
Risk-Based Illegal Information Flow Detection in the IIoT
Argiro Anagnostopoulou
1a
, Ioannis Mavridis
2b
and Dimitris Gritzalis
1c
1
Dept. of Informatics, Athens University of Economics and Business, Patision 76 Ave, Athens, Greece
2
Dept. of Applied Informatics, University of Macedonia, 156 Egnatia St, Thessaloniki, Greece
Keywords: Access Control, Information Flow Control, Illegal Information Flow Detection, Critical Infrastructure
Protection, Industrial Internet of Things (IIoT), Industry 4.0.
Abstract: Industrial IoT (IIoT) consists of a great number of low-cost interconnected devices, including sensors, actua-
tors, and PLCs. Such environments deal with vast amounts of data originating from a wide range of devices,
applications, and services. These data should be adequately protected from unauthorized users and services.
As IIoT environments are scalable and decentralized, the conventional security schemes have difficulties in
protecting systems. Information flow control, along with delegation of accurate access control rules is crucial.
In this work, we propose an approach to assess the existing information flows and detect the illegal ones in
IIoT environments, which utilizes a risk-based method for critical infrastructure dependency modeling. We
define formulas to indicate the nodes with a high-risk level. We create a graph based on business processes,
operations, and current access control rules of an infrastructure. In the graph, the edges represent the infor-
mation flows. For each information flow we calculate the risk level. This aids to reconstruct current access
control rules on the high-risk nodes of the infrastructure.
1 INTRODUCTION
Internet of Things (IoT) describes ubiquitous conne-
ctivity to the Internet, turning common objects into
connected devices, also called smart objects. Smart
objects can sense the surrounding environment, tran-
smit and process acquired data, and then provide
feedback to the environment (Sisinni, 2018). How-
ever, once a device is connected to the Internet, it is
vulnerable to cyber-attacks. The fourth industrial re-
volution (Industry 4.0), the exponential increase in
connected devices worldwide, and the rapidly increa-
sing number of cyber security incidents highlight the
need for enhancing cyber resilience (ENISA, 2018).
In large scale Industrial IoT (IIoT) environments,
all these interconnected devices must be protected a-
gainst unauthorized access. Thus, there is need for the
enforcement of proper access control policies on IIoT
objects. This is the role of access control systems.
Access control systems establish which active entities
(subjects) are authorized to gain access to passive en-
a
https://orcid.org/0000-0003-4199-6257
b
https://orcid.org/0000-0001-8724-6801
c
https://orcid.org/0000-0002-7793-6128
tities (objects), e.g., a resource. Each subject is chara-
cterized by a set of permissions for a specific object
(Samarati, 2001), (Nakamura, 2019), (Jaune, 2011).
Only authorized subjects are allowed to manipulate
objects in authorized operations (Nakamura, 2019).
The interconnected devices exchange data, creating
information flows. However, access control mecha-
nisms cannot always control how the information is
used once it has been accessed. For this reason, infor-
mation flow control (detection) is rising. Information
flow control ensures that data contained in an object
cannot flow into another and thus, these data cannot
be accessed by users that do not have the appropriate
permission (Jaume, 2011).
1.1 Contribution
In this work, we intend to address the improper or
insufficient selection of access control rules that re-
sults to illegal information flows. Working on this di-
rection, we propose an approach to detect and assess
illegal information flows, which utilizes a risk-based
Anagnostopoulou, A., Mavridis, I. and Gritzalis, D.
Risk-Based Illegal Information Flow Detection in the IIoT.
DOI: 10.5220/0012079800003555
In Proceedings of the 20th International Conference on Security and Cryptography (SECRYPT 2023), pages 377-384
ISBN: 978-989-758-666-8; ISSN: 2184-7711
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)
377

analysis method for critical infrastructure dependen-
cy modeling (Kotzanikolaou, 2013a), (Kotzanikola-
ou, 2013b). We focus our proposed work in IIoT en-
vironments. Our approach creates a graph based on
business processes, operations, and current access
control rules of an infrastructure. In the graph, the ed-
ges represent the information flows. Our aim is to de-
tect the high-risk nodes and thus, the nodes that are
susceptible to participate in illegal information flows.
Specifically, we compare the transactions that take
place with the current access control rules, in order to
mark the transaction that the information illegally flo-
ws from one node to another. Finally, we calculate the
risk to each information flow. The calculated risks in-
dicate the nodes that need reconstruction of their cur-
rent access control rules.
1.2 Structure
The remainder of the paper is structured as follows.
