
Design and Research of Bayesian Reasoning Method based on
Wireless Intelligent Nodes
Ruoyu Liu
1, a
, Ming Li
1, b
, Chunlan Jiang
1, c
and Luwei Liu
1, d
1
The School of Mechatronical Engineering, Beijing Institue of Technology, 5 South Zhongguancun, Beijing, China
Keywords: Unmanned system, DBN, decision-making, semi-physical simulation experiment.
Abstract: Aiming at the multi-attribute decision problem of networked ammunition, the research of intelligent
decision method is carried out. Based on the tasks of blocking the key areas in wild, the main factors
affecting the decision are analysed. According to the inherent logical relationship of each factor, a decision
model based on Dynamic Bayesian Network (DBN) is proposed. In addition, in order to better verify the
practical performance of the reasoning method, a simulation system including software and hardware is
designed. The wireless intelligent node includes self-positioning module, communication module, detection
module, signal processing module, feedback module, core processing module and power module. Software,
used Visual Studio 2015 as the development platform, it is based on C# language and includes modules
such as interactive display, communication and algorithm. Through the system test and semi-physical
simulation experiments, the practicability and effectiveness of the reasoning method are verified, which
proves that it can provide support for research and practical use.
1 INTRODUCTION
Networked ammunition is a new type of ammunition
generated by the development of new technologies
such as autonomous networks, situational awareness,
and mission planning. It is a kind of smart weapon
that contains multiple sensors, multiple damage
modes, and multiple nodes to coordinate attacks. It
can be manually deployed, rocket bombs and
airborne dispensers, with the characteristics of small
size, low cost and high efficiency. Multiple
functions can be achieved, such as autonomous
positioning, automatic alert, multi-mode detection,
identification and tracking targets and attack
decisions (
Li Ming, Luo Guohua and Jiang Chunlan,
2017)
Both domestic and foreign research have made
substantial progress and put into use, such as the US
XM-7 “Spider” anti-infantry mine and XM1100
“Scorpion” intelligent ammunition (
Zhao Yuqing, Niu
Xiaomin, Wang Xiaobo and Xia Muquan, 2012), Russian
M225 intelligent ammunition, German “Leap”
intelligent ammunition. Comprehensively, they
already have the ability to use in the battlefield.
Each submunition is a decentralized and
independent wireless intelligent node in networked
ammunition, which is a decentralized information
unit with sensing, communication and decision
functions, which can realize information fast flow
and sharing, interconnection and
intercommunication (
Chen Xiaoqing, 2019).
In the process of battlefield use, networked
ammunition’s functions and tasks are more and more
complicated. The importance of how to make attack
decisions is increasingly prominent. While Bayesian
network (BN) theory is an effective way to solve
uncertain problems, it is similar to human brain
thinking logic and can be represented by directed
acyclic graph (DAG). Dynamic Bayesian network
(DBN) is an extension of the BN theory (
Xiao
Qinkun, Gao Song and Gao Xiaoguang, 2007)
. Due to
the addition of time factors, in addition to the basic
functions of BN, DBN also has the ability to process
time series data
(Ma Guopu, Sha Jichang, Chen Liangjun,
Chen Chao and Jiang Xin, 2010). It has been fully
applied in the fields of automatic driving, risk
assessment and group robot. This paper focus on the
actual task and uses Bayesian network as the
knowledge framework to study the attack decision
problem, in addition, a development system is
carried out.
Liu, R., Li, M., Jiang, C. and Liu, L.
Design and Research of Bayesian Reasoning Method based on Wireless Intelligent Nodes.
DOI: 10.5220/0008874404670473
In Proceedings of 5th International Conference on Vehicle, Mechanical and Electrical Engineering (ICVMEE 2019), pages 467-473
ISBN: 978-989-758-412-1
Copyright
c
2020 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
467

2 SYSTEM COMPOSITION
The system includes a central node, parent nodes,
sub nodes and a command terminal. The network
topology is a single-center and multi-cluster
network. The structure of the system is shown in
Figure1. The node network status is randomly
generated by the networking program. The central
node collects the information of the nodes in the
network and sends to the command terminal. And
parent nodes and sub nodes are mainly used to detect
and attack the target.
