
Fidelis: Verifiable Keyword Search with No Trust Assumption
Laltu Sardar
1 a
and Subhra Mazumdar
2 b
1
Institute for Advancing Intelligence, TCG-CREST, Kolkata, India
2
TU Wien and Christian Doppler Laboratory Blockchain Technologies for the Internet of Things, Vienna, Austria
Keywords:
Searchable Encryption, Keyword Search, Fair Payment, Smart Contract, No-Trust Assumption.
Abstract:
A searchable encryption (SE) scheme allows a client to outsource its data to a cloud service provider (CSP)
without the fear of leaking sensitive information. The latter can search over the outsourced data based on the
client’s query. Such a scheme prevents a malicious CSP from sending incorrect results. However, a malicious
client can deny receipt of the correct result and wrongly blame the CSP. Existing SE schemes fail when the
client acts maliciously.
In this paper, we have studied searchable encryption schemes where none of the parties trust each other. We
propose Fidelis, a novel blockchain-based SE scheme, with keyword-search functionality, that is verifiable
by both parties. None of the parties can cheat, and an honest CSP gets payment upon providing the result.
We implement and evaluate an instance of the protocol on real-life data using Ethereum as the blockchain
platform, deploying it in the Ropsten test network. Upon comparing with existing schemes, we observe that
our protocol is efficient and scalable.
1 INTRODUCTION
Outsourcing storage, as well as computation to a
cloud service provider (CSP), has acquired signifi-
cant popularity among Small and Medium-sized En-
terprises (SMEs). Outsourcing increases security ef-
fectiveness and reduces maintenance costs. However,
directly uploading the data in plaintext form to cloud
service providers (CSP) is subject to risk. An unau-
thorized person can misuse or steal the data stored in
the cloud. To counter the issue, a different encryption
technique called searchable encryption (SE) is used.
SE allows a user to outsource its data in an encrypted
form to a cloud service provider. The cloud can per-
form any number of queries over that encrypted data
at the request of the client. In this process, the client
reveals some controlled amount of information about
the data to the CSP. Thus, privacy of such schemes
is determined by the amount of leakage upon query-
ing over the encrypted database. A malicious server
may not return the correct result, but the users should
have the ability to check whether the result is com-
plete and derived from the actual state of the database.
This is possible only when the client can verify an SE
scheme. A client can be malicious and try to cheat
a
https://orcid.org/0000-0002-7433-0497
b
https://orcid.org/0000-0002-3089-2535
CSP. If the client is the only one involved in verifica-
tion, it can intentionally claim that it got an incorrect
result to avoid paying the CSP. So, when none of the
parties are trusted, we need an SE scheme that is ver-
ifiable by both parties. Blockchain provides service
integrity for storage as well as computation. In ad-
dition, by using Ethereum-based smart contracts (Bu-
terin, 2020), all operations can be executed automat-
ically and trustfully. It efficiently makes data sharing
convenient (Jiang et al., 2019).
However, it is a challenging task to outsource
data in an untrusted distributed environment without
leaking a significant amount of information about the
dataset and queries. In most of the previous works
(Fan et al., 2020),(Wang et al., 2018),(Sardar and Ruj,
2019), the client is assumed to be honest. Some recent
work, such as Jiang et al. (Jiang et al., 2019) consider
a fully-malicious setup where the client can behave
maliciously from the beginning of the protocol. They
used cloud storage to store encrypted files and smart
contracts to store encrypted indexes for a single key-
word search. However, the actual result of a search
is not returned. Secondly, the blockchain is simply
used as verifiable storage, incurring a high cost. Guo
et al. (Guo et al., 2020) used the smart contract to
store the verification tag. Thus, in both cases, most
of the computation is done either by the client (Jiang
698
Sardar, L. and Mazumdar, S.
Fidelis: Verifiable Keyword Search with No Trust Assumption.
DOI: 10.5220/0012082700003555
In Proceedings of the 20th International Conference on Security and Cryptography (SECRYPT 2023), pages 698-703
ISBN: 978-989-758-666-8; ISSN: 2184-7711
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)

et al., 2019) or by the server (Guo et al., 2020), and
the blockchain is used for storage purposes.
