
Detection of Malicious Applications using YOLO V3-Spatial Pyramid
Pooling over Optical Character Recognition for
Computing Access Time
Gowtham V. and Devi T.
Saveetha University, India
Keywords: Android Application, Deep Learning, Novel You Only Look Once V3-Spatial Pyramid Pooling, Internet
Access, National Security, Optical Character Recognition Algorithm, Text Detection, Vulnerability
Detection.
Abstract: The goal of research is to use the Novel YOLO V3 SPP for detecting malicious applications while comparing
it with the OCR technique for computation of access time. Materials and Methods: The Innovative YOLO V3
SPP algorithm is used to determine access time using a sample size of (N=25), a total sample size of (N=50),
and G power is computed to be 80%. In terms of data exploitation prediction, the Novel YOLO V3 SPP has
an access time that is slower (83.36ms) than the OCR algorithm's (79.64ms). According to the results, there
is no statistically significant difference between the Novel YOLO V3 SPP Algorithm and the OCR Algorithm
with p=0.218 (independent sample t-test p<0.05). In comparison to OCR's access time of 79.64ms, the novel
YOLO V3 SPP method predicts vulnerabilities in native programmes with a longer access time of 83.36ms.
1 INTRODUCTION
Deep learning is quickly developing their standards in
text and object recognition all over the world (Zhang
et al. 2022). It's basically working on neural
networking and it's becoming easy to detect all the
solutions to this project. Deep learning basically
works under machine learning in all over internet
access. It is used in most significant manner to find
text in the surrounding images (Garcia-Argibay et al.
2022). It provides a basic ideology of finding
perspective in images. Android applications are
plagued by data exploitation everywhere in internet
access. The model also needed to be in terms of
accuracy (Bergler et al. 2022). As a result, it is used
to collect data more rapidly on a significant scale. To
eradicate data exploitation in native applications,
Data leakage can be detected using deep learning, and
it can be avoided using a variety of techniques.(El-
Amir and Hamdy 2020)(James et al. 2017)
(Sivakumar et al 2022). Speed and security will be
through deep learning in android applications. In this
way, the proposed research aim will be achieved
(PirahanSiah 2019). Data cleansing, computer vision,
customer relationship management, fraud detection,
speech detection, and many other uses are all possible
with deep learning.(Kim 2017).
This proposed work includes numerous research
papers are published in IEEE, 5000 articles from
Springer, 2400 articles from Science Director, and
4090 publications from Google Scholar on text
detection and prediction of data leakage and it have
more citations than 50 times (Amaratunga 2021). The
best cited article is one where the OCR model is a
powerful tool for detecting text in natural
environments and has received significant attention in
the research community, with 77 citations (Ketkar
and Moolayil 2021). One of the key advantages of
this model is its ability to accurately identify text at
various positions and scales, providing insight into
the importance of features for effective text detection.
Overall, the OCR model has proven to be a valuable
resource for researchers studying text detection in
natural situations. The use of deep learning for text
detection in natural environments has significantly
Novel the capabilities of computer processing
applications. This research has paved the way for a
new era of deep learning and has reshaped the way
we approach text detection in natural scenes. Overall,
the advancements in this field have significantly the
effectiveness of text detection using deep learning
techniques (Kelleher 2019). This research focuses on
extracting textual information from natural scenes,
with a particular focus on android applications such
514
T., D. and V., G.
Detection of Malicious Applications Using YOLO V3-Spatial Pyramid Pooling over Optical Character Recognition for Computing Access Time.
DOI: 10.5220/0012571800003739
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 1st International Conference on Artificial Intelligence for Internet of Things: Accelerating Innovation in Industry and Consumer Electronics (AI4IoT 2023), pages 514-519
ISBN: 978-989-758-661-3
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.

as license plate recognition and navigation. The
findings of this research have been highly influential,
as evidenced by the 26 citations it has received
(Kariya, Fujishima, and Zhang 2019). Overall, the
goal of this research is to improve the ability to
identify and extract relevant text from natural
environments, with the potential to facilitate a range
of practical applications and to provide national
security in internet access (Brum et al. 2023).
Existing systems suffer from certain limitations
such as lesser response time for accessing the data.
(Patterson and Gibson 2017). Depending on the
specific font or script used for the letter, the resulting
matrix is labeled as representing a specific character.
