
Do Not Tell Me What I Cannot Do!
(The Constrained Device Shouted under the Cover of the Fog):
Implementing Symmetric Searchable Encryption on Constrained Devices
Eugene Frimpong
1 a
, Alexandros Bakas
1 b
, Hai-Van Dang
2 c
and Antonis Michalas
1 d
1
Tampere University, Tampere, Finland
2
Univerity of Westminster, London, U.K.
Keywords:
Fog Computing, Symmetric Searchable Encryption, Wireless Sensor Networks, Internet of Things, Privacy.
Abstract:
Symmetric Searchable Encryption (SSE) allows the outsourcing of encrypted data to possible untrusted third
party services while simultaneously giving the opportunity to users to search over the encrypted data in a
secure and privacy-preserving way. Currently, the majority of SSE schemes have been designed to fit a typical
cloud service scenario where users (clients) encrypt their data locally and upload them securely to a remote
location. While this scenario fits squarely the cloud paradigm, it cannot apply to the emerging field of Internet
of Things (IoT). This is due to the fact that the performance of most of the existing SSE schemes has been
tested using powerful machines and not the constrained devices used in IoT services. The focus of this paper
is to prove that SSE schemes can, under certain circumstances, work on constrained devices and eventually
be adopted by IoT services. To this end, we designed and implemented a forward private dynamic SSE
scheme that can run smoothly on resource-constrained devices. To do so, we adopted a fog node scenario
where edge (constrained) devices sense data, encrypt them locally and use the capabilities of fog nodes to
store sensed data in a remote location (the cloud). Consequently, end users can search for specific keywords
over the stored ciphertexts without revealing anything about their content. Our scheme achieves efficient
computational operations and supports the multi-client model. The performance of the scheme is evaluated by
conducting extensive experiments. Finally, the security of the scheme is proven through a theoretical analysis
that considers the existence of a malicious adversary.
1 INTRODUCTION
With the rapid advancement and development of inno-
vative and pervasive computing, traditional security
mechanisms such as public key cryptography have be-
come inadequate to properly protect users’ artefacts
on their own due to the increasingly complex nature of
these networks. Computing paradigms such as Inter-
net of Things (IoT), Cloud, and Fog computing have
become mainstays in corporate organizations as well
as in the everyday lives of individuals. The cloud and
fog computing technologies allow users to outsource
resources to external service providers. Fog comput-
ing, in particular, has garnered a lot of academic and
industrial interest beginning from 2014 when it was
a
https://orcid.org/0000-0002-4924-5258
b
https://orcid.org/0000-0002-0731-1851
c
https://orcid.org/0000-0003-2748-0369
d
https://orcid.org/0000-0002-0189-3520
first coined as a term by Cisco (cis, 2019).
Fog computing can be described as a virtual-
ized platform that seeks to provide various techno-
logical services such as computing, storage, control
and networking services between end users and the
Cloud (IEEE, 2018). This has gained lot of attention
due to the increased adoption of IoT applications with
the cloud computing ecosystem. This adoption has
led to an exponential increase in the amount of data
being generated and transmitted between the IoT de-
vices and the cloud. One of the primary advantages
of introducing Fog computing is to provide reduced
latency, reliable operation and eliminate the need for
devices to continually connect to the cloud.
The introduction of fog nodes between an IoT
edge network and the cloud leads to increasingly ad-
vanced and complex network designs such as Vehicu-
lar ad-hoc networks (VANETs). A typical VANET
consists of moving vehicles with sensors that con-
stantly communicate with well placed fog nodes for
Frimpong, E., Bakas, A., Dang, H. and Michalas, A.
Do Not Tell Me What I Cannot Do! (The Constrained Device Shouted under the Cover of the Fog): Implementing Symmetric Searchable Encryption on Constrained Devices.
DOI: 10.5220/0009413801190129
In Proceedings of the 5th International Conference on Internet of Things, Big Data and Security (IoTBDS 2020), pages 119-129
ISBN: 978-989-758-426-8
Copyright
c
2020 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
119

instant or near real-time responses (Kalinin et al.,
2017). The fog nodes after processing the data, for-
ward specific components to the cloud for further
analysis. Such advanced networks face various se-
curity and privacy threats related to trust, authen-
tication, secure communication and end device pri-
vacy (Mukherjee et al., 2017), which are not easily
mitigated with traditional security mechanisms.
To this end, researchers and industry stakehold-
ers have touted the use of promising encryption tech-
niques such as Symmetric Searchable Encryption
(SSE) (Dowsley et al., 2017; Dowsley et al., 2016).
SSE allows users to search directly over encrypted
data stored in remote locations maintained by pos-
sible untrusted third parties (e.g. a cloud service)
without revealing anything about the contents of the
data (Etemad et al., 2018). Additionally, SSE allows
users to encrypt data with a secret key which is not
known to the cloud provider. Hence, providing pro-
tection against both external and internal (e.g. a ma-
licious administrator) attacks. An ideal SSE scheme
should not leak any information during any of the core
processes of the (i.e. add, delete, update files and
search for specific keywords). Information leakage
is a very important problem in SSE due to its direct
impact on both the efficiency and security.
Contribution. The core contribution of this paper
can be summarized in one single sentence: “Running
Symmetric Searchable Encryption on constrained de-
vices is possible!”. This is considered as an important
step towards the widespread adoption of SSE schemes
since majority of SSE have been designed to fit a typ-
ical cloud service scenario that cannot apply to the
emerging field of IoT. Additionally, the performance
of most of the existing SSE schemes has been tested
using powerful machines and not the constrained de-
vices used in IoT services. In this paper, we show
that SSE can run on constrained devices. The main
idea of our approach came from the following obser-
vation: SSE schemes are computationally heavy for
clients only during the setup phase where the entire
database (known as the dictionary) is created. This
process, requires the client to parse all of the contents
of the files that are to be stored in the cloud, extract
all individual keywords and store encrypted versions
of all data in the cloud. The rest of the expensive
operations (e.g. search, delete, add) are mainly tak-
ing place on the cloud where there are unlimited re-
sources. If it was possible to bypass or limit the setup
phase, then SSE could ran in any device. Having this
in mind, our approach was based on the fact that in
an IoT scenario, edge devices will have to sense data
from their actual environment and store them on the
fly in a remote database. In other words, in such a
scenario there is no setup phase since there are no ex-
isting files that needs to be parsed and stored to the
cloud. Each sensor node periodically senses data (e.g.
every 5sec). Additionally, the operations that must be
done on the sensed data are simple calculations (such
as hashing and symmetric encryption) which do not
put any real burden on the device. Based on this as-
sumption, we built a forward private dynamic SSE
scheme that shifts majority of the computational bur-
den from the IoT devices to the fog computing nodes
and we showed that our scheme can run smoothly on
devices with up to 32MHz and 32KB of RAM. We
hope that this work will be seen as a starting point
where researchers will start building more secure and
robust IoT protocols based on the promising concept
of SSE.
