
Lattice-Based Threshold Signature Implementation for Constrained
Devices
Patrik Dobias
1 a
, Sara Ricci
1 b
, Petr Dzurenda
1 c
, Lukas Malina
1 d
and Nikita Snetkov
2,3 e
1
Department of Telecommunications, Brno University of Technology, Brno, Czech Republic
2
Cybernetica AS, M
¨
aealuse 2/1, 12618 Tallinn, Estonia
3
Tallinn University of Technology, Akadeemia Tee 15a, 12618 Tallinn, Estonia
Keywords:
Threshold Signature, Lattice-Based Cryptography, Software Implementation, Dilithium, Homomorphic
Commitment, Embedded Systems, Constrained Devices.
Abstract:
Threshold signatures have gained increased attention especially due to their recent applications in blockchain
technologies. In fact, current cryptocurrencies such as Bitcoin, and Cardano started to support multi-signature
transactions. Even if the Schnorr-based threshold signatures improve the blockchain’s privacy and scalability,
these schemes do not provide post-quantum security. In this paper, we propose the optimization of the DS2
lattice-based (n,n)-threshold signature scheme and present its practical implementation. Moreover, we evalu-
ate our optimized implementation of the DS2 scheme on different platforms. The results demonstrate that our
implementation is easily portable and executable on constrained devices based on ARM Cortex-A53, ARM
Cortex-M3, and ESP32 architectures.
1 INTRODUCTION
In recent years, the use of distributed signature
schemes has received increasing attention, mainly be-
cause of their usage in the blockchain field. A typical
blockchain involves the usage of a signature scheme
for the verification of transactions that are signed only
with one private key, resulting in a single point of
failure. This means that the attacker who compro-
mises the device that stores that private key may cre-
ate a new transaction signed with this key. In con-
trast, multi-signature transactions are signed using at
least two shares of a private key that can be stored on
different devices. The use of multi-signature trans-
actions offers multiple benefits (Freemanlaw, 2022),
e.g., 1) increased security - shares are stored
across multiple devices, eliminating an attack on a
single device, 2) private key backup - losing the
private key share does not lead to access loss as long
as there are enough shares, 3) divided possession
- possession of the cryptocurrency is divided be-
a
https://orcid.org/0000-0002-7321-7003
b
https://orcid.org/0000-0003-0842-4951
c
https://orcid.org/0000-0002-4366-3950
d
https://orcid.org/0000-0002-7208-2514
e
https://orcid.org/0000-0002-1414-2080
tween multiple parties. In this context, threshold
signatures can be used to securely sign messages,
where t parties of the n authorized parties collabo-
rate in the signing process. Current threshold signa-
tures are mainly based on RSA (Damg
˚
ard and Ko-
prowski, 2001; Shoup, 2000) and Elliptic Curve Digi-
tal Signature Algorithm (ECDSA) signatures (Castag-
nos et al., 2020; Cogliati et al., 2018; Damg
˚
ard et al.,
2020; Gennaro and Goldfeder, 2018; Lindell and Nof,
2018). Alternative threshold signature (Komlo and
Goldberg, 2020; Ricci et al., 2022) are based on
Schnorr’s protocol. Even if having more communi-
cation overload, these latter schemes guarantee ro-
bustness as a main feature. For instance, in (Komlo
and Goldberg, 2020), honest participants can detect
and disqualify a malicious participant if he/she mis-
behaves. The Schnorr-based multi and threshold sig-
natures received significant interest recently, espe-
cially in the context of multi-signature transactions.
In fact, several cryptocurrencies (e.g., Bitcoin, Car-
dano, Polkadot, Kusama, Zilliqa, and Decred) start to
integrate the Schnorr signature into their blockchain.
This is due to Schnorr-based distributed signatures’
simplicity, efficiency, flexibility, and short signature
bit length.
All aforementioned schemes rely on Non-
deterministic Polynomial (NP) problems, i.e., Inte-
724
Dobias, P., Ricci, S., Dzurenda, P., Malina, L. and Snetkov, N.
Lattice-Based Threshold Signature Implementation for Constrained Devices.
