
Cloud Computing Adoption Factors and Processes for Enterprises
A Systematic Literature Review
Rania Fahim El-Gazzar
Department of Information Systems, University of Agder, Gimlemoen 25A, Kristiansand, Norway
Keywords: Cloud Computing, Adoption, Implementation, Integration, Evaluation, IT Governance, Decision, Cost,
Security, Regulations, Enterprise.
Abstract: Cloud computing (CC) has received an increasing interest from enterprises since its inception. With its
innovative Information Technology (IT) services delivery model, CC could add technical and strategic
business values to enterprises. However, it poses highly concerning, internal and external, issues. This paper
presents a systematic literature review to explore cloud computing adoption processes in the context of
enterprise users and the factors that affect these processes. This is achieved by reviewing 37 articles
published about CC adoption. Using the grounded theory approach, articles are classified into eight main
categories: internal, external, evaluation, proof of concept, adoption decision, implementation and
integration, IT governance, and confirmation. This is concluded in two abstract categories: CC adoption
factors and CC adoption processes whereas the former affect the latter. The results of this review indicate
that there are serious issues need to be tackled before enterprises decide to adopt CC. Based on the findings
of this review, the paper provides future Information Systems (IS) research directions toward the previously
under-investigated areas regarding the phenomenon. This involved the call for further theoretical and in-
depth empirical contributions to the area of CC adoption by enterprises.
1 INTRODUCTION
CC is receiving a notable interest from enterprise
users nowadays. It could revolutionize the way
enterprises acquire and manage their needs from
computing resources efficiently and cost-effectively.
Thus, enterprises are able to focus on their core
business activities; consequently, productivity is
increased (Garrison et al. 2012). The adoption of CC
is growing rapidly due to the scalability, flexibility,
agility, and simplicity it offers to enterprises
(Parakala and Udhas, 2011); (Herhalt and Cochrane,
2012); (Venters and Whitley, 2012). A recent survey
by (RightScale, 2013) on the adoption rates of CC
by enterprises reported that 77% of large enterprises
are adopting CC while 73% of small and medium
enterprises (SMEs) are adopting CC. CC is defined
by the National Institute of Standards and
Technology (NIST) as “a model for enabling
convenient, on-demand network access to a shared
pool of configurable computing resources (e.g.,
networks, servers, storage, applications, and
services) that can be rapidly provisioned and
released with minimal management effort or service
provider interaction” (Hogan et al. 2011, p.14).
Cloud service providers offer three different service
models depending on the enterprise’s requirements
(i.e., Software-as-a-Service (SaaS), Platform-as-a-
Service (PaaS), and/or Infrastructure-as-a-Service
(IaaS)). CC service models share five common
essential characteristics of CC (i.e., on-demand self-
service, broad network access, resource pooling,
rapid elasticity, and measured service). CC services
can be deployed in one or combination of the four
deployment models (i.e., public, private, community,
or hybrid) (Mell and Grance, 2011). A recent survey
reported that 61% of enterprises are currently using
public clouds while 38% are using private clouds
and 29% are using hybrid clouds (RightScale, 2013).
In spite of its appealing benefits for enterprises,
CC arouses serious technical, economic, ethical,
legal, and managerial issues (Marston et al., 2011);
(Venters and Whitley, 2012). This review is
important for two reasons. First, it complements the
previous literature that focused more on technical
issues of CC with less attention to business issues
regarding the adoption of CC (Yang and Tate,
2012). Second, it systematically offers detailed
78
Fahim El-Gazzar R..
Cloud Computing Adoption Factors and Processes for Enterprises - A Systematic Literature Review.
DOI: 10.5220/0004841900780087
In Proceedings of the 4th International Conference on Cloud Computing and Services Science (CLOSER-2014), pages 78-87
ISBN: 978-989-758-019-2
Copyright
c
2014 SCITEPRESS (Science and Technology Publications, Lda.)

perspectives on CC adoption factors and processes
as CC has unique attributes that involve not only
technical and managerial aspects, but its use also
needs to comply with legal issues (Heiser and
Nicolett, 2008). Further, there is a lack of in-depth
studies about issues related to CC adoption process
in the context of enterprise users (Yang and Tate
2012); (Timmermans et al., 2010).
The purpose of this paper is to systematically
review the extant literature in IS research with an
attempt to answer these two questions: what are the
processes of adopting CC by enterprises? And what
are the factors that affect these processes?
Therewith, the under-investigated issues are
identified and future IS research pathways are
proposed accordingly. This review is important for
two reasons.
The remainder of this paper is organized as
follows: Section 2 presents the methodology
followed for conducting the systematic literature
search process and classification schemes adopted.
Section 3 presents the findings from the review.
Implications for future IS research are discussed in
Section 4. Conclusions of this review are presented
in Section 5.
2 RESEARCH METHOD
This paper aims at conducting a systematic literature
review method to represent the current state of IS
research regarding CC adoption issues in the context
of enterprise users. This literature review process is
following the fundamental guidelines for conducting
an effective literature review by (Webster and
Watson, 2002); (Levy and Ellis, 2006); (vom Brocke
et al., 2009). This literature review process is done
within boundaries (Webster and Watson 2002). The
contextual boundary is within the scope of CC
adoption by enterprise users, as there are significant
issues need to be addressed before enterprises start
using clouds (Marston et al., 2011). The temporal
boundary of this review covers the published articles
in all previous years until August 2013.
