
The Best Route Selection and Internet Routing Application in PT.
IndosatM2
Siswanto, M. Anif and Basuki Hari Prasetyo
Universitas Budi Luhur
Keywords: Route Selection Application, Internet Routing, Router, Ping, BGP.
Abstract: The best internet routing and route selection are one of the crucial parameters together with other parameters
such as network quality and capacity, network device reliability, and a good network monitor system, which
must be considered by PT. IndosatM2 as an Internet Service Provider (ISP). During this time the process of
selecting the best internet route and routing is carried out entirely by the network administrator so that it
cannot be done at any time and the existing alternative lines are checked one by one with a level of accuracy
which often disrupts due to lack of documentation. The Best Route Selection and Routing Internet Application
at PT. IndosatM2 will integrate and connect a web-based online application with network devices that are
routers that interact with each other to run a script command on the router network device, that is, the script
command from BGP routing protocol that is used between Service Providers on the internet to know and
provide track information and the best routing to a particular destination. The output of this application is the
best internet route and routing, also noted the requested changes in the form of 6 requests could be done the
best internet routing and routing processor about 75% of the total 8 requests. 2 requests cannot be made for
the best internet routing and routing processor around 25% of the total 8 requests reducing the processing
time to complete the request for the best internet routing and routing that is very significant, so that it can
improve service levels above the average value of 99.5% to customers
1. INTRODUCTION
PT. IndosatM2 (IM2) a company with a head office
located on Jl. Kebagusan Raya No. 36 Pasar Minggu
South Jakarta and has branches in many major cities
in Indonesia, wholly owned by PT. Indosat Tbk, the
leading provider of telecommunications services in
Indonesia, has been operating fully since 2000 to
build and implement IP, internet and multimedia
based services and products in Indonesia. Serving
four customer segments: corporations (large, medium
and small), government, institutions, residential, and
individuals. Corporate and institutional services
include Virtual Private Network (VPN) networks,
direct connections to international internet
backbones, and multimedia service providers.
IM2, as one of the internet service providers or
often referred to as an Internet Service Provider (ISP)
in Indonesia places great importance on the quality of
internet access for its customers. IM2 as one of the
ISPs is connected to the internet through various other
ISPs called Uplink Providers. The current business
process flow system is that the Helpdesk accepts path
selection requests and internet routing to specific IP
address destinations from customers, then the
helpdesk creates and forwards the ticket to the Person
In Charge (PIC) administrator, then the administrator
processes the request by logging into the gateway
router use the application to telnet and run the script
command to check the number of available IP routing
paths to the destination IP address requested by the
customer, the administrator manually changes the
BGP routing protocol configuration on the router, ie
for the outbound path by increasing the local
preference value and pinging to the destination IP
address and record the time lag results, while for the
inbound path by adding prepend AS and ping the
destination IP address and re-record the time lag
result, the administrator does the work manually for
configuration changes and records the time lag to the
purpose of this particular IP address repeats according
to the number of paths and routing available from the
results of previous checks, after which it will be
selected from the results manually recorded, the
smallest time lag value and configuration are changed
to match the selected path to the destination of a
Siswanto, ., Arif, M. and Prasetyo, B.
The Best Route Selection and Internet Routing Application in PT. IndosatM2.
DOI: 10.5220/0008930601290134
In Proceedings of the 1st International Conference on IT, Communication and Technology for Better Life (ICT4BL 2019), pages 129-134
ISBN: 978-989-758-429-9
Copyright
c
2020 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
129

specific IP address, then obtained the best path and
routing, then the administrator will resolve the ticket,
based on the ticket that has been resolved, the
helpdesk will inform the customer that the path
selection request and internet routing to the
destination IP address requested has been completed.
A router is one of the main devices to connect
between one network and another network which also
functions to manage exchanges and data traffic routes
with each other (Thiel, 2014). Routers are also
connected to other routers throughout the world,
which allows two computer networks connected to
different routers to be able to channel their data with
the best travel routes among various alternative
routes. But not always the route determined by the
router is the most optimal or best because of several
factors that can not be known by the router, for
example, there is a relationship in the middle of the
track with full traffic capacity or a transmission
interruption. Thus human interaction is needed as a
network manager to determine the best route for
themselves to a particular destination after checking
the existing path alternatives. A router’s functions are
to read the destination address marked in an incoming
IP packet, to consult its internal information to
identify an outgoing link to which the packet is to be
forwarded, and then to forward the packet (Medhi and
Ramasamy, 2017).