In Section 2, we present the related work regarding
methodologies used for the detection of illegal infor-
mation flows. In Section 3, we provide the theoretical
background, including the key concepts that are used
in the proposed approach. In Section 4, we present our
approach for the illegal information flow detection in
IIOT environments, while Section 5 provides a case
study in which we evaluate the formulas for the risk
calculation. Finally, the conlusion, limitations and fu-
ture work are exhibited in Section 6.
2 RELATED WORK
Researchers and security professionals distinguish
the terms of access control and information flow con-
trol. Access control verifies that subjects with specific
access rights can manipulate an object, while infor-
mation flow control tracks how information propaga-
tes through the program during execution (Hedin,
2012). In recent years, the detection of illegal infor-
mation flows is a major topic of interest in scientific
research. This section summarizes the main existing
methods that focus on this topic.
Zimmermann et. al propose a policy-based intru-
sion detection approach to verify the legality of infor-
mation flows created by system operations among ob-
jects. The flows that are not authorized by any secu-
rity policy are considered as intrusion symptoms
(Zimmermann, 2003).
Masri et al. present a dynamic information flow
analysis to detect and debug insecure flows in prog-
rams. Authors incorporate a static pre-processing
phase that detects both implicit flows at runtime, and
the explicit ones. They also utilize a dynamic slicing
algorithm that allows their approach to be applied to
structured and unstructured programs (Masri, 2004).
Cai et. al investigate illegal information flows re-
sulting from both roles and users. They obtain illegal
information flows via the operations of difference, in-
tersection, complement, etc. Authors propose, also, a
strategy that focuses on the "writing" operation, as it
is the primary means of creating information flows
(Cai, 2009).
Hammer et. al propose a method based on prog-
ram dependence graphs (PDG) to represent informa-
tion flows in a program. The authors developed a de-
pendence graph generator for full Java bytecode that
requires less annotations than the traditional ones and
provides more precise output. They, also, introduce
flow equations, including the case of the declassifica-
tion handling (Hammer, 2009).
Finally, Jaume et. al propose a framework that
identifies illegal information flows. They present two
implementations: Blare and JBlare. The first observes
system calls and identifies information flows between
OS containers, such as files or sockets. JBlare, an im-
proved version of Blare, identifies information flows
at the language level (Java) (Jaume, 2011).
Our approach assesses the information flows and
detects the illegal ones in IIoT environments by utili-
zing a risk-based method for critical infrastructure de-
pendency modeling (Kotzanikolaou, 2013a), (Kotza-
nikolaou, 2013b). Specifically, we model the business
processes as a graph and assess the risk of all infor-
mation flows to detect the nodes that are susceptible
to participate in an illegal information flow. Current-
ly, there is no research that utilizes a risk-based met-
hod for the detection of illegal information flows.
3 THEORETICAL
BACKGROUND
This section provides a theoretical background, inc-
luding the key concepts of information flow control
and access control.
3.1 Access Control
Access control manages the acceptable operations for
a user or process on system resources. The main con-
cepts of an access control system are policies, models,
and mechanisms. Access control policies specify how
and when a user, or a process, may access a resource.
An access control system enforces the access control
policies through access control mechanisms, which
SECRYPT 2023 - 20th International Conference on Security and Cryptography
378

are responsible for granting or denying access (Salo-
nikias et. al, 2019).
There are several access control models/schemes
that an organisation can adopt to enforce policies and
allocate access rights to its subjects. Below we exhibit
some of the most widely used ones.
Lattice-Based Access Control (LBAC): This
scheme is the first to be developed to secure
information flows in information systems. In a
system, information flows from one object to another.
An object can be defined as a container of informati-
on, such as files and directories in an operating sys-
tem, or relations in a database. Information flow is ty-
pically controlled by assigning a security class to eve-
ry object. Whenever information flows from object a
to object b, there is also information flow from the
security class of a to the security class of b (Sandhu,
1993), (Denning, 1976).
Mandatory Access Control (MAC): This scheme
is based on lattice model of security level. It is based
on two prominent rules: (i) No-read-up, and (ii) No-
write-down. The first describes that a low-level sub-
ject is not allowed to read high-level objects. The lat-
ter describes that high-level objects can only be writ-
ten by low-level subjects. As a result, in MAC scheme
the information flows from lower levels to the higher
ones (Bell et. al, 1972).
Discretionary Access Control (DAC): The prin-
ciple of this scheme is that access to objects can be
restricted based on the identity of the subjects and/or
groups to which they belong. Subjects are the entities
which cause an information flow between objects.
Each object has a subject as an owner. The access po-
licy of an object is determined by its owner. An owner
can transfer information access to other subjects (Do-
wns et. al, 1985).
