
Constant-size Threshold Attribute based SignCryption for Cloud
Applications
Sana Belguith
1
, Nesrine Kaaniche
2
, Maryline Laurent
2
, Abderrazak Jemai
3
and Rabah Attia
1
1
Laboratory of Electronic Systems and Communication Network, Tunisia Polytechnic School, Tunis, Tunisia
2
SAMOVAR, CNRS, Telecom SudParis, University Paris-Saclay, Member of the Chair Values and Policies of Personal
Information, Paris, France
3
Laboratory LIP2, University of Sciences of Tunis, Tunis, Tunisia
Keywords:
Attribute based Signcryption, Public Clouds, Privacy, Confidentiality, Access Control, Anonymous Data
Origin Authentication.
Abstract:
In this paper, we propose a novel constant-size threshold attribute-based signcryption scheme for securely
sharing data through public clouds. Our proposal has several advantages. First, it provides flexible crypto-
graphic access control, while preserving users’ privacy as the identifying information for satisfying the access
control policy are not revealed. Second, the proposed scheme guarantees both data origin authentication and
anonymity thanks to the novel use of attribute based signcryption mechanism, while ensuring the unlinkability
between the different access sessions. Third, the proposed signcryption scheme has efficient computation cost
and constant communication overhead whatever the number of involved attributes. Finally, our scheme sat-
isfies strong security properties in the random oracle model, namely Indistinguishability against the Adaptive
Chosen Ciphertext Attacks (IND-CCA2), Existential Unforgeability against Chosen Message Attacks (EUF-
CMA) and privacy preservation of the attributes involved in the signcryption process, based on the assumption
that the augmented Multi-Sequence of Exponents Decisional Diffie-Hellman (aMSE-DDH) problem and the
Computational Diffie Hellman Assumption (CDH) are hard.
1 INTRODUCTION
Nowadays, technological advances relieve an impor-
tant growth of digital contents which rises the demand
for new storage and network capacities and increases
the need for more cost-effective use of storage and
network bandwidth for data transfer. Thus, cloud stor-
age systems are gaining an expanding interest thanks
to their profitable architecture which supports trans-
mission, storage in a multi-tenant environment, and
intensive computation of outsourced data in a pay
per use business model. However, cloud benefits are
spoiled with significant and persistent security con-
cerns that come primarily from the loss of data con-
trol (Carlin et al., 2015). That is, users are called to
store their sensitive information on remote servers.
These security concerns lead us to the necessity of
designing comprehensive access control mechanism
for outsourced data while ensuring data confidential-
ity, data authenticity and protecting users’ privacy.
Traditional cryptosystems were designed to confiden-
tially encrypt data to a target recipient, however, in a
cloud environment, this may restrict the range of op-
portunities and flexibility offered by cloud systems.
Hence, several access control mechanisms were intro-
duced to ensure data security in outsourced systems
(Bacis et al., 2016; di Vimercati et al., 2016; di Vimer-
cati et al., 2014; Kaaniche et al., 2014; Belguith et al.,
2016; Belguith et al., 2015).
Signcryption, first introduced by Zheng (Zheng,
1997), is an important cryptographic primitive to en-
sure data confidentiality and authenticity. Signcryp-
tion is a logical combination of encryption, providing
confidentiality, and signature, supporting data authen-
ticity and integrity, in a single primitive. This novel
concept offers a reduced cost, in terms of compu-
tation and communication complexity, compared to
the cumulative cost of encryption and signature. At-
tribute Based Signcryption (ABSC) which combines
the functions of Attribute Based Encryption (ABE)
(Bethencourt et al., 2007) and Attribute Based Signa-
ture (ABS) (Maji et al., 2011) is appropriate to en-
sure fine-grained data access control in large-scale
distributed environments mainly cloud storage envi-
212
Belguith, S., Kaaniche, N., Laurent, M., Jemai, A. and Attia, R.
Constant-size Threshold Attribute based SignCryption for Cloud Applications.
DOI: 10.5220/0006469202120225
In Proceedings of the 14th International Joint Conference on e-Business and Telecommunications (ICETE 2017) - Volume 4: SECRYPT, pages 212-225
ISBN: 978-989-758-259-2
Copyright © 2017 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

ronments. Cloud users are able to outsource their
data to cloud servers and achieve efficient data shar-
ing with other users. In this scenario, ensuring con-
fidentiality of outsourced data in remote servers may
not be enough considering that cloud clients should
also be able to anonymously authenticate with the
cloud server, in order to avoid unauthorized storage
and modification of data, while preserving their pri-
vacy.
In this paper, we propose a novel constant-size at-
tribute based signcryption scheme that ensures flex-
ible access control and anonymous data access to out-
sourced data, with respect to a threshold access pol-
icy. Our proposed mechanism has several advan-
tages. First, the proposed scheme ensures flexible ac-
cess control to data which preserves the users’ pri-
vacy while authenticating with the remote server. In
addition, it provides anonymous data origin authen-
tication in order to ensure that outsourced data are
uploaded and modified by an authorised user. Sec-
ond, the size of the signcrypted message does not de-
pend on the number of attributes involved in the ac-
cess policy, which makes our scheme more suitable
for bandwidth-limited applications. Contrary to most-
existing schemes, the size of ciphertext/signature is
linear to the number of signing and encrypting at-
tributes used in the signcryption process. Thus, our
proposal is highly scalable and offers interesting per-
formances, at both the client and the cloud provider
sides. Third, our scheme satisfies strong security
properties in the random oracle model, namely Indis-
tinguishability against the Adaptive Chosen Cipher-
text Attacks (IND-CCA2), Existential Unforgeabil-
ity against Chosen Message Attacks (EUF-CMA) and
privacy preservation of the attributes involved in the
signcryption process.
Paper Organisation – The remainder of this work
is as follows: Section 2 highlights security consid-
erations and design goals. Then, Section 3 reviews
related work and introduces attribute based signcryp-
tion mechanisms. In Section 4, we describe the sys-
tem model, as well as the security model. Afterwards,
we detail the framework design and present our con-
crete construction in Section 5. Section 6 presents
a rigorous security discussion. Finally, a theoretical
analysis of computational performances is presented
in Section 7, before concluding in Section 8.
2 PROBLEM STATEMENT
As cloud computing is achieving increased popular-
ity, several organisations are using the cloud architec-
ture in a collaborative way, for their employees and/or
collaborators to share and collaboratively update a
document in progress. In case of a multinational com-
pany having different sites all over the world, employ-
ees and collaborators can be organized into different
dynamic working groups where each member of the
working group can access documents, modify their
contents and propose suggestions. Hence, users ac-
cess rights have to be specified, for defining which
users can access which data item(s).
Beyond the need for a flexible access control to
data, it is necessary to provide data origin authentica-
tion as documents have to be checked as coming from
a reliable source. The idea is to counteract illegal
data storage by permitting only the authorized users
to upload or update the data files. As such, mem-
bers of the working group have to be able to check
that the document originates from one of the mem-
bers. Also, privacy preservation of the members is
of importance, especially in the following scenario.
A Human Resources (HR) department wants to pub-
lish a survey about the employees satisfaction of the
company’s strategy. The HR manager then uploads a
file on the cloud storage platform and shares the file
with the employees. For the employees to feel free to
post opinions and suggestions on the document, there
is a high interest in that case to support anonymity
of the members, to avoid the members, the HR man-
ager or the cloud provider to identify the origin of a
comment. Finally, as documents are outsourced to
a cloud storage service, and the cloud provider can
not be fully trusted, it is of high importance to sup-
port data confidentiality against curious storage cloud
providers. This collaborative scenario can be used
in different fields, namely, industrial sectors (such as
multinational companies), medical organisations (e.g.
medical research groups), social networks···.
To support all these features with efficiency, we
propose to design a threshold attribute-based sign-
cryption (t-ABSC) to be run at the client side. Indeed,
in collaborative use cases, threshold access structures
are much more appropriate than monotone access
policies. Indeed, they are much more malleable, such
that, an authorized user has to only satisfy t attributes
from n . The idea is first to use the attribute-based
concept to support the flexible sharing of outsourced
data among a dynamic group of users, and second to
benefit from the efficiency of the signcryption concept
as the data secrecy and authenticity mechanisms are
partly merged, contrary to the heavier traditional way
considering separate signature and encryption opera-
tions.
Thus, the design of solution is motivated by pro-
viding the support of both robustness and efficiency
while fulfilling the following properties:
Constant-size Threshold Attribute based SignCryption for Cloud Applications
213

• Data Confidentiality – our t-ABSC scheme has to
protect the secrecy of outsourced and encrypted
data contents against curious users.
• Flexible Access Control – our proposal should
ensure flexible security policies among dynamic
groups of users.
• Data Origin Authenticity – the proposed scheme
has to guarantee the data origin anonymous au-
thentication property, while ensuring the unlinka-
bility between the different access sessions.
• Privacy – our solution must protect group mem-
bers’ access patterns privacy, while creating, up-
loading and requesting access to outsourced data.
That is, the cloud server must be able to grant ac-
cess with no need to additional identifying infor-
mation of the requesting users.
• Low Computation Overhead and Storage Cost –
the proposed algorithms should also have low pro-
cessing complexity and acceptable storage cost, at
both cloud provider side and client side.
3 ATTRIBUTE BASED
SIGNCRYPTION SCHEMES
In 1997, Zheng et al. (Zheng, 1997) proposed the
signcryption concept as a primitive that combines the
functions of digital signature and encryption in a sin-
gle logical step. Afterwards, several signcryption
schemes have been proposed either in public key in-
frastructure or for Identity Based Encryption settings
(Libert and Quisquater, 2004; Dent et al., 2010).
