
Threshold Cryptosystems Based on 2
k
-th Power Residue Symbols
George Tes¸eleanu
1,2 a
1
Advanced Technologies Institute, 10 Dinu Vintil
˘
a, Bucharest, Romania
2
Simion Stoilow Institute of Mathematics of the Romanian Academy, 21 Calea Grivitei, Bucharest, Romania
Keywords:
Threshold Decryption, Homomorphic Encryption, Gap Residuosity Assumption.
Abstract:
In this paper we introduce a novel version of the Joye-Libert cryptosystem that allows users to decrypt without
knowing the factorisation of the composite modulus. Then we use our construction as a building block for a
threshold decryption protocol of the homomorphic Joye-Libert encryption scheme. Finally, we present several
extensions of the threshold cryptosystem.
1 INTRODUCTION
In classical public key encryption systems, only the
owner of the secret key has the ability to decrypt ci-
phertexts. Unfortunately, if an adversary is able to
break into a system administrator’s computer, for ex-
ample, and steal its secret key, the whole system is
compromised. Since, this type of attack by hackers
or Trojan horses or corrupted insiders becomes more
frequent and more easily to perform, the need to de-
velop a method of distributing trust arises. In order to
address this issue, a possible solution is to distribute
the secret key between several servers and then use
threshold decryption algorithms.
Most previous research has mainly focused
on developing threshold decryption algorithms for
RSA-based schemes (Boneh and Franklin, 1997;
Fouque et al., 2000; Fouque and Pointcheval, 2001;
Damg
˚
ard and Jurik, 2001) and discrete logarithm-
based schemes (Desmedt and Frankel, 1989; Fouque
and Pointcheval, 2001; Pedersen, 1991; Shoup and
Gennaro, 1998; Canetti and Goldwasser, 1999). But
according to (Katz and Yung, 2002; Fouque et al.,
2000; Cramer et al., 2001), there is still a need to de-
sign threshold schemes for many specific cryptosys-
tems. Furthermore, as many have pointed out previ-
ously (Franklin and Haber, 1993; Fouque et al., 2000;
Damg
˚
ard and Jurik, 2001; Katz et al., 2001; Cramer
et al., 2001), threshold homomorphic schemes are
useful for achieving goals such as electronic voting
and efficient multi-party computation. In line with
this reasoning, Katz and Yung (Katz and Yung, 2002)
a
https://orcid.org/0000-0003-3953-2744
developed a threshold cryptosystem based on the
Goldwasser-Micali encryption scheme (Goldwasser
and Micali, 1982; Goldwasser and Micali, 1984).
Moreover, their conversion keeps the homomorphic
properties of the original scheme. The Katz-Yung
scheme is revisited in (Desmedt and Kurosawa, 2007)
with the goal of extending it to composite moduli for
which the Katz-Yung scheme fails.
A rather natural extension of the Goldwasser-
Micali cryptosystem was introduced by Joye and Lib-
ert in (Joye and Libert, 2013) and it was reconsidered
in (Benhamouda et al., 2017). Despite the fact that it
is simple and elegant, the Goldwasser-Micali scheme
is quite uneconomical in terms of bandwidth
1
. Var-
ious attempts of generalizing the Goldwasser-Micali
scheme were proposed in the literature in order to ad-
dress the previously mentioned issue. The Joye-Libert
scheme can be considered a follow-up of the cryp-
tosystems proposed in (Naccache and Stern, 1998;
Cohen and Fischer, 1985) and efficiently supports the
encryption of larger messages. The authors of (Joye
and Libert, 2013) leave as an open problem the exten-
sion of their scheme, starting from (Katz and Yung,
2002), to a threshold decryption scheme.
Having in mind the motivations stated in the pre-
vious paragraphs, in this paper we develop a thresh-
old version of the Joye-Libert cryptosystem (Joye and
Libert, 2013; Benhamouda et al., 2017) that gener-
alizes both the Katz-Yung scheme (Katz and Yung,
2002) and the Desmedt-Kurasawa scheme (Desmedt
1
k · log
2
n bits are needed to encrypt a k-bit message,
where n is a composite modulus as described in (Gold-
wasser and Micali, 1982; Goldwasser and Micali, 1984)
Teŧeleanu, G.
Threshold Cryptosystems Based on 2 k-th Power Residue Symbols.
DOI: 10.5220/0012007600003555
In Proceedings of the 20th International Conference on Security and Cryptography (SECRYPT 2023), pages 295-302
ISBN: 978-989-758-666-8; ISSN: 2184-7711
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)
295

and Kurosawa, 2007). Note that our generalization
conserves the homomorphic property of the Joye-
Libert cryptosystem.
