
A Two-Party Hierarchical Deterministic Wallets in Practice
ChihYun Chuang
1
, IHung Hsu
1
and TingFang Lee
2
1
AMIS, Taipei, Taiwan
2
Department of Population Health, NYU Grossman School of Medicine, New York, U.S.A.
Keywords:
Secure Two-Party Computation, Cryptocurrencies, Key Derivation, Key Generation, Wallets.
Abstract:
The applications of Hierarchical Deterministic Wallet are rapidly growing in various areas such as cryptocur-
rency exchanges and hardware wallets. Improving privacy and security is more important than ever. In this
study, we proposed a protocol that fully support a two-party computation of BIP32. Our protocol, similar to
the distributed key generation, can generate each party’s secret share, the common chain-code, and the public
key without revealing a seed and any descendant private keys. We also provided a simulation-based proof of
our protocol assuming a rushing, static, and malicious adversary in the hybrid model. Our master key genera-
tion protocol produces up to total of two bit leakages from a honest party given the feature that the seeds will
be re-selected after each execution. The proposed hardened child key derivation protocol leads up to a one bit
leakage in the worst situation of simulation from a honest party and will be accumulated with each execution.
Fortunately, in reality, this issue can be largely mitigated by adding some validation criteria of boolean circuits
and masking the input shares before each execution. We then implemented the proposed protocol and ran in
a single thread on a laptop which turned out with practically acceptable execution time. Lastly, the outputs of
our protocol can be easily integrated with many threshold sign protocols.
1 INTRODUCTION
Blockchains are well-known for their role in cryp-
tocurrency systems, where they provide a secure and
decentralized record of transactions without requir-
ing a trusted third party. Digital signatures are used
to authorize and validate transactions in which users
must protect their private keys. If a private key is
lost, the user loses all assets that are associated with
it. This makes key management crucial. However,
managing multiple private keys is challenging with
the growing demand of blockchains. Hierarchical
Deterministic (abbrev. HD) Wallet (Wuille, 2013)
and t − n threshold signature scheme (abbrev. TSS)
are current two methods of managing private keys in
blockchains. HD wallet offers convenience, and TSS
provides greater security than a single party scheme.
The goal of this paper is to employ the advantages of
these methods, as previously commented in (Gennaro
and Goldfeder, 2018, Section 6.4).
HD wallets were introduced in the blockchain
world to simplify private key management. With
HD wallets, users utilize deterministic algorithms de-
scribed in BIP32 (Wuille, 2013), a Bitcoin Improve-
ment Proposal, to generate multiple private keys. Ide-
ally, they generate a set of random words called
"seed" S, and then use HMAC-SHA512("Bitcoin
seed", S) to derive the master private key k. Next,
users derive the new private key, which is k +
HMAC-SHA512(chaincode,k, keyID). By iterating
this process, BIP32 provides a tree structure of private
keys generating paths. BIP32 allows users to securely
manage and generate a large number of addresses by
securing only one random seed.
There are some potential security issues of HD
wallets. First, a compromised private key can lead to
the loss of all descendant private keys, which becomes
a risk with improper ECDSA implementations. For
instance, (Breitner and Heninger, 2019) used lattice
attacks against ECDSA signatures to demonstrate that
repeated or non-uniform generation of the nonce can
potentially enable an attacker to compute the long-
term signing key. Second, if given a parent public key
and any non-hardened child private keys, it is possi-
ble to easily recover the parent private key. To address
this issue, (Gutoski and Stebila, 2015) proposed a new
HD wallet (i.e. different from the formula defined by
BIP32) that can tolerate the leakage of up to m private
keys, with a parent public key size of O(m).
TSS enables t out of n parties to generate sig-
850
Chuang, C., Hsu, I. and Lee, T.
A Two-Party Hierarchical Deterministic Wallets in Practice.
DOI: 10.5220/0012138700003555
In Proceedings of the 20th International Conference on Security and Cryptography (SECRYPT 2023), pages 850-856
ISBN: 978-989-758-666-8; ISSN: 2184-7711
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)

natures on behalf of a group. In most TSS imple-
mentations, each party holds the same public key and
their own secret, also known as a "share". The pri-
vate key can only be compromised when all t shares
are stolen simultaneously. However, TSS also fea-
tures "proactive refresh" (Ostrovsky and Yung, 1991),
which voids shares produced from an old epoch.