Organization. The rest of the paper is organized as
follows. In section 2, we discuss related works re-
garding current implementations of SSE schemes and
the fog computing technology as well as the various
security issues relating to it. A brief description of the
cryptographic primitives used throughout our work
and the considered threat model are presented in sec-
tion 3. We formally define our system model in sec-
tion 4 while in section 5, we present the our scheme.
We then delve into a detailed security analysis in sec-
tion 6. Section 7 provides an extended evaluation and
finally in section 8 we conclude the paper.
2 RELATED WORK
Currently, there is an apparent lack of existing litera-
ture on implementing and extending purely symmet-
ric searchable encryption schemes to the Fog com-
puting environment. However, there are a number
of substantial research works in relation to design-
ing SSE schemes for cloud computing environments
as well as securing data in a fog computing environ-
ment. For example, authors in (Etemad et al., 2018)
present an efficient dynamic searchable encryption
with forward-privacy in a cloud computing environ-
ment. This scheme offers efficient searching over out-
sourced encrypted data in an untrusted server. How-
ever, primary deficiencies with this scheme are its
lack of support for multiple clients and the compu-
tational and storage overhead imposed on end entities
(i.e. IoT devices in the context of this paper). Our
work focuses on extending an SSE scheme to an en-
vironment with multiple data owners and end users
who will use the search functionality of our scheme
while reducing the computational overhead imposed
on the resource constrained IoT devices.
IoTBDS 2020 - 5th International Conference on Internet of Things, Big Data and Security
120

Authors in (Ni et al., 2018) present a comprehen-
sive survey of existing fog computing architectures,
features, as well as the roles of fog nodes in provid-
ing real-time services, transient storage, data dissem-
ination and decentralized computations. Authors dis-
cuss the various security and privacy challenges that
arise when utilizing fog computing for IoT applica-
tions. For example, authors discuss several security
challenges that affect specific fog node roles such as
identity authentication, access control, intrusion de-
tection, and resilience to sybil attacks when provid-
ing real-time services. Privacy-preserving data aggre-
gation (Dimitriou and Michalas, 2014), secure data
search, secure content distribution, and privacy pre-
serving packet forwarding when employing fog nodes
for data dissemination. while for transient storage,
they considered sensitive data identification and pro-
tection, data integrity protection, and secure data shar-
ing. For our proposed scheme, we utilize fog comput-
ing nodes as data dissemination agents and designed
our scheme to address the secure data search security
challenge.
An example of a rather innovative security
scheme for the Fog and IoT ecosystem is the use
of Blockchains and Trusted execution environments
(TEE) in (Fan et al., 2019). In this work, au-
thors design a security scheme that guarantees data
source trustworthiness in the fog domain by combin-
ing blockchains and TEE technologies. The scheme
ensures that the information collected by the fog
nodes from the IoT devices cannot be tampered with
by any malicious adversary, while ensuring the safety
of data interaction between interconnected fog de-
vices. Although a very interesting approach, it does
not provide an external user the ability to search over
this secure data. Additionally, the proposed use of
smart contracts essentially means that the IoT devices
can not carry out the security scheme without incur-
ring a substantial computational overhead cost.
To reduce the computational overhead on resource
constrained devices, researchers in (Cao et al., 2019),
proposed a lightweight fine-grained search over en-
crypted data in a similar fog computing environ-
ment by adopting the Ciphertext-Policy Attribute-
based Keyword Search (CP-ABKS) (Zheng et al.,
2014) and shifting majority of the computational bur-
den to the Fog Nodes. Albeit a very powerful cryp-
tographic algorithm that provides fine-grained access
control and keyword search, CP-ABKS incurs very
high computational and storage costs that our imple-
mentation avoids by utilizing SSE. Additionally, au-
thors make the assumption that the CSP is an honest
but curious entity. Hence, the CSP computes cipher-
text retrieval operations based on received tokens. On
the contrary, we propose to limit the functionalities
of the CSP by restricting it to storing the ciphertexts
of files while performing search queries in the Fog
computing layer. As well as eliminating the need to
trust the CSP, this reduces the communication latency
involved in search queries and the return of search re-
sults.
3 BACKGROUND
Notation: Given a set X , we use x ← X to show
that x is sampled from X and x
$
←− X if x is sampled
uniformly at random. |X | denotes the cardinality of
X . Given two strings x and y, we use x||y to denote
the concatenation of x and y. A function negl(·) is
called negligible if ∀n > 0,∃N
n
such that ∀x > N
n
:
|negl(x)|< 1/poly(x). Each IoT device is considered
as a data owner. The set of all IoT devices is de-
noted by D = {d
1
,.. .,d
n
}. Similarly, the set of all
fog nodes is denoted by F = { f
1
,.. ., f
m
}. In our
constructions, the keywords are measurements sent
by the IoT devices to a fog node. The universe of the
measurements is denoted by W = {w
1
,.. .,w
}. Each
measurement w
j
has a unique id, denoted by id(w
j
)
with corresponding ciphertext c
id(w
j
)
. Moreover, we
denote by R the result of a search query. We assume
that each IoT device and each Fog Node holds a pub-
lic/private key pair (pk,sk) used for signing and ver-
ifying messages. The encrypted data base is denoted
by EDB and finally, we assume the existence of a hash
function h(·) : {0,1}
∗
→ {0,1}
m
and that of a keyed
hash function H(·,·) : {0,1}
λ
× {0,1}
∗
→ {0,1}
n
.
Symmetric Searchable Encryption: We now pro-
ceed with the definition of a dynamic symmetric
searchable encryption scheme.
Definition 1. A Dynamic Symmetric Searchable En-
cryption (DSSE) scheme consists of the following PPT
algorithms:
• Setup(1
λ
): A key-generation algorithm that takes
as input the security parameter λ and outputs the
secret key K = (K
SKE
,K
h
) where K
SKE
is a key
for a IND-CPA secure symmetric key cryptosys-
tem and K
h
is a key for the keyed hash function
H(·,·). This algorithm is executed by an IoT de-
vice.
• AddId: This algorithm is executed by an IoT de-
vice d
i
to add a new measurement w
j
to the en-
crypted data base (EDB). All the indexes are up-
dated accordingly.