Haber et al. (Haber and Pinkas, 2001) have first
proposed the idea of combining a public encryption
scheme and a signature scheme to have the common
public parameters and the key. However, in this con-
cept, the Encrypt and Decrypt (resp. Sign and Ver-
ify) of the encryption (resp. signature) schemes were
kept unchanged. Later, Vasco et al. (Vasco et al.,
2008) proposed a combination of the Identity based
Scheme and the Identity based Signature in a joint se-
curity model. In 2010, Gagn
´
e et al. proposed At-
tribute based SignCryption (ABSC) with a threshold
structure (Gagne et al., 2010). In fact, this ABSC
scheme is efficient compared with the encrypt-then-
sign paradigm. As in CP-ABE, an encrypting entity
can specify the access structure for decrypting enti-
ties, and as in ABS, each decryption entity can ver-
ify the encrypting entity’s attributes. Note that the
Gagn
´
e et al. definition does not consider the signer’s
attribute privacy. This permits the decryption entity
to verify the encryption entity’s attribute explicitly.
However, this scheme is based on the use of two dif-
ferent sets of signing attributes and sets of decryp-
tion attributes as well as using two access structures
related to signature and encryption. As such, the
size of the generated signcrypted message increases
linearly with the number of attributes, associated to
the signing and encryption policies In (Emura et al.,
2012), Keita et al. proposed an ABSC scheme with
dynamic property, where the access structures of en-
crypting entity can be changed without reissuing se-
cret keys of users. This signcryption scheme gener-
ates a signcrypted message whose size increases lin-
early with the number of attributes used in the access
structures. Recently, Liu et al. (Liu et al., 2015) intro-
duced an attribute based signcryption inspired from
the ciphertext-policy attribute based encryption in-
troduced by Waters (Waters, 2011) and the attribute
based signature proposed by Maji et al. (Maji et al.,
2011). Their proposal is used to secure personal
health records in cloud storage. This scheme is based
on the use of two different sets of signing attributes
and sets of decryption attributes as well as using two
access structures related to signature and encryption.
As such, the size of the generated signcrypted mes-
sage increases linearly with the number of attributes,
associated to the signing and encryption policies.
The communication and computation overhead as
well as the bandwidth consumption in the existing ci-
phertext policy attribute based signcryption (Gagne
et al., 2010; Emura et al., 2012; Liu et al., 2015)
schemes increase linearly with the number of at-
tributes required in the access policies. In 2014, Rao
et al. (Rao and Dutta, 2014) proposed the first key-
policy attribute based signcryption scheme with con-
stant ciphertext size (Rao and Dutta, 2016). How-
ever, in the key-policy attribute based schemes, the
data owners cannot decide on who has access to their
encrypted data, except by their choice of descriptive
attributes for the data, since the access policy is em-
bedded in the user private keys. As a result, the data
owners have to trust the key issuer. Ciphertext-policy
attribute based schemes remove such inconvenience
by directly embedding the access policy on the cipher-
text. Thus, Ciphertext-policy attribute based schemes
are much more appropriate to data outsourcing. This
motivates us to address the problem of constructing a
ciphertext policy attribute based signcryption scheme
which introduces a signcrypted message with a con-
stant size and constant computation cost for flexible
access control, data confidentiality and anonymous
data origin authenticity.
Table 1 details the computation and storage costs
of different attribute based signcryption schemes. We
denote by n
s
= |A
s
| and n
e
= |A
e
| where A
s
and A
e
SECRYPT 2017 - 14th International Conference on Security and Cryptography
214

present the set of attributes of the user obtained from
the key extraction procedure, for signing and encrypt-
ing respectively. For common setup process, we de-
note by n = |A| the cardinal of the set of user’s at-
tributes. Let l
s
and l
e
denote the size of the signing
policy and the encryption policy, respectively. Let t,
O(M) and m respectively define the threshold value,
the size of the plaintext message M and the cardinal
of the attributes’ universe U.
4 MODEL DESCRIPTION
In this section, we first present the system model of
our constant-size (t, S)-attribute based signcryption
scheme. Then, we detail our security model.
4.1 System Model
We suppose that the signcrypting entity chooses a
subset S from the universe of attributes U and a
threshold t such that 1 ≤ t ≤ |S| to define his (t,S) ac-
cess policy. Then, he signcrypts the message M ∈ M
(i.e; M is the message space) with respect to the pol-
icy (t, S).
Our constant-size threshold attribute based signcryp-
tion consists of four randomized algorithms: Setup,
KeyGen, SignCrypt and UnsignCrypt, defined as
follows:
Setup(ξ) → (PP,msk) – the setup algorithm is
performed by the central trusted authority. It takes
as input a security parameter ξ. The Setup algorithm
outputs the public parameters PP and the secret master
key msk.
KeyGen(PP,msk,E
i
,A
i
) → sk
E
i
– this randomized
algorithm is executed to derive the secret keys of the
user E
i
. Given the public parameters PP, an attribute
set A
i
⊂ U (i.e; U is the attribute universe) of the
user E
i
and the secret master key msk. The algorithm
outputs the user’s secret key sk
E
i
associated to the at-
tribute set A
i
.
SignCrypt(PP,sk
E
S
,A
S
,(t, S),M) → Σ – the sign-
cryption algorithm is performed by a signcrypting en-
tity E
S
. It takes as inputs the public parameters PP,
the user secret key sk
E
S
, the set of signing attributes
A
S
, the (t, S) threshold access policy and the message
M. This algorithm outputs the signcrypted message
M referred to as Σ.
UnsignCrypt(PP,sk
E
U
,A
U
,(t, S),Σ) → M – the
unsigncryption algorithm is executed by the user E
U
.
It takes as inputs the public parameters PP, the set of
attributes A
U
of E
U
, the signcrypted message Σ, the
access policy (t, S) and the user’s private key sk
E
U
.
The algorithm returns the message M if the user E
U
has successfully verified the signature output by E
S
and has obtained the secret key related to the t re-
quired attributes for deciphering the signcrypted mes-
sage. Otherwise, the algorithm outputs a reject sym-
bol ⊥.
Our constant-size (t,S)-attribute based signcryp-
tion scheme has to satisfy the correctness property.
The correctness property requires that for all secu-
rity parameter ξ, all universe descriptions U, all
(PP,msk) ∈ Setup(ξ), all A
i
⊆ U, all domain enti-
ties E
i
, all
sk
E
i
∈ KeyGen(PP,msk, E
i
,A
i
), all M ∈ M , all (t, S) ∈
G (G is the access policy space) and all Σ ∈
SignCrypt(PP,sk
E
S
,A
S
,
(t,S), M) (i.e; E
S
is the signcrypting entity), if the
unsigncrypting user E
U
has successfully verified the
signature output by E
S
and obtained the secret key
related to the t required attributes for deciphering
the signcrypted message such that |A
S
∩ S| ≥ t and
|A
U
∩S| ≥ t, the UnsignCrypt(PP,sk
E
U
,A
U
,(t, S),Σ)
outputs M.
4.2 Security Model
In this section, we consider two threat models for
proving security and privacy properties of our pro-
posed constant-size (t,S)-attribute based signcryption
scheme. We first consider the case of a honest but cu-
rious cloud provider. That is, the cloud server is hon-
est as it provides proper inputs or outputs, at each step
of the protocol, properly performing any calculations
expected from it, but it is curious in the sense that it
attempts to gain extra information from the protocol.
As such, we consider the honest but curious threat
model against the confidentiality and privacy require-
ments with respect to adaptive chosen-ciphertext at-
tacks (IND-CCA2) and the computational privacy of
involved attributes.
Second, we consider the case of malicious users try-
ing to override their rights. That is, malicious users
may attempt to deviate from the protocol or to provide
invalid inputs. As such, we consider the malicious
user security model mainly against the unforgeabil-
ity requirement considering chosen message attacks
(CMA).
4.2.1 Confidentiality
A threshold attribute based signcryption t-ABSC
scheme is said to be indistinguishable against
non-adaptive chosen ciphertext attacks if there is
no probabilistic polynomial time (PPT) adversary
that can win the Exp
con f
security game with non-
negligible advantage. The Exp
con f
security game
is formally defined, between an adversary A and a
Constant-size Threshold Attribute based SignCryption for Cloud Applications
215
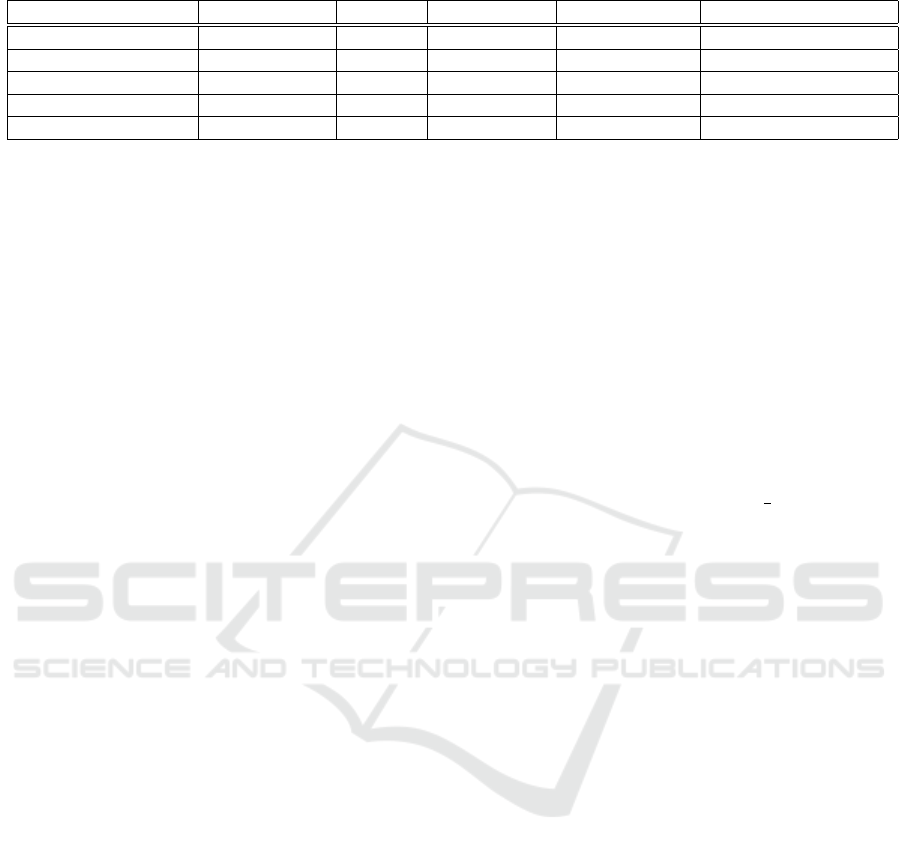
Table 1: Features and Functionality Comparison of Attribute Based Signcryption Schemes.