TSS is secure, robust, and flexible key management
schemes that allow for signature generation without
needing for private keys (Luis et al., 2019). In prac-
tice, users often use multiple addresses to manage
their assets, causing management burden for service
providers who must manage numerous shares for dif-
ferent addresses. Another popular solution is multi-
signature, in which a valid transaction requires mul-
tiple keys instead of a single signature from one key.
Multi-signature also avoids the risk of a single point
of failure and is easier to implement than TSS. How-
ever, the main drawback of multi-signature is its sig-
nificantly higher cost in blockchains.
Current TSS protocols cannot fully support
BIP32’s key generation protocols. To address this, we
employ garbled circuit protocols (Yao, 1986) that al-
low parties to compute a predetermined function us-
ing their inputs while revealing only the output. Vari-
ous garbled circuits have been proposed to ensure se-
curity against malicious adversaries. For efficiency,
we employ the DualEx protocol (Huang et al., 2012),
an enhanced semi-honest protocol with dual execu-
tion against malicious adversaries. It involves con-
ducting two separate runs of a garbled-circuit proto-
col against a semi-honest adversary with the parties
swapping roles, followed by a secure equality test that
leaks no more than one bit against a malicious adver-
sary. The challenge of this paper is to design a “TSS-
type BIP32 protocol”.
(Das et al., 2023) proposed a new and effective
derivation mechanism for BIP32’s type wallet achiev-
ing the threshold setting easily. However, their con-
structions are not fully supporting the specification
of hardened key derivation described in the original
BIP32. Unbound Security
1
, a pioneer in multi-party
computation technology, has developed a two-party
HD wallet protocol that utilizes the garbled circuit
scheme. Unbound’s idea of the master key generation
protocol and child key derivations is to produce the re-
sults through DualEx that conform to BIP32 standard.
To prevent attackers from using incorrect inputs, they
added some randomized information such that shares
of a key are outputs. Eventually, both parties receive
the correct public key and validate their own shares.
In our study, we also apply the DualEx proto-
1
https://github.com/unboundsecurity/blockchain
-crypto-mpc
col (Huang et al., 2012) to BIP32. Our protocol
uses two layers of twist masking r
i
and n
i
of i-th
party to prevent cheating, with the DualEx output
s
′
:= secret + r
i
∗ n
1−i
+ r
1−i
∗ n
i
. Each party then an-
nounces r
i
· G and n
i
sequentially to ensure the cor-
rectness of s
′
. Our protocol’s efficiencies for child
key derivation are comparable to Unbound’s, while
Unbound’s master key generation is more efficient.
