
Towards Secure Data Sharing Processes in Online Social Networks:
Trusty
Gulsum Akkuzu, Benjamin Aziz and Mo Adda
School of Computing, University of Portsmouth, PO1 3HE, Portsmouth, U.K.
Keywords:
Web 2.0 Application, Online Social Networks, Sharing Data.
Abstract:
The development of Web 2.0 has remarkably increased in today’s world. These development has also been
a reason for the increment of online social networks (OSNs). Web 2.0 is the roof of the online social net-
works since online social networks are built on Web 2.0. Users are given an environment in which they can
communicate with others without considering other users locations. The way of communication in OSNs is
done via sharing various contents of data, such as photos, texts, and videos. Sharing data sometimes cause
privacy problems in OSNs, especially in the case that the content involves different users information on itself.
Users are notified after the content is shared and they are allowed to remove tags. The content is still available
in OSNs platforms, users, therefore, find a way to punish other users with being unfriend, or they quit from
OSNs. However, both cases are contradictory with the main of OSNs. By considering the above issues, we de-
velop a framework in which users’ opinions are taken on data sharing process and based on the final decision,
which is taken by the user who posts the content, punishing or rewarding technique is used. We also evaluate
the proposed work with users interactions.
1 INTRODUCTION
The use of Web 2.0 applications have become remark-
ably common in our era, Web 2.0 concepts have in-
creased the development of Web-based services, ap-
plications, and social networking sites (Harris and
Rea, 2019). Online social networks (OSNs) are
well-known Web 2.0 applications, since OSNs are
free social networking sites with the development of
the Internet (Mata and Quesada, 2014). OSNs are
one of the main communication channels for peo-
ple, because, OSNs provide an environment to peo-
ple connect to each other regardless of their locations
(Akkuzu et al., 2019c). The way of communication
in OSNs environments is done via sharing contents
of data, such as, photo, text, video, or event (Keijzer
et al., 2018). Sharing data sometimes causes privacy
issues in OSNs, this is because of the fact that people
like sharing data which involves others users’ infor-
mation on it (Xu et al., 2018). OSNs users choose
two ways to protect themselves for such privacy is-
sues, one way to be unfriend with user, who leaks
his/her privacy, the other way quit from OSNs plat-
forms (Akkuzu et al., 2019a).
In some of the current OSNs platforms such as
Facebook, users are let to remove their ids from the
shared contents (Au, 2019). However, the shared con-
tent is still available which shows that removing the
tag is not a solution in OSNs. Removing the tag is
only available when the data is shared because people
are allowed to see the content they are related when it
is shared. There is no chance for people to give their
opinions in data sharing process in current OSNs. In
OSNs, it is a need to have a data sharing process in
which users, who are related to data, are given chance
to give their opinion when data is being shared. With
respect to this need in OSNs, we propose a framework
in this work. In the developed framework, users rep-
utation values are used to reward or punish the user
who shares the data based on his behaviours in the
sharing process. In order to show the applicability
of the proposed work, we implemented the proposed
work with a Web 2.0 application.
The rest of the paper is structured as follows; In
Section 2, we give similar works done in the web ap-
plication area. We then introduce the proposed work
in Section 3. In Section 4, the implementation of the
proposed work with its details and the analysis on the
implemented Web application are given. Finally, we
conclude the paper in Section 5.
418
Akkuzu, G., Aziz, B. and Adda, M.
Towards Secure Data Sharing Processes in Online Social Networks: Trusty.
DOI: 10.5220/0009806304180425
In Proceedings of the 15th International Conference on Software Technologies (ICSOFT 2020), pages 418-425
ISBN: 978-989-758-443-5
Copyright
c
2020 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

2 RELATED WORKS
Web 2.0 applications provide users an environment
where people can produce contents and disseminate
the produced content with others efficiently (Constan-
tinides and Fountain, 2008). Web 2.0 applications are
used for social networking and commercial purposes
(Mata and Quesada, 2014). Social networks applica-
tions and Web 2.0 terms are frequently considered to-
gether because the Web 2.0 is a baseline for social net-
works (Cooke and Buckley, 2008). In the last decade,
the usage of OSNs has become one of daily activi-
ties for people (Grabner-Kr
¨
auter, 2009). People have
been using the OSNs platforms in order to continue
their interactions with others. These communication
or interaction is mostly done via sharing contents of
data (Krasnova et al., 2010). Sharing data sometimes
cause privacy issues in OSNs because the shared con-
tent might include other users information on itself
(Akkuzu et al., 2019b).
