
A Failure Rate Model of Bit-flipping Decoders for QC-LDPC and
QC-MDPC Code-based Cryptosystems
Marco Baldi
1 a
, Alessandro Barenghi
2 b
, Franco Chiaraluce
1 c
, Gerardo Pelosi
2 d
and Paolo Santini
1 e
1
DII, Università Politecnica delle Marche, Via Brecce Bianche 12, Ancona, Italy
2
DEIB, Politecnico di Milano, Piazza Leonardo da Vinci 32, Milano, Italy
Keywords:
Bit-flipping Decoding, Code-based Cryptosystems, Decoding Failure Rate, LDPC Codes, MDPC Codes,
Quasi-cyclic Codes, Post-quantum Cryptosystems.
Abstract:
The design of quantum-resistant cryptographic primitives has gained attraction lately, especially thanks to
the U.S.A. National Institute of Standards and Technology (NIST) initiative, which is selecting a portfolio
of primitives for standardization. A prime position in the set of asymmetric encryption primitives is occu-
pied by the ones relying on decoding random linear error correction codes as their trapdoor. Among these
primitives, the LEDAcrypt and BIKE cryptosystems have been admitted to the second round of the standard-
ization initiative. They are based on the adoption of iteratively decoded Low- and Moderate-Density Parity
Check (LDPC/MDPC) codes. Characterizing the decoding failure rate of such codes under iterative decoding
is paramount to the security of both the LEDAcrypt and BIKE second round candidates to achieve indis-
tinguishability under adaptive chosen ciphertext attacks (IND-CCA2). For these codes, we propose a new
iterative decoder, obtained through a simple modification of the classic in-place bit-flipping decoder and, in
this paper, we provide a statistical worst-case analysis of its performance. This result allows us to design
parameters for LDPC/MDPC code-based cryptosystems with guaranteed extremely low failure rates (e.g.,
2
−128
), fitting the hard requirement imposed by IND-CCA2 constructions.
1 INTRODUCTION
Building asymmetric cryptosystems resistant against
attacks performed with quantum computers requires a
change in the underlying computationally hard prob-
lem exploited to build a trapdoor. To this end, the aim
is to pick a problem either belonging, or equivalent
to one belonging, to the NP-Complete class (Karp,
1972). Problems belonging to such a computa-
tional complexity class are recognized to not have a
polynomial-time solution algorithm, even on quan-
tum computers. Among these problems we find the
one of decoding a syndrome obtained with a ran-
dom linear block code, and the one of finding a fixed
weight codeword in the said code (Berlekamp et al.,
1978). Indeed, McEliece was the first to propose a
cryptosystem relying on the hardness of the decoding
a
https://orcid.org/0000-0002-8754-5526
b
https://orcid.org/0000-0003-0840-6358
c
https://orcid.org/0000-0001-6994-1448
d
https://orcid.org/0000-0002-3812-5429
e
https://orcid.org/0000-0003-0631-3668
problem (McEliece, 1978), followed by the work of
Niederreiter (Niederreiter, 1986). The trapdoor func-
tion in these cryptosystems is constituted by the fact
that the secret linear block code they employ is not
random, but instead it is picked from a family of lin-
ear block codes for which an efficient decoding al-
gorithm is known. To prevent an attacker from deci-
phering, both cryptosystems provide as a public key
an obfuscated representation of the efficiently decod-
able code, obtained multiplying either its generator
matrix, or its parity-check matrix, by a random non-
singular conformant one. Code-based cryptosystems
have a remarkably good security track, whenever the
hidden code structure is a binary Goppa code (which
is the one originally proposed by McEliece). How-
ever, such strength comes at the disadvantage of quite
large public key sizes (in the hundreds of kilobytes
to a megabyte range). Willing to reduce the key size,
a significant amount of research work was aimed at
employing code families admitting a space-efficient
representation. Quasi-Cyclic (QC) codes provide a
good avenue to decrease the required key sizes by two
238
Baldi, M., Barenghi, A., Chiaraluce, F., Pelosi, G. and Santini, P.
A Failure Rate Model of Bit-flipping Decoders for QC-LDPC and QC-MDPC Code-based Cryptosystems.
DOI: 10.5220/0009891702380249
In Proceedings of the 17th International Joint Conference on e-Business and Telecommunications (ICETE 2020) - SECRYPT, pages 238-249
ISBN: 978-989-758-446-6
Copyright
c
2020 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

orders of magnitude or more. Such codes are char-
acterized by generator and parity-check matrices that
are quasi-cyclic, i.e., composed by circulant square
blocks, where all rows are obtained cyclically rotat-
ing the first one. It is therefore sufficient to store
only the first row of such matrices to preserve their
entire representation. However, employing QC alge-
braic codes has proven to yield security concerns, as
the additional structure given by the quasi-cyclicity
might allow for the efficient recovery of the underly-
ing secret code (Faugère et al., 2010), and this was
reflected by the elimination of QC algebraic candi-
dates from the NIST standardization process (Alagic
et al., 2019). By contrast, families of QC codes de-
fined by a pseudo-random sparse parity-check matrix
without any underlying algebraic structure, other than
their sparsity, do not suffer from the same security
issues, thus leading to the well-assessed proposal of
Quasi-Cyclic Low-Density Parity-Check (QC-LDPC)
codes (Baldi et al., 2007) or Quasi-Cyclic Moderate-
Density Parity-Check (QC-MDPC) codes (Misoczki
et al., 2013) as code families to build instances of ei-
ther the McEliece or the Niederreiter cryptosystem.
The downside of such code families resides in
their decoding procedures, which have a non null
probability of failing, known as Decoding Failure
Rate (DFR). This, in turn, implies that a decryption
action, which relies on the (secret) code decoder, may
fail even on a valid ciphertext. Besides the possible
functional hindrances caused, a non null DFR im-
poses the strict requirement to employ such code-
based encryption/decryption algorithms as building
blocks of constructions providing resistance against
active attackers. Indeed, active attacks, such as the
ones in (Guo et al., 2016; Fabši
ˇ
c et al., 2017; San-
tini et al., 2019b) were shown to be able to exploit the
availability of a decryption oracle, which is the typ-
ical scenario of a Chosen Ciphertext Attack (CCA),
to extract information on the secret QC-LDPC/QC-
MDPC code. To completely avoid these kinds of at-
tacks and attain Indistinguishability under Adaptively
Chosen Ciphertext Attack (IND-CCA2) guarantees,
state-of-the-art constructions, such as (Hofheinz et al.,
2017; Bindel et al., 2019), require the failure rate of
the scheme to be negligible in the security parameter.
Essentially, this implies that codes exhibiting a prob-
ability of decoding failure equal or lower than 2
−λ
must be employed to design a cryptosystem with se-
curity parameter equal to λ. It is clear that assess-
ing such low values of DFR through numerical sim-
ulations is unfeasible; thus, a reliable model for the
behavior of decoders for QC-LDPC and QC-MDPC
codes has become a major need.
Usually, these cryptosystems employ the Bit-
Flipping (BF) decoding technique, originally pro-
posed by Gallager (Gallager, 1963), because of its
good trade-off between error correction capability and
computational complexity. Indeed, the use of com-
mon MDPC parameters yields a O(n
1.5
) average de-
coding complexity, where n is the codeword length.
Briefly, a BF algorithm performs syndrome decoding
through an iterative procedure, in which the bit loca-
tions where the received message is in error are esti-
mated relying on the value of the received syndrome.
The syndrome is subsequently updated according to
the derived estimate, and the procedure is repeated
until either a null syndrome is obtained (indicating a
decoding success), or a prefixed maximum number of
iterations is reached. Depending on the strategy em-
ployed to update the syndrome, BF decoders are clas-
sified in two major classes: out-of-place algorithms
and in-place algorithms. In the former algorithms the
syndrome is updated after all bits have been evalu-
ated, while in the latter ones the update is instantly
performed each time a bit is deemed as an erroneous
one, and thus flipped. The decoder operating princi-
ples, together with the rule employed to detect errors,
is crucial in determining its failure rate. The impossi-
bility of validating the DFR through numerical simu-
lations has spurred significant efforts in modelling the
behaviour of decoders for QC-LDPC and QC-MDPC
codes to find reliable tools for the DFR assessment.