2.1 Literature Search Process
Literature search process of this review involved
querying seven quality scholarly literature databases
(AISeL, IEEE Xplore, ScienceDirect, EBSCOhost,
ProQuest, Wiley online library, and ACM digital
library). These databases provide access to IS
leading journals and high quality peer-reviewed IS
conferences (Levy and Ellis, 2006). The search
criterion was limited to articles’ titles to ensure the
relevance of the articles. The phrases used for
searching all the seven databases are ‘cloud
computing’ and ‘adopt*’. This initially resulted in
69 articles.
The practical screen involved, manually, reading
the abstract of the articles to decide their relevance
to the research question raised by this review.
Further, the filtering criteria involved the exclusion
of recurring articles, research-in-progress articles,
articles that are not written in English, periodical
articles published by news websites, and trade
journals and magazines. These exclusion criteria are
defined to delimit the sample of articles so that the
literature review becomes practically manageable
(Okoli and Schabram, 2010). Eventually, this
resulted in 37 articles ready for the classification.
2.2 Classification Scheme
The reviewed articles are classified according to the
research methods to identify how adequately the
adoption of CC is researched. Research methods
used in the reviewed articles are lab experiment,
field inquiry, Delphi study, interviews, descriptive
research, case study, and survey. Some articles were
labelled under ‘conceptual paper’, as they did not
have a methodology section and providing some
concepts or adopting theories without an empirical
testing.
This review sought to develop a classification
scheme to better gain insights from the preceding
academic contributions to the area of CC adoption.
Classification of the 37 articles according to cloud
adoption issues involved using bottom-up Grounded
Theory (GT) approach (Glaser and Strauss, 1967).
GT approach is said to be valuable for conducting a
rigorous literature review (Wolfswinkel et al., 2011),
“instead of force-fitting the data to an a priori
theory” (Rich 2012, p.3).
The classification process involved a close
reading of the articles. Then, the open coding is
utilized to and resulted in labelling 28 concepts.
Next, the axial coding is applied and resulted in
grouping the 28 subcategories into eight
corresponding categories (i.e., internal, external,
evaluation, proof of concept, adoption decision,
implementation and integration, IT governance, and
confirmation). Then, selective coding was applied to
integrate the eight main categories and resulted in
two abstract categories: cloud adoption factors (i.e.,
internal and external) and cloud adoption processes
(i.e., evaluation, proof of concept, adoption decision,
implementation and integration, IT governance, and
CloudComputingAdoptionFactorsandProcessesforEnterprises-ASystematicLiteratureReview
79

confirmation) whereas the former influence the latter
(see Figure 1). To avoid a coarse analysis, these
factors and processes are elaborated in more details
in this review.
3 FINDINGS
The mapping of articles to the grounded
classification scheme and research methods is
demonstrated in Table 1.
CC Adoption Factors. Comprise internal and
external factors that have impact on CC adoption
processes.
External Factors. This comprises factors related to
the outside social environment in which the
enterprise operates, and by which its CC adoption is
influenced. The adoption of CC is, arguably,
surrounded by different levels of environmental and
inter-organizational uncertainties (Cegielski et al.,
2012). There is a wide emphasize on the importance
of government regulations at the national and
international levels (Espadanal and Oliveira, 2012);
(Nuseibeh, 2011); (Nkhoma et al., 2013). In spite of
their role to facilitate the CC adoption securely, the
lack of government regulations can hinder
enterprises from adopting the cloud (Nkhoma et al.,
2013); (Luoma and Nyberg, 2011). Some
regulations, such as Sarbanes-Oxley Act (SOX) for
corporate accounting data and Health Insurance
Portability and Accountability Act (HIPAA), have
been enacted before CC being increasingly adopted
and they might not be sufficient to facilitate its
adoption (Kim et al., 2009). However, some
countries started to enact laws specific to CC such as
cloud first policy in the USA and cloud computing
strategy by the Australian government (Bhat, 2013).
The inconsistency of international government
regulations is a further concern. Some countries tend
to restrict enterprises to store their data in cloud
infrastructure only if it is within the borders (Jensen
et al., 2011). For instance, the EU’s privacy laws
prohibit the exchange of personal information
outside the users’ jurisdiction (Mcgeogh and
Donnellan 2013). This because of cloud providers
running outside their home country must comply
with the host country’s regulations and government
surveillance which is difficult for enterprises to cope
(Abokhodair et al., 2012); (Bhat, 2013). In line with
this, standards are also cited to be an important
factor for dealing with enterprises’ concerns about
security and interoperability of cloud solutions
(Nuseibeh, 2011); (Mcgeogh and Donnellan, 2013).
Although they are still missing in the puzzle of CC
picture for enterprises (Bhat, 2013); (Lin and Chen,
2012); (Nkhoma et al., 2013), some efforts to
develop security standards took place. For instance,
Cloud Security Alliance (CSA)’s document Security
Guidance for Critical Areas of Focus in Cloud
Computing for managing CC risks (Mcgeogh and
Donnellan, 2013). Eventually, cloud providers
would have to comply with government regulations
and industrial standards to gain liability, reputation,
and trustworthiness among their potential and
present enterprise users (Bhat, 2013).
Cloud providers are required to be transparent in
explaining information to enterprises about possible
benefits and risks from adopting CC (Dargha, 2012).
Cloud providers build their reputation by their
experience in managing enterprises’ needs and
concerns in a responsible manner (Jensen et al.,
2011); (Malladi and Krishnan, 2012); (Nuseibeh,
2011). This is enabled by delivering the promised
benefits from CC to enterprises and protecting their
data from potential threats including fate sharing in
case the cloud provider went out of business (Iyer et
al., 2013); (Nuseibeh, 2011). Further, cloud
providers’ demonstration of successful business
cases and models is likely to enable CC adoption
decision (Lin and Chen, 2012); (Alshamaila and
Papagiannidis, 2013). Cloud providers might trigger
a major concern to if they outsource some of their
services to another service provider (Nuseibeh,
2011). Observing business partners perceiving
benefits from using CC is proved to be an important
motive towards its adoption (Low et al., 2011); (Lin
and Chen, 2012). Business partners’ request, with
power, the enterprise to adopt CC to keep on
collaboration with them (Cegielski et al., 2012).