Figure 1. Structure of the system.
2.1 Wireless Intelligent Node
In order to facilitate the upgrade, the central node,
parent nodes and sub nodes adopt a homogeneous
and modular design, which are based on the
universal development chips. The structure of
wireless intelligent node is shown in Figure 2.
In order to simulate the ammunition’s ESP
warhead, the node contains four feedback modules
including buzzer and LED lighting, which is
convenient for observing in outdoor experiments.
Self-positioning module consists of Beidou and GPS
positioning chips, it is dual-mode design for
improving reliability, especially in one signal weak
condition or interference area. Detection module
contains sound and vibration chips, due to low
power consumption requirements, vibration is used
as early warning signal, when the vibration signal
reaches the threshold, the node starts the active
sound detection mode to locate the targets.
Communication module includes RF and WIFI
chips. RF is used to transmit data between nodes and
WIFI is used to communicate with command
terminal.DSP chip is used for D/A conversion,
filtering and feature extraction of two signals. The
32-bit ARM chip transmits data through the serial
port between modules, self-tests, pre-sets target
information, processes the location information. The
node’s working status can be conveniently observed
through display module, which contains the LCD,
such as "network completion", "alarm detecting",
"attack target", etc. Power module consists of a 12V
lithium battery and a voltage regulator circuit to
supply power to each module of the node.
2.2 Terminal Software
The software used by the command terminal uses
Visual Studio 2015 as the development platform,
mainly based on the C# language. The software
running process is shown in Figure 3.
ICVMEE 2019 - 5th International Conference on Vehicle, Mechanical and Electrical Engineering
468

Figure 2. Structure of wireless intelligent node.
Figure 3. Running process of terminal software.
2.2.1 Display Interaction Module
The quality of the interface directly affects the user's
efficiency
(Zhao Lin, Zhang Lingtao, Wang Zan, Tian
Guohui, Zhang Liang, 2018). The main interface uses
full-screen layout to display geographic information,
node location, network connectivity and target track,
and text and voice prompts for node status and target
status. The top of the screen is the function menu,
and the left and right sides are "information" area
and "control" area which can be hidden.
2.2.2 Communication Module
It is mainly used for information transmission
between nodes and hardware in semi-physical
simulation experiments, using multi-threading
technology. Socket communication mode is adopted
because it has the advantages of self-definable
Design and Research of Bayesian Reasoning Method based on Wireless Intelligent Nodes
469

transmission data, small data volume, short
transmission time and encryption
(Wu Jinghua, Hao
Xiaolong and Wang Haifeng, Gao He, 2018)
.
2.2.3 Algorithm Module
The DBN reasoning algorithm based on wireless
intelligent nodes is written by MATLAB and saved
as ".dll" format for C# calls.
3 DBN-BASED DICISION MODEL
The DBN theory overcomes the time dependence
and computational difficulties of the rule-based
system, and the networked ammunition attack
decision process can be regarded as a discrete
stochastic process. The DBN consists of observation
variables and hidden variables, and uses probability
distribution to describe causality
(Yao Hongfei, Wang
Hongjian, Lyu Hongli and Wang Ying, 2018). The attack
decision model is constructed according to the
DBN’s characteristics and the tasks’ characteristics.
The battlefield’s environment is complicated and
changeable
(Hunkar Toyoghu, Oya Ekin Karasan and
Bahar Yetis Kara, 2011)
, to solve the attack problem,
some assumptions need to be given.
3.1 Assumptions
The information transmission between nodes is
smooth, and the central node can obtain global
information.
The number of targets is less than the number of
nodes, and each target is assigned at least one node
for attack.
The detector’s performance is so excellent that
can get all the information of the targets in the
detection distance.
Once the target is found, it is destroyed
immediately.
