
Nymble: Blocking Misbehaving Client in Anonymizing Networks
M. Marina and L. Gnanaprasanambikai
*
Department of Computer Science, Karpagam Academy of Higher Education (Deemed to be University), Coimbatore, India
Keywords: Anonymous Blacklisting, Anonymous Tracking, Privacy, Nymble, Pseudotracker.
Abstract: To get admission to both well-behaved and poorly-behaved clients. Our current blocking off system, which
allows servers to "blacklist" offending users, is used to address this issue. blockading customers except putting
their privacy at risk. Our device is hence unsure of exceptional servers' descriptions of inappropriate
behaviour. The procedure has been beneficial for defacing the profitable community with defensive manner.
Web page directors robotically depend blocking IP addresses is no longer practical if the abuser uses an
anonymizing network. IP-address blocking is used to deny access to disruptive users. The result is, directors
stop all recognized exit nodes of networks that anonymize users, rejecting nameless able to blacklist customers
for something the privacy of, and the basis for blacklisted customers is preserved. This manner used to end
the misusing approach in approved network.
1 INTRODUCTION
Networks that anonymize users, like Tor route traffic
thru unbiased nodes covering a client's IP address in
various administrative domains. Unfortunately, some
users have abused these networks; using false
identities, people have regularly vandalized well-
known websites like Wikipedia. Web site managers
can blacklist specific IP addresses of dangerous users,
so they blacklist the entire anonymizing network.
Such safeguards prevent criminal behaviour by
anonymizing networks at the expense of denying
logged-in users access. In other words, a few "bad
apples" can ruin the fun for everyone. There are
numerous solutions to this issue, each offering a
different level of accountability. Users enter onto
Web sites using pseudonyms in pseudonymous
credential systems, and if a user misbehaves, their
usernames and passwords are added to a blacklist.
Unfortunately, this strategy reduces the anonymity
provided by the anonymizing network and produces
pseudonymity for all users. The Nymble blocking
method is an innovative approach to online privacy
that provides users with the ability to authenticate
themselves anonymously while also allowing online
services to block malicious users. The Nymble
system addresses some of the limitations of other
privacy-enhancing technologies, such as Tor, by
*
Assistant Professor
providing online services with the ability to block
malicious users while preserving the anonymity of
legitimate users. This makes it a valuable tool for
online businesses and organizations that need to
protect their networks from malicious actors. The
system achieves this by using pseudonyms, also
known as nymble tokens, which are generated for
each user and cannot be linked to their real identity.
In this method, when a user wants to access an online
service, they first authenticate themselves with the
Nymble system, which generates a unique nymble
token for the user. The nymble token is a
cryptographic hash of the user's real identity and a
random nonce. The user can then present this token to
the online service to authenticate themselves
anonymously. If a user misbehaves, the online service
can send the user's nymble token to the Nymble
system to revoke the user's access to the service. The
Nymble system marks the token as revoked,
preventing the user from accessing the service in the
future. This provides online services with an effective
tool to block malicious users without compromising
the privacy of legitimate users. The Nymble blocking
method represents a significant step forward in online
privacy and security, providing users with enhanced
anonymity and online services with better tools to
prevent malicious activity.
252
Marina, M. and Gnanaprasanambikai, L.
Nymble: Blocking Misbehaving Client in Anonymizing Networks.
DOI: 10.5220/0012612900003739
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 1st International Conference on Artificial Intelligence for Internet of Things: Accelerating Innovation in Industry and Consumer Electronics (AI4IoT 2023), pages 252-258
ISBN: 978-989-758-661-3
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.

2 LITERATURE OF REVIEW
Extensive nymble, according to author Durga Prasad,
can both restrict and track unruly users while
maintaining their anonymity, which is a common
feature of anonymizing networks.
Authentication and privacy comparison
considered by Asha Ambhaikar, Nymble is a planned
and constructed complete a credential that can be
used to add an extra layer of accountability to any
publicly known anonymizing network. Servers can
block undesirable clients while yet maintaining client
privacy, proving that both objectives can be achieved
in a way that is practical, efficient, and sensitive to
each client's demands (Patro & Ambhaikar 2012).
Authors Aruna Kadam and Anand Joshi both
discuss the introduction of a desktop that instantly
recognises a post as an instance of inappropriate
behaviour, doing away with the necessity to contact
the pertinent current customers. Internet websites can
selectively block users of anonymizing networks with
the use of our programme. It compromises clients'
confidentiality while enabling internet firms to
blacklist them (Joshi et al 2012).
