
Achieving Private Verification in Multi-stakeholder Environment and
Application to Stable Matching
Toru Nakamura
a
, Hiroki Okada
b
, Kazuhide Fukushima and Takamasa Isohara
KDDI Research, Inc., 2-1-15, Ohara, Fujimino-shi, Saitama-ken, Japan
Keywords:
Verification, Privacy, Multi-Stakeholder Environment.
Abstract:
Services to support decision-making, such as resource allocation and recommendations, are becoming pop-
ular and essential. This paper focuses on two-sided matching as a form of decision-making support. The
stable marriage problem has been thoroughly studied as an exciting research topic related to two-sided match-
ing. Stability is a property in which there is no man and woman who would agree to leave their assigned
partner, and this property is recognized as an ideal condition for participants. This paper assumes a system
where participants provide their preference orders to an assignee, and the assignee provides them with a stable
matching. When considering a multi-stakeholder environment, not only the participants’ requirements but also
the assignee’s intention should be respected. That is, the assignee should be given the discretion to select the
matching which is the best for the assignee among all the stable matchings. However, there is a possibility that
if the assignee is malicious, he/she falsifies and provides an unstable matching in order to maximize his/her
benefit with ignoring the participants’ requirements. It is difficult for the participants to detect it if they want
to keep their preference orders secret from others. This paper proposes a solution of protocol including a
private verification algorithm to judge whether the received matching is stable while keeping their preference
orders private. The proposed protocol is based on fully homomorphic encryption (FHE) and assumes the use
of a semi-honest third-party server. This paper also proposes a general solution that does not limit to specific
requirements from participants.
1 INTRODUCTION
Services to support decision-making, such as resource
allocation and recommendation, are becoming popu-
lar and essential. The stable marriage problem (Gale
and Shapley, 1962) has been throughly studied as a re-
search topic related to decision-making. Informally,
a stable matching is a one-to-one pairing of a set
of men to a set of women, containing no man and
woman who would agree to leave their assigned part-
ners. This paper assumes a system where participants
provide preference orders to an assignee, and the as-
signee provides a stable matching. When discussing
stable matching, we only discuss whether the partici-
pants’ requirements are satisfied while never consid-
ering the intention of the assignee. On the other hand,
in the context of the recommendation system, discus-
sion has begun on the multi-stakeholder environment,
where not only end-users’ requirements but also those
of other stakeholders such as item providers and sys-
a
https://orcid.org/0000-0003-2530-648X
b
https://orcid.org/0000-0002-5687-620X
tem operators are considered (Abdollahpouri et al.,
2020). In this paper, we discuss the issues involved
in providing stable matchings in the multi-stakeholder
environment.
For example, efficient, stable matching algorithms
are used to assign graduating medical students to resi-
dency programs at hospitals in the real-world
1
. In this
case, participants, that is, students and hospitals, pro-
vide their preference orders to an assignee and expect
to receive a stable matching which is decided based
on their preference orders. Here, the assignee may
have another motivation beyond just providing a sta-
ble matching, for example, solving the issue of how to
reduce labor shortages in rural areas. When respect-
ing the assignee’s motivation, an assignee should be
given the discretion to select the matching which is
the best for the assignee among all the stable match-
ings. However, there is a possibility that if the as-
signee is malicious, he/she falsifies and provides an
unstable matching in order to maximize his/her own
1
National Resident Matching Program (NRMP).
http://www.nrmp.org/
768
Nakamura, T., Okada, H., Fukushima, K. and Isohara, T.
Achieving Private Verification in Multi-stakeholder Environment and Application to Stable Matching.
DOI: 10.5220/0011995800003467
In Proceedings of the 25th International Conference on Enterprise Information Systems (ICEIS 2023) - Volume 1, pages 768-775
ISBN: 978-989-758-648-4; ISSN: 2184-4992
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)

benefit. Though participants can easily detect such
falsification if they can share their preference order, it
may be difficult because of privacy concerns.
There is existing work on private stable matching
algorithms, first introduced by Golle (Golle, 2006),
based on the Gale-Shapley algorithm with secure
multiparty computation (MPC). These proposals can
achieve participants’ privacy from other participants
and matching authorities. There is no assignee in this
setting; participants and matching authorities collabo-
rate to execute pre-defined matching algorithms such
as the Gale-Shapley algorithm. However, this setting
may be unrealistic in a business context; naturally, an
assignee would seek benefit commensurate with the
effort of attracting participants to the matching ser-
vice.
1.1 Contributions
The contribution of this paper is to propose a protocol
that satisfies the following requirements. More gener-
ally, we will use “user,” “private input,” and “server”
instead of “participant,” “preference order,” and ”as-
signee,” respectively, in the rest of the paper.