In order to overcome these pitfalls, the proposed
algorithm Novel YOLO V3 SPP is used as an
alternative to OCR algorithm which is basically to
improve the access time. OCR is slower in predicting
the textual materials in images. Also, it does not
provide accurate prediction in small text values
throughout the model (Mueller and Massaron 2019).
It needs vast space to process the model in every
aspect. The quality of image gets lost in processing
the model for national security (Arif Wani et al. 2019)
(G. Ramkuamr et al. 2021). It will not recognize the
printed text only not as hand written text. The goal of
research is to improve the access time using Novel
YOLO V3 SPP comparison with OCR algorithm for
predicting the vulnerability detection and to provide
national security.
2 MATERIALS AND METHODS
The study was carried out in the data analysis lab at
Saveetha School of Engineering, Saveetha Institute of
Medical and Technological Sciences, which has a
high configuration system for carrying out studies and
obtaining results. Two groups were taken into
account for the study, with a sample size of 25.
(Nundy, Kakar, and Bhutta 2021). 80% of the G-
power value, 0.05 alpha, 0.2 beta, and a 95%
confidence range are used to calculate the result
(Kane, Phar, and BCPS n.d.).
CVE (Common Vulnerability and Exposures), a
dataset used in this suggested study, analyses
programmes using predefined threats and
vulnerabilities to generate the vulnerability ratings.
You must use Kaggle to download CVE (Mell 2002).
The dataset used in this analysis helps identify the
vulnerability status. The data set is then subjected to
the methodology devised in this study, and the
outcomes are contrasted with the comparison
algorithm (Brum et al. 2023). Based on the specified
work, these data are logged using real-time apps and
separated into several columns. CVE uses the internet
to enhance national security and is based on a list of
applications that can corrupt data.
In this research, the implementation is carried out
using Jupyter notebook, an open-source web
application that enables the creation and sharing of
documents, including machine learning methods. The
code for this research is saved in the Jupyter
directory, and the system uses darknet-53 to analyze
images in natural scenes. Jupyter notebook allows for
the easy execution and organization of code, making
it a useful tool for researchers and developers. Jupyter
notebook is an open-source web application.
Novel You Only Look Once Algorithm V3 Spatial
Pyramid Pooling Algorithm
Novel YOLO V3 SPP (You Only Look Once V3
Spatial Pyramid Pooling) algorithm is the sample
preparation group 1 and the proposed algorithm for
this proposed work. Novel YOLO v3 SPP is a real-
time object detection algorithm that uses
convolutional neural networks (CNNs) to identify
objects in video. In version 3, the algorithm was
longer to increase both speed and accuracy and to
provide national security. It is designed to detect large
sections of objects at a time, using comparison
methods to quickly identify and classify data as it is
received. The proposed research involves inputting an
image and processing it through CNNs, including 24
convolution and max-pooling layers, followed by
fully connected layers. To reduce the number of
layers, convolution is used followed by layer
convolution. The final layer of Novel YOLO V3 SPP
predicts an output by generating from the fully
connected layers and reshaping them to the size of the
input image in usage of internet access. Overall, the
goal of this research is to improve the speed and
accuracy of object detection, while maintaining a
high level of efficiency to increase national security
in internet access. Table 1 procedure refers to the
procedure of the Novel YOLO V3 SPP algorithm.
Optical Character Recognition Algorithm
Optical character recognition (OCR) is sample
preparation group 2 and is a process and technology
that converts text and images containing text into a
digital format that can be read by a computer. OCR
algorithms work by dividing an image of a text
character into smaller sections and analyzing the
presence or absence of pixels in each section. The
limitations of OCR is that the quality of the image can
be lost and not worth the small amount of text. Also,
it needs lots of space to store an image and even to
process it. Based on the specific font or script used,
Detection of Malicious Applications Using YOLO V3-Spatial Pyramid Pooling over Optical Character Recognition for Computing Access
Time
515
the resulting matrix is labeled as representing a
particular character. This allows OCR to recognize
and transcribe text from images, making it a useful
tool for various applications. OCR also enables the
conversion of large quantities of paper documents
into digital files, improving the efficiency of text
storage, processing, and searching. In summary, OCR
is a valuable tool for digitizing and organizing text-
based information, making it more accessible and
easier to use. The network uses a CNN
(Convolutional Neural Network) approach to classify
the results into two categories, and it is able to
generalize this binary classification effectively. The
future work is to prove that to provide longer access
time, Safe and secure usage will be provided through
this. Table 2 procedure refers to the procedure of
OCR algorithm.