Another important problem that we address is
proving the security of our threshold decryption
scheme against chosen ciphertexts attacks (see the full
paper). This topic was tackled by Katz and Yung
for their scheme (Katz and Yung, 2002). More pre-
cisely, they applied the generic conversion method
from (Fouque and Pointcheval, 2001) that uses two in-
dependent encryption runs and a non-interactive zero-
knowledge proof that the resulting ciphertexts contain
the same message. Although, Katz and Yung pro-
vide such a proof system, they do not formally prove
it secure. On the other hand, Desmedt and Kura-
sawa (Desmedt and Kurosawa, 2007) simply state
that proving the chosen ciphertexts security for their
scheme is quite complex, and thus they only focus on
semantic security. Therefore, we wanted to fill these
gaps. When we tried to directly generalize Katz and
Yung’s proof, we ended up with a cumbersome pro-
tocol. Hence, starting from the examples described
in (Fouque and Pointcheval, 2001) and the signature
protocol from (Girault et al., 2006), we constructed
a novel non-interactive zero-knowledge proof that is
suitable for our threshold scheme and then we prove
it secure. Note that our proof is also suitable for the
Katz-Yung and Desmedt-Kurasawa schemes.
Full Version. The full version of the paper can be
found here (Tes¸eleanu, 2023).
Structure of the Paper. In Section 2 we intro-
duce notations, definitions, security assumptions and
schemes used throughout the paper. Inspired by the
Joye-Libert encryption scheme, in Section 3 we pro-
pose a new scheme based on 2
k
residues, prove it
secure in the standard model and analyze its perfor-
mance compared to other related cryptosystems. A
threshold version of our scheme is proposed in Sec-
tion 4. We conclude in Section 5.
2 PRELIMINARIES
Notations. Throughout the paper, λ denotes a se-
curity parameter. We use the notation x
$
←− X when
selecting a random element x from a sample space X.
We denote by x ← y the assignment of the value y to
the variable x. The probability that event E happens
is denoted by Pr[E].
The Jacobi symbol of an integer a modulo an inte-
ger n is generally represented by J(a, n). J
n
and
¯
J
n
de-
note the sets of integers modulo n with Jacobi symbol
1, respectively −1. Throughout the paper, we let QR
n
be the set of quadratic residues modulo n. We define
the alternative representation of integers modulo an
integer p as Z
p
= {−(p − 1)/2,. ..,−1,0, 1,. .., (p −
1)/2}. The set of integers {0,. .. ,a − 1} is further
denoted by [0,a). For shorthand, we denote the set
[0,a + 1) by [0,a]. Multidimensional vectors v =
(v
0
,. .., v
s−1
) are represented as v = {v
i
}
i∈[0,s)
.
2.1 Number Theoretic Prerequisites
The Legendre symbol can be generalized to higher
powers in several ways. We further consider the 2
k
-
th power residue symbol as presented in (Yan, 2002).
The classical Legendre symbol is obtained when k =
1.
Definition 2.1. Let p be an odd prime such that
2
k
|p − 1. Then the symbol
J
2
k
(a, p) = a
p−1
2
k
(mod p)
is called the 2
k
-th power residue symbol modulo p,
where a
p−1
2
k
∈ Z
p
.
Properties. The 2
k
-th power residue symbol satis-
fies the following properties
1. If a ≡ b (mod p), then J
2
k
(a, p) = J
2
k
(b, p),
2. J
2
k
(a
2
k
, p) = 1,
3. J
2
k
(ab, p) = J
2
k
(a, p)J
2
k
(b, p) (mod p),
4. J
2
k
(1, p) = 1 and J
2
k
(−1, p) = (−1)
(p−1)/2
k
.
In our paper we will make use of a generalized
version of the Chinese Remainder Theorem. More
precisely, we are interested in the case of moduli that
are not pairwise coprime. We further present the the-
orem as stated in (Pei et al., 1996).
Theorem 2.1 (Generalized Chinese Remainder The-
orem). Let m
1
,m
2
,. .., m
t
be positive integers. For a
set of integers a
1
,a
2
,. .., a
t
the system of congruences
x ≡ a
i
(mod m
i
), for i ∈ [1,t]
has solutions if and only if
a
i
≡ a
j
(mod gcd(m
i
,m
j
)), for i ̸= j, i, j ∈ [1,t].
(1)
If Equation (1) holds, then the solution will be unique
modulo lcm(m
1
,m
2
,. .., m
t
).
We additionally use a theorem proved by Dirich-
let in 1837. This theorem establishes the constrains
necessary for the existence of infinitely many primes
in an arithmetic progression. The original proof can
be found in (Kennard, 2006).
SECRYPT 2023 - 20th International Conference on Security and Cryptography
296

Theorem 2.2 (Dirichlet’s theorem). Let r, q be two co-
prime positive integers and let {a
n
}
n∈N
be an arith-
metic progression such that a
n
= qn + r. Then there
exists a subsequence {b
n
′
}
n
′
∈N
⊆ {a
n
}
n∈N
such that
b
n
′
is prime for each n
′
.
2.2 Computational Complexity
To analyze the performance of our scheme, we must
consider the complexities of the mathematical oper-
ations listed in Table 1. These complexities are in
line with those presented in (Crandall and Pomerance,
2005). Note that, instead of using the explicit formula
for the complexity of multiplication, we simply de-
note it by M(·).
Table 1: Computational complexity for µ-bit numbers and
k-bit exponents.