However, it is unclear what security model Unbound
considered, whereas our protocols were proven to be
secure in the hybrid-world.
As far as we know, there have been no formal pa-
pers that study two-party BIP32. Our contributions in
this work are as follows: 1) We present a protocol that
employs two-party computation, including generating
a master private key, hardened private keys, and non-
hardened private keys, that complies with all BIP32
regulations (Figures 1 and 2); 2) We provide a secu-
rity proof for our protocol in the hybrid model using
simulation-based methods. We utilize the concepts of
real/ideal worlds, as described in (Huang et al., 2012),
to demonstrate that the outputs of the two worlds are
indistinguishable. Our master key generation proto-
col allows attackers to use up to two arbitrary boolean
circuit functions, costing up to a two-bit leakage from
the honest party in the ideal world. However, this is
not a significant security concern because the seeds
are re-selected after each execution, preventing the
leakage from accumulating. In contrast, our hard-
ened child key derivation protocol permits attackers
to use only one arbitrary circuit function, resulting in
up to a one-bit leakage from the honest party that ac-
cumulates with each execution. Nevertheless, this is-
sue can be mitigated considerably by adding some cir-
cuit function validation criteria and masking the input
shares before each execution. The leakage of bits in
the ideal world is the worst-case scenario, and can be
prevented in the real world, as discussed in (Huang
et al., 2012); 3) We implement the proposed proto-
col running in a single thread on a laptop, without the
need of downloading boolean circuits, as each exe-
cution uses the same boolean circuits. The average
time spent for the master key generation is 7.37s, and
for the hardened child key derivation it is 2.74s. The
efficiency can be achieved if network bandwidth al-
lows. However, the number of executions required
to generate keys or shares for individual users is usu-
ally less than number of signings. The master key
generation and the translation of the child key only
need to be performed once in most cases. There-
fore, a slightly longer execution time is acceptable
and practical. More importantly, the outputs of our
protocol can be easily integrated with many sign pro-
tocols (Canetti et al., 2020a; Castagnos et al., 2020;
A Two-Party Hierarchical Deterministic Wallets in Practice
851
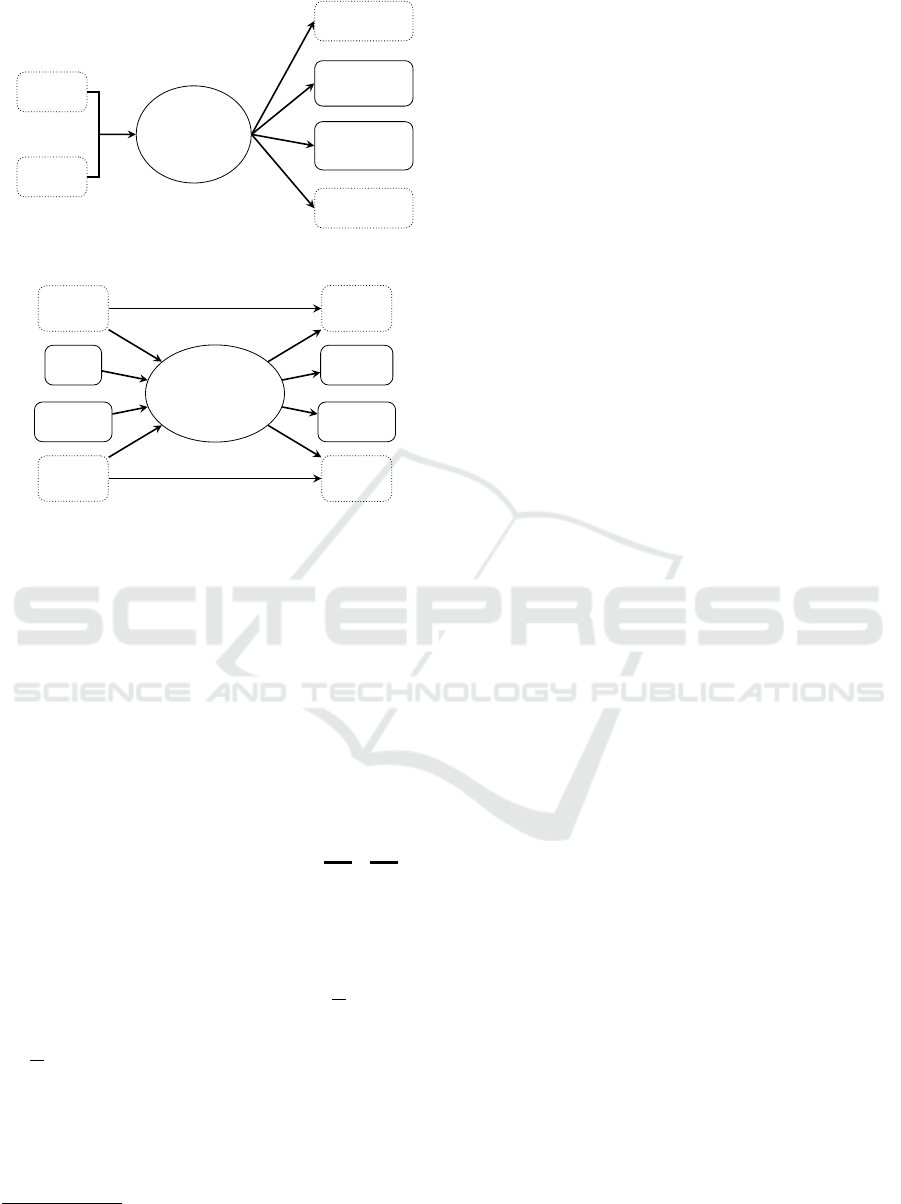
Seed 1
Seed 2
2-party
HMAC-
Machine
Share 1
Master
chain-code
Master
public key
Share 2
Figure 1: BIP32: 2-Party Master Key Generation.
Parent
share 1
Index
Chain-code
Parent
share 2
2-party
HMAC-
Machine
Child
share 1
Public key
Chain-code
Child
share 2
Figure 2: BIP32: 2-Party Child Key Derivation.