Most of the current OSNs platforms provide the
tagging feature. Tagging is specifically classified in
to the multimedia content threats in (Rathore et al.,
2017). Users are allowed to tag other users on OSNs’
contents such as videos, and texts. This tagging fea-
ture unfortunately may cause privacy issues for other
users (Rathore et al., 2017). In OSNs platforms, Al-
though there are users who do not want to like be-
ing tagged on any contents, which is nor uploaded by
themselves, some of their friends can tag them and vi-
sualise not only their photos but also display their pro-
files (Squicciarini et al., 2010). Another issue is that
tagging may link someone who is not member of the
concerned OSN platform and does not want his infor-
mation being appeared in OSNs platforms (Gonz
´
alez-
Manzano et al., 2014). There is also another possible
scenario in which a spammer or malicious user can
tag large number of users in a single post, such as a
picture or video, in order to spread the malicious con-
tent to a large audience with little effort (Ahmed and
Abulaish, 2013).
Recently, Facebook, which is one of the most
common OSNs give users flexibility of removing the
tag on the shared content. It might be considered as
a solution for removing users’ names on the context,
however, the content is still available on other users’
personal pages. Above problems and solutions are
provided by research papers do not focus on having
users opinions on the co-owned content data sharing
process. Also they do not taken having the reputa-
tion systems into the consideration if users leak each
others’ privacy on co-owned data sharing processes in
OSNs platforms. In order to fill this gap in the litera-
ture, this work proposes a framework which is applied
on Web 2.0.
3 PROPOSED WORK
In current OSNs, each content of data has an owner
who produces, uploads, or creates the content. The
owner specifies the targeted group tags people and
takes the decision for sharing the data. If the tagged
users do not want their ids being seen on the content,
then they find ways to punish the user. The punish-
ment is either remove the tag, be unfriend with the
user, or quit from OSNs platforms. The current OSNs
do not have such systems which can award or punish
a user when the users behaves in a certain ways. Also
in the current OSNs, tagged users do not have chance
to express their opinions when data is being shared.
Users do not know which content of data is being
shared until it is appeared in OSNs. Many OSNs
users have serious problems in their lives because of
the privacy leakage which is originated from tagging
or sharing co-owned data (Yu et al., 2018). Quitting
from OSNs is a contradictory action to OSNs plat-
forms main aim, because OSNs are created to bring
people together, connect to each other (i.e. friend-
ship), and make to share contents of data (Heidemann
et al., 2012). Therefore, it is important to have OSNs
environments in which users should be able to express
their opinions in data sharing processes when they
are related to data (this type of data called co-owned
data) and also the OSNs platforms should use a pun-
ishment and awarding system when a user behaves in
a certain way in the co-owned data sharing processes.
With regards to those needs in OSNs platforms, we
have developed a framework which uses group deci-
sion making and users reputation values. The group
decision making technique is used to allow users to
express their opinions on data, which includes their
ids on data (in current OSNs it is tagging). The repu-
tation values are used to punish or award a user when
the user takes a decision on co-owned data.
Figure 1 represents the difference between the
proposed work structure and the current OSNs struc-
ture in a content of co-owned data sharing process.
As it is seen in the figure, the proposed framework
structure uses tagged users opinions before data is
being shared while the current OSNs do not allow
tagged users to give their opinions in the sharing pro-
cess. The proposed framework does not allow the
owner to share the content until tagged users give their
opinions, it is shown in the figure with dashed lines.
