
AN ADVANCED HYBRID P2P BOTNET 2.0
Ta-Te Lu, Hung-Yi Liao and Ming-Feng Chen
Department of Computer Science & Information Engineering, Ching Yun University
Chung-Li, Taoyuan County 320, Taiwan, China
Keywords: Peer-to-peer, Botnets, Botnet 2.0, Hybrid peer-to-peer.
Abstract: Recently, malware attacks have become more serious over the Internet by e-mail, denial of service (DoS) or
distributed denial of service (DDoS). The Botnets have become a significant part of the Internet malware
attacks. The traditional botnets include three parts – botmaster, command and control (C&C) servers and
bots. The C&C servers receive commands from botmaster and control the distributions of computers
remotely. Bots use DNS to find the positions of C&C server. In this paper, we propose an advanced hybrid
peer-to-peer (P2P) botnet 2.0 (AHP2P botnet 2.0) using web 2.0 technology to hide the instructions from
botmaster into social sites, which are regarded as C&C servers. Servent bots are regarded as sub-C&C
servers to get the instructions from social sites. The AHP2P botnet 2.0 can evaluate the performance of
servent bots, reduce DNS traffics from bots to C&C servers, and achieve harder detection bots actions than
IRC-based botnets over the Internet.
1 INTRODUCTION
The Internet is a communication infrastructure that
interconnects the global community of end users and
content servers. In recent years, malware attacks
become more serious over the Internet by e-mail,
denial of service (DoS) or distributed denial of
service (DDoS). The Botnets become a significant
part of the Internet malware attacks.
The traditional botnets consist of three parts -
botmaster, command and control (C&C) servers and
bots. (1) The botmaster sends commands to C&C
servers and do malware attacks. (2) The C&C
servers receive commands from botmaster and
control the distributions of computers remotely. (3)
Bots use DNS to find the positions of C&C server,
and then communicate with C&C servers,
periodically. However, the C&C server is easily
detected or blocked by network manager or firewall
in that the C&C server is a bottleneck in traditional
botnets. Morales et al. (2009) analyze the DNS
traffic to find infected hosts when the infected hosts
first join a botnet. Peer-to-peer (P2P) botnets consist
of three parts – botmaster, servent bots and client
bots. The P2P botnets are distinctive from traditional
botnets in that there is no central C&C server for a
P2P botnet.
The current researchers have focused on
monitoring and detecting the traffic of existing bot-
nets. Jang et al. (2009) and Grizzard et al. (2007)
monitored the Waldac and the Trojan.Peacomm
botnet traffic to detect malicious peer-to-peer botnet,
respectively. Chang et al. (2009) discussed some
mechanisms to detect the existing P2P botnets. Jian
et al. (2010) proposed a neighbour list selecting
mechanism to decrease the connection time from
control nodes to bots in P2P Botnet. Some of
researchers presented specific peer-to-peer botnets
(Wang, Sparks, Zou, 2010; Xie and Tan, 2009;
Hung and Tan, 2009) that they are harder to be
monitor than traditional botnets.
The social websites use Web 2.0 technology to
interact and collaborate with each other in virtual
community, such as blog, video sharing, instant
messaging. Nguyen and Josef (2009) named Bot 2.0
the bots that use Web 2.0 communication methods,
such as when the attacker uses public blog service as
an information temporary storage for C&C server.
Therefore, the motivation of this paper is to
reduce the DNS traffics from bots to C&C servers
and achieve harder detection than traditional botnets
over the Internet. To achieve this, we use social
websites regarded as C&C server to hide the
encryption malware information and index factors to
select the candidates of servent bots. Then, P2P
botnet 2.0 mechanism is applied for botnet structure
to achieve harder detection.
The paper is organized as follows: Section 2 pre-
273
Lu T., Liao H. and Chen M..
AN ADVANCED HYBRID P2P BOTNET 2.0.
DOI: 10.5220/0003504102730276
In Proceedings of the 13th International Conference on Enterprise Information Systems (ICEIS-2011), pages 273-276
ISBN: 978-989-8425-55-3
Copyright
c
2011 SCITEPRESS (Science and Technology Publications, Lda.)
sents the proposed of hybrid P2P botnet 2.0 structure
(AHP2P botnet 2.0). Simulation results are given in
Section 3. Finally, the conclusions are drawn in
Section 4.