DOI: 10.5220/0012112700003555
In Proceedings of the 20th International Conference on Security and Cryptography (SECRYPT 2023), pages 724-730
ISBN: 978-989-758-666-8; ISSN: 2184-7711
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)
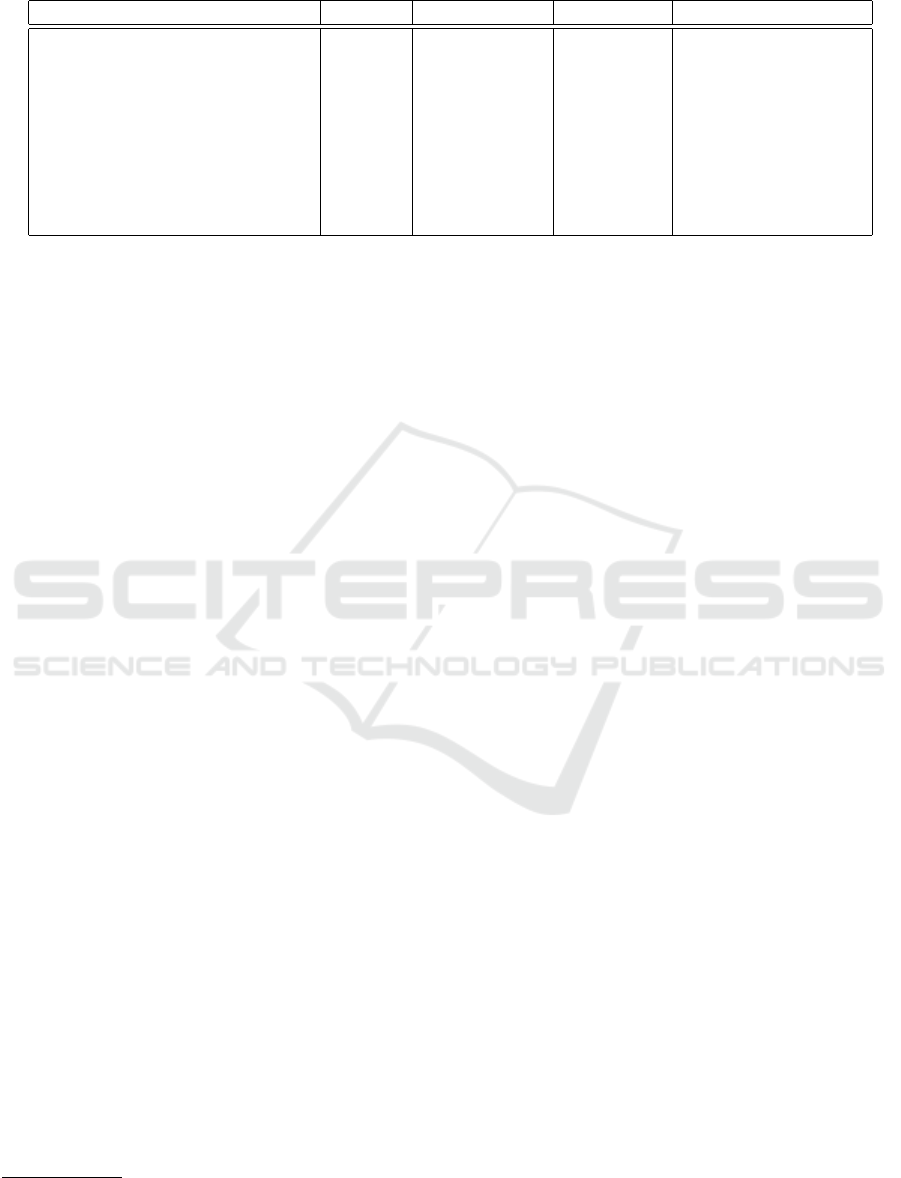
Table 1: Comparison of existing lattice-based threshold signature schemes.
Scheme Problem Type Rounds Building Blocks
(Benhamouda et al., 2016) H&S t-out-of-n 1 Honest majority MPC
(Boneh et al., 2018) FSwA t-out-of-n 1 Threshold FHE
(Fukumitsu and Hasegawa, 2020) FSwA Multisignature 3 -
(Vakarjuk et al., 2021) FSwA 2-out-of-2 3 Homomorphic Hash
(Boschini et al., 2022) FSwA Multisignature 2 (1 offline) Linear combination
(Chen, 2023) FSwA Multisignature 2 Linear combination
(Laud et al., 2022) FSwA 2-out-of-2 3 Homomorphic Com.