Do Not Tell Me What I Cannot Do! (The Constrained Device Shouted under the Cover of the Fog): Implementing Symmetric Searchable
Encryption on Constrained Devices
121

• LocalSearch: This algorithm is executed by a user
in order to search for a measurement w
j
of a spe-
cific type, on the local Fog Node. The indexes are
updated and the Fog Node returns to the user the
encrypted ids that captured the measurement w
j
.
• GlobalSearch: This algorithm is executed by a
user in order to search for a measurement w
j
of a
specific type across multiple Fog nodes using the
CSP. The indexes are updated and the CSP also
returns to the user the encrypted ids that captured
the measurement w
j
.
Security Definitions: The security of an SSE
scheme depends on predefined leakage formalized by
a leakage function L = (L
search
,L
add
), whose com-
ponents correspond respectively to to the Search and
Add operations. Whenever the user triggers one of
these operations, the adversary ADV should not be
able to learn anything that the output of the corre-
sponding leakage function. The idea is the follow-
ing: ADV has full control of the client in the sense
that she can trigger search and add operations at will.
ADV issues a polynomial number of queries and for
each query she records the output. In the real exper-
iment, everything runs honestly. In the ideal exper-
iment however, a simulator S simulates all the func-
tionalities of the real scheme. The scheme is said to be
L-adaptively secure if ADV cannot distinguish be-
tween the real and ideal experiments
Definition 2 (Adaptive Security). Let DSSE =
(Setup,Search,Add) be a dynamic symmetric search-
able encryption scheme. Moreover, let L =
(L
search
,L
add
) be the leakage function of the scheme.
We consider the following experiments between the
adversary ADV and a simulator S :
Real Experiment.
1. Record = {}
2. for κ = 1 to q do
3. if op = Search
4. R
κ
← Search(param
κ
,EDB)
5. else (op = Add)
6. R
κ
← Add(param
κ
,EDB)
7. end if
8. Record = Record ∪ {R
κ
}
9. end for
10. b ← ADV (Record)
11. Output b
Ideal Experiment.
1. Record = {}
2. for κ = 1 to q do
3. if op = Search
4. R
κ
← S(L
search
(param
κ
))
5. else (op = Add)
6. R
κ
← S(L
add
(param
κ
))
7. end If
8. Record = Record ∪ {R
κ
}
9. end for
10. b ← ADV (Record)
11. Output b
The DSSE scheme is L- adaptively secure, with re-
spect to the leakage function L, iff for any PPT adver-
sary ADV issuing a polynomial number of queries
q(λ), ∃ PPT simulator S such that:
|Pr[Real
ADV
(λ,q) = 1] −
Pr[Ideal
ADV ,S,L
(λ,q) = 1|= negl(λ)
Informally, each search query leaks the outcome
of the search – The Access pattern– and whether two
queries were for the same keyword – The Search pat-
tern. We proceed with the formal definitions.
Definition 3 (Access Pattern). The Access Pattern for
a keyword w
i
is defined to be the set of nodes having
measured w
i
at a given time t. The set is denoted by
D
w
i
,t
.
Definition 4 (Search Pattern). The Search Pattern is
a vector sp that maintains a mapping between exe-
cuted queries and keywords. For example, sp[t] = w
j
denotes the query issued at time t, corresponding to
w
j
.
Hence, we conclude that:
Definition 5. The leakage function corresponding to
the Search operation, can be written as:
L
search
= L
0
(D
w
i
,t
,sp)
Where L
0
is a stateless function.
A DSSE scheme is said to be forward private if
for all insertions that take place after the successful
execution of the Setup algorithm, the leakage is lim-
ited to the size of the file, and the number of unique
keywords contained in it. In our case, since we do not
deal with files, the addition operation should not leak
any information at all. More formally:
Definition 6 (Forward Privacy). An L-adaptively SSE
scheme is forward private if the leakage function L
add
can be written as:
L
add
(id(d
i
)) = L
0
(c
id(w
i
)
)
Where L
0
is a stateless function.
IoTBDS 2020 - 5th International Conference on Internet of Things, Big Data and Security
122

4 SYSTEM MODEL
In this section, we provide a description of our system
model by defining the main entities along with their
respective capabilities. Our system model consists of
the sensor nodes referred to as Data Owners (DO), a
set of registered users U, a set of fog nodes F , and a
Cloud Service Provider CS P .
Data Owners. Let D = {d
1
,.. .,d
n
} be the set of all
sensor nodes in our environment deployed to regis-
ter the occurrence of specific environmental events.
The data owners in our system model are able to
add and update encrypted data using our proposed
scheme. For the purposes of our implementation,
we utilize the Zolertia Re-Mote board devices that
are based on the Texas Instruments CC2538 ARM
Cortex-M3 system on chip (SoC). These boards fea-
ture a 2.4GHz IEEE 802.15.4 RF Interface, running
up to 32MHz with 512KB of programmable flash
and 32KB of RAM while possessing a built-in battery
charger (500 mA) with energy harvesting capabili-
ties as well as a CC1200 868/915MHz RF transceiver
which allows for dual band operation. The functions
performed by a data owner are:
• Register the occurrence of a sensed event (e.g.
Temperature, Humidity, etc). Data about a sensed
data is referred to as keyword throughout the rest
of this paper and is denoted by w
i
.
• Generate a hash of data about every sensed event
h(w
i
).
• Generate a unique identifier id
j
for each sensed
event based on the sensing device’s id, timestamp
and the nature of the event (i.e. temperature, hu-
midity, etc).
• Encrypt the unique identifier with a symmetric
key K to generate a keyword value, c
id(w
i
)
, that
corresponds directly to each keyword.
The sensor device then sends both h(w
i
) and c
id(w
i
)
to
the nearest fog node.
Fog Nodes. Let F = { f
1
,.. ., f
m
} be a set of all fog
nodes in our environment. In this work, we consider
a fog node that provides support for a TEE. The spec-
ifications of the TEE are considered to be beyond the
scope of our implementation. Each fog node f
i
de-
fines a sub-network that consists of multiple sensor
devices d
f
i
1
,.. .,d
f
i
n
. During the first run of our pro-
tocol, the fog node generates three indexes.
• The NoApp[w
i
], which contains the hash of the
keyword along with the number of times it has re-
ceived that keyword.
• The NoSearch[w
i
], which contains the number of
times a user has searched for the keyword.
• The Dict, which contains a mapping between each
keyword and a unique identifier of the sensor node
that sent it.
The fog node then stores a local copy of all three in-
dexes and sends a copy of Dict to CS P along with the
identity of the fog node f
j
.