Additionally, competitors play an effective role in
incentivizing enterprises to adopt CC for gaining
market visibility, operation efficiency, and new
business opportunities (Espadanal and Oliveira,
2012); (Borgman et al., 2013), especially when the
enterprise operates in a high-tech rapidly changing
industry (Low et al., 2011); (Alshamaila and
Papagiannidis, 2013). However, competitors
pressure may not be relevant to SMEs as they are
concerned about other CC adoption issues
(Alshamaila and Papagiannidis, 2013).
Internal Factors. This comprises the enterprise’s
internal characteristics and capabilities that affect its
CC adoption process. The enterprise’s willingness to
invest in and use CC both financially and
organizationally is claimed to be an important
indicator for the adoption of CC (Espadanal and
Oliveira, 2012); (Rath et al., 2012). This depends on
CLOSER2014-4thInternationalConferenceonCloudComputingandServicesScience
80

the role of the top management’s IT knowledge and
capability of providing the suitable organizational
climate for adopting CC (Bharadwaj and Lal, 2012);
(Borgman et al., 2013; Alshamaila and
Papagiannidis, 2013). Top management activities
involve: (1) understanding of CC and its
architecture, service models, and strategic values
(Luoma and Nyberg, 2011); (Espadanal and
Oliveira, 2012); (Misra and Mondal, 2011). (2)
identifying enterprise’s business needs and aligning
IT decisions with business strategies (Mcgeogh and
Donnellan, 2013); (Subramanian, 2012). (3)
evaluating the readiness of the existing IT
infrastructure, IT knowledge and skills of the human
resources, available resources, and culture (Luoma
and Nyberg, 2011); (Borgman et al., 2013);
(Espadanal and Oliveira, 2012). (4) holding the
steering wheel towards CC adoption (i.e., decide
adoption strategy, govern integration and
implementation, and evaluate cloud services after
use) with the guidance of external regulatory and
professional bodies (Morgan and Conboy, 2013);
(Mcgeogh and Donnellan, 2013). Additionally, firm
size is an important factor to CC adoption
(Espadanal and Oliveira, 2012); (Borgman et al.,
2013); (Low et al., 2011). A survey study conducted
in Taiwan indicated that large enterprises are likely
to adopt CC (Low et al. 2011). Contrarily, a survey
study in India indicated that SMEs can benefit the
most (Rath et al., 2012). Large enterprises are
claimed to have sufficient resources to afford on-
premise solutions (Borgman et al., 2013).
Enterprises need to further ensure compliance of CC
solutions with the internal (i.e., corporate policies)
and external (i.e., regulations and standards)
constraints (Morgan and Conboy, 2013); (Mcgeogh
and Donnellan, 2013); (Borgman et al., 2013).
Figure 1: Cloud Computing Adoption Factors and
Processes.
Further, the cloud/IT skills of non-IT employees
is said to be a crucial factor affecting CC adoption;
as they may be involved in strategic IT decisions,
their understanding of CC is very important
(Borgman et al., 2013); (Low et al., 2011);
(Espadanal and Oliveira, 2012). Likewise, IT
employees would have to adjust their skills and be
aware of CC benefits and risks and how to deal with
the risks instead of being overprotective (Morgan
and Conboy, 2013). Another factor affecting CC
adoption decision is the enterprise’s prior experience
and familiarity with similar technologies such as
virtualization (Alshamaila and Papagiannidis, 2013).
CC Adoption Processes. Are processes that
enterprises normally follow to adopt CC along with
responsibilities and challenges faced in each process.
Evaluation. Prior to CC adoption, the top
management is responsible for evaluating the
enterprise’s suitability for adopting CC as well as
the suitability of CC for the enterprise (Misra and
Mondal, 2011); (Lin and Chen, 2012). This includes:
(1) evaluating costs and benefits associated with CC
such as profitability, comparing the revenue
generated from the firm’s IT resources with the
revenue expected from CC, ROI, cost of migration
and integration, and cost of implementation (Misra
and Mondal, 2011; (Celine) Hoe et al., 2012). (2)
evaluating the impact of CC on people and business
processes (Mcgeogh and Donnellan 2013). (3)
evaluating the internal readiness of the enterprise,
existing IT infrastructure and IT human resources,
for adopting CC (Low et al., 2011). (4) selecting the
cloud service provider based on cloud provider’s
capability to provide a robust security controls,
enterprise’s understanding of issues related to the
control over the data, the type of service model
needed, and the perceived cloud provider’s honesty,
reputation, and sustainability (Onwudebelu and
Chukuka, 2012); (Bharadwaj and Lal, 2012).