Doerner et al., 2018; Gennaro and Goldfeder, 2018;
Gennaro and Goldfeder, 2020; Lindell, 2021; Pettit,
2021; Xue et al., 2021) to generate signatures.
2 PRELIMINARIES
Notation. The sets of natural numbers, integers are
denoted by N, Z respectively. Given a prime integer
p ∈ N, we define Z
p
to be the quotient field of Z/pZ,
and Z
×
p
to be the multiplicative group of Z
p
. Let E
be an elliptic curve over Z
p
, and G be a point of order
q on the curve E. The point b · G :=
b−times
z }| {
G + · ·· +G is
the scalar multiplication of E by a non-negative inte-
ger b. In the rest of this paper, we will use the com-
monly used elliptic curve defined by secp256k1
2
in
which q is a prime. Given m, n ∈ N, we let ser
m
(n)
serialize a m-bit unsigned integer n as a
l
m
8
m
-byte se-
quence, most significant byte first, parse
m
(n) interpret
a
l
m
8
m
-byte sequence n as a m-bit number, most sig-
nificant byte first, and ser
P
(Q) serialize the coordinate
pair Q = (x, y) as a byte sequence using SEC1’s com-
pressed form. Denote H to be a hash function and
HMAC-SHA512 to be the function specified in RFC
4231(M., 2005). Lastly, the notation ⊕ is the XOR
2
https://csrc.nist.gov/publications/detail/sp/800-57-
part-1/rev-5/final
operation and ∥ is the concatenation.
2.1 Circuit Garbling
A boolean circuit f can be parameterized by
(n,m,ℓ,Gates) with a chosen topological order, where
n is the number of input, m the number of output, ℓ the
number of all wires, and Gates the set of all gates. Cir-
cuit garbling (Yao, 1986) allows that two semi-honest
parties use their own secrets to evaluate a prior agreed
boolean circuit function without leaking any informa-
tion from their inputs beyond what is revealed by the
function output itself. A standard definition of gar-
bling scheme is proposed by (Bellare et al., 2012) as
follows:
Definition 1. A garbling scheme consists of four al-
gorithms (Zahur et al., 2015, Section 2):
GB: On input 1
k
and a boolean circuit f , outputs
(F,e,d). Here F is a garbled circuit, e is encoding
information, and d is decoding information.
En: On input (e,x), where e is as above and x is an
input suitable for f , outputs a garbled input X .
Ev: On input (F,X ) stated as above, outputs a gar-
bled output Y .
De: On input (d,Y ) stated as above, outputs a plain
output y.
The algorithms have the following conditions:
Correctness: For any circuit f and input x, and sam-
pling (F,e,d) ← GB(1
k
, f ), we have
De
d, Ev
F,En(e,x)
= f (x).
Privacy: There exists a simulator S that takes in-
put (1
k
, f , f (x)) and whose output is indistinguishable
from (F, X,d) generated the usual way.
Obliviousness: There must exist a simulator S that
takes input (1
k
, f ) and whose output is indistinguish-
able from (F, X) generated the usual way.
Authenticity: Given input (F,X ) alone, no adversary
should be able to produce
˜
Y ̸= Ev(F,X) such that
De(d,
˜
Y ) ̸=⊥, except with negligible probability.
2.2 Oblivious Transfer
Oblivious transfer (abbrev. OT) is a fundamental
cryptographic primitive in the multi-party computa-
tion. To be more specific, 1-n OT protocol has two
characters called sender and receiver such that the re-
ceiver asks for one of the sender’s n messages, which
satisfies two conditions: the receiver does not know
the other messages except for the selected message,
and the sender does not know the receiver’s choice.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
852

So far, OT has become the most widely used build-
ing block in the two-party setting, such as garbling
scheme.
3 OUR SCHEMES
We describe the one proposed protocol, 2-party mas-
ter key generation(abbrev. 2P-MKG). Another proto-
col harden key derivation appears in the extended ver-
sion. The 2P-MKG allows that while both parties do
not know each other’s seed s
i
, they can receive their
own secret share x
mas,i
, the chain-code I
R
, and the cor-
responding public key Q such that
• HMAC-SHA512("Bitcoin seed", s
0
⊕s
1
) = I
L
∥I
R
,
• x
mas,0
+ x
mas,1
= parse
256
(I
L
) mod q,
• parse
256
(I
L
) ∈ (0, q), and Q = (x
mas,0
+ x
mas,1
)·G.
