
Join Multiple Channels and IEEE 802.15.4e TSCH Protocol Use Effects
on WSN Performance and Energy Efficiency
Diego V. Queiroz
1,2
, Ruan D. Gomes
5
, Cesar Benavente-Peces
2
, Iguatemi E. Fonseca
3
and Marcelo S. Alencar
1,4
1
Federal University of Campina Grande (UFCG), Brazil
2
Universidad Polit
´
ecnica de Madrid (UPM), Spain
3
Federal University of Paraiba (UFPB), Brazil
4
Federal University of Bahia (UFBA), Brazil
5
Federal Institute of Technology (IFPB), Brazil
Keywords:
TSCH, Contiki, Internet of Things, Orchestra, Minimal Schedule, Guard Time, Cooja, Frequency Hopping.
Abstract:
The goal of this paper is analysing the use of the IEEE 802.15.4e standard MAC layer protocol Time-Slotted
Channel Hopping (TSCH) mode in the context of Internet of Things (IoT) and Industrial IoT (IIoT) aimed
at reducing narrow-band interferences and the multi-path fading impact on available channels by using fre-
quency hopping, with network time synchronization to achieve low-power operation. In low disturbances
environments using several channels provides the diversity benefits. However, using several channels requires
channel scanning and switching leads to extra power consumption. It could be accepted in harsh environ-
ments (industrial), due to its influence on channels features, requiring more channels, and it is necessary to
continuously hop seeking for the best one to achieve the best performance. Several experiments have been
simulated and implemented in real testbeds the laboratory as first validation approach. The performance and
energy efficiency of the entire network is analysed for different scheduling methods, packet transmission rates,
number of used channels and guard time. The relevant conclusion showed in this investigation is that using
all the available channels of the standard is not required to achieve the best joint-results given that, regardless
the scheduling method used, considering a higher number channels requires a higher power consumption for
channels quality exploration and packet reception rate decreases.
1 INTRODUCTION
The term Internet of Things (IoT) has been used as
a reference to a new generation of pervasive comput-
ing, i.e., representing the ubiquity of computing re-
sources in people’s consumer products. Usual indus-
trial equipment and products such as cars, telephones,
televisions, refrigerators, and sensors can have built-
in connectivity to the Internet, with remote control,
personalization, automation as well as performance
analysis. This connection is possible through sensors
installed in devices and places from where data are
sent for analysis.
The concept of smart devices is closely linked to
IoT, and Industrial IoT (IIoT) is the application of
these technologies in industrial scenarios, such as in
smart buildings, smart factories, and smart grids (Xu
et al., 2014). IIoT is expanding the traditional au-
tomation systems and industrial informatics systems
into a broader context.
A Wireless Sensor Network (WSN) is a self-
configuring network of small sensor nodes (motes)
communicating among them using radio frequency.
They consist of a microprocessor with limited com-
putational power and memory, one or more antennas,
a power source and one or more sensors.
Among the roles the nodes can play, they can work
as a simple sensor that transmits the sensor readings
to a sink node (base station); as a sink node that re-
ceives the sensor readings from the other nodes and
forwards these readings to a gateway for further pro-
cessing/analysis; and as actuators, which are used to
control the environment, based on triggers revealed by
the sensor readings or by other inputs. In some cases,
the nodes not only sense the environment, but also
forward the data from/to other nodes until this infor-
Queiroz, D., Gomes, R., Benavente-Peces, C., Fonseca, I. and Alencar, M.
Join Multiple Channels and IEEE 802.15.4e TSCH Protocol Use Effects on WSN Performance and Energy Efficiency.
DOI: 10.5220/0008162300830090