In another work (Guo et al., 2022), the authors
have proposed a solution where both the cloud server
and the client are malicious, but their schemes con-
sider the client to be quasi-malicious. The assump-
tion is used for all existing schemes, including (Li
et al., 2020), (Guo et al., 2020), (Miao et al., 2022)
etc. These schemes fail when the client uploads in-
correct encrypted data and/or manipulated encrypted
search index. If the pre-computed search results and
verification information are incorrect, there is no way
for the CSP to check. Such a client can cheat and deny
payment to the cloud, even if the latter has performed
the search correctly. Our aim is to suggest a scheme
that addresses all these shortcomings.
Our Contribution: We propose a novel single key-
word search scheme called Fidelis that aims to pro-
vide verifiability without requiring any trust assump-
tions. To achieve this goal, we utilize the Ethereum
blockchain platform to enable fair interactions be-
tween the cloud and the client. Unlike other schemes,
we do not store any data on the blockchain except
for certain constant-size information that is crucial
for valid search and result verification. Our proto-
col ensures fairness and confidentiality even in the
presence of fully malicious participants. Addition-
ally, we develop prototypes and test them on the Rop-
sten test network using real-world data. Our experi-
mental analysis indicates that our proposed scheme is
highly efficient and feasible to implement, making it
a promising solution for practical use cases.
Organization: Section 2 presents necessary back-
ground knowledge. Section 3 provides detailed de-
scription of Fidelis. In Section 4, we evaluate the effi-
ciency of Fidelis. We conclude the paper in Section 5.
2 PRELIMINARIES
System and Adversarial Model: There are three enti-
ties - owner, server and user.
The owner of the database Owner (O) is fully-
malicious and may follow two strategies: (a) correctly
uploading data and search index but falsely blaming
the cloud to obtain search results without payment,
or (b) manipulating the data initially to obtain search
results without payment.
Server (S) stores encrypted data and search index, and
provides storage and computation services. It may in-
tentionally provide incomplete or incorrect results to
reduce its costs, and is considered fully malicious.
User (U) is a client who uses the database. The owner
can also be one of the users. It is fully-malicious as
owner. We assume, the owner and the users belong
to the same organization, a user trusts the owner, and
the owner will never collude with the server to cheat
a user.
Apart from these, Blockchain (B) used here is a public
blockchain (e.g. Ethereum) that helps to verify the
execution of the search protocol. The client may act
as an owner of the database as well as the user.
TSet: A tuple set TSet (Cash et al., 2013) is a
data structure consisting of a tuple of algorithms
(TSetSetup,TSetGetTag,TSetRetrieve) briefly
described as follow.
• TSetSetup takes as input a security parameter λ
and an array T of lists of equal-length bit strings in-
dexed by the elements of W . It outputs a pair (TSet,
K
T
) where TSet is a tuple set data structure and K
T
is a key. Thus TSetSetup initiates the tuple set data
structure TSet and chooses a key K
T
at random.
• TSetGetTag takes as input the key K
T
and a key-
word w and outputs a search trapdoor stag
w
∈{0,1}
λ
.
• TSetRetrieve takes the TSet and a search trap-
door stag
w
as input and returns a list of strings.
We say that a TSet is correct if for all W , T,
and any w ∈W , TSetRetrieve(TSet,stag
w
) =T[w]
when (TSet,K
T
) ← TSetSetup(T) and stag
w
←
TSetGetTag(K
T
,w).
Interval based Sorted Merkle Tree (IbSMT): Since
we only require non-membership proof, we take
interval-based sorted Merkle tree (IbSMT). IbSMT is
the same as SMT (as Sorted Merkle Tree) (Dahlberg
et al., 2016) except for the leaves. For example, given
a sorted set S = {x
1
,x
2
,... ,x
n
}, SMT keeps x
i
s in the
leaf node. However, IbSMT uses elements of
¯
S =
{y
0
,y
1
,... ,y
n
} as its leaf node, where y
i
= x
i
||x
i+1
.
The two additional elements, x
0
and x
n+1
, are the
minimum and maximum bound and ∀i ∈ [1,n],x
i
∈
(x
0
,x
n+1
). x
0
and x
n+1
can be taken as bit-strings of
all 0 and 1 respectively. An IbSMT data structure con-
sists of three algorithms - BuildTree, NMSearch and
NMVerify:
• IbSMT ←BuildTree(S): It takes a set S and outputs
the sorted Merkle tree IbSMT where the leaves are the
intervals constructed as above, i,e., elements from
¯
S.