(Damg
˚
ard et al., 2022) FSwA n-out-of-n 2 Homomorphic Com.
(Liu et al., 2022) FSwA n-out-of-n 3 Homomorphic Com.
“FSwA” states for s Fiat–Shamir with aborts signatures, ”H&S” for hash-and-sign, and ”MPC” for multi-party computation.
ger Factorization Problem (IFP), Discrete Logarithm
Problem (DLP), and Elliptic Curve DLP (ECDLP)
that are vulnerable to attacks run on quantum com-
puters. In particular, Shor’s algorithm (Bernstein,
2009) allows solving the aforementioned NP problem
in polynomial time. Therefore, the need is to shift to-
wards post-quantum schemes, which are considered
safe against quantum computer attacks. To support
research on post-quantum schemes, the National In-
stitute of Standards and Technology (NIST) initiated
a standardization process in 2016, which led to the se-
lection of three signature schemes for standardization
in 2022
1
, specifically Dilithium and Falcon, which are
lattice-based, and SPHINCS+, which is hash-based.
However, this standardization process focuses only on
plain digital signatures and does not cover distributed
signature schemes. Therefore, distributed signatures’
complexity, their practical usability, and their imple-
mentability on constrained devices for the current In-
ternet of Things (IoTs) ecosystem are not researched.
It is noteworthy that NIST has recently published a
draft for their First Call for Multi-Party Threshold
Schemes (Brandao and Peralta, 2023), which signals
their interest in advancing research in this area.
1.1 Related Work
Table 1 shows a comparison of existing lattice-based
threshold signatures. In (Vakarjuk et al., 2021), au-
thors presented a two-party lattice-based Dilizium
signature scheme that follows the Fiat-Shamir with
Aborts paradigm. Moreover, the scheme is based on
the variant of CRYSTALS-Dilithium scheme (Ducas
et al., 2018), which was presented in (Kiltz et al.,
2018), so it does not require sampling from a dis-
crete Gaussian distribution. They considered a similar
approach to (Damg
˚
ard et al., 2022), but a homomor-
phic hash function was deployed instead of homomor-
1
https://csrc.nist.gov/Projects/
post-quantum-cryptography/selected-algorithms-2022
phic commitments, as they find homomorphic com-
mitments computationally inefficient. (Laud et al.,
2022) presented an updated version of the Dilizium
scheme, where they came back to their previous deci-
sion and used a homomorphic commitment scheme.
Furthermore, they also applied compression mecha-
nisms from the original CRYSTALS-Dilithium pro-
posal to make it closer to the version submitted for
the NIST standardization. In (Damg
˚
ard et al., 2022),
authors proposed a two-round n-out-of-n signature
scheme called DS2, a multi-signatures scheme, and
a trapdoor commitment from lattices. The signature
scheme relies on the homomorphic property of the
proposed commitment scheme and they are based on
the Dilithium-G scheme (Ducas et al., 2018). (Ben-
hamouda et al., 2016) presented a threshold signature
based on GPV hash-and-sign signatures. In particu-
lar, the signature size does not grow with the num-
ber of parties, but the signature requires computing
the lattice Gaussian sampling phase with a multiparty
computation. (Boneh et al., 2018) developed a gen-
eral solution for non-interactive, t-out-of-n threshold
signatures based on Fully Homomorphic Encryption
(FHE). Their proposal has both signature and verifi-
cation phases that do not dependent on the number of
participants. However, a trusted party is needed in the
set-up scheme in contrast with (Damg
˚
ard et al., 2022).
(Fukumitsu and Hasegawa, 2020) proposed a multi-
signature based on Dilithium with signature size com-
pression techniques on contrary to (Damg
˚
ard et al.,
2022) proposal. (Boschini et al., 2022) introduced a
lattice-based multi-signature scheme that does not re-
quire any additional primitive in the protocol. In this
way, the signature sizes are closer to one of a plain
digital signature. Moreover, the scheme consists of
only one online round, resulting in lower communi-
cation overhead. (Chen, 2023) presented an efficient
lattice-based two-round multi-signature scheme. The
scheme is based on Dilithium-G and has smaller pub-
lic keys and signatures compared to (Boschini et al.,
2022). Additionally, they also proposed a novel “dual
Lattice-Based Threshold Signature Implementation for Constrained Devices
725

signing simulation” technique that simulates multi-
signatures in the security proof without trapdoors. At
last, (Liu et al., 2022) proposed a multiparty signature
scheme with detectability in the industrial IoT. They
also implemented this scheme and benchmarked it for
different security levels and different numbers of par-
ties. It is important to notice that in a multi-signature
each signer has its public key instead of secret shares
of a single common public key as in threshold signa-
ture schemes.