Dr. B. Venkata Ramana Reddy states that they
advise employing DTN to conduct a traditional
Behaviour study of nearby malware. We currently
look ahead, together with dogmatic filtering and
adaptive look ahead, to address two specific
challenges: "insufficient proof versus proof collection
risk" and "filtering false proof sequentially and
distributed." This allows us to extend Bayesian
filtering to DTNs (Sai & Reddy 2015).
According to author Sasikanth Venkata Krishna
Kolanu, it is advised to frequently use malware that is
DTN-based and nearby. This paper's current look-
ahead addresses dogmatic filtering, adaptive look-
ahead, and the issues of extending Bayesian filtering
to DTNs, such as insufficient proof vs. proof
collecting risk and filtering false proof sequentially
and dispersed. A difficult yet exciting project in the
future would be to increase the behavioural
characterization of Key (Sasikanth 2015).
Satyanarayana Rajubrough is the author. The
comparison of ERA-Interim reanalysis data was the
primary foundation for the findings in this
investigation. In the boreal, there is a higher
agreement between the PV-blockading index and the
algorithm provided with D12's usable resource.
Iciness and transitional seasons, whereas in the
summer zonal asymmetry appears, with the modified
AGH algorithms producing more blocking off
interest than the PV-index east of the Urals and in
particular across the Bering Strait (Tyrlis et al 2021).
Network influence blocking maximisation by
authors Ling Chin and 8 Network influence analysis
has piqued scholars' interest due to the ongoing
growth of numerous social and trade networks.
Numerous novel models and techniques for
maximising influence on networks have been
presented, many of which are based on various
influence propagation models. Influence blocking
maximisation, which is an extension and enlargement
of the conventional influence maximisation problem,
has become a research hotspot and has been
extensively used in various disciplines, including
physics, computer science, and epidemiology.
Various approaches to the influence blocking
maximisation challenge have been reported in recent
years (Chen et al 2022).
Saurabh Kumar Gupta is the author According to
research on mmWave networks, a big or close-by
item can block numerous communication lines,
which causes a spatial correlation in the likelihood
that a user will be blocked from communicating with
two or more base stations (BSs). This study describes
the blocking correlation and calculates how it affects
a mmWave cellular network's signal-to-interference-
plus-noise ratio (SINR) (Gupta et al 2022).
The author of this study, ApuKapadi, describes an
outline security protocol that makes use of trusted
hardware with few resources to enable anonymous
IP-address blocking in anonymizing networks like
Tor. By employing a network of Tor routers to
obscure the path from the client to the server and
conceal the client's IP address from the server, Tor
enables users to use Internet services privately
(Tsanget al 2006).
Author Peter C. Johnson proposes a system to
address the issue of IP anonymity in which: (1) honest
users remain anonymous and their requests are
unlinkable; (2) a server can file a complaint about a
specific anonymous user and gain the ability to
blacklist the user for future connections; (3) the
accesses made by the blacklisted user prior to the
complaint remain anonymous; and (4) users are aware
of their blacklist status prior to accessing a service.
These characteristics make our system independent of
the misbehaviour definitions used by other servers
(Johnson al 2007).
3 PURPOSED OF NYMBLE
In order to make its implementation feasible, it also
offers the Sybil attack, anonymous authentication,
backward unlink capability, subjective blacklisting,
quick authentication speeds, rate-limited anonymous
Nymble: Blocking Misbehaving Client in Anonymizing Networks
253

connections, and revocation audit ability (where users
can check whether or not they have been blacklisted).
In Nymble, users must amass a collection of
nymbles—a special kind of pseudonym—in order to
connect to Web Servers. These nymbles are logically
difficult to link in the absence of any other
information, therefore using the sequence of nymbles
mimics unauthorised access to services. However,
websites can prevent users from accessing the
resource of receiving a seed for a given nymble,
allowing them to connect with subsequent nymbles.