There are new actions which are assigned to the OSNs
platforms with the proposed work, one is “Notify the
owner with the taken decision” which refers that the
Towards Secure Data Sharing Processes in Online Social Networks: Trusty
419

system is responsible to notify the owner. The other
one is “Punish OR Award” which refers that the sys-
tem should take the responsibility for punishing or
rewarding the owner based on his final decision on
co-owned data. The proposed framework does not re-
move any of the current actions in OSNs platforms
but adds new actions for the OSNs platforms in or-
der to decrease “Removing tags, Quitting, and Being
Unfriend”.
Figure 1: Current Online Social Network Structure vice
versa the Proposed Social Network Structure.
In order to show the applicability of the proposed
work, we have developed an online social network
named with Trusty. In the following section, we give
the details of the Trusty.
4 Trusty SOCIAL NETWORK
Trusty is an online social network which has cur-
rently more than forty thousand users on it (visit
http://www.trusty.gen.tr/). The Trusty aims to make
a balance between data sharing and privacy protec-
tion in co-woned data sharing processes. It uses the
proposed framework which is given in the previous
section. The biggest difference between Trusty and
the current OSNs is that Trusty assigns a reputation
value to a user when a users become a member. We
now give a co-owned data sharing process in Trusty
step by step, the accounts which are used to show
the steps are test accounts. That shows that there is
no anonymity issue on the used accounts. The taken
steps are follows;
• Create an account
• Make friends/ Search friends
• Share a co-owned content
Creating an Account: Figure 2 represent the Trusty
main page, in order to create an account a user needs
to provide his/her first name, surname, email address
and password. Once the required information are pro-
vided by a users, log-in option is activated.
Figure 2: Trusty online social network main page.
Searching Friends: Figure 3 shows the search
engine in the Trusty. It is important to highlight that