Operation Complexity
Multiplication O(µlog(µ)log(log(µ)))
Exponentiation O(kM(µ))
Jacobi symbol O(log(µ)M(µ))
2.3 Security Assumptions
Definition 2.2 (Gap 2
k
-Residuosity - GR). Choose
two large prime numbers p,q ≥ 2
λ
and compute
n = pq. Let A be a probabilistic polynomial-time
(PPT) algorithm that returns 1 on input (x,k,n) if
x ∈ J
n
\ QR
n
. We define the advantage
ADV
GR
A,k
(λ) =
Pr[A(x, k,n) = 1|x
$
←− J
n
\ QR
n
]
−Pr[A(x
2
k
,k, n) = 1|x
$
←− Z
∗
n
]
.
Let p, q ≡ 1 mod 2
k
. The Gap 2
k
-Residuosity as-
sumption states that for any PPT algorithm A the ad-
vantage ADV
GR
A
(λ) is negligible.
2.4 Public Key Encryption
A public key encryption (PKE) scheme usually con-
sists of three PPT algorithms: Setup, Encrypt and De-
crypt. The Setup algorithm takes as input a security
parameter and outputs the public key as well as the
matching secret key. Encrypt takes as input the pub-
lic key and a message and outputs the corresponding
ciphertext. The Decrypt algorithm takes as input the
secret key and a ciphertext and outputs either a valid
message or an invalidity symbol (if the decryption
failed).
Definition 2.3 (Indistinguishability under Chosen
Plaintext Attacks - IND-CPA). The security model
against chosen plaintext attacks for a PKE scheme is
captured in the following game:
Setup(λ): The challenger C generates the public key,
sends it to adversary A and keeps the matching
secret key to himself.
Query: Adversary A sends to C two equal length
messages m
0
,m
1
. The challenger flips a coin
b ∈ {0,1} and encrypts m
b
. The resulting cipher-
text c is sent to the adversary.
Guess: In this phase, the adversary outputs a guess
b
′
∈ {0,1}. He wins the game, if b
′
= b.
The advantage of an adversary A attacking a PKE
scheme is defined as
ADV
IND-CPA
A
(λ) = |Pr[b = b
′
] − 1/2|
where the probability is computed over the random
bits used by C and A. A PKE scheme is IND-CPA
secure, if for any PPT adversary A the advantage
ADV
IND-CPA
A
(λ) is negligible.
Definition 2.4 (Indistinguishability under Chosen Ci-
phertext Attacks - IND-CCA). In the context of Defi-
nition 2.3, if before and after the query phase the ad-
versary has access to a decryption oracle, we say that
scheme is IND-CCA secure. The only restriction im-
posed on the adversary is that after the query phase he
cannot query the decryption oracle with input c.
2.4.1 The Joye-Libert PKE Scheme
The Joye-Libert scheme was introduced in (Joye and
Libert, 2013) as a generalization of the Goldwasser-
Micali cryptosystem (Goldwasser and Micali, 1982)
to multi-bit messages. The scheme is proven se-
cure in the standard model under the GR assumption
(Joye and Libert, 2013; Benhamouda et al., 2017).
We shortly describe the algorithms of the Joye-Libert
cryptosystem.
Setup(λ): Set an integer k ≥ 1. Randomly generate
two distinct large prime numbers p, q such that
p,q ≥ 2
λ
and p,q ≡ 1 mod 2
k
. Output the public
key pk = (n,y,k), where n = pq and y ∈ J
n
\ QR
n
.
The corresponding secret key is sk = (p,q).
Encrypt(pk, m): To encrypt a message m ∈ [0, 2
k
),
we choose x
$
←− Z
∗
n
and compute c ≡ y
m
x
2
k
mod n.
Output the ciphertext c.
Decrypt(sk,c): Compute z ≡ J
2
k
(c, p) and find m
such that the relation [J
2
k
(y, p)]
m
≡ z mod p holds.
Efficient methods to recover m can be found in
(Joye and Libert, 2014).
Threshold Cryptosystems Based on 2 k-th Power Residue Symbols
297

2.4.2 Threshold PKE Schemes
Compared to PKE schemes, the Setup and Decrypt al-
gorithms of threshold schemes use sub-algorithms to
distribute/aggregate information to/from participants.
More precisely, the Setup algorithm takes as input a
security parameter, the number of total players ℓ and
the decryption threshold h; it outputs the public key
and distributes the shares of the secret key to the ℓ
players. The Decrypt algorithm takes as input a ci-
phertext; it forwards it to player i’s decryption algo-
rithm
2
; aggregates the decryption shares from each
player and after receiving at least h shares it outputs
either a valid message or an invalidity symbol.
In our paper we will consider the definition of a
simulatable threshold protocol introduced by Gennaro
et al. in (Gennaro et al., 1996). Informally, a proto-
col is simulatable if we can show how an adversary
attacking the original scheme can simulate the view
of h − 1 players. This implies that this adversary can
use an efficient attacker against the threshold version
to break the original protocol. Hence, we show that if
the original PKE is IND-CPA secure and the threshold
version is simulatable, then the threshold PKE is IND-
CPA secure even when the adversary has corrupted
h − 1 players.
3 A PUBLIC KEY ENCRYPTION
SCHEME
3.1 Prerequisites
Lemma 3.1. Let k,α > 0 be integers and let s ∈ Z
2
α
be odd. For a pair of distinct prime numbers p,q such
that
p ≡ q ≡ s · (2
α
)
k
+ 1 (mod (2
α
)
k+1
),
we have
gcd(p − 1,q − 1)|(p − q)/2
α
.