In Proceedings of the 9th International Conference on Pervasive and Embedded Computing and Communication Systems (PECCS 2019), pages 83-90
ISBN: 978-989-758-385-8
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
83
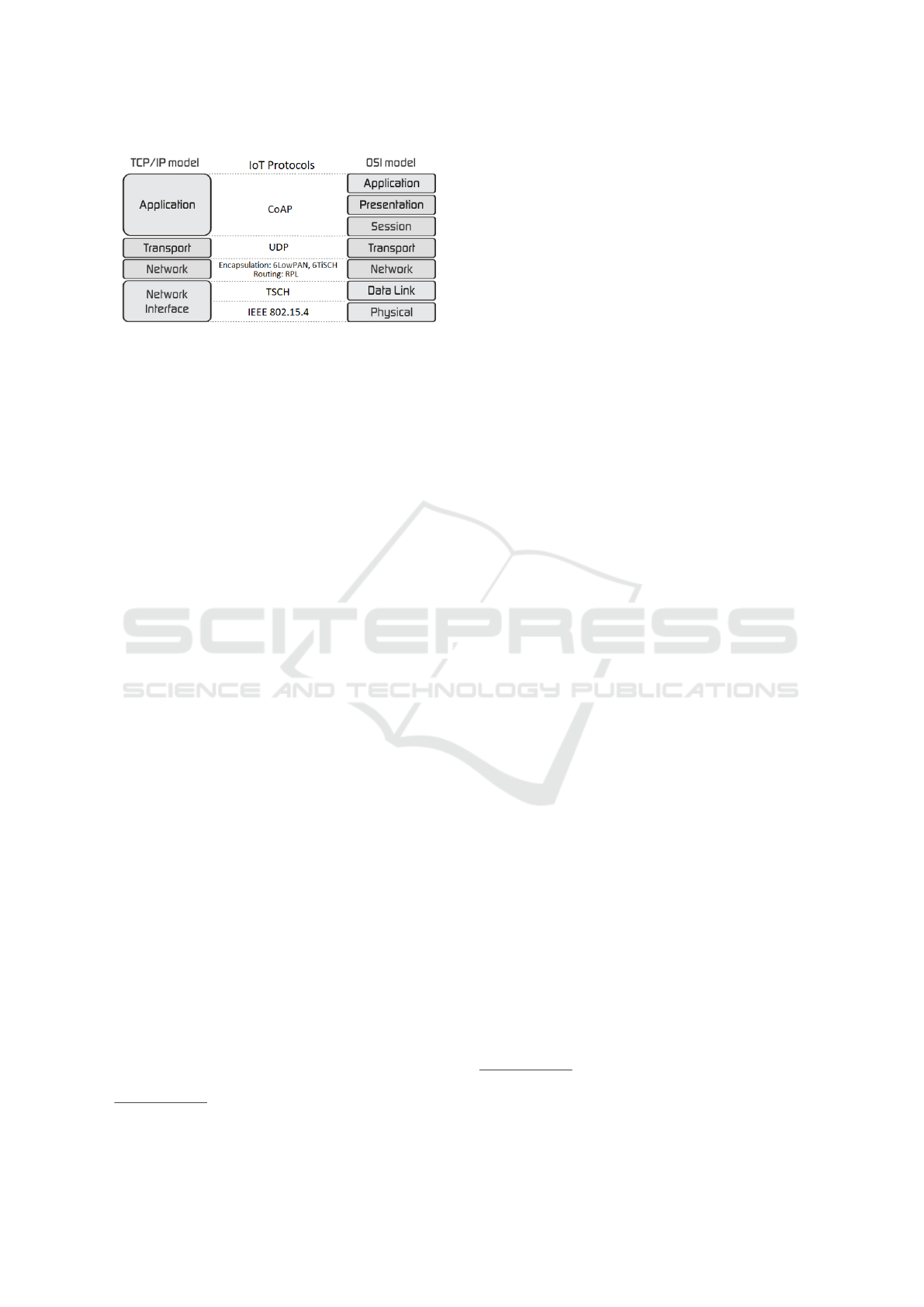
Figure 1: Standardization of low-power and resource-
constrained wireless technologies.
mation arrives at the sink node. There is also the role
of border router which interfaces the sensor network
with the computer network, allowing a user to request
node sensing information through the computer and
from the Internet.
An application that may use the concept of bor-
der router is the Constrained Application Protocol
(CoAP), depicted in Figure 1. CoAP is a specialized
web transfer protocol for use with constrained nodes
and constrained networks in the IoT. The protocol
is designed for machine-to-machine (M2M) applica-
tions such as smart energy and building automation
1
.
In this case, the user (CoAP client) requests resources
from the sensors, represented as CoAP servers, dis-
tributed in different parts of the environment.
Like HTTP, CoAP is based on the Representa-
tional State Transfer (REST) architecture, i.e., servers
make resources available under an URL, and clients
access these resources using methods such as GET,
PUT, POST, and DELETE. The need to maintain such
constrained devices spending the minimum possible
energy for a long time justifies the use of this proto-
col, keeping their communication active through the
Internet.
The experiments performed in this work used a
simple UDP client/server application, in which the
nodes act as UDP clients and transmit packets to the
UDP server, that works as the network coordinator.
However, our scenario could also be implemented us-
ing the CoAP application.
IPv6 over Low power Wireless Personal Area
Networks (6LoWPAN) is the IETF development
group that creates and maintains the specifications
that allows to use IPv6 over IEEE 802.15.4 net-
works. Its most pertinent issues are fragmenta-
tion/defragmentation and compression of IPv6 head-
ers. 6LoWPAN creates an adaptation layer between
IEEE 802.15.4 and IPv6, with specific headers that
can be added or removed, allowing only what is useful
to be sent. A Working Group (WG) recently formed
1
https://coap.technology/, accessed in 16/05/2019.
called 6TiSCH aims to link IEEE802.15.4e TSCH ca-
pabilities with prior IETF 6LoWPAN and ROLL stan-
dardization efforts and recommendations. Defining
IPv6 over TSCH, which is a MAC layer protocol,
6TiSCH is a key to enable the further adoption of IPv6
in industrial standards and the convergence of Opera-
tional Technology (OT) with Information Technology
(IT) (Thubert and Watteyne, 2018).
Besides 6LoWPAN and 6TiSCH, the IoT context
includes another protocol in the network layer called
IPv6 Routing Protocol for Low Power and Lossy Net-
works (RPL). It is a distance vector protocol that de-
fines its routes through routing trees using the Di-
rected Acyclic Graph (DAG) concept. RPL mainly
meets the requirements of low data rates and high er-
ror rates, which makes the network throughput low.
Each node can associate with more than one node,
which differs RPL from other tree-based protocols,
and it deals with alternative routes to avoid interrupt-
ing the data flow.
Contiki operating system provides two implemen-
tations of RPL with different attributes: RPL Classic
and RPL Lite. RPL Classic is the continuation of the
original Contiki’s RPL implementation, ContikiRPL,
and supports multiple instances and DODAGs, stor-
ing and non-storing mode, and multicasting. RPL
Classic is more complex than RPL Lite, which re-
moved support for storing mode in favor of non-
storing mode, and removed the complexity of han-
dling multiple instances and DODAGs. Through
these changes, RPL Lite presents better performance
2
and has a considerably smaller ROM footprint. How-
ever, it has a lower interoperability level with other
implementations, which may use storing mode for in-
stance. In this work, we use the RPL Lite with non-
storing mode.