1. Verifiability: Users can accept a result obtained
from the server if and only if the result satisfies
the users’ requirements.
2. Privacy: The adversary can not obtain any infor-
mation about the private inputs of the users.
3. Selectability: The server can freely choose a re-
sult from among all the results candidates.
We propose a protocol that satisfies the three re-
quirements, verifiability, privacy, and selectability,
with a semi-honest third-party server, called a veri-
fier and fully homomorphic encryption (FHE). FHE
is cryptography that allows the operation of any func-
tions for encrypted data. We first show a general con-
struction of this protocol which does not limit specific
requirements from users but assumes that the verifi-
cation algorithm of the requirement is available on
FHE. Furthermore, we show a specific implementa-
tion of an FHE-based verification algorithm for two-
sided matching that checks whether matching is stable
while users’ private inputs kept secret.
Note that we do not consider the server to be an
adversary to privacy requirements in this paper; there-
fore, we do not regard the server knowing the private
inputs of the users as a privacy issue. Even if we can
exclude the server as a potential adversary of the pri-
vacy requirement, it is still worth discussing even in
this problem setting because no simple solution satis-
fies all of the above requirements.
HEREHEREHERE
1.2 Organization
The remainder of the paper is organized as follows.
Section 2 describes the existing work related to this
paper. Section 3 provides the mathematical model
for our protocol and defines the requirements of the
protocol. Section 4 describes the proposed general
construction of the protocol. Section 5 provides the
specific implementation of our solution for the stable
matching problem. Section 6 presents the discussion,
and Section 7 concludes this paper.
2 RELATED WORK
Homomorphic encryption (HE) is a type of cryptog-
raphy that allows a third party (e.g., cloud service
provider) to perform some mathematical operations
on encrypted data without compromising the encryp-
tion (Acar et al., 2018). In particular, fully homomor-
phic encryption (FHE), which can perform arbitrary
operations an arbitrary number of times, has been ac-
tively studied. Its practicality has been improved sig-
nificantly since Gentry (Gentry, 2009) first proposed
FHE. In this paper, we propose methods based on
FHE.
Verifiable computation is a method that enables a
user to offload the computation of a function π to an-
other untrusted party. The user can verify whether the
received result is truly π(x) at a lower cost than exe-
cuting π(x) by the user himself (Parno et al., 2013).
However, this technique cannot solve the issue ad-
dressed in this paper because users cannot know π in
advance to realize selectability.
The stable marriage problem is a well-known
problem; informally, a stable matching is a one-to-
one pairing of a set of men to a set of women,
containing no man and woman who would agree to
leave their assigned partners. Gale and Shapley pro-
posed an efficient algorithm to find male-dominated
(or female-dominated) stable matching (Gale and
Shapley, 1962). Golle proposed the first private sta-
ble matching algorithm based on the Gale-Shapley
algorithm, where if a majority of matching authori-
ties are honest, the protocol correctly outputs a stable
matching and reveals no other information than what
can be learned from that match and the preferences
of participants controlled by the adversary (Golle,
2006). Franklin et al. pointed out that Golle’s al-
gorithm includes a failure in the communication cost
and proposed a modified version of the algorithm
based on threshold additive homomorphic encryp-
tion (TAHE) and secret sharing (SS) (Franklin et al.,
2007). Franklin et al. also proposed two more ef-
Achieving Private Verification in Multi-stakeholder Environment and Application to Stable Matching
769

fective algorithms; one is based on private informa-
tion retrieval (PIR) in addition to TAHE and SS, and
the other is based on secure multiparty computation
(MPC) and the Naor-Nissim protocol. Teruya and
Sakuma proposed a more effective algorithm based
solely on TAHE (Teruya and Sakuma, 2015). Doerner
et al. (Doerner et al., 2016) and Riazi et al. (Riazi
et al., 2017) proposed practical private stable match-
ing with Oblivious RAM (ORAM). This technique is
effective if the algorithm to find a specific matching is
determined in advance without considering the exis-
tence of a server that manages participants. However,
this technique is not suitable for the problem setting
of this paper because the requirement in this paper is
selectivity, which guarantees the freedom to choose
among the matches that satisfy stability for the server.
3 MODEL AND REQUIREMENTS
In this section, we define the mathematical model and
the requirements for the discussion in this paper. In
addition, the issues of existing methods are summa-
rized from the above viewpoints. The mathematical
model assumes applications that can calculate results
from only user inputs.
