
A Lightweight Access Control Scheme with Attribute Policy for
Blockchain-Enabled Internet of Things
Syed Sajid Ullah
a
, Vladimir Oleshchuk
b
and Harsha S. Gardiyawasam Pussewalage
c
Department of Information and Communication Technology, University of Agder, Grimstad N-4898, Norway
Keywords:
Blockchain, Internet of Things (IoT), Access Control, blockchain-enabled Internet of Things, Digital
Signature, Hyper Elliptic Curve Cryptography.
Abstract:
The Internet of Things (IoT) revolution has increased the number of connected devices, leading to new security
challenges. One of these challenges is the management of access control for these devices. Traditional access
control methods may not be able to address these challenges effectively. This paper proposes attribute-based
access control (ABAC) for the blockchain-enabled Internet of Things (BE-IoT). ABAC allows access to be
granted or denied based on the attributes of the user or device requesting access rather than relying on a central
authority to manage access control information. This allows for more flexible and dynamic access control poli-
cies that can adapt to changing situations and minimize the risk of unauthorized access. Blockchain technology
provides a secure and transparent way to manage access control information for IoT devices. Blockchain is a
decentralized and distributed ledger allowing secure and tamper-proof information storage. By storing access
control information on the blockchain, it can be shared across a network of devices transparently and securely.
The authors conduct a security analysis to evaluate and compare the proposed scheme to existing schemes.
The analysis results indicate that the proposed scheme has the advantage of using minimal computation time
and communication overhead compared to previous solutions. The authors suggest that the ABAC scheme
using blockchain combined with a lightweight Hyperelliptic Curve Cryptosystem (HCC) is well suited for
secure deployment in IoT.
1 INTRODUCTION
The Internet of Things (IoT) refers to the integration
of diverse physical entities equipped with sensors,
embedded software, and network interfaces, such
as household appliances, automobiles, and industrial
machinery (Kumar et al., 2019), (Sinha et al., 2022).
These devices collect and exchange data, thereby ex-
panding their capabilities. The remote interaction and
control of these devices have the potential to radi-
cally alter lifestyle and occupational norms, with sub-
stantial implications for business dynamics. How-
ever, IoT also brings new security challenges to the
table; as the number of connected devices increases,
so does the number of potential vulnerabilities (Omo-
lara et al., 2022), (Swessi and Idoudi, 2022). Protect-
ing IoT devices from unauthorized access is crucial
for preventing data leakage and protecting valuable
and sensitive information stored on these IoT devices.
a
https://orcid.org/0000-0002-5406-0389
b
https://orcid.org/0000-0002-7905-1016
c
https://orcid.org/0000-0002-3623-3362
Access control is a vital aspect of cybersecurity that
ensures that only individuals with the proper autho-
rization can access computer systems, devices, and
the sensitive information stored within them. By im-
plementing effective access control measures, orga-
nizations can safeguard their critical assets and pre-
vent potential security breaches (Sandhu and Sama-
rati, 1994). When it comes to providing a secure and
efficient mechanism for the protection of information
in the large-scale and complex environment of the
IoT, traditional access control models, such as discre-
tionary access control (DAC), mandatory access con-
trol (MAC), and role-based access control (RBAC),
have limitations (Hu et al., 2015). These models were
designed for use in closed systems and did not have
the capability to deal with the dynamic interactions
that can arise between a large number of connected
devices in an IoT environment.
The attribute-based access control (ABAC) (Wang
et al., 2004), allows access to be granted or de-
nied depending on the attributes of the user or de-
vice requesting access. A user’s identity, location,
528
Ullah, S., Oleshchuk, V. and Pussewalage, H.
A Lightweight Access Control Scheme with Attribute Policy for Blockchain-Enabled Internet of Things.
DOI: 10.5220/0012138900003555
In Proceedings of the 20th International Conference on Security and Cryptography (SECRYPT 2023), pages 528-539
ISBN: 978-989-758-666-8; ISSN: 2184-7711
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)

role, or even the device can be considered among
these attributes. Traditional access control methods
have been replaced by ABAC, which offers a finer-
grained level of control over who can access various
resources. In addition, ABAC makes it possible to
have access control policies that are more adaptable
and dynamic, which means they can accommodate
shifting conditions and reduce the likelihood of unau-
thorized access.
Access control information can be stored in
a ledger that is decentralized and distributed if
blockchain technology is used, providing an increased
level of security as well as transparency. In addition,
because blockchain is a decentralized and distributed
ledger, it enables all of the parties in the network to
have a copy of the same data. This makes it extremely
difficult to alter the data, further increasing its secu-
rity. The combination of blockchain technology, IoT,
and ABAC offers a more efficient and secure access
control approach to handle a large number of IoT de-
vices. In a Blockchain-Enabled ABAC (BE-ABAC)
for IoT, each device has a unique identifier stored
on the blockchain. Access requests are sent to the
blockchain network for evaluation. Furthermore, the
blockchain network would verify the attributes of the
user or device against the device’s access control pol-
icy, which is also recorded on the blockchain. Imple-
menting blockchain in this setting offers several ad-
vantages over more conventional approaches to con-
trolling access. Because it is decentralized and dis-
tributed, the blockchain does not have a single point
that can be attacked or compromised. In addition, the
utilization of smart contracts enables the automated
execution of access control policies, which can help
to contribute to an increase in efficiency while simul-
taneously decreasing the likelihood of a mistake being
made by a human.
To guarantee the security of the attributes uti-
lized in the access control determination, ABAC sys-
tems often use various cryptographic methods, such
as RSA, Bilinear pairing (BP), Diffie-Hellman (DH),
Elliptic Curve Cryptosystem (ECC), and HCC (Hus-
sain et al., 2021). It has been demonstrated that HCC
provides superior performance in terms of key length
and efficiency compared to ECC, BP, DH, and RSA
(Hussain et al., 2020). HCC also has a shorter key
length. In addition, HCC uses an 80-bit key, which
offers a high level of protection and has a size ap-
propriate for the resource-constrained devices typi-
cal for IoT environments. In general, the utiliza-
tion of HCC in ABAC systems for IoT, in combi-
nation with Blockchain technology, provides a bal-
ance of security and efficiency, making it an appropri-
ate choice to secure communication in IoT systems.
Also, blockchain allows for creating a decentralized
and tamper-proof record of access control decisions.
This can be used to ensure the integrity of the at-
tributes used in the access control decision and the
authenticity of the devices accessing the resources.
Inspired by the above considerations, we present a
lightweight ABAC scheme for BE-IoT. The proposed
scheme is considered lightweight because it is built on
the fundamental idea of HCC. The main contributions
of the paper are listed below.
• We designed an ABAC system for blockchain-
enabled Internet of Things (BE-IoT) that is both
secure and lightweight.
• We proved that the proposed scheme is secure
based on the hardness of the Hyperelliptic Curve
Discrete Logarithm Problem in the random oracle
model.
• We compare the efficiency of the proposed
scheme with previous schemes, and the results in-
dicate that the proposed scheme has superior ef-
ficiency in terms of computational and communi-
cation costs.
1.1 Paper Organization
The paper is organized into nine sections: Intro-
duction and Motivation (Section 1), Literature Re-
view (Section 2), Threat Model (Section 3), Network
Model for Access Control (Section 4), Proposed Ac-
cess Control Mechanism (Section 5), Deployment and
Workflow (Section 6), Formal Security Analysis (Sec-
tion 7), Performance Analysis (Section 8), and Con-
clusion (Section 9).
