
Detection of Anomalous User Activity for Home IoT Devices
∗
Vishwajeet Bhosale
1
, Lorenzo de Carli
2
and Indrakshi Ray
1
1
Colorado State University, Fort Collins, CO 80523, U.S.A.
2
Worcester Polytechnic Institute, Worcester, MA 01609, U.S.A.
Keywords:
IoT Security, IoT Traffic Classification, IoT Privacy.
Abstract:
Home IoT devices suffer from poor security, and are easy to commandeer for unskilled attackers. Since most
IoTs cannot run host-based detection, detecting compromise via analysis of network traffic is in many cases the
only viable option. Unfortunately, traditional Deep Packet Inspection techniques are not applicable: many IoT
devices encrypt their traffic and common attacks (e.g., credential stuffing) cannot be described via signatures.
Anomaly detection on traffic features, while effective to identify egregious misbehavior (e.g., a DDoS) cannot
identify privacy violations, where an attacker triggers legitimate functions (e.g., streaming video, unlocking a
door), but without consent of the user. In this paper, we propose a novel anomaly detection technique based on
the analysis of user activities. Our approach builds a model to identify user-performed activities on the device
from packet sequences, and uses unsupervised learning to identify deviations from normal user behavior in
activity sequences. Thus, it can flag situations where an attacker misuses an IoT device, even when such
attacks do not involve protocol-level exploits and do not result in significant anomalies in traffic-level features.
Preliminary results show that our approach can effectively map device traffic to activities, and suggest that
such activities can be used to distinguish malicious and benign users.
1 INTRODUCTION
Many home IoT devices suffer from poor security.
IoT manufacturers tend to have limited experience
in secure programming, which results in poor code
written for firmware, front end application, commu-
nicating protocols and APIs. Even if mistakes are
identified, updating the devices is in many cases dif-
ficult due to limited connectivity and lack of user
awareness. Furthermore, many devices are shipped
with default or weak passwords, in some cases hard-
coded (Hall, 2018).
The problem is further compounded by the signif-
icant privacy risks inherent in IoT usage. Devices are
installed inside the home and have various types of
sensors (e.g. camera) as well as vast data collection
capabilities. Some devices are also actuators, influ-
encing the physical space around them (e.g., a ther-
mostat). Given these premises, it is not surprising
that IoT devices can enable theft (Osborne, 2020) and
have been used as vectors for privacy violations, up to
serious domestic abuse cases (Bowles, 2018). We col-
lectively term this class of abuses privacy invasions.
∗
This Work Was Supported in Part by Funding from
Nsf under Award Number Cns 1822118, CableLabs, Ami,
Nist, Cyber Risk Research, Statnett and from Cyber Secu-
rity Center Supported by State of Colorado.
Detecting privacy invasions is difficult. Host-
based threat protection tools are unsuitable for IoTs,
which are resource-constrained and hard to upgrade.
More promising is the analysis of device network
traffic to identify compromise. However, traditional
techniques are unlikely to be effective for this threat
model. DPI tools work by identifying protocol-level
misuse and byte-level patterns (e.g., shellcode) which
are indication of compromise. Unfortunately, many
attacks do not involve any such misuse; in many
cases, the attacker simply takes control of a device
using a known or easy-to-guess password (Goodin,
2019), or bypasses authentication (Reynolds, 2013).
Furthermore, a large fraction of modern IoT device
traffic is encrypted and inaccessible to DPI. Traffic-
level anomaly detection (e.g., (Mirsky et al., 2018))
works even in the presence of encryption, but it has
other limitations. While such a detector can easily
identify egregious misbehavior (e.g., an attacker us-
ing a device to commit DDoS), privacy violations in-
volve an attacker using a device in its intended way
(e.g., change the setting on a thermostat), which is
unlikely to generate any useful anomaly signal purely
at the network traffic level.
In this paper, we propose a novel approach to
IoT anomaly detection that focuses on user activities,
rather than traffic features. Our core observation is
Bhosale, V., de Carli, L. and Ray, I.