• pf
n
← NMSearch(IbSMT,x): Given an element x,
the algorithm finds two x
i
and x
i+1
such that x
i
< x <
x
i+1
and outputs the membership proof pf
n
for the
interval y
i
←x
i
||x
i+1
in
¯
S. p f
n
is the non-membership
proof of x in S.
• b ← NMVeri f y(IbSMT.root, pf
n
,x): It outputs
membership verification bit b result for x and the
Fidelis: Verifiable Keyword Search with No Trust Assumption
699
proof pf
n
. The verification is done with the help of
the root of IbSMT.
Definitions and Terminologies: We define a ver-
ifiable keyword search scheme VKS as a tuple of
algorithms (KeyGen, Build, SrchTknGen, Search,
VerifySrch) briefly described as follows.
• K ← KeyGen(1
λ
): is a Probabilistic Polynomial
Time (PPT) algorithm run by the O that takes a se-
curity parameter 1
λ
and outputs secret key K.
• (EDB,ξ,α) ← Build(DB,K): O runs this PPT al-
gorithm that takes the dataset DB and the secret key
K as input and outputs an encrypted database EDB,
an encrypted index ξ, and auxiliary data α. α consists
of two parts α
o
and α
s
that are stored by the owner
and the server, respectively.
• τ
w
← SrchTkn(w, K): O runs this PPT algorithm
that generates an encrypted search trapdoor τ
w
for a
keyword w with the help of K.
•(R
w
, pf
w
) ←Search(ξ,α
s
,τ
w
): with this PPT algo-
rithm, S searches over ξ for τ
w
and returns the search
result R
w
to the client together with a proof pf
w
.
• b
w
← VerifySrch(R
w
, pf
w
,α
o
): Given the result
R
w
, proof p f
w
and auxiliary data α
o
, U runs this PPT
algorithm, interacting with cloud, and outputs the ver-
ification bit b
w
.
Correctness: Given a security parameter λ ∈N, a ver-
ifiable keyword search scheme is said to be correct, if
for any key K generated using KeyGen(1
λ
) and for all
sequences of search operations, the algorithm Search
outputs the correct set of identifiers, except with a
negligible probability, and for each received correct
result, the result will be verified correctly by the algo-
rithm VerifySrch.
3 OUR PROPOSED SCHEME
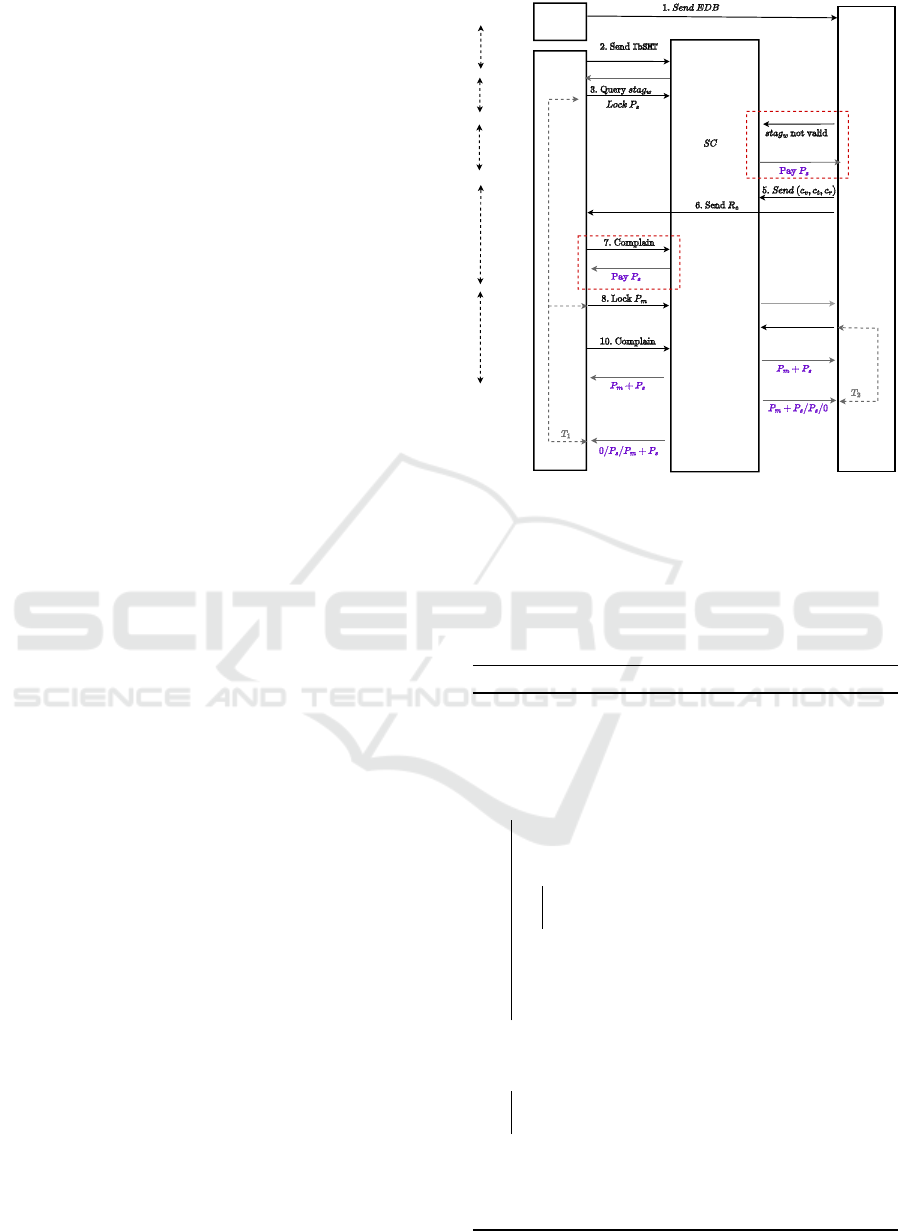
The steps of the protocol Fidelis are encoded in the
smart contract. Owner shares the encrypted database
with the cloud server and sends the keyword space to