2 HYBRID P2P BOTNET 2.0
STRUCTURE
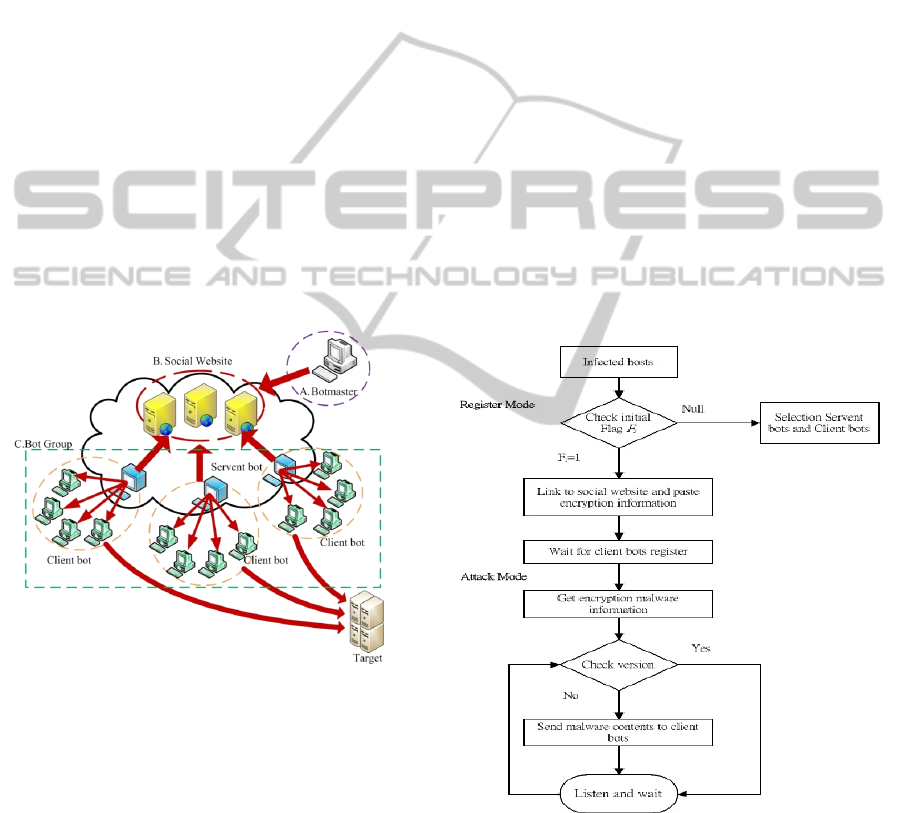
The proposed advanced hybrid P2P botnet 2.0
structure (AHP2P botnet 2.0) is illustrated in Figure-
1. The AHP2P botnet 2.0 consists of three parts –
botmaster, social websites, bot groups. Bot groups
consist of servent bots and client bots. Malware
Information from botmaster is embedded into social
websites. The servent bots in bot groups will link
with the social website to get the malware
information from the social websites and send to
client bots. Client bots attack target after they
receive malware information from servent bot. The
details of the process of embedding social website,
the process of servent bots, and the process of client
bots are described separately as follows.
Figure 1: The proposed hybrid P2P botnet 2.0 structure.
2.1 The Process of Embedding Social
Website
The encryption malware information is embedded
into blog service after the malware information is
encrypted by Message-Digest algorithm 5 (MD5).
The malware information includes an attack version,
malware contents, attack time and peer list about IP
address of servent bots. Attack version is used to
check whether the malware attack has been executed
or not. Malware contents include target’s MAC and
IP address, etc. Peer list addresses the IP address of
existence servent bots.
2.2 Selection Servent Bots and Client
Bots Process
Hardware configuration, online time, and social
websites visiting times are important index factors to
select the servent bots from infected host i.