Scheme Common Setup Type Access Policy Key size Signcryption size
(Emura et al., 2012) No CP-ABE Monotone 2n
s
,2n
e
+ 1 + m O(l
e
) +O(n
s
)
(Liu et al., 2015) No CP-ABE Monotone n
s
+ 2,n
e
+ 2 O(l
s
) +O(l
e
)
(Gagne et al., 2010) No CP-ABE Threshold 3n
e
,2n
s
O(M) +O(n
e
) +O(n
s
)
(Rao and Dutta, 2014) No KP-ABE Monotone m + l
s
,m +l
e
O(1)
Our scheme Yes CP-ABE Threshold n +m + 1 O(1)
challenger C as follows:
Initialisation – in this phase, the adversary A
selects a set of signcryption attributes S
∗
(i.e; S
∗
corresponds to the set of attributes specified for the
access policy) to be used to signcrypt the challenge
ciphertext, and sends S
∗
to the challenger C.
Setup – the challenger C runs the Setup(ξ)
algorithm of the signcryption scheme and sends the
public parameters PP to the adversary A.
Unsigncryption Query Phase 1 – the adversary
A can request, as many times as he wants, the follow-
ing queries:
• KeyGen – the adversary A queries, for each
session i, a signcryption attribute set A
A,i
with
respect to a threshold t
i
where |A
A,i
∩ S
∗
| <
t
i
. The challenger C answers by running the
KeyGen(PP,msk,A, A
A,i
) algorithm and sends the
resulting secret key to the adversary A. The secret
key is referred to as sk
A,i
.
• UnsignCrypt – the adversary A requests the
unisgncryption of Σ with respect to a threshold
t
i
, while considering the signcryption attribute
set A
A,i
. The challenger C executes the KeyGen
algorithm to generate the secret key sk
C,i
=
KeyGen(PP,msk,C,A
C,i
), such that |A
C,i
∩ S
∗
| ≥
t
i
. Finally, the challenger C answers the query by
running the UnsignCrypt(PP,sk
C,i
,A
C,i
,
(t
i
,S
∗
),Σ) algorithm that outputs a message m or
a reject symbol ⊥.
Challenge Phase – during the challenge phase,
the adversary picks two equal length plaintexts
M
0
∗
and M
1
∗
and a threshold signcrypting at-
tribute set (t
∗
,S
∗
) (i.e; t
∗
has never been queried
during the Unsigncryption Query Phase 1) and
sends them to the challenger. The challenger C
chooses a random bit b from {0,1}, extracts a
signcrypting secret key sk
C
= KeyGen(PP,msk, A
C
)
and computes the challenge signcrypted message
Σ
b
∗
= SignCrypt(PP,sk
C
,A
C
,
(t
∗
,S
∗
),M
b
∗
). Then, the challenger sends Σ
b
∗
to the
adversary.
KeyGen Query Phase 2 – in this phase,
the adversary A who has already received Σ
b
∗
,
can query a polynomially bounded number of
queries as in Unsigncryption Query Phase 1,
except that the adversary A can not make an
UnsignCrypt(PP,,sk
A,i
,A
A,i
,(t
i
,S
∗
),Σ
b
∗
) such that
|A
A,i
∩ S
∗
| = t
∗
, where t
i
< t
∗
.
Guess – the adversary tries to guess which
message M
i
, where i ∈ {0,1} corresponds to the
enciphered data Σ
b
∗
. Thus, A outputs a bit b
0
of
b and wins the game if b = b
0
. The advantage of
the adversary A in the above game is defined as
Adv
A
[Exp
Con f
(1
ξ
)] = |Pr[b = b
0
] −
1
2
|.
Definition 1. A t-ABSC scheme satisfies the IND-
CCA2 confidentiality property, if the probability
Adv
A
[Exp
un f
(1
ξ
)] is negligible for any PPT adver-
saries.
4.2.2 Unforgeability
A threshold attribute based signcryption t-ABSC
scheme is unforgeable against chosen message attack
(EUF-CMA) if there is no probabilistic polynomial
time (PPT) adversary that can win the Exp
un f
security
game with non-negligible advantage. The Exp
un f
security game is formally defined, between an adver-
sary A and a challenger C as follows:
Initialisation – in this phase, the adversary A
selects a set of signcryption attributes S
∗
(i.e; S
∗
corresponds to the set of attributes specified for the
access policy) to be used to signcrypt the challenge
ciphertext, and sends S
∗
to the challenger C.
Setup – the challenger C runs the Setup(ξ) algo-
rithm of the scheme and sends the public parameters
PP to the adversary A.
Signcrypt Query Phase – the adversary A can
request, as many times as he wants, the following
queries:
• KeyGen – the adversary A queries, for each
session i, a signcryption attribute set A
A,i
with
SECRYPT 2017 - 14th International Conference on Security and Cryptography
216

respect to a threshold t
i
where |A
A,i
∩ S
∗
| <
t
i
. The challenger C answers by running the
KeyGen(PP,msk,A
A,i
) algorithm and sends the re-
sulting secret key to the adversary A. The secret
key is referred to as sk
A,i
.
• SignCrypt – the adversary A requests the sign-
cryption of a message M while considering for
each session i, a signcryption attribute set A
C,i
and a threshold t
i
. The challenger C exe-
cutes the KeyGen to generate the secret key
sk
C,i
= KeyGen(PP, msk,A
C,i
) and then, he exe-
cutes SignCrypt algorithm and returns the sign-
crypted message Σ
i
= SignCrypt(PP,sk
C,i
,
A
C,i
,(t
i
,S
∗
),M) to the adversary A.
Forgery Phase – after the Signcrypt Query
Phase, the adversary A outputs a ciphertext Σ
∗
with respect to the threshold challenge policy
(t
∗
,S
∗
) (i.e; t
∗
has never been queried during
the Signcrypt Query Phase and where t
i
< t
∗
).
Then, the challenger unsigncrypts Σ
∗
using the
secret key sk
C
and obtains a message M
∗
. The
adversary A wins the game if Σ
∗
is valid and was
not obtained from a SignCrypt query. That is,
UnsignCrypt(PP,sk
C
,A
C
,(t
∗
,S
∗
),Σ
∗
) = M and A
did not issue a SignCrypt(PP,sk
C
,A
C
,(t
∗
,S
∗
),M).
The adversary’s advantage is defined as
Adv
A
[Exp
un f
(1
ξ
)] = |Pr[Exp
un f
(1
ξ
)] = 1|.
Definition 2. A t-ABSC scheme is unforgeable
against chosen-message attack (EUF-CMA), if the
probability Adv
A
[Exp
un f
(1
ξ
)] is negligible for all
PPT adversaries.
This unforgeability property also includes the col-
lusion among users trying to override their rights by
combining their complementary attributes to generate
a signcrypted message satisfying a given access pol-
icy (t, S).
4.2.3 Privacy
A threshold attribute-based signcryption scheme is
said to be computationally private if any adevrsary A
running in polynomial time can not win the Exp
A
Priv
security game with non-negligible advantage. The
Exp
A
Priv
security game is formally defined, between
an adversary A and a challenger C as follows:
Setup – the adversary A chooses an attributes
universe U where |U| = n and sends it to the
challenger C. Then, the challenger runs the setup
algorithm and returns the public parameters to the
adversary A.
Challenge Phase – the adversary A chooses an
access policy (t, S) such that 1 ≤ t ≤ |S| ≤ n, two
attribute sets A
S
1
and A
S
2
satisfying the threshold
access policy such that |A
S
1
∩ S| = |A
S
2
∩ S| = t,
and a message M and sends them to the challenger
C. Afterwards, C picks a random bit b ∈ {0,1}
and executes the KeyGen algorithm such that
sk
C
= KeyGen(PP,msk,C ,A
S
b
) and then, outputs the
signcryption Σ
b
= SignCrypt(PP, sk
C
,A
S
b
,(t, S),M).
The signcrypted message Σ
b
is sent to the adversary
A as a challenge message.
Guess – the adversary outputs a bit b
0
and wins
the game if b
0
= b.
The advantage of the adversary A in the above game
is defined as Adv
A
[Exp
Priv
(1
ξ
)] = |Pr[b = b
0
] −
1
2
|.
Definition 3. A threshold attribute-based sign-
cryption scheme is computationally private if
Adv
A
[Exp
Priv
(1
ξ
)] is negligible with respect to the
security parameter λ, for any adversary A running in
a polynomial time.
5 A NOVEL CONSTANT-SIZE
THRESHOLD ATTRIBUTE
BASED SIGNCRYPTION FOR
CLOUD APPLICATIONS
5.1 Overview
In this paper, we develop a new constant size thresh-
old Attribute Based Signcryption Scheme (t-ABSC)
as a novel security mechanism for the access control,
data encryption, and message authentication in cloud
storage environments. Our proposal is based on the
use of the constant-size threshold identity based en-
cryption scheme proposed by Delerablee et al. (Deler-
abl
´
ee and Pointcheval, 2008) in 2008 and the constant
size attribute based encryption proposed by Harranz
et al. (Herranz et al., 2010) in 2010, which have been
extended to provide all security features as presented
in section 2. For instance, our scheme introduces
a novel attribute based signature which is combined
with the encryption scheme to design a signcryption
scheme. Thus, beyond including the attribute based
ciphertext, the signcrypted message involves the gen-
erated signatures. Moreover, our system supports the
common setup procedures (i.e; public parameters and
users’ keys are same for both encryption and signature
processes). In addition, it supports anonymous data-
origin authentication and provides flexible control to
data.