3.1 Model
Let n be the number of users. Each user has his/her
private inputs x
1
,... x
n
, respectively, where user i’s in-
put is x
i
∈ X. We assume that the users require a server
S to provide a result y ∈ Y for inputs x
1
,. .. ,x
n
that sat-
isfies a requirement L, where Y is the set of possible
ranges of y. L can be represented by L ⊆ X ×···×X ×
Y , that is, the requirement of users is to get a result y
such that (x
1
,. .. x
n
,y) ∈ L. We assume that a server
S chooses and provides y to the users. The server is
expected to return y such that (x
1
,. .. ,x
n
,y) ∈ L from
the users; however, if the server is malicious, it may
choose y
0
that is (x
1
,. .. ,x
n
,y
0
) /∈ L.
Users communicate and execute a protocol with
the server, and in some cases a third-party server, and
obtain a result from the server. We assume that there
exists an efficient verification algorithm V , that out-
puts 1 if (x
1
,. .. ,x
n
,y) ∈ L, otherwise, outputs 0.
3.2 Requirements
We show the requirements of our proposed protocol
as follows.
1. Verifiability: the users can accept the result
y for private inputs x
1
,. .. x
n
if and only if
(x
1
,. .. x
n
,y) ∈ L.
2. Privacy: the protocol reveals no information about
users’ private inputs to the adversary.
3. Selectability: The server S can choose any y ∈ Y .
In other words, server S does not need to fix the
algorithm to be executed in advance.
In this paper, we do not consider the server as
an adversary for privacy requirements; therefore, the
server is allowed to know the private inputs of users,
i.e., we do not regard that as a privacy issue. In the
next section, we will propose a protocol with an ad-
ditional third-party verification server, called verifier.
Therefore, it is necessary to regard the other users and
the verifier as potential adversaries for the privacy re-
quirement in this case. We also consider the assumed
adversaries as semi-honest (passive) adversaries. This
setting is not designed to achieve the most desirable
level of privacy, that is, this is a weaker assumption
than that of a malicious (active) adversary. Neverthe-
less, this study is still worthwhile because the semi-
honest adversary model is generally considered a rea-
sonable assumption. The most important point of this
paper is to discuss protocols that simultaneously real-
ize verifiability, privacy, and selectability. Achieving
stricter privacy requirements will be subject of our fu-
ture work.
3.3 Issues of Naive Methods
In this section, we introduce two naive protocols that
do not require any novelty without the assumption of
a secure communication channel, and describe their
issues.
3.3.1 Naive 1: Not Shared among Users
STEP 1. Each user i sends x
i
∈ X to the server S via
a secure channel.
STEP 2. S selects any y ∈ Y and sends it to each user.
STEP 3. Each user accepts y.
The naive 1 method satisfies privacy and selectability,
however, it does not satisfy verifiability because the
users accept any y even if (x
1
,. .. x
n
,y) /∈ L.
3.3.2 Naive 2: Shared among Users
STEP 1. Each user i sends x
i
∈ X to the server S via
a secure channel.
STEP 2. S selects any y satisfying (x
1
,. .. x
n
,y) ∈ L
and sends it to each user.
STEP 3. Each user i shares x
i
with other users and
executes r ← V (x
1
,. .. x
n
,y). i accepts y if
r = 1, otherwise, rejects y.
ICEIS 2023 - 25th International Conference on Enterprise Information Systems
770

The naive 2 method satisfies verifiability and se-
lectability, however, it does not satisfy privacy be-
cause the users share their private inputs.
4 GENERAL CONSTRUCTION
In this section, we show the general construction of a
protocol that simultaneously satisfies verifiability, pri-
vacy, and selectivity with a semi-honest verifier and
FHE. The general construction does not limit any spe-
cific requirement from users but assumes that the ver-
ification algorithm of the requirement is available on
FHE.
4.1 Fully Homomorphic Encryption
(FHE)
FHE can perform arbitrary operations for an arbi-
trary number of times, We show the definition of FHE
(Brakerski and Vaikuntanathan, 2011)(Acar et al.,
2018) as follows.
Definition 1. Fully Homomorphic En-
cryption FHE is a quintet of algorithms
(Setup,Keygen, Enc,Dec, Eval) which satisfies
authenticity, compactness, and security.
• Setup params ← Setup(1
λ
): outputs a public pa-
rameter param.
• Key Generation (pk,sk) ← Keygen(param): out-
puts public encryption key pk and secret decryp-
tion key sk.
• Encryption c ← Enc(pk, µ): encrypts a message
µ ∈ {0, 1} with pk and outputs a cyphertext c.
• Decryption µ ← Dec(sk, c): decrypts cyphertext
c with sk and outputs µ.
• Homomorphic Evaluation ˆc ←
Eval(C ,(c
1
,. .. c
`
),pk): computes any circuit
C : {0,1}
`
→ {0,1} to c
1
,. .. c
`
with pk and
outputs ˆc.