Contributions. We provide a theoretical analysis
of the DFR of an in-place iterative BF decoder for
QC-LDPC and QC-MDPC codes, acting on the es-
timated error locations in a randomized fashion for
a fixed number of iterations. In particular, we em-
ploy well established assumptions in coding theory
to develop a closed-form statistical model of the said
decoder, keeping into account the worst-case execu-
tion at each iteration for the average QC-LDPC/QC-
MDPC code. We provide a numerical validation of
our model, showing that it actually provides conser-
vative estimates of the actual decoder DFR. Finally,
we show practical sets of code parameters for use in
QC-LDPC/QC-MDPC code-based cryptosystems ex-
hibiting a DFR= 2
−λ
with λ ∈ {128, 192,256} and
targeting a security level equivalent to breaking an in-
stance of the AES block cipher with 128-, 192-, or
256-bit key with pre- and post-quantum resources.
2 PRELIMINARIES
Throughout the paper, we will use uppercase (resp.
lowercase) bold letters to denote matrices (resp. vec-
tors). Given a matrix A, its i-th row and j-th column
will be denoted as A
i,:
and A
:, j
, respectively, while
A Failure Rate Model of Bit-flipping Decoders for QC-LDPC and QC-MDPC Code-based Cryptosystems
239

the entry on the i-th row, j-th column as a
i, j
. The
null vector of length n will be denoted as 0
n
. Given
a vector a, its length will be denoted as |a|, while its
i-th element as a
i
, with 0 ≤ i ≤ |a|−1. Finally, the
support (i.e., the set of positions of the asserted el-
ements in a sequence) and the Hamming weight of
a will be reported as S
a
and w
H
a
, respectively.
We will use P
n
to denote the set of permutations of
n elements, represented as bijections on the set of
integers {0,. .. , n − 1}. For π ∈ P
n
and an integer
i ∈ {0,. .. , n − 1}, we will write π(i) = j if the im-
age of i, according to permutation π, is j. For a vector
a ∈ F
n
2
, we will use π(a) to denote the vector which is
obtained by permuting each of the entries of a accord-
ing to π. We will write π
$
←− P
n
to denote a permuta-
tion π that is randomly and uniformly picked among
the elements in P
n
.
As far as the cryptosystems are concerned, in
the following we will make use of a QC-LDPC/QC-
MDPC code C , with length n = n
0
p, dimension k =
(n
0
− 1)p and redundancy r = n − k = p to correct t
intentional errors. The private-key will coincide with
the parity-check matrix H =
H
0
,H
1
,· ··, H
n
0
−1
∈
F
r×n
2
, where each H
i
, 0 ≤ i ≤ n
0
−1, is a binary circu-
lant matrix of size p × p and fixed Hamming weight v
of each column/row.
In the case of a Niederreiter scheme, the public-
key is defined as the systematic parity-check ma-
trix of the code M ∈ F
r×n
2
and derived from the
private-key as M = H
−1
n
0
−1
H, while the plaintext mes-
sage is mapped to an error vector e ∈ F
1×n
2
having
w
H
e
= t asserted bits. The encryption algorithm
outputs the syndrome c = eM
>
∈ F
1×r
2
, which has
the meaning of ciphertext. The decryption algorithm
takes as input c and the private-key H to compute a
private-syndrome s ∈ F
1×r
2
such that s = cH
>
n
0
−1
=
eM
>
H
>
n
0
−1
= eH
>
(H
>
n
0
−1
)
−1
H
>
n
0
−1
= eH
>
.
Subsequently, to derive the original plaintext message
e, the decryption algorithm feeds with the private-key
and the computed private-syndrome a BF syndrome
decoding algorithm.
In the case of the McEliece scheme, the public-
key is chosen as the systematic generator matrix of
the code: G ∈ F
k×n
2
. The ciphertext is in the form
c = mG + e ∈ F
1×n
2
, where m ∈ F
1×k
2
is a plaintext
message encoded with k bits, and e ∈ F
1×n
2
is a n-bit
error vector with exactly w
H
e
= t asserted bits. The
decryption algorithm takes as input the ciphertext c
and the private-key H to compute the syndrome s =
cH
>
= eH
>
∈ F
1×r
2
and feed a syndrome decoding
algorithm, from which m is recovered, employing the
generation matrix and the vector c − e.
2.1 Bit-flipping Decoding
The BF decoder is an iterative, syndrome decoding
procedure, originally proposed by Gallager (Gallager,
1963), which takes as input a syndrome s = (c +
e)H
>
= eH
>
∈ F
1×r
2
, where c ∈ F
1×n
2
and e ∈ F
1×n
2
denote the codeword and the unknown error vector,
respectively. The algorithm computes an estimate of
the error vector, that we denote as
ˆ
e, and which is
initialized as the null vector. For each bit of the er-
ror estimate, a decision is taken on the ground of
the number of unsatisfied parity-check equations in
which it participates, for a generic error bit in posi-
tion 0 ≤ j ≤ n − 1, such quantity is computed as:
upc
j
=
∑
i∈{S
H
:, j
∩{0,...,r−1}}
s
i
.
Indeed, note that the constant term of a generic i-th
parity-check equation (0 ≤ i ≤ r − 1) corresponds to
the i-th entry in s = eH
>
, and that the equations in-
fluenced by the j-th bit of the error vector coincide
with the ones having an asserted bit at the j-th col-
umn of H. Then, the number of unsatisfied parity-
check equations in which the j-th bit participates can
be simply obtained by summing the entries of the syn-
drome which are indexed by the set of positions in
S
H
:, j
. When upc
j
exceeds a given threshold (e.g.,
when more than a half of the parity check equations
in which the j-th error bit is involved as in the original
proposal by Gallager), then the error bit is flipped and
the syndrome is coherently updated replacing its cur-
rent value with s⊕H
:, j
. In a decoding iteration, all er-
ror bits are evaluated following their positional order
from 0 to n − 1; and the decoding repeats the decoder
iteration until either a null syndrome is obtained or
a prefixed maximum number of iterations is reached.
The procedure sketched above corresponds to an in-
place decoding strategy. When an out-of-place strat-
egy is employed, every error bits is assessed relying
on the syndrome value provided as input at the be-
ginning of the iteration, while the updates of both the
error vector and the syndrome are postponed after all
error bits have been evaluated.
3 IN-PLACE RANDOMIZED
BIT-FLIPPING DECODER
In this section we describe a simple modification to
the canonical in-place decoder proposed by Gallager,
for which we provide a closed form estimate of the
DFR in a worst-case scenario.
SECRYPT 2020 - 17th International Conference on Security and Cryptography
240

Algorithm 1: IR-BF decoder.
Input: s ∈ F
1×r
2
: syndrome
H ∈ F
r×n
2
: parity-check matrix with
column-weight v
Output:
ˆ
e ∈ F
1×n
2
: recovered error value
s ∈ F
1×r
2
: syndrome; if error
ˆ
e = e
then s is null
Data: imax ≥ 1: maximum number of
(outer loop) iterations;
b = [b
0
,. . ., b
k
,. . ., b
imax−1
], with
b
k
∈
d
v
2
e,. . ., v
: flip thresholds
1 iter ← 0
2
ˆ
e ← 0
n
// estimated error initialization
3 while (iter < imax) ∧ (w
H
s
> 0) do
4 π
$
←− P
n
// random permut. of size n
5 for j ← 0 to n − 1 do
6 ` ← π( j) // permuted bit index
7 upc ← 0 // integer value
8 for i ∈ S
H
:,`
do
9 upc ← upc + s
i
10 if upc ≥ b
iter
then
11
ˆ
e
`
←
ˆ
e
`
⊕ 1 // error update
12 s ← s ⊕ H
:,`
// syndrome update
13 iter ← iter + 1 // counter update
14 return {s,
ˆ
e}
3.1 An In-place, Randomized
Bit-flipping Decoder
Algorithm 1 reports an in-place BF decoder where the
estimates on the error vector bits are computed in the
order driven by a randomly picked permutation π. For
this reason, we denote this decoder as In-place Ran-
domized Bit-Flipping (IR-BF) decoder. Introducing
this randomization of the bit estimate evaluation order
allows us to derive an effective worst case analysis for
the DFR, as we describe in Section 3.2.
The inputs to the decoding algorithm are the bi-
nary parity-check matrix H, the syndrome s, the max-
imum number of iterations imax and a vector b of
length imax, such that its k-th entry, b
k
, with 0 ≤ k ≤
imax − 1, is employed during the k-th iteration as a
threshold on the value of the unsatisfied parity-check
counters to trigger a flip of the corresponding error bit
estimates or not.