Heading to the link layer, we have one of the
most important protocols in IoT context, TSCH. In
this protocol, the nodes communicate by following
a Time Division Multiple Access (TDMA) sched-
ule, and a timeslot in this schedule provides a unit
of bandwidth that is allocated for communication be-
tween neighbor nodes. This approach avoids idle lis-
tening and extends battery lifetime for constrained
nodes. Channel-hopping improves reliability in the
presence of narrow-band interference and multi-path
fading (Thubert and Watteyne, 2018).
This work aims to perform experiments using sim-
ulation with Cooja, which is the Contiki’s simula-
tor, and real testbeds M3 Open Node from FIT IoT-
LAB
3
. This device is based on a STM32 (ARM Cor-
2
https://github.com/contiki-ng/contiki-ng/wiki/
Documentation:-RPL/, accessed in 16/05/2019.
3
https://www.iot-lab.info/
PECCS 2019 - 9th International Conference on Pervasive and Embedded Computing and Communication Systems
84

tex M3) 32-bits micro-controller, at 72 MHz, 64kB
RAM, and AT86RF231 2.4 GHz radio. Simulations
use the Zolertia Z1 motes, with 16-bit RISC CPU,
16MHz clock, 8KB RAM, 92KB Flash memory, and
a CC2420 transceiver, IEEE 802.15.4 compliant oper-
ating at 2.4GHz,i.e., lower performance than M3, and
some parameters of TSCH and RPL protocols needed
to be reduced to fit memory size.
FIT IoT-LAB is a laboratory that provides a large-
scale infrastructure suitable for testing small wire-
less sensor devices. It provides full control of net-
work nodes and direct access to the gateways to which
nodes are connected, allowing researchers to monitor
nodes energy consumption and network-related met-
rics, e.g. end-to-end delay, throughput or overhead.
In this work, we used the protocols UDP, 6TiSCH,
RPL and TSCH, and focused the study especially
on the TSCH protocol in relation to the schedul-
ing method, frequency hopping and guard time in a
network with direct connection between client and
server.
The performance and energy efficiency of the
entire network is analysed for different scheduling
methods, packet transmission rates, number of used
channels and guard time. The overall network per-
formance is assessed in terms of network throughput
where the PRR (Packet Reception Rate) seems to be
a good indicator of the presence of disturbances im-
pacting the network.
The rest of this paper is organized as follows. In
Section 2, we introduce the TSCH characteristics,
two main scheduling methods of TSCH, discuss the
Guard Time and channel blacklisting. In Section 3,
we present the performance evaluation with simula-
tions and real testbeds, and finally in Section 4 we
make concluding remarks.
2 IEEE 802.15.4E TSCH
The IEEE 802.15.4e MAC standard (IEEE, 2017) re-
leased in 2012, is an improved version of 802.15.4
MAC protocol. The IEEE 802.15.4e uses many ideas
from WirelessHART and ISA-100.11.a standards, in-
cluding slotted access, shared and dedicated slots,
multi-channel communication, and frequency hop-
ping. Specifically, IEEE 802.15.4e extends the pre-
vious IEEE 802.15.4 standard by introducing five
new MAC behavior modes (protocols), designed to
support specific application domains (De Guglielmo
et al., 2016). Among them, only TSCH, Deterministic
and Synchronous Multi-Channel Extension (DSME),
and Low Latency Deterministic Network (LLDN)
modes have been explored in the literature, so far (De
Guglielmo et al., 2016).
TSCH standard aims to provide bounded delay
and reliable communication in industrial wireless net-
works. It divides the time into slots and uses the Fre-
quency Hopping Scatter Spectrum (FHSS) to reduce
the impact of multipath fading and external interfer-
ences. This technique requires network synchroniza-
tion and changes the communication frequency every
packet is sent making the network more robust against
disturbances affecting only a channels subset.
A link between nodes can be represented by a
pair of timeslots in the slotframe (n), and the chan-
nel offset used by the nodes in that timeslot, de-
fined as [n, channelOffset]. The transmit frequency
f in timeslot n of the slotframe is given by f =
FHS
ASN + channel
O f f set
%FHS
length
, where ASN
(Absolute Slot Number) represents the total number
of timeslots incremented in each time interval from
the beginning of the network, % is the modulus op-
erator, and the length of the sequence (FHS length)
is 16 channels by default, without blacklisting in the
calculation.
In addition to frequency hopping, TSCH uses
blacklists for low quality channels. Other standards,
as WirelessHART and ISA100.11a, use frequency
hopping and blacklisting as well. WirelessHART
employs a central network manager with frequency
hopping and global blacklist. ISA100.11a uses lo-
cal blacklists, where the nodes avoid transmitting on
blacklisted channels, preventing unsuccessful trans-
missions. If packets are dropped before being trans-
mitted the delay may increase and the PRR decrease
at the application layer.
There are 16 different channels available but due
to disturbances the channel quality of some channels
is very and are blacklisted, reducing available ones.
Hence, the FHS must be regenerated every time a
channel is blacklisted.
2.1 Minimal Schedule and Orchestra
The IETF Working Group 6TiSCH is currently stan-
dardizing the mechanisms to use TSCH in low-power
IPv6 scenarios (P. Thubert, 2019). 6TiSCH defines
the sublayer for the management of TSCH nodes and
schedules via a CoAP interface, and 6top, a sub-
layer that enables neighbor-to-neighbor slot installa-
tion/removal (Duquennoy et al., 2017).