3.2 Observation Variables
Multi-node fusion sound detection can calculate the
number of targets, the angle between the target and
the node, the target speed, and judge the target type
according to its noise characteristics. The node can
transport its working status through its own sensor,
such as network status, battery power, and the
remaining number of the warhead. The network
status means that the node is a central node, a parent
node or a child node, and the battery power
represents the remaining capacity of the lithium
battery, and the remaining number of the warhead
represents the remaining number of the warhead
under the angle corresponding to the target. In
addition, the detection distance constraint and the
attack distance constraint are also direct evidence.
The observation variables of the attack decision
model are shown in Table 1.
Table 1. Observation variables.
Variables
Meaning Collection
TA Target angel
AS1, AS2,
AS3, AS4
TS Target speed
HS, MS, LS
TT Target type
TA, VE,
NP Node battery power
EN, LO
NNS
Node network
status
CE, PA, SU
NWR
Node warhead
remain
0, 1
NWS
Node working
status
N, I
DDC
Detect distance
constraint
0, 1
ADC
Attack distance
constraint
0, 1
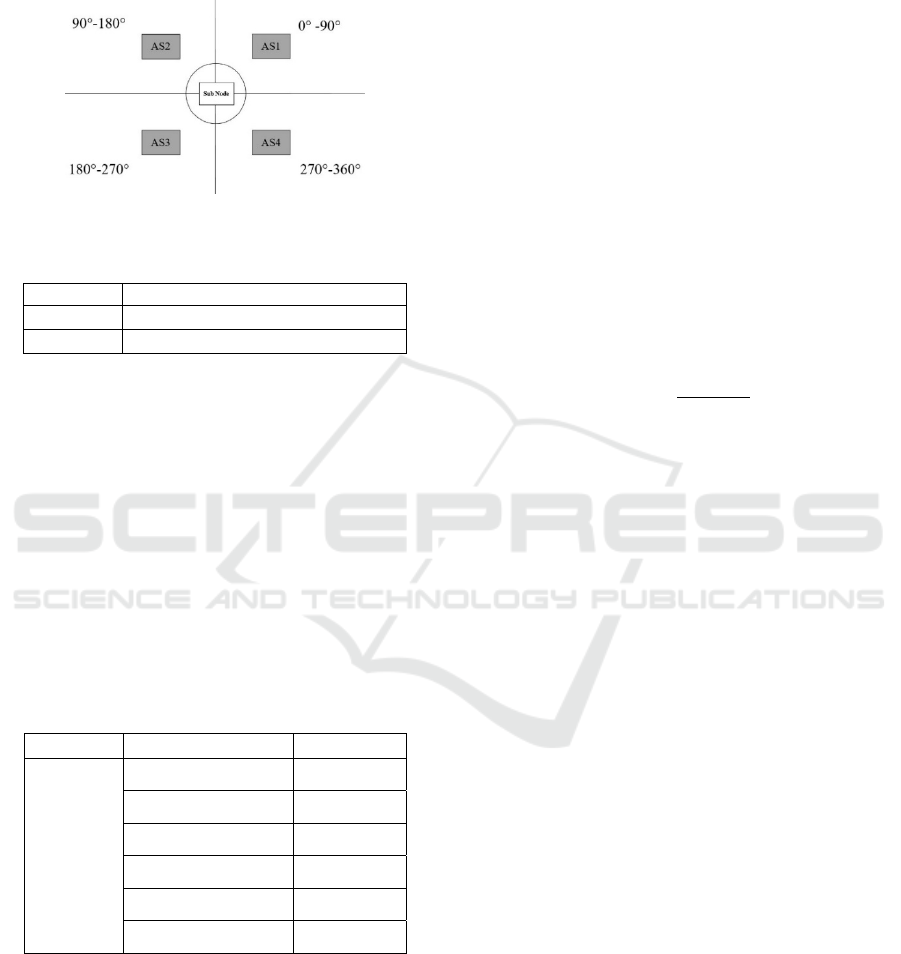
TA = {AS1, AS2, AS3, AS4} indicates target
angel. In order to speed up the calculation, four
regions according to the warhead installation
position are divided. The division of TA is shown in
Figure 4. TS = {HS, MS, LS} represents the speed
of targets which are discovered by the detector. TT =
{TA, VE} is the type of ground targets, vehicle and
tank are the mainly types currently. TP = {EN, LO}
is the nodes’ power, low condition means less than
10% of the capacity of the lithium battery. NNS =
{CE, PA, SU} indicates the network status, such as
central node, parent node and sub node. Regardless
of the network status of the node, it is assigned a
unique number. NWR = {0, 1} means the remaining
number of warheads corresponding to TA. NWS =
{N, I} means whether the node can work according
to the feedback of each module. DDC = {0, 1}
means whether the target is within the detection
distance. ADC = {0, 1} means whether the target is
within the attack distance. In the current situation,
the detection distance is longer than the attack
distance.