Role-Based Access Control (RBAC): In this sche-
me the permissions are linked to roles. Users are as-
signed to appropriate roles based on their responsibi-
lities and qualifications. Roles are created for job fun-
ctions in an organisation. Users can be reassigned
from one role to another. Roles can be granted new
permissions as new applications and systems are in-
corporated, while permissions can be revoked from
roles when is necessary (Sandhu et. al, 1996), (Salo-
nikias et. al, 2019).
Capability-Based Access Control (CapBAC): In
this model an owner of a device issues a capability
token. This token is a set of access rights to a subject.
The subject is allowed to manipulate the device based
on the access rights that are defined in the capability
token (Nakamura et. al, 2019).
3.2 Information Flow Control
An information system is composed of subjects and
objects. An object contains data or operations to ma-
nipulate the data, such as databases or files. A subject
is an entity, i.e., user or transaction, that manipulates
an object. In order a subject to access data, it issues
an operation to the respective object. A transaction re-
fers to a sequence of operations on an object (Naka-
mura, 2018).
It is crucial for information security to define pro-
per access control rules, and tracks how information
is propagated by computing systems during executi-
on. Thus, information flow control aims to enhance
both the confidentiality and the integrity of the infor-
mation (Hedin et. al, 2012).
Let assume that an object o supports one of the
basic operations OP (e.g., read or write). An access
rule is composed of a tuple <s, o, op>, while the pair
<o, op> is called access right. An authorizer grants an
access right to a subject s. Subject s is allowed to ma-
nipulate the object o in an operation op only if s is
granted an access right <o, op> (Nakamura et. al,
2018).
Now, let suppose that a subject s
i
is granted with
the access right <f,read> on an object f, and an access
right <g,write> on object g. Suppose another subject
s
j
is granted with an access right <g,read>. Let assume
that s
i
reads data d in the object f and then writes data
d to the object g. The s
j
is not allowed to read data in
the object f. However, the s
j
can obtain data d in the
object f by reading data d stored in the object g. As a
result, information in the object f illegally flows into
the s
j
via the s
i
and the object g (Nakamura et. al,
2018).
In this work, we use four distinct terms to explain
illegal transactions from one object to another: (i) il-
legal read, (ii) illegal write, (iii) suspicious read, and
(iv) impossible write. Illegal read occurs if and only
if (iff) a transaction reads data that are contained in an
object, in which the transaction does not have the per-
mission to access. Suspicious read occurs iff the tran-
saction reads data in the object whose data is not al-
lowed to be brought to other objects. Illegal write oc-
curs iff the transaction writes data to the object after
illegally reading data in another object. Finally, im-
possible write occurs iff the transaction writes data to
the object after suspiciously reading data in another
object (Nakamura et, al, 2018). Figures 1 and 2 depict
two examples of illegal transactions (Nakamura et. al,
2018).
Risk-Based Illegal Information Flow Detection in the IIoT
379
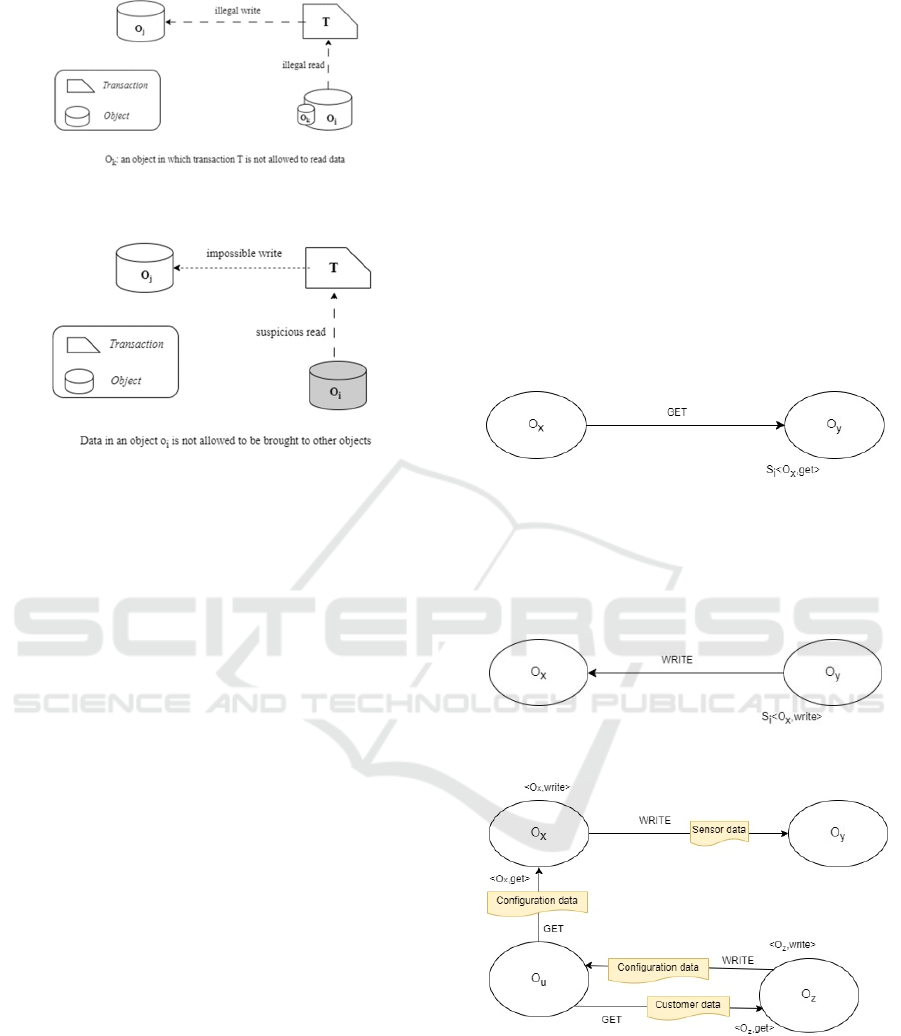
Figure 1: Illegal read and Illegal write transactions (Naka-
mura, 2018).