3.1 A Protocol of Two-Party Master
Key Generation
Let k and k
′
be positive integers and Z
×
q,k
be the
subset of the finite field Z
×
q
with the bit-length of all
elements at most k. Consider the following boolean
circuits with security parameters k < 255 and k
′
.
f
mkg
: {0,1}
k
′
× Z
×
q
× Z
×
q,k
× {0, 1}
k
′
× Z
×
q
× Z
×
q,k
→ {0, 1}
513+k
s
0
,r
0
,n
0
,s
1
,r
1
,n
1
7→ ser
256
(parse
256
(I
L
) + r
0
n
1
+r
1
n
0
mod q)∥I
R
∥ser
256
(n
0
+ n
1
) (1)
and f
aux
: {0,1}
k
′
× Z
×
q
× {0, 1}
k
′
× Z
×
q,k
→ {0, 1}
257
s
0
,r
0
,s
1
,n
1
7→ 1
[0,q)
(parse
256
(I
L
))∥
ser
256
(parse
256
(I
L
) + r
0
n
1
mod q). (2)
Here 1
[0,q)
(x) is the indicator function of the interval
[0,q). Since k and k
′
are fixed in the beginning, we
omit the notation k and k
′
in functions f
mkg
and f
aux
for simplicity. Before introducing our protocol and
theorem, we explain our idea briefly.
Idea. 2P-MKG makes sure that the summation of
obtained secret shares, x
mas,0
and x
mas,1
, is equal to
the master private key s := parse
256
(I
L
) in which
the public key is s · G, under the circumstance that
neither of them know the master private key and
each other’s private share. Both parties can access
f
aux
(s
0
,r
0
,s
1
,n
1
) through a garbled circuit to reach an
agreement of the public key. During this process, a
malicious adversary might attempt to input n
1
= 0 in
(2) for getting the private key. This issue is resolved
by directly sending one non-zero input-wire label of
n
1
(ref. step 1 in Protocol 1). Next, both parties use
DualEx protocol to verify their outputs of the garbled
circuit f
mkg
are the same. At this stage, it is very hard
for malicious adversaries pass a series of the checking
lists through non-consistent inputs without knowing
the another party’s s
i
,r
i
, and n
i
. These processes can
ensure the consistency of garbled circuit inputs and
the correctness of the secret shares.
Let f = (n,m, ℓ,Gates) be a boolean circuit. A
participant P
i
applies the algorithm GB(1
k
, f ) to out-
put (F
i
,e
i
,d
i
) (resp. GB(1
k
, f
∗
) to (F
∗,i
,e
∗,i
,d
∗,i
)),
where i ∈ {0, 1}. We denote the input-wire matrix
X
F
i
=
X
0
F
i
[0] X
0
F
i
[1] . .. X
0
F
i
[n − 1]
X
1
F
i
[0] X
1
F
i
[1] . .. X
1
F
i
[n − 1]
.
Here X
b
F
i
[k] is the k-th input-wire label represent-
ing the bit value b. If v ∈ {0,1}
n
is a bit-string
(i.e. v = v
0
∥v
1
∥. .. ∥v
n−1
), then we set X
v
F
i
:=
(X
v
1
F
i
[0],...,X
v
n−1
F
i
[n−1]) which also writes this vector
to be X
v
F
i
. Moreover, if v
′
is a sub-string of v, which
means v
′
= v
t
∥v
t+1
∥. .. ∥v
t+k−1
with k the bit-Length
of v
′
, then we set X
v
′
F
i
:= (X
v
t
F
i
[t],... ,X
v
t+k−1
F
i
[t + k −
1]) = X
v
′
F
i
. Set X
F
i
(0) (resp. X
F
i
(1) ) to be the partic-
ipant P
0
′
s (resp. P
1
′
s) input-wire matrix. Given two
d
1
× d
2
matrices A = [a
i j
], B = [b
i j
], we define
A∥B =
a
11
.. . a
1d
2
b
11
.. . b
1d
2
a
21
.. . a
2d
2
b
21
.. . b
2d
2
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
a
d
1
1
.. . a
d
1
d
2
b
d
1
1
.. . b
d
1
d
2
d
1
×2d
2
.
Therefore, given an input x = x
0
∥x
1
with x
j
being P
i
′
s
input, one has
En(e
i
,x) = X
x
F
i
= X
x
0
F
i
∥X
x
1
F
i
= X
x
0
F
i
(0)∥X
x
1
F
i
(1).