3.3 Hidden Variables
The hidden variables, which are the intermediate
layer of logical reasoning and constructed according
ICVMEE 2019 - 5th International Conference on Vehicle, Mechanical and Electrical Engineering
470
to the potential logical relationship of the
observation variables, reflect targets and nodes
situation information. The hidden variables of the
attack decision model are shown in Table 2.
Figure 4. The division of TA.
Table 2. Hidden variables.
Variables Meaning
TCS
Target comprehensive situation
NCS
Node comprehensive situation
TCS = TA*TS*TT means target comprehensive
situation information. NCS= NP*NNS*NWR*NWS
means node comprehensive situation information.
3.4 Decision Results
According to the decision result of the previous
moment and the current time observation evidence,
the current decision result is obtained. DMR =
{WA1, WA2, WA3, WA3, DET, GUA}, the
warhead used by the node attack is configured
according to the target angle. The result is shown in
Table 3.
Table 3. Decision result.
Variables Meaning Result
DMR
Warhead 1 attacks
WA1
Warhead 2 attacks
WA2
Warhead 3 attacks
WA3
Warhead 4 attacks
WA4
Keep detecting
DET
Keep guarding
GUA
4 REASONING ALGORITHM
The DAG is used to represent the dependencies and
independent relationships between variables, and the
conditional probability table quantitatively describes
the dependencies between nodes. The graphical
structure qualitatively represents the relationship
between the various variables
(Wang Qingjiang, Peng
Jun, Zeng Ruwei, Xu Xuewen, Ni Baohang and Shan Xin,
2014)
. It mainly studies the filtering in the dynamic
Bayesian network reasoning task, which is to infer