all accounts which are used in this work are test ac-
counts.
Share a Co-woned Content: Figure 4 and Figure
5 show the process of sharing a co-owned data con-
tent. Taken steps are enumerated, first of all the owner
needs to create/upload the content of data see the step
1. Then decide who are related to the content, tag re-
lated users (co-owners) step 2. The number 3 shows
the tagged users ids. The user should also decide the
targeted group for the data. Until now, all steps are
very similar to the current OSNs. The step 5 is the
first difference in Trusty social network. In the current
OSNs, after taking the previous steps users share the
content of data while Trusty does not allow users to
share the content without notifying its co-owners. In
the current OSNs, there some techniques can be used
ICSOFT 2020 - 15th International Conference on Software Technologies
420
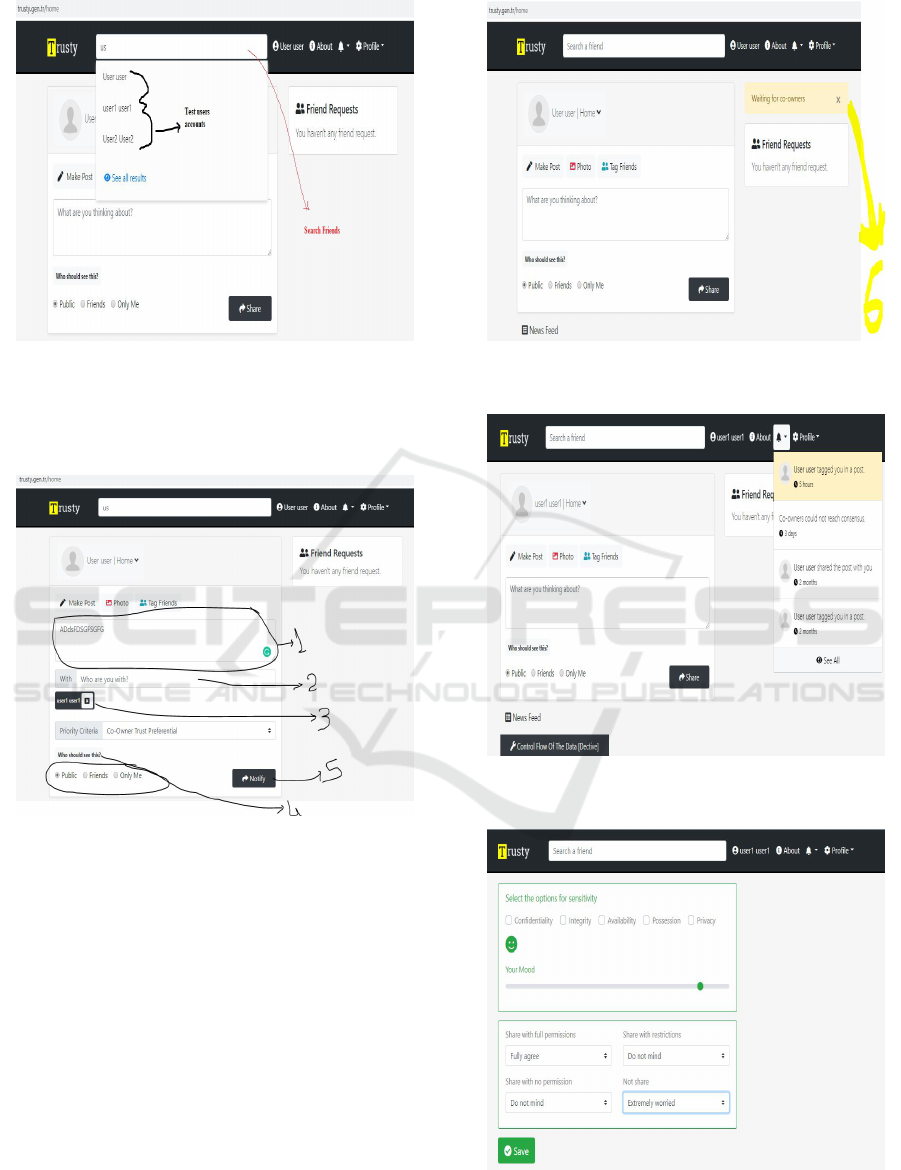
Figure 3: Trusty online social network search engine.
for this feature, for instance face recolonisation tech-
niques can be used. The highlighted point in Figure 5
meets the dashed line part in Figure 1.
Figure 4: Trusty online social network co-owned data shar-
ing steps.
After notifying the tagged users, the system is re-
sponsible to notify the co-owners. Figure 6 presents
how the notification is shown on the co-owner page.
Figure 7 represents the page on the owners’ sides in
order to take co-owners’ opinions on co-owned data
sharing process.
Figure 8 shows the page which gives the notifi-
cation on the owner’s page in order to show that co-
owners take the decision. Figure 9 presents the co-
owners’ decision to the owner.
As it is aforementioned, every user has a reputa-
tion value on users’ profiles. The reputation value
is visible by any user in Trusty network. Figure 10
shows the user’s profile with user’s reputation value.
The reputation value is increased by the system if the
Figure 5: Trusty online social network waiting for co-
owners opinion.
Figure 6: Trusty online social network notification on co-
owners page.
Figure 7: Trusty online social network asking for co-owners