To handle (Joshi et al 2012) the area we can block
misbehaving clients anonymously while allowing
behaving clients to use the choices of server. We have
identified draw backs in Nymble machine and
proposed Extended Nymble system. Nymble
supervisor can blacklist a misbehaving character by
using the usage of collecting seed for a particular
nymble and linking hyperlink ability window. This
seed can be used to hyperlink future connections of
this misbehaving user. Nymble manager makes
misbehaving clients linkable for one Link
functionality window (i.e. 1day). After this
Misbehaving clients flip out to be unlikable. On the
other day if the same man or woman as soon as extra
misbehaves again he will be blacklisted, this
Misbehaving can be a normal activity. This provides
liveness closer to a threshold and protects against
denial-of-service attacks. Second, we describe how to
revoke a purchaser for a period spanning a couple of
hyperlink ability windows (Sai & Reddy 2015),
(Sasikanth 2015). This gives service providers greater
flexibility in how prolonged to block man or female
users. We moreover aspect out how our reply allows
surroundings pleasant blacklist transferability
amongst company providers. Nymble is a privacy-
enhancing technology that allows users to
authenticate themselves with online services without
revealing their identities to service providers. The
basic idea behind Nymble is to use pseudonyms,
called "nymble tokens," to authenticate users. Since
Users register with the Nymble system by providing
their real identities and a password. After registration,
the Nymble system generates a unique nymble token
for each user. The token is a cryptographic hash of the
user's real identity and a random nonce, which
changes every time the user logs in. Nymble servers
are responsible for maintaining the nymble tokens
and responding to requests from online services.
Online services register with the Nymble system by
providing their domain name and a secret key. When
a user wants to access an online service, they provide
their nymble token to the service. The service then
sends the token to the Nymble servers for validation.
The Nymble servers use the user's real identity, the
nonce, and the secret key of the online service to
verify the nymble token. If the token is valid, the
Nymble servers send a "nymble receipt" to the online
service, which allows the user to access the service
without revealing their real identity. n case a user
misbehaves, the Nymble system allows the online
service to revoke the user's nymble token, preventing
them from accessing the service in the future. Overall,
the proposed Nymble blocking system provides users
with privacy and anonymity when accessing online
services, while also allowing services to identify and
block malicious users.
3.1 Nymble - Pseudonym Manager
In this paper, we analysis the nymble used in different
paper of article. Since we used an efficient credential
system is proposed which allows only the valid users
via the routers. Here users acquire a particular kind of
alias used to access websites. The server prepares a
blacklist about the clients to the secure manager. The
secure manager provides the tickets for the users, and
that all have some certain time periods, if the users
misbehave then the server denial that connection
certainly. At first the pseudonym manager will give
the authorization rights to the users. We created an
open-source implementation that is freely accessible
with the intention of contributing a functional system.
Additionally, submit performance data to
demonstrate the viability of this technology. In
additional the users can easily checks whether their IP
is in the blacklist of the server. So it provides the high
efficiency in both user and server. The pseudonym
manager provides the authority to the user by creating
the pseudonyms, after that the user will verify by the
secure manager for the accessibility of the
anonymous network. Nymble pseudonym manager is
a component of the Nymble system that is responsible
for managing the pseudonyms, also known as nymble
tokens, used by users to authenticate themselves with
online services. The pseudonym manager generates,
stores, and revokes nymble tokens for users, ensuring
that each token is unique and cannot be linked to a
user's real identity. The pseudonym manager stores
the nymble token in a secure database, along with the
user's real identity, the nonce, and the expiration time
of the token. To ensure that nymble tokens do not
remain valid indefinitely, the pseudonym manager
sets an expiration time for each token. When a token
expires, the pseudonym manager removes it from the
database, preventing the user from using the token to
authenticate themselves. When a user logs in to an
online service using a nymble token, the pseudonym
AI4IoT 2023 - First International Conference on Artificial Intelligence for Internet of things (AI4IOT): Accelerating Innovation in Industry
and Consumer Electronics
254

manager revalidates the token to ensure that it has not
been revoked or expired. If the token is valid, the
pseudonym manager generates a nymble receipt,
which allows the user to access the service without
revealing their real identity.
Block frequently misbehaving users Nymble
blocking is a technique used to prevent misbehaving
users from accessing web services. It operates by
blocking access to specific users based on their past
behavior. Nymble blocking can be a useful method to
prevent malicious or low-quality users from
accessing a web service or to prevent them from
performing specific actions. One of the key benefits
of Nymble blocking is that it can be an efficient and
effective way to prevent misbehavior without
requiring the user to be identified. This is achieved
through the use of anonymous credentials, which
allow a user to access a service without revealing their
identity. However, if a user misbehaves, their
anonymous credential is blocked, preventing them
from accessing the service in the future. Nymble
blocking can be implemented in a variety of ways,
depending on the specific use case. One common
method is to use a blacklist of known misbehaving
users or sources. This approach involves maintaining
a list of users or sources that have been identified as
engaging in malicious or low-quality behavior and
blocking access to them. Another method is to use
reputation systems, which assign scores to users
based on their behavior, with low-scoring users being
blocked from accessing the service. It's worth noting
that while Nymble blocking can be an effective way
to prevent misbehavior, it does come with some
potential downsides. For example, it can be difficult
to accurately identify misbehaving users, and there is
a risk of false positives, where legitimate users are
mistakenly blocked. Additionally, Nymble blocking
can potentially be circumvented by determined
attackers. As such, it's important to carefully consider
the use case and potential risks before implementing
Nymble blocking.
