
Single Sign On (SSO) System with Application of Central
Authentication Service (CAS) at Manado State Polytechnic
Marike Kondoj
1
, Tineke Saroinsong
2
and Anritsu Polii
1
1
Informatics Engineering, Manado State Polytechnic, Indonesia
2
Mechanical Engineering, Manado State Polytechnic, Indonesia
Keywords: Application, SSO, Polimdo, Integrated.
Abstract: Integrated information systems are an essential requirement in the digital era. However, the number of
currently available/running applications at the Manado State Polytechnic (Polimdo) with different accounts
makes it difficult for users to access or remember their accounts. Based on this condition, it is necessary to
have a solution for implementing a Single Sign On a system that allows users to have one application for
several applications. The purpose of this research is to integrate all applications currently running at Polimdo
to provide effective and efficient conditions for the utilization of each application. The expected result is a
system developed according to user needs so that the utilization of the application can be effective.
1 INTRODUCTION
In the current era of technological development, the
world of information is increasingly dynamic.
Because it is supported by technology and the use of
the internet, which is increasing rapidly and
increasing, according to Emarketer (2013), internet
users (www) will increase from 26.3% in 2012 to
30.7% in 2016 for the Asia-Pacific region. In
Indonesia, internet users reached 63 million users in
2012. It is estimated that an increase of 30% in 2013
was 82 million users, according to the Association of
Indonesian Internet Service Providers (APJII).
The Internet is one form of the development of
information and communication technology (ICT).
ICT has a significant role in the world of education.
In the Ministry of National Education's ICT blueprint,
there are at least seven functions of ICT in education:
learning resources, learning aids, learning facilities,
competency standards, administrative systems,
decision support, and infrastructure. Utilization of the
internet network in previous research by Saroinsong
et al. Design and Implementation of Integrated
Software Research and Community Service at
Manado State Polytechnic (Saroinsong, 2017).
Utilization of the internet network at the Manado
State Polytechnic already has an internet network to
support education and creativity in quality, quality
teaching and learning processes, as well as facilitate
communication and exchange of information in an
academic environment. Many applications require
authentication in the Manado State Polytechnic's
existing infrastructure. Among them are e-learning
learning media, campus mail, and educational
information systems. However, existing web
applications are still not entirely appropriately
integrated. This influences the number of different
login systems for each application at the Manado
State Polytechnic because users must log in to each
application.
In previous studies, a single sign-on (SSO)
method based on the Lightweight Directory Access
Protocol (LDAP) has been researched by Dian
Novera from Bina Darma University. The research
resulted in one username and one password that can
make it easier for users because they don't need to use
many accounts and memorize many passwords.
However, LDAP-based SSO has limitations where
users still have to log in to each application. With that,
the author will test the integration of all applications
into a web portal for further development with the
CAS (Central Authentication Service)-based SSO
method in the Manado State Polytechnic
environment.
In a study by Binu et al., a Single Sign On (SSO)
is an authentication mechanism that allows users to
log in once and access services from various SPs in
the same session. SAML is generally used as a Single
Sign-On protocol. The study proposes a Secure
698
Kondoj, M., Saroinsong, T. and Polii, A.
Single Sign On (SSO) System with Application of Central Authentication Service (CAS) at Manado State Polytechnic.
DOI: 10.5220/0011863100003575
In Proceedings of the 5th International Conference on Applied Science and Technology on Engineering Science (iCAST-ES 2022), pages 698-702
ISBN: 978-989-758-619-4; ISSN: 2975-8246
Copyright © 2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)

Dynamic-ID-based scheme using a smart card or
crypto card that does not require a verification table
and implements the Single Sign On feature using the
SAML protocol, thus enabling users to enjoy all MSE
features along with SSO.
Furthermore, the research pane, Jian Hu et al.,
stated that frequent verification is an obstacle faced in
constructing campus networks. To overcome these
problems, they integrated the application of the B/S
architecture with the Single sign-on (SSO) system. As
a result, a unified personnel database has been created
using an LDAP server and created dynamic groups to
manage the database.
Single Sign On (SSO) is a system where users
only need one username and password to access and
use services on all existing applications. Central
Authentication Service (CAS) based on the CAS
Protocol is one part of the SSO product. CAS is used
to deal with communication problems between
different applications. With the Site on CAS on SSO
on all existing applications at the Manado State
Polytechnic, who can form application integration in
the form of a web portal. Users only need to log in
once to be able to use all the applications in the web
portal. Users also do not need to memorize many
accounts, just one account. Thus the organization and
integration of user data can be facilitated so that the
security of user data is more guaranteed because the
place used for storing user data becomes systematic
and centralized.