Proof of Concept. Trying cloud services prior to the
actual adoption to evaluate its applicability for the
enterprise is likely to convince the enterprise to
adopt CC (Lin and Chen, 2012). Trialability proved
to have a positive impact on the adoption of CC
(Alshamaila and Papagiannidis, 2013). There is a
wide agreement on the significant influence of
perceived benefits and risks on the adoption of cloud
services (Alshamaila and Papagiannidis 2013); (Iyer
et al., 2013). A survey study reported that the
management’s perception of security, cost-
effectiveness, and IT compliance are likely to have a
significant impact on the decision to adopt CC
(Opala and Rahman, 2013). CC brings plenty of
benefits that are relatively convincing for enterprises
CloudComputingAdoptionFactorsandProcessesforEnterprises-ASystematicLiteratureReview
81

to adopt it (i.e., cost savings, agility, flexibility, ease
of use, scalability, facilitating collaboration between
business partners, less operational effort on Chief
Information Officers (CIOs), and increased
productivity) (Borgman et al., 2013); (Malladi and
Krishnan, 2012); (Nkhoma et al., 2013); (Lin and
Chen, 2012). With all these appealing benefits, yet
some SMEs are still negative to adopt CC services
(Alshamaila and Papagiannidis, 2013). They are
concerned about various types of risks (Jensen et al.,
2011); (Nkhoma et al., 2013); (Lin and Chen, 2012);
(Iyer et al., 2013): (a) policy and organizational
risks: this covers the risk of vendor and data lock-in.
(b) technical risks: this includes loss of data,
downtime, and cyber-attacks. (c) Legal risks: this
includes data protection regulations and licensing
issues. (d) Non-technical risks: this refers to the
misuse of cloud services and natural disasters.
According to a survey study in India on four
sectors (SMEs, education, banking, hospital) showed
that vendor risk was dominating among SMEs and
education sectors, while security risk was
dominating among banking and hospital sectors
(Iyer et al., 2013). Regarding performance risks,
moving a huge amount of data to cloud servers takes
a long time, and when moving further in the
adoption, this will require increasing bandwidth and
connectivity which is costly (Morgan and Conboy,
2013).
Adoption Decision. When deciding to adopt CC
services, the top management is involved in: (1)
evaluating core business requirements and
competencies (Subramanian, 2012). (2) determining
what data and applications should move to the cloud
(i.e., critical vs. non-critical data and applications)
(Kim et al., 2009); (Misra and Mondal, 2011);
(Kantarcioglu et al., 2011). (3) evaluating the
strategic value of CC such as agility by delivering
strong coordination IT capabilities, process
management maturity, and reduced operational
burden on CIOs so they can focus on strategic
activities (Malladi and Krishnan, 2012). (4) planning
for implementation of CC systems; the managerial
time required to plan and implement cloud solutions
was not problematic (Rath et al., 2012), while the
problem was the planning for implementation of
specific deployment models that suite the current
applications (Dargha, 2012). (5) selecting the right
service model based on the enterprise’s needs
(Bamiah et al., 2012); (Onwudebelu and Chukuka,
2012). (6) selecting deployment models based on the
sensitivity of the applications; if the applications are
determined to be core, then they should be deployed
on a private cloud, and if the applications are
determined to be non-core, then they should be
deployed on a public cloud (Dargha, 2012). Another
study suggests the core applications should not be
deployed on the cloud at all (Kim et al. 2009). (7)
negotiating cloud service contract and SLA with the
cloud provider based on the sensitivity of the data
(Misra and Mondal, 2011), and reaching an
agreement on data ownership, data confidentiality,
risk management, contract terms and termination
effect, location of the data, and guarantee of service
availability (Tsai et al., 2010); (Onwudebelu and
Chukuka, 2012).
Implementation and Integration. Compared to on-
premise approach, cloud systems can be
implemented and running in 24 hours instead of six
months (Morgan and Conboy, 2013). Thus,
implementation of cloud systems is not problematic
for enterprises, while integrating cloud systems with
the enterprise’s existing IT infrastructure can
negatively impact their adoption of CC (Morgan and
Conboy, 2013). Further, the use of cloud system by
IT staff is straightforward, while it is challenging for
the non-IT staff. This can be attributed to the degree
of complexity of cloud systems in terms of the ease
of understanding, use, and implementation or
integration of cloud services. Although CC proved
to be easy to understand and use, it arouses
integration complexity issues (Borgman et al.,
2013). Complexity is claimed to be a barrier to the
adoption of CC (Lin and Chen, 2012); (Espadanal
and Oliveira, 2012); (Low et al., 2011); (Borgman et
al., 2013). Integration problems emerge from the
less standardized interoperability between cloud
systems and the existing IT infrastructure which
triggers integration cost (Borgman et al., 2013).
Incompatibility of cloud solutions with existing IT
infrastructure can be a barrier to the adoption of CC
(Low et al., 2011).
IT Governance. The loss of IT governance within
the enterprise appeared to be a major concern
because the data and applications are under the
control of the cloud provider (Onwudebelu and
Chukuka, 2012); (Mcgeogh and Donnellan, 2013).
Enterprises are advised to conduct audit trail
meetings with the cloud provider to ensure risk free
implementation of cloud solutions that complies
with regulations, standards, and enterprise policies
(Morgan and Conboy, 2013). This is enabled by the
top management through IT governance structures
(i.e., federal or centralized) and processes (i.e.,
request, prioritize, fund, monitor, enforce, and
realign) (Borgman et al., 2013). Contrarily, IT
governance processes in highly regulated industries
will decelerate the adoption of CC (Borgman et al.,
CLOSER2014-4thInternationalConferenceonCloudComputingandServicesScience
82

2013). Likewise, IT governance processes might
hinder the adoption if the integration of cloud
solutions with the existing infrastructure appeared to
be difficult (Borgman et al., 2013).
Despite the massive advancements in securing
the cloud, yet these security solutions are not tested
extensively (Misra and Mondal, 2011). This matter
could be dissolved by IT governance initiatives to
ensure that enterprise policies, security standards,
and legal requirements are met (Borgman et al.,
2013; Morgan and Conboy, 2013). IT governance is
attained by identifying responsibilities, for instance,
“the cloud provider is responsible for the security of
the hypervisor and below, while the customer’s
responsibility begins at the operating system level
and above” (Mcgeogh and Donnellan, 2013, p.4).