opinions.
Towards Secure Data Sharing Processes in Online Social Networks: Trusty
421
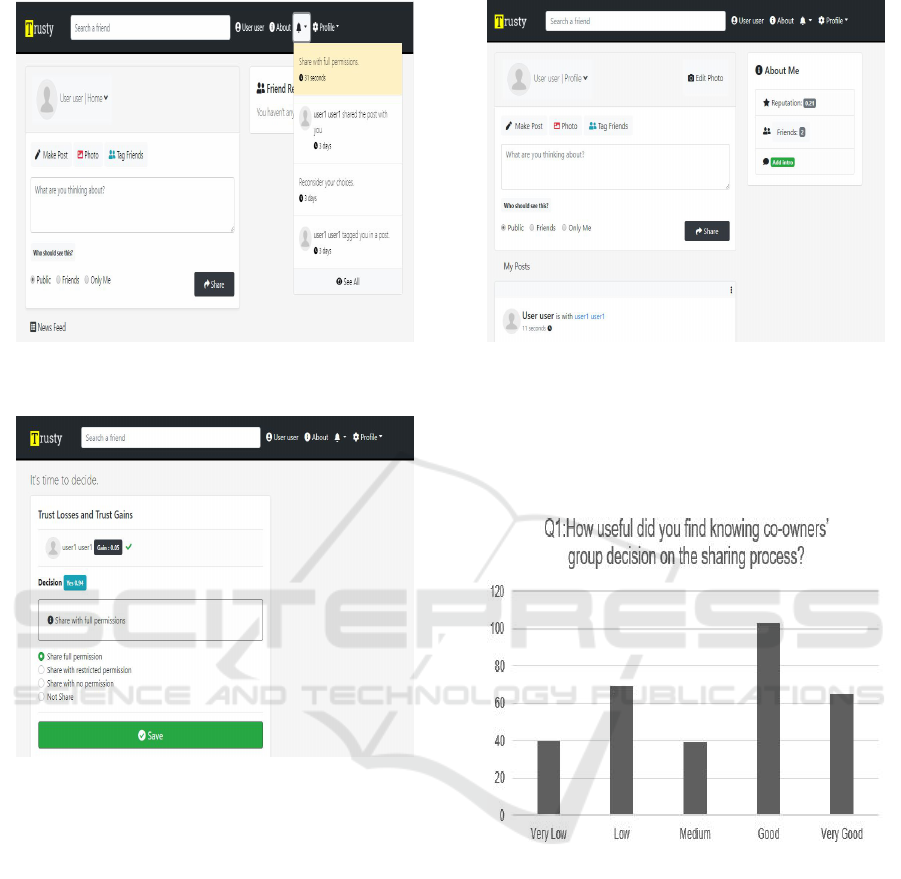
Figure 8: Trusty online social network notification on the
owner page.
Figure 9: Trusty online social network notification which
shows co-owners opinions.
user respects the co-owners’ decision. It is decreased
otherwise.
4.1 Analysis on the Trusty
In order to analyse the usability and the interoper-
ability of the Trusty online social network, we con-
ducted two questionnaires one for the users, who take
the owner role in a co-owned data sharing process,
the other one for the users, who take the co-owners
role in a co-owned data sharing process. The analy-
sis of each questionnaires are as follows; The results
obtained from owner respondents are given on Figure
11, Figure 12, Figure 13, Figure 14, and Figure 15.
Detailed explanations on each figure result are given
below.
Figure 11 provides the results obtained from the
analysis of the first question on the questionnaire
Figure 10: Trusty online social network user profile with
reputation.
which was completed by owners. From the results
in the figure, it is apparent that knowing co-owners’
group decision was found very useful by the majority
of owners in their co-owned data sharing process.
Figure 11: Evaluation on knowing group decision in co-
owned data sharing process.
Owners were asked to rate how useful did they find
knowing data sensitivity value in data sharing pro-
cess, Figure 12 indicates the results of respondents on
the question. There was a significant number of own-
ers found knowing the sensitivity value useful. How-
ever, it is important to mention that there was people
who did not find to know the data sensitivity value in
the sharing process.
Figure 13 provides the results obtained from anal-
ysis of results on question ”How useful did you find
knowing knowing the trust loss and trust gain values
in each co-owner in the sharing process?”. In the fig-
ure, the correlation between the number of choices on
Good and the number of choices on Low is interesting
ICSOFT 2020 - 15th International Conference on Software Technologies