Detection of Anomalous User Activity for Home IoT Devices.
DOI: 10.5220/0010476503090314
In Proceedings of the 6th International Conference on Internet of Things, Big Data and Security (IoTBDS 2021), pages 309-314
ISBN: 978-989-758-504-3
Copyright
c
2021 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
309

that, due to the semantic gap between attack activity
and its footprint in terms of packets, it is difficult for a
traditional detector to distinguish benign and anoma-
lous activity. We solve this problem by lifting the
analysis at the level of user activities, i.e. discrete,
basic operations a user can initiate by remotely oper-
ating the device (e.g., streaming video from a smart
camera). A detector working at the level of activities
can easily identify abnormal user behavior (e.g., use
of functionality not normally triggered by the legiti-
mate owner).
The first challenge we tackle is that, for our de-
tector to work, activities must first be inferred from
network traffic. Establishing such mapping requires
extracting a large amount of traffic from a given de-
vice, while labeling each flow with the activity that
caused it. For the purpose, we built an infrastructure
enabling us to trigger a large number of scripted ac-
tivities for a variety of IoT devices, while capturing
traffic labeled with the corresponding activity. This
resulted in a 19.8-GB traffic dataset which we plan
to release to foster further experimentation. Once
labeled traffic is available, a reliable mapping must
be established between flows and activities. For this
purpose, we train a random-forest classifier to map
packet sequences to activities. Finally, patterns of de-
vice use are user-specific, and should be learned, ide-
ally in an unsupervised fashion. We use clustering to
identify recurring sequences of user activities, and se-
quences of activities which deviate from the expected
behavior.
Preliminary results are promising: we report accu-
racy in the range of 86%-98% for activity identifica-
tion. We also built a proof of concept tool to perform
anomaly detection, and present an example scenario
to demonstrate its working.
2 RELATED WORK
Anomaly detection for IoT devices is a widely re-
searched area (Chandola et al., 2009). Approaches
based on both supervised learning (Alrashdi et al.,
2019; Pacheco et al., 2019) and unsupervised learn-
ing (Bhatia et al., 2019; Hoang and Duong Nguyen,
2019; Alhaidari and Zohdy, 2019) have been pro-
posed. Furthermore, (Hamza et al., 2018) propose
signature-based detection based on manufacturer us-
age descriptions. (Jung et al., 2020; Myridakis et al.,
2017) build a power consumption model using Con-
volution Neural Networks (CNNs) to detect IoT de-
vices turned into botnet. Finally, (Haefner and Ray,
2019) proposes a complexity metric for IoT devices
which is used to fine tune the anomaly detection
algorithm for each device based on its complexity.
Regardless of the specifics, the approaches above
work at the network level, that is, they fail to detect
anomaly in higher level user activities.
Other works investigate orthogonal aspects of IoT
network security. IoT device fingerprinting (Mei-
dan et al., 2017; Ortiz et al., 2019; Bezawada et al.,
2018; Msadek et al., 2019; Miettinen et al., 2017;
Thangavelu et al., 2019; Miettinen et al., 2017)
uses various machine learning classifiers to generate
unique network behavioral patterns of IoT devices.
However, these works do not focus on user activity
identification. (Ren et al., 2019) is a comprehensive
study of privacy in IoT devices. (Acar et al., 2018)
looks at privacy leakage from network traffic and sug-
gests mitigation techniques such as traffic shaping.
Closer to our goal, (Wang et al., 2020) identi-
fies the voice commands given to Amazon Echo and
Google home using deep learning. This work focuses
on a specific class of user activity and device. In
(Apthorpe et al., 2017), the authors identify activities
of IoT devices using Random Forest and K-Nearest
Neighbor (KNN) classifiers. However, the amount of
traffic data collected is small and further experimenta-
tion with large datasets is required to make conclusive
statements.