While in some cases, data security at the level of
PaaS and IaaS service models is a shared
responsibility between the cloud service provider
and the adopting enterprise (Bamiah et al., 2012).
Furthermore, pursuing traceability and auditability
are cited to have impact on CC adoption (Morgan
and Conboy, 2013). Cloud providers are required to
provide traceable access controls to govern (i.e.,
who can access what object under which conditions)
that can be validated, by top management, for its
conformity to internal and external constraints
(Morgan and Conboy, 2013). These controls are
used to ensure data integrity and confidentiality
(Onwudebelu and Chukuka, 2012); (Morgan and
Conboy, 2013).
In regard with risk management during the
planning for CC implementation, a study suggests
that the enterprise should consider evaluating the
risk of storage damage, data loss, and network
security (Tsai et al., 2010). For instance, the
enterprise would maintain an on-site backup of the
data moved to the cloud (Kim et al., 2009).
Eventually, securing enterprise’s information from
potential risks is more than processes, technical
solutions, and people; it is an enterprise wide
security strategy to orchestrate these various
elements (Opala and Rahman, 2013).
Confirmation. Only one study proposed a model for
implementation and confirmation stages in adopting
CC (Dargha, 2012). This study suggests the
evaluation of cloud services based on the perceived
attributes from using cloud services (i.e., relative
advantage, complexity, compatibility, and
trialability) to decide whether to continue on using
cloud services or not.
4 DISCUSSION AND FUTURE
RESEARCH AVENUES
This article sought to review the current state of IS
research regarding CC adoption in the context of
enterprise users. The review involved classifying the
extant literature into CC adoption factors and
processes that emerged from the reviewed articles
along with research methods employed. This review
shows that no IS journal articles found yet
contributing to this research area. While few IS
conference articles appeared to contribute to the
understanding of CC adoption. On the other hand,
articles from other disciplinary journal and
conference outlets were dominant in investigating
the phenomenon.
Table 1 indicates a lack of in-depth field and
case studies regarding CC adoption processes
compared to the CC adoption factors, while the
quantitative (i.e., surveys) studies and conceptual
articles are dominating. However, the majority of
these theoretical attempts have not been tested yet.
For instance, a study proposed, theoretically, a CC
adoption assessment model that considers criteria for
selecting the cloud service provider but this model
has not been tested empirically yet (Nasir and Niazi,
2011). Hence, further qualitative research needs to
be undertaken to explore further issues and test
empirically the previous theoretical developments
regarding this area. Consequently, this triggers
questions on the IS research round table: Why
enterprises adopt CC in spite of its potential risks?
Or reversely, why enterprises do not adopt CC in
spite of its potential benefits? These questions need
to be investigated thoroughly using multiple
qualitative case studies in different contexts (i.e.,
countries and industries) to better understand CC
adoption factors and processes. Noteworthy, all the
reviewed articles study cloud adoption issues in a
list-like broad perspective. Therefore, there is a need
for interpretive case studies to investigate each of
the issues found from this review (Walsham, 1995).
Obviously, Table 1 shows that CC adoption
processes received less attention from IS researchers
in terms of exploring the challenges faced in each
process and how enterprises cope with these
challenges for risk free adoption of cloud services.
Further, there is a conflict regarding the relationship
between the firm’s size and the likelihood to adopt
CC which needs more in-depth studies to address
this conflict. Further, CC is recognized as a cost
reduction solution, however, this cost reduction may
not be significant particularly in SMEs sector as
reported by a survey study conducted in India (Iyer
CloudComputingAdoptionFactorsandProcessesforEnterprises-ASystematicLiteratureReview
83
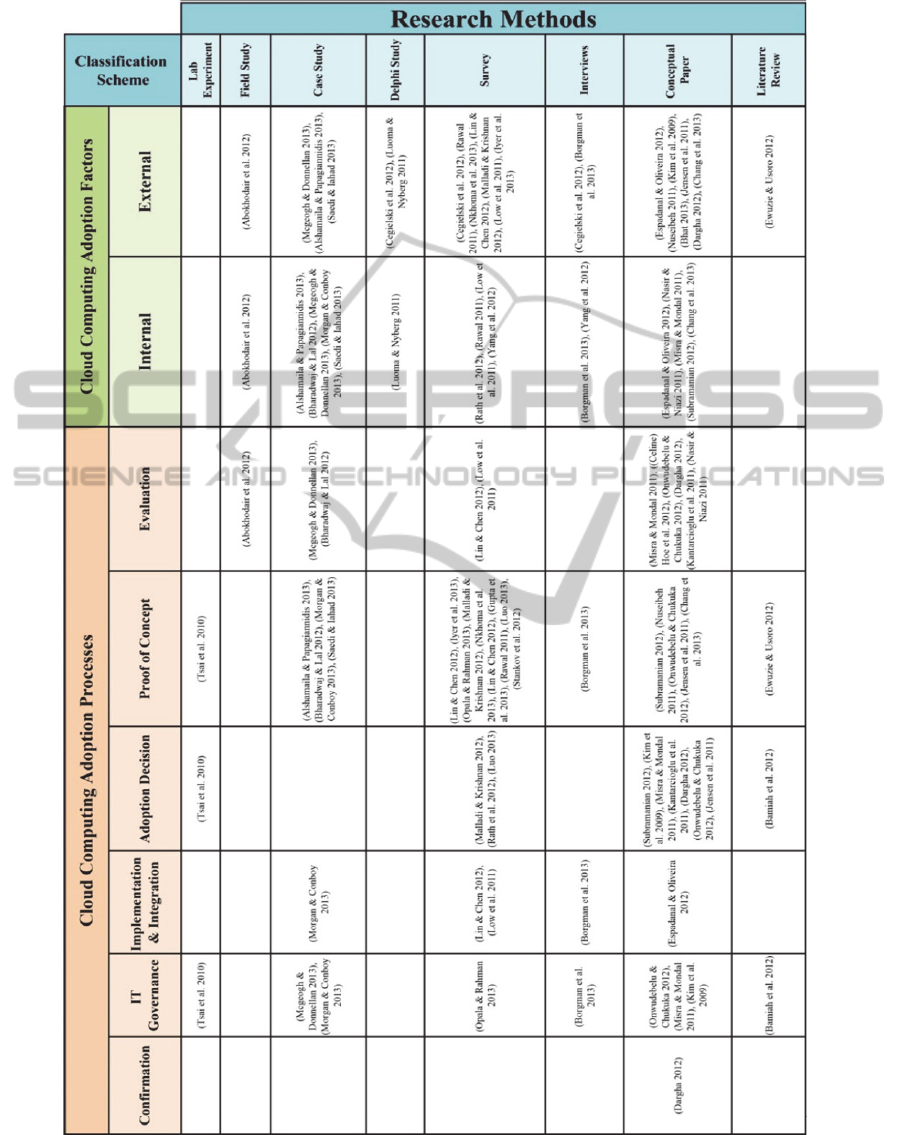
Table 1: Mapping of articles to classification scheme and research methods.