Figure 2: Suspicious read and impossible write transactions
(Nakamura et. al, 2018).
4 THE PROPOSED ILLEGAL
INFORMATION FLOW
DETECTION APPROACH
The proposed approach utilizes a risk-based method
for critical infrastructure dependency modeling (Kot-
zanikolaou, 2013a), (Kotzanikolaou, 2013b) to assess
information flows and detect the illegal ones in IIoT
environments. We aim to find out the high-risk nodes
that are prone to take part in illegal information flows.
The resulting method includes five steps:
Step 1. Dependency Graph Definition. The graph de-
picts information flows and thus the transactions bet-
ween the nodes of the IIoT network.
Step 2. Supporting Metrics Calculation. The support-
ing metrics are: (1) severity, (2) operation factor, and
(3) legality.
Step 3. Illegal Information Flow Likelihood Calcula-
tion for graph connections.
Step 4. Transaction Impact Calculation.
Step 5. Illegal Information Flow Risk Calculation.
4.1 Dependency Graph Definition
In this step, we denote as:
O: set of objects in the IIoT network,
IF: set of information flows between objects, and
T: the set of transactions among object nodes for
each information flow.
Dependencies are modelled in directed, weighted
graphs G = (V, E), where the nodes V represent com-
ponents of an IIoT network and edges E represent in-
formation flows between them. The graph is directio-
nal to represent an information flow from one com-
ponent to another within the IIoT network. An edge
O
x
→ O
y
depicts an information flow IF
x
→
y
from Ob-
ject O
x
to Object O
y
. Each information flow may be
related to many connecting transactions T
(x
→
y)
i
. Each
transaction depicts a “get” or a “write” operation to
an object.
Based on bibliography (Nakamura, 2019), when a
subject S
i
performs a “get” operation to object O
x
, i.e.,
<O
x
, get>, and the information flows from an object
O
x
to an object O
y
, the transaction is depicted as fol-
lows:
Figure 3: Depiction of “get” operation.
Similarly, we define that when a subject S
i
per-
forms a “write” operation to object O
x
, i.e., <O
x
, wri-
te>, and the information flows from an object O
x
to
an object O
y
, this transaction is depicted as follows:
Figure 4: Depiction of “write” operation.
Figure 5: Example of a network dependency graph.
An indicative example of a network dependency
graph is presented on Figure 5. The graph comprises
four (4) objects: O
x
, O
y
, O
u
and O
z
. O
x
writes Sensor
data on O
y
, while it gets Configuration data from O
u
.
Finally, O
z
writes Configuration data to O
u
, while it
gets Customer data from O
u
.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
380
4.2 Supporting Metrics Calculation
This section introduces the metrics used in our appro-
ach to calculate the risk of each node so as to identify
the nodes with the higher risk.
4.2.1 Severity
Depending on the data category that flows from one
node to another, there is a corresponding Severity.
This metric refers to both legal and illegal informati-
on flows. The range of Severity is [1,5], where 1 =
very low, and 5 = very high.
We define six categories of data that usually exist
in smart manufacturing. The catalogue with these ca-
tegories may be enlarged or altered, according to the
infrastructure that the method is applied. Table 1 pre-
sents the selected data categories and their values.
Table 1: Severity values based on data category.
Cate
g
or
y
of Data Severit
y
Confi
g
uration data 5
Sensor data 4
Billin
g
& Pricin
g
data 3
Customer data 2
Meteorolo
g
ical data 1
Acknowled
g
ement data 1
4.2.2 Operation Factor
Depending on the operation type (get, write) of the
transaction, we define two distinct operation values
for this metric. The value depends on the impact that
the operation has to a specific transaction. We consi-
der that the “write” operation may cause greater im-
pact when the intent of the subject is malevolent. The
term transaction defines the connection between two
nodes and thus, the information flow between them.