Authenticity is the property that any ciphertext
obtained by the encryption algorithm and the homo-
morphic evaluation algorithm can be decrypted cor-
rectly. Compactness is the property that the size of
a ciphertext after homomorphic evaluation does not
depend on the size of the circuit in which an op-
eration is performed. Security is the property that
the attack success rate is negligibly small for any
given attacker. See (Brakerski and Vaikuntanathan,
2011)(Acar et al., 2018) for the details of definitions.
Obviously, it is possible to construct a fully homo-
morphic encryption for any algorithm, if it is possible
to homomorphically compute any circuit.
Therefore, we redefine the FHE as follows. Here-
inafter, when we refer to the FHE, the following defi-
nition will be applied.
Definition 2. Fully Homomorphic En-
cryption FHE is a quintet of algorithms
(Setup,Keygen, Enc,Dec, Eval) which satisfies
authenticity, compactness, and security.
• Setup params ← Setup(1
λ
): outputs a public pa-
rameter param.
• Key Generation (pk,sk) ← Keygen(param): out-
puts public encryption key pk and secret decryp-
tion key sk.
• Encryption c ← Enc(pk, µ): encrypts a message
µ ∈ X with pk and outputs a cyphertext c.
• Decryption µ ← Dec(sk, c): decrypts cyphertext
c with sk and outputs µ.
• Homomorphic Evaluation ˆc ←
Eval(A,(c
1
,. .. c
n
),d,pk): computes any al-
gorithm A : X × ··· × X × Y → {0, 1} with
ciphertexts c
1
,. .. c
n
, and d, and public encryption
key pk and outputs ˆc.
If for 1 ≤ i ≤ n, c
1
i
← Enc(pk, x
i
), c
2
←
Enc(pk, y), ˆc ← Eval(A,(c
1
1
,. .. c
1
n
),c
2
,pk), then
Dec(sk, ˆc) = A((x
1
,. .. x
n
),y) from the property of au-
thenticity.
4.2 Proposed FHE-based Protocol
Here, we show a protocol which satisfies all the re-
quirements in the general setting. We assume that
there exists a verification algorithm V that outputs 1
if (x
1
,. .. ,x
n
,y) ∈ L, otherwise, outputs 0, and the ho-
momorphic evaluation algorithm on V is available.
STEP 1. Let i ∈ {1,...n} be the representative of
users. i executes Setup(1
λ
), obtains param,
and publishes it.
STEP 2. i executes Keygen(param) and obtains
(pk,sk). i publishes pk and distributes sk
to all users.
STEP 3. Each user i sends x
i
∈ X to the server S via
a secure channel.
STEP 4. S selects any y ∈ Y and sends it to each user.
STEP 5. Each user i sends c
1
i
← Enc(pk, x
i
) and y
(practically all it takes is one user (e.g. i)
sends c
2
← Enc(pk, y)) to the verifier D via
a secure communication channel.
STEP 6. D executes r
0
← Eval(V, (c
1
,. .. ,c
n
),c
2
,pk)
and sends r
0
to each user.
STEP 7. Each user i executes r ← Dec(r
0
,sk) and i
accepts y if r = 1, otherwise, i rejects y.
Achieving Private Verification in Multi-stakeholder Environment and Application to Stable Matching
771

Verifiability is achieved because each user can ob-
tain r = V (x
1
,. .. ,x
n
,y) by the property of authenticity
in FHE. Selectivity is achieved because S can select
any y ∈Y . Regarding privacy, as mentioned in the pre-
vious section, we assume that the adversary is semi-
honest, that is, passive, hence what the adversary can
obtain is at most pk,{c
1
1
,. .. ,c
1
n
},c
2
. The adversary
can not obtain any information from this because of
the property of security in FHE.
5 APPLICATION TO STABLE
MATCHING
In this section, we show a specific implementation of
a protocol including an FHE-based verification algo-
rithm for stable matching. Although FHE can theo-
retically be used to compute any algorithms with en-
crypted data, the implementation methods are non-
trivial. We focus on the case of the stable matching
and discuss the method for implementing the verifi-
cation algorithm on FHE and its efficiency.
5.1 Definition of Stable Matching
The stable marriage problem is well known as the
problem of finding stable matching, as shown in (Gale
and Shapley, 1962). Informally, a stable matching is a
one-to-one pairing of a set of men to a set of women,
containing no man and woman who would agree to
leave their assigned partners.
An instance of a matching consists of two disjoint
sets where the number of elements is n, and set M is
men and the set W is women. Each person has a strict
total order, called the preference order, on members
on the other side. A matching M is a pair of M and
W , that is, M ⊆ M ×W . If (m,w) ∈ M , we denote
M (m) = w,M (w) = m. The rank of w in m’s pref-
erence order is denoted by P
m
(w), and it is called w’
preference rank in m. In the same way, m’ preference
rank in w is denoted by P
w
(m). If a person p prefers
a to b in an instance I , we denote a
p
b in I .