In this paper, 6TiSCH is used with minimal sched-
ule (Vilajosana et al., 2017) providing basic interop-
erability. The settings include a simple static sched-
uler with a single shared slot for all transmissions and
receptions in a slotframe, and defines how TSCH in-
teracts with upper layers and the RPL routing proto-
Join Multiple Channels and IEEE 802.15.4e TSCH Protocol Use Effects on WSN Performance and Energy Efficiency
85
col, ensuring a consistent mapping between the RPL
routing topology and the TSCH time-source graph.
Additionally, we perform experiments using Orches-
tra, an autonomous scheduler for TSCH and RPL net-
works where nodes maintain their own schedule lo-
cally based on their local RPL state. It has neither
central scheduler nor neighbors negotiation, reducing
traffic overhead.
2.2 Guard Time
When the network has traffic, the nodes that com-
municate need to resynchronize to their time source
neighbor(s) periodically not to drift in time. The peri-
odicity of these control messages depends on the sta-
bility of the clock source and on how “early” each
node starts listening for data using the Guard Time
(GT) (Watteyne, 2015).
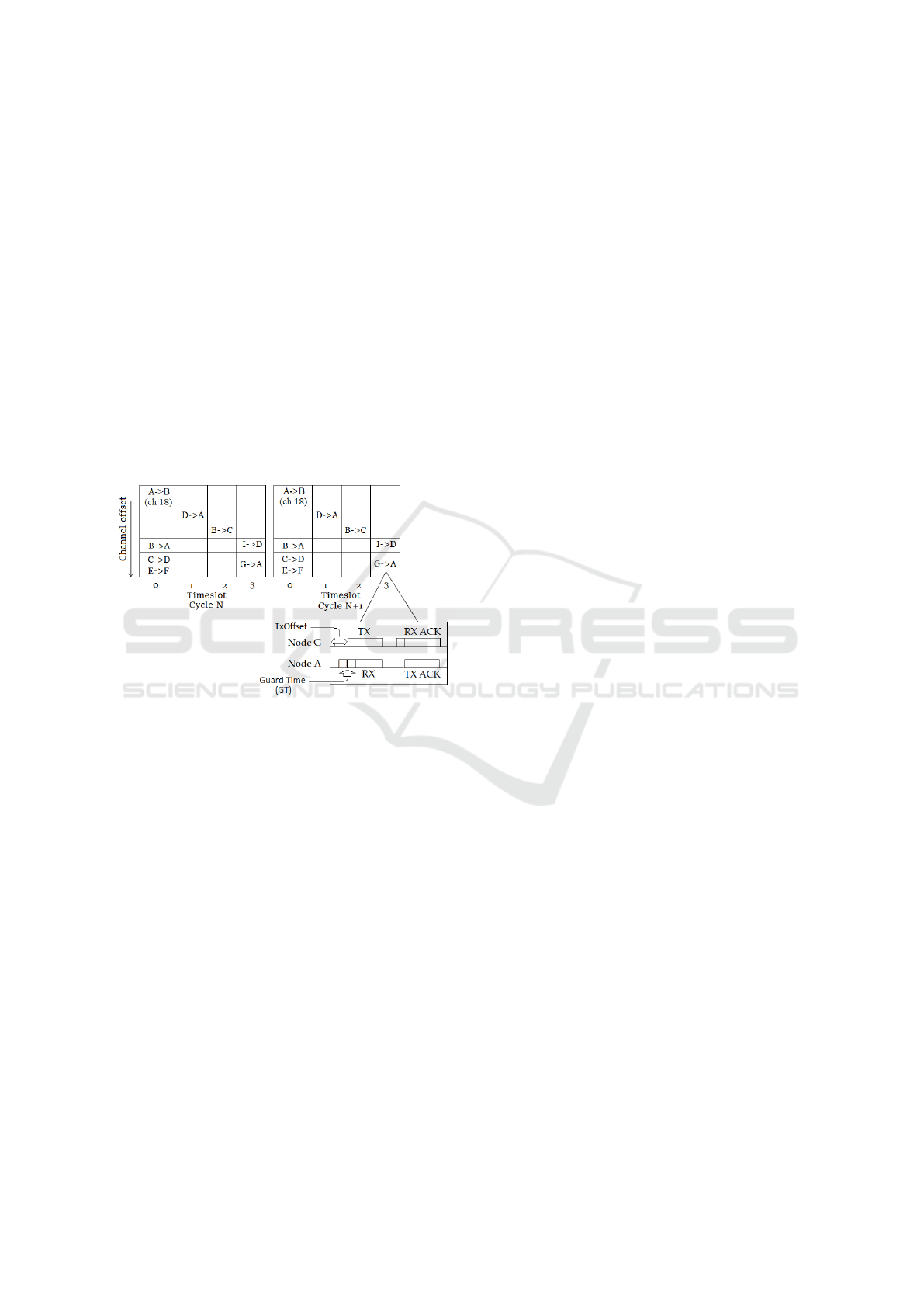
Figure 2: TSCH includes a GT to account for loss of syn-
chronization.
Figure 2 depicts the GT process, in which Node
G transmits its data packet after TxOffset, while the
receiver A uses a GT to avoid missing the incom-
ing packet by turning its radio ON a little before the
packet arrival.