2 RELATED WORK
(Alansari et al., 2017), presented an innovative iden-
tity and access management solution in cloud feder-
ations. The proposed solution utilizes ABAC poli-
cies and blockchain technology with trusted hardware
from Intel to protect users’ identities while ensuring
the policy review process is honest and transparent.
Due to the intensive Bilinear Pairing algorithm, the
proposed method consumes a great deal of compu-
tational and communication resources, and the pro-
posed system requires formal security proof. (Wang
et al., 2018), examine a data storage and sharing
scheme in decentralized storage systems and presents
a framework that integrates the interplanetary file sys-
tem, the Ethereum blockchain, and ABE technology.
This framework allows data owners to encrypt shared
data and control who can access it through access
A Lightweight Access Control Scheme with Attribute Policy for Blockchain-Enabled Internet of Things
529

policies while implementing a keyword search func-
tion on the ciphertext of the data using smart contracts
on the Ethereum blockchain. The proposed method
has a few limitations: it employs a computationally
and communicatively intensive Bilinear Pairing algo-
rithm. Formal security proof is required to ensure
its security and reveal private key attacks. Besides,
the proposed solution improves data storage and shar-
ing in decentralized storage systems; it may require
additional security guarantees for resource use to be
practical. (Alniamy and Taylor, 2020) propose an ar-
chitecture model to offer greater fine-grained access
control over data stored in the cloud. The model in-
tegrates the Hyperledger blockchain technology and
the ABE scheme. This allows data owners to encrypt
shared data and control access through access control
policies connected with attributes. However, the au-
thors fail to provide a formal proof.
(Yang et al., 2021), propose a non-interactive ac-
cess control strategy for the IoT based on blockchain
technology and private set instruction (PSI). The pro-
posed strategy allows data holders to store their infor-
mation on a cloud server and users to access this data
by adding attributes as a transaction to the blockchain.
A smart contract then executes the PSI protocol to
determine whether the characteristics set satisfies the
threshold structure, and if it does, the user is granted
access to the data. However, the proposed method
employs a computationally intensive Bilinear Pairing
algorithm, which is not suitable for a resource-limited
environment. (Liu et al., 2021), offer a revocable
ABAC system for blockchain applications. The de-
sign approach allows for attribute-level access con-
trol and user revocation. The proposed method em-
ploys a resource-intensive Bilinear Pairing algorithm,
which necessitates extensive computational and com-
munication resources. (Rouhani et al., 2021), ABAC
on blockchain will allow reliable auditing of access
attempts. The system’s audibility and openness will
benefit both parties. With Hyperledger Fabric, the
authors claim high efficiency with low computational
overhead. However, due to the intensive Bilinear Pair-
ing algorithm, the proposed method consumes a great
deal of computational and communication resources.
In 2021, (Zaidi et al., 2021) propose a blockchain-
based ABAC approach for the IoT. IoT devices can
control the user’s environment and collect personal
data. Smart contracts automate data access, while
Proof of Authority improves system performance and
reduces gas usage. Data are encrypted and can only
be decrypted within a valid access time when using
blockchains. Due to the intensive Bilinear Pairing al-
gorithm, the proposed method consumes a great deal
of computational and communication resources. (Lu
et al., 2021), propose using ABE with blockchain
technologies to regulate IoT data access. Data encryp-
tion and ABE algorithms create fine-grained access
control while ensuring IoT security. Aside from data
hash values, the blockchain currently stores cipher-
text location, access control policy, and other critical
information in hash values. However, due to the inten-
sive Bilinear Pairing algorithm, the proposed method
consumes a great deal of computational and commu-
nication resources. There also needs to be explicit se-
curity proof for the proposed approach. (Arasi et al.,
2022)propose a new data-sharing system combining
blockchain technology and ABAC management. The
author creates a trustworthy blockchain-based scheme
for safe data sharing with integrity audits that main-
tain data integrity. Due to the intensive Bilinear
Pairing algorithm, the proposed method consumes a
great deal of computational and communication re-
sources, and the proposed system requires formal se-
curity proof. A blockchain-enabled ABAC that main-
tains confidentiality was proposed by (Zhang et al.,
2022) for use in intelligent healthcare systems. The
proposed method prevents failure at a single point
and lowers the expenses of online operations thanks
to online-offline encryption.
(Zhu et al., 2018b), focus on creating a secure
resource-sharing platform that leverages the advan-
tages of a decentralized blockchain environment, flex-
ible and diverse permission management, and a ver-
ifiable and transparent access mechanism. They
propose a transaction-based access control (TBAC)
platform that combines the blockchain system and
the industry-standard ABAC model The authors pro-
pose a TBAC-related cryptosystem (CryptoTBAC)
for secure attribute exchanging and dynamic policy
decision-making. (Zhu et al., 2018a), presented a dig-
ital asset management platform, DAM-Chain, which
utilizes TBAC and combines the benefits of the distri-
bution ABAC paradigm and blockchain technology.
The ABAC in the platform offers flexible and de-
centralized authorization mechanisms for digital asset
management on the blockchain. Blockchain transac-
tions serve as a traceable and verifiable method for
access requests. (Dukkipati et al., 2018), proposed an
ABAC system for the IoT that enables users to access
and manage their data. The authors used a blockchain
model to create access control measures, but there
were privacy concerns and a lack of explicit security
evidence. (Ding et al., 2019), introduced a new ABAC
approach for IoT systems that leverages blockchain
technology to prevent single points of failure and data
tampering. Streamlining access control methods and
technologies has also enhanced low-power processing
efficiency for IoT hardware.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
530
(Jiang, 2021), introduce smart contract-based ac-
cess control, which eliminates the need for a central
trusted server and instead uses the blockchain to com-
plete access authorization. The proposed technique
addresses the standard access control strategy’s cen-
tralization issue. The scheme contains a security flaw
and uses heavy computation and communication re-
sources. (Ghorbel et al., 2021), reveal blockchain-
based ABAC and fine-grained access control, which
maintains user privacy and accountability. The au-
thors constructed a permission blockchain prototype
and ran numerous tests to establish the solution’s scal-
ability, which they presented at the conference. Un-
fortunately, Due to the intensive Bilinear Pairing al-
gorithm, the proposed method consumes a great deal
of computational and communication resources, and
the proposed system requires formal security proof.
After conducting a comprehensive study, it has
been found that the recommended methods, partic-
ularly those using bilinear pairing, have significant
computational and communication resource utiliza-
tion drawbacks. The underlying cryptographic al-
gorithms used in these methods are computationally
intensive and result in substantial overheads, mak-
ing them impractical for many applications. More-
over, despite their popularity, these methods have not
been rigorously tested and analyzed for security, and
proper formal security proof is lacking. This raises
concerns regarding the security of these methods, as
they rely heavily on theoretical assumptions and lack
empirical evidence to support their claims. As a re-
sult, it is essential to conduct more extensive secu-
rity analysis and testing before these methods can be
widely adopted and relied upon. Despite these chal-
lenges, developing a secure and efficient scheme is es-
sential for ensuring the privacy and security of digital
communications and transactions. As such, contin-
ued research and development in this field are critical
for advancing the state of the art and addressing the
current limitations of existing methods.
3 NETWORK MODEL FOR
ACCESS CONTROL IN
BLOCKCHAIN-ENABLED IOT
We used a lightweight ID-based signature and at-
tributes access policy to provide and fill the ac-
cess control requirements for IoT using blockchain.