Proof. We first remark that from the definition of p
and q we obtain 2
α
|p − q.
Lets consider an odd integer r such that r|gcd(p−
1,q − 1). In this case, we obtain that r|p − q and tak-
ing into account the property gcd(2, r) = 1 we derive
the relation r|(p − q)/2
α
.
We further examine the power of 2 in the prime
factorization of the integer gcd(p −1,q −1). Accord-
ing to the definition we have
p = p
′
· (2
α
)
k+1
+ s · (2
α
)
k
+ 1,
q = q
′
· (2
α
)
k+1
+ s · (2
α
)
k
+ 1,
2
which has access to player i’s secret key share
where p
′
,q
′
are positive integers. Hence, we obtain
that
p − q = (p
′
− q
′
)(2
α
)
k+1
. (2)
Since s is odd, we have that
2
αk
|p − 1,2
αk+1
̸ |p −1 and 2
αk
|q − 1,2
αk+1
̸ |q − 1,
and thus
2
αk
|gcd(p − 1,q −1) and 2
αk+1
̸ |gcd(p − 1,q − 1).
In consequence, we need to show that 2
αk
|(p − q)/2
α
,
or equivalently that 2
α(k+1)
|p − q. But this is true ac-
cording to Equation (2).
Corollary 3.1.1. Let k,α > 0 be integers and let s ∈
Z
2
α
be odd. For a pair of distinct prime numbers p, q
such that
p ≡ q ≡ s · (2
α
)
k
+ 1 (mod (2
α
)
k+1
),
the system of congruences
x ≡ (p − 1)/2
α
(mod p − 1),
x ≡ (q −1)/2
α
(mod q − 1),
(3)
has solutions. Note that the solution is unique modulo
lcm(p − 1,q − 1).
Proof. According to Theorem 2.1 the system of con-
gruences (3) has solutions if and only if
(p − 1)/2
α
≡ (q − 1)/2
α
(mod gcd(p − 1,q − 1)).
(4)
Equation (4) is equivalent to
gcd(p − 1,q − 1)|(p − q)/2
α
.
and using Lemma 3.1 we obtain the desired result.
Lemma 3.2. Let α > 0. We consider the set
P
i
= {p prime | ∃k ∈ N s.t. p ≡ (2
i
)
k
+ 1 (mod 2
i(k+1)
)}.
Then there exists infinitely many primes p ∈ ∩
α
i=1
P
i
and integers e,k
i
such that
p ≡ 2
e
+ 1 (mod (2
i
)
k
i
+1
),
for each i ∈ [1, α]. More precisely, we have e =
lcm(1,. .., α) and k
i
= e/i.
Proof. We begin by noticing that gcd(2
e
+1,2
e+α
) =
1. According to Theorem 2.2, there exist infinitely
many prime numbers p such that
p ≡ 2
e
+ 1 (mod 2
e+α
). (5)
We can see that Equation (5) implies p ≡ 2
e
+ 1
(mod 2
e+i
), for each i ∈ [1,α]. This is due to the fact
that 2
e
+ 1 < 2
e+1
< 2
e+2
< .. . < 2
e+α
.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
298

If we can prove that p ∈ ∩
α
i=1
P
i
, then we can con-
clude our proof. Since e = lcm(1, 2,. ..,α), then there
exist an integer k
i
such that e = k
i
·i for each i ∈ [1,α].
As a result, we obtain that
p ≡ 2
e
+ 1 (mod (2
i
)
k
i
+1
),
for each i ∈ [1,α]. Therefore, p ∈ P
i
for each i ∈ [1,α],
which is equivalent to our conclusion.
3.2 Description
Setup(λ): Set integers k ≥ 1 and e = lcm(1,. .. ,k)
such that e + k < λ. Randomly generate two dis-
tinct large prime numbers p, q such that p,q ≥ 2
λ
and p, q ≡ 2
e
+ 1 (mod 2
e+k
). Let n = pq. Select
z
j
, such that the following conditions hold
z
j
≡ (p −1)/2
j
(mod p − 1),
z
j
≡ (q − 1)/2
j
(mod q − 1),
(6)
where j ∈ [1, k]. Output the public key pk =
(n,y,k), where y ∈ J
n
\ QR
n
. The corresponding
secret key is sk = z, where z = {z
j
}
j∈[1,k]
.
Encrypt(pk, m): To encrypt a message m ∈ [0, 2
k
),
we choose x
$
←− Z
∗
n
and compute c ≡ y
m
x
2
k
mod n.
Output the ciphertext c.
Decrypt(sk,c): To recover the message simply com-
pute m = Dec(z,y, c).
Algorithm 1: Dec(Z,y,c).
Input: The secret value z and the ciphertext c
Output: The message m
1 m ← 0, B ← 1
2 foreach j ∈ [1, k] do
3 v ← c
z
j
(mod n)
4 w ← (y
z
j
)
m
(mod n)
5 if v ̸= w then
6 m ← m + B
7 B ← 2B
8 return m
Correctness. Let m =
∑
k−1
w=0
b
w
2
w
be the binary ex-
pansion of m. Note that
c
z
j
≡ J
2
j
(c, p) = J
2
j
(y
m
x
2
k
, p) = J
2
j
(y
m
, p) = J
2
j
(y, p)
∑
j−1
w=0
b
w
2
w
≡ (y
z
j
)
∑
j−1
w=0
b
w
2
w
(mod p)
since
1. J
2
j
(x
2
k
, p) = 1, where 1 ≤ j ≤ k;
2.