The best path selection and internet routing takes
a long time, because routing access permissions
should only be done at the administrator level,
including each connection of each Uplink Provider
connection, all of which are done manually so that it
helps with the long transition, plus the need for data
access and information for the company's internal
interests as a material for analysis, decisions and
strategic decision making of the company going
forward (Goralski, 2017).
The problems faced in the existing system
mechanism are as follows: it is necessary to examine
alternative paths one by one for two directions
(Upstream and Downstream), so that it takes more
than 1 hour, Requires expert staff at administrator
level who have the highest access rights to Router
configuration changes, with a limited number and not
always ready 24 hours to do so, changes made often
cause disruption of internet access due to inadvertent
conduct in checking and changing internet routing
lines, and not well-documented for information on
changes made as reports to supervisor and
management.
The main objectives expected with the
development of application systems are internet
routing and routing, which are: design and implement
the best internet routing and routing application
system in PT. IndosatM2, provides an easy, precise
and fast system that is the result of automation of the
best internet routing and routing processes., providing
continuity of information systems for the best internet
route and routing selection, providing recapitulation
of the best internet routing and routing processes, so
as to produce information that is more accurate and
can be utilized by internal and company management.
In this paper, we propose the use of a blockchain-
based mechanism to secure the Internet BGP and
DNS infrastructure; A tamper-resistant DNS
infrastructure also ensures that it is not possible for
the application-level PKI to spoof HTTPS traffic
(Hari and Lakshman, 2016).
Nearly all network applications rely on the global
Internet routing infrastructure to compute routes and
deliver packets; unfortunately, false Internet routes
can be maliciously introduced with relative ease into
the routing infrastructure. This is because Border
Gateway Protocol(BGP), the Internet’s global routing
protocol, lacks basic authentication and monitoring
functionalities, currently, it is impossible to prevent
such malicious injection off also traffic routes, we
believe that an ability to identify false paths through
efficient validation, proper recording and forensic
analysis of routing data, will considerably help in the
prosecution of them is creant and will act as a strong
deterrent (Kim, Massey and Ray, 2005).
BGP routing updates collected by monitoring
projects such as Route Views and RIPE have been a
vital source to our understanding of the global routing
system. However, the collected BGP data contains
both the updates generated by actual route changes
and the updates of BGP routing table transfers
resulted from BGP session resets between operational
routers and the data collection stations, In this paper,
we present the design and evaluation of the minimum
collection time (MCT) algorithm. Given a BGP
update stream, MCT can identify the start and
duration of each routing table transfer in the stream
with high accuracy. We evaluated MCT performance
by using three months of BGP data formal l RIPE
collectors. Our results show that out of the total 1664
BGP resets with 166 monitors, MCT can identify
BGP routing table transfers with over 95% accuracy,
and pinpoint the exact starting time of the detected
table transfers in 83% of such cases (Chenga, Zhang,
and Massey, 2011).
Abnormal BGP events such as attacks,
misconfigurations, electricity failures, can cause
anomalous or pathological routing behavior at either
a global level or prefix level, and thus must be
detected in their early stages. Instead of using ad-hoc
ICT4BL 2019 - International Conference on IT, Communication and Technology for Better Life
130

methods to analyze BGP data, in this paper we
introduce an Internet Routing Forensics framework to
systematically process BGP routing data, discover
rules of abnormal BGP events, and apply these rules
to detect the occurrences of these events (Li, Dou,
Wu, Kim and Agarwal, 2005).
The Border Gateway Protocol(BGP) is one of the
fundamental computer communication protocols.