the user. The latter needs to pay the cloud server for
retrieval of data against a query. This is enabled by
locking coins, denominated in the native currency of
the blockchain, in the smart contract. User sends a
query to the server and the latter returns the result. If
the server has performed his actions correctly, it gets
the coins, else the coins are refunded to the user. The
outline of the protocol is provided in Fig. 1.
Initialization: A tuple of keys, K = (K
s
,
¯
K
s
,K
T
), is
generated by the owner. K
s
is a λ-bit string, taken
at random, used to encrypt the keywords that a user
Cloud
User
Smart
Contract
4. Complain
If User malicious
Initialized
Locked
Complain not valid
Complain valid
Server
Initialization
Query
Query
Validity
Response
Payout
Complain valid
Refund on Lock
Pay on Reveal
Complain valid
9. Reveal
If response
not correct
Owner
Figure 1: Outline of the protocol.
intends to query.
¯
K
s
is a λ-bit string, taken at ran-
dom, used to compute verification tags corresponding
to each queried keyword. A pseudo-random function
(PRF) F : {0,1}
λ
×{0,1}
λ
→ {0, 1}
λ
is used for en-
cryption using keys K
s
and
¯
K
s
. Different hash func-
Algorithm 1: Fidelis.Init(DB).
K
s
,
¯
K
s
$
−→ {0,1}
λ
for PRF F
Parse DB as {id
1
,... ,id
d
}
Find {W
1
,... ,W
d
}
W ← ∪
d
i=1
W
i
; StgSET = φ; T = φ
for w ∈ W do
Initialize t to be an empty list
Set K
w
← F(K
s
,w); vtag
w
← H
1
(
¯
K
S
,w)
for i = 1 to n
w
= |DB(w)| do
e
i
← Sym.Enc(K
w
,id
w
i
)
append e
i
to t.
end
h
w
← H
2
(vtag
w
||e
1
||e
2
||... ||e
n
w
)
append h
w
to t.
Set T[w] ← t.
end
(TSet,K
T
) ← TSetSetup(T).
for each w ∈ W do
stag
w
← TSetGetTag(K
T
,w)
StgSET ← StgSET ∪{stag
w
}
end
IbSMT = BuildTree(StgSET)
O keeps K = (K
s
,
¯
K
s
,K
T
)
O sends EDB, ξ = TSet,IbSMT to S.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
700

tions H
1
, H
2
, and H
3
are used for generating commit-
ments. Each of them is a cryptographic one-way hash
function {0,1}
∗
→ {0,1}
λ
. The owner uses a sym-
metric encryption Sym to encrypt each file in DB and
generates EDB. We assume every encrypted file f
i
can be accessed with the identifier id
i
, and the owner
gives this encryption key to the users.