Definition 3. Given a matching M , a pair of a man
and a woman (m,w) is a blocking pair for M if all
the following conditions are met;
1. (m
0
,w
0
) ∈ M and m
0
∈ M,w
0
∈ W ,
2. w
0
m
0
M (m
0
),
3. m
0
w
0
M (w
0
).
Definition 4. A matching M is stable if M has no
blocking pair.
5.2 Stability Checking Algorithm
Various studies have been conducted on algorithms to
find stable matching. Gale and Shapley proved that
at least one stable matching exists for all instances
and gave an efficient algorithm to find a stable match-
ing (Gale and Shapley, 1962). Gale-Shapley’s algo-
rithm is called the man-optimal algorithm because ev-
ery man has the best partner he can have in any sta-
ble matching, but every woman has the worst part-
ner. If applied with the roles of men and women re-
versed, the algorithm serves as the woman-optimal
algorithm. Algorithms for finding stable matching
based on optimizations different from that of Gale-
Shapley’s one have also been studied, such as egali-
tarian stable matching, minimum regret stable match-
ing (Irving et al., 1987), and sex-equal stable match-
ing (Kato, 1993).
On the other hand, to the best of our knowldege,
few studies have been conducted on stability check-
ing algorithms. A simple and efficient (O(n
2
)) sta-
bility checking algorithm (shown in Algorithm 1) is
described in (Gusfield and Irving, 1989); hence we
construct the implementation of our protocol based
on this algorithm.
Algorithm 1: Standard stability checking algorithm.
1: for m ← 1 to n do
2: for each w such that m prefers w to M (m) do
3: if w prefers to m to M (w) then
4: return 0
5: break
6: end if
7: end for
8: end for
9: return 1
A critical issue with implementing FHE is that
the results of conditional expressions in conditional
branchings cannot be known. Therefore, the stability
checking algorithm is modified not to use any condi-
tional branchings in our implementation.
5.3 Specific Implementation
Some open-source software libraries implement ho-
momorphic encryption such as HElib
2
. Such libraries
provide essential functions for homomorphic evalua-
tions. We provide a specific implementation of the
stability checking algorithm with the essential func-
tions from libraries such as HElib. The essential
2
HElib Documentation, https://homenc.github.io/
HElib/
ICEIS 2023 - 25th International Conference on Enterprise Information Systems
772
functions which are used for our implementation are
shown as follows.
1. Addition of two integers: ADD(x,y) outputs x+y,
where x and y are integers.
2. Multiplication of an integer and a bit: MULT(x,y)
outputs x if y = 1, otherwise outputs 0, where x is
an integer, y is a bit.
3. Comparison of two integers: COMP(x, y) outputs
1 if x < y, otherwise outputs 0, where x and y are
integers.
4. AND of two bits
5. OR of two bits
6. NOT of a bit
In order to execute our protocol, some prelim-
inary steps are required. First, the users’ pri-
vate inputs, which in this case are preference or-
ders, are converted to lists of preference ranks.
That is, m
i
’s list can be denoted by L
m
i
=
(P
m
i
(w
1
),P
m
i
(w
2
),. .. ,P
m
i
(w
n
)) and w
i
’s list can be
denoted by L
w
i
= (P
w
i
(m
1
),P
w
i
(m
2
),. .. ,P
w
i
(m
n
)).
The private inputs of the list are encrypted element-
by-element of the list, that is, the cyphertext from m
i
to the verifier is c
m
i
= (c
m
i,1
,c
m
i,2
,. .. c
m
i,n
), where c
m
i, j
←
Enc(pk,P
m
i
(w
j
)).
The matching result y sent to the verifier is repre-
sented by a pair (y
m
,y
w
) of lists of one-hot-vectors. If
the partner of m
i
is w
j
(that is, M (m
i
) = w
j
), let y
m
i
be a n-bit strings where j th bit y
m
i
[ j] is only 1 and
all the others 0. In the same way, if M (w
i
) = m
j
, let
y
w
i
be a n-bit strings where j th bit y
w
i
[ j] is only 1 and
all the others 0. This may seem redundant since y
w
is
just a permutation of y
m
; however, it is necessary to
construct our protocols using FHE.
We describe the algorithm that can return the
same result as the stability checking algorithm by
only ADD,MULT,COMP,AND,OR,NOT in Algo-
rithm 2.
The computation cost of this algorithm is O(n
2
).