3 OUR APPROACH
3.1 Threat Model
In this work, we focus on an attacker who acquires
the credentials of the legitimate user and controls the
IoT devices in unintended ways. This includes acti-
vating/deactivating a device, performing various op-
erations, and configuring it in a manner that compro-
mises user security/privacy. Conventional anomaly
detection based on analyzing network flows may be
unable to distinguish between normal and anomalous
activities. Our work aims to classify user activities
based on network traffic and identify if the activity
pattern of the user has changed. We make two as-
sumption based on previous work – 1. IoT devices
can be distinguished from conventional computing
devices (e.g. - laptop) and 2. IoT devices can be fin-
gerprinted to identify them.
3.2 Experimental Setup
Conventional network anomaly detection techniques
focus on distinguishing normal and anomalous flows.
Our work, in contrast, focuses on distinguishing be-
tween normal and anomalous activities performed by
IoTBDS 2021 - 6th International Conference on Internet of Things, Big Data and Security
310

Internet
Android
Smartphone
USB connection
Iview Smart
Bulb
Smart Camera
Wemo smart
switch
Amazon
Echo
Echo dot
Thin client as
Router
Speaker
IoT lab network
perimeter
sas
Figure 1: Setup Diagram.
the user. We use machine learning for activity classifi-
cation and anomalous activity detection. Activity is an
action being performed by the user on an IoT device
(e.g., starting a video stream from a camera). Activity
classification and anomalous activity detection setup
involves the following pre-processing steps.
Packet Capture: This step involves capturing the
network packets of the device and storing them in a
trace.
Activity Log Generation: This step involves gener-
ating a log of the timestamps of when a particular ac-
tivity has been started.
Packet Labeling: This step involves labeling packets
with activity. Packets generated between the interval
t and t + δ are assigned to the activity that started at t.
Note that δ depends on the specific activity.
Packet Capture. We are interested in annotating
packets with user activities. At the time of exper-
imentation, there were no available datasets, except
for (Ren et al., 2019), which however does not allow
experimenting with the values of δ. Since our goal is
to annotate packets with associated activities, we pro-
vided our own infrastructure for packet capture. Most
of the experiments were carried out at IoT laboratory
at Colorado State University. Some of the experi-
ments were repeated in home settings. The results
we obtained at these two settings were comparable,
helping to demonstrate the repeatability of results.
We used a Acer Veriton 2620G thin client with
Open vSwitch as the router and wireless access point.
For wired devices, an Aruba switch was connected to
the thin client. The thin client was connected to the
university network for Internet connection. An An-
droid smartphone was connected to the desktop com-
puter which was a HP workstation with Intel Xeon
E3-1230 V2 @ 3.30GHz processor via USB connec-
tion. This desktop in turn was connected to the thin
client. It also had a speaker connected to it. Figure 1
illustrates the packet capture setup.
Activity Log Generation. We initiated activities
using two methods:
Android applications on smart phone: We used
AndroidViewClient (AndroidViewClient, ) python
library which makes use of android debugger bridge
to control the smartphone from a python script. It can
start and stop applications on the smartphone and can
simulate a screen touch using XY coordinates.
Voice commands: For devices which use voice com-
mands to take inputs from users, we converted text
to speech using google translate API. The converted
voice commands were then played on the speaker.
We simulated power cycle using a WeMo Smart Plug
(WemoInsight, ) and connected the power cord of the
IoT device to this plug. This plug can be controlled
by smartphone.
The packets were captured on the thin client using
tshark and then sent to the Desktop, which generated
the activity log. A python script was used to automate
the packet capture and activity log generation. The
dataset currently has captures for 9 IoT devices with
total size of 19.8 GB.
Packet Labeling. Packet captures and the activity
logs are fed to the packet labeling module. For each
activity with timestamp t, all packets from the device
having a timestamp T , where t ≤ T ≤ t + δ are an-
notated with the activity id (δ is expressed in seconds
and varies for different activities of a device).
The window size δ specifies the time it takes for
an activity to finish from the time a user initiated it
using smartphone or other interaction method. It is an
important parameter and can only be approximated
as it is not possible to accurately calculate it due to
factors such as network delays, device response time
variation, etc. Initially we calculated it manually for
each activity. However, to make the process scalable,
we assigned the same delta to activities of similar na-
ture. The accuracy trade-off of this was not significant
enough to affect the results of classification.