the posterior probability of the current moment
based on the decision result of the previous moment
and the evidence of the current moment. Since the
current information propagation direction is forward
broadcast, the improved reasoning algorithm can
improve the reasoning problem under the condition
of conclusive evidence and the reasoning problem
under the condition of multiple types of evidence.
4.1 Bayes’ Rule
Bayes’ rule is the basis of DBN theory. Suppose that
the probability of occurrence of random event x and
random event y is P(x) and P(y). The probability of
event x conditioned knowing event y is defined as
|
|
(1)
4.2 Algorithm Description
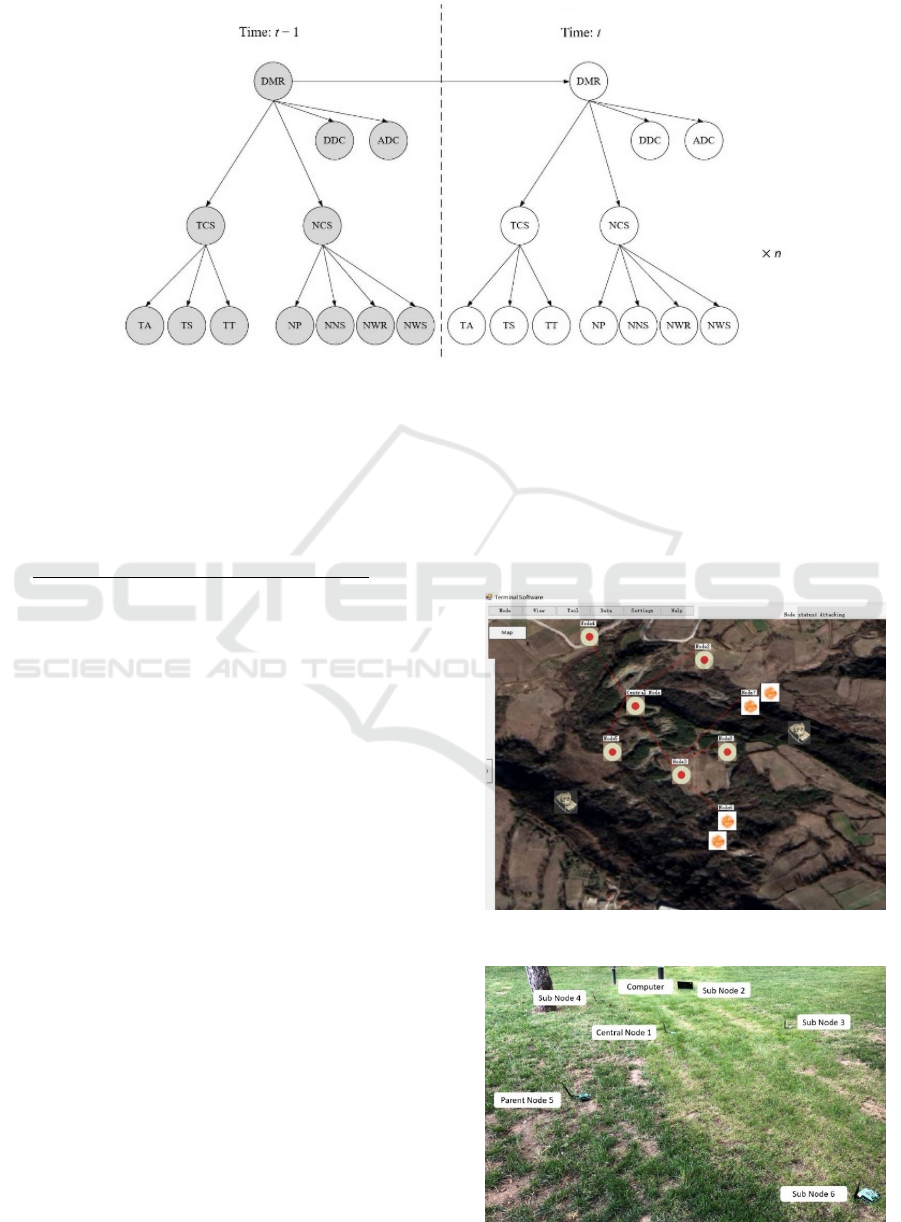
In the improved reasoning algorithm, there are t – 1
and t time moments, t – 1 time moment represents
past time and t time moment represents current.
There are one root node, nine observation nodes and
two hidden nodes in each time slice. The structure of
the DBN for nodes attack decision is shown in
Figure 5.
is the value of the root node at time t, is
a collection of observed variables, is the
normalization factor,
|
is the
probability of state transition,
|
:
is
the reasoning result at time t – 1. So, the reasoning
equation for the root node at time t is
|
:
|
∑
|
|
:
(2)
Based on the conditional independence and chain
passing rule, the root node at time t under the
condition of the observed variable is
|
|
|
|
|
|
|
’
|
|
|
(3)
A link with a hidden variable can derive the
conditional probability from the same principle.
Take
|
as an example
Design and Research of Bayesian Reasoning Method based on Wireless Intelligent Nodes
471
|
∑
|
|
(4)
Figure 5. The structure of DBN for attack decision.