5.4 Example
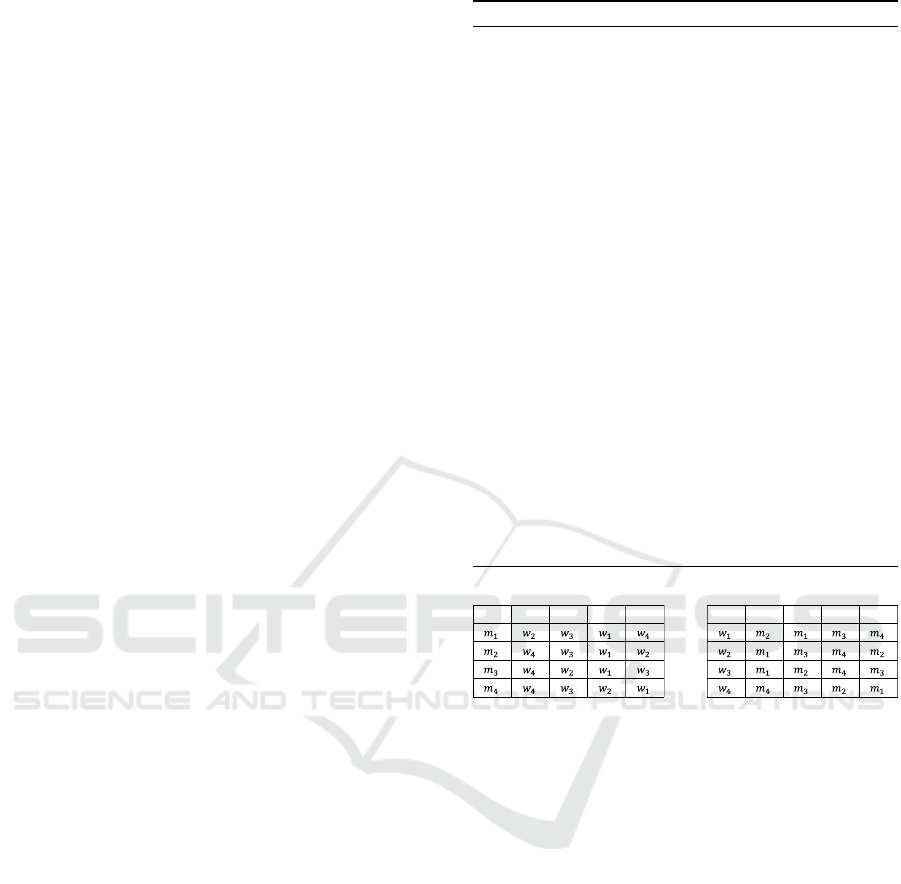
We show an example for a proof sketch of the
proposed algorithm. Let n = 4. Each member’s
preference order is shown in Figure 1. Let M =
{(m
1
,w
3
),(m
2
,w
1
),(m
3
,w
2
),(m
4
,w
4
)}. In this case,
this matching is not stable because (m
1
,w
2
) is block-
ing pair as shown in Figure 2.
In our protocol, the preference orders are
converted to the lists of preference ranks
shown in Figure 3. M is represented by y
m
=
((0,0, 1,0), (1,0,0,0),(0,1,0,0),(0,0,0,1)) and
y
w
= ((0,1, 0,0),(0,0,1,0),(1,0,0,0),(0,0,0,1)).
Algorithm 2: Stability checking algorithm for FHE.
1: r = 0
2: for i ← 1 to n do
3: s
m
= 0
4: s
w
= 0
5: for j ← 1 to n do
6: u
m
= MULT(P
m
i
(w
j
),y
m
i
[ j])
7: s
m
= ADD(s
m
,u)
8: u
w
= MULT(P
w
i
(m
j
),y
w
i
[ j])
9: s
w
= ADD(s
w
,u)
10: end for
11: for j ← 1 to n do
12: e
m
i, j
← COMP(P
m
i
(w
j
),s
m
)
13: e
w
i, j
← COMP(P
w
i
(m
j
),s
w
)
14: end for
15: end for
16: for i ← 1 to n do
17: for j ← 1 to n do
18: t
i, j
← AND (e
m
i, j
,e
w
j,i
)
19: r ← OR(r,t
i, j
)
20: end for
21: end for
22: r = NOT(r)
23: return r
ϭ Ϯ ϯ ϰ ϭ Ϯ ϯ ϰ
Figure 1: An example of preference orders.
The ranks of the pair of each member can be calcu-
lated by multiplication and addition of the preference
ranks and y
m
,y
w
. For example, for m
1
, his preference
rank is (3,1, 2,4) and his pair is w
3
(represented by
(0,0, 1,0)). w
3
’s rank of m
1
’s preference order is
3 · 0 +1 · 0 + 2 · 1 + 4 · 0 = 2.
Next, the ranks of each member in his/her pref-
erence list are compared with the preference rank of
his/her pair. If a rank is smaller than the rank of the
pair, 1 is assigned, otherwise, 0 is assigned as shown
in Figure 4. Here, 1 means a member who is preferred
to the current pair.