We use the TSet (see Section 2) data structure
to construct encrypted index for the database DB =
{id
i
: i = 1,..., d}. Let W = ∪
d
i=1
W
i
be the set of
keywords present in DB where W
i
is the set of key-
words in the file with identifier id
i
. For each keyword
w ∈ W , a list t = [e
1
,e
2
,... ,e
n
w
,h
w
] is generated by
the owner. We define DB(w) ⊂ DB as the set of file
identifiers that contain the keyword w and n
w
is the
cardinality of DB(w). e
i
← Sym.Enc(K
w
,id
w
i
),1 ≤
i ≤n
w
is the encrypted identifiers of the files contain-
ing w and h
w
←H(vtag
w
||e
1
||e
2
||... ||e
n
w
) is the hash
value that binds the set of identifiers and vtag
w
. Here
vtag
w
= H
1
(
¯
K
S
,w) is the verification tag used to ver-
ify the correctness of search results. An array T of
length W is used to store the list t for each keyword,
i.e., T[w] =t. Finally, TSet for the array T is gener-
ated as (TSet,K
T
) ← TSetSetup(T).
We encrypt each keyword w ∈ W using key K
T
,
generate stag
w
, and store it in StgSET. The encryp-
tion is done by TSetSetup. An IbSMT is built for
StgSET. The key K = (K
s
,
¯
K
s
,K
T
) and root of IbSMT,
defined α
o
= IbSMT.root, are shared with the user.
The encrypted search index ξ = TSet is outsourced
to the cloud along with α
s
= IbSMT. Algo. 2 de-
scribes the initialization which is generating the keys
and building the encrypted database.
Query: To query a keyword w, user computes search
token τ
w
= stag
w
and sends it to the server. It ini-
tializes the smart contract SC
w
with the root of IbSMT
(see Algo. 3). The user calls StoreandLock in SC
w
,
where it locks P
s
coins for time T
1
and stores stag
w
.
On receiving stag
w
, the server checks if the
value exists in IbSMT. If stag
w
/∈ IbSMT, the server
generates a proof of non-membership, p f
n
, using
IbSMT.root and submits it to SC
w
. Upon evaluation,
if the proof p f
n
is found to be correct, then the server
receives P
s
coins, and the protocol aborts. If the proof
is not valid, then the server does not get any payment,
P
s
gets unlocked, and the protocol is aborted.
Response and Commit: If stag
w
exists in IbSMT, the
server searches for stag
w
in TSet. Then it encrypts t
using key K
v
and generates R
e
. It shares R
e
with the
user and sends commitment of t (c
t
), commitment of
R
e
(c
r
), commitment of K
v
(c
v
), and h
w
to SC
w
.
Check Response: The user checks if the commitment
of R
e
is c
r
. If not, then it complaints to SC
w
and un-
locks P
s
coins. Else, the it regenerates vtag
w
, which is
used to generate h
w
. The user submits vtag
w
to SC
w
and locks additional P
m
coins.
Algorithm 2: Fidelis.Search(w).
Algorithm 2: Fidelis.Search(w)
User (U):
takes K = (K
s
,
¯
K
s
,K
T
) and a keyword w.
computes stag
w
← TSetGetTag(K
T
,w)
executes StoreandLock(stag
w
,P
s
) in SC
w
and locks P
s
coins till time T
1
.
Server (S):
if IbSMT.root in SC
w
̸= α
s
, then S aborts
if stag
w
does not exist then
p f
n
← NMSearch(IbSMT,x)
if QueryValid(p f
n
) = valid then
S gets P
s
coins and protocol aborts.
else
P
s
gets unlocked and abort.
else if stag
w
exists then
t ← TSetRetrieve(TSet,stag
w
)
[e
1
,e
2
,.. .,e
n
w
,h
w
] ← t; K
v
$
←− {0, 1}
λ
;
R
e
← Sym.Enc(K
v
,t)
c
t
← H
3
(t); c
v
← H
3
(K
v
); c
r
← H
3
(R
e
)
SendCommitment(c
t
,c
r
,c
v
,h
w
)
Sends R
e
to the U
end
User:
if c
r
̸= H
3
(R
e
) then
U complains as v
b
=
ComplainResponse(R
e
);
if v
b
is valid bit then
B unlocks P
s
coins and aborts.