1.2 Contribution and Paper Structure
In this work, we present the first implementation
of DS2 (n,n)-threshold signature scheme (Damg
˚
ard
et al., 2022). We optimize this scheme and define its
parameters to increase its computational speed, and
reduce its key, signature sizes, and communication
overhead. We do several benchmarks of our imple-
mentation on devices with different performances, in-
cluding constrained devices using ARM Cortex-A53,
ARM Cortex-M3, and ESP32 architectures. Our im-
plementation is easily portable and executable on con-
strained devices capable of running C applications.
The paper is organized as follows. Section 2
presents our DS2 architecture, choice of parameters,
and detailed description of our lightweight implemen-
tation written in C programming language. Section 3
presents the experimental benchmarks of our imple-
mentation on various constrained devices. In the last
section, we conclude this work.
2 IMPLEMENTATION DETAILS
This section describes our implementation of the DS2
scheme, which was implemented using the C pro-
gramming language. It depends only on the stan-
dard libc library. Furthermore, the implementation
uses CMake for project management, and therefore,
it is easily portable and executable on different plat-
forms and constrained devices capable of running C
applications. Additionally, a lattice-based trapdoor
commitment scheme was implemented with the pa-
rameters specified in Section 2.1. To be more pre-
cise, we implemented the three most important al-
gorithms, i.e., CGen, Commit, and Open algorithms.
The Commit algorithm was implemented to compute
com = ck · r +
0
x
reusing polynomial functions
for DS2 with different parameters, the commitment
key is generated per message using CGen algorithm
implemented as a hash function ck := H
3
(µ, pk), and
the Open algorithm is simply the Commit algorithm
Table 2: Choice of parameters for DS2 scheme.
n α σ B M
2 22 298694 27034695 1.7272
5 55 746735 67586737 1.2440
10 110 1493470 135173474 1.1153
20 220 2986940 270346948 1.0561
50 550 7467350 675867370 1.0221
with the comparison of commitments at the end. We
refer to (Damg
˚
ard et al., 2022) for more details. As
the original DS2 design is based on non-optimized
version of Dilithium-G (Ducas et al., 2018) that would
be inefficient to implement, we apply changes to each
phase based on the optimized version of Dilithium-G.
For each phase, a modified algorithm is shown and
implementation details are provided. The red marked
text indicates our changes in individual algorithms
compared to the original algorithms of DS2 (Damg
˚
ard
et al., 2022). Our implementation is open-source and
available on the public GitLab repository
2
.
2.1 Chosen Parameters
Since (Damg
˚
ard et al., 2022) does not provide
the instantiation of the parameters, the recom-
mended parameters for Security Level 128b from the
Dilithium-G specification (Ducas et al., 2018) were
used. Specifically, N = 256, q = 8380417,(k,ℓ) =
(4,4),η = 5,κ = 60, d = 12. Additional parameters
specific to the DS2 scheme were chosen to satisfy the
required bounds specified in (Damg
˚
ard et al., 2022)
and to reduce the complexity of communication and
the size of the resulting signature. For the differ-
ent number of parties n and targeting the total num-
ber of rejections during the signing phase M
n
= 3,
the parameters are presented in Table 2. In partic-
ular, M states for ”the expected number of restarts
until a single party can proceed”, B for ”the maxi-
mum L
2
-norm of signature share z
j
for j = 1,.. .,n,
σ for the ”standard deviation of the Gaussian distri-
bution”, and α for a ”parameter defining σ and M”.
Note that a new commitment needs to be sent any time
a rejection appears, so the transmitted data increases
by d
com
= 5888B for each rejection. Moreover, the
total transmitted data d
sig
increases linearly with the
number of rejections. Furthermore, the parameters for
the lattice-based commitment scheme were chosen to
satisfy the specified bounds. Specifically, the follow-
ing parameters were chosen: ¯s = 2059,s = 815,B =
48414,l = 23,w = 23.