For the output-wire matrix
Y
F
i
:=
Y
0
F
i
[0] Y
0
F
i
[1] . .. Y
0
F
i
[m − 1]
Y
1
F
i
[0] Y
1
F
i
[1] . .. Y
1
F
i
[m − 1]
,
we define the hash matrix of Y
F
i
,
HY
F
i
:=
H
Y
0
F
i
[0]
H
Y
0
F
i
[1]
... H
Y
0
F
i
[m − 1]
H
Y
1
F
i
[0]
H
Y
1
F
i
[1]
... H
Y
1
F
i
[m − 1]
.
– The input of P
0
: x
0
.
– The input of P
1
: x
1
.
– The output of P
0
and P
1
: if x
0
equals x
1
, re-
turn 1; otherwise, return 0.
Figure 3: The ideal functionality f
VT
for Validation Test.
We consider Protocol 1 runs in a hybrid world
where the parties are given access to the trusted party
A Two-Party Hierarchical Deterministic Wallets in Practice
853

Protocol 1: π
MKG
: 2-party master key generation 1.
Input: two security parameters k, k
′
and a seed
s
i
∈ {0, 1}
k
′
.
output: a share x
mas,i
, the corresponding public
key Q, and the chain code.
1: Each participant P
i
:
• randomly chooses r
i
∈ Z
×
q
and an odd integer n
i
∈
[1,2
k
).
• performs GB in Definition 1 with f
mkg
and
f
aux
to obtain (F
mkg,i
,e
mkg,i
,d
mkg,i
), and
(F
aux,i
,e
aux,i
,d
aux,i
).
• computes X
s
i
∥ser
256
(r
i
)∥ser
k
(n
i
)
F
mkg,i
=
En
e
mkg,i
,s
i
∥ser
256
(r
i
)∥ser
k
(n
i
)
, X
s
i
∥ser
256
(r
i
)
F
aux,i
=
En
e
aux,i
,(s
i
∥ser
256
(r
i
))
.
• performs the OT protocol with P
1−i
to ob-
tain garbled input-wire labels X
s
i
∥ser
256
(r
i
)∥ser
k
(n
i
)
F
mkg,1−i
(resp. X
s
i
∥ser
k
(n
i
)
F
aux,1−i
) except for X
1
F
mkg,1−i
[ ˙n
mkg,i
]
(resp. X
1
F
aux,1−i
[ ˙n
aux,i
]), where ˙n
mkg,i
(resp. ˙n
aux,i
)
is the index of all input-wire labels correspond-
ing to the least significant bit of n
i
. Sends
X
1
F
mkg,i
[ ˙n
mkg,1−i
], X
1
F
aux,i
[ ˙n
aux,1−i
], and the first
message of OT.
2: Each participant P
i
:
• After OT completed, sends the garbled message
(F
aux,i
,X
s
i
∥ser
256
(r
i
)
F
aux,i
,d
aux,i
), and the point r
i
· G to
the participant P
1−i
.
3: Each participant P
i
:
• interprets the coming point to be R
1−i
.
• uses Ev to get Y
F
aux,1−i
and then applies De to ob-
tain the binary string v
aux,i
, interpret v
aux,i
to be
the result of the indicator function 1
[0,q)
(I
L
) and
w
aux,i
.
• denotes Q := w
aux,i
· G − n
i
· R
1−i
which is the
shared public key. If Q = 0 · G, then sets Q be
an arbitrary point of the elliptic curve E.
• if the indicator function 1
[0,q)
(I
L
) = 0, then as-
sign (F
mkg,i
,X
s
i
∥ser
256
(r
i
)∥ser
k
(n
i
)
F
mkg,i
,HY
F
mkg,i
) to be an
arbitrary chosen message with the valid length.
• performs the validation test in (Huang et al.,
2012, Figure 5) with P
1−i
to compare the shared
public key Q.
4: Each participant P
i
:
• sends (F
mkg,i
,X
s
i
∥ser
256
(r
i
)∥ser
k
(n
i
)
F
mkg,i
,HY
F
mkg,i
) to the
participants P
1−i
.
Protocol 1: π
MKG
: 2-party master key generation 2.
5: Each participant P
i
:
• uses Ev to get Y
F
mkg,1−i
and the incoming hash ta-
ble HY
F
mkg,1−i
to obtain the binary string v
mkg,i
.
