
PUF based Lightweight Authentication and Key Exchange Protocol
for IoT
Sourav Roy
a
, Dipnarayan Das
b
, Anindan Mondal
c
, Mahabub Hasan Mahalat
d
, Suchismita Roy
and Bibhash Sen
e
Department of Computer Science and Engineering, National Institute of Technology Durgapur, Durgapur, WB, India
Keywords:
Internet of Things (IoT), Physically Unclonable Function (PUF), Hardware Security, Lightweight,
Authentication, One-Time Pad (OTP), Proverif.
Abstract:
Internet-of-Things (IoT), an integral part of today’s smart society, is facing tremendous challenges of differ-
ent security and interoperability attacks. Also, IoT device works in resource-constrained environments with
limited storage. Conventional cryptography is not suitable for low-cost IoTs, and also they are susceptible
to physical attacks. This work proposes a lightweight authentication and key exchange protocol utilizing the
physically unclonable function (PUF) as security primitive. A single PUF challenge-response pair (PUF-CRP)
is utilised to overcomes the server’s storage overhead in the proposed protocol. Also, this protocol ensures the
secret message passing using the lightweight XOR function. The proposed protocol authenticates the end-user
successfully as well as maintains the security of the shared secret. The two-pass approach of the proposed
method builds confidence in communicating entities. Formal analysis by automated Proverif tool validates its
security. Performance evaluation advocates the superiority of the proposed protocol over the existing methods
upholding its strong security and lightweight feature.
1 INTRODUCTION
The Internet of Things (IoT) has emerged as the core
technology for making smart cities, building automa-
tion, automotive engineering, cyber-physical systems,
smart homes, e-healthcare, agriculture monitoring,
etc. IoT has also become the backbone of the current
century’s industrial automation, referred to as Indus-
try 4.0 or industrial IoT (IIoT). Besides the ease of
accessibility of IoT, researchers face challenges like
interoperability, security, and connectivity to resolve.
Also, in a conventional network, only internet users
face privacy concerns. But in the context of IoTs,
those who are unaware of technology also join the
rally.
Components of an IoT (i.e., sensors, actuators,
nodes, RFID tags, mobile phones, etc.) connected
with a particular server can easily be deployed solitary
a
https://orcid.org/0000-0003-1885-3995
b
https://orcid.org/0000-0002-7185-2978
c
https://orcid.org/0000-0002-6175-1380
d
https://orcid.org/0000-0003-3047-236X
e
https://orcid.org/0000-0003-4803-3074
even in extreme environments, and chances arose to
be attacked by an adversary. IoT devices are suscep-
tible to unauthorized physical access by an intruder
due to limited or no protection in a diverse environ-
ment.Again, a tiny battery-backed IoT device has lim-
ited hardware resources that prevent the usage of ex-
pensive classical cryptographic algorithms.Hence, al-
ternative approaches require addressing those limita-
tions.
In this direction, physically unclonable function
(PUF), which extracts the fabrication variation to pro-
vide a unique identity, has emerged as a viable so-
lution(R
¨
uhrmair and van Dijk, 2013; Aman et al.,
2020). The security achieved through the use of PUFs
is in the full range of scalable security while maintain-
ing low power system operation in a small footprint.
PUF-based low-cost authentication requires less area,
power, and mask layers than any traditional approach.
Several works on PUF based security protocol
have been developed for the IoT security framework
(Chatterjee et al., 2018). However, very few of these
PUF based protocols are available to address the chal-
lenges of resource-limitation, largely distributed wire-
less heterogeneous nature of IoT network. Also,
698
Roy, S., Das, D., Mondal, A., Mahalat, M., Roy, S. and Sen, B.
PUF based Lightweight Authentication and Key Exchange Protocol for IoT.
DOI: 10.5220/0010550906980703
In Proceedings of the 18th International Conference on Security and Cryptography (SECRYPT 2021), pages 698-703
ISBN: 978-989-758-524-1
Copyright
c
2021 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

these protocols suffer from various overheads, such
as NVM use in IoT devices, costly MAC and excess
CRP storage in servers. Moreover, lack of formal se-
curity analysis for these protocols makes them very
hostile.