Statistical Analysis
The statistical programme used to calculate the
standard derivation, mean and standard error means,
mean difference, sig, and F value uses IBM SPSS of
version 26.0. The number of installations discovered
in real time is an independent variable, and
application access time is a dependent variable. An
independent T-test analysis is carried out in this
investigation.(Brum et al. 2023).
3 RESULTS
Table 1: Novel YOLO V3 SPP procedure for a novel (You
Only Look Once Version3 spatial pyramid pooling). This
Novel YOLO V3 SPP technique makes it possible to
predict the used data outside of the application quickly. It
also demonstrates the access value much better.
Input: CVE (Common Vulnerability and Exposures) dataset
Output: Longer access time
Step 1: First input is a captured natural scene image.
Step 2: It undergoes through the convolutional layers, it uses 1*1 laye
r
which predicts the size of the image.
Step 3: Observing the image and calculating the weights in the image.
Step 4: It has three anchors which are called anchors which predicts
the log space.
Step 5: The outcome is computed using access time and picture
detection accuracy.
The Novel YOLO V3 SPP (You Only Look Once)
procedure is shown in Table 1. And information is
collected from the dataset. The novel YOLO V3 SPP
operates by recognising each image in the
surrounding natural scene. These parameters are
specified for additional model testing. must make an
effort to improve the access time. The OCR procedure
is shown in Table 2. The Novel YOLO V3 SPP and
OCR method is compared using the dataset. OCR
predicts less accurately than Novel YOLO V3 SPP. It
is therefore tested using the methods for faster access
time. The raw data table of access time in Table 3
includes both the Novel YOLO V3 SPP and OCR.
Table 2: Procedure for OCR (Optical Character
Recognition). The OCR algorithm takes the dataset of
vulnerability in apps and helps to predict it by using this
algorithm.
Input: CVE (Common Vulnerability Exposure) Dataset
Output: Longer access time
Step 1: Captured image from the natural scene is further divided into
scales.
Step 2: Observes the output and predicts the weight.
Step 3: The image undergoes the neural networks techniques.
Step 4: Dividing images in no of scales.
Step 5: Finally, predicting the output by score generation.
Table 3: Table of raw data for access times Novel YOLO
V3 SPP (You Only Look Once V3-Spatial Pyramid
Pooling) and OCR (Optical Character Recognition).
S.NO
Novel YOLO V3 SPP (You Only
Look Once V3-Spatial Pyramid
Pooling) Access time (ms)
OCR
(Optical Character
Recognition)
(
Access time
)
(
ms
)
1 62 98
2 64 96
3 66 94
4 68 92
5 70 90
6 72 88
7 74 86
8 76 85
9 78 84
10 80 83
11 82 82
12 84 81
13 86 80
14 88 79
15 89 78
16 90 77
17 91 76
18 92 75
19 93 74
20 94 72
21 95 71
22 96 70
23 97 68