Detection of Anomalous User Activity for Home IoT Devices
311
Arlo Q
camera
Amazon
echo dot
Google
home mini
Omna
180 camera
Samsung
HDTV
0.0
0.2
0.4
0.6
0.8
1.0
Precision
(a) Precision.
Arlo Q
camera
Amazon
echo dot
Google
home mini
Omna
180 camera
Samsung
HDTV
0.0
0.2
0.4
0.6
0.8
1.0
Recall
(b) Recall.
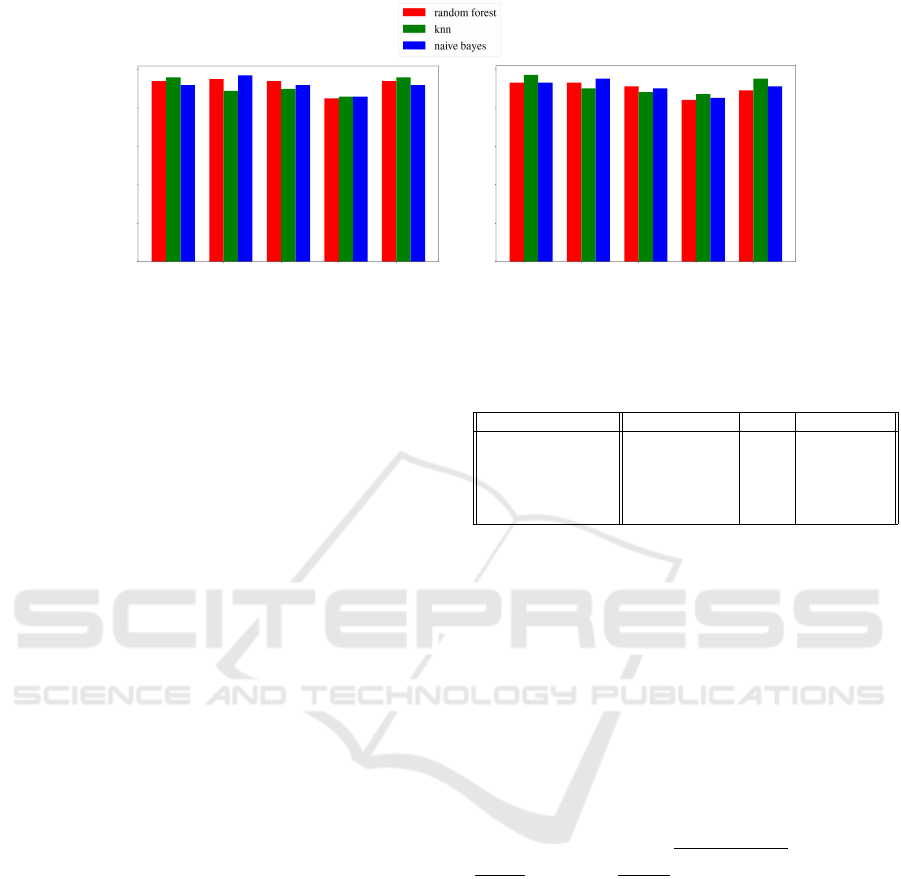
Figure 2: Precision and Recall.
3.3 Data Preprocessing and Feature
Selection
Errors and retransmissions are removed from the cap-
tures to reduce noise. Packet information are ex-
tracted and fed, along with the activity log, to the
packet labeling module which, based on the provided
window size δ, labels the packet according to the ac-
tivity with which they are associated.
We partition the network traffic in three cate-
gories: captures having incoming, outgoing, and both
incoming and outgoing packets. From these three cat-
egories we extract characteristic and statistical fea-
tures. Examples include time delay, incoming mean,
incoming number of packets, outgoing 30th, 20th per-
centiles, in out ratio, kurtosis, variance, incoming
10th, 40th, 50th, 60th percentiles, outgoing mean, and
outgoing skew.