These issues motivate us to propose a lightweight
authentication and key exchange protocol for IoT se-
curity comprising PUF as a hardware fingerprint to
prevent physical attacks, like tampering, MAC spoof-
ing, etc. This protocol reduces the overhead of crypto-
graphic engines in resource-constrained IoT devices,
reducing the authentication overhead between an IoT
device and server. The contribution of the proposed
work are as follows:
• A PUF based lightweight two-pass authentication
protocol which allows secure authentication be-
tween an IoT node and server.
• The proposed protocol stores a single CRP into
the serve to reduce storage overhead and improve
efficiency in a large-scale heterogeneous IoT net-
work.
• Formal security analysis using the automated
Proverif tool validates the security of the proposed
protocol.
• Finally, the performance analysis signifies the su-
periority of the proposed protocol.
2 BASICS OF PHYSICALLY
UNCLONABLE FUNCTION
(PUF)
Physically Unclonable Function (PUF) extracts the
unique inherent fabrication variation of a device to
provide it a unique identity. The physical system of
a PUF maps a set of input (i.e., challenge) into an
output set (i.e., response) which is hard to character-
ize (i.e., unique), model, or reproduce (i.e., unclon-
able). This system is unique for every hardware in-
stance, and the static mapping is random in nature.
A PUF has its application in low-cost authentication
and cryptographic key generation, keyless authentica-
tion, IC anti-counterfeiting, device identification, etc.
(Mukhopadhyay, 2016).A weak PUF has its linear or
polynomial set of CRPs, whereas a strong PUF can
go with exponential scaling of CRPs production. For
an ideal strong PUF, CRPs are infeasible to fully read-
out or make a computer model predict its output be-
cause of its complex features.
Mathematically a PUF can be expressed as:
f
PUF
: C → R
Where, C
i
∈ C, R
i
∈ R for any i ∈ N.
C and R represent the set of challenges and generated
responses by a PUF instance f
PUF
.
• Uniqueness Property of PUF. Uniqueness mea-
sures the difference between the response of two
similar PUF instance generated against the same
challenge. An ideal PUF should have uniqueness
of 50%.
• Reliability of PUF Response. Reliability mea-
sures the stability of a PUF response for a fixed
challenge in different environmental conditions.
Ideally, the reliability is 100%. An efficient ECA
can be accessed in (Gao et al., 2018), which has
very low hardware overhead.
Without loss of generality, we consider an ideally re-
liable strong PUF for the proposed protocol.
3 RELATED WORKS
The PUF concept was first introduced in (Pappu et al.,
2002). The IoT protocol in (Aman et al., 2016) re-
ports PUF as security primitive against physical and
side-channel attacks with the help of cryptographic
message authentication code (MAC) for integrity pre-
serving and entity authentication. A PUF based au-
thentication and key exchange protocol for IoT is pro-
posed in (Chatterjee et al., 2018). Another PUF based
authentication scheme in (Muhal et al., 2018) is appli-
cable for secure interaction among IoT devices. Secu-
rity achieves from these conventional cryptographic
MAC, ECC, Key-ed hash, and encryption-decryption
schemes are causes overhead for resource-constrained
IoT. Lightweight PUF based WiFi protocol between
IoT and router in (Mahalat et al., 2018) utilize three
sets of PUF-CRPs. The use of cryptographic XOR
reduces computation overhead. However, any large
WiFi-connected system router incurs the overhead for
holding three CRPs for each entity authentication and
reduces the scalability. These factors motivate us to
design a lightweight protocol for secure authentica-
tion and key exchange for rapidly growing heteroge-
neous IoT devices.
4 DESIGN OF THE
LIGHTWEIGHT PROTOCOL
Here, we first describe a generic threat model for the
application of the proposed protocol, and then intro-
duced the proposed lightweight PUF embedded mu-
tual authentication protocol for IoT networks.