Monitoring and mining BGP update messages can
directly reveal the health and stability of Internet
routing; specifically, we developed BGPlens, an
automated BGP updates analysis tool,that has three
desirable properties: it is effective, able to identify
phenomena that would otherwise go unnoticed, such
as a peculiar ‘clothesline’ behavior or prolonged
‘spikes’ that last as long as 8 hours; it is scalable,
using algorithms that are all linear on the number of
time-ticks (Prakash, Valler, Andersen, Faloutsos and
Christos, 2009).
2. METHOD
This study uses a research method with the following
steps:
2.1 Running System Analysis
One of the activities carried out by the Network
Operation & Monitoring sub-section, the Network
Operation Center (NOC) Division of PT. IndosatM2
(IM2) is monitoring continuity and carrying out
operational systems and production networks for the
continuity of services and products of PT. IndosatM2
is used by customers, which includes the process of
selecting the best internet route and routing.
Previously there was no application system that
was made to determine the best online and automatic
route and internet routing selection that could serve
customers' requests easily, quickly and precisely, so
the process flow in the system was still done
manually, both from the start of the request, forward
the ticket to the Administrator, check and report the
results of the internet routing and routing selections
made. This manual method is very inefficient, and the
report data obtained is no longer accurate.
2.2 Running System Process Flow
The process flow that is written is limited to the
process flow of the best internet routing and routing
received by IM2 NOC. Explanation of the system
process flow running for the best internet routing and
routing paths is as follows:
2.2.1 The customer requests and makes a ticket to
the Helpdesk.
2.2.2 The Helpdesk creates and forwards the
ticket to the Personal in Charge (PIC)
Administrator concerned.
2.2.3 The administrator processes the ticket
request for the best internet route and routing
and resolves the ticket after getting the best
internet route.
2.2.4 Based on the ticket that has been resolved,
the Helpdesk informs the Customer that the
request has been completed.
2.3 Data Savings Analysis
Deposits of data are still in the form of paper
documents, so it needs to be stored in the form of a
database as part of the system application for the best
internet routing and routing.
2.4 Analysis of Problems in the
Running System
After discussing and analyzing the system that is
running, various problems can be found in the system.
The problems in question are:
2.4.1 Storage of data from the best path and
internet routing results is manual so that it can
cause data duplication and data search will take
a long time, then new and automatic database
storage is needed.
2.4.2 The best internet routing and routing process
are still manual, so the implementation of the
best internet routing and routing process from
many customers will take time and be
hampered if the Administrator is not available,
so the process automation is needed in the best
internet routing and routing to overcome the
problem.
2.4.3 The recording and recapitulation of tickets
by the Helpdesk produced are still manual, so
it takes a long time in grouping and calculating
tickets and difficulties in compiling reports for
management, it requires a new reporting
process that is automated so that fast and
accurate data reporting needs can be resolved.
2.4.4 There needs to be a policy regarding the best
process of internet routing and routing that is
automatic in a system. This policy will enable
the old problems handling the process of
requesting the best internet route and routing
and can only be done by the Administrator is
not an obstacle, and the availability of reports
for management regarding the process and the
best internet routing can be handled and
presented online.
The Best Route Selection and Internet Routing Application in PT. IndosatM2
131

2.4.5 Based on observations, it can be seen that the
flow of the process of requesting the best
internet routing and routing paths rests
everything on the Administrator who must be
stand-by on the spot.
2.5 Problem Solving Strategies
Based on problem analysis, it is necessary to make the
design and implementation of the best internet path
and routing selection system.
2.6 Problem Solving Strategy Process
Flow
Explanation of the process flow of problem-solving
strategies for the best internet route and routing
selection is as follows:
2.6.1 The customer requests the best internet route
and routing request to the Helpdesk.
2.6.2 The Helpdesk accepts requests, ensures
customer profiles are in the customer database,
and assigns tickets to requests for the best
internet routing and route selection.
2.6.3 The system processes the best internet path
and routing for the internet IP address as
requested on the ticket.
2.6.4 From the results of the new route and routing
obtained, the helpdesk resolves the ticket and
information that is ready to be delivered to the
customer.
2.6.5 From the resolving ticket, the Helpdesk
informs the results to the Customer.