3.4 Devices Generating Limited Traffic
We use deep packet inspection for devices that use
unencrypted packets for communication and generate
very small amount of traffic when an activity is per-
formed. For such devices, machine learning meth-
ods for classification fail. We used this approach
on Wemo smart plug (WemoInsight, ), Iview bulb,
Koogeek smart plug(KogeekPlug, ). We extract pay-
load from packets and calculate Levenshtein Distance
from training data to perform classification. We get
near perfect accuracy, however this approach suffers
from scaling issues as each requires manual model-
ing.
Table 1: 5-Fold cross validation average (accuracy).
Device Random Forest kNN Naive Bayes
Arlo Q camera 0.972 0.974 0.934
Amazon Echo dot 0.982 0.972 0.984
Google home mini 0.946 0.916 0.944
Omna camera 0.858 0.876 0.872
Samsung smart TV 0.958 0.968 0.932
4 RESULTS AND DISCUSSION
4.1 Activity Classification
We performed activity classification using random
forest, kNN and Naive Bayes classifiers. We used
Python package scikit-learn to build the model
and test it on the captured data. We used 75/25
train-test split for the classification. The classifica-
tion is one to many. We used the following eval-
uation metrics to compare the performance of the
classifiers - Accuracy =
T P+T F
T P+T F+FP+FN
, Precision =
T P
T P+FP
, Recall =
T P
T P+FN
. Naive Bayes classifier per-
formed the best overall among the three with the least
error rate. The results are given in Table 1. Figure 2
details precision and recall of the Naive Bayes classi-
fier.
4.2 Anomaly Detection
We synthetically generated benign and malicious user
activity for a device for a period of 7 days using the
same method used for performing activity classifica-
tion. Both users were scripted according to realistic
but different usage patterns (an attacker may attempt
to mimic a user’s behavior, but leave detecting this
to future work). We then passed those packet cap-
tures though the activity classification module to get
a sample usage pattern for some given activity.
IoTBDS 2021 - 6th International Conference on Internet of Things, Big Data and Security
312
cluster center
benign activity
anomalous activity
(a) Benign vs malicious activity for video stream
on Arlo Q camera.
cluster center
benign activity
anomalous activity
(b) Benign vs malicious activity for voice com-
mands on echo dot.
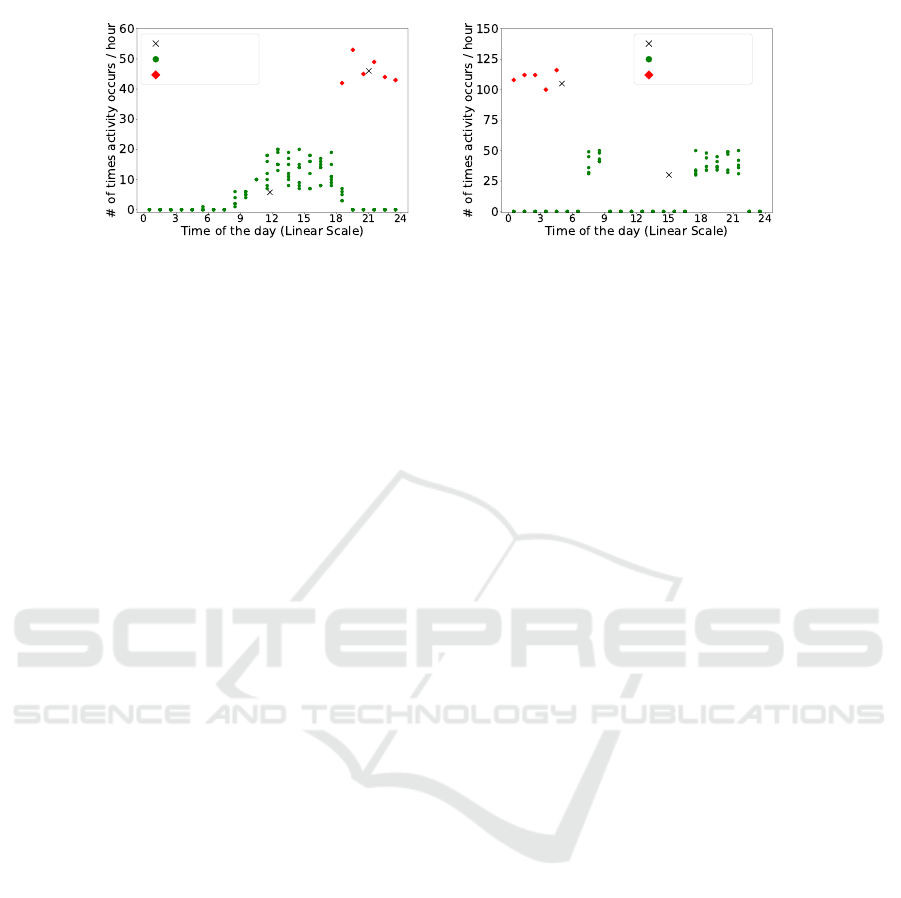
Figure 3: Anomalies in behavioral patterns.