Constant-size Threshold Attribute based SignCryption for Cloud Applications
217

5.2 Complexity Assumptions
In, our constant size threshold attribute based sign-
cryption construction, we rely on the Computational
Diffie Hellman Assumption (CDH) and the aug-
mented multi-sequence of exponents computational
Diffie-Hellman ((
˜
l, ˜m,
˜
t)-aMSE-CDH), which was in-
troduced by Delerabl
´
ee et al. (Delerabl
´
ee et al., 2007;
Delerabl
´
ee and Pointcheval, 2008) in 2007. These as-
sumptions are defined as follows:
Definition 4. Computational Diffie Hellman As-
sumption (CDH) – Let G be a group of a prime or-
der p, and g is a generator of G. The CDH prob-
lem is, given the tuple of elements (g,g
a
,g
b
), where
{a,b}
R
←− Z
p
, there is no efficient probabilistic algo-
rithm A
CDH
that computes g
ab
.
Definition 5. (
˜
l, ˜m,
˜
t)-augmented multi-sequence of
exponents computational Diffie-Hellman ((
˜
l, ˜m,
˜
t)-
aMSE-CDH) – The (
˜
l, ˜m,
˜
t)-aMSE-CDH problem re-
lated to the group pair (G,G
T
) is to compute T =
e(g
0
,h
0
)
k· f (γ)
. It takes as input: the vector ~x
˜
l+ ˜m
=
(x
1
,·· · ,x
˜
l+ ˜m
)
>
whose components are pairwise dis-
tinct elements of Z
p
which define the polynomials f(X)
and g(X) as follows:
f (X) =
˜
l
∏
i=1
(X +x
i
); g(X) =
˜
l+ ˜m
∏
˜
l+1
(X +x
i
) (1)
where the values x
i
are random and pairwise distinct
of Z
∗
p
, and the values:
g
0
,g
γ
0
,·· · ,g
γ
˜
l+
˜
t−2
0
,g
k·γ· f (γ)
0
g
ωγ
0
,·· · ,g
ωγ
˜
l+
˜
t−2
0
g
α
0
,g
αγ
0
,·· · ,g
αγ
˜
l+
˜
t
0
h
0
,h
γ
0
,·· · ,h
γ
˜m−2
0
h
ω
0
,h
ωγ
0
,·· · ,h
ωγ
˜m−1
0
h
α
0
,h
αγ
0
,·· · ,h
αγ
2( ˜m−
˜
t)+3
0
Where k,α,γ, ω are unknown random elements of
Z
p
and g
0
and h
0
are generators of G. We can solve
the problem if we get an output b ∈ {0,1} where b = 1
if T = e(g
0
,h
0
)
k· f (γ)
or b = 0 when T is a random
value from G
T
.
5.3 Aggregate Algorithm
Our scheme construction relies on the aggregate algo-
rithm Aggreg introduced by Delerablee et al. (Deler-
abl
´
ee et al., 2007; Delerabl
´
ee and Pointcheval, 2008).
This algorithm is explained in the following descrip-
tion:
Let us consider a list of values {g
r
γ+x
i
,x
i
}
1≤i≤n
,
where r,γ ∈ Z
∗
p
and x
1
,·· · ,x
n
are pairwise different.
Then , the algorithm proceeds as follows:
Aggreg({g
r
γ+x
i
,x
i
}
1≤i≤n
) = g
r
∏
n
i=1
(γ+x
i
)
Concretely, the Aggreg algorithm defines P
0,m
=
g
r
γ+x
m
for each m ∈ {1, ·· · ,n}. Afterwards, the al-
gorithm computes sequentially P
i,m
for i = 1 · ··n − 1
and m = i +1, ··· ,n using the induction:
P
i,m
= (
P
i−1,i
P
i−1,m
)
1
x
m
−x
i
(2)
Then, we get P
i,m
= g
r
(γ+x
m
)
∏
i
k=1
(γ+x
k
)
where 1 ≤ i ≤
m ≤ n.
Therefore, since the elements x
1
,·· · ,x
n
are pair-
wise different (Herranz et al., 2010; Attrapadung
et al., 2012) and using the equation 2, we can com-
pute P
i,m
for i = 1 · ··n − 1 and m = i + 1 · ·· n such as
P
n,n−1
= g
r
∏
n
i=1
(γ+x
i
)
5.4 Concrete Construction
Our construction is based on the four algorithms de-
fined as follows:
• Setup – the trusted authority defines a bilinear
group triple (G
1
,G
2
,G) of prime order p, a bi-
linear map ˆe : G
1
× G
2
→ G and a collusion re-
sistant hash function H : {0, 1}
∗
→ Z
p
. In ad-
dition, It specifies an encoding function τ such
that τ : U → (Z/pZ)
∗
, where |U| = n and U is
an attribute universe supported by the trusted au-
thority. For each attribute a ∈ U, the encoded
attribute values τ(a) = x are pairwise different.
Then, the Setup algorithm selects two generators
g and h of G
1
and G
2
, respectively. It also chooses
a set of pairwise different elements of (Z/pZ)
∗
,
D
i
= {d
1
,·· · ,d
i
} where i ≤ n − 1. Finally, it out-
puts the global public parameters PP defined as
follows:
PP = {G
1
,G
2
,G, ˆe,{h
αγ
i
}
{i=0,···,2n−1}
,D
i
,τ,u =
g
α·γ
,e(g
α
,h),H }
We note that the master key of the trusted author-
ity is referred to as msk = (g,α,γ) where α,γ are
two random from values (Z/pZ)
∗
.
• KeyGen – for any subset A
i
⊂ U of attributes as-
sociated with a user E
i
, the algorithm chooses a
random value r
E
i
∈ (Z/pZ)
∗
and computes the re-
lated secret key as follows:
SECRYPT 2017 - 14th International Conference on Security and Cryptography
218

sk
E
i
= ({g
r
E
i
γ+τ(a)
}
a∈A
i
,{h
r
E
i
γ
i
}
i=0,···,m−2
,h
r
E
i
−1
γ
)
= (sk
E
i
1
,sk
E
i
2
,sk
E
i
3
)
• SignCrypt – let (t,S) be the access policy where
S ⊂ U is an attribute set of size s = |S| such that
1 ≤ t ≤ |S| and let A
S
be the sub-set of attribute set
related to the signcrypting entity E
S
where |A
S
∩
S| = t.
To signcrypt the message M with respect to (t, S),
E
S
uses his secret key and the aggregate algorithm
Aggreg introduced in the Section 5.3 and com-
putes T
1
such as:
T
1
= Aggreg({g
r
E
S
γ+τ(a)
,τ(a)}
a∈A
S
) = g
r
E
S
∏
a∈A
S
(γ+τ(a))
Then, E
S
defines the polynomial P
(A
S
,S)
(γ) such
as:
P
(A
S
,S)
(γ) =
1
γ
(
∏
a∈S∪D
n+t−1−s
\A
S
(γ + τ(a)) − B
1
)
Where B
1
=
∏
a∈S∪D
n+t−1−s
\A
S
τ(a)
Afterwards, using the element sk
E
i
2
, the sign-
crypting entity derives B
2
as follows:
B
2
= h
r
E
S
P
(A
S
,S)
(γ)/B
1
In the sequel, E
S
computes H (M) and generates
the signature σ = (σ
1
,σ
2
,σ
3
) defined as:
σ
1
= T
1
· g
H (M)
∏
a∈A
S
(γ+τ(a))
σ
2
= sk
E
S
3
· B
2
· h
H (M)P
(A
S
,S)
(γ)/B
1
σ
3
= h
α·H (M)
Finally, E
S
picks a random κ ∈ (Z/pZ)
∗
and
computes C
1
, C
2
and C
3
. Note that the elements
C
1
, C
2
are computed using the public parameters
u and ˆe(g,h)
α
. Moreover, the set {h
αγ
i
}
i=0,···,2n−1
is used to compute C
3
with respect to the equation
1. C
1
, C
2
and C
3
are detailed as follows:
C
1
= (g
α·γ
)
−κ
C
2
= h
κα·
∏
a∈S
(γ+τ(a))
∏
d∈D
n+t−1−s
(γ+d)
C
3
= ˆe(g, h)
α·κ
· ˆe(g,h)
α·H (M)
· M = K · M
Finally, the signcrypting entity out-
puts the signcryption of the message M,
Σ = (C
1
,C
2
,C
3
,σ
1
,σ
2
,σ
3
,P
(A
S
,S)
(γ),B
1
).
• UnsignCrypt – any user E
U
having a set of at-
tributes A
U
where |A
U
∩ S| = t can verify and de-
crypt the signcrypted message under the access
policy (t, S).
First, to verify that the received message has been
correctly signed by E
S
, E
U
has to check the fol-
lowing equality:
s = ˆe(u
−1
,σ
2
) · ˆe(σ
1
B
1
1
,h
α·
∏
a∈S∪D
n+t−1−s
(γ+τ(a))
)
· ˆe(g
α
,h)
H (M)
= ˆe(g
α
,h)
where U
1
=
∏
a∈S∪D
n+t−1−s
\A
S
γ+τ(a)
τ(a)
.
Then, for all a ∈ A
U
, E
U
has to aggregate the re-
quired attributes such as:
A
2
= Aggreg({g
r
E
U
γ+τ(a)
,τ(a)}
a∈A
U
) = g
r
E
U
∏
a∈A
U
(γ+τ(a))
(3)
Afterwards, E
U
uses the aggregated secret key A
2
and the sk
E
U
2
key element to compute:
[ ˆe(C
1
,h
r
E
U
P
(A
S
,S)
(γ)
)· ˆe(A
2
,C
2
)]
1
B
1
= e(g,h)
(κ·α)·r
E
U
Then, the unsigncrypting entity E
U
deduces the
deciphering key K such as:
K =
ˆe(C
1
,sk
E
U
2
) · ˆe(g,σ
3
)
ˆe(g,h)
κ·r
E
U
·α
= ˆe(g, h)
α·(H (M)+κ)
= ˆe(g,h)
α·κ
· ˆe(g,h)
α·H (M)
Finally, E
U
recovers the message by computing
M =
C
3
K
.