et al., 2013). Likewise, when the enterprise
maintains an on-premise backup, this adds to the
cost as well (Kim et al., 2009). Moreover, there is a
need for further exploring the impact of IT
CLOSER2014-4thInternationalConferenceonCloudComputingandServicesScience
84

governance processes throughout the
implementation process. There still plentiful legal,
ethical and inter-organizational or institutional issues
need to be investigated regarding improvements of
laws and standards. It would be insightful to
investigate internal readiness and selection of cloud
provider issues in the context of SMEs and/or large
enterprises.
Further, if CC helps enterprises reduce IT-related
costs, then how significant will be this cost
reduction? Further studies should explore the impact
of vendor and cloud solutions compatibility,
trialability, and observability on the adoption of
cloud services. Trust issues are not addressed
extensively in the reviewed articles although it is
claimed to be important for a successful adoption of
CC (Garrison et al., 2012). In spite of its appealing
merits it brings to enterprises (i.e., cost savings,
flexibility, efficiency, agility and so forth), CC puts
enterprises in a decisive choice between on-premise
and on-demand approaches. In this regard, the
Delphi method would provide insights for IT
managers about what are the most important issues,
and their priorities, that shall be considered when
deciding to adopt cloud solutions (Dalkey, 1972).
Another issue to consider, if CC releases enterprises
from managing the IT infrastructure so they can
focus on their core business activities, then what
data and applications should be moved to the cloud
and what should remain in-house? Delphi studies
can be appropriate for providing recommendations
for practice regarding internal preparation, service
model selection, and contract negotiation issues.
Finally, this review advocates the need for
conducting longitudinal studies to assess the impact
of CC implementation on both technical and
managerial capabilities of the enterprise (i.e.,
integration with existing IT infrastructure, planning,
risk management, and IT governance) as well as the
impact of the confirmation process on the
organizational innovation.
5 CONCLUSION
This paper sought to conduct a systematic review of
the extant literature regarding issues related to CC
adoption process in the context of enterprise users.
This involved exploring the under-investigated
issues and the contributions of IS research regarding
the phenomenon. The classification of reviewed
articles, findings, and implications for future IS
research is achieved according to research methods
and CC adoption factors and processes that emerged
from the utilized grounded theory approach. Yet,
plentiful legal, ethical, and technical, and managerial
issues waiting for IS researchers to explore. Thus,
the paper suggested a future IS research agenda
based on the discussed findings. This article is not
free of limitations; it sought to review only academic
articles from seven literature databases leaving white
papers, magazine articles, other scholarly literature
databases, and articles from forward and backward
search which would help capturing more issues
about CC adoption by enterprises. The search
criteria might be limited as some articles discuss CC
adoption entitled with different words (i.e., utility
computing or application service provision) that may
not have been included in the search results of this
review.
REFERENCES
(Celine) Hoe, S., Kantarcioglu, M. and Bensoussan, A.,
2012. Studying Dynamic Equilibrium of Cloud
Computing Adoption with Application of Mean Field
Games. In Proceedings of the 50th Annual Allerton
Conference on Communication, Control, and
Computing (Allerton). IEEE, pp. 220–224.
Abokhodair, N. et al., 2012. Heading for the Clouds?
Implications for Cloud Computing Adopters. In
Proceedings of the 18th Americas Conference on
Information Systems (AMCIS 2012).
Alshamaila, Y. and Papagiannidis, S., 2013. Cloud
computing adoption by SMEs in the north east of
England: A multi-perspective framework. Journal of
Enterprise Information Management, 26(3), pp.250–
275.
Bamiah, M. et al., 2012. A Study on Significance of
Adopting Cloud Computing Paradigm in Healthcare
Sector. In Proceedings of the International Conference
on Cloud Computing Technologies, Applications and
Management (ICCCTAM 2012). IEEE, pp. 65–68.
Bharadwaj, S.S. and Lal, P., 2012. Exploring the Impact of
Cloud Computing Adoption on Organizational
Flexibility: A Client Perspective. In Proceedings of
the International Conference on Cloud Computing
Technologies, Applications and Management
(ICCCTAM 2012). IEEE, pp. 121–131.
Bhat, J.M., 2013. Adoption of Cloud Computing by SMEs
in India : A study of the Institutional Factors. In
Proceedings of the 19th Americas Conference on
Information Systems. pp. 1–8.