Therefore, one of the solutions to the problems
obtained for the centralized user authentication
system to access all applications at the Manado State
Polytechnic is expected to be implemented by
conducting SSO Technology Analysis with the
application of CAS at the Manado State Polytechnic,
where this research can help users more efficiently
and safely in accessing all existing applications.
From the explanation of the background above,
what can find problems can be discussed and studied
together? The authors formulate the problem in this
study, namely the use of Single Sign On System
Technology Analysis (SSO) with the Central
Authentication Service (CAS) application to access
web applications. Centrally in the system within the
Manado State Polytechnic.
2 PROPOSED METHOD
2.1 Action Research
Action research aims to develop the most efficient
work methods so that what can reduce production
costs and the productivity of institutions can be
increased. Action Research, or Action Research,
according to Davison, Martinsons, and Kock, is
action research that describes, interprets and explains
a social situation or, at the same time, makes changes
or interventions with the aim of improvement or
participation. The stages of research that are part of
this Action Research are:
1. Diagnosing: Identifying existing problems in
previous research becomes the basis for groups
or organizations so that further changes occur.
2. Action Planning: Understanding the main
problem, then developing an appropriate action
plan to solve the existing problem.
3. Action Taking: This action plan is expected to
solve the problem at the implementation stage.
4. Evaluating: The implementation results are
evaluated after the implementation period is
deemed sufficient.
Specifying Learning: This stage is the final part
that has been passed after the criteria in the learning
principle so that the research can end by reviewing
the stages.
2.2 Data Collection
In the data collection method, the authors obtain data
and information in the following ways:
1. Observation: Researchers directly reviewed the
Manado State Polytechnic for the UPT-IT,
which is the centre of the campus information
system.
2. Interview: At this stage, questions are submitted
to UPT-IT Manado State Polytechnic to get
accurate and direct information and data from
sources who know about the research conducted
by the author.
3. Literature: In this literature study, data is
obtained by searching and obtaining materials
on the internet, libraries and journals and books
that are by the object to be studied by the author.
2.3 Design System
The design of the Single Sign On (SSO) system in this
study is described by using a flowchart, as shown in
Figure 1. Starting with login access to the system, it
will then be checked if the user is registered or not. If
not, it is necessary to input the application username
and password and proceed to the SSO registration and
Single Sign On (SSO) System with Application of Central Authentication Service (CAS) at Manado State Polytechnic
699
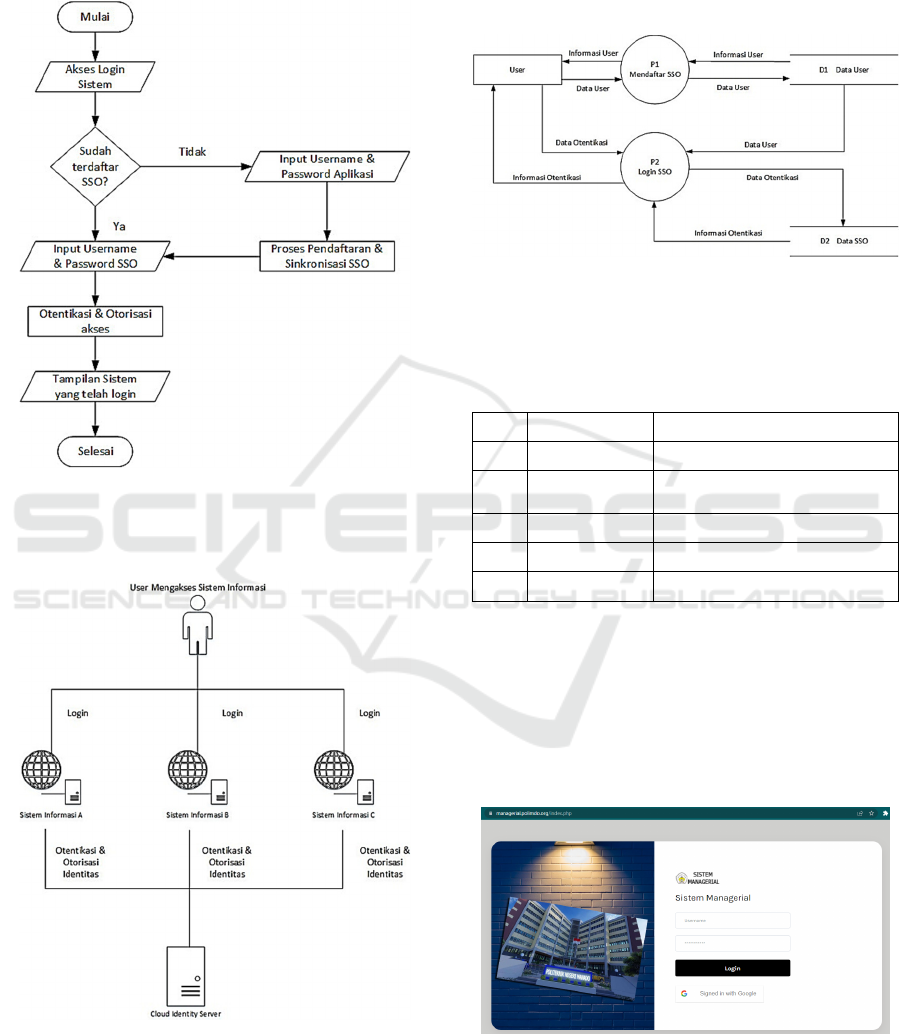
synchronization process. If registered, you will input
data as an SSO username and password. The next step
is authentication, and access authorization will then
be followed by a display to the system.
Figure 1: Flowchart System Single Sign On (SSO).
Furthermore, the depiction of the use case in the
Single Sign On (SSO) System is shown in Figure 2.