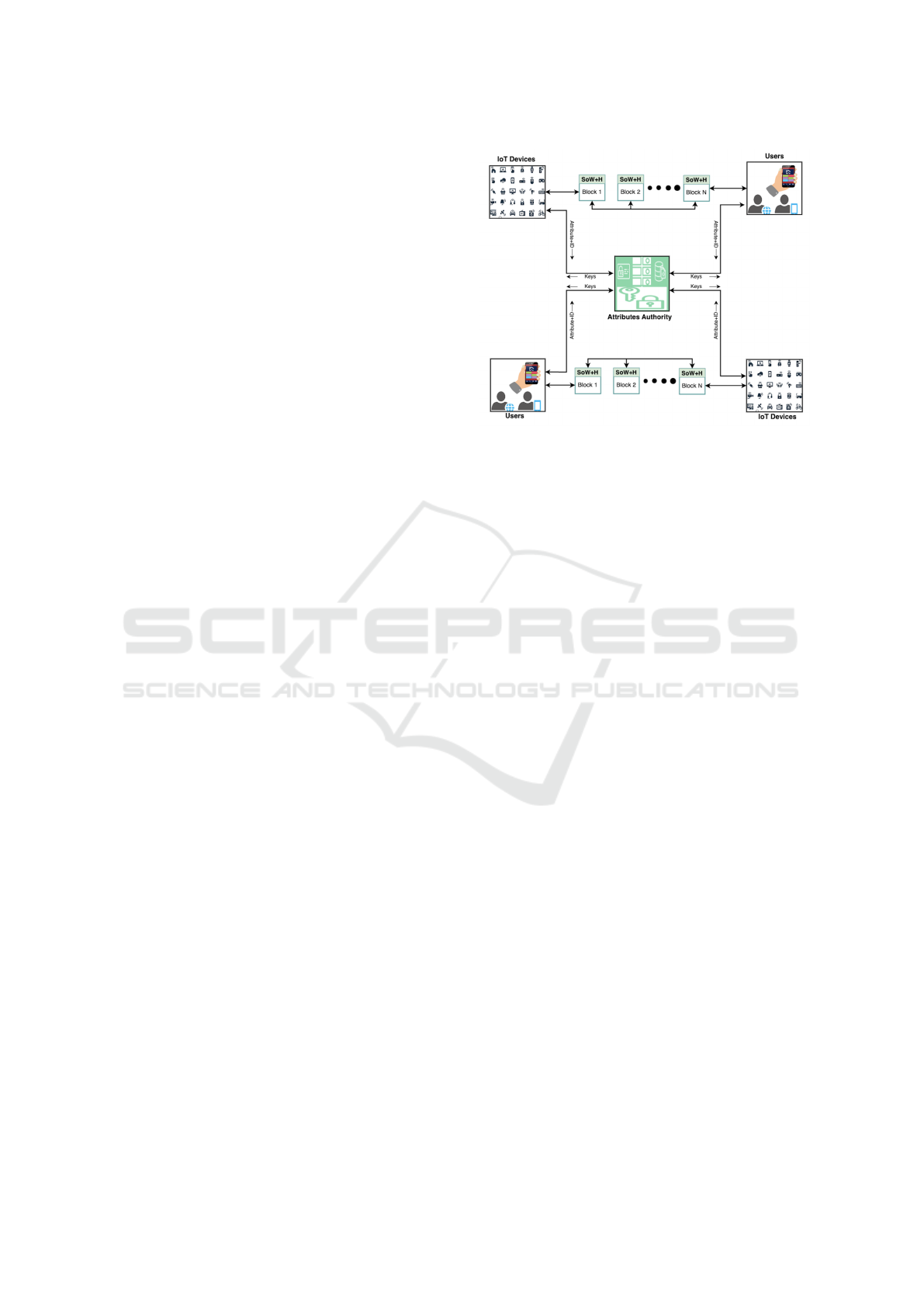
Figure 1 presents a network model for secure and
well-managed access control in blockchain-enabled
IoT. This modal consists of IoT Devices, Users,
Blockchain, and Attributes Authority participants.
Figure 1: Proposed network modal for access control in
blockchain-enabled IoT.
IoT Device: The IoT is a network of physical de-
vices equipped with sensors, software, and network
connectivity that allow them to gather and exchange
data. In the context of a blockchain-enabled IoT (BE-
IoT) infrastructure, an IoT device refers to any phys-
ical device that is used in IoT applications such as
smart healthcare, smart homes, banking, and smart
contract trading. These devices can include devices
like smart thermostats, cameras, door locks, and many
other types of connected devices. These devices pro-
vide access and data to users using blockchain tech-
nology.
Users: Users refer to end-users or devices that want to
access and retrieve data from IoT devices. The users
can be individuals or organizations looking to access
data from IoT devices for various reasons like mon-
itoring, control, and decision-making. These users
need to be authenticated and authorized to access the
IoT data.
Blockchain: In a BE-IoT infrastructure, the data is
stored in a combination of blocks containing IoT de-
vice requests. Blockchain is a decentralized tech-
nology that uses a digital ledger to record and se-
cure transactions between multiple parties. It employs
cryptography to ensure the authenticity, integrity, and
immutability of the data stored on the ledger. The
data are organized in blocks, each containing a set of
transactions and a cryptographic hash of the previous
block. This structure creates a blockchain that forms
the blockchain, making it tamper-resistant.
Attributes Authority (AA): An essential aspect of
a BE-IoT infrastructure is the Attributes Authority
(AA), which is a trustworthy authority that establishes
secure access. The AA assigns access attributes and
provides participants with a key pair. These attributes
can be things like user identification, location, time,
A Lightweight Access Control Scheme with Attribute Policy for Blockchain-Enabled Internet of Things
531

and other information that can be used to make access
decisions. The key pair is used to sign and verify data,
ensuring only authorized parties can access it. The AA
is a critical element in a BE-IoT system, playing a cru-
cial role in maintaining data security and protection.
It verifies the attributes and identity of users to ensure
that only authorized entities are granted access to IoT
device data, preventing any unauthorized access and
safeguarding the integrity of the data.
The algorithm sections explain in detail the activ-
ities of all participants in the proposed access control
scheme.
4 THREAT MODEL
In a BE-IoT infrastructure, the main issue that could
compromise the system is illegal access to IoT data.
Threats in a BE-IoT include actions that compro-
mise data access, integrity, availability, and verifica-
tion of data owner. Individuals with malicious in-
tent and technical capabilities can exploit these vul-
nerabilities. Researchers have developed various ac-
cess control cryptographic schemes to address secu-
rity and privacy concerns in the open BE-IoT envi-
ronment. These schemes aim to ensure secure data
exchange between peers and prevent adversaries from
accessing, retrieving, or tampering with the informa-
tion. The typical threat model for designing these se-
curity solutions is the (Dolev and Yao, 1983), which
assumes an insecure public channel and powerful ad-
versaries who can access and receive data through the
BE-IoT network. However, this model does not ac-
count for the possibility of an attacker guessing ran-
dom numbers or obtaining access without a valid key.
In this work, our proposed access control scheme for
BE-IoT is based on the DY threat model and assumes
that only the AA is trusted and secure. The scheme
leverages digital signatures to verify devices and data
sources and grant secure access to end users. The dig-
ital signatures-based access control allows for secure
verification of devices and data sources, granting se-
cure access to end-users. The proposed scheme aims
to provide enhanced security compared to previous
solutions while still operating within the constraints
of the DY threat model.