422
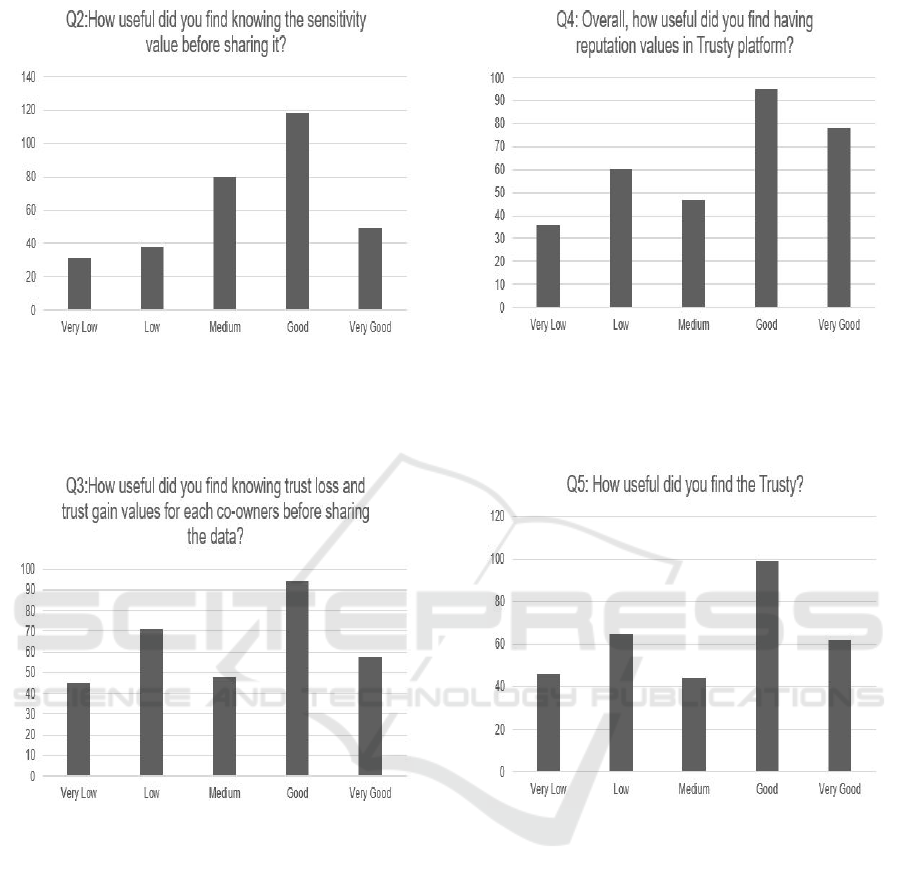
Figure 12: Evaluation on knowing co-owned data sensitiv-
ity value in sharing process.
because the difference between two choices is twenty
respondents.
Figure 13: Evaluation on knowing trust loss and trust gain
values in each co-owner.
From the result in Figure 14, it is apparent that
having reputation values in online social network was
found advantageous by respondents. The number of
respondents, who chose Low option, from this fig-
ure were compared with the number of respondents in
Figure 13 which shows the result for Low option, the
comparison analysis showed that people who chose
Low for both question were same. It can therefore be
assumed that those respondents do not want to know
they are punished for sharing the data.
The implementation of the developed models have
been done with Trusty online social network, there-
fore, it is important to have a question which can
be used to evaluate the network. Respondents were
asked to evaluate Trusty with question ”How use-
ful did you find the Trusty?”, of the 316 respondents
Figure 14: Evaluation on having reputation values in online
social networks.
who completed the questionnaire, just thirty percent
of them rated the Trusty with Good option.
Figure 15: Overall evaluation on Trusty social network.
As it is aforementioned, two questionnaires were
conducted, one was filled by data owners and the
other one was filled by data co-owners. Figure 16,
Figure 17, Figure 18, and Figure 19 represent the re-
sults obtained from data co-owners’ answers on the
questionnaire given in Appendices.
Figure 16 presents the results on the question
”How useful did you find giving your opinion on the
sharing process”, this question was developed to un-
derstand the applicability of group decision making in
online social networks. Of the data co-owners giving
their opinions in the sharing process, 50% rated either
good or very good.
Co-owners have been given chance to give their
concerns on co-owned data security features in order
to decide the data sensitivity value of a co-owned data.