For each outer loop iteration (beginning at line 3),
a permutation is randomly generated (line 4) to estab-
lish the evaluation order of the bits in the estimated
error vector, for the current iteration. The algorithm
proceeds applying the said permutation to each value
taken by the counter j ∈ {0, 1, . . . , n − 1} of the in-
ner loop iterations (line 5) to obtain the bit position
` = π( j) of the estimated error vector to be processed
during the inner loop iteration at hand. The number
of unsatisfied parity-checks (upc) in which the `-th
bit of the error estimate
ˆ
e is involved is computed
by summing the syndrome bits having a position cor-
responding to the asserted elements of the `-th col-
umn of the parity check matrix H (lines 7–9). If the
number of unsatisfied parity-checks in which the `-
th bit participates exceeds the threshold, b
iter
, cho-
sen for the current outer loop iteration, then the value
of the `-th position of the estimated error vector, ˆe
`
,
is changed (i.e., flipped, hence the name of the de-
coding technique) and the value of the syndrome is
updated to reflect this change, adding to it the `-th
column of H (lines 10–12). Once the inner loop at
lines 5–12 terminates, the decoder has completed the
iteration, and thus proceeds to increment the iteration
counter iter and checks whether the syndrome is the
null vector, or not, or if the maximum number of it-
erations is reached. We note that this classical formu-
lation of the IR-BF decoder does not entail a constant
iteration number. However, it is readily transformed
into one with a constant iteration number substitut-
ing the while loop at lines 3–13 with a countable for
loop executing exactly imax iterations. Indeed, exe-
cuting extra iterations of the IR-BF algorithm when
the syndrome is already the null vector does not alter
the correctness of the results. Indeed, once the syn-
drome is the null vector, all the upc values will be
equal to zero, and, since the least functional threshold
is strictly positive, the estimate-changing if construct
at lines 10–12 is never triggered.
3.2 Assessing Bit-flipping Probabilities
In the following we describe a statistical approach to
model the behaviour of the IR-BF decoder. From now
on, we will employ the following notation:
e denotes the actual error vector, with Hamming
weight weight t;
¯
e denotes the error estimate at the beginning of the
outer loop of Algorithm 1 (line 3), while
ˆ
e will denote
the error estimate at the beginning of the inner loop of
Algorithm (line 5). In other words,
¯
e is a snapshot of
the error estimate made by the IR-BF decoder before
a sweep of n estimated error bit evaluations is made,
while
ˆ
e is the value of the estimated error vector be-
fore each estimated error bit is evaluated;
¯
e
0
= e ⊕
¯
e, that is,
¯
e
0
denotes the vector such that its
asserted positions are only those corresponding to po-
sitions in which e and
¯
e are different; the number of
A Failure Rate Model of Bit-flipping Decoders for QC-LDPC and QC-MDPC Code-based Cryptosystems
241

such mismatches is denoted as
¯
t = w
H
¯
e
0
. In analo-
gous way, we define
ˆ
e
0
= e ⊕
ˆ
e and
ˆ
t = w
H
ˆ
e
0
.
We remark that, for the first decoding iteration, we
have
¯
e = 0
n
,
¯
e
0
= e and
¯
t = t. To avoid cumbersome
notation, we will not introduce analogous formalism
for the syndrome and will always use s to denote it. At
the beginning of the outer loop iteration in Algorithm
1, the syndrome corresponds to (e ⊕
¯
e)H
>
=
¯
e
0
H
>
while, inside the inner loop iteration, an estimate
ˆ
e
will be associated to the syndrome (e⊕
ˆ
e)H
>
=
ˆ
e
0
H
>
.
We introduce the following probabilities:
• P
f |1
= Prob
( j-th upc) ≥ b
iter
| e
j
⊕ ˆe
j
= 1
as
the probability that the computation of the j-th
upc yields an outcome greater than or equal to
the current threshold (thus, triggering a flip of ˆe
j
),
conditioned by the event e
j
⊕ ˆe
j
= 1;
• P
m|0
= Prob
( j-th upc) < b
iter
| e
j
⊕ ˆe
j
= 0
as
the probability that the computation of the j-
th upc yields an outcome less than the cur-
rent threshold (thus, maintaining the bit ˆe
j
un-
changed), conditioned by the event e
j
⊕ ˆe
j
= 0.
To derive a theoretical model for the DFR of the IR-
BF decoder, we assume that the above probabilities
only depend on the number of mismatches between
the actual error and the estimated one, that is, on the
weight of
ˆ
e
0
; formally, the following property is as-
sumed to hold.
Assumption 1. Both P
f |1
and P
m|0
are not a func-
tion of the bit-position (i.e., j in their definitions), al-
though both probabilities are a function of the total
number
ˆ
t = w
H
ˆ
e
0
= w
H
e ⊕
ˆ
e
of positions over
which the unknown error e and the estimated error
vector
ˆ
e differ, at the beginning of the j-th inner loop
iteration (line 5 in Algorithm 1).
To derive closed formulae for both P
f |1
and P
m|0
,
we focus on QC-LDPC/QC-MDPC parity-check ma-
trices, as described in Section 2, with column weight
v and row weight w = n
0
v. We observe that Algo-
rithm 1 uses the columns of the parity-check matrix,
for each outer loop iteration, in an order chosen by
the random permutation at line 4, and that the com-
putation accumulating the syndrome bits into the upc
at lines 8–9 is independent of the order in which they
are added.
Following these observations, we consider the
structure of the parity-check matrix, to be such that
each row of H is independent of the others and mod-
eled as a sample of a uniform random variable, dis-
tributed over all possible sequences of n bits with
weight w. More formally, the following assumption
holds.
Assumption 2. Let H be an r × n quasi-cyclic block-
circulant (v, w)-regular parity-check matrix and let s
be the 1 × r syndrome corresponding to a 1 × n error
vector
ˆ
e
0
that is modeled as a sample from a uniform
random variable distributed over the elements in F
1×n
2
with weight
ˆ
t.
We assume that each row h
i,:
, 0 ≤ i ≤ r − 1, of the
parity-check matrix H is well modeled as a sample
from a uniform random variable distributed over the
elements of F
1×n
2
with weight w.
We note that the same assumption was adopted
since the inception of LDPC codes in (Gallager, 1963)
and, more recently also in (Chaulet, 2017, Lemmae
2.3-2.5) and (Tillich, 2018). From Assumption 2, the
probabilities P
f |1
and P
m|0
can be derived as stated in
the following Lemma
Lemma 1. From Assumption 2, the probabilities of
having the i-th bit of the syndrome (0 ≤ i ≤ r −
1) asserted, knowing that the z-th bit of
ˆ
e
0
, (0 ≤
z ≤ n − 1) is null or not, i.e., Prob
s
i
= 1| ˆe
0
z
=
Prob
hh
i,:
,
ˆ
e
0
i = 1| ˆe
0
z
, being hh
i,:
,
ˆ
e
0
i =
L
n−1
j=0
h
i, j
· ˆe
0
j
,
can be expressed for each bit position z, 0 ≤ z ≤ n−1,
of the error vector as
Prob
hh
i,:
,
ˆ
e
0
i = 1 | ˆe
0
z
= 0
= ρ
0,u
,
Prob
hh
i,:
,
ˆ
e
0
i = 1 | ˆe
0
z
= 1
= ρ
1,u
,
with:
ρ
0,u
=
∑
min{w,
ˆ
t}
j=0, j odd
w
j
n−w
ˆ
t− j
n−1
ˆ
t
,
ρ
1,u
=
∑
min{w−1,
ˆ
t−1}
j=0, j even
w−1
j
n−w
ˆ
t−1− j
n−1
ˆ
t−1
.
Consequently, denoting the decoding threshold as
b ∈ {1, . . . , v}, the probabilities P
f |1
and P
m|0
are ob-
tained as
P
f |1
=
v
∑
upc=b
v
upc
ρ
upc
1,u
(1 − ρ
1,u
)
v−upc
,
P
m|0
=
b−1
∑
upc=0
v
upc
ρ
upc
0,u
(1 − ρ
0,u
)
v−upc
.
The proof, which follows a straightforward count-
ing argument, is omitted for the sake of brevity, and
can be found in full in (Baldi et al., 2019b, Lemma
3.1.1)).
3.3 Determining a Worst-case Iteration
Scenario for the IR-BF Decoder
In this section we focus on a single iteration of the
outer loop of Algorithm 1 and derive a statistical
model for the IR-BF decoder, employing the probabil-
ities P
f |1
and P
m|0
as derived in the previous section,
under Assumption 1.
SECRYPT 2020 - 17th International Conference on Security and Cryptography
242

In particular, we consider a worst-case evolution
for the decoder, proving what is the computation path
which ends in a decoding success with the lowest
probability. To this end, we denote a decoding suc-
cess the case when the decoder terminates the inner
loop iteration in the state where the estimate of the
error
ˆ
e matches the actual error e. Indeed, in such a
case, we have w
H
e ⊕
ˆ
e
= 0.