3.2 User Authentication
This module is the basic module for every network
process; here the user should register themselves to
the admin or the controller of the particular network.
In this project the user security provider is
pseudonym manager so that will response to the user
while register into the network. In this module, every
time a user registers for the first time, the pseudo
manager creates a key value known as a pseudo
number. This number will be entered into the security
manager and used to contact the server. Actually, the
server will utilize these fictitious numbers to create a
blacklist of users who behave badly.In Nymble, user
authentication is a crucial component of the system's
ability to block misbehaving users. Nymble is a
pseudonymous system that allows users to access web
services without revealing their true identities.
However, to prevent misbehaving users from
accessing web services, Nymble requires user
authentication to ensure that only authorized users are
granted access. When a user attempts to access a web
service through Nymble, the following occur:User
authentication: The user enters their Nymble
credentials, which include a pseudonym and a secret
key. Nymble authentication: Nymble verifies the
user's credentials and generates a Nymble token,
which is a proof of the user's identity and
authorization. Access control: The user's Nymble
token is sent to the web service, which verifies the
token and grants access to the requested resource,
system, or application. If a user is found to be
misbehaving, Nymble can revoke their authorization
by adding their pseudonym to a blacklist. This
prevents the user from accessing any web services
that use Nymble authentication, even if they attempt
to create a new pseudonym. However, it's important
to note that Nymble is not designed to identify
specific misbehaving users, but rather to prevent them
from accessing web services pseudonymously.
3.3 Secure Verification
Secure verification is a critical aspect of the Nymble
blocking method, ensuring that only legitimate users
can access online services anonymously while
preventing malicious users from exploiting the
anonymity provided by the system. The Nymble
system uses various cryptographic techniques to
verify the authenticity and integrity of data, including
user identities, nymble tokens, and nymble receipts.
Here are some ways the Nymble system ensures
secure verification: Before generating a nymble
token, the Nymble system verifies a user's real
identity to prevent the creation of fake identities.
Users must provide valid credentials, such as a
username and password, to prove their identity. The
Nymble system stores the user's real identity securely
to ensure that it cannot be accessed or linked to the
nymble token. The Nymble system uses a
cryptographic hash function to generate nymble
tokens for users. The hash function takes the user's
real identity and a random nonce as input and
generates a unique token that cannot be reversed to
reveal the user's real identity. When an online service
receives a nymble token from a user, the service sends
Nymble: Blocking Misbehaving Client in Anonymizing Networks
255
the token to the Nymble system for validation. The
Nymble system checks the token's authenticity by
verifying the user's real identity, the nonce used to
generate the token, and the secret key of the online
service. This ensures that the token is valid and
belongs to the user who generated it.
When a user authenticates with an online service
using a nymble token, the service generates a nymble
receipt that includes the token and a unique nonce.
The receipt is signed by the online service using a
secret key that only the service knows. When a user
presents a nymble receipt to an online service, the
service sends the receipt to the Nymble system for
validation. The Nymble system verifies the receipt's
authenticity by checking the user's nymble token, the
nonce used to generate the receipt, and the secret key
of the online service. This ensures that the receipt is
valid and was issued by the Nymble system. the
Nymble blocking method ensures secure verification
by using robust cryptographic techniques to verify
user identities and data integrity. This provides users
with enhanced privacy and security while allowing
online services to prevent malicious activity without
compromising the anonymity of legitimate users.