Interpret v
mkg,i
to be w
mkg,i
, chain-code, and n.
• verifies w
mkg,i
= v
aux,i
+ (n − n
i
) · r
i
mod q.
• computes x
mas,i
:=
w
mkg,i
2
− (n − n
i
) · r
i
mod q
• uses HW
f
0
,1−i
to learn the bit-string v
i
.
• computes
h
mkg,i
:=
H
Y
v
mkg,i
F
mkg,i
∥Y
F
mkg,1−i
, if i = 0,
H
Y
F
mkg,1−i
∥Y
v
mkg,i
F
mkg,i
, if i = 1.
• performs the validation test with P
1−i
to compare
h
mkg,i
, and h
mkg,1−i
. If they are equal, then the
protocol is complete. Otherwise, abort.
computing two functionalities: oblivious transfer f
OT
(Chuang et al., 2023, Figure 5) and validation testing
f
VT
(ref. Figure 3). Then one has the following theo-
rem:
Theorem 1. Assume that a garbling scheme satis-
fies correctness, privacy, and obliviousness, a hash
function H is modeled as an random oracle, and the
discrete logarithm problem is hard, then π
MKG
is se-
curely computed f
π
MKG
with 2-bit leakage in the hy-
brid world described above. Here for input s
0
,s
1
∈
{0,1}
k
′
, the function f
π
MKG
= ( f
0
, f
1
) with
f
i
(s
0
,s
1
) :=
parse
256
I
L
+ (−1)
i
· r
2
mod q,
I
R
,parse
256
I
L
· G
∈ Z
q
× {0,1}
256
× E,
for r uniformly random in Z
q
and
HMAC-SHA512(“Bitcoin seed”, s
0
⊕ s
1
) = I
L
∥I
R
.
The correctness and the security proof of our the-
orem can be found in (Chuang et al., 2023).
4 IMPLEMENTATION,
BENCHMARKS, AND
EVALUATION
The garbled scheme were generated using Two
Halves Make a Whole (Zahur et al., 2015) to en-
hance the efficacy. We employ OT that proposed by
(Canetti et al., 2020b) and optimize the security ac-
cording to the suggestions in (McQuoid et al., 2021,
Section 3.3). In the validation protocol, we let both
parties use one-side validation protocol in (Huang
SECRYPT 2023 - 20th International Conference on Security and Cryptography
854

et al., 2012, Figure 5) to verify that both outputs
from garbled circuit are the same. All benchmarks
without downloading boolean circuits were ran in a
single-threaded on an Intel i5 CPU 2.3GHz and 16GB
2133MHz LPDDR3 of RAM in the 13-inch (2018)
macbook pro.
Table 1: Basic information of circuits: f
mkg
, f
aux
, and f
ckd
.
f
mkg
f
aux
f
ckd
Total number of gates 847,420 796,827 507,581
Total number of wires 850,558 799,676 510,463
Table 2: Time consuming for running 20 samples.
2P-MKG 2P-CKD
Fast time 7.181s 2.688s
Slow time 7.748s 2.839s
Avg time 7.374s ± 0.14s 2.739s ± 0.04s
The bit-length of seed = 512, n = 33, and Paillier public key = 2048;
The number of base OT = 128; The half-gates scheme uses the
Hash function
[
MMO
E
(ref. (Guo et al., 2020, Section 7.3))
with the ideal cipher AES-128.
5 CONCLUSION AND
DISCUSSION
The proposed protocols comply with all BIP32 regu-
lations. We also provided a security proof in the hy-
brid model using simulation-based methods and ex-
perimental data. Theoretically, there will be risk in
leaking bits while using DualEx protocol since we
considered the worst scenario without any restric-
tions on g in the security proof. The leaking risk
can be potentially overcame by utilizing garbled cir-
cuit schemes against malicious adversaries such as
authenticated Garbling method.
REFERENCES
Bellare, M., Hoang, T., and Rogaway, P. (2012). Founda-
tions of garbled circuits. In Proceedings of the 2012
ACM Conference on Computer and Communications
Security, CCS ’12, pages 784–796. Association for
Computing Machinery.
Breitner, J. and Heninger, N. (2019). Biased Nonce Sense:
Lattice Attacks Against Weak ECDSA Signatures in
Cryptocurrencies, pages 3–20. Springer-Verlag.