Borgman, H.P. et al., 2013. Cloudrise: Exploring Cloud
Computing Adoption and Governance with the TOE
Framework. In Proceedings of the 46th Hawaii
International Conference on System Sciences. IEEE,
pp. 4425–4435.
Vom Brocke, J. et al., 2009. Reconstructing the Giant: On
the Importance of Rigour in Documenting the
Literature Search Process. In the 17th European
CloudComputingAdoptionFactorsandProcessesforEnterprises-ASystematicLiteratureReview
85

Conference on Information Systems (ECIS 2009).
Verona, Italy, pp. 2206–2217.
Cegielski, C.G. et al., 2012. Adoption of Cloud
Computing Technologies in Supply Chains: An
Organizational Information Processing Theory
Approach. International Journal of Logistics
Management, The, 23(2), pp.184–211.
Chang, B.-Y. et al., 2013. The Determinant of Adoption in
Cloud Computing in Vietnam. In Proceedings of the
International Conference on Computing, Management
and Telecommunications (ComManTel 2013). IEEE,
pp. 407–409.
Dalkey, N.C., 1972. The Delphi method: An experimental
study of group opinion. In N. C. Dalkey, ed. Studies in
the quality of life: Delphi and decision-making.
Lexington Books, p. 161.
Dargha, R., 2012. Cloud Computing : From Hype to
Reality . Fast Tracking Cloud Adoption. In Proceedins
of the Intermational Conference on Advances in
Computing, Communications, and Informatics. pp.
440–445.
Espadanal, M. and Oliveira, T., 2012. Cloud Computing
Adoption by Firms. In Proceedings of the
Mediterranean Conference on Information Systems
(MCIS 2012).
Ewuzie, I. and Usoro, A., 2012. Exploration of Cloud
Computing Adoption for E-Learning in Higher
Education. In Proceedings of the Second Symposium
on Network Cloud Computing and Applications. IEEE,
pp. 151–154.
Garrison, G., Kim, S. and Wakefield, R.L., 2012. Success
Factors for Deploying Cloud Computing.
Communications of the ACM, 55(9), pp.62–68.
Glaser, B.G. and Strauss, A.L., 1967. The Discovery of
Grounded Theory: Strategies for Qualitative Research,
Chicago: Aldine Publishing Company.
Gupta, P., Seetharaman, a. and Raj, J.R., 2013. The usage
and adoption of cloud computing by small and
medium businesses. International Journal of
Information Management, 33(5), pp.861–874.
Heiser, J. and Nicolett, M., 2008. Assessing the Security
Risks of Cloud Computing Available at:
http://www.globalcloudbusiness.com/SharedFiles/Do
wnload.aspx?pageid=138andmid=220andfileid=12
Herhalt, J. and Cochrane, K., 2012. Exploring the Cloud:
A Global Study of Governments’ Adoption of Cloud,
Hogan, M. et al., 2011. NIST Cloud Computing Standards
Roadmap, Available at: http://www.nist.gov/customcf/
get_pdf.cfm?pub_id=909024.
Iyer, E.K. et al., 2013. Analysis of Dissatisfiers that Inhibit
Cloud Computing Adoption across Multiple Customer
Segments. In Proceedings of the European Conference
on Information Management and Evaluation. pp. 145–
152.
Jensen, M. et al., 2011. Security Prospects through Cloud
Computing by Adopting Multiple Clouds. In
Proceedings of the 4th International Conference on
Cloud Computing (CLOUD). IEEE, pp. 565–572.
Kantarcioglu, M., Bensoussan, A. and (Celine) Hoe, S.R.,
2011. Impact of Security Risks on Cloud Computing
Adoption. In Proceedings of the 49th Annual Allerton
Conference on Communication, Control, and
Computing (Allerton). IEEE, pp. 670–674.
Kim, W. et al., 2009. Adoption Issues for Cloud
Computing. In Proceedings of the 11th International
Conference on Information Integration and Web-
based Applications and Services - iiWAS’09. New
York, New York, USA: ACM Press, p. 2.
Levy, Y. and Ellis, T.J., 2006. A Systems Approach to
Conduct an Effective Literature Review in Support of
Information Systems Research. Informing Science
Journal, 9, pp.181–212.
Lin, A. and Chen, N.-C., 2012. Cloud Computing as an
Innovation: Percepetion, Attitude, and Adoption.
International Journal of Information Management,
32(6), pp.533–540.
Low, C., Chen, Y. and Wu, M., 2011. Understanding the
Determinants of Cloud Computing Adoption.
Industrial Management and Data Systems, 111(7),
pp.1006–1023.
Luo, L., 2013. Reference Librarians’ Adoption of Cloud
Computing Technologies: An Exploratory Study.
Internet Reference Services Quarterly, 17(3-4),
pp.147–166.
Luoma, E. and Nyberg, T., 2011. Four Scenarios for
Adoption of Cloud Computing in China. In
Proceedings of the European Conference on
Information Systems (ECIS 2011).
Malladi, S. and Krishnan, M.S., 2012. Cloud Computing
Adoption and its Implications for CIO Strategic Focus
– An Empirical Analysis. In Proceedings of 33rd
International Conference on Information Systems
(ICIS 2012). pp. 1–19.
Marston, S. et al., 2011. Cloud Computing – The Business
Perspective. In Proceedings of the 44th Hawaii
International Conference on System Sciences (HICSS
2011). pp. 1–11.
Mcgeogh, B.T. and Donnellan, B., 2013. Factors That
Affect The Adoption Of Cloud Computing For An
Enterprise : A Case Study Of Cloud Adoption Within
Intel Corporation. In Proceedings of the 21st
European Conference on Information Systems. pp. 1–
13.