Figure 17 presents the results on the question related
Towards Secure Data Sharing Processes in Online Social Networks: Trusty
423
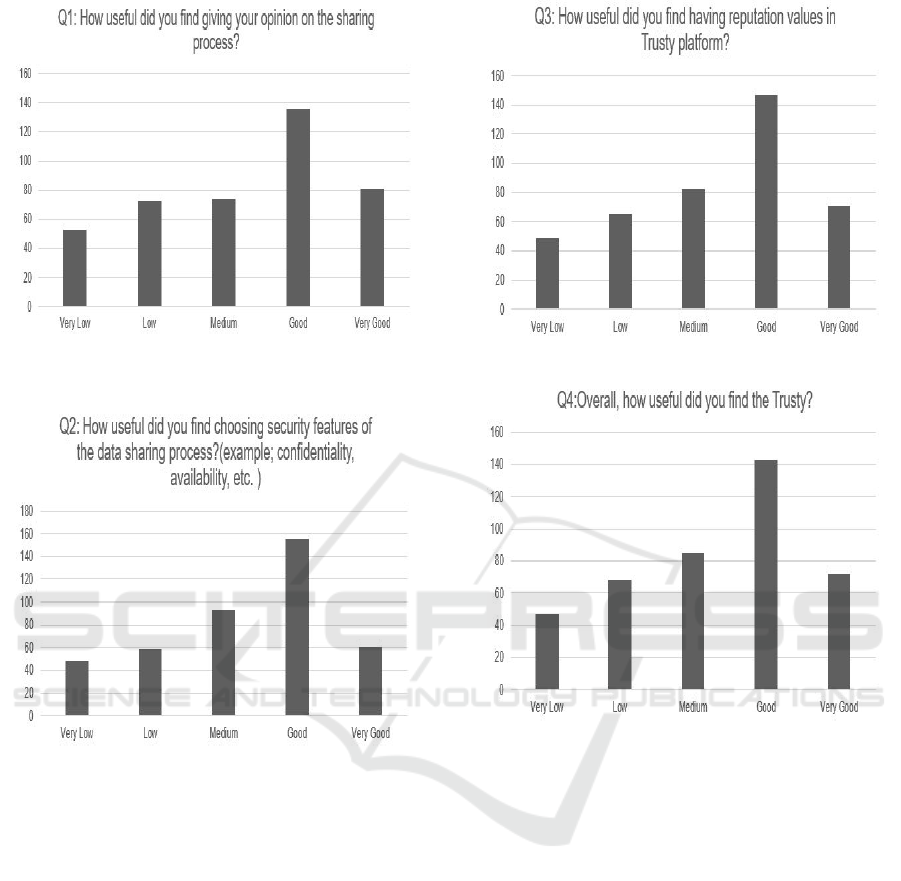
Figure 16: Evaluation of taking co-owners opinions on the
sharing process.
Figure 17: Evaluation on data security features.
to data security features, we can see that the majority
of co-owners chose the option Good.
The next question was related to having reputation
values in online social network platforms. This ques-
tion and the next question were same on data own-
ers’ questionnaire. From Figure 18, it is apparent that
having reputation values in online social networks,
specifically on Trusty, was considerably good.
The last question on the questionnaire was about
rating Trusty network. From the chart, it can be seen
that by far the greatest choice is for Good.
The implementation and analysis of the proposed
work have shown that it is a crucial need to use fuzzy
decision systems and users reputation values in co-
owned data sharing processes in OSNs. Users eval-
uation in the implemented work has shown that the
proposed work users have positive views on the im-
plemented models.
Figure 18: Evaluation of having reputation values in Trusty.
Figure 19: Overall evaluation on Trusty social network.
5 CONCLUSION
Web 2.0 applications have become remarkably com-
mon in today’s world. The Web 2.0 applications
and social networks terms are considered together be-
cause the Web 2.0 is a baseline for the social net-
works. The use of online social networks has been
one of the daily activities for people. People use the
online social networks for interacting others, the in-
teraction or communication is done via sharing data
in OSNs. Shared contents sometimes include more
than one user id on, this type of data sharing might
cause privacy problems in OSNs. In order to protect
users privacy, current OSNs provide precautions such
as removing tag on the shared content. However, re-
moving tag sometimes is not enough for users. The
problem here is that users are able to see the content,
which includes their ids, after it is shared not in the
process of sharing. In such cases, users choose ei-
ther being unfriend with the user, who leaks their pri-
ICSOFT 2020 - 15th International Conference on Software Technologies
424

vacy, or quit from OSNs platforms. Both actions are
contradicting with the main of OSNs because OSNs
main purpose is to bring people into OSNs ans sup-
port them to be friend with others. By considering
the above issues, we propose a framework which uses
a punishment and rewarding system in order to en-
courage users to consider other users’ opinions in a
data sharing process. We implemented our proposed
framework with a Web 2.0 application, named Trusty
social network. We then analysed the implemented
work with users evaluations. The result has shown
that users want to give their opinions when the con-
tent is being shared not after it is shared. The result
has also shown that using punishment and rewarding
system give users satisfaction on data sharing process.