2
https://gitlab.com/brno-axe/chess/ds2/ds2-opt-c-impl
SECRYPT 2023 - 20th International Conference on Security and Cryptography
726

2.2 Key Generation Phase
In the original DS2 scheme, the individual shares of
A matrix are exchanged between the parties followed
by the shares of part of public key t. In contrast, in
our implementation, participants have to collaborate
in creating the seed ρ which is then used to expand
matrix A as highlighted in Algorithm 1.
The matrix A is then sampled uniformly from
this seed, ensuring that it remains indistinguishable
from a uniformly distributed random matrix. During
the computation of the combined public key t
1
, we
used power2round rounding, as it is proposed in the
Dilithium-G scheme, to reduce the size of the trans-
mitted data. The total data transferred by a single
party is only dependent on the number of parties and
is calculated as d
gen
(n) = 1472 × (n − 1) B.
Algorithm 1: KeyGen(1
κ
).
1: ρ
n
← {0,1}
256
2: Send out ρ
n
and receive ρ
i
;i ∈[n −1]
3: ρ = H(ρ
1
|ρ
2
|...ρ
n
)
4:
¯
A := [A|I] ∈R
k×(ℓ+k)
q
; A ← R
k×ℓ
q
:= Sam(ρ)
5: t
n
:=
¯
As
n
;s
n
← S
ℓ+k
η
6: (t
n
1
,t
n
0
) := Power2Round(t
n
,d); g
n
:= H
2
(t
n
1
)
7: Send out g
n
and receive g
i
;i ∈[n −1]
8: Send out t
n
1
, receive t
i
1
and check
g
i
= H
2
(t
i
1
);i ∈[n −1]
9: t
1
:=
∑
i∈[n]
t
i
1
10: tr ∈ {0,1}
384
:= CRH(ρ||t
1
)
11: return pk = (ρ, t
1
), sk = (ρ,tr, s
n
,t
n
0
)
2.3 Signing Phase
During the signing phase, n parties collaborate to gen-
erate a valid signature. To reduce the size of the
signature, we use the Fiat-Shamir trick of express-
ing the signature as (c,z,r) instead of (com,z,r), as
shown in Algorithm 2. In this way, only a small chal-
lenge seed c is sent to the verifier instead of the full
commitment com. As a result of this, the resulting
signature size is reduced approximately by 3%. For
example, with 2 parties, we transfer 218128 B in-
stead of 224256 B. The commitment is then com-
puted during the verification phase using the recon-
structed vector of polynomials w. The signature is
still large compared to the standard signature size due
to the commitment randomness. Additionally, since
we use Power2Round algorithm during the key gen-
eration phase to reduce communication, computation
of the signature part z
n
2
needs to be altered as high-
lighted on line 8 in Algorithm 2. During the sign-
ing phase, there are two messages exchanged between
each party. First, the commitment to w
n
with size
d
com
n
= (|com| · ⌈log
2
q⌉ · N · k)/8 = 5888 B.
Followed by the signature part z
n
and r
n
with sizes
d
z
n
= (⌈log
2
q⌉ · (k + ℓ) · N)/8 = 5888 B and
d
r
n
= (⌈log
2
q⌉ · (l + 2w) · N · k)/8 = 203136 B.
The total data transferred by a single party during
signing also depends on the number of rejections.
Therefore only the average number can be computed
as d
sig
(n) = 226688 ×(n −1) B.
Algorithm 2: Sign(pk,sk
n
,µ ∈ M).
1: ck := H
3
(µ, pk)
2: w
n
:=
¯
Ay
n
;y
n
← D
ℓ+k
s
3: com
n
:= Commit
ck
(w,r
n
);r
n
← D(S
r
)
4: Send out com
n
and receive com
i
;i ∈[n −1]
5: c := H
0
(com,µ,tr);com =
∑
i∈[n]
com
i
6: z
n
:=
z
n
1
z
n
2
:= cs
n
+ y
n
7: Rejection sampling on (cs
n
,z
n
), with probabil-
ity min(1,D
l+k
s
(z
n
)/(M ·D
l+k
s
(z
cs
n
,n
))) continue,
otherwise goto 2
8: z
n
2
= z
n
2
−ct
n
0
9: Send out (z
n
,r
n
) and receive (z
i
,r
i
);i ∈[n −1]
10: for i ∈ [n −1] do
11: w
i
:=
¯
Az
i
−ct
i
1
·2
d
12: if ||z
i
||
2
> B or Open
ck
(com
i
,r
i
,w
i
) ̸= 1 then
abort
13: z :=
∑
i∈[n]
z
i
;r :=
∑
i∈[n]
r
i
14: return Σ = (c, z,r)
2.4 Verification Phase
Algorithm 3: Verify(pk,Σ,µ ∈M).