2.6.6 The Flow of the Path Selection Process and
the Best Internet Routing in General
Explanation of the best flow path and internet
routing process, are as follows:
2.6.7 Connection and Login to the gateway router
console using Telnet.
2.6.8 Check each connection to the existing
internet, by typing the console command: show
IP BGP, note the available alternative path,
namely the BGP Peer IP address for each
available BGP path that is visible on the
console.
2.6.9 Specify the path to the destination address
(Upstream):
a) Of all the alternative paths available from
number 2.7.2 above, prioritize one for the
destination IP address requested by the
Customer, by increasing the local-preference
prefix IP value obtained from BGP Peer for this
path, with console commands namely like the
following example:
(1) IP IN permit 10.10.100.0/24 prefixes
(2) route-map IN permit 5
(3) Match IP IN. Prefix-list
(4) local-preference set of 150
(5) clear IP BGP peer-group IN soft in
b) Check and record the amount of latency
obtained at the destination IP address using the
console ping command to the destination IP
address, which is the average round-trip value.
c) Repeat steps a) and b) above for each of the
other paths until all BGP Peers in number 2)
above.
d) From the latency recorded, prioritize the
destination address requested to the alternative
path with the smallest latency, by way of point
a) above.
2.7.1 Determine the return path from the
destination address (Downstream):
a) From all the alternative paths available from
number 2.7.2 above, make the downstream
path to the Origin IP address pass one of the
paths, by advertising the Customer IP prefix by
doing a US Prepend to all BGP Peers on the
other path, with commands console that is like
the following example:
(1) IP prefix-list UPLINK1-OUT permit
20.20.200.0/24
(2) IP UPLINK2-OUT permit prefix-list
20.20.200.0/24
(3) UPLINK1-OUT permit-map route 5
(4) match IP UPLINK1-OUT prefix-list
(5) set as-path prepend 4795 4795 4795 4795
(6) UPLINK2-OUT permit route-map 5
(7) match IP UPLINK2-OUT prefix-list
(8) set as-path prepend 4795 4795 4795 4795
(9) clear IPBGP peer-group UPLINK1-OUT
soft out
(10) clear IPBGP peer-group UPLINK2-OUT
soft out
b) Check and record the amount of latency
obtained at the destination IP address using the
console ping command to the destination IP
address, which is the average round-trip value.
c) Repeat steps a) and b) above until all BGP
Peers from number 2.7.2.
d) From the latency recorded, prioritize
downstream to the Customer address to the
alternative path with the smallest latency, as in
point a) above.
2.7.2 The best internet path and routing to the
requested destination has been obtained and
Customer traffic has gone through that path
both Upstream and Downstream.
ICT4BL 2019 - International Conference on IT, Communication and Technology for Better Life
132
3. RESULT AND DISCUSSION
By implementing the implementation process and
using the best internet routing and routing application
system programs, an analysis was achieved by the
program. Analysis of the results achieved by the
program during the first 2 weeks (17-30 April 2019)
the use of the best internet routing and routing
application system, including:
3.1 The best internet routing and routing
application system program can be used easily,
precisely and quickly and runs well to process the best
customer routing and internet routing for a total of 8
requests, as in figure 1.
Figure 1: Pie Chart Best Total Path Selection Requests and
Internet Routing
With the explanation for the Pie Chart above are:
3.1.1 6 requests can be carried out by the best
internet routing and routing processor, around 75% of
the total 8 requests.
3.1.2 2 requests cannot be carried out by the best
internet routing and routing processor around 25% of
the total 8 requests because the IP Destination
requested by the Customer cannot be pinged.
3.2 The program can do the best internet routing
and routing selection from 6 Customer requests with
Latency and Processing Time as shown in figure 2.