Table 2 presents operations and their values.
Table 2: Operation factor values based on operation type.
T
y
pe of Operation Operation facto
r
g
e
t
2
write 3
4.2.3 Legality
The Legality metric characterizes a transaction based
on six categories: (i) Legal Read, (ii) Legal Write, (iii)
Illegal Read, (iv) Illegal Write, (v) Suspicious Read,
and (vi) Impossible Write. The categories have been
defined in section 3.2. The range of Legality is [1,5],
where 1 = totally legal, and 5 = totally illegal. Table
3 depicts the legality values according to the category
of the transaction that takes place.
Table 3: Legality values based on the transaction type.
Categor
y
of Transaction Legalit
y
Legal Rea
d
1
Le
g
al Write 1
Ille
g
al Rea
d
2
Ille
g
al Write 3
Suspicious Rea
d
4
Impossible Write 5
4.3 Illegal Information Flow Likelihood
Each relationship is assigned with a likelihood value,
which declares how likely an illegal information flow
is to occur. Intuitively, this value is a probability, ba-
sed on which we can make predictions about the in-
formation flow state, at different times.
For each information flow IF
x
→
y
from O
x
to O
y
,
every transaction T
(x
→
y)
i
is marked either as “Good”
or as “Bad”. A transaction is marked as “Good” when
it is characterized as legal read or legal write. When
it is characterized as illegal read, suspicious read, ille-
gal write or impossible write, we mark it as “Bad”.
Formula 1 calculates the Illegal Information Flow Li-
kelihood, denoted as Likelihood
x
→
y
. The range of Li-
kelihood
x
→
y
is [0, 1]. The parameter n is the total
number of transactions between two nodes.
𝐿𝑖𝑘𝑒𝑙𝑖ℎ𝑜𝑜𝑑
→
=
∑
(𝑇
(→)
𝑚𝑎𝑟𝑘𝑒𝑑 𝑎𝑠 "𝐵𝑎𝑑
")
∑
(𝑇
(→)
)
(1)
4.4 Transaction Impact
Each transaction T
(x
→
y)
i
is assigned with an impact va-
lue, denoted as Impact
(x
→
y)
i
. Since there is no standard
available for evaluating the legality of information
flows, we propose the following formula for the cal-
culation of the Impact
(x
→
y)
i
.
𝐼𝑚𝑝𝑎𝑐𝑡
(→𝑦)
𝑖
= 𝑆𝑒𝑣𝑒𝑟𝑖𝑡𝑦 ∗ 𝑂𝑝𝑒𝑟𝑎𝑡𝑖𝑜𝑛 𝐹𝑎𝑐𝑡𝑜𝑟
∗𝐿𝑒𝑔𝑎𝑙𝑖𝑡𝑦
(2)
When the value of Impact
(x
→
y)
i
is high, a security
incident may cause a serious impact to the operation
of the IIoT environment.
We have thoroughly estimated all the possible
combinations of the values for each parameter of the
formula, and we concluded that the Impact
(x
→
y)
i
va-
lues range between [2,75]. We rescale the range of the
calculated Impact
(x
→
y)
i
values into the range [1,10].
Risk-Based Illegal Information Flow Detection in the IIoT
381
Rescaling helps all values to be in the same range. It
adjusts the numbers to make it easy to compare the
values of different metrics with different value ran-
ges. Data rescaling assists in extracting inferences a-
bout the applicability and performance of an appro-
ach. Formula 3 depicts the function used for the res-
caling of the Impact
(x
→
y)
i
values:
𝑓
(
𝐼
)
=
(
𝑏−𝑎
)
(𝐼 − 𝑚𝑖𝑛)
𝑚𝑎𝑥 − 𝑚𝑖𝑛
+𝑎
(3)
where I is a particular Impact
(x
→
y)
i
value.
Specifically, let assume that we want to scale a
range [min, max] to [a, b]. We need a continuous fun-
ction that satisfies the conditions: (i) f(min) = a, and
(ii) f(max) = b. In our case min = 2, max = 75, a=0,
and b=10. Table 4 assigns the ranges of the scaled Im-
pact values to five concrete levels.
Table 4: Rescaling of the Impact values.
Calculated Impact
Values
Scaled Impact
Values
Scaled Impact
Level
[2, 10
)
[1,2
)
Ver
y
Low
[10,26
)
[2,4
)
Low
[26,42) [4,6) Mediu
m
[42,58) [6,8) High
[58,75] [8,10] Very High
Having calculating impact for each individual
transaction T
(x
→
y)
i
, we evaluate the Total Impact va-
lue of an information flow IF
x
→
y
from O
x
to O
y
as the
average impact of the transactions T
(x
→
y)
i
performed.