Users. We denote with U = {u
1
,.. .,u
p
} the set of
all users registered in the network to search, perform
computations and receive updates on sensed events.
These users submit a hash of a keyword h(w
j
) to a
nearest fog node for the computation of a search to-
ken. The user has the option to search locally on a
single fog node f
j
or to perform a global search in-
volving multiple fog nodes (in this case, the CSP per-
forms the search).
Cloud Service Provide (CSP). In this work, we con-
sider a top level cloud computing service much like
the one described in (Paladi et al., 2017). However,
unlike the fog nodes, we do not require the CSP to
have support for a TEE. The CSP creates a merged
dictionary comprising of all Dict and the identity of
the fog node f
j
that sent it.
5 SEARCHING IN THE FOG
In this section, we present a detailed description
of the Searching in the Fog scheme (a multi client
DSSE scheme for IoT devices with forward privacy)
along with the construction of the core algorithms the
scheme utilizes. The proposed scheme takes advan-
tage of the Fog computing paradigm to provide effi-
cient computational operations and decrease commu-
nication latency. Our protocol is made up of two main
algorithms; (i) Add Data and (ii) Search Data. The
proposed scheme is influenced by the forward private
scheme proposed in (Bakas and Michalas, 2019b)
Add Data. The Add Data algorithm is undertaken
by both a sensor device, d
f
j
and the nearest fog node
f
j
. The d
f
j
is deployed to register the occurrence of
an environmental event such as temperature, humid-
ity, motion, etc. Data about a sensed event is referred
to as a keyword w
i
. Once an event has been registered,
w
i
is hashed to produce h(w
i
). d
f
j
then generates a
unique identifier that will be used to identify the par-
ticular keyword. This unique identifier ID is made
up on the sensor device’s id, timestamp and the type
of event being registered (i.e. temperature, humidity,
etc). The ID is then encrypted with a secret shared key
K
SKE
to produce c
id(w
i
)
(line 4 of algorithm 1). The
sensor device sends h(w
i
) and c
id(w
i
)
to the nearest fog
node.
Do Not Tell Me What I Cannot Do! (The Constrained Device Shouted under the Cover of the Fog): Implementing Symmetric Searchable
Encryption on Constrained Devices
123
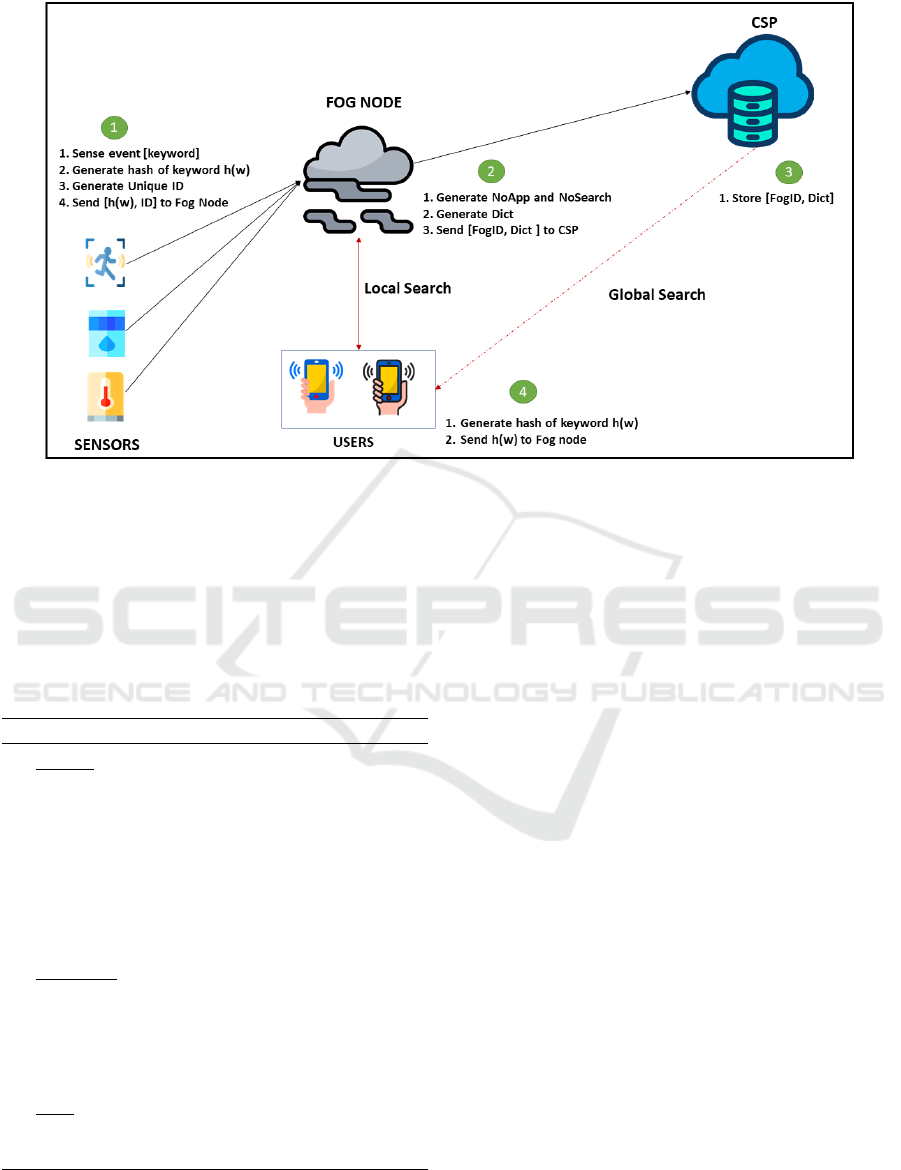
Figure 1: System Architecture.
Upon receipt by the fog node, f
j
retrieves the
corresponding NoApp[h(w
i
)] and NoSearch[h(w
i
)]
from the local database based on h(w
i
). Using
NoApp[h(w
i
)], the fog node computes the Dict ad-
dress addr
w
i
for the c
id(w
i
)
received from d
f
j
(line 6
- 9 of algorithm 1). Once this stage is done, f
j
sends
a copy of the dictionary and its identity [FogID,Dict]
with the C S P .
Algorithm 1: Add Data.
Sensor
1: Register data about a sensed event w
i
2: Compute hash of the data h(w
i
)
3: Generate a unique identifier for the sensed data
ID. (ID = SensorID||t||T ), where SensorID is the
unique id of the sensor, t is the timestamp, T is
the type of the measurement.