else
Computes vtag
w
← H
1
(
¯
K
S
,w)
StoreandLock(vtag
w
,P
m
)
locks P
m
coins by B in SC
w
till time T
1
.
end
Server:
if h
w
̸= H
2
(vtag
w
||e
1
||e
2
||.. .||e
n
w
) then
abort!
else Reveal(K
v
)
User:
[e
1
,e
2
,.. .,e
n
w
,h
w
] ← Dec(K
v
,R
e
)
h
′
w
← H
2
(vtag
w
||e
1
||e
2
||.. .||e
n
w
)
if h
′
w
̸= h
w
or H
3
(t) ̸= c
t
then
p f
e
= (R
e
,t)
executes Complain(p f
e
) by B in SC
w
if current time < T
2
then
B evaluates correctness of p f
e
else S gets P
m
+ P
s
coins
else if h
′
w
= h
w
then
U re-generates K
w
← F(K
s
,w);
U decrypts each e
i
as
id
w
i
← Sym.Dec(K
w
,e
i
)
U gets R = {id
1
,id
2
,.. .,id
n
w
}
S receives payment after time T
2
.
end
Fidelis: Verifiable Keyword Search with No Trust Assumption
701

Commit Reveal: Using vtag
w
and e
′
i
s, if it is possible
to generate h
w
, then the server reveals the decommit-
ment of c
v
. Else, it aborts.
Algorithm 3: Smart Contracts.
Algorithm 2: Fidelis Search(w)
User (U):
takes K = (K
s
,
¯
K
s
,K
T
) and a keyword w.
computes stag
w
← TSetGetTag(K
T
,w)
executes StoreandLock(stag
w
,P
s
) in SC
w
and locks P
s
coins till time T
1
.
Server (S):
if IbSMT.root in SC
w
̸= α
s
, then S aborts
if stag
w
does not exist then
p f
n
← NMSearch(IbSMT,x)
if QueryValid(p f
n
) = valid then
S gets P
s
coins and protocol aborts.
else
P
s
gets unlocked and abort.
else if stag
w
exists then
t ← TSetRetrieve(TSet,stag
w
)
[e
1
,e
2
,.. ., e
n
w
,h
w
] ← t; K
v
$
←− {0, 1}
λ
;
R
e
← Sym.Enc(K
v
,t)
c
t
← H
3
(t); c
v
← H
3
(K
v
); c
r
← H
3
(R
e
)
SendCommitment(c
t
,c
r
,c
v
,h
w
)
Sends R
e
to the U
end
User:
if c
r
̸= H
3
(R
e
) then
U complains as v
b
=
ComplainResponse(R
e
);
if v
b
is valid bit then
B unlocks P
s
coins and aborts.
else
Computes vtag
w
← H
1
(
¯
K
S
,w)
StoreandLock(vtag
w
,P
m
)
locks P
m
coins by B in SC
w
till time T
1
.
end
Server:
if h
w
̸= H
2
(vtag
w
||e
1
||e
2
||.. .||e
n
w
) then
abort!
else Reveal(K
v
)
User:
[e
1
,e
2
,.. ., e
n
w
,h
w
] ← Dec(K
v
,R
e
)
h
′
w
← H
2
(vtag
w
||e
1
||e
2
||.. .||e
n
w
)
if h
′
w
̸= h
w
or H
3
(t) ̸= c
t
then
p f
e
= (R
e
,t)
executes Complain(p f
e
) by B in SC
w
if current time < T
2
then
B evaluates correctness of p f
e
else S gets P
m
+ P
s
coins
else if h
′
w
= h
w
then
U re-generates K
w
← F(K
s
,w);
U decrypts each e
i
as
id
w
i
← Sym.Dec(K
w
,e
i
)
U gets R = {id
1
,id
2
,.. ., id
n
w
}
S receives payment after time T
2
.