Then, to verify the authenticity of the signature
of the signcrypting entity, the user E
U
uses the
retrieved message M to compute H (M). After-
wards, E
U
verifies that σ
3
= h
α·H (M)
6 SECURITY ANALYSIS
In this section, we prove the correctness and the se-
curity of our construction with respect to the security
model as defined in section 4.2.
6.1 Correctness
Any user E
U
having a set of attributes A
U
where
|A
U
∩ S| = t can verify and decrypt the signcrypted
message under the policy (t, S).
In the following, we denote by s, the
Constant-size Threshold Attribute based SignCryption for Cloud Applications
219

quantity ˆe(u
−1
,σ
2
) · ˆe(g
α
,h)
H (M)·(1−U
1
−
1
U
1
)
·
ˆe(σ
1
B
1
1
,h
α·
∏
a∈S∪D
n+t−1−s
(γ+τ(a))
), where U
1
=
∏
a∈S∪D
n+t−1−s
\A
S
γ+τ(a)
τ(a)
.
First, E
U
has to verify that E
S
has correctly signed
the message M, such as:
s = ˆe(g
−α·γ
,h
r
E
S
−1
γ
· h
(r
E
S
+H (M))·P
(A
S
,S)
(γ)
∏
a∈S∪D
n+t−1−s
\A
S
(τ(a)+γ)
)
· ˆe(g
α
,h)
H (M)·(1−U
1
−
1
U
1
)
·
ˆe(g
(r
E
S
+H (M))
∏
a∈A
S
(γ+τ(a))·
∏
a∈S∪D
n+t−1−s
\A
S
τ(a)
,
h
α·
∏
a∈S∪D
n+t−1−s
(τ(a)+γ)
)
= ˆe(g
−α·γ
,h
r
E
S
−1
γ
h
r
E
S
·
P
(A
S
,S)
(γ)
∏
a∈S∪D
n+t−1−s
\A
S
(τ(a)+γ)
)
· ˆe(g
−α·γ
,h
H (M)·
P
(A
S
,S)
(γ)
∏
a∈S∪D
n+t−1−s
\A
S
τ(a)
)
· ˆe(g
α
,h)
H (M)
· ˆe(g
α
,h)
−H (M)·U
1
· ˆe(g
α
,h)
−H (M)
U
1
· ˆe(g
r
E
S
∏
a∈A
S
(γ+τ(a))·
∏
a∈S∪D
n+t−1−s
\A
S
τ(a)
,
h
α·
∏
a∈S∪D
n+t−1−s
(τ(a)+γ)
) ·
ˆe(g
H (M)
∏
a∈A
S
(γ+τ(a))·
∏
a∈S∪D
n+t−1−s
\A
S
τ(a)
,
h
α·
∏
a∈S∪D
n+t−1−s
(τ(a)+γ)
)
= ˆe(g
α
,h)
H (M)
· ˆe(g
α
,h)
−H (M)·U
1
· ˆe(g
α
,h)
−H (M)
U
1
ˆe(g
α
,h) · ˆe(g
α
,h)
H (M)·
∏
a∈S∪D
n+t−1−s
\A
S
γ+τ(a)
τ(a)
· ˆe(g
α
,h)
−H (M)·
∏
a∈S∪D
n+t−1−s
\A
S
τ(a)
τ(a)
· ˆe(g
α
,h)
H (M)·
∏
a∈S∪D
n+t−1−s
(γ+τ(a))
∏
a∈A
S
(γ+τ(a))·
∏
a∈S∪D
n+t−1−s
\A
S
τ(a)
= ˆe(g
α
,h)
In the sequel, E
U
aggregates his secret keys to ob-
tain A
2
, as defined in Equation 3, uses the sk
E
U
2
key
element and computes:
ˆe(C
1
,h
r
E
U
P
(A
U
,S)
(γ)
) · ˆe(A
2
,C
2
) (4)
= e(g,h)
κ·α·r
E
U
∏
a∈S∪D
n+t−1−s
\A
U
τ(a)
and
ˆe(C
1
,h
r
E
U
−1
γ
) = ˆe(g, h)
−κ·r
E
U
·α
· ˆe(g,h)
κ·α
(5)
Afterwards, to derive the deciphering key K, the
user E
U
executes Equations 6, 7 and 8 defined as fol-
lows:
ˆe(g,h)
κ·r
E
U
·α
= ( ˆe(C
1
,h
r
E
U
P
(A
U
,S)
(γ)
))· (6)
ˆe(A
2
,C
2
))
1
∏
a∈S∪D
n+t−1−s
\A
U
τ(a)
ˆe(g,h)
κ·α
= ˆe(C
1
,h
r
E
U
−1
γ
) ˆe(g, h)
κ·r
E
U
·α
(7)
ˆe(g,σ
3
) = ˆe(g, h
α·H (M)
) = ˆe(g, h)
α·H (M)
(8)
Finally, the user can retrieve the message:
M =
C
3
ˆe(g,h)
α·(H (M)+κ)
=
C
3
K
(9)
Then, he computes H (M), using the retrieved mes-
sage M, in order to verify that the received σ
3
is equal
to h
α·H (M)
.
6.2 Confidentiality
For the security game against the confidentiality prop-
erty introduced in Section 4.2.1, the adversary A
tries to distinguish between two signcrypted messages
generated using the signcryption scheme. In other
words, the adversary A tries to solve the aMSE −
CDH problem using a challenging algorithm B.
In a first phase, the adversary A sets a set of
signcryption attributes S
∗
. Then, the algorithm
B generates and publishes the public parameters.
In the second phase, the adversary A tries to
gain knowledge about the unsigncryption process
by requesting the execution of the KeyGen and
UnsignCrypt algorithms. Thanks to the hardness
of the aMSE − CDH problem, the adversary A
cannot recognize the secret values such as r
i
,γ used
to generate the users’ secret keys. The Challenge
Phase consists of choosing two messages by the
adversary and sending them to the algorithm B.
Then, B randomly chooses a message, signcrypts
it and returns it to the adversary. A tries to guess
the original message being signcrypted. However,
with respect to the hardness of the aMSE − CDH
problem (Definition 5), the adversary is not able to
guess the message even if he might after seeing the
challenge ciphertext. Note that the adversary may
not request decryption of the challenge message itself.
In the following detailed proof, we prove that
our scheme is IND-CCA2 secure assuming that the
aMSE −CDH problem is hard to solve with respect
to Theorem 1.
Theorem 1. Let ξ be an integer. For any adversary A
against the IND-CCA2 security of our attribute-based
signcryption scheme, for a universe of m attributes
U, and a challenge pair (t
∗
,S
∗
) with s = |S
∗
|, there
exists a solver B of the (
˜
l, ˜m,
˜
t)-aMSE-CDH problem,
for
˜
l = m − s, ˜m = m + t − s and
˜
t = t + 1, such that
Pr[Exp
B
aMSE−CDH
(1
ξ
)] ≥
1
2
Pr[Exp
A
con f
(1
ξ
)].
Proof. We consider an algorithm B that uses the ad-
versary A as a black-box and that solves the (
˜
l, ˜m,
˜
t)-
aMSE-CDH problem.
SECRYPT 2017 - 14th International Conference on Security and Cryptography
220

Let I( ~x
2m+t−1−s
,κ,µ, α,γ,ω,T ) be the input of
the algorithm B where the components of the vector
~x
2m+t−1−s
= (x
1
,·· · ,x
2m+t−1−s
) are pairwise distinct
elements of (Z/pZ)
∗
and let define the polynomials
f (X) and g(X) as detailed in Definition 5. First, B
chooses a universe of attributes U = {a
1
,·· · ,a
m
}.
Then, the adversary A defines a set S
∗
⊂ U where
|S| = s and a threshold t
∗
such that 1 ≤ t
∗
≤ s. We
assume that S
∗
= {a
m−s+1
,·· · ,a
m
} ⊂ U. We denote
by A
A
the subset A ∩ S
∗
, for any subset of attributes
A.
Setup – the algorithm B sets τ(a
i
) = x
i
for i =
1,·· · ,m as the encoding function of the attributes.
Notice that the encoding of the first m − s elements
are the opposite of the roots of f (X), and the en-
coding of the attributes in S
∗
are the opposite of
some roots of g(X) (Delerabl
´
ee and Pointcheval,
2008). Then, B defines the values corresponding to
the dummy attributes D = {d
1
,·· · ,d
m−1
} as d
j
=
x
m+ j
if j = 1,· ·· , m + t − 1 − s. For j = m + t −
s,·· · ,m − 1, where the d
j
values are selected at ran-
dom in (Z/pZ)
∗
so that the elements of the sub-
set {x
1
,·· · ,x
2m+t−1−s
,d
m+t−s
,·· · ,d
j−1
} are pairwise
distinct. The algorithm B defines g = g
0
f (γ)
which
can be computed using f . To complete the Setup
phase, the algorithm B sets h = h
0
and computes:
• u = g
α·γ
= g
0
α·γ· f (γ)
can be computed since
X f (X) is a polynomial of degree
˜
l + 1. In fact,
the quantity αγ f (γ) is a linear combination of
αγ,·· · ,αγ
˜
l+1
where its coefficients are known to
B.
• v = ˆe(g,h)
α
= ˆe(g
0
α· f (γ)
,h
0
), where g
α
is com-
puted based on Equation 5.
The algorithm B derives the values {h
αγ
i
}
i=0,···,2m−1
from the input set I . Finally, the algorithm B returns
the public parameters to the adversary A.