24 98 66
25 99 62
AI4IoT 2023 - First International Conference on Artificial Intelligence for Internet of things (AI4IOT): Accelerating Innovation in Industry
and Consumer Electronics
516
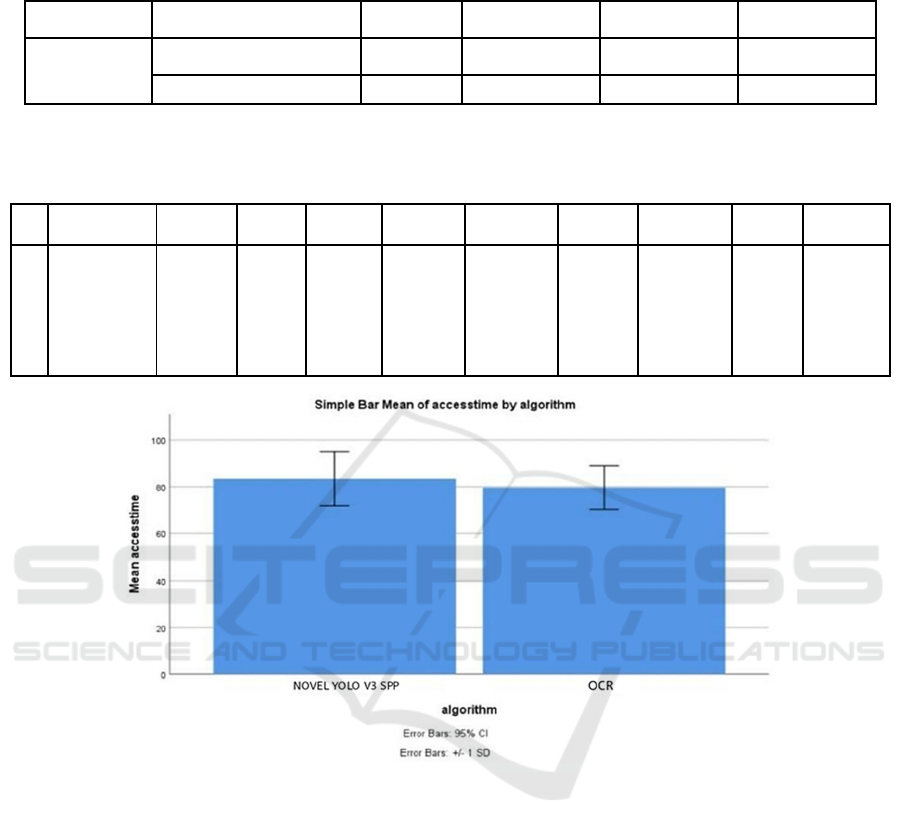
Table 4: Group statistics for contrasting Novel YOLO V3 SPP and OCR Algorithm using independent samples. The mean
access time in Novel YOLO V3 SPP is 83.36 milliseconds, compared to 79.64 milliseconds in OCR.
Algorithm N Mean Std. Deviation Std. Error Mean
Access time
Novel YOLO V3 SPP 25 83.36 11.626 2.325
OCR 25 79.64 9.327 1.865
Table 5: T-Test for Comparing Independent Statistical Samples of Novel YOLO V3 SPP with OCR Algorithm, 95%
confidence interval. It shows that there is no statistical significance difference between the Novel YOLO V3 SPP Algorithm
and OCR Algorithm with p=0.218 (p>0.05).
F Sig t df Sig(2-tailed)
Mean
Difference
Std. Error
Difference
Lower Upper
Access time
Equal Variances
assumed
Equal variances
not assumed
2.743 .104
1.248
1.248
48
45.845
.218
.218
3.720
3.720
2.981
2.981
-
2.274
-
2.281
9.714
9.721
Figure 1: Comparison between Novel YOLO V3 SPP and OCR algorithm based on mean access time. The access time of
Novel YOLO V3 SPP is significantly better than OCR algorithm. X-axis: Novel YOLO V3 SPP Vs OCR algorithm Y-axis:
Mean access time. Error Bar +/- 1 SD.
The values for the Novel YOLO V3 SPP (You
Only Look Once) and the OCR Algorithm are shown
in Table 4 as N (25), Mean (83.36), Standard
Deviation (11.626), and Std. Error Mean values
(2.325) respectively. The T-Test results for
statistically independent samples are shown in Table
5. The Novel YOLO V3 SPP and OCR algorithm has
a mean difference of 3.720, a standard error of 2.981,
and a 95% confidence interval. According to the
results, there is no statistically significant difference
between the Novel YOLO V3 SPP Algorithm and the
OCR Algorithm with p=0.218 (p>0.05). The T-Test
results for the Novel YOLO V3 SPP and OCR
algorithm are shown in a bar graph in Figure 1. It
displays the Novel YOLO V3 SPP and OCR
algorithm's access time. The bar graph gain and
values compute the access time and use it.
4 DISCUSSION
The YOLO V3 SPP access time has a significance
value of 83.36, which is higher than the OCR rate.
The OCR significance value of 73.64 is more than the
significance of the YOLO V3 SPP method in terms of
statistical outcome values. More than (p>0.05) is the
no statistical significance value of 0.103.
The basic principle behind OCR learning is to
combine the predictions of multiple base learners into
Detection of Malicious Applications Using YOLO V3-Spatial Pyramid Pooling over Optical Character Recognition for Computing Access
Time
517

a single result that is expected to outperform any
individual member of the group, along with an
unrelated error on the target data sets (Tejas et al.