PUF based Lightweight Authentication and Key Exchange Protocol for IoT
699
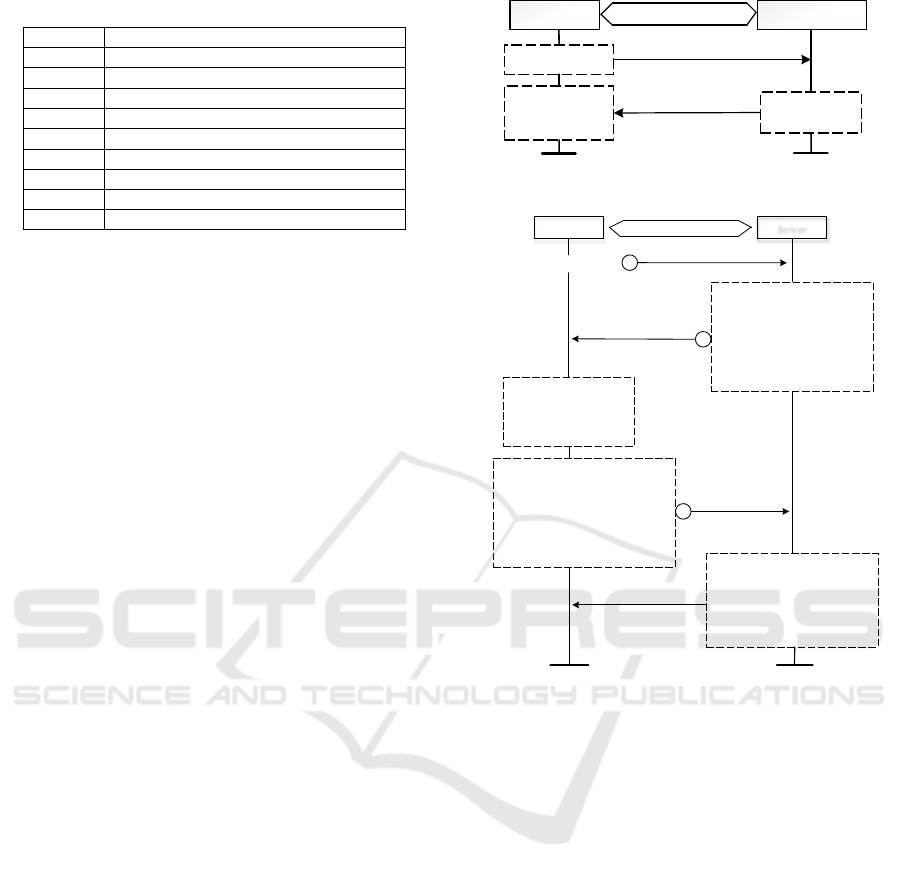
Table 1: Notation Description Table.
Notation Description
id
node
Unique identity of the IoT device
C
i
PUF challenge for any i
th
iteration
R
i
PUF responses for C
i
nonce A random number
f
PUF
Function to represent PUF-CRP mapping
⊕ Cryptographic XOR operation
H Instance variable of hashing
N Set of natural numbers
LFSR Linear feedback shift register
4.1 Protocol Threat Model
The following premises are taken into account for the
proposed protocol.
• Any physical tampering of the device immedi-
ately affects the PUF, i.e., the PUF based IoT de-
vice is tamper-resistive.
• Once the PUF embedded nodes are deployed in
operation, the PUF response can only be accessed
through the existing communication protocol.
• Database of the server that holds CRPs is secure
enough against adversarial attacks.
• Considering large IoT network, a resource con-
strained IoT node is chosen. On the other hand, a
server is considerably resourceful.
4.2 Proposed Protocol Design
The protocol consists of two modules. First, i. one-
time enrollment phase to enroll a newly connected IoT
node with the server. Second, ii. device authentica-
tion phase The notations used throughout the paper
are summarized in “Table 1”.
4.2.1 One-time Enrollment Phase
Enrolling the PUF-CRP for secure authentication is
done in a secure environment without any access to
the adversary. In this phase, server generates a ran-
dom challenge (C
i
) for the PUF, embedded in IoT
(id
node
) and collect the generate response (R
i
) and
stored in a secure database of the server as CRP,
shown in “Figure 1”.
R
i
= f
PUF
(C
i
)
4.2.2 Authentication Phase
Authentication starts with ‘Message 1’ i.e. connec-
tion initialization phase of “Figure 2”, where the IoT
node sends connection request to the server after suc-
cessful completion of one-time enrollment.
Node (id
node
)
Generate: C
i
Store:
id
node
<C
i
, R
i
>
C
i
R
i
R
i
= PUF(C
i
)
Server
Secure environment
Figure 1: PUF embedded one-time enrollment.