1: ck
′
:= H
3
(µ, pk)
2: w
′
:=
¯
Az −ct
1
·2
d
3: c
′
:= H
0
(Commit
ck
′
(w
′
,r),µ, CRH(pk))
4: if ||z||
2
≤
√
nB and c = c
′
then return 1
5: else return 0
The verification phase is similar to the standard
Dilithium-G scheme. In the original DS2 design,
commitments must be opened with the reconstructed
vector w and verified. As we used the Fiat-Shamir
trick and the commitments are not part of the signa-
ture, the commitments are computed from the recon-
structed vector w, then a new challenge is computed
using the hash function and is compared with the chal-
lenge that is a part of the signature. The changes are
highlighted in Algorithm 3. This phase is indepen-
dent of the number of parties and anyone with access
to the common public key can verify the signature.
The correctness of our proposal is proven in the fol-
lowing theorem.
Lattice-Based Threshold Signature Implementation for Constrained Devices
727

2 5 10 20 50
10
0
10
1
0.25
0.28
0.34
0.45
0.87
7.15
7.84
10.52
14.86
31.41
Number of parties
Execution time [ms]
Macbook Air
(Parameters from Section 2.1)
Key generation
Signing
2 5 10 20 50
10
1
10
2
10
3
19
22
26
34
59
756
743
912
1,038
1,714
Number of parties
Execution time [ms]
ESP32
(Dilithium-G weak parameters, l = w = 4)
2 5 10 20 50
10
2
10
3
26
38
53
82
145
501
595
870
1,410
3,109
Number of parties
Execution time [ms]
ARM Cortex-A53
(Parameters from Section 2.1)
2 5 10 20 50
10
2
10
3
99
109
130
167
275
2,269
2,342
2,468
2,544
2,836
Number of parties
Execution time [ms]
ARM Cortex-M3
(Dilithium-G weak parameters, l = w = 2)
Figure 1: Execution times during key generation and signing phases.
Theorem 1 (Correctness). The Verification process in
Algorithm 3 is correct.
Proof. For the signature to be accepted, we
need to show that the newly computed c
′
is
equal to c, that is H
0
(com,µ,tr) is equal to
H
0
(Commit
ck
(w
′
,r),µ, CRH(pk)). This can be done by
proving that com is equal to Commit
ck
(w
′
,r). In fact,
by definition, tr := CRH(ρ||t
1
), where pk is a public
value and, likewise, ck
′
:= H
3
(µ, pk) is equal to ck.
Therefore, the commitments equality can be proven
as follows:
Commit
ck
(w
′
,r) = Commit
ck
(
¯
Az −ct
1
·2
d
,r)
= Commit
ck
(
∑
i∈[n]
¯
Az
i
−ct
i1
·2
d
,
∑
i∈[n]
r
i
)
=
∑
i∈[n]
Commit
ck
(z
i
−ct
i1
·2
d
,r
i
)
=
∑
i∈[n]
Com
i
= Com
Note that it is straightforward that ||z||
2
≤
√
nB
since the signers only output a signature shares that
respect ||z
i
||
2
≤B. We refer to (Damg
˚
ard et al., 2022),
Lemma 2 for more details.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
728

2 5 10 20 50
10
2
10
4
10
6
10
8
1,472
5,888
13,248
27,968
72,128
2.39 ·10
5
9.46 ·10
5
2.13 ·10
6
4.49 ·10
6
1.15 ·10
7
Number of parties
Data transferred [B]
Key Generation
Signing
Figure 2: Number of data transferred (from/to one device)
needed during key generation and signing phases.
1.25 1.5 2 3
1.95
2
1.94
1.95
1.98
2.03
Number of rejections
Data transferred [MB]
Data transferred
8
9
10
7.83
8.15
8.9
10.52
Execution time [ms]
Execution time
Figure 3: Number of data transferred needed and execution
times during signing with 10 parties.