2016). Group learning is based on using different
models to solve problems related to accuracy and
access time (Yu 2021). The OCR algorithm is
particularly effective when there is a significant
difference between the models in terms of access time
(Kariya, Fujishima, and Zhang 2019). To avoid errors
due to multiple images being captured at once, the
algorithm removes unwanted data outside the
bounding boxes (Daneshfar, Fathy, and Alaqeband
2018). This also helps to select and predict specific
objects or parts with an accuracy of 86% (Bao et al.
2022). One of the key advantages of OCR is that it is
designed to meet all assumptions consistent with the
training data, with an access time of 85% (Bao et al.
2022). Overall, OCR is a powerful tool for object
detection and prediction, with a range of benefits and
android applications (Xu, Xue, and Zhao 2022).
Factors affecting the research work are
identifying and predicting data leakage in android
applications using various algorithms, including the
OCR algorithm as an object detection tool. The
limitations of OCR is that the quality of the image can
be lost and not worth a small amount of text. Also, it
needs lots of space to store an image and even to
process it. The version 3 of the OCR algorithm can be
used to extract textual data from images, dividing the
data into smaller sections to facilitate quick
processing in android applications. The algorithm
generates a grid for each image in the task and is
useful for predicting text or objects in the virtual
world. The OCR algorithm has many applications,
including traffic control and license plate
identification, as well as speed detection. However, it
has limitations in terms of access time and accuracy,
which may impact future work. Overall, the aim of
this research is to improve the security and usability
of android applications, while providing accurate and
efficient text detection in images. And provide longer
access time. The future work is to prove that to
provide longer access time, Safe and secure usage
will be provided through this in android applications.
5 CONCLUSION
Novel YOLO V3 SPP and the OCR algorithms have
predicted real-time data leakage applications for
Android using various trained detection datasets.
When comparing the two algorithms, Novel YOLO
V3 SPP has a higher access rate than the OCR
algorithm. The Novel YOLO V3 SPP's performance
and sensitivity are superior to the OCR's (83.36ms)
(73.64ms). In comparison to the OCR method, data
loss is reduced in the Novel YOLO V3 SPP.
REFERENCES
Amaratunga, Thimira. (2021). “What Is Deep Learning?”
Deep Learning on Windows.
https://doi.org/10.1007/978-1-4842-6431-7_1.
Arif Wani, M., Farooq Ahmad Bhat, Saduf Afzal, and Asif
Iqbal Khan. 2019. Advances in Deep Learning.
Springer.
Bao, Wuzhida, Cihui Yang, Shiping Wen, Mengjie Zeng,
Jianyong Guo, Jingting Zhong, and Xingmiao Xu.
(2022). “A Novel Adaptive Deskewing Algorithm for
Document Images.” Sensors 22 (20).
https://doi.org/10.3390/s22207944.
Bergler, Christian, Simeon Q. Smeele, Stephen A. Tyndel,
Alexander Barnhill, Sara T. Ortiz, Ammie K. Kalan,
Rachael Xi Cheng, et al. (2022). “ANIMAL-SPOT
Enables Animal-Independent Signal Detection and
Classification Using Deep Learning.” Scientific
Reports 12 (1): 21966.
Brum, Mauro, Luciano Pereira, Rafael Vasconcelos
Ribeiro, Steven Jansen, Paulo R. L. Bittencourt, Rafael
S. Oliveira, and Scott R. Saleska. (2023). “Reconciling
Discrepancies in Measurements of Vulnerability to
Xylem Embolism with the Pneumatic Method: A
Comment on Chen et Al. (2021) ‘Quantifying
Vulnerability to Embolism in Tropical Trees and Lianas
Using Five Methods: Can Discrepancies Be Explained
by Xylem Structural Traits?’: A Comment on Chen et
Al. (2021) ‘Quantifying Vulnerability to Embolism in
Tropical Trees and Lianas Using Five Methods: Can
Discrepancies Be Explained by Xylem Structural
Traits?’” The New Phytologist 237 (2): 374–83.
Daneshfar, F., W. Fathy, and B. Alaqeband. (2018). “A
Metaheuristic Algorithm for OCR Baseline Detection
of Arabic Languages.” Computer Vision.
https://doi.org/10.4018/978-1-5225-5204-8.ch027.
El-Amir, Hisham, and Mahmoud Hamdy. (2020). “Deep
Learning Fundamentals.” Deep Learning Pipeline.
https://doi.org/10.1007/978-1-4842-5349-6_9.