4: Compute c
id(w
i
)
= Enc
K
SKE
(ID)
5: Send [h(w
i
),c
id(w
i
)
] to the nearest Fog Node
Fog Node
6: NoApp[h(w
i
)] + +
7: K
w
i
= H (K
h
,h(w
i
)||NoSearch[h(w
i
)])
8: addr
w
i
= h(K
w
i
,NoApp[h(w
i
)]||0)
9: Map = Map ∪ {addr
w
i
,c
id(w
i
)
}
10: Send [Map,FogID] to CSP
CSP
11: Add Map into central Dict and store along with
the FogID
Search Data: For a successful run of the Search
Data algorithm, we assume that the user has access to
the secret shared key K
SKE
(used by the sensor device
in line 4 of algorithm 1 to encrypt the ID). Users can
search for a sensed input value, w
i
with the aid of the
nearest fog node f
j
. To perform the search data algo-
rithm, a user u
k
computes the hash value, h(w
i
), of the
sort after value w
i
and sends to the nearest fog node
f
j
. Our scheme provides support for two variations of
the search algorithm; (i) Local search, which involves
just one fog node, and (ii) Global search, which in-
volves multiple fog nodes and the CSP. We describe
both instances of the Search Data algorithm below;
Local Search. This search algorithm involves
a single neighbouring fog node. Upon recep-
tion, f
j
retrieves the corresponding NoApp[h(w
i
)]
and NoSearch[h(w
i
)] from the local database. Af-
ter f
j
receives these values, it computes K
w
i
=
h(K
h
,h(w
i
)||NoSearch[w
i
]) in order to calculate the
addresses addr
w
i
of all instances of h(w
i
) in the
dictionary Dict. The fog node then increases
NoSearch[h(w
i
)], which is then used to compute a
new key K
w
i
0
. The new key is used to calculate new
addresses addr
w
i
0
, which is packed in a list L
s
. Based
on the initial addresses generated, f
j
retrieves the cor-
responding ciphertext values, c
id(w
i
)
, in the locally
stored dictionary Dict. The ciphertext values are re-
turned to the user for decryption and the addresses
replaced with the new addresses in L
s
.
Global Search. This search algorithm constitutes
searching over multiple fog nodes and the CSP. We
designed this algorithm to be used in the event that
a user wishes to search for a specific keyword in an
entire region spanning multiple fog nodes. Upon the
IoTBDS 2020 - 5th International Conference on Internet of Things, Big Data and Security
124

reception of h(w
i
) from a user, a neighbouring fog
node, f
j
, generates a search token that is forwarded
to the CSP. The search token is generated by retriev-
ing the NoApp[h(w
i
)] and NoSearch[h(w
i
)] values of
h(w
i
) from the local database. The fog node proceeds
to compute K
w
i
= h(K
h
,h(w
i
)||NoSearch[w
i
]) in or-
der to calculate the addresses addr
w
i
of all possible
instances of h(w
i
) in the merged Dict at the CSP. A
list L
s
is created containing all the addresses. The fog
node then increases NoSearch[h(w
i
)], which is then
used to compute a new key K
w
i
0
. The new key is
used to calculate new addresses addr
w
i
0
, which is also
packed into another list L
s
0
. Both lists, (L
s
,L
s
0
), along
with the user’s identity is sent to the CSP.
Upon reception of the lists, the CSP uses the ad-
dresses in L
s
to search the central Dict for the corre-
sponding ciphertext values c
id(w
i
)
. The CSP returns
the ciphertext values to the user and replaces corre-
sponding addresses with a new address in L
s
0
.
Algorithm 2: Search Data - Local Search.
User
1: Compute and send h(w
i
) to the Fog Node Fog
node is TEE enabled
Fog Node
2: Retrieve the values NoApp[h(w
i
)] and
NoSearch[h(w
i
)] from the local database
3: K
w
i
= H(K
h
,h(w
i
)||NoSearch[w
i
])
4: NoSearch[w
i
] + +
5: K
w
i
0
= H(K
h
,h(w
i
)||NoSearch[h(w
i
)])
6: L
s
= {}
7: for i = 1 to i = NoApp[h(w
i
)] do
8: addr
w
i
= h(K
w
i
0
,i||0)
9: L
s
= L
s
∪ {addr
w
i
}
10: R = {}
11: for i = 1 to i = NoApp[h(w
i
)] do
12: c
id(w
i
)
= Map[h(K
w
,i||0)]
13: R = R ∪ {c
id(w
i
)
}
14: Delete the row on Map and update it accord-
ing to the address in L
s
15: Send R to the user
5.1 A Protocol-based Approach
In this section, we present a protocol-based approach
of our construction based on the algorithms we de-
scribed. We assume that each entity has a public and
private key pair and that all the public keys are pre-
shared and that each sensor node of the same sub-
network shares the same symmetric key K
SKE
gen-
erated by the Fog Node
1
1
Key sharing is out of the scope of this paper. However,
interesting approaches that fit squarely the cloud paradigm
Algorithm 3: Search Data - Global Search.
User
1: Compute and send h(w
i
) to the Fog Node Fog
node is TEE enabled
Fog Node
2: Retrieve the values NoApp[h(w
i
)] and
NoSearch[h(w
i
)] from the local database
3: K
w
i
= H(K
h
,h(w
i
)||NoSearch[w
i
])
4: NoSearch[w
i
] + +
5: K
w
i
0
= H(K
h
,h(w
i
)||NoSearch[h(w
i
)])
6: L
s
= {}
7: for i = 1 to i = NoApp[h(w
i
)] do
8: addr
w
i
= h(K
w
i
,i||0)
9: L
s
= L
s
∪ {addr
w
i
}
10: L
s
0
= {}
11: for i = 1 to i = NoApp[h(w
i
)] do
12: addr
w
i
0
= h(K
w
i
0
,i||0)
13: L
s
0
= L
s
0
∪ {addr
w
i
0
}
14: Send (L
s
,L
s
0
) to the CSP
CSP
15: R = {}
16: for i = 1 to i = Sizeof(L
s
) do
17: c
id(w
i
)
= Dict[L
s
[i]]
18: R = R ∪ {c
id(w
i
)
}
19: Delete the row on Dict and update it accord-
ing to the address in L
s
0
20: Send R to the user
To add a new measurement w
i
to the lo-
cal Fog Node f
j
, a sensor node d
f
j
i
first cal-
culates h(w
i
) and then generates the unique
ID of the measurement. As a next step, it
computes the value c
id(w
i
)
and finally, sends
m
1
= hr
1
,h(w
i
),c
id(w
i
)
,σ
i
(h(r
1
,h(w
i
),c
id(w
i
)
))i,
where r
1
is a random number. Upon reception, f
j
verifies both the freshness of the message and the
signature and proceeds by calculating the address of
the measurement addr
w
i
. Finally, f
j
stores addr
w
i
and
c
id(w
i
)
to its local dictionary and also sends them to
CSP along with its unique identifier FogID via m
2
=
hr
2
,Map,pk
CSP
(FogID),σ
f
j
(h(r
2
||Map||FogID))i.