Formula 4 calculates the Total Impact value of an in-
formation flow, where n denotes the number of trans-
actions T
(x
→
y)
i
between node x and node y.
𝑇𝑜𝑡𝑎𝑙 𝐼𝑚𝑝𝑎𝑐𝑡
→
=
∑
𝐼𝑚𝑝𝑎𝑐𝑡
(→)
𝑛
(4)
4.5 Illegal Information Flow Risk
The proliferation of impact and likelihood values
indicate the illegal information flow Risk, denoted as
R
x
→
y
, for an information flow IF
x
→
y
from an object O
x
to an object O
y
as follows:
𝑅
= 𝑇𝑜𝑡𝑎𝑙 𝐼𝑚𝑝𝑎𝑐𝑡
→
∗ 𝐿𝑖𝑘𝑒𝑙𝑖ℎ𝑜𝑜𝑑
→
(5)
This metric identifies the information flows with
the higher risk. Estimating risk helps identifying the
flows and thus the nodes that are susceptible to illegal
information flows. As a result, the nodes that partici-
pate in these flows need more accurate and stricter ac-
cess control rules.
We establish a scale to determine whether the risk
of a node is acceptable. The level of acceptability de-
pends on the infrastructure and the criticality of its sy-
stems. In general, the lower the risk level, the more
acceptable it is. Table 5 assigns the ranges of R
x
→
y
values to five distinct levels.
Table 5: Levels of Illegal Information Flow Risk.
Illegal Information Flow
Risk Value
Illegal Information Flow
Ris
k
Level
[0,2
)
Ver
y
Low
[2,4
)
Low
[4,6) Mediu
m
[6,8) High
[8,10] Ver
y
Hi
g
h
5 CASE STUDY
In this section we apply our method on an IIoT infra-
structure network. Figure 6 presents a dependency
graph which depicts how the network components
(e.g., O
a
, O
b
, etc.) are connected, along with the cate-
gory of data (e.g., configuration data, sensor data,
etc.) that flow from an object to another. Each transa-
ction refers its operation type (e.g., get, write). The
illegal transactions are notated with the flag “Bad”,
along with their category (e.g. illegal write, illegal re-
ad, suspicious read, impossible write).
Let assume that our interest focuses on object A.
This object takes part in totally nine transactions.
However, seven of them are marked as “Bad”. Thus,
we suppose that O
a
has a primarily malicious behavi-
our. Firstly, we calculate the Illegal Information Flow
Likelihood for all the transactions of object A. The
results are presented on Table 6.
Table 6: Illegal Information Flow Likelihood Calculation.
From To
Illegal Information
Flow Likelihoo
d
O
a
O
b
0.5
O
a
O
c
1
O
a
O
f
0
O
a
O
g
1
O
a
O
h
1
SECRYPT 2023 - 20th International Conference on Security and Cryptography
382
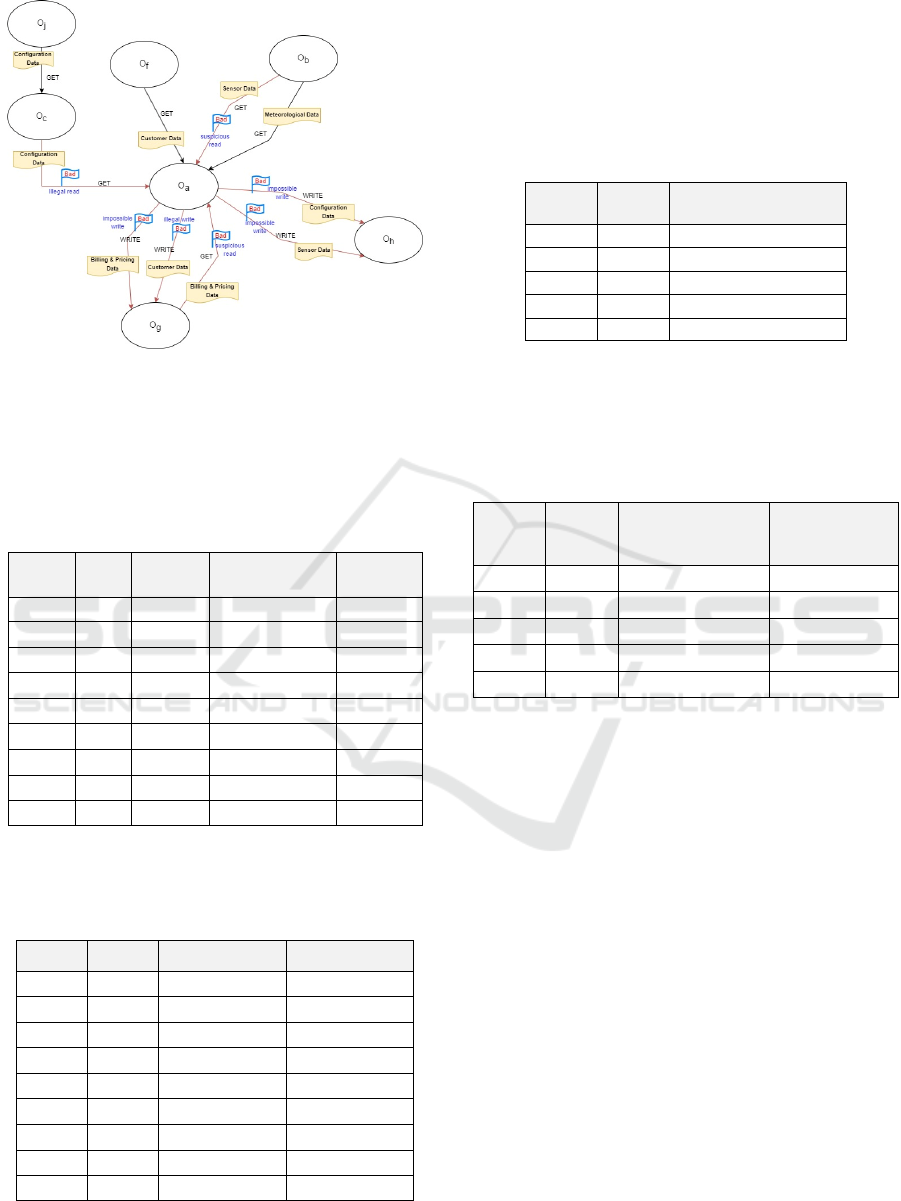
Figure 6: IIoT Infrastructure Network Dependency Graph.