Figure 2: Bar Line Chart Latency and Processing Time
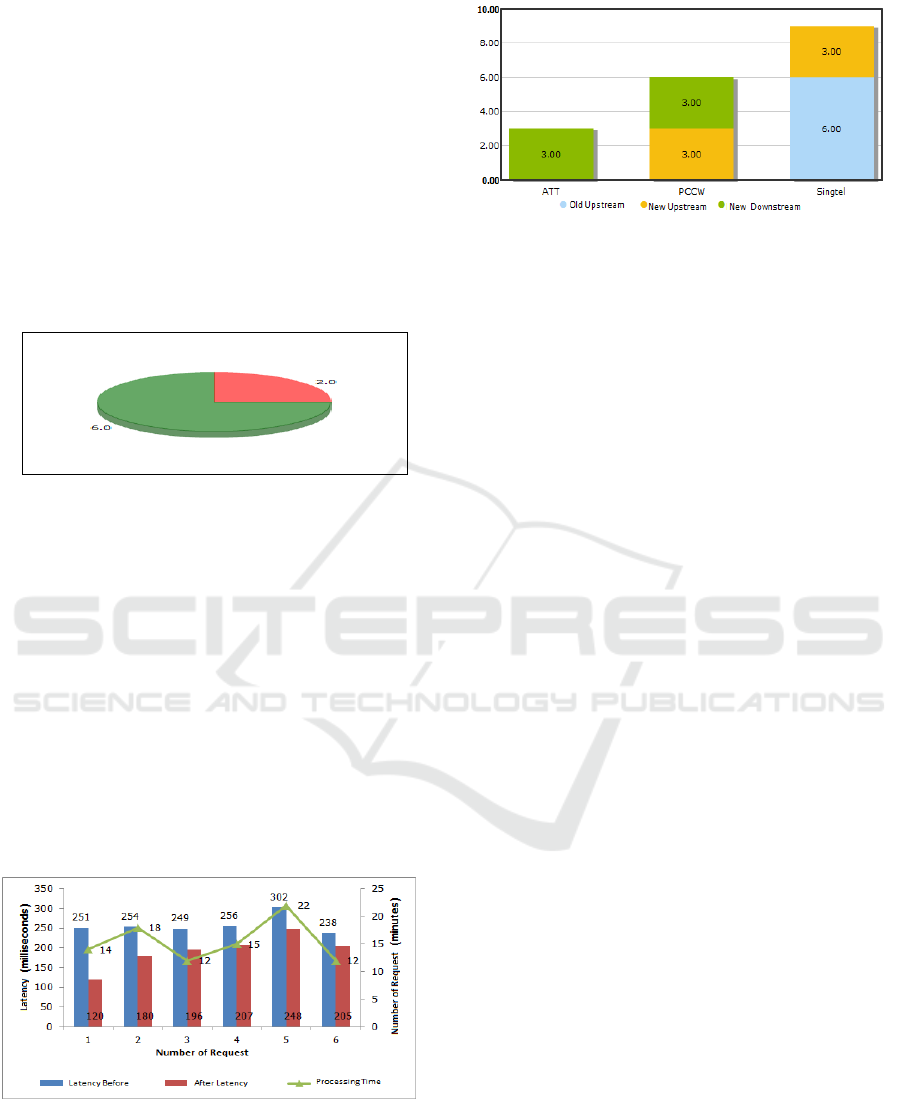
3.3 From the results of a new internet routing
and routing check for 6 requests from the Customer,
there is the best internet routing and routing selection
based on the Uplink Provider, as shown in figure 3.
Figure 3: Uplink Bar Chart For Best Internet Path and
Routing Selection
With the explanation for the Chart Bar above are:
3.3.1 Singtel is an old Upstream path of 6 requests
and selected as the best new Upstream for 3 requests
resulting from the process of selecting the best
internet route and routing.
3.3.2 PCCW is selected as the best new Upstream
for 3 requests and selected as the best new
Downstream for 3 requests resulting from the best
internet routing and routing process.
3.3.3 ATT is selected as the best new Downstream
for 3 requests as a result of the best internet routing
and routing process.