∑
k−1
w=0
b
w
2
w
=
∑
j−1
w=0
b
w
2
w
+2
j
∑
k−1
w= j
b
w
2
w− j
.
Similarly, we obtain that
c
z
j
≡ (y
z
j
)
∑
j−1
w=0
b
w
2
w
(mod q).
Therefore, we obtain that
c
z
j
≡ (y
z
j
)
∑
j−1
w=0
b
w
2
w
(mod n).
As a result, the message m can be recovered bit by bit
using z
j
.
Remark. When k = 1 we obtain the Desmedt-
Kurosawa encryption scheme (Desmedt and Kuro-
sawa, 2007).
Remark. Note that is sufficient to set the secret key
only as sk = z
k
, since the remaining values can be
easily computed as z
k− j
= z
2
k− j+1
for j ∈ [1,k − 1].
But, for simplicity and clarity of the exposition, we
describe it as such.
Remark. In the Setup phase, we have to select an y
from J
n
\ QR
n
. An efficient way to perform this step
is to randomly select y
p
$
←− Z
∗
p
\ QR
p
and y
q
$
←− Z
∗
q
\
QR
q
, and then use the Chinese Remainder Theorem
to compute the element y ∈ Z
∗
n
such that y ≡ y
p
mod p
and y ≡ y
q
mod q.
Optimized Decryption Algorithm. When study-
ing Algorithm 1, we can observe that the values y
z
j
are known beforehand. Hence, we can precompute
D
j
= y
z
j
(mod n) for j ∈ [1,k] and augment the pri-
vate key with these values.
3.3 Security Analysis
Theorem 3.3. Assume that the QR and SJS assump-
tions hold. Then, the proposed scheme is IND-CPA
secure in the standard model.
Proof. To prove the statement, we simply change the
distribution of the public key y. More precisely, in-
stead of picking y uniformly from J
n
\QR
n
, we choose
it from the multiplicative subgroup of 2
k
residues
modulo n. According to the GR assumption, the ad-
versary does not detect the difference between the
original scheme and the one with the modified pub-
lic key. In this case, the value c is not carrying any
information about the message.
Formally, let A be an efficient PPT adversary, then
there exist two efficient PPT algorithms B
1
and B
2
such that
ADV
IND-CPA
A
(λ) ≤
3
2
((k −
1
3
)ADV
QR
B
1
(λ)
+(k − 1)ADV
SJS
B
2
(λ)
.
Thus, the IND-CPA security of our proposed cryp-
tosystem follows.
Threshold Cryptosystems Based on 2 k-th Power Residue Symbols
299
Parameter Selection. In order for our scheme to
work, we need to choose special primes p, q ≡ 2
e
+ 1
(mod 2
e+k
). This means that the first least significant
e + k bits of both p and q are known to everybody.
These facts have a very important impact in the secu-
rity of the scheme. Due to a powerful attack described
by Coppersmith (Coppersmith, 1997) the size of e +k
must be at most 0.25log n. Otherwise, it is possible to
factor n.
3.4 Complexity Analysis
To facilitate our analysis, we consider that both
primes have length λ when determining the ciphertext
expansion and the encryption/decryption complexi-
ties. Considering the complexities listed in Table 1,
our scheme achieves the performances presented in
Table 2. Note that GM, JL and DK are presented
in (Goldwasser and Micali, 1982), (Joye and Libert,
2013) and (Desmedt and Kurosawa, 2007), respec-
tively.
Table 2: Performance analysis for an η-bit message.
Scheme
Ciphertext Encryption
size Complexity
GM 2λη O(2M(2λ)η)
JL 2λ
l
η
k
m
O
2(k + 1)M(2λ)
l
η
k
m
Scheme
Decryption
Complexity
GM O(log(λ)M(λ)η)
DK O(2λM(2λ)η)
JL O
(2kλ + k)M(λ)
l
η
k
m
This work O
(4kλ + k)M(2λ)
l
η
k
m
3.5 Implementation Details
We further provide the reader with benchmarks for
our proposed PKE scheme. We ran each of the three
sub-algorithms on a CPU Intel i7-4790 4.00 GHz
and used GCC to compile it (with the O3 flag acti-
vated for optimization). Note that for all computa-
tions we used the GMP library (gmp, ) and the run-
ning times were calculated using the omp get wtime()
function (omp, ). To obtain the average running time
we chose to encrypt 100 128/192/256-bit messages,
representing random symmetric keys. In order to
have the same security as the symmetric keys we con-
sidered λ to be 1536/3840/15360, which according
to NIST (Barker, 2016) offers a security strength of
128/192/256 bits.
According to our security analysis e + k has to be
less than 768/1920/3840. Using Lemma 3.2 we ob-
tain that the first couples (k, e) are
(k, e) ∈ {(1,1), (2,2),(3, 6),(4,12),(5,60),
(6,60),(7,420),(8, 840),(9,2520),
(10,2520),(11,27720)}.