Finally, AND function between each row of the
left table and each column of the right table is calcu-
lated as shown in Figure 5. Here, 1 means a blocking
pair. Therefore, the matching is stable if all the ele-
ments of the table are 0, otherwise, it is not stable.
Achieving Private Verification in Multi-stakeholder Environment and Application to Stable Matching
773
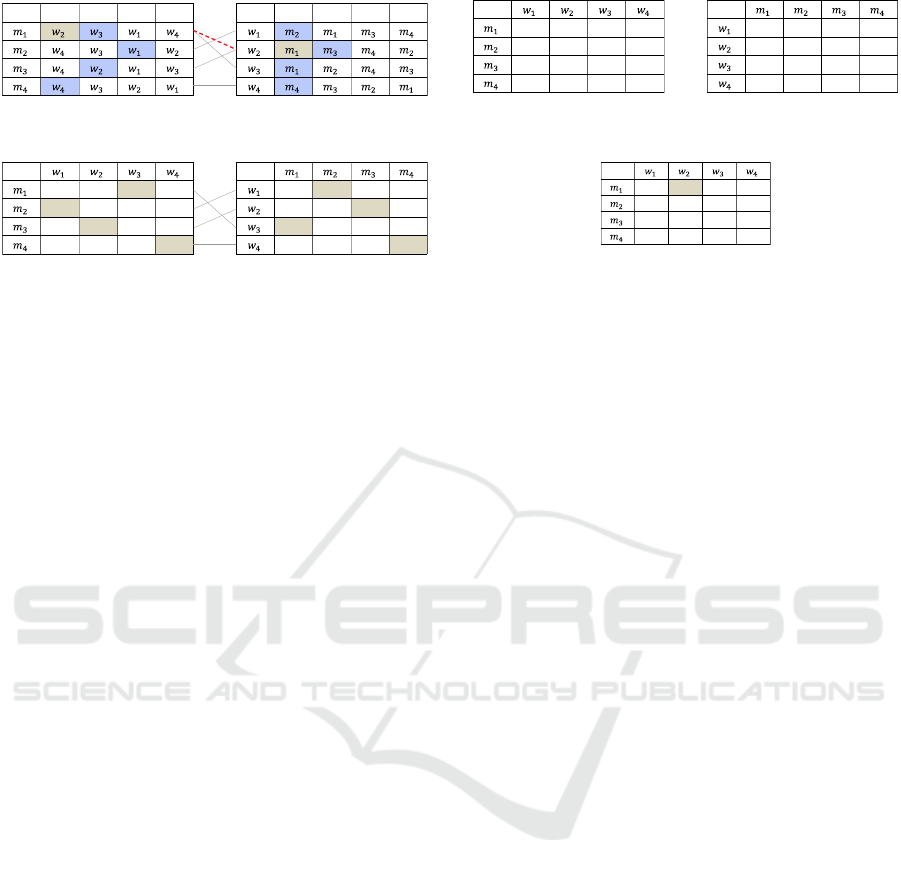
ϭ Ϯ ϯ ϰ ϭ Ϯ ϯ ϰ
ůŽĐŬŝŶŐ
WĂŝƌ
Figure 2: A blocking pair of the example.
ϯ ϭ Ϯ ϰ
ϯ ϰ Ϯ ϭ
ϯ Ϯ ϰ ϭ
ϰ ϯ Ϯ ϭ
Ϯ ϭ ϯ ϰ
ϭ ϰ Ϯ ϯ
ϭ Ϯ ϰ ϯ
ϰ ϯ Ϯ ϭ
Figure 3: Preference ranks.
6 DISCUSSION
The proposed method assumes the use of a semi-
honest verifier. Future directions include (1) the mod-
ification of the methods without the verifier and (2)
the modification for stricter assumptions of an adver-
sary such as a malicious adversary. For the methods
without the verifier, constructing an MPC-based veri-
fication algorithm may be a promising direction.
Sharing FHE private keys among users can be a
privacy risk; hence it is better to be able to use in-
dividual keys. Multi-key FHE or Secure Multiparty
Computation (MPC) (Ohata, 2020) may be a potential
solution for this issue; however, it requires all users to
participate in the verification calculation.
We have shown that the computational complex-
ity of our proposed algorithm is O(n
2
). On the other
hand, the number of bits handled and the depth of
operations also affect the computational cost in the
implementation using FHE. We will implement and
evaluate our protocol and optimize it as future work.
In this paper, we limit the target of the mathemat-
ical model to applications that can calculate results
solely from users’ inputs such as matchings. We will
discuss the FHE implementation of the verification al-
gorithm for a different problem from matching and
the extension for more complex models where param-
eters other than user inputs affect the results.