4. CONCLUSIONS
Conclusions can be taken as follows: the program can
run well according to the objectives and design of the
program and as a solution to the problems faced
beforehand and can be used quickly, precisely and
easily by the user as part of process automation to
support daily operational activities,remote
application process or remote control directly to the
router gateway device automatically and real time,
reducing dependence on administrators and reducing
the possibility of errors during the inspection process
and the best internet routing and routing, checking
and selecting the best internet routes and routing can
be done in a fairly short and efficient time, reducing
the process time to complete the request for the best
internet routing and routing that is very significant, so
that it can increase service levels above the average
value of 99.5% to customers, and documentation of
the process and results of examinations as well as the
best internet route and routing selection, so that a
report on recapitulation of requests and completion of
the best internet route and routing selection can be
made based on the time period needed quickly and
accurately to support the continuity of information
The Best Route Selection and Internet Routing Application in PT. IndosatM2
133

systems company management to support and
improve company performance and services.
Suggestions for further enhancing and developing
application systems, namely: there is a monitor
feature to monitor the best internet routes and routing
to the IP destination address requested by the
customer so that it can be known if there is a change
back and can be used all the time as long as this
feature is activated, the visualization feature of the
best internet routing and routing process is done so
that it can help and as an illustration for the uplink
provider selection process, the best internet routes
and routing going forward, and
can be integrated with a Web Analyzer system that
has a world-wide popular website address data bank
that is accessed by many customers, so that the
system can monitor and select the best internet routes
and routing to the website's IP address.
REFERENCES
Thiel, D. (ed.), 2014. The Ultimate Router Guide: Jigs,
Joinery, Projects & More from Popular Woodworking,
Popular Woodworking Books, ISBN: 1440339821,
9781440339820, https://www.pdfdrive.com/the-
ultimate-router-guide-jigs-joinery-projects-more-from-
popular-woodworking-d157831157.html, pp. 5 -32.
Medhi, D., and Ramasamy, K., 2017. Network Routing:
Algorithms, Protocols, and Architectures2nd Edition,
eBook ISBN: 9780128008294 Paperback ISBN:
9780128007372 Imprint: Morgan Kaufmann Published
Date: 11th September 2017, pp. 5-7
Goralski, W., 2017. The Illustrated Network: How TCP/IP
Works in a Modern Network, 2nd Edition, eBook
ISBN: 9780128110287 Paperback ISBN:
9780128110270 Imprint: Morgan Kaufmann,
Published Date: 28th April
2017.https://www.elsevier.com/books/the-illustrated-
network/goralski/978-0-12-811027-0., pp. 247 -287.
Hari, A., and Lakshman, T.V., 2016. The Internet
Blockchain: A Distributed, Tamper-Resistant
Transaction Framework for the Internet Nokia Bell
Labs, USA,
http://web.kaust.edu.sa/Faculty/MarcoCanini/classes/C
S390G/S17/papers/InternetBlockchain.pdf, HotNets-
XV, November 09 - 10, 2016, Atlanta, GA,
USAc©2016 Copyright held by the owner/author(s).
Publication rights licensed toACM. ISBN 978-1-4503-
4661-0/16/11,
DOI:http://dx.doi.org/10.1145/3005745.300577, pp.
204-210.
Kim, E., Massey, D. and Ray, I., 2005. Global Internet
Routing Forensics:Validation Of Bgp Paths Using Icmp
Traceback, https://www.researchgate.net/scientific-
contributions/44257010_Eunjong_Kim, pp. 1-12.
Chenga, P., Zhang, B., Massey, D.l, and Zhang, L., 2011.
Identifying BGP routing table transfers, Computer
Networks 55, www.elsevier.com/locate/comnet,
http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.
1.1.221.3083&rep=rep1&type=pdf, pp. 636–649.
Li, J., Dou, D., Wu, Z., Kim, S., and Agarwal, V., 2005. An
Internet Routing Forensics Framework for Discovering
Rules of Abnormal BGP Events, ACM SIGCOMM
Computer Communication Review 55 Volume 35,
Number 5, October 2005, pp 54-66.
Prakash, B. A., Valler, N., Andersen, D., Faloutsos, M., and
Christos, 2009. BGP-lens: Patterns and Anomalies in
Internet Routing Updates, KDD’09, June 28–July 1,
2009, Paris, France.Copyright 2009 ACM 978-1-
60558-495-9/09/06 ...$5.00, pp. 1315-1323.
ICT4BL 2019 - International Conference on IT, Communication and Technology for Better Life
134