For all the transactions we calculate the metrics of
Legality, Operation factor and Severity. The values of
these metrics are presented in Table 7.
Table 7: Calculation of the metrics Legality, Operation
factor, and Severity.
From To Legality Operation factor Severity
O
a
O
b
4 2 1
O
a
O
b
1 2 5
O
a
O
c
2 3 4
O
a
O
h
5 3 5
O
a
O
h
5 3 2
O
a
O
g
3 3 3
O
a
O
g
5 2 3
O
a
O
g
4 2 2
O
a
O
f
1 2 1
Next step is the Impact calculation for all the tran-
sactions. Table 8 presents the values of this metric.
Table 8: Calculation of the Impact of all transactions.
From To Impact Scaled Impact
O
a
O
b
32
4.7
O
a
O
b
2
1
O
a
O
c
20
3.22
O
a
O
h
60
8.15
O
a
O
h
75
10
O
a
O
g
18
2.97
O
a
O
g
45
6.3
O
a
O
g
24
3.71
O
a
O
f
4
1.25
Having calculating impact for each individual
transaction, we evaluate the Total Impact value of an
information flow IF
x
→
y
from object O
x
to object O
y
as
the average impact of the transactions T
(x
→
y)
i
perfor-
med. The results are presented on Table 9.
Table 9: Calculation of Illegal Information Flow Impact.
From To
Illegal Information
Flow Im
p
act
O
a
O
b
2.85
O
a
O
c
3.22
O
a
O
h
9.08
O
a
O
g
4.33
O
a
O
f
1.25
In Table 10, we estimate the Illegal Information
Flow Risk. For this calculation we combine the values
of Illegal Information Flow Impact, and Illegal Infor-
mation Flow Likelihood.
Table 10: Calculation of Illegal Information Flow Risk.
From To
Illegal
Information Flow
Risk Value
Illegal Infor-
mation Flow
Risk Level
O
a
O
b
1.43 Very Low
O
a
O
c
3.22 Low
O
a
O
h
9.08 Very High
O
a
O
g
4.33 Medium
O
a
O
f
0.00 Very Low
We observe that the information flow from object
A to object H contains a very high risk. This indicates
that there is great possibility any transaction with
such an information flow to be illegal. Thus, security
experts should pay enough attention on objects A and
H. The current access control rules should be exami-
ned and more accurate ones should be enforced.
6 CONCLUSIONS
In this work, we propose an approach to detect the il-
legal information flows in ΙΙοΤ environments. For
this purpose, we utilise a risk-based analysis method
for assessing the information flows on bussiness pro-
cesses. For each information flow we calculate the
metrics of: (a) illegal information flow likelihood,
and (b) illegal information flow risk. This will help to
control the information that illegally transmitted from
one node to another within an IIoT infrastructure net-
work.