Higher synchronization accuracy enables the re-
duction of idle listening time on receivers, saving
more energy. In (Papadopoulos et al., 2016), a set of
experiments were performed using Cooja to evaluate
the minimum GT under different clock drift values (0,
±10, ±20, ±30 and ±40 ppm - parts per million). In
the results, with a ±20 ppm drift, 390 µs is the mini-
mum GT length for operation without compromising
network reliability due to loss of synchronization us-
ing emulated Z1 motes. They decreased the GT dura-
tion when motes were closer to their sink and this ap-
proach saved energy significantly with good network
reliability. In our work, we compared three different
GT lengths, 2200 µs (Contiki’s default), 1500 µs and
900 µs using the M3 platform. Reducing this value to
400 µs, the average power consumption per receiver
node could decrease by more than 40% in the scenar-
ios studied in (Papadopoulos et al., 2016).
One of the main reasons for clock drift is caused
by oscillator crystals deviating from their nominal fre-
quency due to production spread (Elsts et al., 2016).
In OpenMote-CC2538, which is the platform we will
use in future works to perform experiments in indus-
try, a 32 MHz crystal clocks the radio, and has a drift
of up to 30 ppm from -20 C to +70 C (Vilajosana et al.,
2015). To achieve tight time synchronization, a sec-
ond 32 kHz crystal clocks the microcontroller’s RTC
(Real Time Clock), allowing to keep track of time,
even when in deep sleep. The second crystal is rated
at 10 ppm from -40 C to +85 C, which is the industrial
temperature range.
2.3 Channel Blacklisting
Appropriate blacklist is proposed in this investiga-
tion approach to improve the overall performance.
Blacklist and transmissions node scheduling are used
to avoid neighbor links interferences by restricting
the simultaneous use of adjacent channels. This ar-
rangement is critical to achieve the best overall net-
work performance. There are two approaches to cre-
ate blacklists: global and local. In the first one,
all the nodes use the same channels-list. Neverthe-
less, this solution could become suboptimal, since
the channels may present different qualities for dis-
tinct network links, even when nodes are close to
each other (Gomes et al., 2017b). In the second ap-
proach, each nodes pair can use different sets of chan-
nels (Kotsiou et al., 2017), i.e., a specific blacklist is
defined per link.
The use of local blacklists increase the complex-
ity, and it could produce collisions when two or more
nodes transmit in the same timeslot with different
blacklists, resulting in multiple nodes broadcasting on
the same channel at the same time. Besides, if the en-
vironment is very unstable and the blacklist is mod-
ified very often, the local blacklist is not useful due
to the amount of signalling frames required for resyn-
chronization.
Blacklists identify channels to be included using
a Link Quality Estimator (LQE) which analyses in-
terferences in the same frequency range in the 2.4
GHz band and blacklist them. In this paper, since
harsh environment is not considered the LQE is not
used. However, channels sets are randomly chosen to
be blacklisted, while keeping active (whitelisted) up
to four channels in the deployed test-beds, and eight
channels in the simulations. This feature guarantees
the required diversity and reduces the synchronization
and resynchronization delay. Future works will in-
PECCS 2019 - 9th International Conference on Pervasive and Embedded Computing and Communication Systems
86

clude using LQE in industrial environments to black-
list channels before and after the network starts.
The relevance of setting the most appropriate
channels blacklist in TSCH has been neglected by
most of previous developments which mainly focus
on scheduling strategies while ignoring the channels
quality assessment.
The TSCH protocol is implemented in three types
of topologies: star, tree and mesh. Tree and mesh
topologies are more challenging than the star one
because two or more nodes can send packets over
the same channel at the same time (timeslot) caus-
ing packet losses. Even when transmitting on ad-
jacent channels exits a certain level of interference
which must be mitigated. In the star topology, each
node connecting with the coordinator transmits over
a different channel and timeslot, although it is possi-
ble to allocate shared slots for many nodes. In con-
sequence, a contention-based approach is requires to
manage packets collisions. This investigation focuses
on mesh topology where nodes are connected directly
to the sink node.
In (Queiroz et al., 2018), the authors analysed the
channel blacklisting for networks with star and tree
topologies using the TSCH protocol. In the case of
tree topology, they divided the network into clusters,
and in each cluster, there is a cluster head (CH) which
acts as LQE, network coordinator and router, and for-
wards the packets from the leaves to the sink node.
The quality estimation is performed locally, i.e., each
leaf has its own blacklist. The authors conclude that
implementing the blacklisting has a noticeable im-
pact on the overall network performance, and there
must be a limit in the number of blocked (black-listed)
channels to avoid packet losses. It does not happen in
the star topology since there is no simultaneous trans-
missions; each node has its own timeslot to transmit
and receive an acknowledgement, and in that case, the
more the blocked channels the higher the PRR, sur-
viving only one and the best for each end node.
In (Zorbas et al., 2018), the algorithm LOST is
introduced and relies on information gathered by its
1-hop neighbours only. It multiplexes the different
transmissions across different channels by allocating
properly the channel offsets. A localized blacklist
method is employed in the scheduler to avoid using
the bad radio channels.
In (Du and Roussos, 2012), the authors introduced
the Adaptive TSCH (A-TSCH), which uses channel
blacklisting. The transmitting nodes become aware of
the neighbors’ blacklist, and both the transmitter and
receiver use the same hopping sequence to communi-
cate by inserting the list information into transmission
packets.
Figure 3: Exp4-5 with Orchestra, Exp10-11 with Minimal
Schedule, one and four channels with M3 motes.
In (Gomes et al., 2017a), the algorithm MABO-
TSCH assigns in a centralized manner a collection of
cells for each radio link considering local blacklists.