end
Algorithm 3: Smart Contracts
Function Initialize(IbSMT.root):
Record IbSMT.root in B
Function StoreandLock(value,P):
Lock P in the contract
Record value in B
if current time is T
1
then
Unlock coins locked in contract for
User
Function QueryValid(p f
n
):
if p f
n
is valid w.r.t IbSMT.root then
Unlock P
s
for Server
Function
SendCommitment(c
t
,c
r
,c
v
,h
w
):
Record c
t
,c
r
,c
v
,h
w
in B
Function Reveal(K
v
):
Store K
v
in B
if current time is T
2
then
Unlock coins locked in contract for
Server
Function ComplainResponse(R
e
):
if c
r
̸= H
3
(R
e
) then
Unlock coins locked in contract for
User
Function Complain(p f
e
):
Parse p f
e
if p f
e
= (K
v
,c
v
) and c
v
̸= H
3
(K
v
) then
Unlock P
s
+ P
m
for User
else
Compute t
′
=Dec(K
v
,R
e
)
(e
1
||e
2
||.. .||e
n
i
,h
w
) ← Parse(t
′
)
Compute
h
′
w
= H
2
(vtag
w
||e
1
||e
2
||.. .||e
n
i
)
if h
′
w
̸= h
w
or R
e
̸= Sym.Enc(K
v
,t)
then
Unlock P
s
+ P
m
for User;
else
Unlock P
s
+ P
m
for Server;
end
end
Response Retrieval: The user checks the commitment
of K
v
. If unmatched, it raises a complaint and submits
a proof p f
e
= (K
v
,c
v
) to the function complain in SC
w
before time T
2
. The client has to raise the complaint
and send proof of error p f
e
within time T
2
, else the
server gets the payment P
m
+P
s
. The waiting times T
1
and T
2
can be fixed at the beginning of the protocol.
If K
v
is valid, the user decrypts R
e
using K
v
and
gets t. Next, he parses t to get e
′
i
s and recomputes
h
′
w
. If h
′
w
̸= h
w
or c
t
! = Commitment(t), he submits
a proof of invalid response to SC
w
, again before time
T
2
. SC
w
evaluates whether the complaint raised by the
user is valid. If valid, then the user gets a refund of
P
m
+ P
s
coins. If not, then the server gets the total
amount for performing the task correctly.
If h
′
w
= h
w
, the user decrypts e
i
s using K
w
=
F(K
s
,w). If the user has not raised a complaint within
T
2
, then the server claims the full amount.
Fidelis is verifiable by both the user and the server.
If anyone cheats, it can be detected by others. Fair-
ness is guaranteed as well. The server cannot get pay-
ment from the user without giving the correct result.
Moreover, there is no way a user can get a correct
result from the server without payment. Confidential-
ity is retained as there is no leakage of information
that would benefit an adversary. The proofs justifying
these properties along with the proof for correctness
and soundness will be discussed in the full version of
the paper.
4 PERFORMANCE ANALYSIS
We implement and evaluate the protocol w.r.t.
Ethereum as a blockchain platform. The smart con-
tracts are written in Solidity language and deployed
in the Ropsten test network.The gas price is 38.66
GWei (or 0.00007132 USD on 9
th
, February, 2023).
We vary number of files from 10K to 100K, keywords
from 35K to 109K and queries from 10 and 1000.
The gas cost for deploying the smart contract
and for executing Initialize are around 163.957
USD (gas usage: 2298905) is 12.277 USD (gas us-
age: 172144) respectively. For querying a existing
or a non-existing keyword, the gas cost for executing
StoreandLock for a single query remains the same
which is is around 7.366 USD (gas usage: 103287).
(i) Searching existing keyword: For a single exist-
ing keyword, executing SendCommitment takes
16s and costs is 9.487 USD (gas usage: 133021)
payed by the server. They are same for
StoreandLock. However, executing Reveal,
they are 21 s, and 10.045 USD (gas usage:
140846). Finally, the time taken to finalize the
payment is 18s and the gas cost is 2.857 USD (gas
usage: 40063).
(i) Searching a non-existing keyword: The only func-
tion that gets executed in QueryValid, where the
proof size varies with the size of the database. The
time taken for execution varies between 20s and
34s whereas the gas cost increases slightly from
41.296 USD (gas usage: 579030) to 43.528 USD
(gas usage: 610329).
Apart from this, we plot the initial encrypt time
taken by owner in Fig.2(a). It varies between 38s
SECRYPT 2023 - 20th International Conference on Security and Cryptography
702

(a) Owner Computation Time upon varying file size
(b) User and Server’s Computation Time upon varying
number of keywords
Figure 2: Time taken for computation.
and 360s with the increase in the size of the database.
For the bad case, when a given keyword is not a
part of the database, the computation time of user
is around 0.02ms but in the case of server, the time
varies between 25ms to 70ms. If the keyword is part
of the database, then with an increase in the number
of keywords, the user time varies between 0.045ms
to 0.1ms, and the server time varies between 0.05ms
and 0.15ms, as shown in Fig.2(b).