Node
connection request
Compute:
1. R
i
PUF(C
i
)
2. nonce R
i
M
node
Verify: H
node
Assign:
1. C
i+1
nonce
Compute:
1. R
i+1
PUF(C
i+1
)
2. nonce LFSR(nonce)
3. M
server
R
i+1
nonce
4. H
server
hash(C
i+1
|| R
i+1
||nonce)
id
node
Server
Fetch corresponding: <C
i
,R
i
>
Generate:
1. nonce
Compute:
1. M
node
R
i
nonce
2. H
node
hash(C
i
||R
i
||nonce)
3. nonce LFSR(nonce)
Compute:
1. R
i+1
M
server
nonce
Verify: H
server
Assign:
1. C
i+1
nonce
Replace and store: id
node
<C
i+1
, R
i+1
>
1
M
server
, H
server
3
connection establish
insecure / public network
C
i
, M
node
, H
node
2
Figure 2: Proposed PUF embedded authentication protocol
for IoT.
• Server searches for id
node
in its secure database
and fetches corresponding C
i
,R
i
to perform the
authentication.
• Sever generates a random number nonce. This
nonce is then masked with R
i
using XOR as OTP
to get the message M
node
.
M
node
← R
i
⊕ nonce
• This nonce act as a trusted freshness to prevent
replaying older messages.
• Hash value H
node
is calculated by concatenating
C
i
, R
i
and nonce. Then it is forwarded to the node
for verification.
H
node
← hash(C
i
||R
i
||nonce)
The server sends ‘Message 2’ to the node.
a. Server Authentication. Upon receiving ‘Message
2’ from the server, the communicating node having
id
node
first feed the C
i
to its embedded PUF. Then
produce a response R
i
similar to its previously
stored response in the server’s secure database.
R
i
= f
PUF
(C
i
)
SECRYPT 2021 - 18th International Conference on Security and Cryptography
700

• Generated R
i
is then used to get nonce, in the
step
nonce ← R
i
⊕ M
node
• Message integrity and authenticity is then rat-
ified by verifying the H
node
by the IoT node.
The successful verification confirms that the
communicated messages are not tampered in-
between.
• The IoT node is then uses the collected nonce as
C
i+1
to update old challenge C
i
. It foster a new
response R
i+1
from the updated C
i+1
.
C
i+1
← nonce
R
i+1
← PUF(C
i+1
))
• The IoT node improvises nonce to nonce
0
by
passing the nonce into a linear feedback shift
register (LFSR), same as the server does after
sending ‘Message 2’ to the node (in compute:
step 3 of server).
nonce
0
← LFSR(nonce)
• Newly generated PUF R
i+1
is then masked with
nonce
0
and transferred as M
server
to the server.
Integrity preserving hash H
server
for node au-
thentication is also sent to the server (shown by
‘Message 3’) by the IoT node.
R
i+1
⊕ nonce
0
H
server
← hash(c
i+1
||R
i+1
||nonce
0
)
b. Node Authentication. R
i+1
is decrypted by the
server from M
server
of received ‘Message 3’.
R
i+1
← M
server
⊕ nonce
0
• The server verifies the received H
server
by com-
puting hash value with help of R
i+1
, C
i+1
and nonce
0
. Trusted integrity and authenticity
claimed by the node hold for successful verifica-
tion. This authenticates the intended IoT device,
and the use of OT P helps in the secure exchange
of new volatile secret R
i+1
.
• On confirmation, the server replaces the pre-
vious CRP with this newly acknowledged
(C
i+1
,R
i+1
) of id
node
in its secure database for
the next iteration of communication.
Success of the proposed protocol (“Figure: 2)” de-
pends on the PUF function having volatile secret
R
i
. The random number nonce masked with OTP
eliminates the trust issue in key transportation sce-
narios as a cryptographic secret. For every genera-
tion of nonce, a new communication is initiated to
preserve freshness.
Finally, after successful authentication, actual mes-
sage transmission takes place between an IoT node
and server. PUF response R
i+1
is used as shared se-
cret. This shared secret helps to establish session
key after authentication to resist attack against chosen
plain text and chosen cipher text. So, proper analy-
sis is required to establish the validity of our claimed
security.
5 SECURITY ANALYSIS
Analysis of security taxonomy for the proposed pro-
tocol is as follows:
Probabilistic Analysis. Repetition probability (P
rep
)
of nonce combined with a R
i
is:
P
rep
(M
node
) = 1/(2
2n
)
where 2
n
exemplify each outcomes for any n.
Similarly, repetition frequency of any R
i+1
⊕ nonce
0
stored as M
server
is 2
2n
. So, in reality brute force at-
tack is quite impossible for some sufficiently large n
(i.e. 64 bits or 128 bits in practice).