Several channel offsets are assigned within the same
timeslot, so that a radio link can pick one of the chan-
nel offsets that does not give a blacklisted physical
frequency. A pair of nodes locally decides the chan-
nels to be blacklisted, and to maintain a consistent
list for the link, they insert it into the ACK package,
combined with a sequence number. Channel quality
MABO-TSCH is based on Stochastic Multi-Armed
Bandits (MAB).
Dynamic whitelisting method is used in (Tavakoli
et al., 2015) and proposes improved TSCH (Enhanced
TSCH, ETSCH), which uses a non-intrusive chan-
nel quality estimation technique called NICE. The
ETSCH uses the Energy Detection (ED) method to
estimate the channels quality at every time interval. It
frequently updates a channel stream and sets-up a sec-
ondary list with the best channels to transmit the EBs.
At least two samples of channel energy are taken per
time interval. Using a secondary list reduces the like-
lihood of losing EBs.
In (Kotsiou et al., 2019) is proposed grouping ra-
dio links to guarantee links in a group share the same
whitelist, and different groups have distinct ones.
The goal is avoiding a global whitelist, which de-
creases network performance, and a local whitelist,
which may cause collisions. The solution forces all
the nodes sharing the same timeslot using the same
whitelist, performing better than approaches without
blacklist, with global blacklist, with a common black-
list per timeslot, and better than MABO-TSCH algo-
rithm.
3 PERFORMANCE EVALUATION
This section analyses the performance of TSCH using
the settings depicted in Table 1. From the 1st to the
12th, Cooja was used for simulating a network with
ten nodes (nine UDP clients and one sink node - UDP
server), and from 13th to 17th real testbeds were used.
Join Multiple Channels and IEEE 802.15.4e TSCH Protocol Use Effects on WSN Performance and Energy Efficiency
87

Table 1: Experiments performed, some of them with both simulation and real testbeds. The last three for two hours.
Experiments
Powertrace (s)
Simulations
PTR
Scheduling
Method
Number of
Channels
Maximum Payload
Length
Simulation
Real
Testbeds
Number of
Nodes
Guard
Time
Exp1 10 1 pkt / 30 s Orchestra 1 30 Yes - 10 Default
Exp2 10 1 pkt / 30 s Orchestra 4 30 Yes - 10 Default
Exp3 10 1 pkt / 30 s Orchestra 8 30 Yes - 10 Default
Exp4 10 / - 1 pkt / 5 s Orchestra 1 30 Yes Yes 10 Default
Exp5 10 / - 1 pkt / 5 s Orchestra 4 30 Yes Yes 10 Default
Exp6 10 1 pkt / 5 s Orchestra 8 30 Yes - 10 Default
Exp7 10 1 pkt / 30 s Minimal Schedule 1 30 Yes - 10 Default
Exp8 10 1 pkt / 30 s Minimal Schedule 4 30 Yes - 10 Default
Exp9 10 1 pkt / 30 s Minimal Schedule 8 30 Yes - 10 Default
Exp10 10 / - 1 pkt / 5 s Minimal Schedule 1 30 Yes Yes 10 Default
Exp11 10 / - 1 pkt / 5 s Minimal Schedule 4 30 Yes Yes 10 Default
Exp12 10 1 pkt / 5 s Minimal Schedule 8 30 Yes - 10 Default
Exp13 - 1 pkt / 10 s Orchestra 4 30 - Yes 30 Default
Exp14 - 1 pkt / 10 s Minimal Schedule 4 30 - Yes 30 Default
Exp15 - 1 pkt / 10 s Orchestra 4 30 - Yes 29 2200
Exp16 - 1 pkt / 10 s Orchestra 4 30 - Yes 29 1500
Exp17 - 1 pkt / 10 s Orchestra 4 30 - Yes 29 900
Four simulation experiments were also evaluated us-
ing real M3 testbeds. Contiki’s Powertrace applica-
tion is used in the simulations allowing monitoring
nodes energy consumption every ten seconds. In the
testbed at the FIT IoT Lab, Powertrace was not re-
quired as a manager node was used to monitor the
radio channels power and consumption.
Packet Transmission Rate (PTR) was fixed at 1
packet every 30, 10, and 5 sec. A predefined list of
whitelisted channels. In the last five experiments we
chose four channels to provide diversity, despite the
slightly higher energy consumption compared to the
network with one channel, as depicted in Figure 3.
Figure 4 depicts the results obtained after 12 sim-
ulation experiments aimed at assessing network per-
formance, energy efficiency and the number of syn-
chronization requests. In Orchestra (Exp1-Exp6), the
number of synchronization requests is directly related
to the PRR, the number of channels and power con-
sumption. As the number of whitelisted channels in-
creases the nodes require a longer time interval to syn-
chronize with the network, and consequently the PPR
decreases and the energy efficiency drops. The en-
ergy efficiency regards the amount of energy required
to successfully transmit and receive a data packet. In
this work power consumption absolute values are not
considered but relative ones.
In the case of Minimal Schedule (Exp7-Exp12),
using several channels impacts negatively on the
PRR. However, the energy consumption is directly
related to the number of synchronization requests.
Using four channels instead of one or eight led to
a higher number of synchronization requests, conse-
quently to a higher energy consumption. This behav-
ior was evaluated through the real nodes in the labo-
ratory in Figure 3.
Figures 3 and 4 show that simulation results fit
testbeds conclusion, but the PRR with Orchestra
(Exp4 and Exp5). In this case, the PRR with one
and four channels showed almost the same results
with M3 testbeds. More experiments are needed to
achieve stronger conclusions because even consider-
ing that the laboratory environment is somehow sta-
ble, it’s always changing, since the lab is used by
other researchers who develop independent experi-
ments at the same time producing interferences im-
pacting the channels behaviour.