The CSP verifies the freshness and the signature and
stores w
addr
and c
id(w
i
)
to the global dictionary Dict
along with the identity of the fog node.
When a user u
i
wishes to search on the
encrypted database, she first hashes the key-
word w
j
she is looking for and then sends
the result h(w
i
) to the Fog Node f
k
via m
3
=
hr
3
,h(w
i
),Enc
pk
f
k
(flag),σ
u
i
(h(r
3
||h(w
i
)||flag))i,
and leverage the power of secure hardware can be found
in (Michalas, 2019; Bakas and Michalas, 2019a; Michalas
et al., 2019b; Michalas et al., 2019a).
Do Not Tell Me What I Cannot Do! (The Constrained Device Shouted under the Cover of the Fog): Implementing Symmetric Searchable
Encryption on Constrained Devices
125

where flag ∈ {local,global}. If flag = local, then
f
k
proceeds with the search as described in Algo-
rithm 2 and sends the result R back to the u
i
via
m
4
= hr
4
,R,σ
f
k
(h(r
4
||R)). R is a list on encrypted
id’s so there is no need to re-encrypt it. On the other
hand, if flag = global, f
k
computes the lists L
s
and
L
0
s
as described in Algorithm 3 and forwards them
to the CSP via m
5
= hr
5
,L
s
,L
0
s
,σ
f
k
(h(r
5
||L
s
||L
0
s
))i.
Upon reception, the CSP will verify the freshness
and the signature of the message. If the verification is
successful, the CSP proceeds with locating the entries
on Dict that correspond to the search keyword and
updates Dict as specified by the L
0
s
. Finally, the result
R is outsourced to u
i
via m
6
= hr
6
,R,σ
CSP
(h(r
7
||R))i.
6 SECURITY ANALYSIS
We prove the security of our construction according
to definition 2 in Section 3. Our goal is to construct a
simulator S that will simulate the addition and search
tokens in such a way that no PPT adversary ADV
will be able to distinguish whether the tokens were
generated by the real algorithms or by S.
Theorem 1. Let SKE be an IND-CPA secure sym-
metric key cryptosystem. Moreover, let h be a secure
cryptographic hash function. Then, our construction
is secure according to definition 2.
In a pre-processing phase S generates a key for
the IND-CPA secure cryptosystem. Moreover, S gen-
erates a dictionary KeyStore to store the last key as-
signed to each keyword and a dictionary Oracle to re-
ply to the random oracle queries. Both of these dictio-
naries can be resized over time. To prove our theorem,
we make use of a hybrid argument.
Proof. Hybrid 0: Everything runs as specified by
the protocol.
Hybrid 1: Like Hybrid 0 but now S gets as input
L
add
and proceeds as follows:
Add Token Simulation
Generate a random string s
val ← Enc(K
SKE
,0
λ
)
v = val ⊕ id(d
i
)
Output (s,val)
Based on s simulate a random address a
Store (c
id(w
i
)
,{a,v}) into Dict
The random string s has exactly the same length
as the output of the hash function h. Moreover, due
to the IND-CPA security of the encryption scheme,
ADV cannot distinguish between the real encryption
of the node id and that of zeros. Thus we have:
(1)|Pr[Hybrid 0 = 1]−Pr[Hybrid 1 = 1]|= negl(λ)
Hybrid 2: Like Hybrid 1 but now S gets as input
L
search
. S proceeds as follows:
Search Token Simulation
: Number of c
id(w
i
)
to be retuned
R = {}
if KeyStore[w
j
] = Null
yo KeyStore[w
j
] ← {0,1}
λ
for i = 1 to i =
yo if Oracle[K
w
j
][0][i] is Null
yoyo Pick a (c
id(w
i
)
,{a
i
,v
i
}) pair
yo else
yoyo a
i
= Oracle[K
w
][0][i]
yoyo v
i
= Oracle[K
w
][1][i]] ⊕ val
yoend if
yo Remove a
i
from the dictionary but keep v
i
yo R = R ∪ {c
id(w
i
)
}
end for
U pdatedVal = {}
K
0
w
← {0,1}
λ
KeyStore[w
j
] = K
0
w
j
for i = 1 to i =
yo Generate new a
i
and match it with v
i
that
was kept from before
yo Add (c
id(d
i
),{a
i
,v
i
}) to the dictionary
yo U pdatedVal = U pdatedVal ∪ {c
id(w
i
)
,a
i
}
yo Oracle[K
0
w
j
][0][i] = a
i
yo Oracle[K
0
w
j
][1][i] = v
i
⊕ c
id(w
i
)
end for
τ
s
(w) = (K
w
j
,,U pdatedVal)
R is retuned to ADV
The KeyStore[w] dictionary is used to keep track
of the last key K
w
used for each keyword w. The
Oracle[K
w
][ j][i] dictionary is used to reply to ADV’s
queries. For example, Oracle[K
w
][0][i] represents the
address of a Dict entry assigned to the i − th id con-
tained in the result R. Similarly, Oracle[K
w
][1][i] rep-
resents the masked value needed to recover id(d
i
). It
is clear, that the simulated search token has exactly
the same size and format as the real one and thus:
(2)|Pr[Hybrid 1 = 1]−Pr[Hybrid 2 = 1]|= negl(λ)
By combining equations (1) and (2) we get:
|Pr[Hybrid 0 = 1] − Pr[Hybrid 2 = 1]|= negl(λ)
which is equivalent to:
|Pr[Real
ADV
(λ,q) = 1] −
Pr[Ideal
ADV ,S,L
(λ,q) = 1|= negl(λ)
And thus our proof is complete.
IoTBDS 2020 - 5th International Conference on Internet of Things, Big Data and Security
126

6.1 Side Channel Attacks
Many recent works (Xu et al., 2015; Lee et al., 2017;
Costan and Devadas, 2016) have shown that SGX is
vulnerable to software attacks. However, according
to (Fisch et al., 2017) leakage can be avoided if the
programs running in the enclaves do not have mem-
ory access patterns or control flow branches that de-
pend on the values of sensitive data. In our case, no
heavy computations occur in the Fog Node enclave
and the only operattion is is the application of a hash
function. To this end, we could use leakage resilient
primitives as in (Taha and Schaumont, 2014). Hence,
by assuming a constant time implementation for the
software running in an SGX enclave, our construction
is secure against timing attacks.