,
(1)
where IF
i
is index factor for host i, WF
CPU
is number
of process weighting value, WF
FREQ
is CPU
frequency weighting value, WF
MEM
is a weighting
value for memory size, WF
OT
is a weighting value
for online time, WF
VT
is a weighting value for
visiting social websites times
(2)
Initial flag F
i
is null for each infected host i. If the
index factor IF
i
is larger than threshold T
0
, then the
host i set as a servent bot, F
i
=1. Otherwise, the host
set as a client bot, F
i
=0. The next sections describe
the servent bots and client bots process.
2.3 The Process of Servent Bots
Figure 2: Steps of servent bots process: register mode and
attack mode.
The steps of servent bots process include register
mode and attack mode are shown in Figure 2. Step 1
to step 3 is register mode and step 4 to step 5 is
attack mode that all of the steps are described as
follows:
<=
≥=
clientisihostTIFF
serventisihostTIFF
ii
ii
,0
,1
0
0
ICEIS 2011 - 13th International Conference on Enterprise Information Systems
274
Register mode
Step 1: Check initial flag F
i
. If F
i
=1 go to step 2.
Otherwise, F
i
=null return to section 2.2;
Step 2: Link to social website to paste the peer list
about encryption IP address information;
Step 3: Save MAC and IP address about client bot
and go to step 4 if client bot register is succeed;
Attack mode
Step 4: Link to social website to get encryption
malware information from botmaster;
Step 5: Check attack version and send malware
contents to client bots in bot group if attack version
hasn’t been executed; Otherwise, the servent bot
goes to step6;
Step 6: Wait for the next malware commands from
botmaster and go to step 4;
2.4 The Process of Client Bots
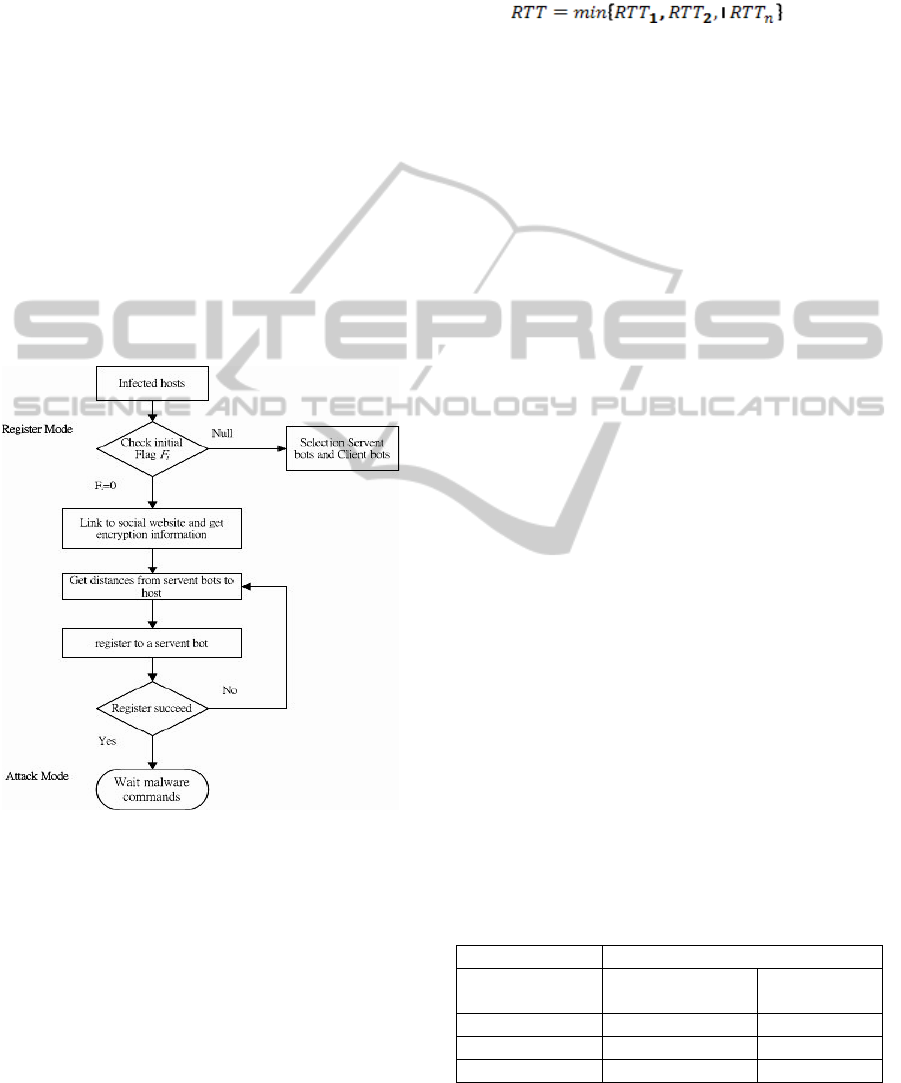
Figure 3: Steps of client bots process: register mode and
attack mode.