Let
¯
e denote the error estimate at the beginning
of the iteration, and
¯
t = w
H
e ⊕
¯
e
denote the corre-
sponding number of residual mismatched bit estima-
tions. We will study, in statistical terms, the evolu-
tion of the number of mismatches between the vec-
tors e and
ˆ
e, which we denote with
ˆ
t. From now on,
we highlight the dependence of P
f |1
and P
m|0
on the
current value of
ˆ
t, writing them down as P
f |1
(
ˆ
t) and
P
m|0
(
ˆ
t), respectively.
We denote as π the permutation picked in line 4 of
Algorithm 1 and as P
∗
n
the set of permutations π
∗
∈P
∗
n
such that
S
π
∗
(e ⊕
¯
e)
= {n−
¯
t, n−
¯
t +1, ··· , n−1}, ∀π
∗
∈ P
∗
n
.
Let Prob
ˆ
e 6= e
|
π ∈ P
n
be the probability that
the estimated error vector
ˆ
e at the end of the current
inner loop iteration is different from e, conditional
on the fact that the permutation π was applied before
the inner loop execution started. Similarly, we define
Prob
ˆ
e 6= e
|
π
∗
∈ P
∗
n
, by considering π
∗
in place of
π.
It can be verified that P
f |1
(
ˆ
t) ≥ P
f |1
(
ˆ
t + 1), and
P
m|0
(
ˆ
t) ≥ P
m|0
(
ˆ
t + 1), ∀
ˆ
t, as increasing the number of
current mis-estimated error bits, increases the likeli-
hood of a wrong decoder decision. By leveraging As-
sumptions 1 and 2 , we now prove that the decoder
reaches a correct decoding at the end of the outer loop,
with the lowest probability, each time a permutation
π
∗
∈ P
∗
n
is applied at the beginning of the outer loop.
Lemma 2. The execution path of the inner loop in
Algorithm 1, yielding the worst possible decoder suc-
cess rate is the one taking place when π
∗
∈ P
∗
n
is
applied at the beginning of the outer loop. In other
words, ∀π ∈ P
n
, and ∀π
∗
∈ P
∗
n
, the following inequal-
ity holds
Prob
ˆ
e 6= e
|
π ∈ P
n
≤ Prob
ˆ
e 6= e
|
π
∗
∈ P
∗
n
.
Proof. We consider one execution of the outer loop
in Algorithm 1, and denote with
¯
t the initial num-
ber of mismatches between the actual error (that
is, e) and its estimate (that is,
¯
e). We can write
Prob
ˆ
e 6= e
|
π ∈ P
n
= 1 − β(π), where β(π) is the
probability that all bits, evaluated in the order speci-
fied by π, are correctly processed.
To visualize the effect of a permutation π
∗
∈ P
∗
n
,
we can consider the following representation
π
∗
(e) ⊕ π
∗
(
¯
e) = [0, 0,· ··, 0
| {z }
length n −
¯
t
,1, 1, ·· ·,1
| {z }
length
¯
t
], ∀π
∗
∈ P
∗
n
.
The decoder will hence analyze first a run of n −
¯
t po-
sitions where the differences between the permuted
error π
∗
(e) vector and π
∗
(
¯
e) contain only zeroes, fol-
lowed by a run of
¯
t positions containing only ones.
Thus, we have that
β(π
∗
) =
P
m|0
(
¯
t)
n−
¯
t
· P
f |1
(
¯
t) · P
f |1
(
¯
t − 1)·· ·P
f |1
(1).
The former expression can be derived thanks to As-
sumption 1 as follows. Note that, the first elements
in the first n −
¯
t positions of π
∗
(
¯
e) and π
∗
(e) match,
therefore the decoder makes a correct evaluation if it
does not change the corresponding entries in
ˆ
e. This
implies that, in case a sequence of n −
¯
t correct deci-
sions are made in the corresponding iterations of the
inner loop, each iteration will have the same proba-
bility P
m|0
(
¯
t) of correctly evaluating the current esti-
mated error bit. This leads to a probability of perform-
ing the first n −
¯
t iterations taking a correct decision
equal to
P
m|0
(
¯
t)
n−
¯
t
.
Through an analogous line of reasoning, we ob-
serve that the decoder will need to change the value
of the current estimated error bit during the last
¯
t it-
erations of the inner loop. As a consequence, if all
correct decisions are made, the number of residual er-
rors will decrease by one at each inner loop iteration,
yielding the remaining part of the expression.
Consider now a generic permutation π, such that
the resulting π(e) has support {u
0
,· ··, u
¯
t−1
}; we have
β(π) =
=
P
m|0
(
¯
t)
u
0
P
f |1
(
¯
t)
P
m|0
(
¯
t − 1)
u
1
−u
0
−1
P
f |1
(
¯
t − 1) ·· · P
f |1
(1)
P
m|0
(0)
n−1−u
¯
t−1
=
P
m|0
(
¯
t)
u
0
P
m|0
(0)
n−1−u
¯
t−1
∏
¯
t−1
j=1
P
m|0
(
¯
t − j)
u
j
−u
j−1
−1
∏
¯
t−1
l=0
P
f |1
(
¯
t − l).
We now show that we always have β(π) ≥ β(π
∗
).
Indeed, since P
m|0
(0) = 1, due to the monotonic
trends of the probabilities P
m|0
(
ˆ
t) and P
f |1
(
ˆ
t), the
following chain of inequalities can be derived
β(π) =
=
P
m|0
(0)
n−1−u
¯
t−1
P
m|0
(
¯
t)
u
0
∏
¯
t−1
j=1
P
m|0
(
¯
t − j)
u
j
−u
j−1
−1
∏
¯
t−1
l=0
P
f |1
(
¯
t − l)
≥
P
m|0
(0)
n−1−u
¯
t−1
P
m|0
(
¯
t)
u
0
∏
¯
t−1
j=1
P
m|0
(
¯
t)
u
j
−u
j−1
−1
∏
¯
t−1
l=0
P
f |1
(
¯
t − l)
=
P
m|0
(0)
n−1−u
¯
t−1
P
m|0
(
¯
t)
u
0
P
m|0
(
¯
t)
u
¯
t−1
−u
0
−(
¯
t−1)
∏
¯
t−1
l=0
P
f |1
(
¯
t − l))
=
P
m|0
(0)
n−1−u
¯
t−1
P
m|0
(
¯
t)
u
¯
t−1
−(
¯
t−1)
∏
¯
t−1
l=0
P
f |1
(
¯
t − l)
≥
P
m|0
(
¯
t)
n−1−u
¯
t−1
P
m|0
(
¯
t)
u
¯
t−1
−(
¯
t−1)
∏
¯
t−1
l=0
P
f |1
(
¯
t − l)
=
P
m|0
(
¯
t)
n−
¯
t
∏
¯
t−1
l=0
P
f |1
(
¯
t − l) = β(π
∗
).
A Failure Rate Model of Bit-flipping Decoders for QC-LDPC and QC-MDPC Code-based Cryptosystems
243

3.4 A Worst-case DFR Estimate for the
IR-BF Decoder
From now on we will assume that, in each iteration,
a permutation from the set P
∗
n
is picked; in other
words, we are assuming that the decoder is always
constrained to reach a decoding success through the
worst possible execution path. We consider one outer
loop iteration, and denote with
¯
e the error estimate
at the beginning of the iteration; we recall that the
number of mismatches between
¯
e and e is denoted as
¯
t = w
H
e ⊕
¯
e
. Let us define the following two sets:
E
1
=S(e⊕
¯
e), and E
0
={0,. . ., n−1}\E
1
. Denote with
ˆ
t
0
the number of places where the estimated error dif-
fers from the actual e, in positions included in E
0
. At
the beginning of the outer loop iteration, we have
ˆ
t
0
=
S
e ⊕
¯
e
∩ E
0
= 0.
Analogously, we define
ˆ
t
1
as the number of positions
in which the estimated error and the actual one differ,
in positions included in E
1
; at the beginning of the
outer loop iteration, we have
ˆ
t
0
= 0 and
ˆ
t
1
=
S
e ⊕
¯
e
∩ E
1
=
¯
t.