Therefore, we have that k must be less than 8/9/11
when λ is 1536/3840/15360.
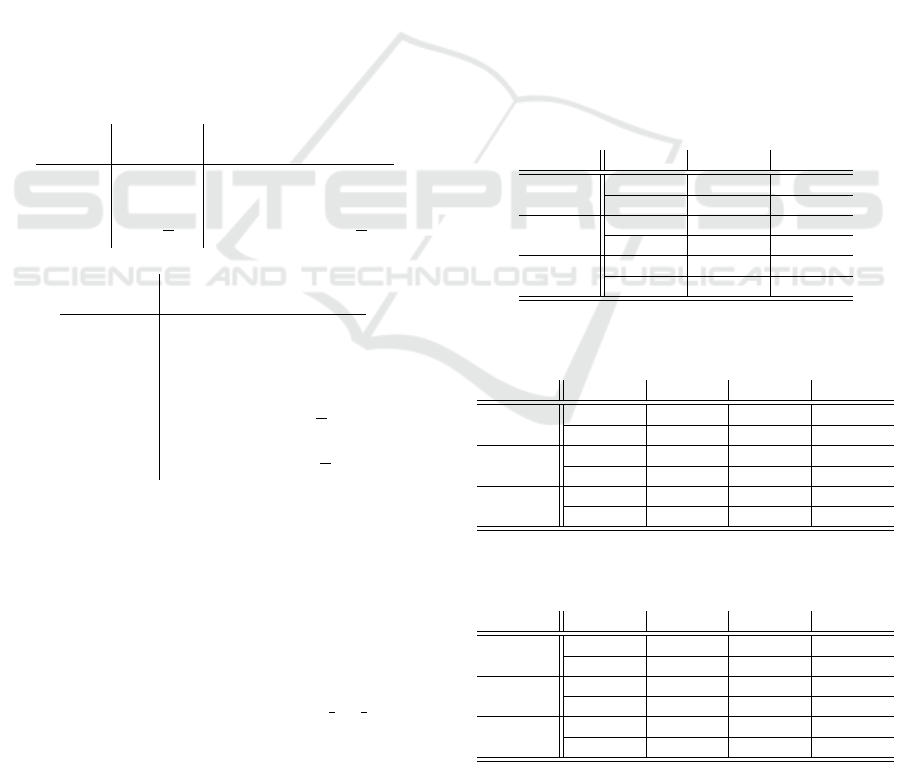
We further list our results in Tables 3 to 5 (run
times are given in seconds). It should be noted that in
Tables 3 to 5, the first lines of each algorithm cor-
respond to Algorithm 1, while the second ones to
the optimized decryption version. When analyzing
Table 3, note that in the case k = 1 we obtain the
Desmedt-Kurosawa scheme.
For completeness, in Table 6 we also present the
ciphertext size (in kilobytes = 10
3
bytes) for the pre-
viously mentioned parameters.
Table 3: Average running times (seconds) for a 128-bit mes-
sage.
k = 1 k = 2 k = 4
Setup
0.42484 0.47193 0.44816
0.44641 0.46838 0.51512
Encrypt
0.00692 0.00455 0.00305
0.00700 0.00450 0.00311
Decrypt
2.10024 2.60676 3.16701
2.11705 2.11393 2.08517
Table 4: Average running times (seconds) for a 192-bit mes-
sage.
k = 1 k = 2 k = 4 k = 8
Setup
10.8222 12.4561 11.3062 10.7336
10.1334 12.9877 11.9022 12.4903
Encrypt
0.04134 0.02802 0.02005 0.01573
0.04109 0.02804 0.02004 0.01551
Decrypt
35.7803 44.6466 54.6832 54.6622
35.5898 35.5451 35.4484 30.9529
Table 5: Average running times (seconds) for a 256-bit mes-
sage.
k = 1 k = 2 k = 4 k = 8
Setup
1259.44 1241.65 1381.09 1341.92
1401.10 1191.06 1246.21 1475.49
Encrypt
0.46191 0.31205 0.22357 0.17134
0.45907 0.31003 0.22131 0.16992
Decrypt
1520.86 1895.35 2308.22 2530.18
1508.40 1499.50 1492.01 1435.41
SECRYPT 2023 - 20th International Conference on Security and Cryptography
300

Table 6: Ciphertext expansion.
k = 1 k = 2 k = 4 k = 8
λ = 1536 49.15 24.57 12.28 −
λ = 3840 184.32 92.16 46.08 23.04
λ = 15360 983.04 491.52 245.76 122.88
4 A THRESHOLD
HOMOMORPHIC
ENCRYPTION SCHEME
4.1 Description
For simplicity and clarity, we begin by describing a
threshold protocol that requires a trusted dealer and is
of type ℓ-out-of-ℓ. More precisely, we consider that
the number of participants in our scheme is ℓ and that
all of them are required to decrypt a ciphertext. On the
other hand, if an adversary corrupts ℓ− 1 participants
it is infeasible for him to decrypt a given ciphertext.
The exact details of our protocol are provided below.
Dealing Phase: In the case of threshold decryption,
the Setup phase of our PKE scheme is replaced by
the following protocol.