CIA Triad. Encrypting R
i
and R
i+1
with crypto-
graphic secure XOR along with equal length nonce
and nonce
0
respectively preserve message confiden-
tiality in communication. The hashing algorithm en-
sures that the data has not been modified in transit. It
is to preserve message integrity between the intended
sender and receiver of the message. The presence of
tamper resistive and uniquely identifiable PUF in the
IoT device and the PUF CRP in the server’s secure
database assists to authenticate both the sender and
receiver.
Non-repudiation. The unclonability property of
PUF, where each response is random in nature, and
every PUF module is unique by its implementation.
It works as a digital fingerprint for every device to
safeguard against message repudiation, where denial
of generated response carries the PUF feature. This
non-repudiation with the mentioned CIA triad pro-
vides more robust security features for the proposed
protocol.
5.1 Formal Security Verification using
Proverif Tool
The security property of the protocol is formally ver-
ified using the ProVerif tool (Blanchet, 2013; Roy,
2021). Based on the proposed protocol, node and
PUF based Lightweight Authentication and Key Exchange Protocol for IoT
701

Table 2: Comparison Study.
Protocol
Application
TC1 TC2 TC3 TC4 TC5
Area
(Aman et al., 2016) IoT N N XOR 1 high
(Muhal et al., 2018) IoT N N cipher 1 high
(Chatterjee et al., 2018) IoT N Y ecc 1 high
(Mahalat et al., 2018) WiFi N N XOR 3 high
(Alladi et al., 2020) IoD Y N XOR 1 low
Proposed Here IoT N N XOR 1 low
Note: TC1: PUF-CRP database in IoT, TC2: Explicit storage for key holding, TC3: Message transmission mode,
TC4: Number of PUF-CRPs accessed for every authentication phase, TC5: Incurred hardware overhead.
server are the two roles, and their corresponding be-
haviors are defined in ProVerif as eventA and eventB
respectively. begin < event > defines the starting or
initiation of authentication request and end < event >
defines the termination of the existing request. The
occurrence of two events (event A and event B) in
proverif result is described as follows:
i. Server Authentication by IoT Node: eventB will
terminate the execution only when it has initiated
the execution, which means if any attacker imper-
sonate and initiate a authentication request, this
proverif implication will return false value.
in j − event(endB f ull(..)) ==>
in j − event(beginB f ull(..))
ii. Node Authentication by the Server: eventA will
terminate the execution only when it has initiated
the execution, which means if any attacker imper-
sonate and initiate a authentication request, this
proverif implication will return false value.
in j − event(endA f ull(..)) ==>
in j − event(beginA f ull(..))
iii. Secret Communication between Node and server:
The presence of an adversary in protocol commu-
nication through a public channel is incorporated
as attacker in this security automation tool. At-
tacker query executes throughout the protocol’s
completion to eavesdrop on the shared secret be-
tween the node and the server.
query attacker(ARa);attacker(ARb)
attacker(BRa);attacker(BRb)
attacker(AR
new
);attacker(BR
new
)
These attacker are inculcated in the execution
query to check secrecy of nonce and R
(i+1)
with
respect to node as well as server side.
This automated verification result shows that our pro-
posed protocol is resistive against defined adversarial
attack.
5.2 Modelling Robustness
In the proposed protocol, an adversary is able to ob-
tain C
i
from ‘message 2’ and ‘message 3’. Corre-
sponding R
i
is also required to create a PUF model
based on machine learning attacks. The XOR en-
crypted R
i
is hard to guess for any sufficient large bit
length. Hence, building a numerical model with an
exact randomness feature is considered infeasible.
It is also convenient that, once the enrollment pro-
cess is complete, PUF responses are accessible only
through the proposed authentication protocol. So, the
one-time enrollment immunises cloning attack from
an adversary with physical access to the PUF enabled
IoT. Hence, the proposed protocol can prevent physi-
cal attacks.