To enhance security in the BE-IoT environment
with minimal cost, an access control scheme has been
proposed. The objective of this scheme is to provide
secure access to the users while operating in the BE-
IoT where adversaries can access, retrieve, and ex-
change block data. The scheme is designed to be Ex-
istentially Unforgeable and Secure against Attacks on
Access Control (UAACA). In this scheme, a game
is played between the adversary (AV ) and the chal-
lenger (CA). The AV inputs the public parameter P,
which has a polynomial running time and tries to win
a game with a probability of non-negligibility. The
CA, on the other hand, must respond to the queries
made by the AV in order to play the game. The aim of
the game is to ensure that the access control scheme
remains secure and prevents unauthorized access to
the data and devices in the BE-IoT environment.
• For any participants identity ID
u
, the AV issues an
extraction query Q
ex
, and the CA executes a key
generation query using ID
u
as input, obtaining a
private key PV K
u
, which is then sent back to the
AV as a response.
• When the AV receives a Signature Generation
Query Q
signature
, they provide PV K
u
as input. The
CA then runs the Signature Generation Algorithm
using PV K
u
and provides the resulting signature
Sd to the AV .
• The AV inputs ID
′
u
and user/object attributes or
data Π
′
. It generates Z
′
as the signature. The
extraction query Q
ex
and the signature generation
query Q
signature
have not been executed previously
for ID
′
u
and Π
′
.
5 PROPOSED ACCESS CONTROL
ALGORITHM FOR
BLOCKCHAIN-ENABLED IOT
The following is the detail of the proposed algorithm
and its working steps.
Access Policy and Condition: Let S be a set of at-
tributes, U be a set of users with identities (ID
u
), and
Π be an object or data in our BE-IoT. Every user and
object must sign attributes or data (Sd). The access
will grant according to the following conditions and
rules R.
• Access grants if Sd verified (S |= R).
• Access denied if Sd verification field (S ⊭ R).
Setup for Registration: The Attribute Authority (AA)
executes this phase. The AA takes the parameter of se-
curity (ps), selects finite field (FF) and divisor (Dv)
of HCC of order n.
• Choose the master secret key (Ms), such that
Ms ∈{1,2,3,. . . ,n-1}.
• calculate the master public key (Mb), Mb = Ms ·
Dv.
• choose hash functions H
1
, H
2
of SHA-256 nature.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
532

The AA then publishes P = (n,H
1
,H
2
,Dv,Mb) as
public parameters set in the blockchain-enabled IoT
network and keeps (Ms) secret with itself.
Key Generation: In this step, the IoT devices, and
users send the identities (attributes) (ID
u
) to AA. The
AA calculates keys for all participants by computing
follow steps.
• Calculate private keys for participants (PV K
u
).
• At the start, the AA pick a number randomly Rn ∈
1,2,3, ... ,n − 1.
• Compute h
1
= H
1
(ID
u
,Mb).
• Set the PV K
u
= Rn + h
1
· Ms mod n where PV K
u
of every participants will be different.
• In the same, the AA calculate public keys (PBK
u
)
for participants as PBK
u
= Rn · Dv where PBK
u
of every participants will be different from each
other. Then AA set a factor FA = h
1
· Mb.
After calculations, the AA sends (PV K
u
,PBK
u
) to the
participants via a secure channel.
Access: In this step, the IoT devices, users, or block
owner requests to access any data or block addition in
IoT networks.
• Grants access if the attribute matches S |= R.
• Denied access if the attribute does not match S ⊭
R.
The following steps of signature generation and veri-
fication will be used to find the validity of IoT devices,
and users, in our BE-IoT.
Signature Generation: The signature will be applied
to validate the user for access, or data sources authen-
tication. This algorithm will be run by IoT devices,
a user when requested to access IoT data, IoT data
owner for delivering data. It takes an attribute, object,
or IoT data as input represented by Π, a nonce (Fn),
ID
u
, PV K
u
, PBK
u
, and executes the following steps.
• The participant picks a random number Rs ∈
{1,2,3, ... ,n − 1} and calculates Pn = Rs · Dv.
• The participant computes a message digest h
2
=
H
2
(Π,Pn,ID
u
,Fn) where ID
u
and h
2
of every
IoT device, users, and IoT Data Owner will be dif-
ferent from each other. Here We use an additional
fresh nonce (Fn) to achieve the goal of revoca-
tion.
• The participant generate Z = Rs + h
2
· PV K
u
mod
n
The participant delivers the signed attribute or data
Sd = ID
u
,Z,PV K
u
to the recipient.
Note: The user will execute this algorithm to re-
quest access, and the sender, after access is granted,
signs the data.
Signature Verification: To find the validation of the
user for access, verification of block addition, IoT de-
vices, and data source verification, the applied signa-
ture (Z) will be verified as.
• Compute the digest of a message h
2
= H
2
(Π,
Pn,ID
u
,Fn).
• Compute Z · Dv=Pn + h
2
(PBK
u
+ FA)
If Sd is verified it holds S |= R then access will be
granted. Otherwise, denied access according to S ⊭ R.
Note: The sender will execute this algorithm to
verify the requested users for access grant, IoT Data
Owner for allowing block addition, and receivers to
verify the data source.
5.1 Consistency of the Proposed Scheme
The following calculations proved the correctness of
the designed attribute for access.
Z = Rs + h
2
· PV K
u
To prove this, we multiply Dv by both sides;
Z · Dv = (Rs + h
2
· PV K
u
)Dv
Multiply Dv by both elements of the brackets;
Z · Dv = Rs · Dv + (h
2
· PV K
u
)Dv
As we know Rs · Dv = Pn, so put the value of Rs;
Z · Dv = Pn + h
2
(PV K
u
)Dv
Similarly PV K
u
= PBK
u
+ h
1
· Mb, put the value;
Z · Dv = Pn + h
2
(PBK
u
+ h
1
· Mb)
Also h
1
· Mb = FA, so put the value of h
1
· Mb;
Z · Dv = Pn + h
2
(PBK
u
+ FA)
So, the above equations securely calculate the
value of Z.
6 DEPLOYMENT AND
WORKFLOW OF THE
PROPOSED SCHEME
As depicted in Figure 2, our access control scheme is
intended to be used in a BE-IoT environment. This
scheme aims to allow multiple users to securely ac-
cess IoT devices while ensuring that only valid users
are granted access as per the set Blockchain policies.
To achieve this goal with minimal resource consump-
tion, the scheme is designed to operate in the follow-
ing consecutive steps:
Access Policy and Condition : Let S be a set of at-
tributes, U set of users with identities (ID
u
), and Π
be objects or data in our BE-IoT. Every user and ob-
ject must sign attributes or data (Sd). Access grants if
Sd verified (S |= R). Access denied if Sd verification
field (S ⊭ R).