3 EXPERIMENTAL RESULTS
In this section, we present the experimental results
of our implementation. We used devices with dif-
ferent computing power such as Macbook Air 2020
(CPU Apple M1, 3.2 GHz) representing a personal
computer, and constrained devices based on ARM
Cortex-A53 (represented by Raspberry Pi Zero),
ARM Cortex-M3 (represented by Arduino Due), and
ESP32 processors. We benchmark the scheme de-
pending on the number of signers and the number of
rejections. Due to the high memory requirements of
the DS2 scheme, we had to use smaller parameters
during the benchmarking on ARM Cortex-M3 and
ESP32. This involved using Dilithium-G weak pa-
rameters and setting the lattice commitment l = w = 2
for ARM Cortex-M3 and l = w = 4 for ESP32.
3.1 Communication Complexity and
Performance Results
For execution times, only computation time was mea-
sured, not including the time needed for communica-
tion. The results are presented in Figure 1. The aver-
age times for 1000 runs are used for the signature gen-
eration phase. The execution time of verification does
not depend on the number of parties or the number of
rejections, so it is the same for all measurements and
it was 1.87 ms on Macbook, 102.55 ms on ESP32,
179.26 ms on ARM Cortex-A53, and 342.50 ms on
ARM Cortex-M3. In Figure 2, the data transferred
from/to one device in bytes during the key genera-
tion and signing phases are presented for the different
number of parties. In Figure 3, the execution times
and data transferred are presented for different num-
ber of rejections. The measurements are presented for
the constant number of parties n = 10 on Macbook.
4 CONCLUSION
In this work, we propose optimization techniques and
parameter selection for the DS2 scheme. To our best
knowledge, we provide the first implementation of
this scheme which is easily portable and executable
on different platforms and constrained devices capa-
ble of running C applications. Further, we provide
benchmarks of our DS2 implementation on various
devices. The experimental results show the efficiency
of our optimized implementation even on constrained
devices, where the signing phase (without a commu-
nication overhead) takes less than 2 s on ESP32 and
less than 3 s on ARM Cortex-M3. Our future work
will focus on further optimization of algorithms, e.g.,
the use hint algorithm.
ACKNOWLEDGEMENTS
This work is supported by Ministry of the Inte-
rior (CZ) under grant VJ01010008 and by the Euro-
pean Union under Grant Agreement No. 101087529
CHESS. Views and opinions expressed are however
those of the author(s) only and do not necessarily
reflect those of the European Union or European
Research Executive Agency. Neither the European
Union nor the granting authority can be held respon-
sible for them.
Lattice-Based Threshold Signature Implementation for Constrained Devices
729

REFERENCES
Benhamouda, F., Krenn, S., Lyubashevsky, V., and Pietrzak,
K. (2016). Efficient zero-knowledge proofs for com-
mitments from learning with errors over rings. In
Computer Security–ESORICS 2015: 20th European
Symposium on Research in Computer Security, Vi-
enna, Austria, September 21-25, 2015, Proceedings,
Part I, pages 305–325. Springer.
Bernstein, D. J. (2009). Introduction to post-quantum cryp-
tography. In Post-quantum cryptography, pages 1–14.
Springer.
Boneh, D., Gennaro, R., Goldfeder, S., Jain, A., Kim, S.,
Rasmussen, P. M., and Sahai, A. (2018). Thresh-
old cryptosystems from threshold fully homomorphic
encryption. In Advances in Cryptology–CRYPTO
2018: 38th Annual International Cryptology Confer-
ence, Santa Barbara, CA, USA, August 19–23, 2018,
Proceedings, Part I 38, pages 565–596. Springer.
Boschini, C., Takahashi, A., and Tibouchi, M. (2022).
Musig-l: Lattice-based multi-signature with single-
round online phase. In Advances in Cryptology–
CRYPTO 2022: 42nd Annual International Cryptol-
ogy Conference, CRYPTO 2022, Santa Barbara, CA,
USA, August 15–18, 2022, Proceedings, Part II, pages
276–305. Springer.
Brandao, L. and Peralta, R. (2023). Nist first call for multi-
party threshold schemes.
Castagnos, G., Catalano, D., Laguillaumie, F., Savasta, F.,
and Tucker, I. (2020). Bandwidth-efficient threshold
ec-dsa. In IACR International Conference on Public-
Key Cryptography, pages 266–296. Springer.