REFERENCES
Ahmed, F. and Abulaish, M. (2013). A generic statistical
approach for spam detection in online social networks.
Computer Communications, 36(10-11):1120–1129.
Akkuzu, G., Aziz, B., and Adda, M. (2019a). Advantages of
having users’ trust and reputation values on data shar-
ing process in online social networks. In 2019 Sixth
International Conference on Social Networks Analy-
sis, Management and Security (SNAMS), pages 189–
195. IEEE.
Akkuzu, G., Aziz, B., and Adda, M. (2019b). Application
of extended iowa operator for making group decision
on co-owned contents in osns. In 10th IEEE Interna-
tional Conference on Intelligent Systems. Institute of
Electrical Engineers.
Akkuzu, G., Aziz, B., and Adda, M. (2019c). Fuzzy
logic decision based collaborative privacy manage-
ment framework for online social networks. In 3rd
International Workshop on FORmal Methods for Se-
curity Engineering: ForSE.
Au, M. Y. (2019). Removing sensitive parts of an image.
Constantinides, E. and Fountain, S. J. (2008). Web 2.0:
Conceptual foundations and marketing issues. Jour-
nal of direct, data and digital marketing practice,
9(3):231–244.
Cooke, M. and Buckley, N. (2008). Web 2.0, social net-
works and the future of market research. International
Journal of Market Research, 50(2):267–292.
Gonz
´
alez-Manzano, L., Gonz
´
alez-Tablas, A. I., de Fuentes,
J. M., and Ribagorda, A. (2014). Cooped: Co-owned
personal data management. Computers & Security,
47:41–65.
Grabner-Kr
¨
auter, S. (2009). Web 2.0 social networks: the
role of trust. Journal of business ethics, 90(4):505–
522.
Harris, A. L. and Rea, A. (2019). Web 2.0 and virtual world
technologies: A growing impact on is education. Jour-
nal of Information Systems Education, 20(2):3.
Heidemann, J., Klier, M., and Probst, F. (2012). Online
social networks: A survey of a global phenomenon.
Computer networks, 56(18):3866–3878.
Keijzer, M. A., M
¨
as, M., and Flache, A. (2018). Communi-
cation in online social networks fosters cultural isola-
tion. Complexity, 2018.
Krasnova, H., Spiekermann, S., Koroleva, K., and Hilde-
brand, T. (2010). Online social networks: Why we dis-
close. Journal of information technology, 25(2):109–
125.
Mata, F. J. and Quesada, A. (2014). Web 2.0, social net-
works and e-commerce as marketing tools. Journal of
theoretical and applied electronic commerce research,
9(1):56–69.
Rathore, S., Sharma, P. K., Loia, V., Jeong, Y.-S., and Park,
J. H. (2017). Social network security: Issues, chal-
lenges, threats, and solutions. Information sciences,
421:43–69.
Squicciarini, A. C., Shehab, M., and Wede, J. (2010). Pri-
vacy policies for shared content in social network
sites. The VLDB Journal, 19(6):777–796.
Xu, L., Jiang, C., He, N., Han, Z., and Benslimane, A.
(2018). Trust-based collaborative privacy manage-
ment in online social networks. IEEE Transactions
on Information Forensics and Security, 14(1):48–60.
Yu, L., Motipalli, S. M., Lee, D., Liu, P., Xu, H., Liu, Q.,
Tan, J., and Luo, B. (2018). My friend leaks my pri-
vacy: Modeling and analyzing privacy in social net-
works. In Proceedings of the 23nd ACM on Sym-
posium on Access Control Models and Technologies,
pages 93–104.
Towards Secure Data Sharing Processes in Online Social Networks: Trusty
425