A Lightweight Access Control Scheme with Attribute Policy for Blockchain-Enabled Internet of Things
533
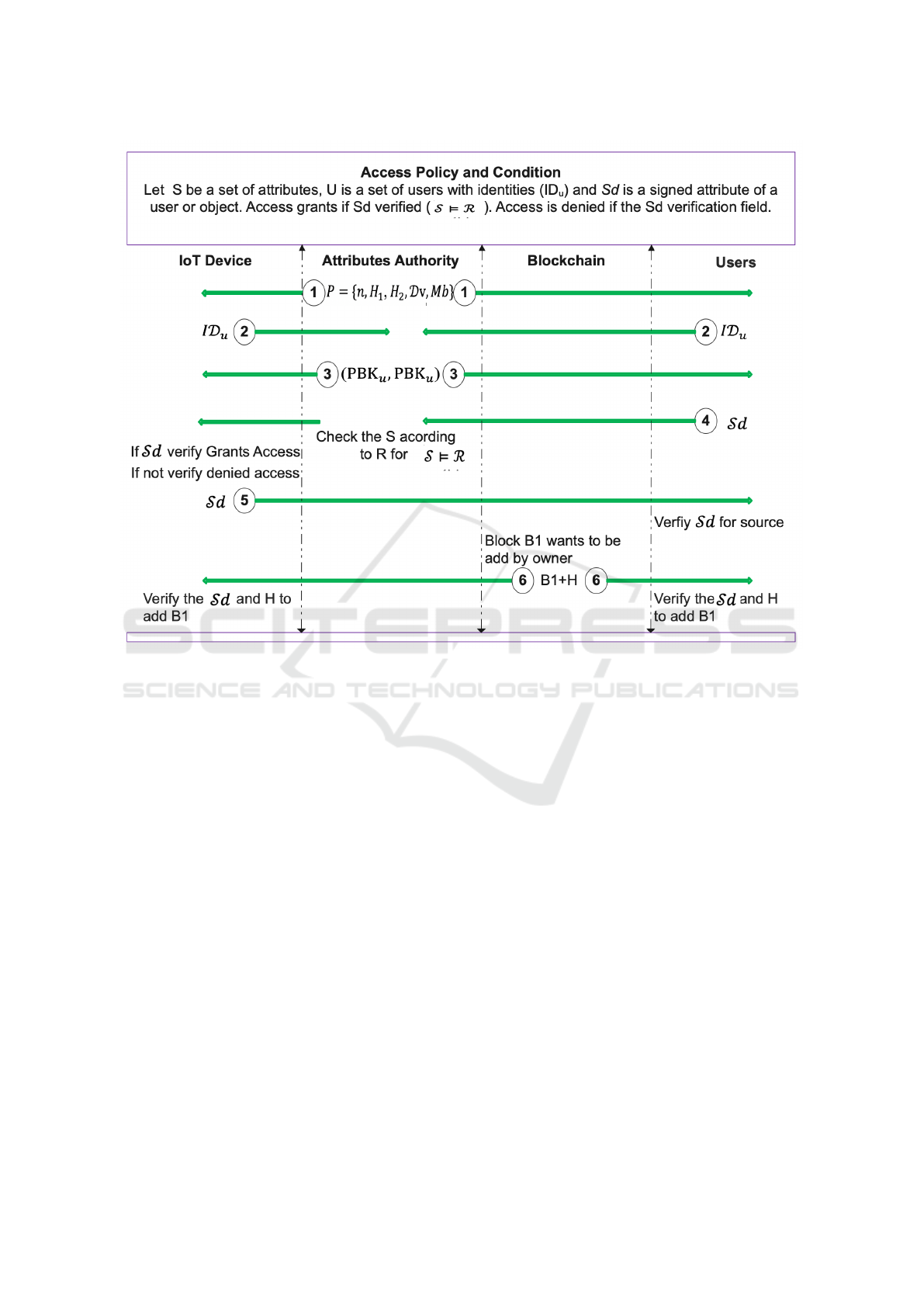
Figure 2: Deployment and workflow of the proposed scheme.
Setup for Registration and Connectivity: To connect
to the network. First, the Attribute Authority (AA)
take the parameter of security (ps), selects finite field
FF and divisor Dv of order n, chooses master se-
cret key (Ms), where Ms ∈ {1,2,3,...,n − 1}, cal-
culate the master public key (Mb), Mb = Ms· Dv, and
chose hash functions H
1
, H
2
. The AA then publishes
P = (n, H
1
,H
2
,Dv,Mb) as public parameters set in the
IoT network publicly and keeps (Ms) secret with it-
self. To connect to the network, the IoT devices and
users send the identities (attributes) (ID
u
) to AA. The
AA calculates private keys for participants (PV K
u
).
At the start, the AA pick a number randomly Rn ∈
{1,2,3, ... ,n − 1}, compute h
1
= H
1
(ID
u
,Mb).Then
set PV K
u
= Rn + h
1
· Ms mod n where PV K
u
of every
participant will differ. In the same, the AA calculates
public keys (PBK
u
) for participants as PBK
u
= Rn·Dv
where PBK
u
of every participant will be different
from each other. Then AA set a factor FA = h
1
· Mb.
After calculations, the AA sends (PV K
u
,PBK
u
) to the
participants via a secure channel.
Request for Access: Let the user request to access data
(Π). The user will apply a digital signature (Z); for
that, the user takes the requested data name (Π), a
fresh nonce (Fn), ID
u
, PV K
u
, PBK
u
. To generate Z,
the user picks a random number Rs ∈ {1, 2,3,. .., n −
1} , calculate Pn = Rs · Dv, compute data name digest
h
2
= H
2
(Π,Pn, ID
u
, Fn). The user generates Z = Rs
+ h
2
· PV K
u
mod n and sends an access request. The
requested data must include attributes like the thing’s
name, identity, etc.
User Verification to Grant or Denied Access: To val-
idate the user’s access, the attributes must be present
in S according to R, and the applied signature Z
will be verified by computing the digest data name
h
2
= H
2
(Π,Pn,ID
u
,Fn) and computing Z ·Dv = Pn+
h
2
(PBK
u
+ FA). If Z is verified according to R, then
the conditions S |= R are satisfied, and access will be
granted. Otherwise, access will be denied according
to the state S ⊭ R. When access is granted, the IoT
devices will apply a digital signature on the requested
data Sd = ID
u
,Z,PV K
u
using the same signature gen-
eration process as explained in the request for access
step. The user can verify the signature to validate the
data sources of the IoT device.
Block Verification for Addition: let the owner want
to add a new block. IoT Data Owner will contain sig-
nature Z, and the block will be hash h and informa-
SECRYPT 2023 - 20th International Conference on Security and Cryptography
534

tion of the last block. Here, the same digital signature
process will be applied to generate the signature, and
every user and IoT Data Owner will verify the sig-
nature using our verification process. If the IoT Data
Owner’s signature is confirmed, it will be added to the
chain. Otherwise, it will remove.
7 FORMAL ANALYSIS OF
SECURITY
In this section of the paper, we will demonstrate
the security of our access control scheme under the
assumption of the hardness of the HCDLP prob-
lem using the Random Oracle Model (ROM). If
an attacker/adversary AV has non-negligible advan-
tage NNA and can make at most MosT queries for
hash Q
hash
, extraction Q
ex
, and signature genera-
tion Q
signature
, then the security of the scheme is
guaranteed against malicious access, unverified data
sources, and unverified block additions. The CA
with an execution time of
23(Q
hash
H
τ
2
)
NNA
and a prob-
ability of NNA
′
⩾
1
9
can solve the HCDLP prob-
lem if
NNA ⩾
10(Q
hash
H
2
+1)(Q
hash
H
2
+Q
signature
)
2
ps
and
MosT
′
⩽
23(Q
hash
H
τ
2
)
NNA
(Ullah et al., 2020).
PROOF: Let a be such that the CA is challenged with
an HCDLP. Also, the task of the CA is to calculate Z
from W = Z · Dv, where Z ∈ {1, 2,3,. .., n − 1}. The
CA sets P = (n,H
1
,H
2
,Dv,Mb) as a set of parameters
for the public. The response to the AV queries is given
below.
1. Queries on H
1
: The CA in start maintains an
empty list H
LS
1
containing the tuples (ID
u
,PBK
u
).
If the tuples (ID
u
,PBK
u
) exist in H
LS
1
, the CA
returns h
1
; otherwise, the CA chooses a random
h
1
∈ {1, 2,3,. .., n −1} and stores (ID
u
,PBK
u
,h
1
)
in H
LS
1
and returns h
1
.