In all the simulation scenarios of PRR, the net-
work with a single channel performed better than with
four and eight channels, as depicted in Figure 5. This
can be explained by the fact that, as mentioned pre-
viously, the simulated environment and the channel
model of Cooja does not implement harsh environ-
ments such as the industrial one, that harms the qual-
ity of a subset of channels. The RSSI value remains
almost the same during the simulation period, which
does not happen in industrial environments, already
studied in several papers (Queiroz et al., 2017). A
fairly stable RSSI value is considered in the labora-
tory environment with static nodes. Orchestra and
Minimal Schedule showed very close results in PRR.
Regarding the experiments with M3 motes and
four channels in Figure 6, both Orchestra and Mini-
mal Schedule presented almost the same results using
the Guard Time with its default value, 2200 µs.
To implement the expected fully autonomous net-
work next steps consider the autonomous scheduler
Orchestra to evaluate GT values. Figure 7 shows
the PRR and energy consumption with GTs 2200 µs,
1500 µs and 900 µs, respectively, using Orchestra.
In the topology with 28 motes sending packets every
10 sec. to a single sink node without confirmation
(ACK), where nodes connect directly to the sink, the
GT with 1500 µs showed the best result, with 99.5%
of PRR and the least energy consumption. Reduc-
ing the GT, the receiver wakes up earlier and is able
PECCS 2019 - 9th International Conference on Pervasive and Embedded Computing and Communication Systems
88

Figure 4: Relation among the PRR, energy efficiency and synchronization requests in simulations (E1 stands for Exp1).
Figure 5: The total PRR comparing the schedule methods
and number of channels in simulations.
Figure 6: Comparison with Orchestra and Minimal Sched-
ule in terms of PRR and energy consumption with M3.
Figure 7: Orchestra with 2200 µs, 1500 µs, and 900 µs GT.
to receive more packets. However, when this value
is too low, it may lead to packet losses due to syn-
chronization failure. Energy consumption differences
were small given just one node receives packets, any
change in the value of the GT will generate a small
change in the total network energy consumption. Us-
ing more sink nodes the increment is more remark-
able.
TSCH parameters impact analysis is important to
achieve the best network performance and energy ef-
ficiency. It’s worthy to note that some of them are
configured with the M3 testbeds, as follows:
• To estimate the drift of the time-source neighbor
and compensate for it:
TSCH_CONF_ADAPTIVE_TIMESYNC 1
• With TSCH ADAPTIVE TIMESYNC enabled,
keep-alive timeout used after reaching accurate
drift compensation:
TSCH_CONF_KEEPALIVE_TIMEOUT(20*CLOCK_SECOND)
TSCH_CONF_MAX_KEEPALIVE_TIMEOUT
(60*CLOCK_SECOND)
• Enhanced Beacon Advertising Period; the shorter
the period, the higher the advertising packets fre-
quency, smaller the synchronization errors, in
contrast, the higher the network traffic:
TSCH_CONF_EB_PERIOD(16*CLOCK_SECOND)
TSCH_CONF_MAX_EB_PERIOD(50*CLOCK_SECOND)
• 6TiSCH minimal schedule length. Larger values
in less active slots, reducing capacity and saving
energy. With Orchestra the TSCH schedule length
must be set to zero:
TSCH_SCHEDULE_CONF_DEFAULT_LENGTH 3
4 CONCLUSIONS
This investigation showed and compared the results
of several experiments carried out by using both a
simulation tool and actual testbeds where the TSCH
protocol is used to improve the overall network. The
goal was evaluating the impact of using one or sev-
eral channels on packet transmissions. Various exper-
iments has been conducted in the laboratory and us-
ing a simulator, where both the laboratory and simu-
lation environments didn’t affect noticeably channels
quality. This feature lead to a remarkable conclusion:
sensor-nodes using a single channel could show a per-
formance superior than that showed by set-ups us-
ing several channels. In real industrial environments,
given the level of interferences is stronger and mul-
tipath is present affecting the network performance,
using just one channel leads to worse performance be-
cause transmitting over only one channel affected by
strong interferences and multipath disturbances pro-
vokes loosing lots of packets. The results obtained
along the various experiments show that, regardless
the scheduling method, increasing the number of used
channels decreases the PRR, considering set-ups us-
ing up to 30 motes in non-hard-harsh environments
such as offices, homes and laboratories. Next steps
will consider networks with more motes, since the
probability of simultaneous transmissions over the
same and/or adjacent channels increases, leading to a
Join Multiple Channels and IEEE 802.15.4e TSCH Protocol Use Effects on WSN Performance and Energy Efficiency
89

higher number of collisions and packet losses. How-
ever, in harsh environments, the network performance
when using few channels would decrease, due to more
channels suffer from interferences and multipath dis-
turbances. In these cases using a link quality es-
timators should be considered in order to use only
those channels showing the best quality. In future
works, the investigation will focus on developing ex-
periments using the Openmote-CC2538 in industrial
environments to evaluate the GT with a Link Quality
Estimator, and a Transmission Power Manager to en-
sure an appropriate overall network performance and
energy efficiency.
ACKNOWLEDGEMENTS
Authors acknowledge: the COPELE-UFCG, the
Iecom, the CNPq, SMART2 Program, the GIRA Re-
search Group, and the FIT IoT Lab.
REFERENCES
De Guglielmo, D., Brienza, S., and Anastasi, G. (2016).
IEEE 802.15.4e: A survey. Computer Communica-
tions.