Let
i) Prob
P
∗
n
ω
E
0
−→ x
denote the probability that the
decoder in Algorithm 1, starting from a state
where w
H
¯
e ⊕ e
= ω, and acting in the order
specified by a worst case permutation π
∗
∈ P
∗
n
,
ends in a state with
ˆ
t
0
= x residual errors among
the bits indexed by E
0
after completing the inner
loop at lines 5 – 12;
ii) Prob
P
∗
n
ω
E
1
−→ x
denote the probability that the
decoder in Algorithm 1, starting from a state
where w
H
¯
e ⊕ e
= ω, and acting in the order
specified by a worst case permutation π
∗
∈ P
∗
n
ends in a state with
ˆ
t
1
= x residual errors among
the bits indexed by E
1
after completing the loop
at lines 5–12;
iii) Prob
P
∗
n
ω −→
i
x
be the probability that, start-
ing from a state such that w
H
¯
e ⊕ e
= ω, after i
iterations of the outer loop at lines 5–12 of Algo-
rithm 1, each one operating with a worst case per-
mutation, ends in a state where w
H
ˆ
e ⊕ e
= x.
The expressions of the probabilities i) and ii) are de-
rived in the Appendix, and only depend on P
f |1
(
ˆ
t) and
P
m|0
(
ˆ
t).
We now describe how the aforementioned prob-
abilities can be used to express the worst case DFR
after imax iterations, which we denote as DFR
∗
itermax
.
First of all, we straightforwardly have
Prob
P
∗
n
ω −→
1
x
=
=
ω
∑
δ=max{0 ; x−(n−ω)}
Prob
P
∗
n
ω
E
0
−→ x − δ
Prob
P
∗
n
ω
E
1
−→ δ
.
From now on, we will denote with
ˆ
e
(iter)
the error
vector estimate after the iter + 1 outer loop iter-
ations; coherently, we write
ˆ
t
(i)
= w
H
e ⊕
ˆ
e
(iter)
,
that is:
ˆ
t
(i)
corresponds to the number of residual er-
rors after the i-th outer loop iteration. Then, by con-
sidering all possible configurations of such values,
and taking into account that the first iteration begins
with t residual errors, we have
Prob
P
∗
n
t −−−−→
imax−1
ˆ
t
(imax−1)
=
n
∑
ˆ
t
(0)
=0
···
·· ·
n
∑
ˆ
t
(imax−2)
=0
Prob
P
∗
n
ˆ
t
(i
max−2
)
−→
1
ˆ
t
(imax−1)
imax−2
∏
j=0
Prob
P
∗
n
ˆ
t
( j−1)
−→
1
ˆ
t
( j)
where, to have a consistent notation, we consider
ˆ
t
(−1)
= t.
The above formula takes into account all possible
transitions starting from an initial number of residual
errors equal to t and ending in
ˆ
t
(imax−1)
residual errors
Taking this probability into account, the DFR after
imax iterations is
DFR
∗
imax
= 1 −
n
∑
ˆ
t
(imax−1)
=0
Prob
P
∗
n
t −−−−→
imax−1
ˆ
t
(imax−1)
Prob
P
∗
n
ˆ
t
(imax−1)
−→
1
0
.
In the case of the decoder performing just one iter-
ation, the expression of the DFR, keeping into account
Lemma 2, is
DFR
∗
1
= 1 − Prob
P
∗
n
t −→
1
0
= 1 −
P
m|0
(t)
n−t
t
∏
j=1
P
f |1
( j).
A bonus point of the analysis we propose is that
it is easy to obtain also an estimate for the average
DFR of one decoding iteration, (i.e., corresponding
to one outer loop iteration, using a random permuta-
tion π). Indeed, let π(e) be the vector obtained by ap-
plying the permutation π on e, with support S
π(e)
.
Let a
i
, a
i+1
be two consecutive elements of S
π(e)
,
with 0 ≤ i ≤ t − 2, and denote as d the average zero-
run length in e. It can be easily seen that, when π
is randomly drawn from P
n
and e is uniformly dis-
tributed over all binary n-uples, then the average zero-
run length between two consecutive set entries in e
corresponds to d =
n−t
t+1
.
Consequently, we can obtain a simple estimate for
the average DFR after one iteration as
DFR
1
≈ 1 −
t
∏
j=1
P
m|0
( j)
d
!
t
∏
`=1
P
f |1
(`).
SECRYPT 2020 - 17th International Conference on Security and Cryptography
244

10 20 30 40
50 60
70 80 90
10
−6
10
−5
10
−4
10
−3
10
−2
10
−1
10
0
t
DFR
Est. DFR
1
,
Sim. DFR
1
Est. DFR
∗
1
Sim. DFR
∗
1
Sim. DFR
id
(a) One Iteration
40
50 60
70 80 90
10
−6
10
−5
10
−4
10
−3
10
−2
10
−1
10
0
t
DFR
Est. DFR
∗
2
Sim. DFR
∗
2
Sim. DFR
2
(b) Two Iterations
Figure 1: Numerical validation of the DFR estimates (Est.) through numerical simulations (Sim.). The QC-MDPC code
parameters are n
0
= 2, p = 4801 and v = 45. Figure (a) refers to the case of one decoding iteration (i.e., imax = 1), figure
(b) refers to a maximum number of decoding iterations equal to 2 (i.e., imax = 2). The chosen decoding threshold, for both
cases, is b = 25. The results marked with “Est.” are obtained via the computation of closed formulas as opposed to the ones
marked “Sim.” which are the result of a numerical simulation.
4 NUMERICAL VALIDATION
In this section we report the results of the numerical
validation of the proposed analysis for the IR-BF de-
coder as well as practical sets of code parameters for
use in QC-LDPC/QC-MDPC code-based cryptosys-
tems. With the goal of validating our bounds on the
DFR by simulations, we choose a QC-MDPC code
having the parity check matrix H formed by n
0
= 2
circulant blocks of size p = 4801 and column weight
v = 45. We assess the DFR varying the error weight t
from 10 to 100, attempting to decode 10
6
≈ 2
20
error
vectors for each value of the error weight. We re-
port the results considering a bit-flipping threshold of
b = 25, for all iterations; however, we obtained anal-
ogous results varying the bit-flipping threshold. The
results with thresholds different from 25 are omitted
for lack of space.
We implemented the IR-BF decoder in C99,
compiled the code with the GCC 8.3.0 on Debian
GNU/Linux 10.2 (stable), and run the experiments on
an Intel Core i5-6500 CPU running at 3.20 GHz. The
computation of the worst case DFR estimates were
realized employing the NTL library.
Figure 1 reports the results of numerical simula-
tions of the DFR of the IR-BF decoder (Sim. datasets
in Figure 1) running for either one or two iterations,
while employing either a random permutation (DFR
1
and DFR
2
, respectively) or one selected among the
worst case ones (DFR
∗
1
and DFR
∗
2
, respectively). For
the case of one iteration, also the simulated DFR with-
out the initial permutation, noted as DFR
id
, is con-
sidered. Note that we are able to pick one of the
worst-case permutations in practice since the actual
error vector e is known to us, therefore allowing the
computation of the discrepancies between the current
error estimate and the actual error itself. The results
are matched against the closed-form estimates as de-
rived in the previous section.
As it can be seen in Figure 1 (a), our technique
for the DFR estimate provides a perfect match for
the case of a single iteration. Indeed, our estimated
worst-case DFR (dotted cyan line) matches perfectly
the simulated DFR picking a worst-case permutation
π
∗
(cyan × symbols), and dominates the actual sim-
ulated DFR (blue × symbols). Finally, we also ob-
served that omitting the permutation before the first
iteration has no practical impact on the DFR. Such a
fact can be easily justified by the random nature of
the error vector, which in turn makes the initial po-
sitions where a discrepancy between the error esti-
mate at the beginning of the decoding (which is com-
pletely null) and the error vector itself already com-
pletely random. This fact can be observed looking at
the black dots in Fig. 1 (a), which report the values of
DFR
id
, and observing that they essentially match the
DFR of the decoder employing a random permutation
(blue × symbols). Finally, we note that our simple
technique to estimate the average DFR of the IR-BF
decoder (depicted as a dotted blue line) also provides
A Failure Rate Model of Bit-flipping Decoders for QC-LDPC and QC-MDPC Code-based Cryptosystems
245

Table 1: Designed parameters, targeting the security levels of 2
λ
and DFR=2
−λ
, λ={128,192, 256}.