4 IMPLEMENTATION & RESULT
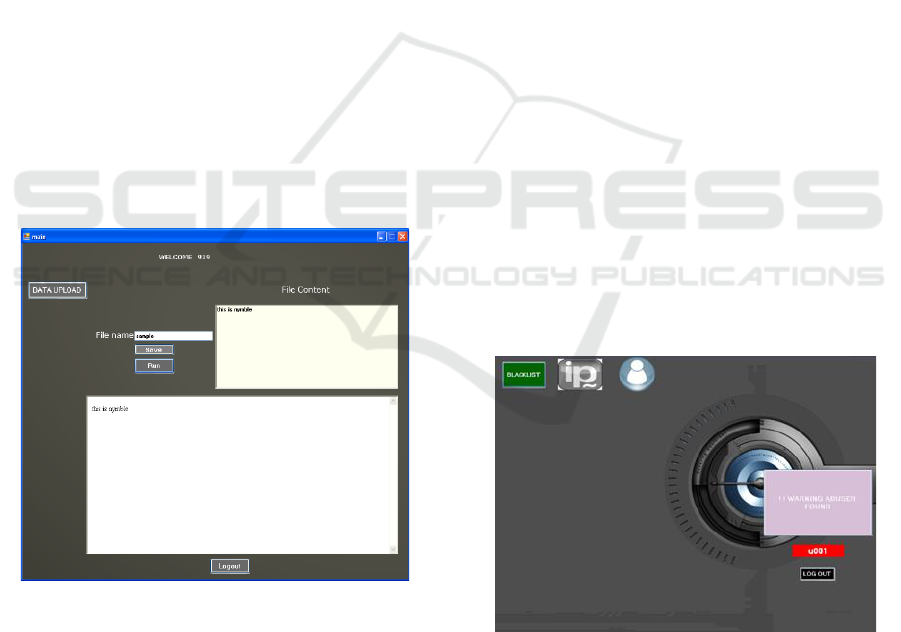
Figure 1: Data uploading, verification method.
The traditional systems system not maintain any
blacklist for the user, if once the route will denial by
the server then the user should get proper permission
again from the server, this will makes lot of
difficulties and over burden for the users. Anonymous
credential system employs the group signature, this
will helps server to revoke the abusers. There was lot
of defacing on the websites, the abusers blocks the
sites and use the every possible route to hack the data
and also to get the server permission. when the server
came to know the malicious activity about the user, it
will block the entire router and the data was already
defected. Although the abusers router blocked, the
other users was affected a lot in the traditional system.
There will be lack of data efficiency in the
anonymous network due to the several anonymity.
Data verification is an essential aspect of the
Nymble blocking system, which is designed to
prevent malicious users from exploiting the
anonymity provided by the system. The Nymble
system uses various techniques to verify the
authenticity and integrity of data, including user
identities, nymble tokens, and nymble receipts.
Before generating a nymble token, the Nymble
system verifies a user's real identity to prevent the
creation of fake identities. Users must provide valid
credentials, such as a username and password, to
prove their identity. When an online service receives
a nymble token from a user, the service sends the
token to the Nymble system for validation. The
Nymble system checks the token's authenticity by
verifying the user's real identity, the nonce used to
generate the token, and the secret key of the online
service. This ensures that the token is valid and
belongs to the user who generated it. The Nymble
system regularly checks the revocation status of
nymble tokens to prevent revoked tokens from being
used for authentication. When a user presents a
revoked token or a token that has expired, the Nymble
system rejects the token, preventing the user from
accessing the online service.
Figure 2: Blocking misused id.
Pseudonymous authentication system: Implement
a pseudonymous authentication system that allows
users to access web services without revealing their
true identity. This system should generate
pseudonyms and secret keys for each user, and use
these credentials to verify the user's identity when
AI4IoT 2023 - First International Conference on Artificial Intelligence for Internet of things (AI4IOT): Accelerating Innovation in Industry
and Consumer Electronics
256

they attempt to access a web service misbehaving
user blacklist which maintain a blacklist of
misbehaving users who have violated the terms of
service or engaged in other forms of misbehavior.
This blacklist should include the pseudonyms of these
users and should be regularly updated to ensure that
only misbehaving users are blocked.
Figure 3: Token key access.
Revocation mechanism when a user is found to be
misbehaving, revoke their authorization by adding
their pseudonym to the blacklist. This prevents the
user from accessing any web services that use
Nymble authentication, even if they attempt to create
a new pseudonym. Integration with web services.
Integrate Nymble blocking with web services that
require user authentication. This integration should
include a mechanism for verifying the user's Nymble
token and checking the blacklist to ensure that the
user is not misbehaving. It's important to note that
implementing Nymble blocking requires careful
consideration of privacy concerns and the potential
impact on user behavior. Additionally, the
effectiveness of Nymble blocking may depend on the
quality of the blacklist and the ability to detect and
prevent misbehaving behavior.