Unsigncryption Query Phase 1 – during this
phase, B and A proceed as follows:
• KeyGen – for each KeyGen query i, A requests
the key extraction for a subset A
A
from B,
where |A
A
| < t
i
. To compute the queried secret
keys, B chooses r
i
= (ωy
i
γ + 1)Q
i
(γ), where
y
i
is randomly picked in (Z/pZ)
∗
, and B de-
fines the polynomial Q
i
(X) as Q
i
(γ) = 1 when
|A
A
| = 0, or Q
i
(X) = λ
i
·
∏
a∈A
A
(X + τ(a)) where
λ
i
= (
∏
a∈A
A
τ(a))
−1
.
Then, the algorithm B can compute
the components of the secret key tuple
sk
A
= ({g
r
i
γ+τ(a)
}
a∈A
A
,{h
r
i
γ
k
}
k=0,···,m−2
,h
r
i
−1
γ
)
for a set of attributes A
A
= {a
i
1
,·· · ,a
i
n
} ⊂ U,
queried at session i, as follows:
– for each a
k
∈ A
A
, the algorithm B com-
putes Q
a
k
(γ) =
Q
i
(γ)
(γ+τ(a
k
))
= λ
i
·
∏
˜a
k
∈A
A
, ˜a
k
6=a
k
(γ+
τ( ˜a
k
)). Then, B calculates the first secret
key element sk
A
1
= {g
r
i
γ+τ(a
k
)
}
a
k
∈A
A
defined as
sk
A
1
= {g
0
f (γ)ωy
i
Q
a
k
(γ)
· g
0
f (γ)Q
a
k
(γ)
}
a
k
∈A
A
.
– for each a
k
∈ A \ A
A
, the algorithm B de-
fines f
a
k
(X) =
f (X)
(X+τ(a
k
))
. Then, B computes
the first secret key element such as sk
A
1
=
{g
r
i
γ+τ(a
k
)
}
a
k
∈A
A
= {g
0
f
a
k
(γ)ωy
i
Q
i
(γ)
· g
0
f
a
k
(γ)Q
i
(γ)
}
a
k
∈A
A
.
– B calculates the second item of the secret
key sk
A
2
= {h
r
i
γ
j
}
j=0,··· ,m−2
such as h
r
i
γ
j
=
h
ωy
i
γ
j+1
Q
i
(γ)
· h
γ
j
Q
i
(γ)
.
– finally, B computes the third secret key element
such as sk
A
3
= h
r
i
−1
γ
= h
ωy
i
Q
i
(γ)
· h
Q
i
(γ)−1
γ
.
• UnsignCrypt – the adversary A can adaptively
requests the unsigncryption queries while con-
sidering the signcryption attribute set A
U
. The
algorithm B executes the KeyGen to generate
the secret key sk
B
= KeyGen(PP,msk, A
U
)
and finally, B answers by running the
Unsigncrypt(PP,sk
B
,A
U
,(t
i
,S
∗
),Σ
i
) algo-
rithm and forwards M
i
to the adversary.
Challenge Phase – the adversary A chooses the
two equal length plaintext messages M
0
∗
and M
1
∗
and
sends them to B, who flips a coin b ∈ {0,1}. Then,
B sets C
∗
3
= T · M
b
. Afterwards, B chooses a random
value for the encryption as κ
0
= κ/α and computes
H (M
b
). Then, B sets C
∗
2
= h
κ
0
·g(γ)
0
, C
∗
1
= (g
κ
0
·γ· f (γ)
0
)
−1
and σ
∗
3
= h
0
H (M
b
)
.
Unsigncryption Query Phase 2 – the queries are
executed as in the Unsigncryption Query Phase 1.
Guess – the adversary A outputs a bit b
0
. If b
0
= b,
B answers 1 as the solution to the given instance of
the aMSE-CDH problem with respect to Definition
5, meaning that T = ˆe(g
0
,h
0
)
(κ+H (M
b
))
· f (γ). Other-
wise, B answers 0, meaning that T is a random ele-
ment. The advantage of the algorithm B is as follows:
Pr[Exp
aMSE−CDH
B
(1
ξ
)] = |Pr[B(I( ~x
2m+t−1−s
,κ,µ,
α,γ,ω, T) = 1|real]
−Pr[B(I( ~x
2m+t−1−s
,κ,µ,
α,γ,ω, T) = 1|random]|
= |Pr[b = b
0
|real]
−Pr[b = b
0
|random]|
Constant-size Threshold Attribute based SignCryption for Cloud Applications
221

When the event real occurs, then A is playing
a real attack and therefore |Pr[b = b
0
|real] −
1
2
]| =
1
2
Exp
A
con f
(1
ξ
). During the random event, the view
of A is completely independent of the bit b; in this
case, the probability Pr[b = b
0
] is equal to 1/2. Then,
we obtain:
Pr[Exp
B
aMSE−CDH
(1
ξ
)] ≥
1
2
Pr[Exp
A
con f
(1
ξ
)]
Thus, for all PPT adversaries, the advantage of
the adversary A is negligeable. Then, our proposed
t − ABSC scheme satisfies the confidentiality prop-
erty.
6.3 Unforgeability
In the security game defined in Section 4.2.2, the ad-
versary A tries to forge a valid signature based on
the use of an algorithm B who is able to solve the
aMSE −CDH problem.
Thus, the adversary A chooses a set of signcryp-
tion attributes S
∗
and a threshold t, in the Setup phase.
Afterwards, the adversary A requests the execution of
the KeyGen queries while changing the threshold t
i
.
Moreover, the adversary A asks for the signcryption
of a message M under different signcryption attribute
sets and threshold values. By executing this Sign-
crypt Query Phase, the adversary tries to get infor-
mation about the secret values included in the KeyGen
and SignCrypt algorithms.
Afterwards, the adversary A tries to generate a
valid signcryption with respect to the challenge pol-
icy (t
∗
,S∗). Thus, the adversary A has to solve the
aMSE −CDH problem with respect to the Definition
5 for proving that he has the required attributes to sat-
isfy the (t
∗
,S
∗
) access policy. Moreover, thanks to the
random values added to the generated signature, the
adversary A has to solve the CDH problem with re-
spect to the Definition 4.
However, thanks to the hardness of to the aMSE −
CDH problem and the CDH problem, the adversary
cannot learn information about the secret values used
in the key generation and the signcryption process.
In the following, we prove that our construction
is unforgeable against chosen message attack with re-
spect to Theorem 2.
Theorem 2. The scheme is adaptive-message un-
forgeable under chosen message attacks for a uni-
verse U of m attributes, and a challenge pair (t
∗
,S
∗
)
with s = |S
∗
|, there exists a solver B of the ((
˜
l, ˜m,
˜
t)-
aMSE-CDH problem, for
˜
l = m − s, ˜m = m + t − s
and
˜
t = t + 1, such that Pr[Exp
B
aMSE−CDH
(1
ξ
)] ≥
Pr[Exp
A
un f
(1
ξ
) = 1] assuming that the (
˜
l, ˜m,
˜
t)-
aMSE-CDH problem holds.
Proof. We consider an algorithm B that uses the ad-
versary A as a black-box and that solves the (
˜
l, ˜m,
˜
t)-
aMSE-CDH problem.
Let I( ~x
2m+t−1−s
,κ,µ, α,γ,ω,T ) be the input of
the algorithm B where the components of the vec-
tor ~x
2m+t−1−s
= (x
1
,·· · ,x
2m+t−1−s
) are pairwise dis-
tinct elements of (Z/pZ)
∗
and define the polynomi-
als f (X) and g(X) as detailed in Definition 5. First,
B chooses a universe of attributes U = {a
1
,·· · ,a
m
}.
Then, the adversary A chooses a set S
∗
⊂ U where
|S| = s and a threshold t
∗
such that 1 ≤ t
∗
≤ s. We
assume that S
∗
= {a
m−s+1
,·· · ,a
m
} ⊂ U. We denote
by A
A
the subset A∩S
∗
, for any subset of attributes A.
We consider the same setting for the Setup phase
as detailed in the Exp
con f
security game. For the
Signcrypt Query Phase, the adversary A requests,
as many times as he wants, the key extraction oracle
KeyGen and the signcryption oracle SignCrypt. For
each KeyGen query i, A requests the key extraction
for a subset A
A
from B, as detailed in the Exp
con f
se-
curity game.
Afterwards, the adversary A can adap-
tively request a SignCrypt query i while
considering the signcryption attribute set A
U
and a message M
i
. The algorithm B exe-
cutes the KeyGen to generate the secret key
sk
B
= KeyGen(PP,msk, A
U
) and finally, B answers
by running the signCrypt(PP,sk
B
,A
U
,(t
i
,S
∗
),M
i
)
algorithm and forwards Σ
i
to the adversary.
The algorithm B sets Q
i
(γ)/λ
i
=
∏
a∈A
U
(γ+ τ(a))
and computes:
• σ
1,i
= g
0
(ωy
i
γ+1) f (γ)λ
i
· g
0
f (γ)
λ
i
H (M
i
)
Q
i
(γ)
.
• σ
2,i
= h
ωy
i
Q
i
(γ)
· h
Q
i
(γ)−1
γ
· h
(ωy
i
γ+1)Q
i
(γ)·P
(A
U
,S
∗
)
(γ)
∏
a∈S
∗
∪D
n+t−1−s
\A
U
τ(a)
·
h
H (M
i
)P
(A
U
,S
∗
)
(γ)
∏
a∈S
∗
∪D
n+t−1−s
\A
U
τ(a)
.
• σ
3,i
= h
α·H (M
i
)
.
• finally, B computes C
1,i
, C
2,i
and C
3,i
, as detailed
in the Exp
con f
security game.
Forgery Phase – during this phase, A outputs a
signcrypted message Σ
∗
with respect to the thresh-
old challenge policy (t
∗
,S
∗
). For this purpose, A can
compute C
∗
1
, C
∗
2
, C
∗
3
and σ
∗
3
, based on public parame-
ters and the selected random κ
∗
and H (M
i
). Finally,
A has to compute valid σ
∗
1
and σ
∗
2
to win the un-
forgeability security game. Hence, A has to solve the
aMSE-CDH problem with respect to Definition 5 for
proving that he has the required attributes to satisfy
the (t
∗
,S
∗
) access policy. Similarly, the adversary A
has to solve the CDH problem with respect to Defini-
tion 4. Thus, A has the same advantage as the Exp
con f
security game.