2. Queries on H
2
: The CA initially maintains an
empty H
LS
2
containing the tuples (Π, Pn,ID
u
).
If the tuples (Π,Pn,ID
u
) exist in H
LS
2
, the CA
returns h
2
; otherwise, the CA selects a num-
ber at random h
2
∈ {1,2, 3,.. .,n − 1}, stores
(Π,Pn,ID
u
) in H
LS
2
, and returns h
2
.
3. Query on Extraction Q
ex
: When CA submits
a request with ID
u
, then CA randomly selects
x,y ∈ {1, 2,3,. .., n − 1}, sets PBK
u
= x · Mb +
y · Dv, PV K
u
= x, and h
1
= (ID
u
,PBK
u
) = −i
mod n. The tuple (PV K
u
,PBK
u
) satisfies the
equation PV K
u
· Dv = Pub
u
+ FA in the key gen-
eration algorithm, where FA = h
1
· Mb and h
1
=
H
1
(ID
u
,PBK
u
). The CA generates (PV K
u
,PBK
u
)
as the public-private key pair of ID
u
and copies
the tuple (PV K
u
,PBK
u
,H
1
(ID
u
,PBK
u
),ID
u
) in
the H
LS
1
.
4. Queries on Signature Generation Q
signature
: Upon
request with ID
u
from the AV, CA performs the
following steps.
• The Q
signature
check determines whether it
has been queried for ID
u
. If it has been
queried for Q
hash
or Q
signature
, it retrieves
(ID
u
,PV K
u
,PBK
u
,H
1
(ID
u
,FA),ID
u
) from the
list H
LS
1
. Then, the Signature Generation pro-
cess is performed by the CA, which produces Z
and inserts it into H
2
(Π,Pn,ID
u
) within H
LS
2
.
• If it is not asked to perform the Q Queries on
Signature Generation (Q
signature
), then the CA
processes the specified oracle and retrieves the
matching secret key to generate a signature for
access.
• If it is queried, then the CA selects two random
numbers x and y from the set 1, 2,3,. ..,n − 1.
It retrieves h
1
= H
1
(ID
u
,PBK
u
) from H
LS
1
and
calculates Pn = x · Dv − y · PBK
u
− y · h
1
· Mb.
Then, it sets x = Z and h
1
= y, and inserts
(Π,Pn,ID
u
,y) into H
LS
2
. If (Π,Pn,ID
u
,y) al-
ready exists in H
LS
2
, the CA response is false,
and it exits. The failure probability is not more
than 1/n
′
as y is selected randomly.
When AV can produce the same signa-
ture for access as described in the Signature
Generation procedure by using the function
NNA⩾10(Q
hash
H
2
+1)·(Q
hash
H
2
+Q
signature
)
2
ps
. It is im-
portant to note that if CA has not undergone the
Signature Generation oracle for access, two valid
signatures can be created: (Π,PBK
u
,Pn,h
2
,Z) and
(Π,PBK
′
u
,Pn
′
,h
′
2
,Z
′
).
Thus, verification processes are necessary to grant
access or verify data
Firstly,
Pn=g(Dv), PBK
u
= x · Mb + y · Dv, Mb = Ms · Dv
Z(Dv) = g · Dv + h
2
· x · sMs · Dv + h
2
· h
1
· Ms · Dv
Secondly,
Z
′
(Dv) = g · Dv + h
′
2
· x · Ms · Dv + g · Dv = h
′
2
· y ·
Dv + h
′
2
· h
1
· Ms · Dv
Z
′
·Z · Dv = Z
′
·g ·Dv+Z
′
·h
2
·x ·Ms ·Dv +Z
′
·h
2
·
y · Dv + Z
′
· h
2
· h
1
· Ms · Dv
Z · Z
′
· Dv = Z · g · Dv + Z · h
′
2
· x · Ms · Dv + Z · h
′
2
·
y · Dv + Z · h
′
2
· h
1
· Ms · Dv
So, if we perform the subtraction, then we have
(Z · −Z
′
·g+Z ·h
′
2
·y−Z
′
·h
2
·y)·(Dv = Z · h
′
2
·x−Z
′
·
h
1
· x + Z ···h
′
2
· h
1
) · Ms · Dv.
Then we have k = (Z · g − Z
′
· g + Z · h
′
2
· x − Z
′
·
h
1
· x) mod n and (ζ) mod n = (Z · h
′
2
· x − Z · h
2
·
A Lightweight Access Control Scheme with Attribute Policy for Blockchain-Enabled Internet of Things
535

x + Z · h
′
2
· h
1
)
−1
mod n, which is the solution of the
HCDLP for CA with the time MosT
′
⩽
23(Q
hash
H
τ
2
)
NNA
and probability NNA
′
⩾
1
9
(Ullah et al., 2020).
8 EFFICIENCY ANALYSIS
The goal is to determine how well the scheme per-
forms in terms of its resource requirements. For ef-
ficiency analysis, we selected four schemes ((Wang
et al., 2018), (Liu et al., 2021), (Zhang et al., 2022),
and (Zhu et al., 2018a)) based on their formal proofs
and clear cryptographic operations. This analysis is
essential because it helps to assess the feasibility of
using a particular scheme in a given application and
can also be used to compare different schemes and
choose the most appropriate one. Some factors that
are commonly considered in efficiency analysis in-
clude the time and number of bits required for secure
access, as well as the size of the keys and ciphertext.
8.1 Computation Time
In the ABAC system, the attributes of both users and
a resource are embedded in a digital signature, which
is then checked to ensure that the attributes are correct
and have not been altered in any way. Verifying a dig-
ital signature is a computationally expensive process.
The more attributes used in a policy, the more signa-
tures must be verified, which drives up the computa-
tion cost. The computation cost is also affected by
the size of the digital signature and the complexity of
the algorithm being used. The computation cost will
be increased, for instance, if a larger key size is used
for the algorithm that generates digital signatures or a
more complex algorithm, such as RSA, is used. Using
a more efficient digital signature algorithm, such as
the ECC and HCC, which is more efficient than RSA,
is one approach to reducing the computation cost in
an ABAC system. Similarly, reducing the number of
characteristics used in the policies by only utilizing
the attributes required to determine who has access to
the resources.
The cost of pairing-based point multiplication
(P
mp
), bilinear pairing (B
p
), exponentiation (E
xp
),
and Hyperelliptic Curve Divisor Multiplication (H
dm
)
are essential parameters in evaluating the perfor-
mance and efficiency of pairing-based cryptography
methods. The authors in (Khan et al., 2020) and (Ul-
lah et al., 2021), report that the cost of one pairing-
based point multiplication is 4.31 milliseconds, the
cost of a single bilinear pairing is approximately
14.90 milliseconds, the cost of single exponentiation
is approximately 1.25 milliseconds, and the cost of a
single HCDM is about 0.48 milliseconds. These val-
ues are used to measure the performance of the cryp-
tographic algorithm and can be used to compare dif-
ferent methods.
In Table 1, the performance of the designed
scheme is compared to previously related access con-
trol schemes, such as (Wang et al., 2018), (Liu et al.,
2021), (Zhang et al., 2022), and (Zhu et al., 2018a)
in terms of the computation time required in millisec-
onds. Table 1 suggests that our scheme is more ef-
ficient than the previously related schemes regarding
the time required for cryptographic operations. The
designed scheme is evaluated for its performance by
comparing the cost of mathematical operations used
with the previously related schemes. The perfor-
mance is measured in terms of time required for the
cryptographic operations, and based on the compari-
son results, the designed scheme is more efficient than
the previous ones as shown in Figure 3.
