-
tational time of Test() remains constant with respect
to the number of keywords in the query set (Figure3l).
Figure 3n show that the cost of decryption is in linear
with the number of documents. Figure 3o show the
computational time of verification of break-the-glass
policy is constant as it require only 2 pairing opera-
tions, independent of number of attributes.
7 CONCLUSIONS AND FUTURE
EXTENSION
The main contribution of this paper is to provide a
mechanism which can handle emergency situations
where no authorized user exists to perform (or to dele-
gate) a time-critical task. The proposed BTG-RKASE
system supports three ways for searchable group data
sharing and accessing encrypted dataset: delegation,
policy-based fine-grained multi-delegation and break-
the-glass access. In normal situations, the authorized
user with the delegated key can access the shared
dataset, provided ciphertext class is within the range
of aggregate key. In fine-grained multi-delegation
mode, if the attributes of the delegatee satisfy the hid-
den access policy (defined by the data owner), the
delegatee can delegate his received rights to another
user. The expensive computation of re-encryption
required for multi-delegation is outsourced to proxy
server without compromising the data confidentiality.
In exceptional situation (when the authorized users
are not available), the break-glass access mechanism
allow timely access to the data, provided the attributes
of the user satisfy the break-the-glass policy. The
proposed scheme also allows revocation of delegated
rights even in case of multi-delegation. The other con-
tribution of the proposed approach is that it supports
multi-keyword search over the shared dataset using a
BTG-RKASE: Privacy Preserving Revocable Key Aggregate Searchable Encryption with Fine-grained Multi-delegation Break-The-Glass
Access Control
123

single trapdoor (instead of multiple trapdoors). Our
performance evaluation and simulation results indi-
cated that the proposed method is efficient and secure.
In future, we plan to design an trust and risk-based
auto-delegation mechanism which can respond auto-
matically to the absence of appropriately authorized
users, after finding the legitimacy of the user (based
on trust and risk value) for emergency access.
ACKNOWLEDGMENTS
The second author acknowledges the support received
from Indian Institute of Technology Jammu under the
Faculty Professional Development Grant and the first
author acknowledges the Visveswaraya PhD Support
Scheme at Sardar Vallabhbhai National Institute of
Technology, Surat.
REFERENCES
(2019). Hospital compare. available at
https://data.medicare.gov/data/hospital-compare,
accessed on February 13, 2019.
Ardagna, C. A., Di Vimercati, S. D. C., Foresti, S., Grandi-
son, T. W., Jajodia, S., and Samarati, P. (2010). Access
control for smarter healthcare using policy spaces.
Computers & Security, 29(8):848–858.
Ardagna, C. A., di Vimercati, S. D. C., Grandison, T., Ja-
jodia, S., and Samarati, P. (2008). Regulating excep-
tions in healthcare using policy spaces. In IFIP An-
nual Conference on Data and Applications Security
and Privacy, pages 254–267. Springer.
Banu, A. S. (2015). Efficient data sharing in cloud medium
with key aggregate cryptosystem. Networking and
Communication Engineering, 7(3):118–121.
Blaze, M., Bleumer, G., and Strauss, M. (1998). Divertible
protocols and atomic proxy cryptography. Advances
in Cryptology—EUROCRYPT’98, pages 127–144.
Cheon, J. H. (2006). Security analysis of the strong diffie-
hellman problem. In Advances in Cryptology - EU-
ROCRYPT 2006, pages 1–11. Springer Berlin Heidel-
berg.
Chu, C.-K., Chow, S. S., Tzeng, W.-G., Zhou, J., and Deng,
R. H. (2014). Key-aggregate cryptosystem for scal-
able data sharing in cloud storage. IEEE transactions
on parallel and distributed systems, 25(2):468–477.
Crampton, J. and Khambhammettu, H. (2008). On delega-
tion and workflow execution models. In Proceedings
of the 2008 ACM symposium on Applied computing,
pages 2137–2144. ACM.
Cui, B., Liu, Z., and Wang, L. (2016). Key-aggregate
searchable encryption (kase) for group data sharing
via cloud storage. IEEE Transactions on computers,
65(8):2374–2385.
Dang, H., Chong, Y. L., Brun, F., and Chang, E.-C. (2016).
Practical and scalable sharing of encrypted data in
cloud storage with key aggregation. In Proceedings
of the 4th ACM Workshop on Information Hiding and
Multimedia Security, pages 69–80. ACM.
De Caro, A. and Iovino, V. (2011). jpbc: Java pairing
based cryptography. In Computers and communica-
tions (ISCC), 2011 IEEE Symposium on, pages 850–
855. IEEE.
Ferreira, A., Cruz-Correia, R., Antunes, L., Farinha, P.,
Oliveira-Palhares, E., Chadwick, D. W., and Costa-
Pereira, A. (2006). How to break access control in
a controlled manner. In Computer-Based Medical
Systems, 2006. CBMS 2006. 19th IEEE International
Symposium on, pages 847–854. IEEE.
Joint, N. (2004). Break-glass: An approach to granting
emergency access to healthcare systems. COCIR/JIRA
Security And Privacy Committee (SPC).
Kiayias, A., Oksuz, O., Russell, A., Tang, Q., and Wang, B.
(2016). Efficient encrypted keyword search for multi-
user data sharing. In European Symposium on Re-
search in Computer Security, volume NA, pages 173–
195. Springer.
Li, T., Liu, Z., Jia, C., Fu, Z., and Li, J. (2018). Key-
aggregate searchable encryption under multi-owner
setting for group data sharing in the cloud. Interna-
tional Journal of Web and Grid Services, 14(1):21–43.
Li, T., Liu, Z., Li, P., Jia, C., Jiang, Z. L., and Li, J. (2016).
Verifiable searchable encryption with aggregate keys
for data sharing in outsourcing storage. In Informa-
tion Security and Privacy, pages 153–169. Springer
International Publishing.
Mahalle, R. V. and Pawade, P. P. A review of secure data
sharing in cloud using key aggregate cryptosystem
and decoy technology. International Journal of Sci-
ence and Research (IJSR), 3.
Marinovic, S., Craven, R., Ma, J., and Dulay, N. (2011).
Rumpole: a flexible break-glass access control model.
In Proceedings of the 16th ACM symposium on Access
control models and technologies, pages 73–82. ACM.
Padhya, M. and Jinwala, D. (2018). Mulkase - a novel
approach for key aggregate searchable encryption for
multi-owner data. Frontiers of Information Technol-
ogy Electronic Engineering, -1(-1).
Patranabis, S., Shrivastava, Y., and Mukhopadhyay, D.
(2015). Dynamic key-aggregate cryptosystem on el-
liptic curves for online data sharing. In Interna-
tional Conference in Cryptology in India, pages 25–
44. Springer.
Sahai, A., Waters, B., et al. (2005). Fuzzy identity-based
encryption. In Eurocrypt, volume 3494, pages 457–
473. Springer.
Sandhu, R. S., Coyne, E. J., Feinstein, H. L., and Youman,
C. E. (1996). Role-based access control models. Com-
puter, 29(2):38–47.
Schaad, A. and Moffett, J. D. (2002). Delegation of obli-
gations. In Policies for Distributed Systems and Net-
works, 2002. Proceedings. Third International Work-
shop on, pages 25–35. IEEE.
Zhou, R., Zhang, X., Du, X., Wang, X., Yang, G., and
Guizani, M. (2018). File-centric multi-key aggregate
keyword searchable encryption for industrial internet
of things. IEEE Transactions on Industrial Informat-
ics.
SECRYPT 2019 - 16th International Conference on Security and Cryptography
124