The steps of client bots process include register
mode and attack mode as shown in Figure 3. Step 1
to step 4 is register mode and step 5 is attack mode.
All of the steps are described as follows:
Register mode
Step 1: Check initial flag F
i
. If F
i
=0 go to step 2.
Otherwise, F
i
=null return to section 2.2;
Step 2: Link to social website to get the peer list
about IP address of servent bots from encryption
information;
Step 3: Round-trip time (RTT) represents the
distances between client bot and servent bots. RTT
mechanism is applied to get the minimum distance
of servent bot from peer list;
(3)
Step 4: Each client bot will register to a servent bot
from step 3 and get one ID’s number;
(4)
The client bot i joins into the bot group i and go to
step 5 if register succeeds. Otherwise, the client bot
returns to step 3 and gets the next IP address of
servent bot.
Attack mode
Step 5: Wait malware commands from servent bot;
3 EXPERIMENT RESULTS
Index factor IF is used to evaluate the performance
for each infected host. If the number of process is
larger than 2, WF
CPU
=3. If CPU frequency is larger
than 3.0 GHz, WF
FREQ
=1. If memory size is larger
than 2 G, WF
MEM
=2. If online time exceed 24 hours,
WF
OT
=3. If visiting social websites times exceed 2,
WF
VT
=4. The threshold T
0
= 10 and T
1
= 300 are
chosen for the simulation test.
Table 1 shows the
percentage of CPU used and P2P traffic in
each servent
bot to control numbers of client bots.
Table 2
compares the percentage of CPU used for
AHP2P botnet
2.0 and Hung and Tan, 2009. Simulation results
show that AHP2P botnet 2.0 has better performance
than Hung and Tan for the percentage of CPU used
over 50 client bots. Table 3 compares the numbers
of DNS queries in 24 hours for AHP2P botnet 2.0,
Waledac. 5, and Waledac. D.gen. In our simulation
results, AHP2P botnet 2.0 has the lowest DNS
queries than Waledac. 5 and Waledac. D. gen.
AHP2P botnet 2.0 actually
achieves harder detection
than traditional botnets.
Table 1: AHP2P botnet 2.0 simulation results.
AHP2P botnet 2.0
Numbers of client
bots / servent bot
Percentage of CPU
used
P2P traffic (
byte /sec)
50 0.4% 10.5 K
100 0.77% 17 K
150 1.15% 27.5 K
>
≤
failregisterTID
succeedregisterTID
i
i
,
,
1
1
AN ADVANCED HYBRID P2P BOTNET 2.0
275
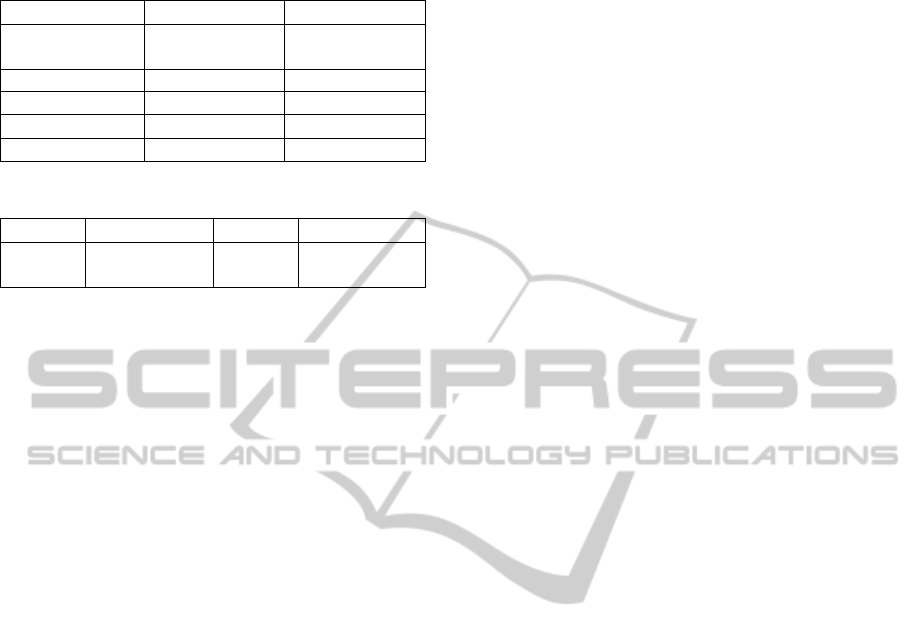
Table 2: Comparison the percentage of CPU used for
AHP2P botnet 2.0 and Hung and Tan.