Mell, P. and Grance, T., 2011. The NIST Definition of
Cloud Computing Recommendations of the National
Institute of Standards and Technology, Available at:
http://csrc.nist.gov/publications/nistpubs/800-145/SP
800-145.pdf.
Misra, S.C. and Mondal, A., 2011. Identification of a
Company’s Suitability for the Adoption of Cloud
Computing and Modelling its Corresponding Return
on Investment. Mathematical and Computer
Modelling, 53(3-4), pp.504–521.
Morgan, L. and Conboy, K., 2013. Factors Affecting The
Adoption Of Cloud Computing : An Exploratory
Study. In Proceedings of the 21st European
Conference on Information Systems. pp. 1–13.
Nasir, U. and Niazi, M., 2011. Cloud Computing Adoption
Assessment Model ( CAAM ). In Proceedings of the
12th International Conference on Product Focused
CLOSER2014-4thInternationalConferenceonCloudComputingandServicesScience
86

Software Development and Process Improvement. pp.
34–37.
Nkhoma, M.Z., Dang, D.P.T. and Souza-daw, A. De,
2013. Contributing Factors of Cloud Computing
Adoption : A Technology- Organisation-Environment
Framework Approach. In Proceedings of the
European Conference on Information Management
and Evaluation. pp. 180–189.
Nuseibeh, H., 2011. Adoption of Cloud Computing in
Organizations. In Proceedings of the 17th Americas
Conference on Information Systems (AMCIS 2011).
Okoli, C. and Schabram, K., 2010. Working Papers on
Information Systems A Guide to Conducting a
Systematic Literature Review of Information Systems
Research. Sprouts: Working Papers on Information
Systems, 10(26).
Onwudebelu, U. and Chukuka, B., 2012. Will Adoption of
Cloud Computing Put the Enterprise at Risk? In
Proceedings of the 4th International Conference on
Adaptive Science and Technology (ICAST 2012).
IEEE, pp. 82–85.
Opala, O.J. and Rahman, S. (Shawon) M., 2013. An
Exploratory Analysis of the Influence of Information
Security on the Adoption of Cloud Computing. In
Proceedings of the 2013 8th International Conference
on System of Systems Engineering. pp. 165–170.
Parakala, K. and Udhas, P., 2011. The Cloud Changing the
Business Ecosystem, KPMG.
Rath, A. et al., 2012. Decision Points for Adoption Cloud
Computing in Small , Medium Enterprises (SMEs). In
Proceedings of the 7th International Conference for
Internet Technology and Secured Transactions
(ICITST 2012). pp. 688–691.
Rawal, A., 2011. Adoption of Cloud Computing in India.
Journal of Technology Management for Growing
Economies, 2(2), pp.65–78.
Rich, P., 2012. Inside the Black Box : Revealing the
Process in Applying a Grounded Theory Analysis. The
Qualitative Report, 17, pp.1–23.
RightScale, 2013. RightScale State of The Cloud Report,
Available at: http://www.rightscale.com/pdf/
rightscale-state-of-the-cloud-report-2013.pdf.
Saedi, A. and Iahad, N.A., 2013. An Integrated
Theoretical Framework for Cloud Computing
Adoption by Small and Medium-Sized Enterprises. In
PACIS 2013 Proceedings. pp. 1–12.
Stankov, I., Miroshnychenko, Y. and Kurbel, K., 2012.
Cloud Computing Adoption in German Internet Start-
up Companies. In Proceedings of BLED Conference
(BLED 2012).
Subramanian, B., 2012. The Disruptive Influence of Cloud
Computing and its Implications for Adoption in the
Pharmaceutical and Life Sciences Industry. Journal of
Medical Marketing: Device, Diagnostic and
Pharmaceutical Marketing, 12(3), pp.192–203.
Swanson, E.B. and Ramiller, N.C., 2004. Innonvating
Mindfully with Information Technology. MIS
Quarterly, 28(4), pp.553–583.
Timmermans, J. et al., 2010. The Ethics of Cloud
Computing: A Conceptual Review. In Proceedings of
the Second International Conference on Cloud
Computing Technology and Science. IEEE, pp. 614–
620.
Tsai, C. et al., 2010. Information Security Issue of
Enterprises Adopting the Application of Cloud
Computing. In
Proceedings of the 6th International
Conference on Networked Computing and Advanced
Information Management (NCM 2010). pp. 645–649.
Venters, W. and Whitley, E. a, 2012. A Critical Review of
Cloud Computing: Researching Desires and Realities.
Journal of Information Technology, 27(3), pp.179–
197.
Walsham, G., 1995. Interpretive Case Studies in IS
Research : Nature and Method. European Journal of
Information Systems, 4, pp.74–81.
Webster, J. and Watson, R., 2002. Analysing the Past to
Prepare for the Future: Writing a Literature Review.
MIS Quarterly, 26(2), pp.xiii–xxiii.
Wolfswinkel, J.F., Furtmueller, E. and Wilderom, C.P.M.,
2011. Using grounded theory as a method for
rigorously reviewing literature. European Journal of
Information Systems, 22(1), pp.45–55.
Yang, C., Hwang, B. and Yuan, B.J.C., 2012. Key
Consideration Factors of Adopting Cloud Computing
for Science. In Proceedings of the 4th International
Conference on Cloud Computing Technology and
Science. pp. 597–600.
Yang, H. and Tate, M., 2012. A Descriptive Literature
Review and Classification of Cloud Computing
Research. Communications of the Association for
Information Systems, 31(1).
CloudComputingAdoptionFactorsandProcessesforEnterprises-ASystematicLiteratureReview
87