Security 2 iter.s (Santini et al., 2019) 1st iter. IR-BF + 2nd iter. (Baldi et al., 2019d) 2 iter.s IR-BF
Level v t p τ p τ p
2
128
71 130 28, 277 10 26,171 10 19,813
2
192
103 195 52, 667 15 50,227 15 38,069
2
256
137 260 83, 579 18 80,309 18 61,211
a good match for the actual DFR itself. Considering
the case of a two iterations IR-BF decoder, reported in
Fig. 1 (b), we note how our technique provides a con-
servative estimate for the worst case DFR of the IR-
BF decoder. The previous comparison shows that, for
the range of values that can be reached with numerical
simulations, the presented theoretical analysis yields
conservative estimates for the DFR of the IR-BF de-
coder. Thus, we have employed the presented DFR
analysis to design parameters for code-based cryp-
tosystems employing QC-LDPC/QC-MDPC codes,
targeting a security level equivalent to breaking an in-
stance of the AES block cipher with 128-, 192-, or
256-bit keys. Focusing on the case of n
0
= 2, we
provide the resulting size and column weight of the
circulant blocks in the parity-check matrix H, which
we respectively denote with p and v, in Table 1; the
number of errors which need to be corrected (denoted
with t in the table) has been computed to guarantee
security levels of 2
λ
(Baldi et al., 2019a). We recall
that, in the example of a Niederreiter based key encap-
sulation mechanism, employing a quasi-cyclic parity-
check matrix with two circulant blocks, as it is the
case in the reported parameters, the public key of the
cryptosystem will be p bit long and the encapsulated
session key will also be p bits long.
Table 1 compares the parameter sets for the two-
iterations out of place decoder proposed in (San-
tini et al., 2019), a decoder obtained with an itera-
tion of the IR-BF decoder, followed by one iteration
of the out-of-place LEDAcrypt decoder (Baldi et al.,
2019d), computing the resulting DFR on the base
of the number of residual error distribution after the
first iteration provided by our technique, and a two-
iteration IR-BF decoder. In the table, the values of τ
refers to the number of errors that can be corrected
with certainty by an iteration of an out-of-place BF
decoder. As it can be seen from the reported results,
even employing a hybrid approach, where the first de-
coder iteration is performed in-place by the IR-BF de-
coder, and the second one is performed out-of-place,
allows a small reduction of the key size. Moving to
our in-place decoding strategy allows to reduce the
public key and ciphertext size by ≈ 25% with respect
to the approach described in (Santini et al., 2019).
5 RELATED WORK AND
DISCUSSION
A code-specific analysis to establish the total error
correction capability (i.e., null DFR) for a single BF
iteration has first appeared in (Tillich, 2018) and has
then been improved in (Santini et al., 2019). With
similar arguments, an assumption-free, conservative
upper bound for the DFR of a single decoder itera-
tion was derived in (Santini et al., 2019a). However,
employing such approaches to design the secret code
parameters results in impractically large public-key
sizes. To obtain keys with smaller size, in (Tillich,
2018; Santini et al., 2019; Baldi et al., 2019c; Baldi
et al., 2018) the DFR of a two-iteration out-of-place
decoder is analyzed, providing a closed-form method
to derive an upper bound on the average DFR over
all the QC-LDPC/QC-MDPC codes with the same
length, rate and density, under reasonable assump-
tions. However, the second and final decoding itera-
tion is analyzed in a conservative way, thus designing
code parameters which may be further improved.
In (Sendrier and Vasseur, 2019b), the authors pro-
pose a characterization of a variant of the out-of-place
decoder based on the extrapolation of the DFR curve
in the desired regime of low DFR values, starting
from higher DFR values estimated through numeri-
cal simulations. This method assumes that the expo-
nentially decreasing trend of the DFR curve is steady
as the code length increases, while all the other pa-
rameters are kept constant. This assumption is made
in the scenario where numerical simulations allow to
examine a DFR in the range of 2
−27
, assuming that
the trend is still the same for DFR values of 2
−128
and
lower. A qualitative justification is provided for this
assumption in the appendix of (Sendrier and Vasseur,
2019a). In the said appendix, the authors rely on the
so-called concavity assumption, according to which
the DFR curve remains concave for all values of prac-
tical interest. Such an assumption in turn implies that
the so-called error floor region of the DFR curve,
where the said curve changes concavity, and that is
present in all LDPC/MDPC codes, after the so-called
waterfall region, does not occur for DFR values of
practical interest.
SECRYPT 2020 - 17th International Conference on Security and Cryptography
246

We find this assumption to be difficult to main-
tain, since predicting the beginning of the error floor
region is an extremely challenging task, which has
currently no satisfactory closed form solution. In-
deed, phenomena such as the existence of the so-
called trapping sets (particular sets of error patterns
which cause an iterative decoder to fail), which are
deemed to have a negligible impact in the assump-
tion made in (Sendrier and Vasseur, 2019a), are one
of the prime objects of study to determine the location
of the error floor region (Richardson, 2003; Hashemi
and Banihashemi, 2019).
We note that if either a concavity change, or sim-
ply the change in the rate of the exponential decrease
of the DFR curve before the concavity change, takes
place before the region of practical interest, the ex-
trapolations made in (Sendrier and Vasseur, 2019a)
will provide cryptosystem parameters which are not
matching the DFR needed in IND-CCA2 construc-
tions. We therefore believe that relying on DFR curve
extrapolations may provide overly optimistic cryp-
tosystem parameter designs (Drucker and Gueron,
2017; Drucker et al., 2019).
In (Sendrier and Vasseur, 2019a), the authors also
analyze an in-place decoding algorithm, called Step-
by-step decoder modeling its DFR. The proposed
analysis however, obtains a DFR estimate which is
lower than the actual DFR obtained via numerical
simulation, and thus cannot be employed when an up-
per bound of the DFR value is desired. Furthermore,
the proposed analysis considers the asymptotic be-
haviour of the Step-by-step decoder when an infinite
number of iterations is performed. Such an approach
provides a practical hindrance in principle to the im-
plementation of the decoding procedure as a constant
time one, as there is no fixed upper bound to the num-
ber of iterations a-priori.
In this work, we obtain a characterization of a
simple in-place decoder with a finite number of iter-
ations, allowing its constant-time implementation in
practice. Our characterization provides a statistical
model which, by considering the worst case evalua-
tion of the decoder, provides a conservative estimate
of the decoder evolution. As a result, we do not rely
on any specific a-priori assumption on the behaviour
of the DFR curve but, on the contrary, completely de-
rive it as a function of the scheme parameters and the
decoder setting.
6 CONCLUSION
We have presented a statistical analysis of the be-
haviour of an in-place randomized bit-flipping (IR-
BF) decoder, derived from the classic in-place bit-
flipping decoder by randomizing the order in which
the estimated error positions are processed. The said
modification allows us to derive a worst-case analy-
sis for the DFR of syndrome-decoding based systems,
which is employed to design code parameters for QC-
LDPC/QC-MDPC based cryptoystems matching the
DFR figures of merit needed to provide IND-CCA2
guarantees. Differently from other solutions available
at the state-of-the-art, the proposed analysis allows
to fix the number of iterations of the IR-BF decoder
a-priori (e.g., imax = 2), allowing an easy constant-
time implementation, preventing timing-based side
channel attacks.
REFERENCES
Alagic, G., Alperin-Sheriff, J., Apon, D., Cooper, D., Dang,
Q., Miller, C., Moody, D., Peralta, R., Perlner, R.,
Robinson, A., Smith-Tone, D., and Liu, Y.-K. (2019).
Status report on the first round of the NIST post-
quantum cryptography standardization process. Tech-
nical Report NISTIR 8240.
Baldi, M., Barenghi, A., Chiaraluce, F., Pelosi, G., and San-
tini, P. (2018). LEDAkem: A post-quantum key en-
capsulation mechanism based on QC-LDPC codes. In
Lange, T. and Steinwandt, R., editors, Post-Quantum
Cryptography - 9th Int.’l Conference, PQCrypto 2018,
Fort Lauderdale, April 9-11, 2018, volume 10786 of
LNCS, pages 3–24. Springer.
Baldi, M., Barenghi, A., Chiaraluce, F., Pelosi, G., and San-
tini, P. (2019a). A finite regime analysis of informa-
tion set decoding algorithms. Algorithms, 12:209.
Baldi, M., Barenghi, A., Chiaraluce, F., Pelosi, G., and
Santini, P. (2019b). LEDAcrypt 2.5 specification.
https://www.ledacrypt.org/documents/LEDAcrypt_
spec_2_5.pdf.
Baldi, M., Barenghi, A., Chiaraluce, F., Pelosi, G., and San-
tini, P. (2019c). LEDAcrypt: QC-LDPC code-based
cryptosystems with bounded decryption failure rate.