Du, P. and Roussos, G. (2012). Adaptive time slotted chan-
nel hopping for wireless sensor networks. In 2012 4th
Computer Science and Electronic Engineering Con-
ference (CEEC), pages 29–34. IEEE.
Duquennoy, S., Elsts, A., Nahas, B. A., and Oikonomo, G.
(2017). TSCH and 6TiSCH for Contiki: Challenges,
Design and Evaluation. In 2017 13th International
Conference on Distributed Computing in Sensor Sys-
tems (DCOSS), pages 11–18. IEEE.
Elsts, A., Duquennoy, S., Fafoutis, X., Oikonomou, G.,
Piechocki, R., and Craddock, I. (2016). Microsecond-
Accuracy Time Synchronization Using the IEEE
802.15.4 TSCH Protocol. In 2016 IEEE 41st Confer-
ence on Local Computer Networks Workshops (LCN
Workshops), pages 156–164. IEEE.
Gomes, P. H., Watteyne, T., and Krishnamachari, B.
(2017a). Mabo-tsch: Multihop and blacklist-based
optimized time synchronized channel hopping. Trans-
actions on Emerging Telecommunications Technolo-
gies, page e3223.
Gomes, R. D., Queiroz, D. V., Filho, A. C., Fonseca, I. E.,
and Alencar, M. S. (2017b). Real-time link quality es-
timation for industrial wireless sensor networks using
dedicated nodes. Ad Hoc Networks, 59:116–133.
IEEE (2017). IEEE 802.15 WPAN Task Group 4e (TG4e).
Kotsiou, V., Papadopoulos, G. Z., Chatzimisios, P., and
Theoleyre, F. (2017). Label: Link-based adaptive
blacklisting technique for 6tisch wireless industrial
networks. In Proceedings of the 20th ACM Interna-
tional Conference on Modelling, Analysis and Sim-
ulation of Wireless and Mobile Systems - MSWiM
’17, pages 25–33, New York, New York, USA. ACM
Press.
Kotsiou, V., Papadopoulos, G. Z., Chatzimisios, P., and
Theoleyre, F. (2019). Whitelisting without collisions
for centralized scheduling in wireless industrial net-
works. IEEE Internet of Things Journal, 6(3):5713–
5721.
P. Thubert, E. (2019). An architecture for ipv6 over
the tsch mode of ieee 802.15.4, update 2019-03-
01. https://datatracker.ietf.org/doc/draft-ietf-6tisch-
architecture/. Accessed in: 24/04/2019.
Papadopoulos, G. Z., Mavromatis, A., Fafoutis, X.,
Montavont, N., Piechocki, R., Tryfonas, T., and
Oikonomou, G. (2016). Guard time optimisation
and adaptation for energy efficient multi-hop tsch net-
works. In 2016 IEEE 3rd World Forum on Internet of
Things (WF-IoT), pages 301–306.
Queiroz, D. V., Alencar, M. S., Gomes, R. D., Fonseca,
I. E., and Benavente-Peces, C. (2017). Survey and
systematic mapping of industrial Wireless Sensor Net-
works. Journal of Network and Computer Applica-
tions, 97:96–125.
Queiroz, D. V., Gomes, R. D., Benavente-Peces, C., Fon-
seca, I. E., and Alencar, M. S. (2018). Evaluation of
Channels Blacklists in TSCH Networks with Star and
Tree Topologies. In Proceedings of the 14th ACM In-
ternational Symposium on QoS and Security for Wire-
less and Mobile Networks - Q2SWinet’18, pages 116–
123, New York, New York, USA. ACM Press.
Tavakoli, R., Nabi, M., Basten, T., and Goossens, K. (2015).
Enhanced time-slotted channel hopping in wsns us-
ing non-intrusive channel-quality estimation. In 2015
IEEE 12th International Conference on Mobile Ad
Hoc and Sensor Systems, pages 217–225. IEEE.
Thubert, P. and Watteyne, T. (2018). Char-
ter for working group - 6tisch: ”ipv6
over the tsch mode of ieee 802.15.4e”.
https://datatracker.ietf.org/wg/6tisch/about/. Ac-
cessed in: 20/04/2019.
Vilajosana, X., Pister, P., and Watteyne, T. (2017). Minimal
6tisch configuration. https://tools.ietf.org/html/draft-
ietf-6tisch-minimal-21. Accessed in: 17/05/2019.
Vilajosana, X., Tuset, P., Watteyne, T., and Pister, K. (2015).
Openmote: Open-source prototyping platform for the
industrial iot. In Mitton, N., Kantarci, M. E., Gal-
lais, A., and Papavassiliou, S., editors, Ad Hoc Net-
works, pages 211–222. Springer International Pub-
lishing, Cham.
Watteyne, T. (2015). Using ieee 802.15.4e time-
slotted channel hopping (tsch) in the in-
ternet of things (iot): Problem statement.
https://tools.ietf.org/html/rfc7554. Accessed in:
01/05/2019.
Xu, L. D., He, W., and Li, S. (2014). Internet of Things in
Industries: A Survey. IEEE Transactions on Industrial
Informatics, 10(4):2233–2243.
Zorbas, D., Kotsiou, V., Theoleyre, F., Papadopoulos, G. Z.,
and Douligeris, C. (2018). LOST: Localized black-
listing aware scheduling algorithm for IEEE 802.15.4-
TSCH networks. In 2018 Wireless Days (WD), pages
110–115. IEEE.
PECCS 2019 - 9th International Conference on Pervasive and Embedded Computing and Communication Systems
90