SECRYPT 2017 - 14th International Conference on Security and Cryptography
222

Thus, for all PPT adversaries, the advantage of the
adversary A is negligible. Then, our proposed t −
ABSC is unforgeable against chosen-message attack.
6.4 Privacy
The privacy game begins when the challenger C exe-
cutes the Setup algorithm to generate the public pa-
rameters. Then, the challenger C sends the public pa-
rameters to the adversary A. Afterwards, the adver-
sary A chooses two attribute sets A
S
1
and A
S
1
satisfy-
ing the threshold access policy (t, S) and sends them
to the challenger C. The challenger generates the pri-
vate keys related to the sets of attribute A
S
1
and A
S
2
as
follows:
sk
E
C
1
= ({g
r
E
C
γ+τ(a)
}
a∈A
S
1
,{h
r
E
C
γ
i
}
i=0,···,m−2
,h
r
E
C
−1
γ
)
sk
E
C
2
= ({g
r
E
C
γ+τ(a)
}
a∈A
S
2
,{h
r
E
C
γ
i
}
i=0,···,m−2
,h
r
E
C
−1
γ
)
Moreover, the adversary A outputs a challenge
message M and asks the challenger C to generate the
signcryption of M using one of the private keys sk
E
C
1
or sk
E
C
2
. Thus, the challenger chooses a random bit
b ∈ {0,1}, and computes a signcryption Σ
b
by running
the algorithm SignCrypt(PP,sk
E
C
b
,sk
E
C
b
,(t, S),M).
Since |A
S
b
∩S| = t, the challenger can generate a valid
signcrytpion on the message M. Thus, to prove that
the scheme is private, we just have to prove that the
signcrypted message created using sk
E
C
1
or sk
E
C
2
are
identical.
Using the private key related to sk
E
C
b
, the gen-
erated signcryption Σ
b
= (C
1
,C
2
,C
3
,σ
1
,σ
2
,σ
3
) is
detailed as follows:
C
1
= (g
α·γ
)
−κ
C
2
= h
κα·
∏
a∈S
(γ+τ(a))
∏
d∈D
n+t−1−s
(γ+d)
C
3
= ˆe(g, h)
α·κ
· ˆe(g,h)
α·H (M)
· M = K · M
and
σ
1
= g
r
E
C
∏
a∈A
S
b
(γ+τ(a))
· g
H (M)
∏
a∈A
S
b
(γ+τ(a))
σ
2
= h
r
E
C
−1
γ
h
r
E
C
·P
(A
S
b
,S)
(γ)
∏
a∈S∪D
n+t−1−s
\A
S
b
τ(a)
· h
H (M)P
(A
S
b
,S)
(γ)
∏
a∈S∪D
n+t−1−s
\A
S
b
τ(a)
σ
3
= h
α·H (M)
While receiving the signcrypted message, the ad-
versary A verifies the signature, by computing:
s = ˆe(u
−1
,σ
2
) · ˆe(σ
1
B
1
1
,h
α·
∏
a∈S∪D
n+t−1−s
(γ+τ(a))
) ·
ˆe(g
α
,h)
H (M)·(1−U
1
−
1
U
1
)
= ˆe(g
α
,h)
Since |A
S
b
∩ S| = |A
S
1
∩ S| = |A
S
2
∩ S| = t, we
can prove that the signature generated using the set
of attributes A
S
1
( in other words, using the secret
key sk
E
C
1
) is similar to the signature generated using
the set of attributes A
S
2
( using the secret key sk
E
C
2
).
Hence, the challenger A cannot know the set of at-
tributes used to generate the signature with respect to
the hardness of the CDH problem (Definition 4).
Thus, our proposed attribute based signcryption
scheme is computationally private.
7 PERFORMANCES ANALYSIS
In this section, we present the computation and the
storage complexities of our proposed signcryption
scheme. In our analysis, we are interested in the com-
putations performed to execute the SignCrypt and
the UnsignCrypt algorithms as well as the size of
the generated signcrypted message (signcryption size)
and the size of the secret keys as introduced in Table
2. In the following, we denote by E
1
the exponen-
tiation cost in G
1
, E
T
the exponentiation cost in G
T
and τ
P
the computation cost of a pairing function ˆe.
Table 2 details the performance comparison of ABSC
schemes.
7.1 Storage Complexities
Our signcryption scheme consists of using a common
setup procedure to generate the public parameters and
the secret keys used to sign and encrypt the mes-
sage. Our proposal relies on the use of a single access
structure for both signature and encryption phases on
the signcryption procedure unlike other signcryption
schemes. Thus, the key size is equal to n +m where m
and n = |A| are the cardinals of the attributes’ universe
U and the set of the user’s attributes, respectively.
The proposal of Emura et al. (Emura et al., 2012)
consists of using two access structures. As such, it
uses two different secret keys’ sets related to the sig-
nature and the encryption procedures. The size of the
first part of the keys is equal to 2n
s
while the size of
the second part is equal to 2n
e
+ 1 where n
s
and n
e
are the sizes of the set of the signing attributes and the
size of the set of the encryption attributes of the user,
respectively. Similarly, Liu et al. (Liu et al., 2015)
use two access structures. So that, the sizes of the se-
cret keys are equal to n
s
+ 2 and n
e
+ 2 for signing
and encrypting, respectively. The proposal of Gagn
´
e
et al. (Gagne et al., 2010) also uses different access
structures for signature and encryption and consists
of using secret keys which their sizes are equal to
2n
s
and 3n
e
. Finally, Rao et al.(Rao and Dutta, 2014)
Constant-size Threshold Attribute based SignCryption for Cloud Applications
223
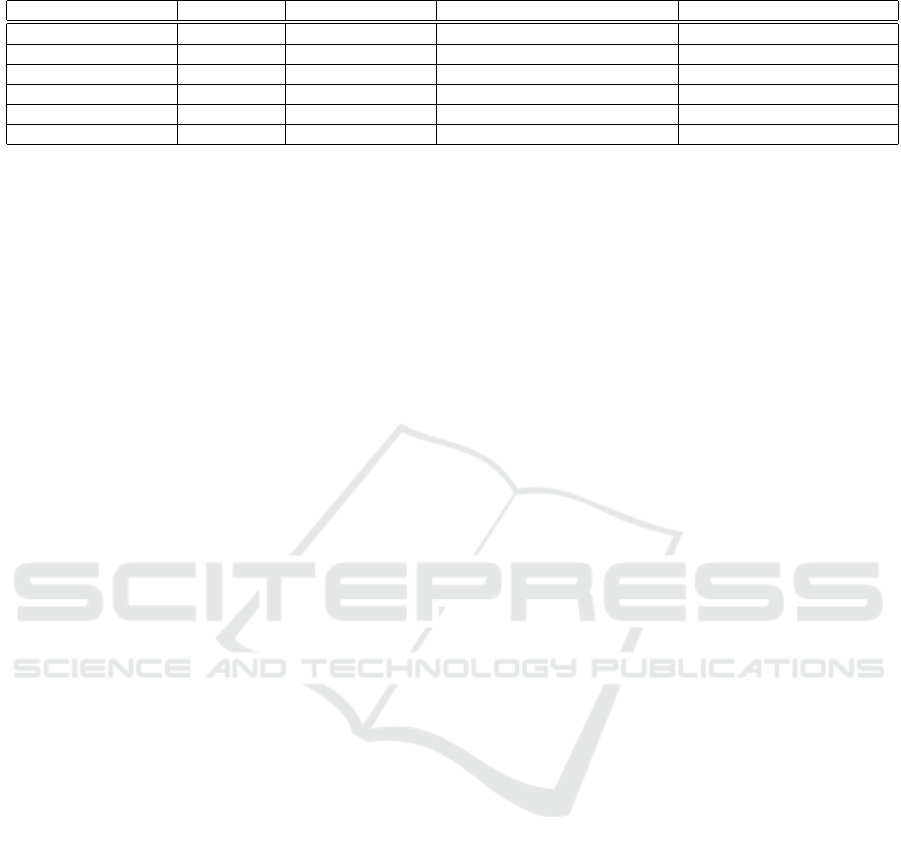
Table 2: Computation and Storage Costs of Attribute Based Signcryption Schemes.
Scheme Key size Signcryption size Signcrypt time Unsigncrypt time
(Emura et al., 2012) 2n
s
,2n
e
+ 1 2 + 5l
e
+ 2n
s
E
1
(10 + 4n
s
) + E
T
+ τ
p
τ
p
(3n
s
+ 2 +2n
e
+ 2m)
(Liu et al., 2015) n
s
+ 2, n
e
+ 2 4 + 2l
s
+ l
e
τ
p
+ E
T
+ E
1
(3 + l
e
+ 3l
s
) τ
p
(3n
s
+ 5) +2n
s
E
T
+ 2n
s
E
1
(Gagne et al., 2010) 3n
e
,2n
s
O(M) + 4 + n
e
+ n
s
E
1
(2O(M) + mn
e
+ 4n
e
+ 3 +n
s
) 2E
1
+ τ
p
(2t + 2 +n
s
) + tE
T
+
(Rao and Dutta, 2014) m +l
s
,m + l
e
8 E
1
(10 + l
e
+ 3l
s
+ n
s
) 6τ
p
+ E
1
(n
e
+ 3l
e
)
(Rao and Dutta, 2016) m +l
s
,m + l
e
8 E
1
(10 + l
e
+ 3l
s
+ n
s
) 6τ
p
+ E
1
(n
e
+ 3l
e
)
Our scheme n + m 8 E
1
(6 + t) + 2E
T
E
1
(5 + t) + 9τ
p
+ 4E
T
proposal consists of a key-policy attribute based sign-
cryption scheme which relies on the use of different
access structures for signing and encrypting. Thus,
the sizes of the secret keys are equal to m + l
s
and
m + l
e
where l
s
and l
e
denote the sizes of the signing
policy and the encryption policy, respectively.