1. First, the dealer sets integers k ≥ 1 and e =
lcm(1,. .., k) such that e + k < λ. Then, he ran-
domly generates two distinct large prime num-
bers p, q such that p,q ≥ 2
λ
and p,q ≡ 2
e
+ 1
(mod 2
e+k
). Finally, he sets n = pq.
2. Let j ∈ [1,k]. The dealer computes z
j
, such that
the system of congruences (6) holds. Then, he
randomly chooses z
j,1
,z
j,2
,. .., z
j,ℓ
$
←− [0,2
2λ
]
and computes z
j,0
= z
j
−
∑
ℓ
i=1
z
j,i
. The public
key of the protocol is pk = (n,y, k, Z
0
), where
y ∈ J
n
\ QR
n
and Z
0
= {z
j,0
}
j∈[1,k]
.
3. Lastly, the dealer sends the secret key share
Z
i
= {z
j,i
}
j∈[1,k]
to player i for i ∈ [1,ℓ].
Decryption Phase: The decryption process of a ci-
phertext c proceeds as follows.
1. Player i computes β
j,i
≡ c
z
j,i
(mod n) for
each j ∈ [1,k] and broadcasts the vector β
i
=
{β
j,i
}
j∈[1,k]
.
2. All the players publicly compute the values
β
j,0
= c
z
j,0
for all j ∈ [1,k].
3. Each player computes C
j
≡
∏
ℓ
i=0
β
j,i
(mod n)
and then it uses algorithm Dec(z, y,c) to recover
message m.
Correctness: In order to see why algorithm
Dec(z,y,c) works, all we have to prove is that C
j
≡ c
z
j
(mod n). Thus, we have
C
j
≡
ℓ
∏
i=0
β
j,i
≡
ℓ
∏
i=0
c
z
j,i
≡ c
∑
ℓ
i=0
z
j,i
≡ c
z
j
(mod n).
Therefore, as is stated in Section 3.2, we are now able
to decrypt the message bit by bit.
4.2 Security Analysis
The proof of our result can be found in (Tes¸eleanu,
2023).
Theorem 4.1. The protocol presented in Section 4.1
is simulatable for any adversary who passively eaves-
drops on at most ℓ− 1 participant. Moreover, the pro-
tocol is IND-CPA, assuming the hardness of the GR
assumption.
5 CONCLUSIONS
In this paper we have constructed a novel variant of
the Joye-Libert cryptosystem that allows an user to
decrypt messages even if he does not know the fac-
torization of the composite modulus. Based on this
variant, we showed how to achieve threshold decryp-
tion for the Joye-Libert cryptosystem, and therefore
solving some open problems stated in (Joye and Lib-
ert, 2013; Fouque et al., 2000; Katz and Yung, 2002).
In the full paper, we also present several exten-
sions of our basic threshold scheme. We first provide
an example of converting the ℓ-out-of-ℓ threshold into
an h-out-of-ℓ one. Then, we provide a non-interactive
zero-knowledge protocol that can be used to protect
the proposed cryptosystems from chosen ciphertext
attacks. Note that our NIZK can also be used to pro-
tect the Desmedt-Kurasawa PKE, and thus filling a
gap left by the authors in (Desmedt and Kurosawa,
2007).
Future Work. A possible method for accelerating
our proposed systems would be to use small multiple
primes instead of only two primes. Therefore, an in-
teresting research direction would be to find a method
to modify the multi-prime Joye-Libert version pro-
posed in (Maimut¸ and Tes¸eleanu, 2020; Tes¸eleanu,
2022) such that it allows decryption without knowing
the factorization of n.
REFERENCES
OpenMP. https://www.openmp.org/.
Threshold Cryptosystems Based on 2 k-th Power Residue Symbols
301

The GNU Multiple Precision Arithmetic Library. https://
gmplib.org/.
Barker, E. (2016). NIST SP800-57 Recommendation for
Key Management, Part 1: General. Technical report,
NIST.
Benhamouda, F., Herranz, J., Joye, M., and Libert, B.
(2017). Efficient Cryptosystems from 2
k
-th Power
Residue Symbols. Journal of Cryptology, 30(2):519–
549.
Boneh, D. and Franklin, M. (1997). Efficient Generation of
Shared RSA Keys (Extended Abstract). In CRYPTO
1997, volume 1294 of Lecture Notes in Computer Sci-
ence, pages 425–439. Springer.
Canetti, R. and Goldwasser, S. (1999). An Efficient Thresh-
old Public Key Cryptosystem Secure Against Adap-
tive Chosen Ciphertext Attack. In EUROCRYPT 1999,
volume 1592 of Lecture Notes in Computer Science,
pages 90–106. Springer.
Cohen, J. and Fischer, M. (1985). A Robust and Verifiable
Cryptographically Secure Ellection Scheme (extended
abstract). In FOCS 1985, pages 372–382. IEEE Com-
puter Society Press.
Coppersmith, D. (1997). Small Solutions to Polynomial
Equations, and Low Exponent RSA Vulnerabilities.
Journal of Cryptology, 10(4):233–260.