We demonstrate the applicability of our method
by presenting an example that is composed of both
Risk-Based Illegal Information Flow Detection in the IIoT
383

legal and illegal information flows. Overall, our met-
hod can successfully identify the high-risk informa-
tion flows, and thus the high-risk nodes that are sus-
ceptable to participate in an illegal information flow.
This is an important feedback, because we can point
out the nodes that are vulnerable and need more accu-
rate access control rules.
Our future work is to identify whether potential il-
legal information flow risk is transferred from the
previous connection to the next one, where illegal in-
formation flow of one transaction may be propagated
to the next transaction within a business process. Our
vision is to evaluate our approach in real world IIoT
environments, such as smart manufacturing or smart
grid.
ACKNOWLEDGEMENTS
This work has been supported in part by a research
grant offered by the Hellenic Ministry of Digital Go-
vernance to the Research Centre of the Athens Uni-
versity of Economics & Business, Greece (2022-24).
REFERENCES
Bell, D., & La Padula, L., Secure computer systems: Unifi-
ed exposition and Multics interpretation. MTR-2997,
MITRE Corp., USA, 1976.
Cai, G., Shi, L., & Sui, X. (2009, October). Illegal Infor-
mation Flow Detection in Electronic Institution. In
2009 3
rd
International Conference on Genetic and
Evolutionary Computing (pp. 240-243). IEEE.
Denning, D. E. (1976). A lattice model of secure informa-
tion flow. Com. of the ACM, 19(5), 236-243.
Downs, D., Rub, J., Kung, K., & Jordan, C. (1985, April).
Issues in discretionary access control. In 1985 IEEE
Symposium on Security and Privacy (pp. 208-208).
IEEE.
ENISA (2018). Good Practices for Security of Internet of
Things in the context of Smart Manufacturing. Euro-
pean Union Agency for Network and Information Se-
curity (ENISA).
Hammer, C., & Snelting, G. (2009). Flow-sensitive, context
-sensitive, and object-sensitive information flow con-
trol based on program dependence graphs. Inter-
national Journal of Information Security, 8(6), 399-
422.
Hedin, D., & Sabelfeld, A. (2012). A perspective on infor-
mation-flow control. In Software safety and securi-
ty (pp. 319-347). IOS Press.
Jaume, M., Tong, V., & Mé, L. (2011, December). Flow
based interpretation of access control: Detection of il-
legal information flows. In ICISS (pp. 72-86).
Kotzanikolaou, P., Theoharidou, M., & Gritzalis, D. (2013
a, March). Cascading effects of common-cause failures
in critical infrastructures. In 7
th
IFIP International Co-
nference (pp. 171-182). Springer.
Kotzanikolaou, P., Theoharidou, M., & Gritzalis, D. (2013
b). Assessing n-order dependencies between critical
infrastructures. International Journal of Critical Infra-
structures 6, 9(1-2), 93-110.
Masri, W., Podgurski, A., & Leon, D. (2004, November).
Detecting and debugging insecure information flows.
In 15
th
International Symposium on Software Re-
liability Engineering (pp. 198-209). IEEE.
Nakamura, S., Ogiela, L., Enokido, T., & Takizawa, M.
(2018). An information flow control model in a topic-
based publish/subscribe system. Journal of High-Speed
Networks, 24(3), 243-257.
Nakamura, S., Enokido, T., Barolli, L., & Takizawa, M.
(2019, June). Capability-based information flow con-
trol model in the IoT. In 13
th
International Conference
on Innovative Mobile and Internet Services in
Ubiquitous Computing (pp. 63-71). Springer
Salonikias, S., Gouglidis, A., Mavridis, I., & Gritzalis, D.
(2019). Access control in the industrial internet of
things. Security and privacy trends in the industrial
internet of things, 95-114.
Samarati, P., & de Vimercati, S. C. (2001). Access control:
Policies, models, and mechanisms. In Foundations of
Security Analysis and Design: Tutorial Lectures 1 (pp.
137-196). Springer.
Sandhu, R. (1993). Lattice-based access control mo-
dels. Computer, 26(11), 9-19.
Sandhu, R., Coyne, E., Feinstein, H., & Youman, C. (1996).
Role-based access control models. Computer, 29 (2),
38-47.
Sisinni, E., Saifullah, A., Han, S., Jennehag, U., & Gidlund,
M. (2018). Industrial internet of things: Challenges,
opportunities, and directions. IEEE transactions on
industrial informatics, 14(11), 4724-4734.
Zimmermann, J., Mé, L., & Bidan, C. (2003). An improved
reference flow control model for policy-based intrusion
detection. Lecture notes in Computer Science, 2808,
291-308.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
384