The prior probability and state transition
probability need to be given in advance when
calculating. Recursive calculation according to DBN
reasoning method, the equation is
|
:
|
∑
|
:
:
(5)
5 EXPERIMENT
5.1 System Test
Using the terminal software as the carrier to predict
the effectiveness of the algorithm, open the software
and load the wild mountain map. The single-
machine test mode is selected to generate eight
nodes including one central node and one parent
node, and four ground targets which are the same
type of tank. The nodes are networked according to
the actual networking process. After the networking,
the nodes enter the guarding state. When the targets
appear, the algorithm module starts operation. Two
of the targets enter the attack area, then the software
calculates that the Node 6 and Node 7 are attacking.
The result is WA3 of Sub Node 6 and WA1 of Sub
Node 7. The running result is shown in Figure 5.
5.2 Semi-physical Simulation Experiment
In order to better test the performance of the
algorithm, an outdoor semi-physical simulation
experiment combining hardware and software is
performed. The scene of outdoor semi-physical
experiment is shown in Figure 7. Six wireless
intelligent nodes in good working condition
communicate with the terminal software after setting
up. When the networking process is completed, one
central node, one parent node, and four child nodes
are displayed. Two ground targets’ information are
preset before the experiment.
Figure 6. Running result of system test.
ICVMEE 2019 - 5th International Conference on Vehicle, Mechanical and Electrical Engineering
472

Figure 7. The scene of outdoor semi-physical experiment.
When the two targets appear, the algorithm
module starts running, one target is not in the attack
range, and the other target assigns Node 6 to attack.
The result is WA3 of Node 6. The running result is
shown in Figure 8. The DBN inference method has
dynamic adaptability. During the experiment,
changing the node position, changing the node state
and inputting new target information, the operation
result will be changed accordingly. For example,
when changing the node's battery power to low
condition, this node will be given the priority to
attack.
Figure 8. The running result of semi-physical experiment.
6 CONCLUSIONS
A multi-objective and multi-attribute attack decision
model under uncertain conditions based on DBN is
designed. According to tasks in wild, DBN
reasoning method is used in the simulation system,
which contains software and hardware. In the
simulation test and the semi-physical simulation
experiment, the DBN reasoning method is verified.
The experiment shows that the method is practical
and can provide decision support for researchers or
commanders.
REFERENCES
Chen Xiaoqing, 2019. Research on the paradigm of
military informatization construction, National
Defense Technology.
Hunkar Toyoghu, Oya Ekin Karasan, Bahar Yetis Kara,
2011. Distribution network design on the battlefield,
Naval Research Logistics.
Li Ming, Luo Guohua, Jiang Chunlan, 2017. Algorithm of
Networked Ammunition Attack Decision Based on
AHP-TOPSIS, Transaction of Beijing Institute of
Technology.
Ma Guopu, Sha Jichang, Chen Liangjun, Chen Chao,
Jiang Xin, 2010. Coordination decision based on
dynamic Bayesian network and blackboard
mechanism, Systems Engineering and Electronics.
Wang Qingjiang, Peng Jun, Zeng Ruwei, Xu Xuewen, Ni
Baohang, Shan Xin, 2014. Decision-making of UAVs
for air-to-ground multi-target attacking, Electronics
Optics & Control.
Wu Jinghua, Hao Xiaolong, Wang Haifeng, Gao He,
2018. Realize S7-1500PLC and server communication
by using Socket,Application of Automation.
Xiao Qinkun, Gao Song, Gao Xiaoguang, 2007. Dynamic
Bayesian network reasoning learning theory and its
application, National Defense Industry Press,
Yao Hongfei, Wang Hongjian, Lyu Hongli, Wang Ying,
2018. Threat assessment of UUV based on genetic
algorithm DDBN parameter learning, Journal of
Harbin Engineering University.
Zhao Lin, Zhang Lingtao, Wang Zan, Tian Guohui, Zhang
Liang, 2018. Multi-objective coordinated optimization
of active and reactive power of distribution network
integrated with High Proportion of photovoltaic
generation, Automation of Electric Power Systems.
Zhao Yuqing, Niu Xiaomin, Wang Xiaobo, Xia Muquan,
2012. The development present and trend of intelligent
submunitions, Guidance&Fuze.
Design and Research of Bayesian Reasoning Method based on Wireless Intelligent Nodes
473