Figure 3: Computation time analysis.
Concluding Remarks: We evaluated the performance
of various ABAC schemes for IoT using blockchain
technology in terms of computation time. The ta-
ble above summarizes the results of the evaluation,
which show that the computation time for the existing
schemes evaluated ranges from 65.69 milliseconds to
75.75 milliseconds. In contrast, the computation time
for our proposed scheme is significantly lower at 1.44
milliseconds. This indicates that the proposed scheme
is more efficient in computation time as it takes less
time to perform cryptographic operations. This makes
it a more suitable option for real-world IoT applica-
tions requiring low computation time and real-time
processing, such as applications with many users or
real-time data processing.
8.2 Communication Overhead
In the context of ABAC, the term ”communication
overhead” refers to the amount of data that needs to
be exchanged between the client, the attribute author-
ity, and the access control decision point to arrive at
an access control decision. This must take place be-
SECRYPT 2023 - 20th International Conference on Security and Cryptography
536

Table 1: Computation time analysis.
Ref. No Costly cryptographic operations Computation time in milliseconds (ms)
(Wang et al., 2018) 3E
xp
+ 4P
mp
+ 3B
p
65.69 ms
(Liu et al., 2021) 3E
xp
+ 1P
mp
+ 3B
p
52.76 ms
(Zhang et al., 2022) 6E
xp
+ 4B
p
67.1 ms
(Zhu et al., 2018a) 1E
xp
+ 5B
p
75.75 ms
Proposed 3H
dm
1.44 ms
fore an access control decision can be made. The size
of the messages exchanged can be measured to deter-
mine this, including the size of the attribute query, the
size of the attribute response, and the size of the ac-
cess control decision. Another method for determin-
ing the extent of the communication burden caused
by ABAC is to count the number of messages passed
back and forth between the various entities. Count-
ing the number of attribute queries, the number of at-
tribute responses, and the number of access control
decisions made is one way to determine this (Hussain
et al., 2020).
In this comparison, the designed approach is be-
ing evaluated against some of the previously sug-
gested schemes regarding communication overhead.
The proposed scheme is compared with (Wang et al.,
2018), (Liu et al., 2021), (Zhang et al., 2022), and
(Zhu et al., 2018a). The analysis assumes certain
variables such as bilinear pairing (G), hyperelliptic
curve cryptosystem (q), and message (m), as shown
in Table 1. The results, as shown in Figure 3 and Ta-
ble 2, indicate that the designed scheme substantially
improves communication overhead compared to the
previous schemes. The length of the elements in dif-
ferent cryptographic schemes are assumed to be spe-
cific values: bilinear pairing (G) is assumed to have
a length of 1024 bits, message (m) is considered to
have a length of 512 bits, and Hyperelliptic curve (q)
is considered to have a length of 80 bits.
The communication overhead for (Wang et al.,
2018) scheme is calculated to be 4|G| + |m|, and
for (Liu et al., 2021) scheme it is calculated to be
3|G| + |m|, for (Zhang et al., 2022) scheme it is cal-
culated to be 4|G| + |m|, Zhu et a. (Zhu et al., 2018a)
scheme is calculated to be 3|G| + |m| and for the pro-
posed is calculated to be 3|q| + |m|. The results, as
presented in Figure 4 and Table 2, indicate that the
designed scheme significantly improved communica-
tion overhead compared to the previous schemes. We
suggest that the proposed scheme is a better option
than the previous ones based on the comparison re-
garding communication overhead and cost reduction.
Concluding Remarks: We have evaluated the commu-
nication overhead of several ABAC schemes for IoT
using blockchain technology. The results of our anal-
ysis are summarized in the table above, which shows
Figure 4: Communication overhead in bits.
the communication overhead in bits for four exist-
ing schemes and our proposed scheme. The existing
schemes considered in this research are (Wang et al.,
2018), (Liu et al., 2021), (Zhang et al., 2022), and
(Zhu et al., 2018a). The communication overhead of
these schemes ranges from 4608 bits to 3584 bits. It is
worth noting that two of the existing schemes, (Wang
et al., 2018) and (Zhang et al., 2022), have the same
communication overhead of 4608 bits.
On the other hand, our proposed scheme has a
communication overhead of 752 bits, which is signifi-
cantly lower than the existing schemes. This indicates
that our proposed scheme is more efficient in terms of
communication overhead.
9 CONCLUSION AND FUTURE
WORK
The Internet of Things (IoT) revolution has cre-
ated new security challenges, particularly managing
access control for connected devices. Traditional
methods may not be effective in addressing these
challenges. This paper proposes the use of IoT-
enabled attribute-based access control (ABAC) using
blockchain technology as a solution to this problem.
ABAC allows access to be granted or denied based on
the attributes of the user or device requesting access
rather than relying on a central authority. This allows
for more flexible and dynamic access control policies
that can adapt to changing situations and minimize
the risk of unauthorized access. Blockchain technol-
ogy provides a secure and transparent way to manage
access control information for IoT devices. The au-
thors propose a new lightweight ABAC scheme for
A Lightweight Access Control Scheme with Attribute Policy for Blockchain-Enabled Internet of Things
537
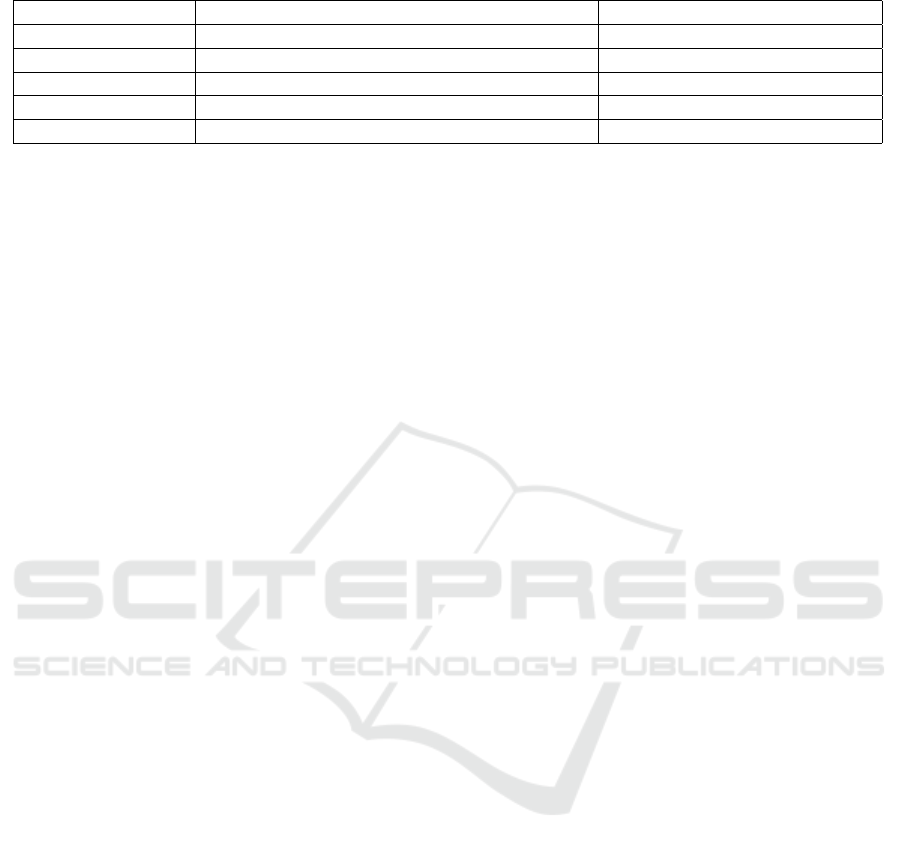
Table 2: Communication overhead analysis.