6 PERFORMANCE EVALUATION
AND COMPARISON
“Table 2” represent the performance evaluation with
existing literature in terms of the protocol architec-
ture. It is evident from the table that this proposed
protocol need not require storing PUF CRP in the IoT
Node. Using a single PUF CRP for entity authen-
tication and easy-to-implement cryptographic XOR
has superior performance improvements over conven-
tional cryptographic cipher message or ECC execu-
tion. The final column, ‘TC5’ concludes the overall
overhead incurred by the different protocols in terms
of hardware architectural dependency, and We restrict
the proposed protocol design in lightweight. “Figure
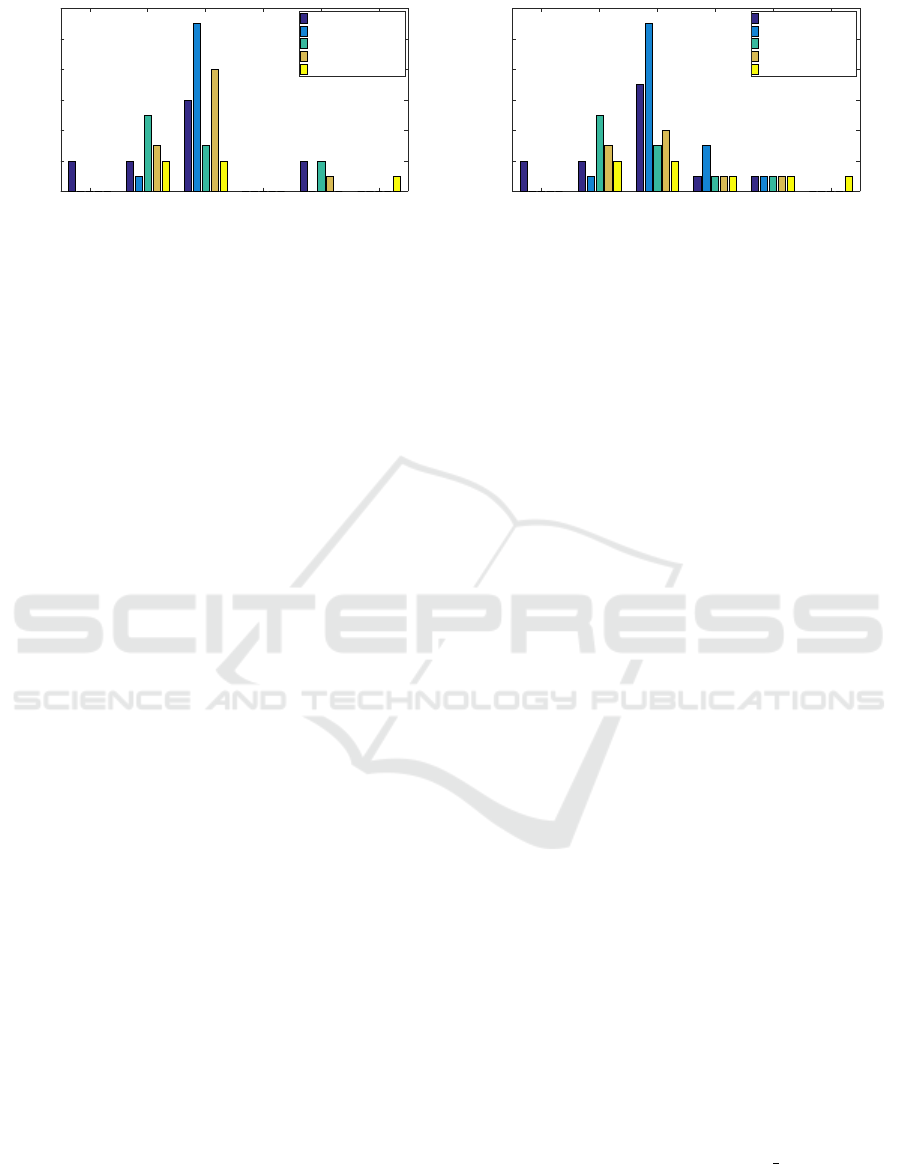
3” compare the computation performance of differ-
ent protocols along with the proposed here. “Figure
3(a)” shows the computation made by the IoT Node
and “Figure 3(b)” for server. This comparison is made
between different similarly performed protocols.