5 CONCLUSIONS
Nymble blocking is a pseudonymous authentication
system that is designed to prevent misbehaving users
from accessing web services. It does this by requiring
users to authenticate themselves pseudonymously
and maintaining a blacklist of misbehaving users.
When a user is found to be misbehaving, Nymble can
revoke their authorization, preventing them from
accessing any web services that use Nymble
authentication. Nymble blocking is a useful tool for
web service providers who want to protect their
systems from malicious users while preserving user
privacy. However, it is important to note that Nymble
blocking is not foolproof and may require ongoing
efforts to maintain the blacklist and improve the
system's ability to detect and prevent misbehaving
behavior. Nymble blocking is a valuable addition to
the suite of tools available for protecting web services
from malicious users, and it can help ensure the
security and integrity of sensitive information and
critical systems. the Nymble blocking system is an
innovative approach to online privacy that allows
users to authenticate themselves anonymously while
providing online services with the ability to revoke
access to malicious users. The system achieves this
by using pseudonyms, also known as nymble tokens,
which are generated for each user and cannot be
linked to their real identity. The Nymble system
provides several benefits, including enhanced privacy
for users, reduced risk of online identity theft, and
improved security for online services. Users can
authenticate themselves without revealing their real
identity, protecting them from online tracking and
surveillance. Additionally, online services can revoke
access to malicious users without knowing their real
identity, reducing the risk of identity theft and
cyberattacks. The Nymble system also addresses
some of the limitations of other privacy-enhancing
technologies, such as Tor, by providing online
services with the ability to block malicious users
while preserving the anonymity of legitimate users.
This makes it a valuable tool for online businesses
and organizations that need to protect their networks
from malicious actors. Overall, the Nymble blocking
system represents a significant step forward in online
privacy and security, providing users with enhanced
anonymity and online services with better tools to
prevent malicious activity. With continued
development and adoption, the Nymble system has
the potential to revolutionize the way we approach
online identity and privacy.
REFERENCES
Prasad, M. D., Reddy, P. C., & Samya, B. (2013). Extended
Nymble: Method for Tracking Misbehaving Users
Anonymosly while Blocking. AIRCC's International
Journal of Computer Science and Information
Technology, 87-93.
Patro, S., & Ambhaikar, (2012) A. Privacy Preserving
Technique for Blocking Misbehaviors in Anonymous
Networks.
Joshi, A., Shaikh, A., Kadam, A., & Sahu, V. (2012).
NYMBLE BLOCKING SYSTEM. International
Journal of Computer Science and Engineering Survey,
3(2), 57.
Nymble: Blocking Misbehaving Client in Anonymizing Networks
257

Sai, S. N., & Reddy, D. B. V. R. (2015). Detecting Malware
Behavior in DTN’s Networks using Dogmatic and
Look-Ahead Approaches.
Sasikanth, K. V. K., & Raju, K. S. (2015). Detection of
Behavioral Malware in Delay Tolerant Networks,
IJSEAT, Vol.3, Issue 8.
Tyrlis, E., Bader, J., Manzini, E., & Matei, D. (2021).
Reconciling different methods of high‐latitude blocking
detection. Quarterly Journal of the Royal
Meteorological Society, 147(735), 1070-1096.
Chen, B. L., Jiang, W. X., Chen, Y. X., Chen, L., Wang, R.
J., Han, S., ...& Zhang, Y. C. (2022). Influence blocking
maximization on networks: Models, methods and
applications. Physics Reports, 976, 1-54.
Gupta, S. K., Malik, V., Gupta, A. K., & Andrews, J. G.
(2022). Impact of blocking correlation on the
performance of mmwave cellular networks. IEEE
Transactions on Communications, 70(7), 4925-4939.
Tsang, P. P., Kapadia, A., & Smith, S. W. (2006).
Anonymous IP-address Blocking in Tor with Trusted
Computing (Short Paper: Work in Progress).
Proceedings of WATC.
Johnson, P. C., Kapadia, A., Tsang, P. P., & Smith, S. W.
(2007). Nymble: Anonymous IP-address blocking. In
Privacy Enhancing Technologies: 7th International
Symposium, PET 2007 Ottawa, Canada, June 20-22,
2007 Revised Selected Papers 7 (pp. 113-133). Springer
Berlin Heidelberg..
AI4IoT 2023 - First International Conference on Artificial Intelligence for Internet of things (AI4IOT): Accelerating Innovation in Industry
and Consumer Electronics
258