Figure 2: Usecase Single Sign On (SSO).
Figure 2 illustrates a user who can log into several
information systems. All authentication and identity
authorizations are stored on one server.
Figure 3 shows the context diagram of the Single
Sign On (SSO) System. First, the user needs to
register to the system so that they can store the data
in the user database. Furthermore, the user can
perform the login process and who will authenticate
the data first.
Figure 3: Single Sign On (SSO) Context Diagram.
The server specifications used in this study are presented
in table 2.
Table 1: Server Specifications.
No Name Specifications
1 Monitor 14 Inch FHD IPS Anti Glare
2 Processor AMD Ryzen 3 3200U
(2.6GHz up to 3.5GHz)
3 Graphics Radeon Vega 3 Graphics
4 Memory 8GB DDR4
5 Storage 512GB SSD
3 RESULT
The study's results of testing Single Sign On (SSO)
First, they test the organizational information system
using Google email as Single Sign On authentication.
Figure 4 shows the login display of the system.
Figure 4: Managerial System Login Display.
If the option to log in with Google is selected, a
display will appear, as shown in Figure 5.
iCAST-ES 2022 - International Conference on Applied Science and Technology on Engineering Science
700

Figure 5: Google Login Page.
If the email is not connected to any account, a
message will appear that there is no account
connected to the email, and then you must activate
Single Sign On in the settings menu.
Figure 6: Email not connected to SSO.
Emails linked to more than one message will appear
stating that more than one account is linked to that
email, so it is necessary to log in and change the email
in one of the accounts. As shown in figure 7.
Figure 7: Email connected to more than one account.
If you have more than one account connected to the
email that has been used, you must use another email,
as shown in Figure 8.
Figure 8: Multiple accounts are linked by email.
If you change your email to an email that has never
been used, a description will appear, as shown in
Figure 9.
Figure 9: Change the mail with an email that has never been
used.
The results of this study are also presented in the form
of a test table, as shown in table 2.
Table 2: System Testing.
Testing Scenario Test Method Expected Results Test Result Conclusion
SSO login with the condition
that you have added Google
email data to the
organizational information
system and there is no
duplicate email on other
accounts.
Press the "Signed in with
Google" button, then log in
using the google account that
has been registered in the
organizational information
system.
Displays the page according to
the access rights and with the
appropriate account session
Correct Normal
SSO login with the email
condition added is not
registered in the organizational
information system.
Press the "Signed in with
Google" button, then log in
using a google account that
never registered in the
organizational information
system.
If no account is connected to
your email, please log in and
activate Single Sign On in the
Settings menu.
Correct Normal
SSO login with email
conditions registered in 2
different accounts but have the
same email
Press the "Signed in with
Google" button, then log in
using a google account that
never registered in the
organizational information
system.
If you have more than one
account linked to this email,
please log in and change your
email in one of the accounts!