7 CONCLUSION
In this paper, we focused on a system where partici-
pants provided preference orders to an assignee, and
the assignee provided a stable matching. When con-
sidering a multi-stakeholder environment, not only
the participants’ requirements but also the assignee’s
intention should be respected, that is, the assignee
should be given the discretion to select the match-
Ϭ ϭ Ϭ Ϭ
Ϭ Ϭ ϭ ϭ
Ϭ Ϭ Ϭ ϭ
Ϭ Ϭ Ϭ Ϭ
Ϭ Ϭ Ϭ Ϭ
ϭ Ϭ Ϭ Ϭ
Ϭ Ϭ Ϭ Ϭ
Ϭ Ϭ Ϭ Ϭ
Figure 4: Comparison with the current pair.
Ϭ ϭ Ϭ Ϭ
Ϭ Ϭ Ϭ Ϭ
Ϭ Ϭ Ϭ Ϭ
Ϭ Ϭ Ϭ Ϭ
Figure 5: Existence of blocking pairs.
ing that is the best for him/her among all the sta-
ble matchings, which satisfy the requirements from
participants. In this paper, we proposed a protocol
that satisfies the three requirements, verifiability, pri-
vacy, and selectability, with a semi-honest third-party
server, called a verifier and fully homomorphic en-
cryption (FHE). We first provided a general construc-
tion of this protocol which does not limit specific
requirements from users but assumes that the verifi-
cation algorithm of the requirement is available on
FHE. Furthermore, we proposed a specific implemen-
tation of an FHE-based verification algorithm for two-
sided matching that checks whether matching is stable
while users’ private inputs kept secret.
REFERENCES
Abdollahpouri, H., Adomavicius, G., Burke, R., Guy, I.,
Jannach, D., Kamishima, T., Krasnodebski, J., and
Pizzato, L. (2020). Multistakeholder recommenda-
tion: Survey and research directions. User Modeling
and User-Adapted Interaction, 30(1):127–158.
Acar, A., Aksu, H., Uluagac, A. S., and Conti, M. (2018). A
survey on homomorphic encryption schemes: Theory
and implementation. ACM Computing Surveys (Csur),
51(4):1–35.
Brakerski, Z. and Vaikuntanathan, V. (2011). Efficient
fully homomorphic encryption from (standard) lwe. In
2011 IEEE 52nd Annual Symposium on Foundations
of Computer Science, pages 97–106.
Doerner, J., Evans, D., and shelat, a. (2016). Secure stable
matching at scale. In Proceedings of the 2016 ACM
SIGSAC Conference on Computer and Communica-
tions Security, CCS ’16, page 1602–1613, New York,
NY, USA. Association for Computing Machinery.
Franklin, M., Gondree, M., and Mohassel, P. (2007). Im-
proved efficiency for private stable matching. Lecture
Notes in Computer Science (including subseries Lec-
ture Notes in Artificial Intelligence and Lecture Notes
in Bioinformatics), 4377 LNCS:163–177.
Gale, D. and Shapley, L. S. (1962). College admissions and
ICEIS 2023 - 25th International Conference on Enterprise Information Systems
774

the stability of marriage. The American Mathematical
Monthly, 69:9–15.
Gentry, C. (2009). A fully homomorphic encryption
scheme. STANFORD UNIVERSITY.
Golle, P. (2006). A private stable matching algorithm. In
Proceedings of the 10th International Conference on
Financial Cryptography and Data Security, FC’06,
page 65–80, Berlin, Heidelberg. Springer-Verlag.
Gusfield, D. and Irving, R. W. (1989). The Stable Marriage
Problem: Structure and Algorithms. The MIT Press.
Irving, R. W., Leather, P., and Gusfield, D. (1987). An
efficient algorithm for the “optimal” stable marriage.
Journal of the ACM (JACM), 34(3):532–543.
Kato, A. (1993). Complexity of the sex-equal stable mar-
riage problem. Japan Journal of Industrial and Ap-
plied Mathematics, 10:1–19.
Ohata, S. (2020). Recent advances in practical secure multi-
party computation. IEICE Transactions on Funda-
mentals of Electronics, Communications and Com-
puter Sciences, 103(10):1134–1141.
Parno, B., Howell, J., Gentry, C., and Raykova, M. (2013).
Pinocchio: Nearly practical verifiable computation. In
2013 IEEE Symposium on Security and Privacy, pages
238–252. IEEE.
Riazi, M. S., Songhori, E. M., Sadeghi, A.-R., Schneider,
T., and Koushanfar, F. (2017). Toward practical secure
stable matching. Proceedings on Privacy Enhancing
Technologies, 1:62–78.
Teruya, T. and Sakuma, J. (2015). Round-efficient private
stable matching from additive homomorphic encryp-
tion. In Information Security, pages 69–86. Springer.
Achieving Private Verification in Multi-stakeholder Environment and Application to Stable Matching
775