We used K-means clustering algorithm to define
cluster boundaries from the generated benign data. As
parameters to the algorithm, we used frequency of oc-
currence of that particular activity per hour and time
of the day. The use of clustering instead of binary
classification allows us to perform anomaly detection
in an unsupervised manner. The model is trained on
the generated data. Figure 3a describes the video
streaming activity of an Arlo Q camera. The x-axis
corresponds to the time of the day. The y-axis de-
notes the number of times that activity is classified
in that hour. The green dots show the normal occur-
rence of the activity and the red ones shows anoma-
lous behavior. The ‘X’s indicate the two cluster cen-
ters. Similarly, Figure 3b shows benign vs malicious
activity for echo dot. We used various voice com-
mands to generate the activities. This figure shows
a typical home scenario where the echo dot is used
earlier in the day and in the evening. The malicious
activity models a bad actor using a physical attack
vectors—such as lasers (Sugawara et al., 2020) or ul-
trasonic audio frequencies (Zhang et al., 2017)—to
inject voice commands from a distance. While these
are difficult attack vectors to exploit, they are repre-
sentative of physical attacks with no network footprint
other than the unexpected device behavior itself. Note
however that a similar attack could also be carried us-
ing an Alexa app with compromised credentials. In
both proposed scenarios, a boundary between benign
and malicious activity can easily be established.
5 CONCLUSION AND FUTURE
WORK
Home IoT devices often have poor security and are
vulnerable to attacks. Our work focuses on detecting
compromise; towards this end, we demonstrate how
to identify the activities performed on the device by
analyzing network traffic, and how to identify anoma-
lies in user activities. Our future work involves ex-
tending this work to other types of devices, perform-
ing the anomaly detection experiments in a real-world
setting, and doing a comparison of results.
REFERENCES
Acar, A., Fereidooni, H., Abera, T., Sikder, A. K., Mi-
ettinen, M., Aksu, H., Conti, M., Sadeghi, A.-R.,
and Uluagac, A. S. (2018). Peek-a-boo: I see
your smart home activities, even encrypted! ArXiv,
abs/1808.02741.
Alhaidari, S. and Zohdy, M. (2019). Hybrid learning ap-
proach of combining cluster-based partitioning and
hidden markov model for iot intrusion detection. In
ICISDM.
Alrashdi, I., Alqazzaz, A., Aloufi, E., Alharthi, R., Zohdy,
M., and Ming, H. (2019). Ad-iot: Anomaly detection
of iot cyberattacks in smart city using machine learn-
ing. In CCWC.
AndroidViewClient.
Apthorpe, N., Reisman, D., Sundaresan, S., Narayanan, A.,
and Feamster, N. (2017). Spying on the smart home:
Privacy attacks and defenses on encrypted iot traffic.
Bezawada, B., Bachani, M., Peterson, J., Shirazi, H., Ray,
I., and Ray, I. (2018). Behavioral fingerprinting of iot
devices. In ASHES.