AHP2P botnet 2.0 Hung and Tan
Numbers of client
bots / servent bot
Percentage of
CPU used
Percentage of
CPU used
50 0.4% 5%
64 0.5% 50%
100 0.77% -
150 1.15% -
Table 3: Numbers of packet in DNS queries.
AHP2P botnet 2.0 Waledac.5 Waledac.D.gen
DNS
Packets/24ur
4 360 792
4 CONCLUSIONS
This work presents an advanced hybrid peer-to-peer
(P2P) botnet 2.0 mechanism using web 2.0
technology to instruct social sites. The approach is
particularly suitable for hiding the encryption
malware information. Simulation results show that
the proposed method reduces DNS traffics from bots
to C&C servers and achieves harder detection than
traditional botnets.
ACKNOWLEDGEMENTS
The authors would like to thank the National
Science Council for financially supporting this
research under Contract No. NSC 99-2221-E-231-
031.
REFERENCES
Morales, J. A., Xu, S. and Sandhu, R., 2009, ‘Analyzing
DNS Activities of Bot Processes’, in Proc. IEEE Int.
Conf. Malicious and Unwanted Software, pp. 98-103.
Jang, D. I., Kim, M., Jung, H. C. and Noh, B. N., 2009,
‘Analysis of HTTP2P Botnet: Case Study Waledac’,
in Proc. IEEE Int. Conf. Communications, pp. 409-
412.
Gizzard, J. B., Sharma, V., Nunnery, C., Kang, B. B. and
Dagon, D., 2007, ‘Peer-to-peer botnets: Overview and
case study’, in Proce. Hot Topics in Understanding
Botnets, pp. 1-8.
Chang, S., Zhang, L., Guan, Y. and Daniels, T. E., 2009,
‘A Framework for P2P Botnets’, in Proc. IEEE Int.
Conf. Communications and Mobile Computing, pp
594-599.
Jian, G., Yang, Y., Zheng, K. F. and Hu, Z. M., 2010,
‘Research of An Innovative P2P-Based Botnet’, in
Proc. IEEE Int. Conf. Machine Vision and Human-
machine Interface, pp 214-218.
Wang, P., Sparks, S. and Zou, C. C., 2010, ‘An Advanced
Hybrid Peer-to-Peer Botnet’ IEEE Trans. Dependable
and Computing, vol. 7, no. 2, pp. 113-127
Xie, J. and Tan, L., 2009, ‘Detection Methods Research of
Half Distributed P2P Botnet’, Application Research of
Computers, vol. 26, no. 10, pp. 3925-3928
Hung, P. and Tan, L., 2009, ‘Design and Implementation
of Partially Decentralized P2P Botnet Control’,
Journal of Computer Applications, vol. 29, no. 9, pp.
2446-2449.
Nguyen, H., Josef, P., 2010, ‘Protecting Web 2.0 Services
from Botnet Exploitations’, in Proc. IEEE Int. Conf.
Cybercrime and Trustworthy Computing Workshop,
pp.18-28.
ICEIS 2011 - 13th International Conference on Enterprise Information Systems
276