Garcia-Argibay, Miguel, Yanli Zhang-James, Samuele
Cortese, Paul Lichtenstein, Henrik Larsson, and
Stephen V. Faraone. (2022). “Predicting Childhood and
Adolescent Attention-Deficit/hyperactivity Disorder
Onset: A Nationwide Deep Learning Approach.”
Molecular Psychiatry, December.
https://doi.org/10.1038/s41380-022-01918-8.
G. Ramkumar, R. Thandaiah Prabu, Ngangbam Phalguni
Singh, U. Maheswaran, Experimental analysis of brain
tumor detection system using Machine learning
approach, Materials Today: Proceedings, 2021, ISSN
2214-7853,
https://doi.org/10.1016/j.matpr.2021.01.246.
James, J., Lakshmi, S. V., & Pandian, P. K. (2017). A
preliminary investigation on the geotechnical properties
AI4IoT 2023 - First International Conference on Artificial Intelligence for Internet of things (AI4IOT): Accelerating Innovation in Industry
and Consumer Electronics
518

of blended solid wastes as synthetic fill material.
International Journal of Technology, 8(3), 466-476.
Kane, Sean P., Phar, and BCPS. n.d. “Sample Size
Calculator.” Accessed April 18, 2023.
https://clincalc.com/stats/samplesize.aspx.
Kariya, Ken, Takahiro Fujishima, and Lifeng Zhang.
(2019). “Development of OCR Mobile Application
Including Miss-Recognized Proofreading System
Using Database Search Algorithm.” Proceedings of The
7th International Conference on Intelligent Systems
and Image Processing 2019. https://doi.org/1
0.12792/icisip2019.034.
Kelleher, John D. (2019). Deep Learning. MIT Press.
Ketkar, Nikhil, and Jojo Moolayil. (2021). “Introduction to
Machine Learning and Deep Learning.” Deep Learning
with Python. https://doi.org/10.1007/978-1-4842-5364-
9_1.
Kim, Phil. 2017. “Deep Learning.” MATLAB Deep Learning.
https://doi.org/10.1007/978-1-4842-2845-6_5.
Mell, Peter. 2002. Use of the Common Vulnerabilities and
Exposures (CVE) Vulnerability Naming Scheme:
Recommendations of the National Institute of Standards
and Technology.
Mueller, John Paul, and Luca Massaron. 2019. Deep
Learning For Dummies. John Wiley & Sons.
Patterson, Josh, and Adam Gibson. (2017). Deep Learning:
A Practitioner’s Approach. “O’Reilly Media, Inc.”
PirahanSiah, Farshid. (2019). “Computer Vision, Deep
Learning, Deep Reinforcement Learning.”
https://doi.org/10.14293/s2199-1006.1.sor-
uncat.clzwyuz.v1.
Sivakumar, V. L., Nallanathel, M., Ramalakshmi, M., &
Golla, V. (2022). Optimal route selection for the
transmission of natural gas through pipelines in
Tiruchengode Taluk using GIS–a preliminary study.
Materials Today: Proceedings, 50, 576-581.
Tejas, Bhonsale, Department Of Computer Engineering, A.
I. S. S. M. S. College of Engineering, Pune,
Maharashtra, and India. (2016). “Number Plate
Recognition and Document Verification Using Feature
Extraction OCR Algorithm.” International Journal Of
Engineering and Computer Science. https://doi.org/
10.18535/ijecs/v5i11.84.
Xu, Xing, Zhenpeng Xue, and Yun Zhao. (2022).
“Research on an Algorithm of Express Parcel Sorting
Based on Deeper Learning and Multi-Information
Recognition.” Sensors 22 (17).
https://doi.org/10.3390/s22176705.
Yu, Ling. (2021). “State-of-the-Art OCR Algorithm for
Translation Guiding: An Online-Offline Combinational
Model.” 2021 Third International Conference on
Inventive Research in Computing Applications
(ICIRCA). https://doi.org/10.1109/icirca51532.2021
.9544563.
Zhang, Lisheng, Wentao Wang, Hanqing Yu, Zheng Zhang,
Xianbin Yang, Fengwei Liang, Shen Li, Shichun Yang,
and Xinhua Liu. (2022). “Remaining Useful Life and
State of Health Prediction for Lithium Batteries Based
on Differential Thermal Voltammetry and a Deep
Learning Model.” iScience 25 (12): 105638.
Detection of Malicious Applications Using YOLO V3-Spatial Pyramid Pooling over Optical Character Recognition for Computing Access
Time
519