Chen, Y. (2023). Dualms: Efficient lattice-based two-round
multi-signature with trapdoor-free simulation. Cryp-
tology ePrint Archive.
Cogliati, B., Dodis, Y., Katz, J., Lee, J., Steinberger, J.,
Thiruvengadam, A., and Zhang, Z. (2018). Prov-
able security of (tweakable) block ciphers based on
substitution-permutation networks. In Annual In-
ternational Cryptology Conference, pages 722–753.
Springer.
Damg
˚
ard, I., Jakobsen, T. P., Nielsen, J. B., Pagter, J. I., and
Østerg
˚
ard, M. B. (2020). Fast threshold ecdsa with
honest majority. In International Conference on Secu-
rity and Cryptography for Networks, pages 382–400.
Springer.
Damg
˚
ard, I. and Koprowski, M. (2001). Practical thresh-
old rsa signatures without a trusted dealer. In Interna-
tional Conference on the Theory and Applications of
Cryptographic Techniques, pages 152–165. Springer.
Damg
˚
ard, I., Orlandi, C., Takahashi, A., and Tibouchi, M.
(2022). Two-round n-out-of-n and multi-signatures
and trapdoor commitment from lattices. Journal of
Crypatology, 35(2):1–56.
Ducas, L., Lepoint, T., Lyubashevsky, V., Schwabe, P.,
Seiler, G., and Stehl
´
e, D. (2018). Crystals–dilithium:
Digital signatures from module lattices.
Freemanlaw (2022). Cryptocurrency transactions: Multi-
signature arrangements explained.
Fukumitsu, M. and Hasegawa, S. (2020). A lattice-based
provably secure multisignature scheme in quantum
random oracle model. In Provable and Practical Se-
curity: 14th International Conference, ProvSec 2020,
Singapore, November 29–December 1, 2020, Pro-
ceedings 14, pages 45–64. Springer.
Gennaro, R. and Goldfeder, S. (2018). Fast multiparty
threshold ecdsa with fast trustless setup. In Proceed-
ings of the 2018 ACM SIGSAC Conference on Com-
puter and Communications Security, pages 1179–
1194.
Kiltz, E., Lyubashevsky, V., and Schaffner, C. (2018).
A concrete treatment of fiat-shamir signatures in
the quantum random-oracle model. In Advances in
Cryptology–EUROCRYPT 2018: 37th Annual Inter-
national Conference on the Theory and Applications
of Cryptographic Techniques, Tel Aviv, Israel, April
29-May 3, 2018 Proceedings, Part III 37, pages 552–
586. Springer.
Komlo, C. and Goldberg, I. (2020). Frost: flexible round-
optimized schnorr threshold signatures. In Interna-
tional Conference on Selected Areas in Cryptography,
pages 34–65. Springer.
Laud, P., Snetkov, N., and Vakarjuk, J. (2022). Dilizium
2.0: Revisiting two-party crystals-dilithium. Cryptol-
ogy ePrint Archive.
Lindell, Y. and Nof, A. (2018). Fast secure multiparty ecdsa
with practical distributed key generation and applica-
tions to cryptocurrency custody. In Proceedings of
the 2018 ACM SIGSAC Conference on Computer and
Communications Security, pages 1837–1854.
Liu, J., Wen, J., Zhang, B., Dong, S., Tang, B., and Yu, Y.
(2022). A post quantum secure multi-party collabora-
tive signature with deterability in the industrial inter-
net of things. Future Generation Computer Systems.
Ricci, S., Dzurenda, P., Casanova-Marqu
´
es, R., and
Cika, P. (2022). Threshold signature for privacy-
preserving blockchain. In Business Process Man-
agement: Blockchain, Robotic Process Automation,
and Central and Eastern Europe Forum: BPM 2022
Blockchain, Germany, September 11–16, 2022, Pro-
ceedings, pages 100–115. Springer.
Shoup, V. (2000). Practical threshold signatures. In Interna-
tional Conference on the Theory and Applications of
Cryptographic Techniques, pages 207–220. Springer.
Vakarjuk, J., Snetkov, N., and Willemson, J. (2021). Diliz-
ium: A two-party lattice-based signature scheme. En-
tropy, 23(8):989.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
730