Correct Normal
After successfully logging in,
change the email with the
email that has been registered
in another account
Login to the organizational
information system, then open
the settings menu and change
email with an email that
another account has used.
Please use another email if you
have more than one account
linked to this email. Correct Normal
After successfully logging in,
change the email to an email
that has not been registered in
another account
Login to the organizational
information system, open the
settings menu and change
email with an email not used
by another account.
Successfully updated profile,
thank you!
Correct Normal
Single Sign On (SSO) System with Application of Central Authentication Service (CAS) at Manado State Polytechnic
701

SSO makes it possible for users to perform logins that
can be accepted by several separate applications.
With the SSO method, admins can manage users
centrally.s
4 CONCLUSION
The results of research on creating a Single Sign On
(SSO) system based on the Central Authentication
Service (CAS) at the Manado State Polytechnic can
be divided into several parts.
1. The implementation of Single Sign helps portal
users On because it can make it easier for users.
Users do not need to use multiple accounts, only
by using one account that the system has
authenticated.
2. Single Sign On also helps organise users
because the Lightweight Data Access Protocol
(LDAP) is used as a single data user.
ACKNOWLEGMENT
Thank you to the Manado State Polytechnic for facilitating
this research activity and all those who have helped so that
we can complete this research correctly.
REFERENCES
Asosiasi Penyelenggara Jasa Internet Indonesia (APJII).
http://www.apjii.or.id/v2/index.php/read/page/halama
n-data/9/statistik.html. Diakses 29 Juli 2022.
Central Authentication Service (CAS). www.jasig.org/cas.
Diakses 29 Juli 2022
Cartealy, Imam. (2013). Linux Networking. Jakarta:
Jasakom.
Dian, Novera. (2013). Single Sign On (SSO) dengan
Menggunakan Lightweight Directory Access Protocol.
Palembang, Universitas Bina Darma.
Emarketer. (2013). “Asia-Pasific: Digital Ad Spending
Share WorldWide, by Region, 2010- 2016”.
https://www.emarketer.com/Cover age/Asia-Pacific.aspx.
Diakses 28 Juli 2022.
Jian Hu, Qizhi Sun and Hongping Chen, "Application of
Single sign-on (SSO) in Digital Campus," 2010 3rd
IEEE International Conference on Broadband Network
and Multimedia Technology (IC-BNMT), 2010, pp.
725-727, doi: 10.1109/ICBNMT.2010.5705185.
Kasahara, Y., Shimayoshi, T., Ito, E. and Fujimura, N.,
2018, September. The Past, Current, and Future of Our
Email Services in Kyushu University. In Proceedings of
the 2018 ACM SIGUCCS Annual Conference (pp. 103-
106).
Radha, V. and Reddy, D.H., 2012. A survey on single sign-
on techniques. Procedia Technology, 4, pp.134-139.
Rudy, dan Riechie, Odi Gunadi. (2009). Integrasi Aplikasi
Menggunakan Single Sign On Berbasiskan Lightwight
Directory Access Protocol (LDAP) dalam Portal
binus@ccess (BEE-PORTAL). Jakarta, Universitas
Bina Nusantara.
S. Binu, M. Misbahuddin and P. Raj, "A Single Sign on
based secure remote user authentication scheme for
Multi-Server Environments," International Conference
on Computing and Communication Technologies,
2014, pp. 1-6, doi: 10.1109/ICCCT2.2014.7066715.
Saputro, Muhammad Yanuar Ali. (2012). Jurnal
Implementasi Sistem Single Sign On/Single Sign Out
Berbasis Central Authentication Service Protocol pada
Jaringan Berbasis Lightweight Directory Access
Protocol. Universitas Diponegoro.
T. Saroinsong, M. A. S. Kondoj, G. Kandiyoh, and G.
Pontoh, “Design and Implementation of Integrated
Software Research and Community Service at State
Polytechnic of Manado,” J. Phys. Conf. Ser., vol. 953,
p. 012037, Jan. 2018, doi: 10.1088/1742-
6596/953/1/012037.
Xin, L., Liang, L. and Yong, D., 2010, October. Email
information integration with sso in portal service based
on ajax. In 2010 International Conference on Computer
Application and System Modeling (ICCASM 2010)
(Vol. 12, pp. V12-544). IEEE.
iCAST-ES 2022 - International Conference on Applied Science and Technology on Engineering Science
702