Bhatia, R., Benno, S., Esteban, J., Lakshman, T. V., and
Grogan, J. (2019). Unsupervised machine learning
for network-centric anomaly detection in iot. In Big-
DAMA.
Bowles, N. (2018). Thermostats, Locks and Lights: Digital
Tools of Domestic Abuse. The New York Times.
Chandola, V., Banerjee, A., and Kumar, V. (2009).
Anomaly detection: A survey. ACM Comput. Surv.,
41(3).
Goodin, D. (2019). 600,000 GPS trackers for people and
pets are using 123456 as a password.
Haefner, K. and Ray, I. (2019). Complexiot: Behavior-
based trust for iot networks. In TPS-ISA.
Hall, K. (2018). Hyperoptic’s ZTE-made 1Gbps routers had
hyper-hardcoded hyper-root hyper-password.
Detection of Anomalous User Activity for Home IoT Devices
313

Hamza, A., Gharakheili, H. H., and Sivaraman, V. (2018).
Combining mud policies with sdn for iot intrusion de-
tection. In IOT S&P.
Hoang, D. H. and Duong Nguyen, H. (2019). Detecting
anomalous network traffic in iot networks. In ICACT.
Jung, W., Zhao, H., Sun, M., and Zhou, G. (2020). Iot bot-
net detection via power consumption modeling. Smart
Health, 15:100103.
KogeekPlug.
Meidan, Y., Bohadana, M., Shabtai, A., Guarnizo, J. D.,
Ochoa, M., Tippenhauer, N. O., and Elovici, Y.
(2017). Profiliot: A machine learning approach for
iot device identification based on network traffic anal-
ysis. In SAC.
Miettinen, M., Marchal, S., Hafeez, I., Asokan, N., Sadeghi,
A., and Tarkoma, S. (2017). Iot sentinel: Automated
device-type identification for security enforcement in
iot. In ICDCS.
Mirsky, Y., Doitshman, T., Elovici, Y., and Shabtai, A.
(2018). Kitsune: An Ensemble of Autoencoders for
Online Network Intrusion Detection. In NDSS.
Msadek, N., Soua, R., and Engel, T. (2019). Iot device fin-
gerprinting: Machine learning based encrypted traffic
analysis. In WCNC.
Myridakis, D., Spathoulas, G., and Kakarountas, A. (2017).
Supply current monitoring for anomaly detection on
iot devices. In PCI.
Ortiz, J., Crawford, C., and Le, F. (2019). Devicemien:
Network device behavior modeling for identifying un-
known iot devices. In IoTDI.
Osborne, C. (2020). Smart locks opened with nothing more
than a MAC address.
Pacheco, J., Benitez, V., and F
´
elix, L. (2019). Anomaly
behavior analysis for iot network nodes. In ICFNDS.
Ren, J., Dubois, D. J., Choffnes, D., Mandalari, A. M., Kol-
cun, R., and Haddadi, H. (2019). Information expo-
sure from consumer iot devices: A multidimensional,
network-informed measurement approach. In IMC.
Reynolds, J. (2013). Dahua dvr authentication bypass - cve-
2013-6117.
Sugawara, T., Cyr, B., Rampazzi, S., Genkin, D., and Fu, K.
(2020). Light commands: Laser-based audio injection
attacks on voice-controllable systems. In USENIX Se-
curity.
Thangavelu, V., Divakaran, D. M., Sairam, R., Bhunia,
S. S., and Gurusamy, M. (2019). Deft: A distributed
iot fingerprinting technique. IEEE Internet of Things
Journal, 6(1):940–952.
Wang, C., Kennedy, S., Li, H., Hudson, K., Atluri, G., Wei,
X., Sun, W., and Wang, B. (2020). Fingerprinting
encrypted voice traffic on smart speakers with deep
learning. In WiSec.
WemoInsight.
Zhang, G., Yan, C., Ji, X., Zhang, T., Zhang, T., and Xu, W.
(2017). Dolphinattack: Inaudible voice commands. In
CCS.
IoTBDS 2021 - 6th International Conference on Internet of Things, Big Data and Security
314