We observe that querying existing keywords, the
gas cost is around 23 USD. In Guo et al. (Guo
et al., 2022), the gas cost for uploading a digest in-
creases with the increase in index pairs, varying be-
tween 712.08 USD (gas usage: 9984351, for 1K index
pairs) and 14,252.8388 USD (gas usage:199843506,
for 16K index pairs). In Fidelis, the gas cost for up-
loading data/locking coins is around 46.877 USD (gas
usage: 65727700), being invariant with the frequency
of occurrence of the keyword. The cost of storage
on-chain is fixed (only 320 B) for our protocol, com-
pared to (Guo et al., 2022), where the cost of storage
increases to 1MB when the number of index-pairs is
20K. For non-existing keywords, the smart contract
needs to verify whether the proof sent by server is cor-
rect. The length of the proof increases with the size
of the database, hence the gas cost is much higher.
5 CONCLUSION
We have proposed Fidelis, a blockchain-based search-
able encryption scheme that operates without any
trust assumption and ensures the verifiability of
search results. We provide proof of its security and
fairness. We deploy and test our prototype in the
Ethereum Ropsten testnet with real-life data which
demonstrates the feasibility and efficiency of our pro-
posed scheme. We can see that the protocol can be
executed by all involved parties efficiently.
REFERENCES
Buterin, V. (2020 (accessed November 4, 2020)). Ethereum.
Cash, D., Jarecki, S., Jutla, C. S., Krawczyk, H., Rosu,
M., and Steiner, M. (2013). Highly-scalable search-
able symmetric encryption with support for boolean
queries. In Advances in Cryptology - CRYPTO 2013 -
33rd Annual Cryptology Conf., pp 353–373.
Dahlberg, R., Pulls, T., and Peeters, R. (2016). Efficient
sparse merkle trees - caching strategies and secure
(non-)membership proofs. In Secure IT Systems - 21st
Nordic Conf., NordSec 2016, vol. 10014 of LNCS, pp.
199–215.
Fan, C., Dong, X., Cao, Z., and Shen, J. (2020). VCKSCF:
efficient verifiable conjunctive keyword search based
on cuckoo filter for cloud storage. In, 19th IEEE Int.
Conf. on Trust, Security and Privacy in Computing
and Communications, TrustCom 2020, pp. 285–292.
IEEE.
Guo, Y., Zhang, C., and Jia, X. (2020). Verifiable
and forward-secure encrypted search using blockchain
techniques. In ICC 2020 - 2020 IEEE Int. Conf. on
Communications (ICC), pp. 1–7.
Guo, Y., Zhang, C., Wang, C., and Jia, X. (2022). To-
wards public verifiable and forward-privacy encrypted
search by using blockchain. IEEE Trans. on Depend-
able and Secure Computing, pp. 1–1.
Jiang, S., Liu, J., Wang, L., and Yoo, S. (2019). Verifiable
search meets blockchain: A privacy-preserving frame-
work for outsourced encrypted data. In 2019 IEEE Int.
Conf. on Communications, ICC 2019, pp. 1–6. IEEE.
Li, H., Zhou, H., Huang, H., and Jia, X. (2020). Veri-
fiable encrypted search with forward secure updates
for blockchain-based system. In Wireless Algorithms,
Systems, and Applications - 15th Int. Conf., WASA
2020, vol. 12384, LNCS, pp. 206–217. Springer.
Miao, Y., Tong, Q., Deng, R., Choo, K.-K. R., Liu, X.,
and Li, H. (2022). Verifiable searchable encryption
framework against insider keyword-guessing attack in
cloud storage. IEEE Trans. on Cloud Computing,
10(2):835–848.
Sardar, L. and Ruj, S. (2019). Fspvdsse: A forward secure
publicly verifiable dynamic sse scheme. In Provable
Security - 13th Int. Conf., ProvSec 2019, pp. 355–371.
Wang, J., Chen, X., Sun, S., Liu, J. K., Au, M. H., and
Zhan, Z. (2018). Towards efficient verifiable conjunc-
tive keyword search for large encrypted database. In
Computer Security - 23rd European Symposium on
Research in Computer Security, ESORICS 2018, vol.
11099, LNCS, pp. 83–100. Springer.
Fidelis: Verifiable Keyword Search with No Trust Assumption
703