In IoT node side computation, the proposed proto-
col eliminates computationally expensive MAC with
hash functions. But, even though the hash count sur-
SECRYPT 2021 - 18th International Conference on Security and Cryptography
702
MAC HASH XOR PUF-CRP RNG LFSR
0
2
4
6
8
10
12
Total number of executions
Aman et al., 2016
Mahalat et al., 2018
Muhal et al., 2018
Alladi et al., 2020
Proposed
MAC HASH XOR PUF-CRP RNG LFSR
0
2
4
6
8
10
12
Total number of executions
Aman et al., 2016
Mahalat et al., 2018
Muhal et al., 2018
Alladi et al., 2020
Proposed
Figure 3: (a) Performance comparison of IoT device. (b) Performance comparison of Server.
passed mahalat et. al., the balanced use of single
PUF CRP and LFSR in this protocol reduces down
the number of XOR count at a certain optimal com-
pared with by them. Similarly, in server-side com-
putation, fast computing LFSR balances the perfor-
mance of hash and XOR together. Here we have
also eliminated the cryptographic MAC for faster and
lightweight performance. Thus, the claimed authenti-
cation and lightweight key exchange in this proposed
protocol is successfully established.
7 CONCLUSION
A single PUF CRP-based two-pass mutual authen-
tication and key exchange protocol are presented in
this paper. Comparison analysis makes the proto-
col lightweight in nature, and ease of implementation
make the protocol suitable for heterogeneous WSN
and the internet of connected things. Less computa-
tional functionality with adequate security raises the
proposed protocol’s acceptability while maintaining
power consumption at its optimal level. The PUF
based challenge-response mechanism helps in unique
device identification and authentication resists any
physical attack while maintaining communication se-
curity as the utmost priority.
ACKNOWLEDGMENT
This work is supported by DST-SERB under core re-
search scheme (Formerly EMR) through grant No.
EMR/2017/003206 and Young Faculty Research Fel-
low of Visvesvaraya PhD scheme through the grant
No. MLA/MUM/GA/10(37)B.
REFERENCES
Alladi, T., Naren, N., Bansal, G., Chamola, V., and Guizani,
M. (2020). Secauthuav: A novel authentication
scheme for uav-base station scenario. IEEE Trans-
actions on Vehicular Technology.
Aman, M. N., Basheer, M. H., and Sikdar, B. (2020). A
lightweight protocol for secure data provenance in the
internet of things using wireless fingerprints. IEEE
Systems Journal.
Aman, M. N., Chua, K., and Sikdar, B. (2016). Position
paper: Physical unclonable functions for iot security.
In 2nd ACM international workshop on IoT privacy,
trust, and security, pages 10–13. ACM.
Blanchet, B. (2013). Automatic verification of security pro-
tocols in the symbolic model: The verifier proverif. In
Foundations of security analysis and design VII, pages
54–87. Springer.
Chatterjee, U., Govindan, V., Sadhukhan, R., Mukhopad-
hyay, D., Chakraborty, R. S., Mahata, D., and Prabhu,
M. M. (2018). Building puf based authentication and
key exchange protocol for iot without explicit crps in
verifier database. IEEE transactions on dependable
and secure computing, 16(3):424–437.
Gao, Y., Su, Y., Xu, L., , and Ranasinghe, D. C. (2018).
Lightweight (reverse) fuzzy extractor with multiple
reference puf responses. IEEE Transactions on Infor-
mation Forensics and Security, 14(7):1887–1901.
Mahalat, M. H., Saha, S., Mondal, A., and Sen, B. (2018).
A puf based light weight protocol for secure wifi au-
thentication of iot devices. In 2018 8th International
Symposium on Embedded Computing and System De-
sign (ISED), pages 183–187. IEEE.
Muhal, M. A., Luo, X., Mahmood, Z., and Ullah, A.
(2018). Physical unclonable function based authen-
tication scheme for smart devices in internet of things.
In 2018 IEEE International Conference on Smart In-
ternet of Things (SmartIoT), pages 160–165. IEEE.
Mukhopadhyay, D. (2016). Pufs as promising tools for
security in internet of things. IEEE Design & Test,
33(3):103–115.
Pappu, R., Recht, B., Taylor, J., and Gershenfeld, N.
(2002). Physical one-way functions. Science,
297(5589):2026–2030.
Roy, S. (2021). Github: Proverif scripts for node server
authentication protocol. GitHub repository: https://
github.com/sourav-roy-git/Proverif
scripts.
R
¨
uhrmair, U. and van Dijk, M. (2013). Pufs in security
protocols: Attack models and security evaluations. In
2013 IEEE symposium on security and privacy, pages
286–300. IEEE.
PUF based Lightweight Authentication and Key Exchange Protocol for IoT
703