In Baldi, M., Persichetti, E., and Santini, P., editors,
Code-Based Cryptography. CBC 2019, volume 11666
of LNCS, pages 11–43. Springer, Cham.
Baldi, M., Barenghi, A., Chiaraluce, F., Pelosi, G., and San-
tini, P. (2019d). LEDAcrypt website. https://www.
ledacrypt.org/.
Baldi, M., Chiaraluce, F., Garello, R., and Mininni, F.
(2007). Quasi-cyclic low-density parity-check codes
in the McEliece cryptosystem. In ICC 2007.
Barenghi, A., Fornaciari, W., Galimberti, A., Pelosi, G.,
and Zoni, D. (2019). Evaluating the Trade-offs in the
Hardware Design of the LEDAcrypt Encryption Func-
tions. In 26th IEEE International Conference on Elec-
tronics, Circuits and Systems, ICECS 2019, Genoa,
Italy, November 27-29, 2019, pages 739–742. IEEE.
Berlekamp, E. R., McEliece, R. J., and van Tilborg, H.
C. A. (1978). On the inherent intractability of certain
coding problems. IEEE Trans. Information Theory,
24(3):384–386.
A Failure Rate Model of Bit-flipping Decoders for QC-LDPC and QC-MDPC Code-based Cryptosystems
247

Bindel, N., Hamburg, M., Hövelmanns, K., Hülsing, A.,
and Persichetti, E. (2019). Tighter proofs of CCA se-
curity in the quantum random oracle model. https:
//eprint.iacr.org/2019/590.
Chaulet, J. (2017). Etude de cryptosystèmes à clé publique
basés sur les codes MDPC quasi-cycliques. PhD the-
sis, Université Pierre et Marie Curie - Paris VI.
Drucker, N. and Gueron, S. (2017). A toolbox for software
optimization of QC-MDPC code-based cryptosys-
tems. Cryptology ePrint Archive, Report 2017/1251.
https://eprint.iacr.org/2017/1251.
Drucker, N., Gueron, S., and Kostic, D. (2019). QC-
MDPC decoders with several shades of gray. eprint
2019/1423. https://eprint.iacr.org/2019/1423.
Fabši
ˇ
c, T., Hromada, V., Stankovski, P., Zajac, P., Guo,
Q., and Johansson, T. (2017). A reaction attack on
the QC-LDPC McEliece cryptosystem. In PQCrypto
2017. Springer.
Faugère, J.-C., Otmani, A., Perret, L., and Tillich, J.-P.
(2010). Algebraic cryptanalysis of McEliece variants
with compact keys. In EUROCRYPT, volume 6110 of
LNCS. Springer.
Gallager, R. G. (1963). Low-Density Parity-Check Codes.
PhD thesis, M.I.T.
Guo, Q., Johansson, T., and Stankovski, P. (2016). A key
recovery attack on MDPC with CCA security using
decoding errors. In ASIACRYPT 2016, volume 10031
of LNCS, pages 789–815. Springer.
Hashemi, Y. and Banihashemi, A. H. (2019). Characteri-
zation and efficient search of non-elementary trapping
sets of LDPC codes with applications to stopping sets.
IEEE Trans. Inf. Theory, 65(2):1017–1033.
Hofheinz, D., Hövelmanns, K., and Kiltz, E. (2017). A
modular analysis of the Fujisaki-Okamoto transfor-
mation. In Theory of Cryptography. TCC 2017, vol-
ume 10677 of LNCS, pages 341–371. Springer.
Karp, R. M. (1972). Reducibility among combinatorial
problems. In Miller, R. E., Thatcher, J. W., and
Bohlinger, J. D., editors, Complexity of Computer
Computations, pages 85–103. Springer, Boston, MA.
McEliece, R. J. (1978). A public-key cryptosystem based
on algebraic coding theory. Deep Space Network
Progress Report, 44.
Misoczki, R., Tillich, J.-P., Sendrier, N., and Barreto, P. L.
(2013). MDPC-McEliece: New McEliece variants
from moderate density parity-check codes. In ISIT
2013, Istambul, Turkey.
Niederreiter, H. (1986). Knapsack-type cryptosystems and
algebraic coding theory. Prob. Con. and Inf. Theory,
15.
Richardson, T. (2003). Error floors of LDPC codes. In Proc.
41st Annu. Allerton Conf. Commun. Control Comput.,
pages 1426–1435, Monticello, IL, USA.
Salomaa, A. (1969). Chapter II - Finite Non-deterministic
and Probabilistic Automata. In Theory of Automata,
volume 100 of of Monographs on Pure and Applied
Mathematics. Pergamon.
Santini, P., Battaglioni, M., Baldi, M., and Chiaraluce, F.
(2019). Hard-decision iterative decoding of LDPC
codes with bounded error rate. In Proc. IEEE Conf.
on Communications (ICC 2019), Shanghai, China.
Santini, P., Battaglioni, M., Baldi, M., and Chiar-
aluce, F. (2019a). A theoretical analysis of
the error correction capability of LDPC and
MDPC codes under parallel bit-flipping decoding.
https://arxiv.org/abs/1910.00472.
Santini, P., Battaglioni, M., Chiaraluce, F., and Baldi, M.
(2019b). Analysis of reaction and timing attacks
against cryptosystems based on sparse parity-check
codes. In Code-Based Cryptography. CBC 2019.
Springer , Cham.
Sendrier, N. and Vasseur, V. (2019a). About low DFR for
QC-MDPC decoding. Cryptology ePrint Archive, Re-
port 2019/1434. https://eprint.iacr.org/2019/1434.
Sendrier, N. and Vasseur, V. (2019b). On the decoding
failure rate of QC-MDPC bit-flipping decoders. In
PQCrypto 2019, volume 11505 of LNCS, pages 404–
416. Springer, Cham.
Tillich, J. (2018). The decoding failure probability of
MDPC codes. In ISIT 2018, Vail, CO, USA.
APPENDIX
Denote with
ˆ
t
0
=
|{
S(e ⊕
¯
e) ∩ E
0
}|
, that is, the number
of places where the estimated error at the beginning
of the outer loop iteration
¯
e differs from the actual
e, in positions included in E
0
. Analogously, define
ˆ
t
1
=
|{
S(e ⊕
¯
e) ∩ E
1
}|
.
We now characterize the statistical distribution of
ˆ
t
0
and
ˆ
t
1
after n iterations of the inner loop of the IR-
BF decoder are run, processing the estimated error bit
positions in the order pointed out by π
∗
∈ P
∗
n
, i.e., the
permutation which places at the end all the positions
j where ˆe
j
6= e
j
. We point out that, at the first iter-
ation of the outer loop of the decoder, this coincides
with placing all the positions where e
j
= 1 at the end,
since
¯
e is initialized to the n-binary zero vector, hence
¯
e ⊕ e = e. In characterizing the distribution of
ˆ
t
0
, be-
cause of Assumption 1, we rely only on the probabil-
ities P
f |0
(
ˆ
t) and P
m|0
(
ˆ
t), i.e., the probability that an
error estimate bit will be flipped or maintained. In the
following, for the sake of simplicity, we will consider
ˆ
t
1
= t, which is the case of the IR-BF decoder per-
forming the first outer loop iteration. To model the
statistical distribution of
ˆ
t
0
we employ the framework
of Probabilistic Finite State Automata (PFSA) (Salo-
maa, 1969). Informally, a PFSA is a Finite State Au-
tomaton (FSA) characterized by transition probabili-
ties for each of the transitions of the FSA. The state
of a PFSA is a discrete probability distribution over
the set of FSA states and the probabilities of the tran-
sitions starting from the same FSA state, reading the
same symbol, must add up to one.