Canetti, R., Gennaro, R., Goldfeder, S., Makriyannis, N.,
and Peled, U. (2020a). Uc non-interactive, proactive,
threshold ecdsa with identifiable aborts. In Proceed-
ings of the 2020 ACM SIGSAC Conference on Com-
puter and Communications Security, pages 1769–
1787. Association for Computing Machinery.
Canetti, R., Sarkar, P., and Wang, X. (2020b). Blazing Fast
OT for Three-Round UC OT Extension, pages 299–
327. Springer International Publishing.
Castagnos, G., Catalano, D., Laguillaumie, F., Savasta, F.,
and Tucker, I. (2020). Bandwidth-Efficient Threshold
EC-DSA, pages 266–296. Springer International Pub-
lishing.
Chuang, C., Hsu, I., and Lee, T. (2023). A two-party hi-
erarchical deterministic wallets in practice (extended
version). https://eprint.iacr.org/2023/714.
Das, P., Erwig, A., Faust, S., Loss, J., and Riahi, S.
(2023). Bip32-compatible threshold wallets. Cryp-
tology ePrint Archive.
Doerner, J., Kondi, Y., Lee, E., and Shelat, A. (2018). Se-
cure two-party threshold ecdsa from ecdsa assump-
tions. In 2018 IEEE Symposium on Security and Pri-
vacy (SP), pages 980–997.
Gennaro, R. and Goldfeder, S. (2018). Fast multiparty
threshold ecdsa with fast trustless setup. In Proceed-
ings of the 2018 ACM SIGSAC Conference on Com-
puter and Communications Security, pages 1179–
1194. Association for Computing Machinery.
Gennaro, R. and Goldfeder, S. (2020). One round thresh-
old ecdsa with identifiable abort. Cryptology ePrint
Archive.
Guo, C., Katz, J., Wang, X., and Yu, Y. (2020). Efficient and
secure multiparty computation from fixed-key block
ciphers. In 2020 IEEE Symposium on Security and
Privacy (SP), pages 825–841.
Gutoski, G. and Stebila, D. (2015). Hierarchical determin-
istic bitcoin wallets that tolerate key leakage. In Fi-
nancial Cryptography, pages 497–504.
Huang, Y., Katz, J., and Evans, D. (2012). Quid-pro-quo-
tocols: Strengthening semi-honest protocols with dual
execution. Proceedings - IEEE Symposium on Secu-
rity and Privacy, pages 272–284.
Lindell, Y. (2021). Fast secure two-party ecdsa signing.
Journal of Cryptology, 34.
Luis, A., Nicky, M., and Apostol, V. (2019). Threshold
schemes for cryptographic primitives.
M., N. (2005). Identifiers and test vectors for hmac-sha-
224, hmac-sha-256, hmac-sha-384, and hmac-sha-
512. https://datatracker.ietf.org/doc/html/rfc4231.
McQuoid, I., Rosulek, M., and Roy, L. (2021). Batching
Base Oblivious Transfers, pages 281–310. Springer
International Publishing.
Ostrovsky, R. and Yung, M. (1991). How to withstand mo-
bile virus attacks (extended abstract). In Proceedings
of the Tenth Annual ACM Symposium on Principles of
Distributed Computing, PODC ’91, pages 51–59. As-
sociation for Computing Machinery.
Pettit, M. (2021). Efficient Threshold-Optimal ECDSA,
pages 116–135. Springer-Verlag.
Wuille, P. (2013). Hierarchical deterministic wal-
lets. https://github.com/bitcoin/bips/blob/master/bip-
0032.mediawiki.
A Two-Party Hierarchical Deterministic Wallets in Practice
855

Xue, H., Au, M. H., Xie, X., Yuen, T., and Cui, H. (2021).
Efficient online-friendly two-party ecdsa signature. In
Proceedings of the 2021 ACM SIGSAC Conference on
Computer and Communications Security, pages 558–
573. Association for Computing Machinery.
Yao, A. (1986). How to generate and exchange secrets. In
27th Annual Symposium on Foundations of Computer
Science (sfcs 1986), volume 10, pages 162 – 167.
Zahur, S., Rosulek, M., and Evans, D. (2015). Two halves
make a whole. In Advances in Cryptology - EURO-
CRYPT 2015, volume 9057, pages 220–250. Springer
Berlin Heidelberg.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
856