7 EXPERIMENTAL RESULTS
In this section, we present the results of experi-
ments conducted to demonstrate the feasibility of our
proposed work. Our experiments focused primarily
on evaluating the performance of the algorithms de-
scribed in section 5 on both the sensor device and the
fog node. For this work, we utilized a zolertia device
with 512KB programmable flash and 32KB RAM as
our sensor device while using an Intel i7 Ubuntu desk-
top with 16GB RAM as the fog node. To implement
the necessary algorithms, we developed a Contiki-NG
application on the sensor device written in C, using
modified cryptographic functions from the Tinycrypt
library (Wood, 2019). On the fog node, we developed
a node js application to interact with a local database.
With regards to this database, our dictionary is im-
plemented as tables in a MySQL database hosted on
the fog node. Although existing works in the field of
SSE rely on data structures such as arrays, maps, sets,
lists, trees, etc, we opted for a relational database to
represent a persistent storage.
The experiments measure the performance of the
core cryptographic components of our work on the re-
source constrained sensor device, as well as the over-
all performance of the add and search algorithms us-
ing datasets of arbitrary sizes.
Datasets: To comprehensively measure the perfor-
mance of both the search and add algorithms, it was
important that we utilized datasets of different sizes.
Due to the uniqueness of our work, the datasets had
to be created as part of our experiments (i.e. using
the add algorithm of the protocol). We left the sensor
device to collect the temperature in a room every 5s
Table 1: Dataset Size.
Duration (hrs) Number of Entries
DS1 1 737
DS2 4 2,844
DS3 12 8,617
DS4 24 17,287
for a varying number of hours and forwarded that in-
formation to the fog node. We did this for 1hr, 4hrs,
12hrs and 24hrs with a temperature range of 10-to-35
degrees (Table 1).
Add Algorithm: This part of our work consists of
two phases and is performed on both the sensor device
and the fog node:
PH1: The sensor device collects data on a sensed
event, generates a unique id, hashes the data
about the sensed event, encrypts the unique id,
and finally sends both the hashed data and the
ciphertext to the fog node;
PH2: The fog node retrieves the NoApp and
NoSearch from the database based on the
hashed message received from the sensor de-
vice, builds the encrypted index and generates
the dictionary.
We measure the total performance of the add algo-
rithm by evaluating the performance of the crypto-
graphic components on the sensor device and the time
taken by the fog node to complete the algorithm.
Performance of Cryptographic Components on
Sensor Device. As mentioned during the description
of our dataset, the sensor device is left to collect mea-
surements for a varying period of time. From table 1,
it is observed that, for a timespan of 24 hours, the sen-
sor device and the fog node run through various por-
tions of the add algorithm 17,287 times. The system
time for the CC2538 platform for which the sensor
device is based on is represented as CPU ticks. As a
result of this limitation, the performance metrics on
the sensor devices are recorded in ticks and externally
converted to seconds. Specific figures are derived by
dividing the number of ticks by 128 (CPU ticks per
second (Kurniawan, 2018)). In 17,287 iterations of
the first part of the add function, the sensor device
takes an average of 4.5 ticks to generate the hash of
the keyword (temperature) and the ciphertext of the
unique filename. This corresponds to 0.035s.
Execution Time on the Fog Node. In this part of
our experiments, we measured the time taken by the
fog node to build the index table and generate the en-
crypted dictionary. For 17,287 runs of our protocol,
the fog node takes an average of 14.516ms for each
Do Not Tell Me What I Cannot Do! (The Constrained Device Shouted under the Cover of the Fog): Implementing Symmetric Searchable
Encryption on Constrained Devices
127

keyword hash received from the sensor device. This
time includes the time taken to query and update the
database. This is a very encouraging result as it illus-
trates that the fog node will continue to be very effi-
cient even if we increase the number of sensor devices
that communicate with it. We acknowledge that the
results for this section would better resemble real life
scenarios if we utilized multiple sensor devices. Un-
fortunately, our current implementation supports just
one sensor device per fog node.
From the measurements described above, it can
be seen that the add algorithm is quite efficient and
fast. Hence, we can safely assume that there will be
no backlog on both the sensor device and the fog node
even if the sensor device collects data every 1s and
sends to the fog node. The total execution time of the
add algorithm is 0.0495s.
Search Algorithm: In this part of our experiments,
we measured the total time taken to complete the
search algorithm over the encrypted dictionary gener-
ated by the add algorithm. As described in Section 5,
the search algorithm is performed on the fog node in a
local search and is performed on the CSP in a global
search. For the purposes of our experiments, we as-
sumed that the CSP has the same specifications as the
fog node. Hence, the performance of both the local
and global search will only vary based on the size of
the dataset. The search time is calculated by measur-
ing the following:
1. Time taken by the fog node to generate a search
token from a hashed keyword sent by a user;
2. Time needed to find the respective matches in the
database;
3. Generate a new keyword address to replace the
address retrieved in the dictionary.
On average, the time taken to generate the search
token is 0.066ms. The search algorithm involves gen-
erating a new keyword address for every keyword
value found. As such, the actual search time also in-
cludes the time taken to generate new keyword ad-
dresses. Searching for a keyword that appears 760
times in a database with 17,287 entries takes approx-
imately 11.36s (i.e. time taken to find all the key-
word values and generate new keyword addresses for
all 760 instances of the keyword). The search al-
gorithm for a keyword that appears 22 times in a
database with 737 entries takes approximately 134ms.
These two times represent the fastest and slowest
search operation times for our experiments. The
search operation times correlate directly to the size
of the dataset and the number of times the keyword
appears in that dataset.
Table 2: Performance Summary.
Function Execution Time (ms)
Add (Sensor Side) 35
Add (Fog Node Side) 14.516
Total Add Algorithm 49.51
Search Token Generation 0.066
Science & Reproducible Research: To support
open science and reproducible research and to give
the opportunity to other researchers to use, test and
hopefully extend our scheme, the add algorithm and
search schemes for both the IoT device and Fog node
has been uploaded to Gitlab
2
and is available online.
Additionally, the scripts used for testing the search al-
gorithm have also been uploaded as a research artefact
(Open Access) on Zenodo
3
.