We model the statistical distribution of
ˆ
t
0
as the
state of a PFSA having n − t FSA states, each one
mapped onto a specific value for
ˆ
t
0
, as depicted in
SECRYPT 2020 - 17th International Conference on Security and Cryptography
248
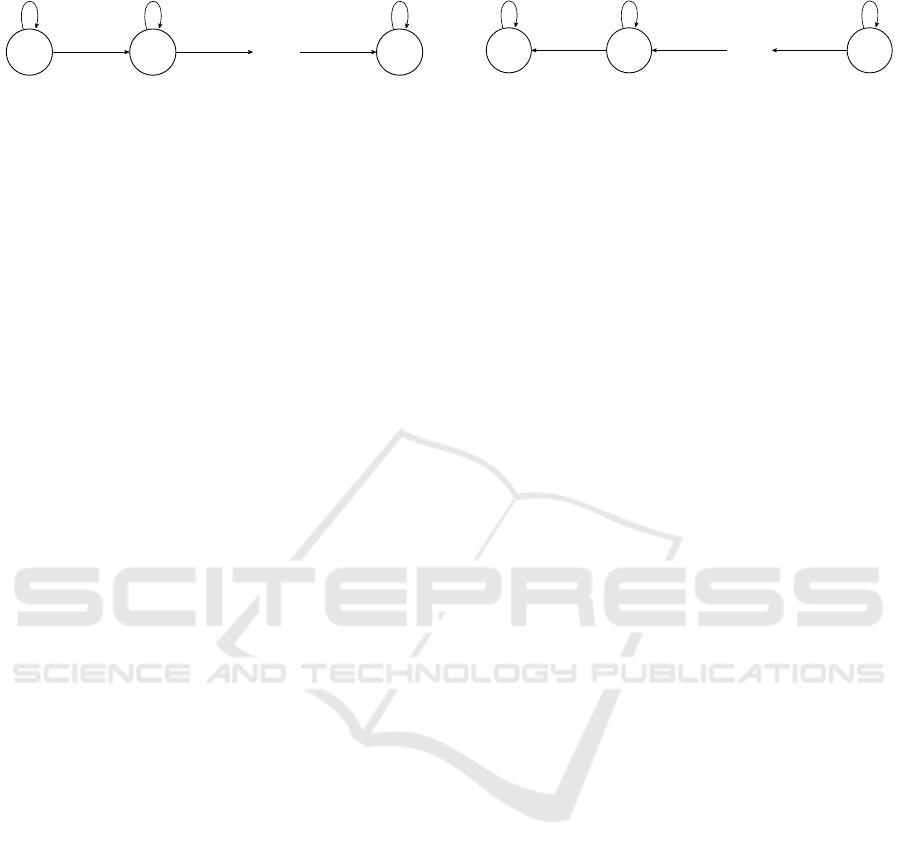
t
0
= 0 t
0
= 1
...
t
0
=n−t
0, P
f |0
(t) 0, P
f |0
(t + 1) 0, P
f |0
(n − 1)
0, P
m|0
(t) 0, P
m|0
(t + 1) 0, P
m|0
(n)
Figure 2: Structure of the probabilistic FSA modeling the
evolution of the distribution of the
ˆ
t
0
variable. Read charac-
ters are reported in black, transition probabilities in red.
Fig. 2. We consider the underlying FSA to be accept-
ing the input language constituted by binary strings
obtained as the sequences of ˆe
j
6= e
j
values, where j is
the error estimate position being processed by the IR-
BF decoder at a given inner loop iteration. We there-
fore have that, for the PFSA modeling the evolution
of
ˆ
t
0
while the IR-BF decoder acts on the first n−t po-
sitions specified by π
∗
, all the read bits will be equal
to 0, as π
∗
sorts the positions of
ˆ
e so that the (n −t, at
the first iteration) positions with no discrepancy be-
tween
¯
e and e come first. The transition probability
for the PFSA transition from a state
ˆ
t
0
= i to
ˆ
t
0
= i + 1
requires the IR-BF decoder to flip a bit of
ˆ
e equal to
zero, and matching the one in the same position of
e, causing a discrepancy. Because of Assumption 1,
the probability of such a transition is P
f |0
(t +i), while
the probability of the self-loop transition from
ˆ
t
0
= i
to
ˆ
t
0
= i itself is P
m|0
(t + i). Note that, during the
inner loop iterations of the IR-BF decoder acting on
positions of
ˆ
e which have no discrepancies, it is not
possible to decrease the value
ˆ
t
0
, as no reduction on
the number of discrepancies between
ˆ
e and e can be
done changing values of
ˆ
e which are already equal to
the ones in e. Hence, we have that the probability of
transitioning from
ˆ
t
0
= i to
ˆ
t
0
= i − 1 is zero.
The evolution of a PFSA can be computed sim-
ply taking the current state, represented as the vec-
tor y of probabilities for each FSA state, and multi-
plying it by an appropriate matrix which character-
izes the transitions in the PFSA. Such a matrix is de-
rived as the adjacency matrix of the PFSA graph rep-
resentation, keeping only the edges for which the read
character matches the edge label, and substituting the
one-values in the adjacency matrix with the probabil-
ity labelling the corresponding edge. We obtain the
transition matrix modeling an iteration of the IR-BF
decoder acting on an ˆe
j
= e
j
(i.e., reading a 0) as the
(n − t + 1) × (n − t + 1) matrix
K
0
=
P
m|0
(t) P
f |0
(t) 0 0 0 0
0 P
m|0
(t + 1) P
f |0
(t + 1) 0 0 0
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
0 0 0 0 P
m|0
(n − 1) P
f |0
(n − 1)
0 0 0 0 0 P
m|0
(n)
.
Since we want to compute the effect on the distri-
bution of
ˆ
t
0
after n − t iterations of the IR-BF de-
coder acting on positions j such that ˆe
j
= e
j
, we
t
1
= 0 t
1
= 1
...
t
1
= t
1, P
f |1
(t
∗
−t +1) 1, P
f |1
(t
∗
−t +2) 1, P
f |1
(t
∗
)
1, P
m|1
(t
∗
−t) 1, P
m|1
(t
∗
−t +1) 1, P
m|1
(t
∗
)
Figure 3: Structure of the probabilistic FSA modeling the
evolution of the distribution of the
ˆ
t
1
variable. Read charac-
ters are reported in black, transition probabilities in red.
can obtain it simply as yK
n−t
0
. Note that the subse-
quent t iterations of the IR-BF decoder will not alter
the value of
ˆ
t
0
as they act on positions j such that
e
j
= 1. Since we know that, at the beginning of the
first iteration y = [Prob
ˆ
t
0
= 0
= 1,Prob
ˆ
t
0
= 1
=
0,Prob
ˆ
t
0
= 2
= 0, ··· , Prob
ˆ
t
0
= n − t
= 0], we
compute Prob
P
∗
n
ω
E
0
−→ x
as the (x+1)-th element
of yK
n−t
0
. We now model the distribution of
ˆ
t
1
, during
the last t iterations of the inner loop of the IR-BF de-
coder performed during an iteration of the outer loop.
Note that, to this end, the first n − t iterations of the
inner loop have no effect on
ˆ
t
1
. Denote with t
∗
the in-
correctly estimated bits w
H
e +
ˆ
e
at the beginning of
the inner loop iterations acting on positions j where
ˆe
j
6= e
j
. Note that, at the first iteration of the outer
loop of the IR-BF decoder, t
∗
=
ˆ
t
0
+ t, when the IR-
BF decoder is about to analyze the first position for
which w
H
e ⊕
¯
e
. We now model the distribution of
ˆ
t
1
, during the last
ˆ
t rounds of the loop in the random-
ized in-place iteration function. Note that, to this end,
the first n − t iterations of the inner loop have no ef-
fect on
ˆ
t
1
. Denote with
˜
t the incorrectly estimated bits
in
ˆ
e
0
= e ⊕
ˆ
e, that is,
˜
t = w
H
ˆ
e
0
, when the iteration
function is about to evaluate the first of the positions
j where ˆe
j
6= e
j
. Note that, at the beginning we have
˜
t =
˜
t
0
+
ˆ
t
1
, where
˜
t
0
is the number of discrepancies in
the first n −
ˆ
t positions when the iteration is about to
analyze the first position of ˆe for which w
H
e +
ˆ
e
.
Analogously to the PFSA describing the evolution for
ˆ
t
0
, we obtain the PFSA modeling the evolution of
ˆ
t
1
,
reported in Fig. 3. The initial distribution of the val-
ues of
ˆ
t
1
, constituting the initial state of the PFSA in
Fig. 3, is such that Prob
ˆ
t
1
= t
= 1, corresponding
to the
ˆ
t
1
-element vector z = [0,0, . .. , 0,1]. The tran-
sition matrix of the PFSA is
K
1
=
P
m|1
(
˜
t − t) 0 0 0 0 0
P
f |1
(
˜
t − t + 1) P
m|1
(
˜
t − t + 1) 0 0 0 0
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
0 0 0 P
f |1
(
˜
t − 1) P
m|1
(
˜
t − 1) 0
0 0 0 0 P
f |1
(
˜
t) P
m|1
(
˜
t)
.
We are thus able to obtain the Prob
P
∗
n
ω
E
1
−→ x
com-
puting zK
t
1
and taking its (x + 1)-th element.
A Failure Rate Model of Bit-flipping Decoders for QC-LDPC and QC-MDPC Code-based Cryptosystems
249