Emura et al. (Emura et al., 2012) propose a CP-ABSC
scheme where the size of the signcrypted message is
equal to 2 + 5l
e
+ 2n
s
. Thus, it increases linearly with
both the number of attributes introduced in the en-
cryption access policy l
e
and the number of the sign-
ing attributes of the user n
s
. Moreover, the proposal
of Liu et al. (Liu et al., 2015) introduces a signcryp-
tion scheme where the size of the signcrypted mes-
sage depends on the number of attributes used on both
encryption and signature policies (l
s
,l
e
). For instance,
this scheme outputs a signrypted message whose size
is 4+ 2l
s
+l
e
. The threshold attribute based signcryp-
tion scheme proposed by Gagn
´
e et al. outputs a sign-
crypted message’s size depending on both the number
of the user’s attributes related to signing and decrypt-
ing, n
s
and n
e
, respectively. The size of the signrypted
message is equal to O(M) + 4 + n
e
+ n
s
. The pro-
posal of Rao et al.(Rao and Dutta, 2014) is the first
constant size key-policy attribute based signcryption
scheme. Indeed, the size of the signcrypted message
is equal to 8 and it is independent from the number
of attributes involved in the access policy. Similarly,
our t-ABSC proposal is the first threshold ciphertext-
policy attribute based signcryption scheme that out-
puts a constant signcrypted message’s size equal to 8,
where the size of the signcrypted message does not
depend on the size of the access policy.
Consequently, our proposal is the only threshold
ciphertext-policy attribute based signcryption that
uses a common setup based on a single access
policy for encryption and signing. Although, our
scheme presents less expressiveness compared to
other schemes, it presents interesting performances
especially related to the key size and the constant size
of the encrypted message.
7.2 Computation Complexities
In (Emura et al., 2012), Emura et al. proposal con-
sists of computing (10 + 4n
s
) exponentiations in G
1
,
one exponentiation in G
T
and one pairing function
while performing the signcryption algorithm. More-
over, the unsigncryption algorithm computes (3n
s
+
2 + 2n
e
+ 2m) pairing function. Recently, Liu et al.
(Liu et al., 2015) executes (3 + l
e
+ 3l
s
) exponentia-
tions in G
1
, one exponentiation in G
T
and one pair-
ing function during the signcryption procedure. Both
the proposed schemes by Rao et al. (Rao and Dutta,
2014; Rao and Dutta, 2016) introduce an attribute
based signcryption scheme where the signcryption
and unsigncryption processing overheads are equal
to E
1
(10 + l
e
+ 3l
s
+ n
s
) and 6τ
p
+ E
1
(n
e
+ 3l
e
), re-
spectively. The threshold attribute based signcryp-
tion scheme proposed by Gagn
´
e et al. introduces a
signcryption mechanism where the signcrypting con-
ists of performing (2O(M) + mn
e
+ 4n
e
+ 3 + n
s
) ex-
ponentiation in G
1
, where O(M) is the size of the
plaitext message. Moreover, the unsigncryption al-
gorithm consists of (2t + 2 + n
s
) pairing function, 2
exponentiations in G
1
and t exponentiations in G
T
.
Finally, our proposed t-ABSC scheme consists of per-
forming (6 +t) exponentiations in G
1
and 2 exponen-
tiations in G
T
in the signcryption phase. In addition,
it computes (5 +t) exponentiations in G
1
, 2 exponen-
tiations in G
T
and 9 pairing function to perform the
unsigncryption algorithm. It is noteworthy that the
computation overheads of the signcryption and un-
signcryption procedures introduced in our threshold
attribute based signcryption scheme only depends on
the threshold value t.
Our proposed scheme presents interesting computa-
tion costs compared to other signcryption schemes
thanks to the use of common setup phase to gener-
ate public parameters and the use of the same access
policy for both signature and encryption phases. For
instance, our proposal consists of performing a fixed
number of pairing functions whose computation over-
head are heavy compared to the exponentiation oper-
ations.
SECRYPT 2017 - 14th International Conference on Security and Cryptography
224

8 CONCLUSIONS
The widespread use of cloud data storage and the
attractive properties offered by the attribute based
mechanisms lead us to combine them in order to en-
sure data security and user’s privacy. In this paper, we
have proposed a novel threshold attribute based sign-
cryption (t-ABSC) scheme ensuring flexible access
control, data confidentiality, user’s privacy as well as
data origin authentication with anonymity. Moreover,
the size of signcrypted messages does not depend on
the number of attributes involved in the access pol-
icy, which makes our t-ABSC scheme more suitable
for bandwidth-limited applications. Finally, our con-
struction is proven to ensure strong security properties
in the random oracle model, namely confidentiality
against the chosen ciphertext attacks, unforgeability
against chosen message attacks and privacy preserva-
tion, based on formal security games.
REFERENCES
Attrapadung, N., Herranz, J., Laguillaumie, F., Libert, B.,
De Panafieu, E., and R
`
afols, C. (2012). Attribute-
based encryption schemes with constant-size cipher-
texts. Theoretical Computer Science, 422:15–38.
Bacis, E., di Vimercati, S. D. C., Foresti, S., Paraboschi,
S., Rosa, M., and Samarati, P. (2016). Access con-
trol management for secure cloud storage. In Proc.
of the 12th International Conference on Security and
Privacy in Communication Networks (SecureComm
2016), Guangzhou, China.
Belguith, S., Jemai, A., and Attia, R. (2015). Enhancing
data security in cloud computing using a lightweight
cryptographic algorithm. In ICAS 2015 : The
Eleventh International Conference on Autonomic and
Autonomous Systems, pages 98–103. IARIA.
Belguith, S., Kaaniche, N., Jemai, A., Laurent, M., and At-
tia, R. (2016). Pabac: a privacy preserving attribute
based framework for fine grained access control in
clouds. In 13th IEEE International Conference on Se-
curity and Cryptography(Secrypt).
Bethencourt, J., Sahai, A., and Waters, B. (2007).
Ciphertext-policy attribute-based encryption. In IEEE
Symposium on Security and Privacy.
Carlin, A., Hammoudeh, M., and Aldabbas, O. (2015). In-
trusion detection and countermeasure of virtual cloud
systems-state of the art and current challenges. Inter-
national Journal of Advanced Computer Science and
Applications, 6(6):1–15.
Delerabl
´
ee, C., Paillier, P., and Pointcheval, D. (2007).
Fully collusion secure dynamic broadcast encryption
with constant-size ciphertexts or decryption keys. In
International Conference on Pairing-Based Cryptog-
raphy, pages 39–59. Springer.
Delerabl
´
ee, C. and Pointcheval, D. (2008). Dynamic thresh-
old public-key encryption. In Annual International
Cryptology Conference. Springer.
Dent, A. W., Fischlin, M., Manulis, M., Stam, M.,
and Schr
¨
oder, D. (2010). Confidential signatures
and deterministic signcryption. In Public Key
Cryptography–PKC.
di Vimercati, S. D. C., Foresti, S., and Samarati, P. (2014).
Selective and fine-grained access to data in the cloud.
In Secure Cloud Computing, pages 123–148. Springer.
di Vimercati, S. D. C., Livraga, G., Piuri, V., Samarati, P.,
and Soares, G. A. (2016). Supporting application re-
quirements in cloud-based iot information processing.
In Proc. of the International Conference on Internet of
Things and Big Data (IoTBD 2016), Rome, Italy.
Emura, K., Miyaji, A., and Rahman, M. S. (2012). Dynamic
attribute-based signcryption without random oracles.
International Journal of Applied Cryptography, 2(3).
Gagne, M., Narayan, S., and Safavi-Naini, R. (2010).
Threshold attribute-based signcryption. In Security
and Cryptography for Networks. Springer.
Haber, S. and Pinkas, B. (2001). Securely combining
public-key cryptosystems. In The 8th ACM confer-
ence on Computer and Communications Security.
Herranz, J., Laguillaumie, F., and R
`
afols, C. (2010). Con-
stant size ciphertexts in threshold attribute-based en-
cryption. In International Workshop on Public Key
Cryptography, pages 19–34. Springer.
Kaaniche, N., Laurent, M., and El Barbori, M. (2014).
Cloudasec: A novel publickey based framework to
handle data sharing security in clouds. In 11th IEEE
International Conference on Security and Cryptogra-
phy(Secrypt).
Libert, B. and Quisquater, J.-J. (2004). Efficient signcryp-
tion with key privacy from gap diffie-hellman groups.
In Public Key Cryptography–PKC.
Liu, J., Huang, X., and Liu, J. K. (2015). Secure shar-
ing of personal health records in cloud computing:
ciphertext-policy attribute-based signcryption. Future
Generation Computer Systems, 52.
Maji, H. K., Prabhakaran, M., and Rosulek, M. (2011).
Attribute-based signatures. In Topics in Cryptology–
CT-RSA 2011. Springer.
Rao, Y. S. and Dutta, R. (2014). Expressive bandwidth-
efficient attribute based signature and signcryption in
standard model. In Australasian Conference on Infor-
mation Security and Privacy. Springer.
Rao, Y. S. and Dutta, R. (2016). Efficient attribute-based
signature and signcryption realizing expressive access
structures. International Journal of Information Secu-
rity, 15(1):81–109.
Vasco, M. I. G., Hess, F., and Steinwandt, R. (2008). Com-
bined (identity-based) public key schemes. IACR
Cryptology ePrint Archive, 2008.
Waters, B. (2011). Ciphertext-policy attribute-based en-
cryption: An expressive, efficient, and provably se-
cure realization. In Public Key Cryptography–PKC.
Zheng, Y. (1997). Digital signcryption or how to achieve
cost (signature & encryption) ¡ cost (signature)+ cost
(encryption). In Advances in Cryptology, Crypto97.
Springer.
Constant-size Threshold Attribute based SignCryption for Cloud Applications
225