8 CONCLUSION
In this paper, we proposed a forward private dynamic
SSE scheme that can ran on constrained devices. Our
system model is utilizing fog computing to reduce the
computational burden on the sensor devices and in-
crease the overall efficiency of the scheme. Our pro-
posed scheme allows sensor devices to securely en-
crypt data on sensed events, store them in a remote
location and then search over the encrypted data with-
out revealing anything about the content of the stored
data. Our scheme achieves efficient computational
operations and supports the multi-client model. The
performance of the scheme is evaluated by conduct-
ing extensive experiments while its security is proven
through a theoretical analysis that considers the ex-
istence of a malicious adversary. From our experi-
ments, it is observed that the add function is highly
efficient even though it involves both the sensor de-
vice and a fog node. However, the search function’s
efficiency varied based on the size of the dataset and
the number of times the keyword appeared in that
dataset. This is because the fog node is required to
compute two addresses for each instance of a value
(the first address is used to find the sort after value
and the second address is used as a replacement for
the first address once the value has been returned).
We believe this work can serve as groundwork for re-
searchers who wish to build IoT services based on the
promising concept of SSE.
2
https://gitlab.com/nisec/fogsse-experiments.git
3
https://zenodo.org/record/3686873
IoTBDS 2020 - 5th International Conference on Internet of Things, Big Data and Security
128

ACKNOWLEDGEMENT
This research has received funding from the EU re-
search projects ASCLEPIOS (No. 826093) and CY-
BELE (No 825355).
REFERENCES
(2019). Edge computing vs. fog computing: Definitions and
enterprise uses.
Bakas, A. and Michalas, A. (2019a). Modern family: A re-
vocable hybrid encryption scheme based on attribute-
based encryption, symmetric searchable encryption
and sgx. In International Conference on Security and
Privacy in Communication Systems, pages 472–486.
Springer.
Bakas, A. and Michalas, A. (2019b). Multi-client symmet-
ric searchable encryption with forward privacy. IACR
Cryptology ePrint Archive, 2019:813.
Cao, M., Wang, L., Qin, Z., and Lou, C. (2019).
A lightweight fine-grained search scheme over en-
crypted data in cloud-assisted wireless body area net-
works. Wireless Communications and Mobile Com-
puting, 2019:1–12.
Costan, V. and Devadas, S. (2016). Intel sgx explained.
IACR Cryptology ePrint Archive, 2016(086):1–118.
Dimitriou, T. and Michalas, A. (2014). Multi-party trust
computation in decentralized environments in the
presence of malicious adversaries. Ad Hoc Networks,
15:53–66.
Dowsley, R., Michalas, A., and Nagel, M. (2016). A report
on design and implementation of protected searchable
data in iaas. Technical report, Swedish Institute of
Computer Science (SICS).
Dowsley, R., Michalas, A., Nagel, M., and Paladi, N.
(2017). A survey on design and implementation of
protected searchable data in the cloud. Computer Sci-
ence Review.
Etemad, M., K
¨
upc¸
¨
u, A., Papamanthou, C., and Evans, D.
(2018). Efficient dynamic searchable encryption with
forward privacy. Proceedings on Privacy Enhancing
Technologies, 2018(1):5–20.
Fan, Y., Zhao, G., Sun, X., Wang, J., Lei, X., Xia, F., and
Peng, C. (2019). A security scheme for fog computing
environment of iot. Proceedings of the 2nd Interna-
tional ACM Workshop on Security and Privacy for the
Internet-of-Things - IoT S and P19.
Fisch, B., Vinayagamurthy, D., Boneh, D., and Gorbunov,
S. (2017). Iron: functional encryption using intel
sgx. In Proceedings of the 2017 ACM SIGSAC Con-
ference on Computer and Communications Security,
pages 765–782. ACM.
IEEE (2018). Ieee standard for adoption of openfog refer-
ence architecture for fog computing.
Kalinin, M., Krundyshev, V., Zegzhda, P., and Belenko, V.
(2017). Network security architectures for vanet. Pro-
ceedings of the 10th International Conference on Se-
curity of Information and Networks - SIN 17.
Kurniawan, A. (2018). Practical Contiki-NG: Program-
ming for Wireless Sensor Networks. Apress.
Lee, S., Shih, M.-W., Gera, P., Kim, T., Kim, H., and
Peinado, M. (2017). Inferring fine-grained control
flow inside {SGX} enclaves with branch shadowing.
In 26th {USENIX} Security Symposium ({USENIX}
Security 17), pages 557–574.
Michalas, A. (2019). The lord of the shares: Combin-
ing attribute-based encryption and searchable encryp-
tion for flexible data sharing. In Proceedings of the
34th ACM/SIGAPP Symposium on Applied Comput-
ing, SAC ’19, pages 146–155, New York, NY, USA.
ACM.
Michalas, A., Bakas, A., Dang, H.-V., and Zalitko, A.
(2019a). Abstract: Access control in searchable en-
cryption with the use of attribute-based encryption
and sgx. In Proceedings of the 2019 ACM SIGSAC
Conference on Cloud Computing Security Workshop,
CCSW’19, page 183, New York, NY, USA. Associa-
tion for Computing Machinery.
Michalas, A., Bakas, A., Dang, H.-V., and Zaltiko, A.
(2019b). Microscope: Enabling access control in
searchable encryption with the use of attribute-based
encryption and sgx. In Nordic Conference on Secure
IT Systems, pages 254–270. Springer.
Mukherjee, M., Matem, R., Shu, L., Maglaras, L., Amine,
M., Choudhury, N., and Kumar, V. (2017). Security
and privacy in fog computing: Challenges. IEEE Ac-
cess.
Ni, J., Zhang, K., Lin, X., and Shen, X. (2018). Secur-
ing fog computing for internet of things applications:
Challenges and solutions. IEEE Communications Sur-
veys and Tutorials, 20(1):601–628.
Paladi, N., Gehrmann, C., and Michalas, A. (2017). Pro-
viding user security guarantees in public infrastruc-
ture clouds. IEEE Transactions on Cloud Computing,
5(3):405–419.
Taha, M. and Schaumont, P. (2014). Side-channel counter-
measure for SHA-3 at almost-zero area overhead.
Wood, M. (2019). Tinycrypt.
Xu, Y., Cui, W., and Peinado, M. (2015). Controlled-
channel attacks: Deterministic side channels for un-
trusted operating systems. In 2015 IEEE Symposium
on Security and Privacy, pages 640–656. IEEE.
Zheng, Q., Xu, S., and Ateniese, G. (2014). Vabks: Veri-
fiable attribute-based keyword search over outsourced
encrypted data. IEEE INFOCOM 2014 - IEEE Con-
ference on Computer Communications.
Do Not Tell Me What I Cannot Do! (The Constrained Device Shouted under the Cover of the Fog): Implementing Symmetric Searchable
Encryption on Constrained Devices
129