Cramer, R., Damg
˚
ard, I., and Nielsen, J. B. (2001). Mul-
tiparty Computation from Threshold Homomorphic
Encryption. In EUROCRYPT 2001, volume 2045 of
Lecture Notes in Computer Science, pages 280–300.
Springer.
Crandall, R. and Pomerance, C. (2005). Prime Numbers: A
Computational Perspective. Number Theory and Dis-
crete Mathematics. Springer.
Damg
˚
ard, I. and Jurik, M. (2001). A Generalisation, a Sim-
plification and Some Applications of Paillier’s Prob-
abilistic Public-Key System. In PKC 2001, volume
1992 of Lecture Notes in Computer Science, pages
119–136. Springer.
Desmedt, Y. and Frankel, Y. (1989). Threshold Cryptosys-
tems. In CRYPTO 1989, volume 435 of Lecture Notes
in Computer Science, pages 307–315. Springer.
Desmedt, Y. and Kurosawa, K. (2007). A Generalization
and a Variant of Two Threshold Cryptosystems Based
on Factoring. In ISC 2007, volume 4779 of Lecture
Notes in Computer Science, pages 351–361. Springer.
Fouque, P.-A. and Pointcheval, D. (2001). Threshold Cryp-
tosystems Secure against Chosen-Ciphertext Attacks.
In ASIACRYPT 2001, volume 2248 of Lecture Notes
in Computer Science, pages 351–368. Springer.
Fouque, P.-A., Poupard, G., and Stern, J. (2000). Shar-
ing Decryption in the Context of Voting or Lotteries.
In Financial Cryptography, volume 1962 of Lecture
Notes in Computer Science, pages 90–104. Springer.
Franklin, M. K. and Haber, S. (1993). Joint Encryption and
Message-Efficient Secure Computation. In CRYPTO
1993, volume 773 of Lecture Notes in Computer Sci-
ence, pages 266–277. Springer.
Gennaro, R., Jarecki, S., Krawczyk, H., and Rabin, T.
(1996). Robust Threshold DSS Signatures. In EURO-
CRYPT 1996, volume 1070 of Lecture Notes in Com-
puter Science, pages 354–371. Springer.
Girault, M., Poupard, G., and Stern, J. (2006). On the
Fly Authentication and Signature Schemes Based on
Groups of Unknown Order. Journal of Cryptology,
19(4):463–487.
Goldwasser, S. and Micali, S. (1982). Probabilistic Encryp-
tion and How to Play Mental Poker Keeping Secret
All Partial Information. In STOC 1982, pages 365–
377. ACM.
Goldwasser, S. and Micali, S. (1984). Probabilistic En-
cryption. Journal of Computer and System Sciences,
28(2):270–299.
Joye, M. and Libert, B. (2013). Efficient Cryptosystems
from 2
k
-th Power Residue Symbols. In EUROCRYPT
2013, volume 7881 of Lecture Notes in Computer Sci-
ence, pages 76–92. Springer.
Joye, M. and Libert, B. (2014). Efficient Cryptosystems
from 2
k
-th Power Residue Symbols. IACR Cryptology
ePrint Archive, 2013/435.
Katz, J., Myers, S., and Ostrovsky, R. (2001). Crypto-
graphic Counters and Applications to Electronic Vot-
ing. In EUROCRYPT 2001, volume 2045 of Lecture
Notes in Computer Science, pages 78–92. Springer.
Katz, J. and Yung, M. (2002). Threshold Cryptosystems
Based on Factoring. In ASIACRYPT 2002, volume
2501 of Lecture Notes in Computer Science, pages
192–205. Springer.
Kennard, L. (2006). Two Classic Theorems from Number
Theory: The Prime Number Theorem and Dirichlet’s
Theorem.
Maimut¸, D. and Tes¸eleanu, G. (2020). A New Generalisa-
tion of the Goldwasser-Micali Cryptosystem Based on
the Gap 2
k
-Residuosity Assumption. In SecITC 2020,
volume 12596 of Lecture Notes in Computer Science,
pages 24–40. Springer.
Naccache, D. and Stern, J. (1998). A New Public Key Cryp-
tosytem Based on Higher Residues. In CCS 1998,
pages 59–66. ACM.
Pedersen, T. P. (1991). A Threshold Cryptosystem without a
Trusted Party. In EUROCRYPT 1991, volume 547 of
Lecture Notes in Computer Science, pages 522–526.
Springer.
Pei, D., Salomaa, A., and Ding, C. (1996). Chinese Re-
mainder Theorem: Applications in Computing, Cod-
ing, Cryptography. World Scientific Publishing.
Shoup, V. and Gennaro, R. (1998). Securing Threshold
Cryptosystems against Chosen Ciphertext Attack. In
EUROCRYPT 1998, volume 1403 of Lecture Notes in
Computer Science, pages 1–16. Springer.
Tes¸eleanu, G. (2022). The Case of Small Prime Numbers
Versus the Joye-Libert Cryptosystem. Mathematics,
10(9).
Tes¸eleanu, G. (2023). Threshold Cryptosystems Based
on 2
k
-th Power Residue Symbols. IACR Cryptology
ePrint Archive, 2023/601.
Yan, S. Y. (2002). Number Theory for Computing. Theoret-
ical Computer Science. Springer.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
302