Ref. No Costly operations for Communication overhead Communication overhead in bits
(Wang et al., 2018) 4|G| + |m| 4608 bits
(Liu et al., 2021) 3|G| + |m| 3584 bits
(Zhang et al., 2022) 4|G| + |m| 4608 bits
(Zhu et al., 2018a) 3|G| + |m| 3584 bits
Proposed 3|q| + |m| 752 bits
IoT using blockchain technology and conduct a se-
curity analysis to evaluate and compare the proposed
scheme to existing schemes. The results indicate that
the proposed scheme has the advantage of using mini-
mal computation time and communication bandwidth
compared to previous solutions. The authors suggest
that the ABAC scheme using blockchain combined
with a lightweight Hyperelliptic Curve Cryptosystem
(HCC) is well suited for secure deployment in IoT.
In the future, we will address the privacy concerns
that are raised by the practice of storing access histo-
ries on a blockchain. We will look into a more ad-
vanced privacy-preserving technique that offers the
benefits of blockchain technology without compro-
mising user privacy.
REFERENCES
Alansari, S., Paci, F., and Sassone, V. (2017). A distributed
access control system for cloud federations. pages
2131–2136. IEEE.
Alniamy, A. and Taylor, B. D. (2020). Attribute-based
access control of data sharing based on hyperledger
blockchain. pages 135–139.
Arasi, V. E., Gandhi, K. I., and Kulothungan, K. (2022).
Auditable attribute-based data access control using
blockchain in cloud storage. Journal of Supercomput-
ing, 2022(1):1–27.
Ding, S., Cao, J., Li, C., Fan, K., and Li, H. (2019).
Novel attribute-based access control scheme using
blockchain for iot. IEEE Access, 7(1):38431–38441.
Dolev, D. and Yao, A. (1983). On the security of public key
protocols. IEEE Trans. Inf. theory, 29(2):198–208.
Dukkipati, C., Zhang, Y., and Cheng, L. C. (2018). Decen-
tralized, blockchain based access control framework
for the heterogeneous internet of things. pages 61–69.
ACM.
Ghorbel, A., Ghorbel, M., and Jmaiel, M. (2021). Account-
able privacy preserving attribute-based access control
for cloud services enforced using blockchain. Interna-
tional Journal of Information Security, 2021(1):1–22.
Hu, Vincent, C., Kuhn, D. R., Ferraiolo, D. F., and Voa,
J. (2015). Attribute-based access control. Computer,
48(2):85–88.
Hussain, S., Ullah, I., Khattak, H., Adnan, M., Kumari, S.,
Ullah, S. S., Khan, M. A., and Khattak, S. J. (2020).
A lightweight and formally secure certificate based
signcryption with proxy re-encryption (cbsre) for in-
ternet of things enabled smart grid. IEEE Access,
8(1):93230–93248.
Hussain, S., Ullah, I., Khattak, H., Khan, M. A., Chen, C.,
and Kumari, S. (2021). A lightweight and provable
secure identity-based generalized proxy signcryption
(ibgps) scheme for industrial internet of things (iiot).
Journal of Information Security and Applications,
58:102625.
Jiang, X. (2021). Decentralized, blockchain based access
control framework for the heterogeneous internet of
things. pages 21–23. J. Phys Conf. Ser. 1955.
Khan, M., Rehman, S., Uddin, M., Nisar, S., and Noor,
F. (2020). n online-offline certificateless signature
scheme for internet of health things. Journal of
Healthcare Engineering, 2020(1):1–10.
Kumar, S., Tiwari, P., and Zymbler, M. (2019). Internet
of things is a revolutionary approach for future tech-
nology enhancement: a review. Journal of Big data,
6(1):1–21.
Liu, X., Zheng, Y., and Li, X. Z. (2021). A re-
vocable attribute-based access control system using
blockchain. In Journal of Physics: Conference Series,
1971(1):012058.
Lu, X., Fu, S., Jiang, C., and Lio, P. (2021). A fine-grained
iot data access control scheme combining attribute-
based encryption and blockchain. Security and Com-
munication Networks, 2021:1–13.
Omolara, Esther, A., Alabdulatif, A., Abiodun, I., Alaw-
ida, M., and Arshad, H. (2022). The internet of
things security: A survey encompassing unexplored
areas and new insights. Computers and Security,
112(1):102494.
Rouhani, S., Belchior, R., and Cruz, R. S. (2021). Dis-
tributed attribute-based access control system us-
ing permissioned blockchain. World Wide Web,
24(1):617–644.
Sandhu, S. R. and Samarati, P. (1994). Access control: prin-
ciple and practice. IEEE communications magazine,
32(9):40–48.
Sinha, Bahadur, B., and Dhanalakshmi, R. (2022). Recent
advancements and challenges of internet of things in
smart agriculture: A survey. Future Generation Com-
puter Systems, 126(1):169–184.
Swessi, D. and Idoudi, H. (2022). A survey on internet-
of-things security: threats and emerging coun-
termeasures. Wireless Personal Communications,
124(2):1557–1592.
Ullah, I., Khan, M. A., F.Khan, M.A.Jan, R.Srinivasan,
S.Mastorakis, S.Hussain, and Khattak, H. (2021). An
efficient and secure multimessage and multireceiver
SECRYPT 2023 - 20th International Conference on Security and Cryptography
538

signcryption scheme for edge-enabled internet of ve-
hicles. IEEE Internet of Things Journal, 29(9):2688–
2697.
Ullah, S. S., Ullah, I., Khattak, H., Khan, M., Adnan, M.,
Hussain, S., Amin, N., and Khattak, M. (2020). A
lightweight identity-based signature scheme for mit-
igation of content poisoning attack in named data
networking with internet of things. IEEE Access,
8(1):98910–98928.
Wang, L., Wijesekera, D., and Jajodia, S. (2004). A logic-
based framework for attribute based access control.
pages 45–55. ACM.
Wang, S., Zhang, Y., and Zhang, Y. (2018). Blockchain-
based framework for data sharing with fine-grained
access control in decentralized storage systems. IEEE
Access, 6(1):38437–38450.
Yang, Q., Zhang, M., Zhou, Y., Xia, T. W. Z., and Yang, B.
(2021). Non-interactive attribute-based access control
scheme by blockchain for iot. Electronics, 15:1–11.
Zaidi, S. Y. A., Shah, M. A., Khattak, H. A., Maple, C.,
Rauf, H. T., El-Sherbeeny, A. M., and El-Meligy,
M. A. (2021). An attribute-based access control for
iot using blockchain and smart contracts. Sustainabil-
ity, 13(21):10556.
Zhang, Y., Wei, X., Cao, J., Ning, J., Ying, Z., and
Zheng, D. (2022). Blockchain-enabled decentralized
attribute-based access control with policy hiding for
smart healthcare. Journal of King Saud University -
Computer and Information Sciences.
Zhu, Y., Qin, Y., Gan, G., Shuai, Y., and Chu, W. C. C.
(2018a). Digital asset management with distributed
permission over blockchain and attribute-based access
control. pages 535–544. IEEE.
Zhu, Y., Qin, Y., Zhou, Z., Song, X., Liu, G., and Chu, W. C.
(2018b). Digital asset management with distributed
permission over blockchain and attribute-based access
control. pages 193–200. IEEE.
A Lightweight Access Control Scheme with Attribute Policy for Blockchain-Enabled Internet of Things
539
